Traffic Modeling Approaches to construct Traffic Models TraceDriven

- Slides: 34

Traffic Modeling

Approaches to construct Traffic Models Ø Trace-Driven: Collect traces from the network using a sniffing tool and utilize it directly in simulations. Ø Empirical Distribution: Generate an empirical distribution from collected traces and accordingly generate random variables to drive the simulations. Ø Distribution Fitting: Fitting collected traces to a well-known distribution. Use the fitted distribution for both simulations and analysis. © Tallal Elshabrawy 2

Lecture Outline Ø Some Practical Traffic Models with Distribution Fitting Ø Evolution of Distribution Types for Traffic Modeling Ø Self-Similar Traffic Models Ø An Example of Capturing Traffic Traces © Tallal Elshabrawy 3

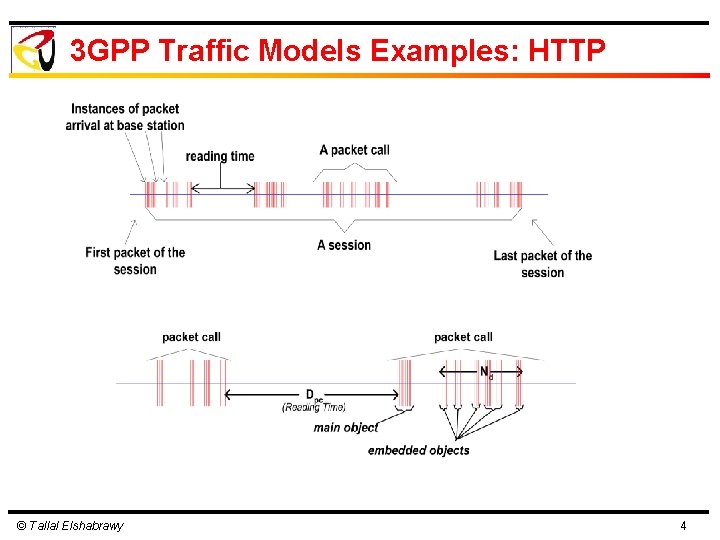
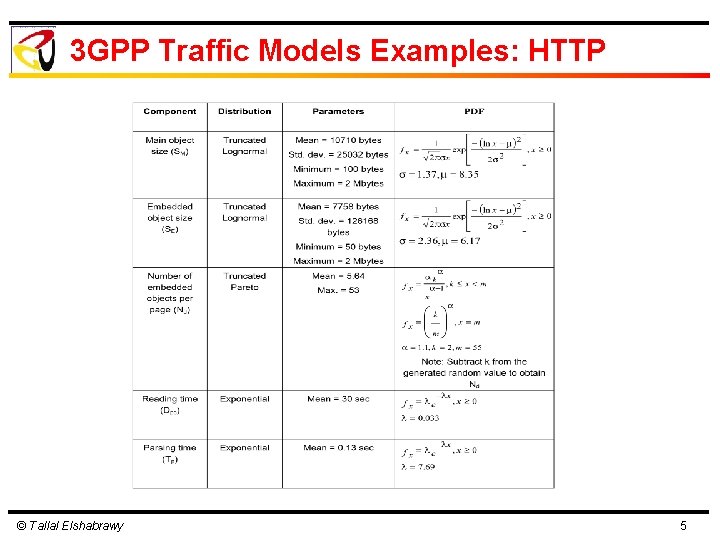
3 GPP Traffic Models Examples: HTTP © Tallal Elshabrawy 4

3 GPP Traffic Models Examples: HTTP © Tallal Elshabrawy 5

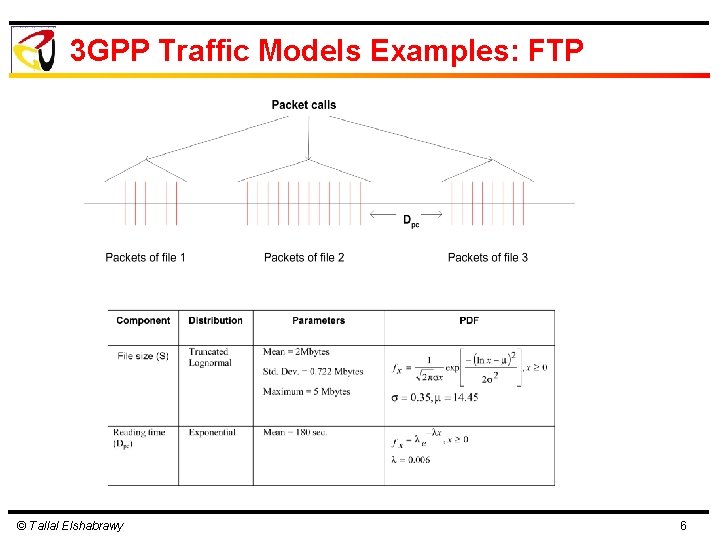
3 GPP Traffic Models Examples: FTP © Tallal Elshabrawy 6

