Using MIS 10 th Edition Chapter 10 Information



















- Slides: 48

Using MIS 10 th Edition Chapter 10 Information Systems Security Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -1

“I think you’ll see that we really do take security seriously. ” • Video conference with exercise equipment manufacturer Canyon. Back Fitness (potential ARES partner). • Security concerns about integrating ARES with Canyon. Back exercise bikes. • Does ARES systems have acceptable level of security? • Can their bikes get hacked? Customers hurt? Personal data stolen? Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -2

“I think you’ll see that we really do take security seriously. ” (cont’d) • ARES implements secure coding practices and secure data backup. • Users interact with radio buttons, dropdown menus, and other interactive AR elements. • Reduces the possibility of an SQL injection attack. • New technology typically brings new risks. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -3

Study Questions Q 10 -1 What is the goal of information systems security? Q 10 -2 How big is the computer security problem? Q 10 -3 How should you respond to security threats? Q 10 -4 How should organizations respond to security threats? Q 10 -5 How can technical safeguards protect against security threats? Q 10 -6 How can data safeguards protect against security threats? Q 10 -7 How can human safeguards protect against security threats? Q 10 -8 How should organizations respond to security incidents? Q 10 -9 2027? Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -4

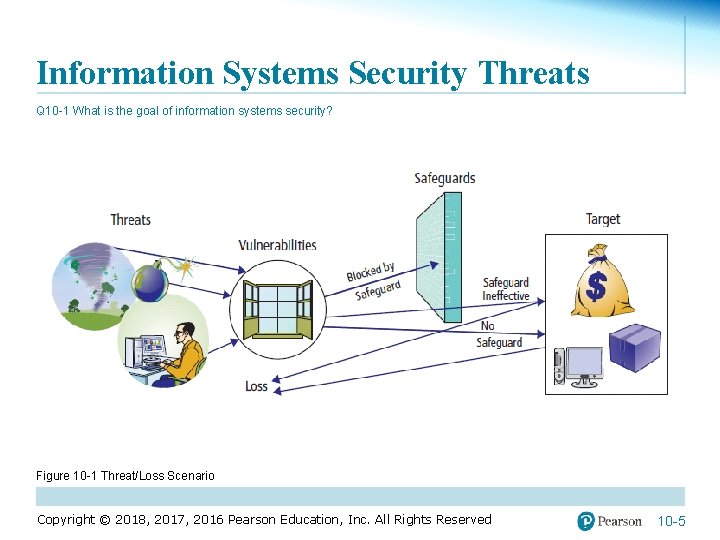
Information Systems Security Threats Q 10 -1 What is the goal of information systems security? Figure 10 -1 Threat/Loss Scenario Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -5

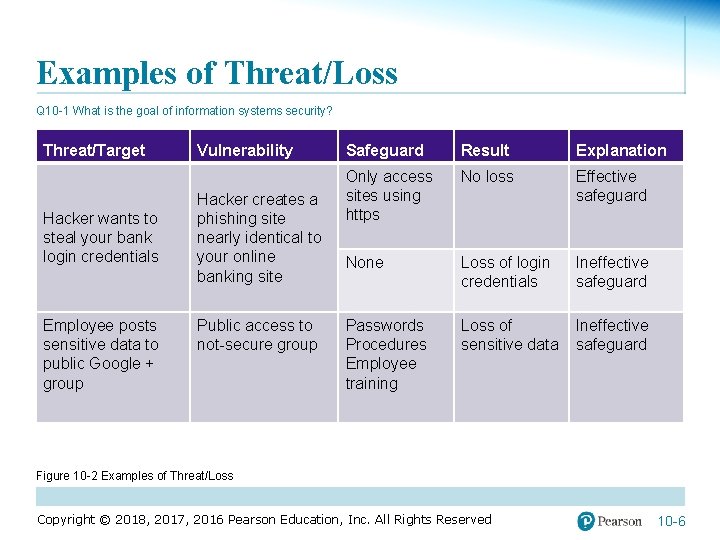
Examples of Threat/Loss Q 10 -1 What is the goal of information systems security? Threat/Target Hacker wants to steal your bank login credentials Employee posts sensitive data to public Google + group Vulnerability Hacker creates a phishing site nearly identical to your online banking site Public access to not-secure group Safeguard Result Explanation Only access sites using https No loss Effective safeguard None Loss of login credentials Ineffective safeguard Passwords Procedures Employee training Loss of sensitive data Ineffective safeguard Figure 10 -2 Examples of Threat/Loss Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -6

