Security in Wireless Personal Area Networks Wireless personal













- Slides: 28

Security in Wireless Personal Area Networks

Wireless personal area networks (WPANs) provide connectivity between nodes that are relatively close, within 10 m. WPANs function as an alternative to a cable, e. g. , linking a wireless headphone to a portable CD player. Bluetooth is an industry standard protocol for WPANs and is now developed as one of the IEEE 802 standards [IEEE 802. 15]. 1/7/2022 2

Bluetooth specifications There are three classes of Bluetooth transmission: Class 1: 100 m. W (+20 d. Bm) max (100 m range) Class 2: 2. 5 m. W (+4 d. Bm) max Class 3: 1 m. W (0 d. Bm) max (10 m range) 1/7/2022 3

Bluetooth network terms Master Slave Piconet Scatternet (Multipoint) 1/7/2022 4

Bluetooth node states. Hold. Devices placed in hold mode are completely inactive, except for an internal timer that determines when the device leaves hold mode and resumes normal operation. The master places a slave in hold mode; a slave also can request that its master place it in hold mode. This is used for low-power nodes. 1/7/2022 5

Park. Devices in park mode remain synchronized to the piconet but have no 3 -bit piconet address and do not participate in the piconet. They listen to traffic from the master in order to resynchronize with the piconet and receive broadcast messages. The master places nodes in and out of the park state 1/7/2022 6

Sniff. Devices in sniff mode listen to the piconet at a reduced rate, thus saving power. 1/7/2022 7

Bluetooth security mechanisms Bluetooth has several mechanisms to provide security. First, the transmitters use the lowest power required for their data to be received. This means that intruder nodes farther away from the transmitter than the receiver is find the signal to be weak at best. This requires the intruder to be in very close physical proximity, which may expose the intruder to a higher risk of detection than he is willing to accept. In truth, this mechanism was designed to save power and increase the life of the device, but it also has the fortunate side effect of increasing physical security 1/7/2022 8

Channel hopping provides additional protection, making it difficult to snoop on the data stream. The fast rate of hopping makes it hard for a casual observer to “sniff ” the data stream off of one channel or guess the hopping sequence. Again, this mechanism was not designed for security but instead was designed to allow many nodes to share the same frequency bands without interfering with each other. 1/7/2022 9

Data are protected by the optional use of encryption. The encryption algorithm is, essentially, a stream cipher that XORs the data stream with a stream of numbers from a pseudorandom-number generator (PRNG) seeded by an encryption key. 1/7/2022 10

Bluetooth Security Modes Bluetooth defines three modes of security for devices: Non secure. A device in the non secure mode does not initiate any security procedure. This is intended for public use devices, such as a walkup printer. Service-level enforced security. A device in the service-level enforced security mode permits access to itself depending on the service request. For example, a PC may allow a user to download files to it but does not allow its own files to be read. Link-level enforced security. A device in the link-level enforced security mode requires authentication and authorization for use, e. g. , cell phones. 1/7/2022 11

Basic Security Mechanisms Bluetooth uses encryption and link-layer keys. Encryption keys protect the data in a session, whereas link-layer keys provide authentication and serve as a parameter when deriving the encryption keys. Linklayer key lifetimes are either semi permanent or temporary. Semi permanent keys can be used after the current session to authenticate Bluetooth devices. Temporary keys can be used only during the current session; they are often used in point-to-multipoint communication in which the same information is transmitted to several recipients. 1/7/2022 12

Four entities are used for link-layer security: A 48 -bit publicly available device address, fixed and unique for each device A 128 -bit pseudorandom private key for authentication An 8 - to 128 -bit private key for encryption (The variable length accommodates different countries’ export restrictions. ) A 128 -bit pseudorandom number generated by the device 1/7/2022 13