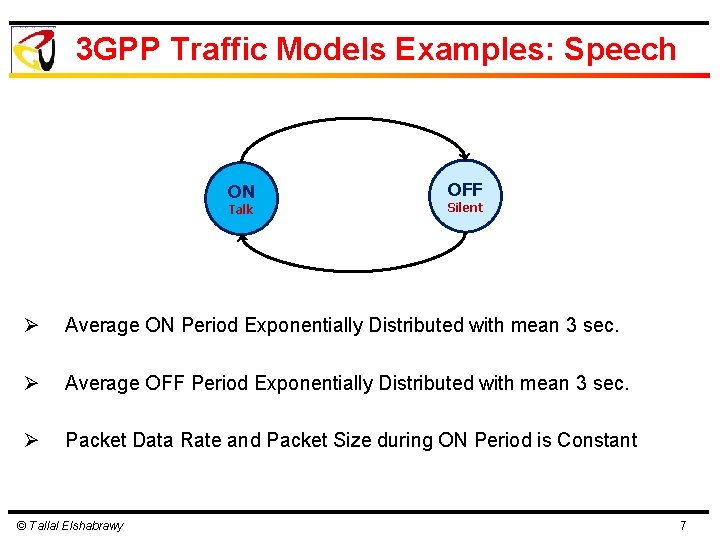
3 GPP Traffic Models Examples: Speech ON Talk OFF Silent Ø Average ON Period Exponentially Distributed with mean 3 sec. Ø Average OFF Period Exponentially Distributed with mean 3 sec. Ø Packet Data Rate and Packet Size during ON Period is Constant © Tallal Elshabrawy 7

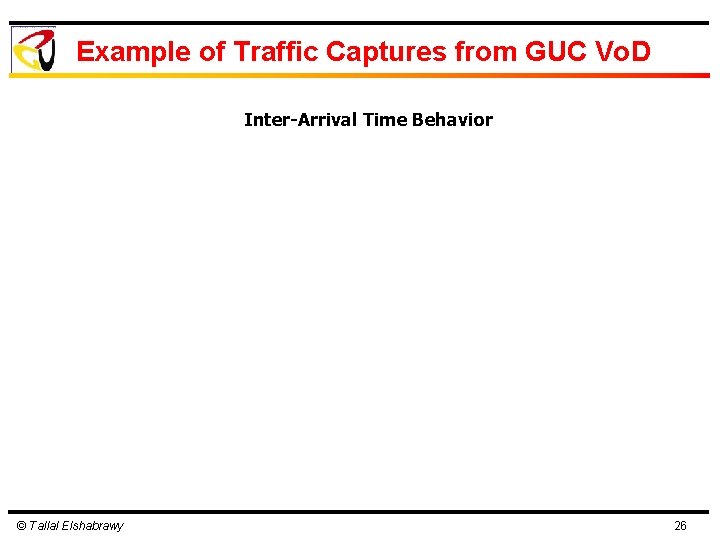
Parameters for Traffic Modeling Ø Parameters needed to model traffic of any type Ø Packet size Ø Inter-arrival times Ø Auto-correlation behavior Ø Packet size might be easier to model. It is mainly subject to protocol behavior Ø Inter-arrival times are more challenging Ø Effect of aggregation Ø Sources of delay within network Ø Auto-correlations may have significant impact on network performance © Tallal Elshabrawy 8