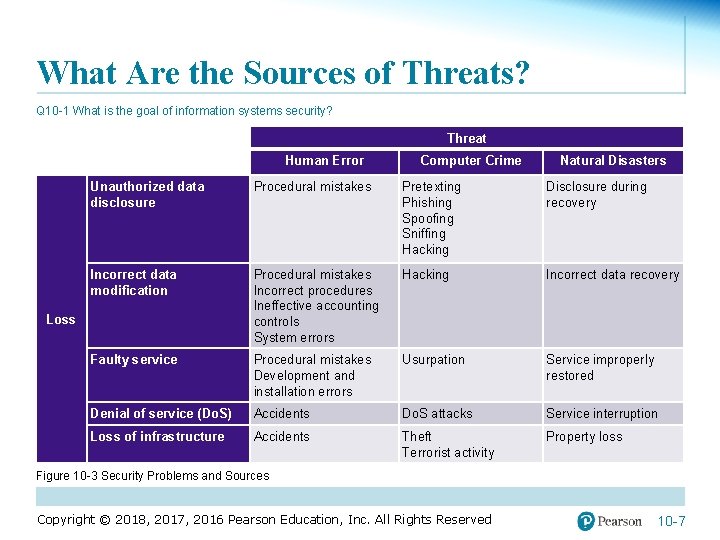
What Are the Sources of Threats? Q 10 -1 What is the goal of information systems security? Threat Human Error Computer Crime Natural Disasters Unauthorized data disclosure Procedural mistakes Pretexting Phishing Spoofing Sniffing Hacking Disclosure during recovery Incorrect data modification Procedural mistakes Incorrect procedures Ineffective accounting controls System errors Hacking Incorrect data recovery Faulty service Procedural mistakes Development and installation errors Usurpation Service improperly restored Denial of service (Do. S) Accidents Do. S attacks Service interruption Loss of infrastructure Accidents Theft Terrorist activity Property loss Loss Figure 10 -3 Security Problems and Sources Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -7

What Types of Security Loss Exists? Q 10 -1 What is the goal of information systems security? • Unauthorized Data Disclosure – Pretexting – Phishing – Spoofing § IP spoofing § Email spoofing – Drive-by sniffers § Wardrivers – Hacking – Natural disasters Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -8

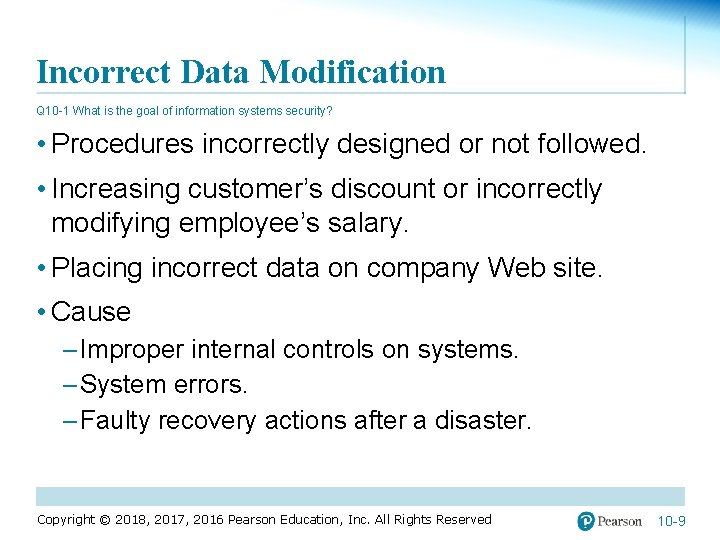
Incorrect Data Modification Q 10 -1 What is the goal of information systems security? • Procedures incorrectly designed or not followed. • Increasing customer’s discount or incorrectly modifying employee’s salary. • Placing incorrect data on company Web site. • Cause – Improper internal controls on systems. – System errors. – Faulty recovery actions after a disaster. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -9

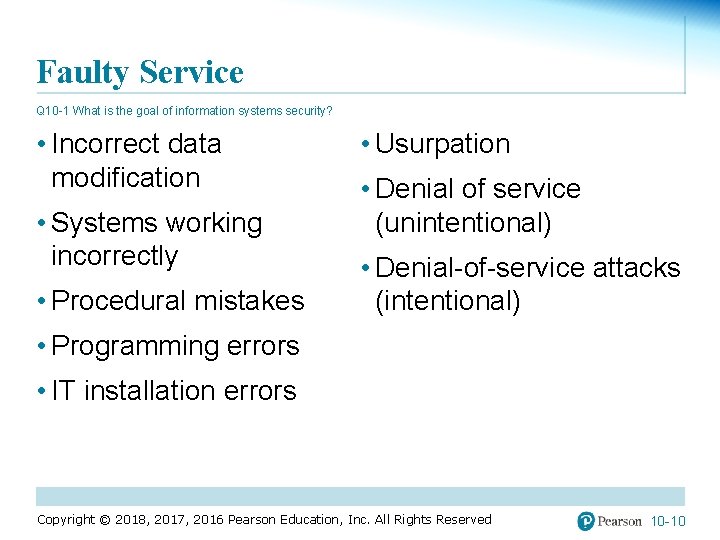
Faulty Service Q 10 -1 What is the goal of information systems security? • Incorrect data modification • Systems working incorrectly • Procedural mistakes • Usurpation • Denial of service (unintentional) • Denial-of-service attacks (intentional) • Programming errors • IT installation errors Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -10