The four basic types of link-layer keys used in Bluetooth security are: The initialization key is used as a link-layer key when there are not yet any unit or combination keys. This key is used only during installation and typically requires the user to enter a personal identification number (PIN) on the unit. The unit key is generated in each device when the device is installed and is stored in nonvolatile memory and (almost) never changed. 1/7/2022 14

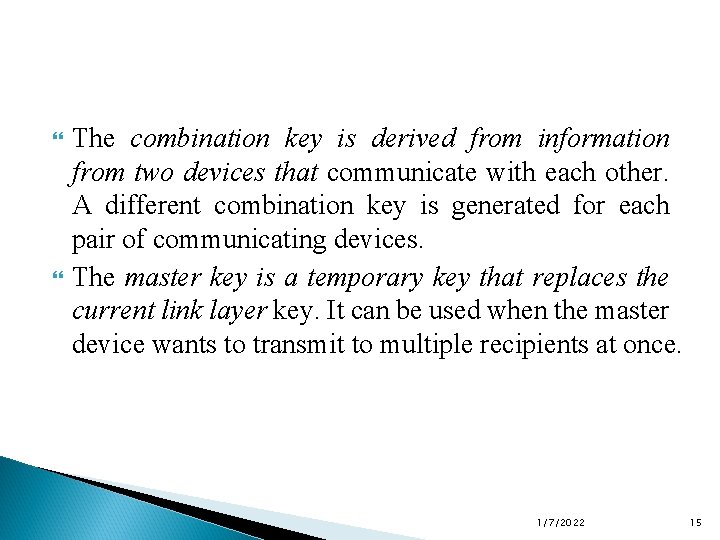
The combination key is derived from information from two devices that communicate with each other. A different combination key is generated for each pair of communicating devices. The master key is a temporary key that replaces the current link layer key. It can be used when the master device wants to transmit to multiple recipients at once. 1/7/2022 15

1/7/2022 16

1/7/2022 17

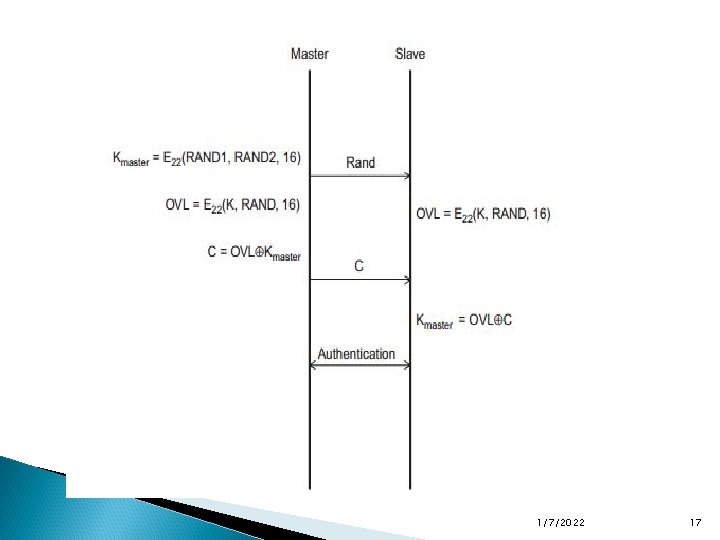
Encryption There are three modes for Bluetooth encryption: In the first mode, nothing is encrypted. In the second mode, broadcast traffic is not encrypted, but individually addressed traffic is encrypted with the master key. In the third mode, all traffic is encrypted with the master key. 1/7/2022 18