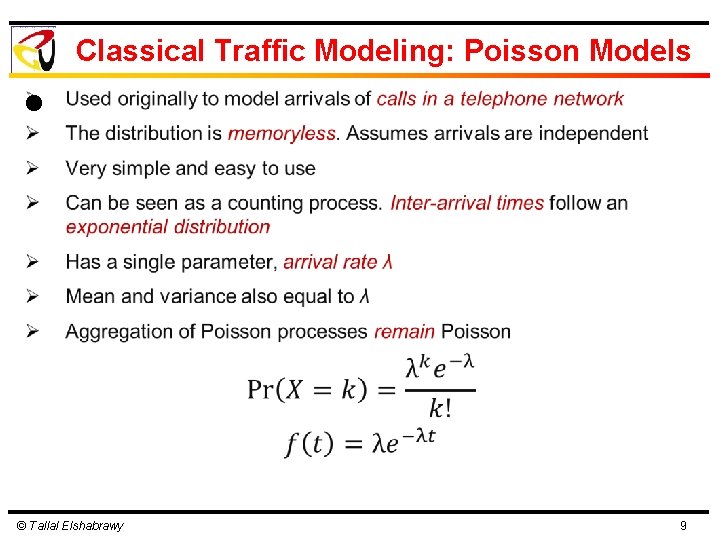
Classical Traffic Modeling: Poisson Models l © Tallal Elshabrawy 9

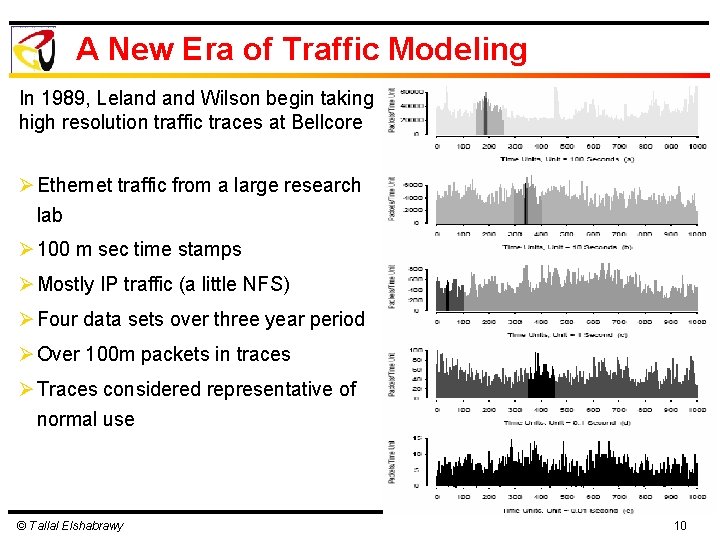
A New Era of Traffic Modeling In 1989, Leland Wilson begin taking high resolution traffic traces at Bellcore Ø Ethernet traffic from a large research lab Ø 100 m sec time stamps Ø Mostly IP traffic (a little NFS) Ø Four data sets over three year period Ø Over 100 m packets in traces Ø Traces considered representative of normal use © Tallal Elshabrawy 10

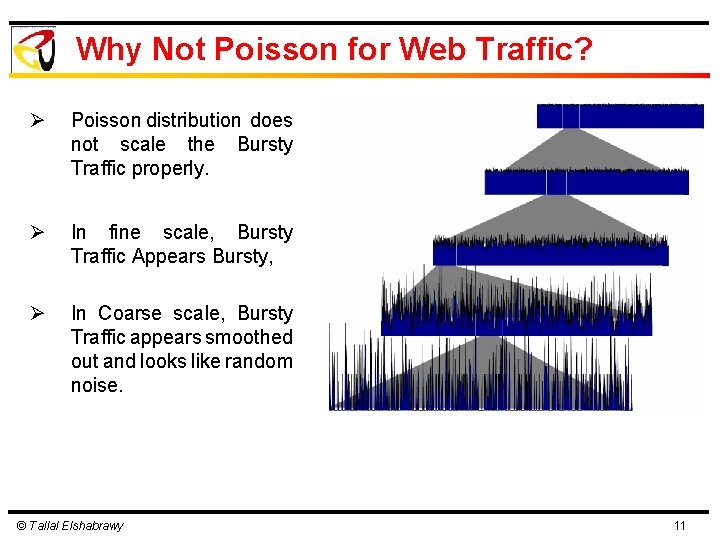
Why Not Poisson for Web Traffic? Ø Poisson distribution does not scale the Bursty Traffic properly. Ø In fine scale, Bursty Traffic Appears Bursty, Ø In Coarse scale, Bursty Traffic appears smoothed out and looks like random noise. © Tallal Elshabrawy 11