Loss of Infrastructure Q 10 -1 What is the goal of information systems security? • Human accidents • Theft and terrorist events • Disgruntled or terminated employee • Natural disasters • Advanced Persistent Threat – APT 29 (Russia) and Deep Panda (China) – Theft of intellectual property from U. S. firms. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -11

Goal of Information Systems Security Q 10 -1 What is the goal of information systems security? • Find appropriate trade-off between risk of loss and cost of implementing safeguards. • Protective actions – Use antivirus software. – Delete browser cookies? – Make appropriate trade-offs to protect yourself and your business. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -12

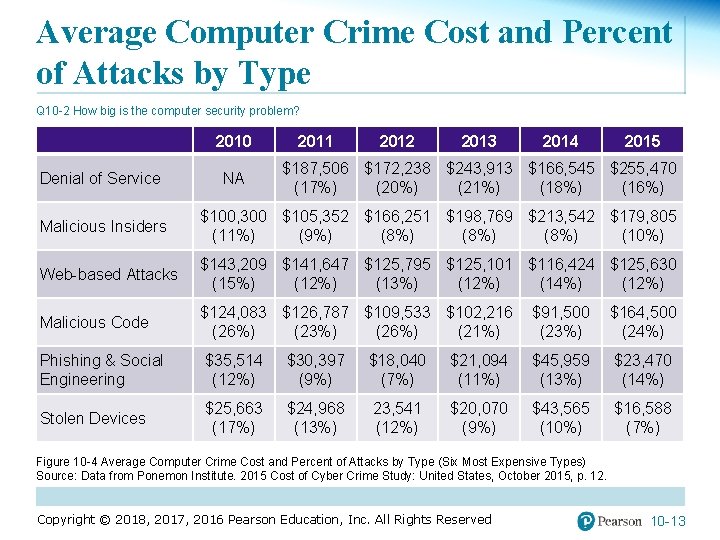
Average Computer Crime Cost and Percent of Attacks by Type Q 10 -2 How big is the computer security problem? Denial of Service 2010 NA 2011 2012 2013 2014 2015 $187, 506 $172, 238 $243, 913 $166, 545 $255, 470 (17%) (20%) (21%) (18%) (16%) Malicious Insiders $100, 300 $105, 352 $166, 251 $198, 769 $213, 542 $179, 805 (11%) (9%) (8%) (10%) Web-based Attacks $143, 209 $141, 647 $125, 795 $125, 101 $116, 424 $125, 630 (15%) (12%) (13%) (12%) (14%) (12%) Malicious Code $124, 083 $126, 787 $109, 533 $102, 216 (26%) (23%) (26%) (21%) $91, 500 (23%) $164, 500 (24%) Phishing & Social Engineering $35, 514 (12%) $30, 397 (9%) $18, 040 (7%) $21, 094 (11%) $45, 959 (13%) $23, 470 (14%) Stolen Devices $25, 663 (17%) $24, 968 (13%) 23, 541 (12%) $20, 070 (9%) $43, 565 (10%) $16, 588 (7%) Figure 10 -4 Average Computer Crime Cost and Percent of Attacks by Type (Six Most Expensive Types) Source: Data from Ponemon Institute. 2015 Cost of Cyber Crime Study: United States, October 2015, p. 12. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -13

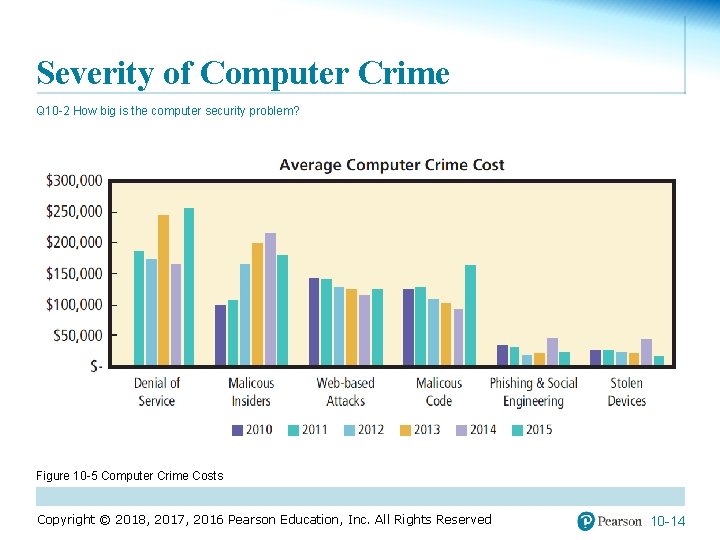
Severity of Computer Crime Q 10 -2 How big is the computer security problem? Figure 10 -5 Computer Crime Costs Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -14