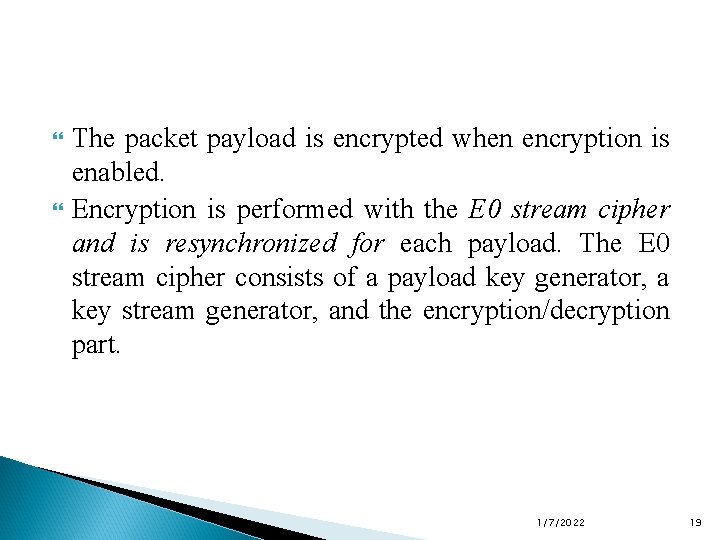
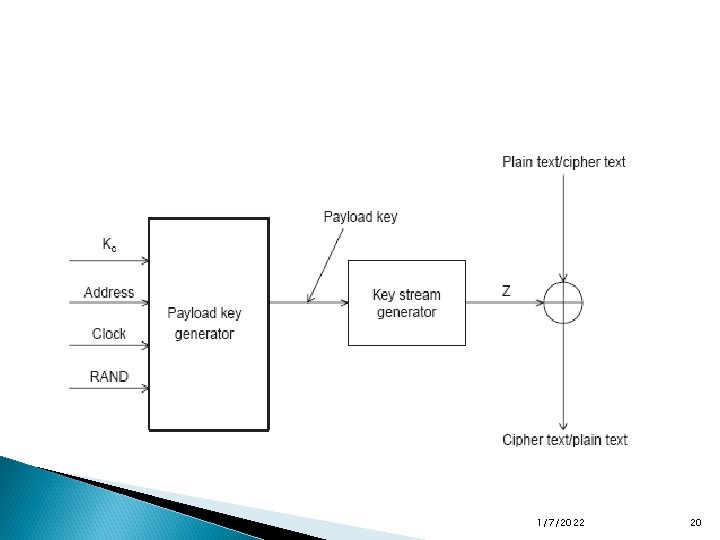
The packet payload is encrypted when encryption is enabled. Encryption is performed with the E 0 stream cipher and is resynchronized for each payload. The E 0 stream cipher consists of a payload key generator, a key stream generator, and the encryption/decryption part. 1/7/2022 19