Enhancing the Poisson Model? Compound Poisson Process Ø The model is extended to deliver batches of traffic at once. Ø The inter-batch arrival times are exponentially distributed, while the batch sizes are geometric. Ø The model has two parameters: Ø The mean inter-batch arrival time 1/λ Ø The batch parameters ρ (between 0 and 1) Ø Thus, mean packet arrival over time period t is tλ/ρ Ø The model is still essentially Poisson, which is memoryless © Tallal Elshabrawy 12

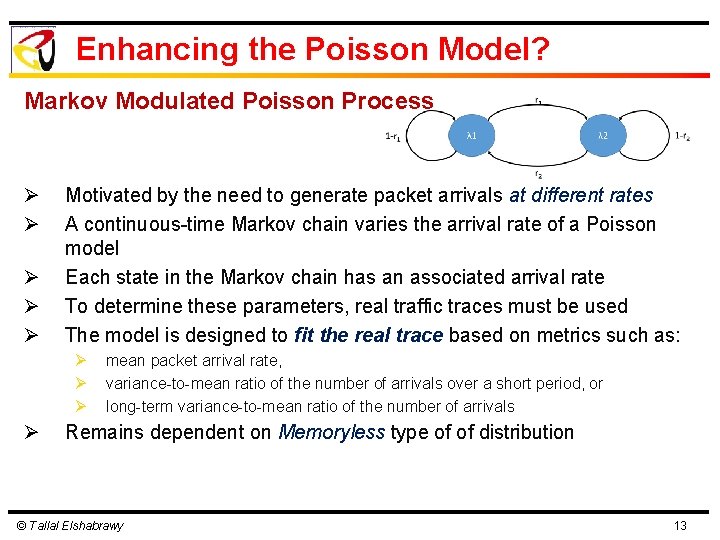
Enhancing the Poisson Model? Markov Modulated Poisson Process Ø Ø Ø Motivated by the need to generate packet arrivals at different rates A continuous-time Markov chain varies the arrival rate of a Poisson model Each state in the Markov chain has an associated arrival rate To determine these parameters, real traffic traces must be used The model is designed to fit the real trace based on metrics such as: Ø Ø mean packet arrival rate, variance-to-mean ratio of the number of arrivals over a short period, or long-term variance-to-mean ratio of the number of arrivals Remains dependent on Memoryless type of of distribution © Tallal Elshabrawy 13

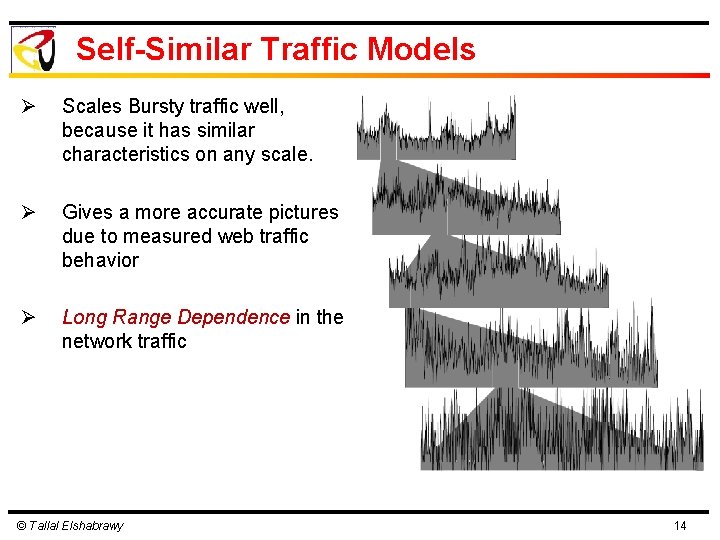
Self-Similar Traffic Models Ø Scales Bursty traffic well, because it has similar characteristics on any scale. Ø Gives a more accurate pictures due to measured web traffic behavior Ø Long Range Dependence in the network traffic © Tallal Elshabrawy 14