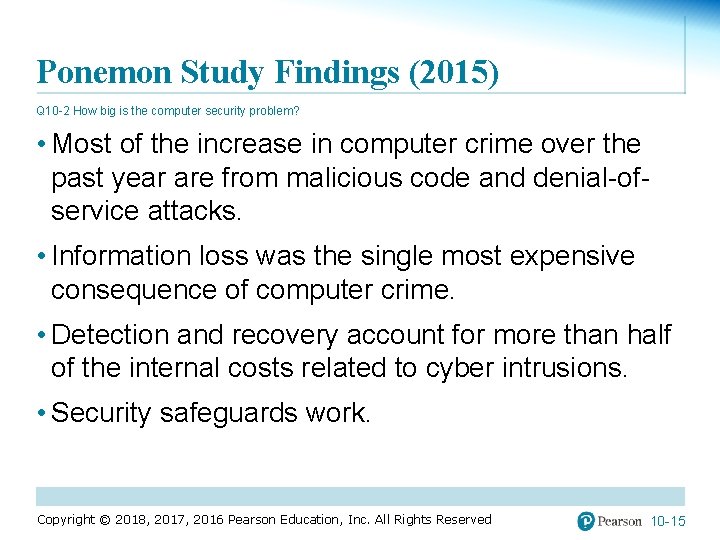
Ponemon Study Findings (2015) Q 10 -2 How big is the computer security problem? • Most of the increase in computer crime over the past year are from malicious code and denial-ofservice attacks. • Information loss was the single most expensive consequence of computer crime. • Detection and recovery account for more than half of the internal costs related to cyber intrusions. • Security safeguards work. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -15

Personal Security Safeguards Q 10 -3 How should you respond to security threats? Figure 10 -6 Personal Security Safeguards Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -16

New from Black Hat 2015 So What? • Briefings on how to hack things. • Show to exploit weaknesses in hardware, software, protocols, or systems including smartphones, Io. T devices, cars, etc. • Encourage companies to fix product vulnerabilities. • Serves as educational forum for hackers, developers, manufacturers, and government agencies. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -17

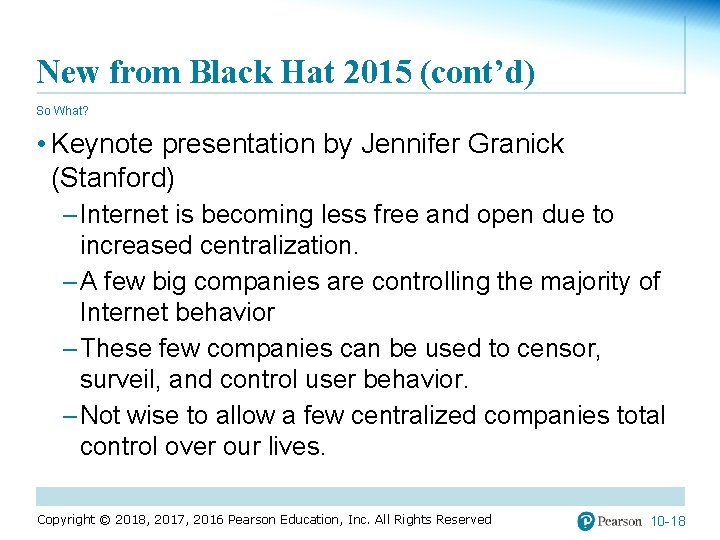
New from Black Hat 2015 (cont’d) So What? • Keynote presentation by Jennifer Granick (Stanford) – Internet is becoming less free and open due to increased centralization. – A few big companies are controlling the majority of Internet behavior – These few companies can be used to censor, surveil, and control user behavior. – Not wise to allow a few centralized companies total control over our lives. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -18

Security Policies Q 10 -4 How should organizations respond to security threats? • Senior management creates company-wide policies: – What sensitive data will be stored? – How will data be processed? – Will data be shared with other organizations? – How can employees and others obtain copies of data stored about them? – How can employees and others request changes to inaccurate data? • Senior management manages risks. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -19

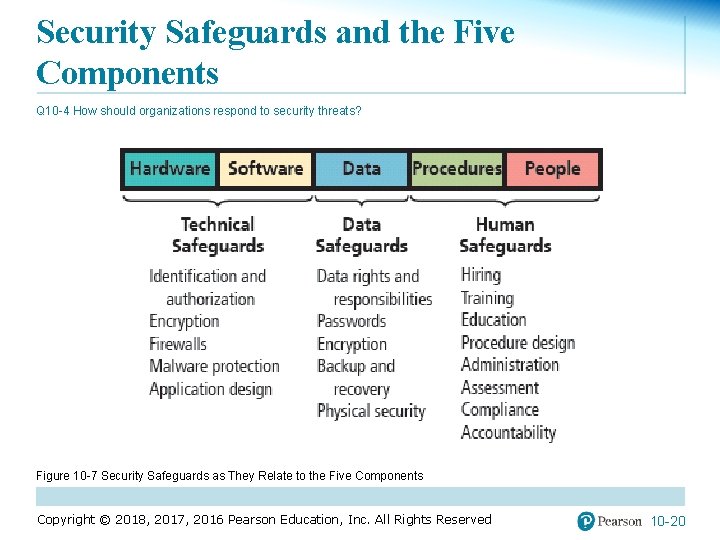
Security Safeguards and the Five Components Q 10 -4 How should organizations respond to security threats? Figure 10 -7 Security Safeguards as They Relate to the Five Components Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -20