1/7/2022 20

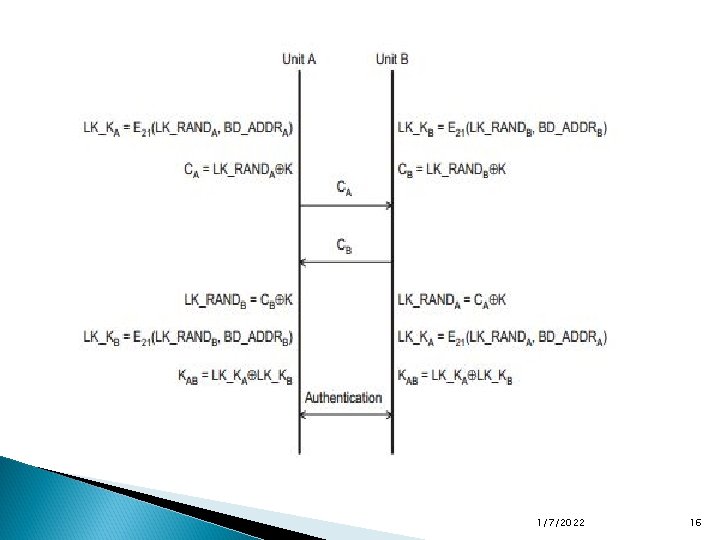
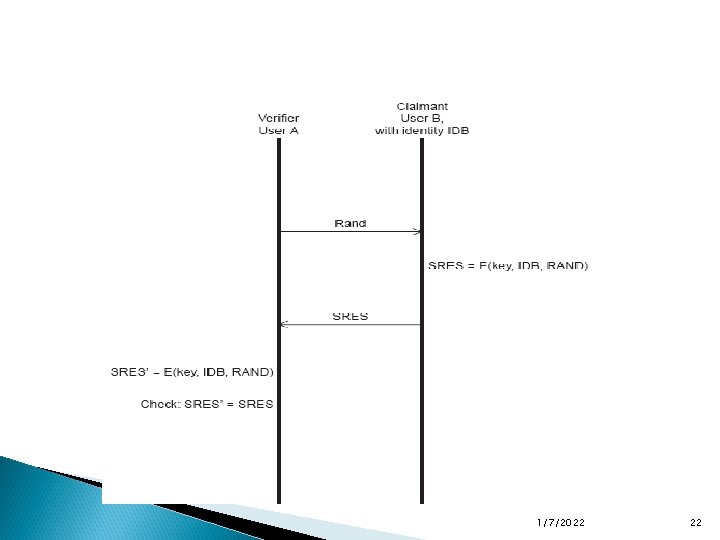
Authentication Bluetooth authentication uses a challenge/response protocol with symmetric encryption and shared secrets. If unit A wants to verify unit B’s claim of identity, unit A sends a challenge to unit B. Unit B encrypts the challenge and sends the result back as a response. Unit A also encrypts the challenge and then compares it with the response it receives from unit B. If they match, then they both share the same secret key, and thus unit A has authenticated unit B. If unit B wants to authenticate unit A, then the process repeats, with unit B sending a (different) challenge to unit A 1/7/2022 21

1/7/2022 22

The challenge is a random number that becomes an input to the encryption algorithm E 1. The algorithm takes two other inputs, the Bluetooth device address of the “claimant” (unit B) and the link -layer key, which is the shared secret. The E 1 function produces a value, the authenticated ciphering offset (ACO), that is used as a parameter for the encryption key generation if authentication is successful. 1/7/2022 23

Limitations and Problems Since Bluetooth uses the unlicensed 2. 4 -GHz radio band. it is susceptible to both unintentional and intentional jamming. Other devices that operate in the same band, including some 802. 11 and home/RF devices, as well as microwave ovens, could interfere with signal reception. The signals also could be jammed intentionally by transmitters that are nearby or significantly stronger than the Bluetooth transmitters. However, the low power requirements and signal hopping make Bluetooth more resilient to casual jamming. 1/7/2022 24

Other problems include key management. Until a secure link is established, the keys and data used to derive them are sent in the clear. The only mitigation is to use a PIN code entered into each device, but this can be cumbersome. Bluetooth supports only device authentication, not user authentication. Thus, a stolen device, such as a PDA, could gain unauthorized access to data and resources unless the applications themselves provide an additional layer of security. 1/7/2022 25

Bluetooth Attacks In addition to the previously discussed limitations, Bluetooth is vulnerable to a number of attacks. If two sites, A and B, communicate with each other using A’s unit key (KA) because of limited memory on A, then afterwards site B can impersonate A as well as eavesdrop on A’s communications because B knows that the key that will be used. Variations of a man in-the-middle attack are possible. If an attacker can synchronize with the frequencyhopping sequence, then it can eavesdrop. 1/7/2022 26

The secrecy of the combination key depends on the PIN, which is 1 to 16 characters long and typically has a default value of zero. Many PINs are only four characters long, so brute-force attacks against the PIN are quite feasible. It should be noted that short PINs are a problem in the implementation and use, not in the Bluetooth specification. 1/7/2022 27

These authors also describe another type of attack in which the location and movements of the victim are tracked rather than the content of the data. For example, tracker devices could be installed at airports and train stations and record the IDs of all Bluetooth devices that pass. When fed to a central repository, attackers would build up a picture of people’s movements as well as their current location. 1/7/2022 28