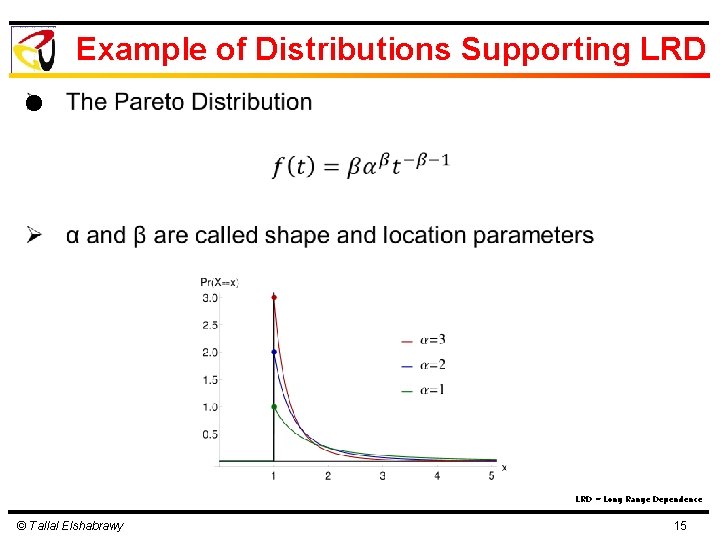
Example of Distributions Supporting LRD l LRD = Long Range Dependence © Tallal Elshabrawy 15

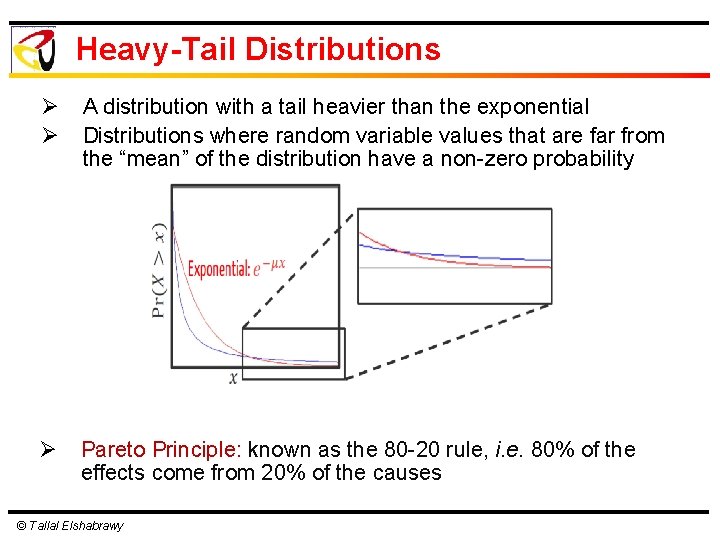
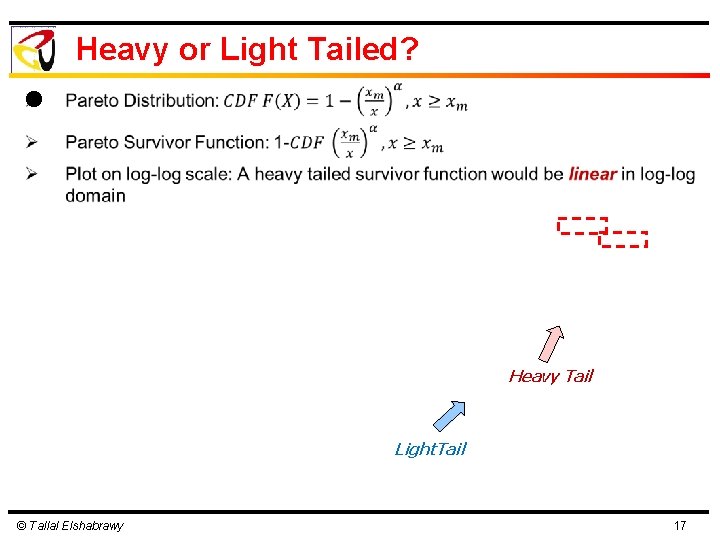
Heavy-Tail Distributions Ø Ø A distribution with a tail heavier than the exponential Distributions where random variable values that are far from the “mean” of the distribution have a non-zero probability Ø Pareto Principle: known as the 80 -20 rule, i. e. 80% of the effects come from 20% of the causes © Tallal Elshabrawy

Heavy or Light Tailed? l Heavy Tail Light. Tail © Tallal Elshabrawy 17

Observations from Practical Measurements Ø Characterizing aggregate network traffic is hard Ø Lots of (diverse) applications Ø Just a snapshot: traffic mix, protocols, applications, network configuration, technology, and users change with time © Tallal Elshabrawy

Observations from Practical Measurements Ø Packet traffic is bursty Ø Ø Average utilization may be very low Peak utilization can be very high Depends on what interval you use!! Traffic may be self-similar: bursts exist across a wide range of time scales Ø Defining burstiness (precisely) is difficult © Tallal Elshabrawy