Securing Privacy Ethics Guide • “The best way to solve a problem is not to have it. ” – Resist providing sensitive data. – Don’t collect data you don’t need. • Gramm-Leach-Bliley (GLB) Act, 1999 • Privacy Act of 1974 • Health Insurance Portability and Accountability Act (HIPAA), 1996 • Australian Privacy Act of 1988 – Government, healthcare data, records maintained by businesses with revenues in excess of AU$3 million. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -21

Securing Privacy: Wrap Up Ethics Guide • Business professionals must consider legality, ethics, and wisdom when requesting, storing, or disseminating data. • Think carefully about email you open over public, wireless networks. • Use long, strong passwords. • If unsure, don’t give the data. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -22

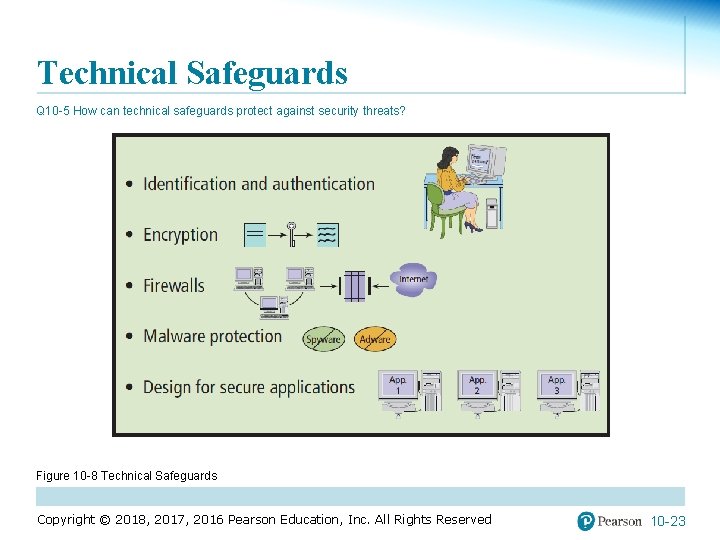
Technical Safeguards Q 10 -5 How can technical safeguards protect against security threats? Figure 10 -8 Technical Safeguards Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -23

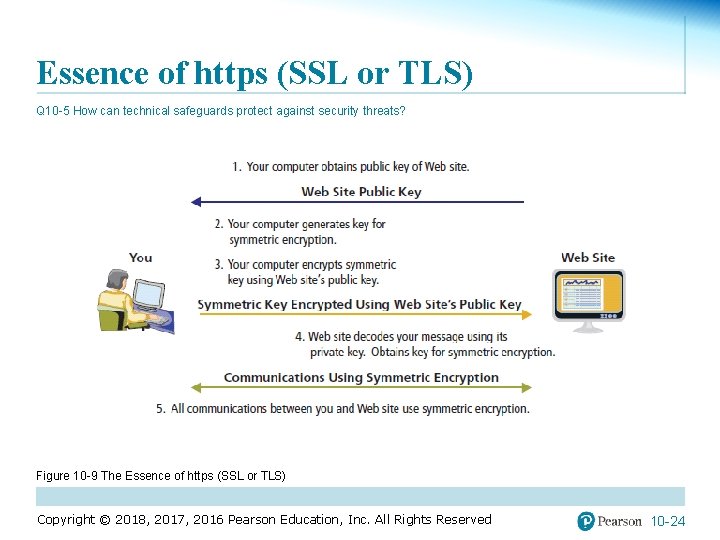
Essence of https (SSL or TLS) Q 10 -5 How can technical safeguards protect against security threats? Figure 10 -9 The Essence of https (SSL or TLS) Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -24