Observations from Practical Measurements Ø Traffic is non-uniformly distributed amongst the hosts on the network Ø Example: 10% of the hosts account for 90% of the traffic (or 20 -80) Ø Why? Clients versus servers, geographic reasons, popular ftp sites, web sites, etc. © Tallal Elshabrawy

Observations from Practical Measurements Ø Well over 90% of the byte and packet traffic on most networks is TCP/IP Ø By far the most prevalent Ø Often as high as 95 -99% Ø Most studies focus only on TCP/IP for this reason © Tallal Elshabrawy

Observations from Practical Measurements Ø Traffic is bidirectional Ø Ø Data usually flows both ways Not JUST acks in the reverse direction Usually asymmetric bandwidth though Pretty much what you would expect from the TCP/IP traffic for most applications © Tallal Elshabrawy

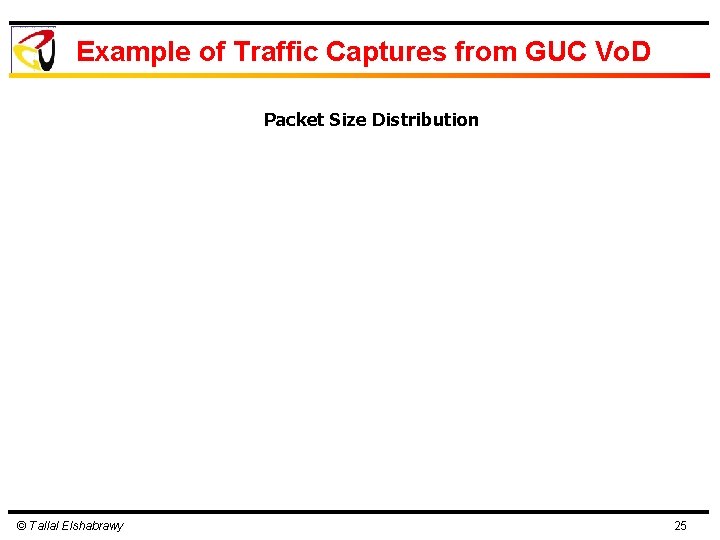
Observations from Practical Measurements Ø Packet size distribution is bimodal Ø Lots of small packets for interactive traffic and acknowledgements Ø Lots of large packets for bulk data file transfer type applications Ø Very few in between sizes © Tallal Elshabrawy

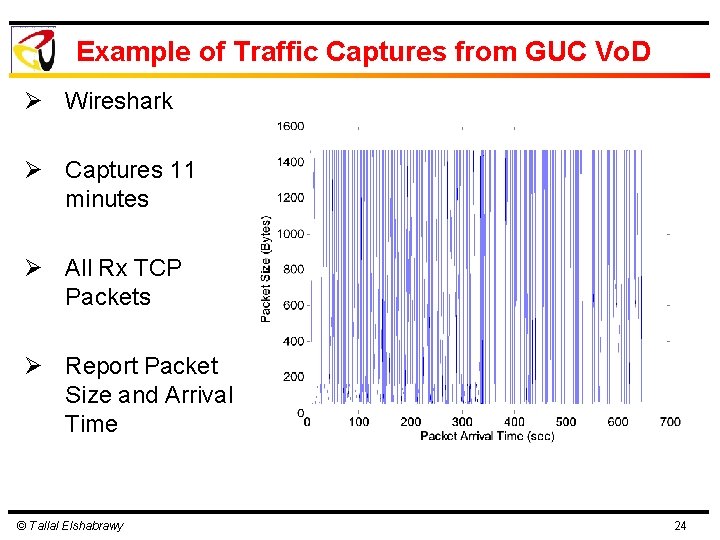
Example of Traffic Captures from GUC Vo. D Ø Wireshark Ø Captures 11 minutes Ø All Rx TCP Packets Ø Report Packet Size and Arrival Time © Tallal Elshabrawy 24

Example of Traffic Captures from GUC Vo. D Packet Size Distribution © Tallal Elshabrawy 25

Example of Traffic Captures from GUC Vo. D Inter-Arrival Time Behavior © Tallal Elshabrawy 26

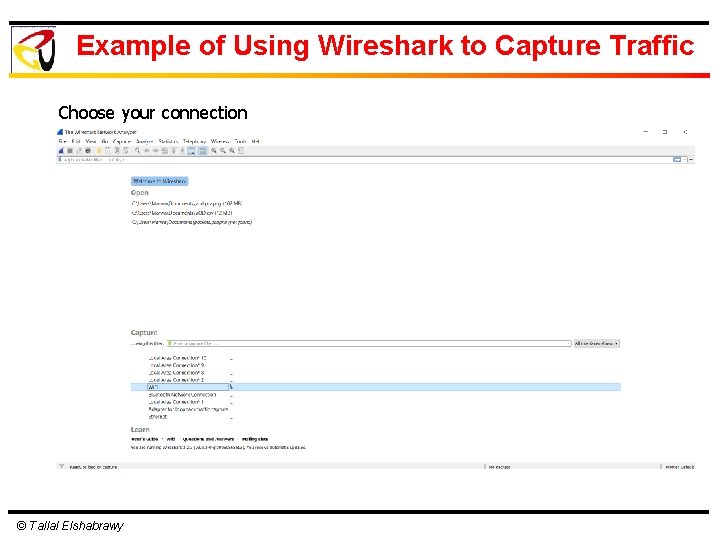
Example of Using Wireshark to Capture Traffic Choose your connection © Tallal Elshabrawy

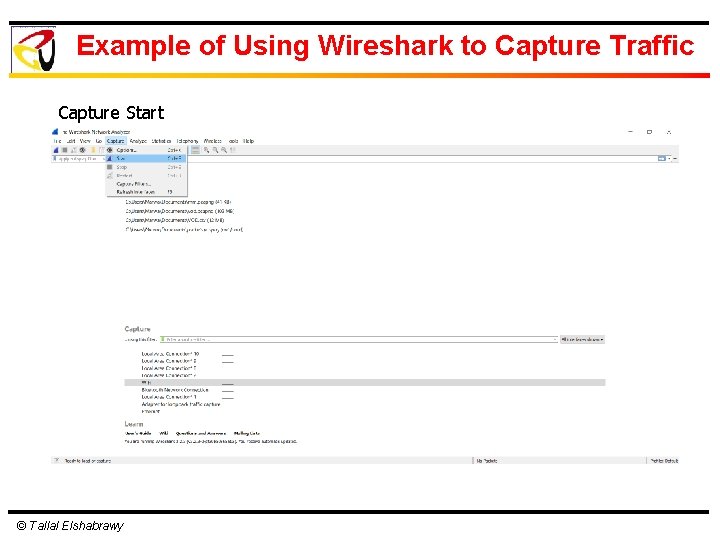
Example of Using Wireshark to Capture Traffic Capture Start © Tallal Elshabrawy

Example of Using Wireshark to Capture Traffic Start browsing © Tallal Elshabrawy

Example of Using Wireshark to Capture Traffic Open Videos © Tallal Elshabrawy

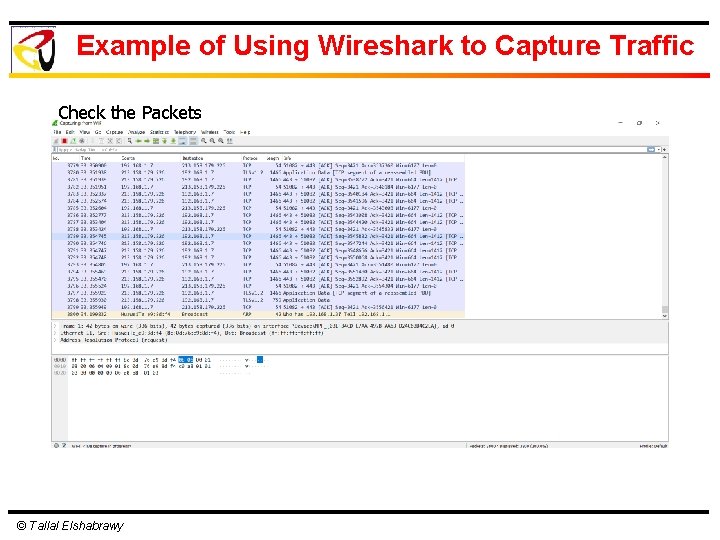
Example of Using Wireshark to Capture Traffic Check the Packets © Tallal Elshabrawy

Example of Using Wireshark to Capture Traffic Stop Capture © Tallal Elshabrawy

Example of Using Wireshark to Capture Traffic Export © Tallal Elshabrawy

Thank You!