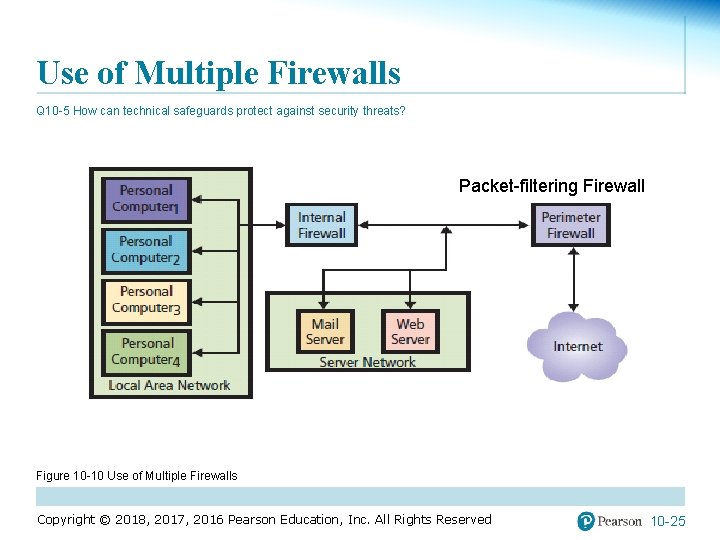
Use of Multiple Firewalls Q 10 -5 How can technical safeguards protect against security threats? Packet-filtering Firewall Figure 10 -10 Use of Multiple Firewalls Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -25

Malware Protection (Viruses, Spyware, Adware) Q 10 -5 How can technical safeguards protect against security threats? 1. Antivirus and antispyware programs. 2. Scan frequently. 3. Update malware definitions. 4. Open email attachments only from known sources. 5. Install software updates. 6. Browse only reputable Internet neighborhoods. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -26

Spyware/Adware Symptoms and Types of Malware Q 10 -5 How 10 -11 can technical safeguards protect against security threats? Figure Spyware and Adware Symptoms • Malware – Viruses – Trojan horses – Worms – Spyware – Adware – Ransomware – Payload Figure 10 -11 Spyware and Adware Symptoms Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -27

Design for Secure Applications Q 10 -5 How can technical safeguards protect against security threats? • SQL injection attack – User enters SQL statement into a form instead of a name or other data. – Result § SQL code becomes part of database commands issued. § Improper data disclosure, data damage and loss possible. – Well designed applications make injections ineffective. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -28

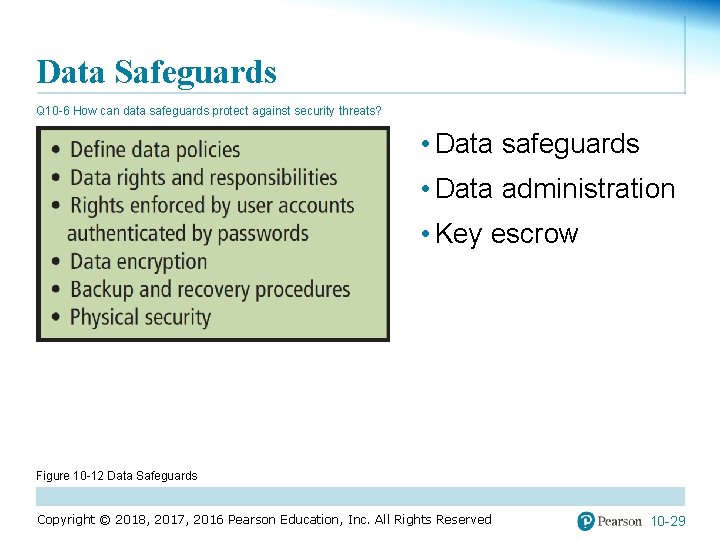
Data Safeguards Q 10 -6 How can data safeguards protect against security threats? • Data safeguards • Data administration • Key escrow Figure 10 -12 Data Safeguards Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -29

Security Policies for In-House Staff Q 10 -7 How can human safeguards protect against security threats? • Position definition – Separate duties and authorities – Determine least privilege – Document position sensitivity • Hiring and screening Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -30

Security Policies for In-House Staff (cont’d) Q 10 -7 How can human safeguards protect against security threats? • Dissemination and enforcement – Responsibility – Accountability – Compliance • Termination – Friendly – Unfriendly Figure 10 -13 Security Policy for In-House Staff Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -31

Human Safeguards for Nonemployee Personnel Q 10 -7 How can human safeguards protect against security threats? • Temporary personnel, vendors, partner personnel (employees of business partners), and the public. • Require vendors and partners to perform appropriate screening and security training. • Contract specifies security responsibilities. • Provide accounts and passwords with least privilege and remove accounts as soon as possible. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -32

Public Users Q 10 -7 How can human safeguards protect against security threats? • Web sites and other openly accessible information systems. – Hardening § Special versions of operating system. § Lock down or eliminate operating systems features and functions not required by application. – Protect such users from internal company security problems. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -33

Account Administration Q 10 -7 How can human safeguards protect against security threats? • Account Management – Standards for new user accounts, modification of account permissions, removal of unneeded accounts. • Password Management – Users change passwords frequently. • Help Desk Policies – Provide means of authenticating users. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -34

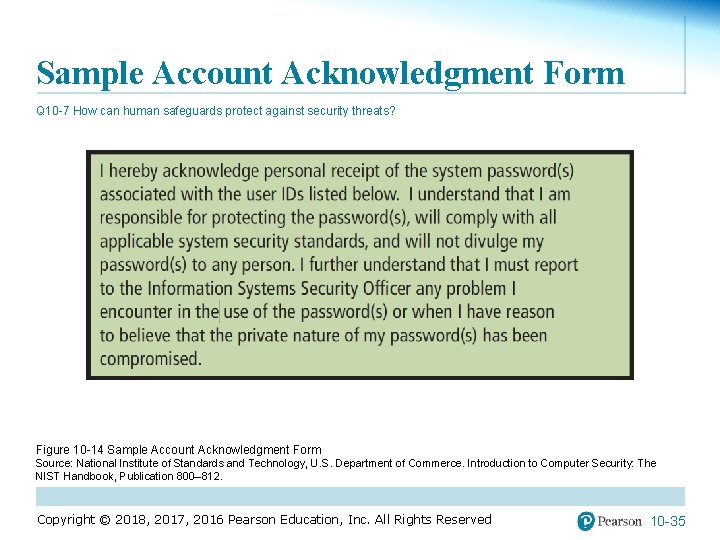
Sample Account Acknowledgment Form Q 10 -7 How can human safeguards protect against security threats? Figure 10 -14 Sample Account Acknowledgment Form Source: National Institute of Standards and Technology, U. S. Department of Commerce. Introduction to Computer Security: The NIST Handbook, Publication 800– 812. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -35

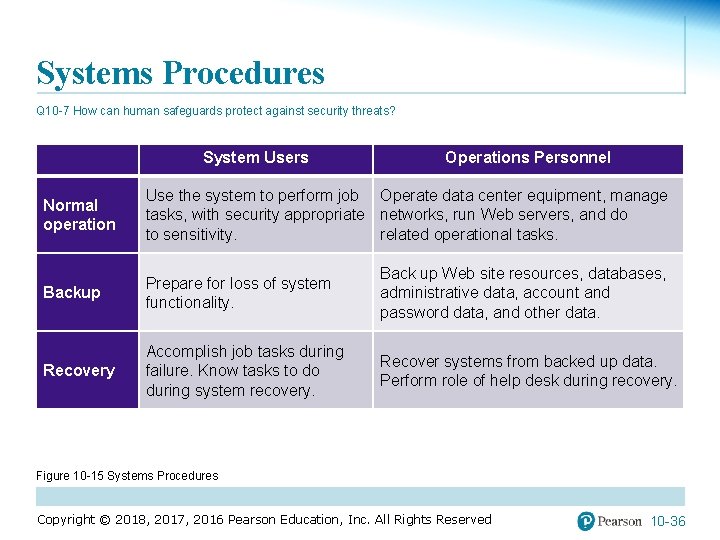
Systems Procedures Q 10 -7 How can human safeguards protect against security threats? System Users Operations Personnel Normal operation Use the system to perform job Operate data center equipment, manage tasks, with security appropriate networks, run Web servers, and do to sensitivity. related operational tasks. Backup Prepare for loss of system functionality. Back up Web site resources, databases, administrative data, account and password data, and other data. Recovery Accomplish job tasks during failure. Know tasks to do during system recovery. Recover systems from backed up data. Perform role of help desk during recovery. Figure 10 -15 Systems Procedures Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -36

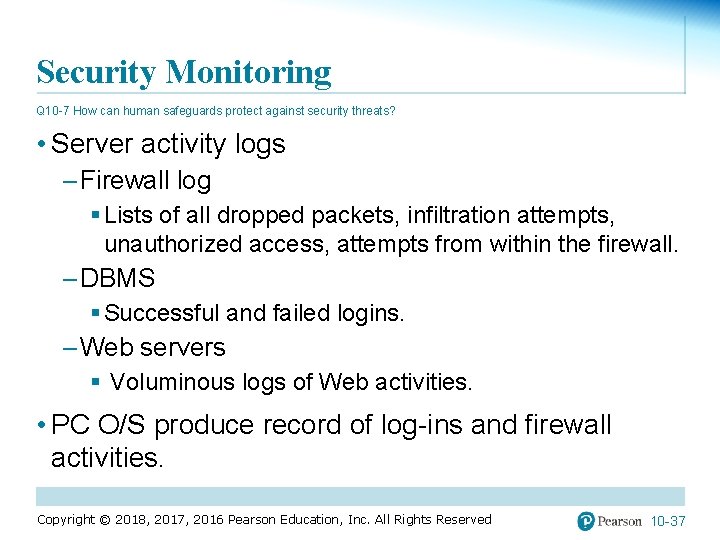
Security Monitoring Q 10 -7 How can human safeguards protect against security threats? • Server activity logs – Firewall log § Lists of all dropped packets, infiltration attempts, unauthorized access, attempts from within the firewall. – DBMS § Successful and failed logins. – Web servers § Voluminous logs of Web activities. • PC O/S produce record of log-ins and firewall activities. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -37

Security Monitoring (cont’d) Q 10 -7 How can human safeguards protect against security threats? • Employ utilities to assess vulnerabilities. • Honeypots for computer criminals to attack. • Investigate security incidents. • Constantly monitor to determine adequacy of existing security policy and safeguards. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -38

Factors in Incident Response Q 10 -8 How should organizations respond to security incidents? Figure 10 -16 Factors in Incident Response Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -39

Information Systems Security in 2027 Q 10 -9 2027? • APTs more common. • Concern about balance of national security and data privacy. • Security on devices will be improved. • Skill level of cat-and-mouse activity increases substantially. • Improved security at large organizations. • Strong local “electronic” sheriffs. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -40

Exhaustive Cheating Security Guide • Employees (possibly managers) created deceptive software to cheat standardized emissions testing. • Black-box software made it difficult to detect the malicious software. • Embedded software was designed to: – Temporarily improve fuel savings – Reduce torque and acceleration • When normal performance resumed, emissions output rose well above legal levels. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -41

IT Security Analyst Career Guide Stefanie at Overstock. com Q. What attracted you to this field? A. “I was first attracted to the field of IT security as a sophomore in college when I took my initial MIS class. In one session, the professor deployed a honeypot, and we watched as attackers scanned the system for vulnerabilities. There were so many scans! I liked the idea that I could find and stop attackers from taking advantage of people. ” Q. What advice would you give to someone who is considering working in your field? A. “Read, read—and start playing with toys! I’ve seen so many potential analysts tank in interviews because they didn’t have the foundational building blocks of security down. ” Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -42

Active Review Q 10 -1 What is the goal of information systems security? Q 10 -2 How big is the computer security problem? Q 10 -3 How should you respond to security threats? Q 10 -4 How should organizations respond to security threats? Q 10 -5 How can technical safeguards protect against security threats? Q 10 -6 How can data safeguards protect against security threats? Q 10 -7 How can human safeguards protect against security threats? Q 10 -8 How should organizations respond to security incidents? Q 10 -9 2027? Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -43

Hitting the Target Case Study 10 • Lost 40 million credit and debit card numbers. • Later, announced additional 70 million customer accounts stolen that included names, emails, addresses, phone numbers, etc. • 98 million customers affected. – 31% of 318 million people in US. • Stolen from point-of-sale (POS) systems at Target stores during holiday shopping season. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -44

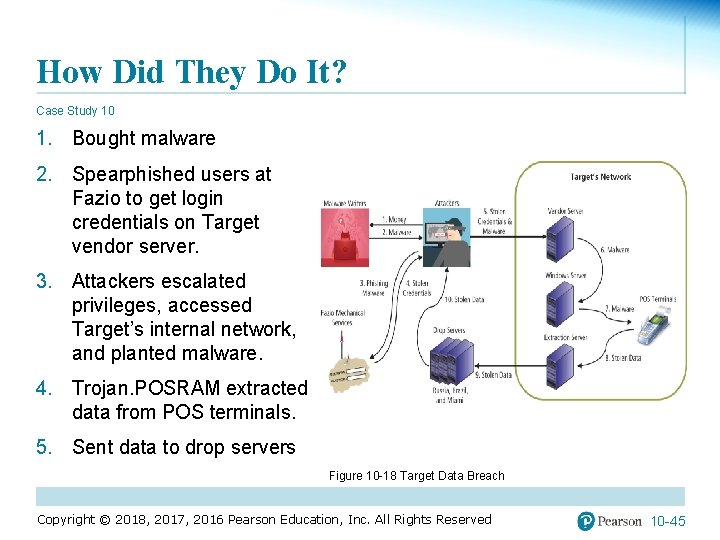
How Did They Do It? Case Study 10 1. Bought malware 2. Spearphished users at Fazio to get login credentials on Target vendor server. 3. Attackers escalated privileges, accessed Target’s internal network, and planted malware. 4. Trojan. POSRAM extracted data from POS terminals. 5. Sent data to drop servers Figure 10 -18 Target Data Breach Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -45

Damage Case Study 10 • Card and pin numbers of 2 million cards for $26. 85 each ($53. 7 M). • Costs – Upgraded POS terminals to support chip-and-pin cards, – Increased insurance premiums, – Paid legal fees, – Settled with credit card processors, – Paid consumer credit monitoring, – Paid regulatory fines. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -46

Damage (cont’d) Case Study 10 • Loss of customer confidence and drop in revenues (46% loss for quarter). • Direct loss to Target as high as $450 million. • CIO resigned, CEO paid $16 million to leave. • Cost credit unions and banks more than $200 million to issue new cards. • Insurers demand higher premiums, stricter controls, and more system auditing. • Consumers must watch their credit card statements, and fill out paperwork if fraudulent charges appear. Copyright © 2018, 2017, 2016 Pearson Education, Inc. All Rights Reserved 10 -47
