Topic 1 Direct Link Network Media Access Control






![References Section 2. 6: Direct Link Networks [P&D] References Section 2. 6: Direct Link Networks [P&D]](https://slidetodoc.com/presentation_image/0de861b22020993306b156f96f680810/image-29.jpg)

- Slides: 30

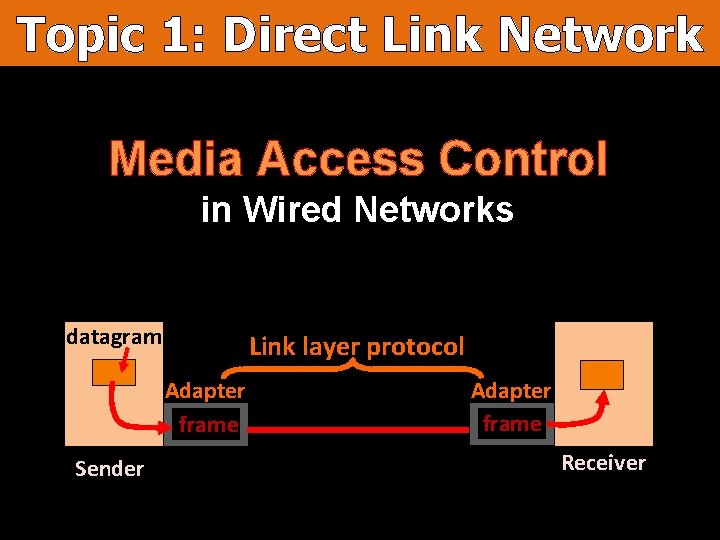
Topic 1: Direct Link Network Media Access Control in Wired Networks datagram Link layer protocol Adapter frame Sender Adapter frame Receiver

Recap Fundamental problems 1. Encoding 2. Framing 3. Error detection 4. Reliable delivery 5. Access Mediation

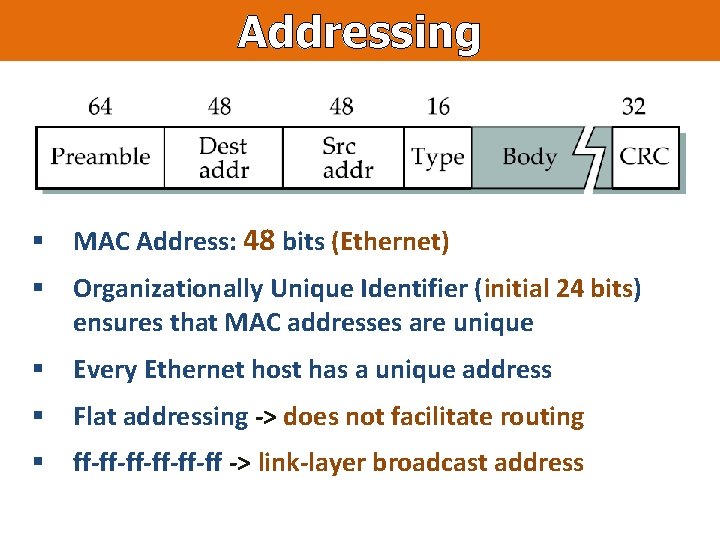
Addressing § MAC Address: 48 bits (Ethernet) § Organizationally Unique Identifier (initial 24 bits) ensures that MAC addresses are unique § Every Ethernet host has a unique address § Flat addressing -> does not facilitate routing § ff-ff-ff-ff -> link-layer broadcast address

Today’s topic 1. Encoding 2. Framing 3. Error detection 4. Reliable delivery 5. Access Mediation

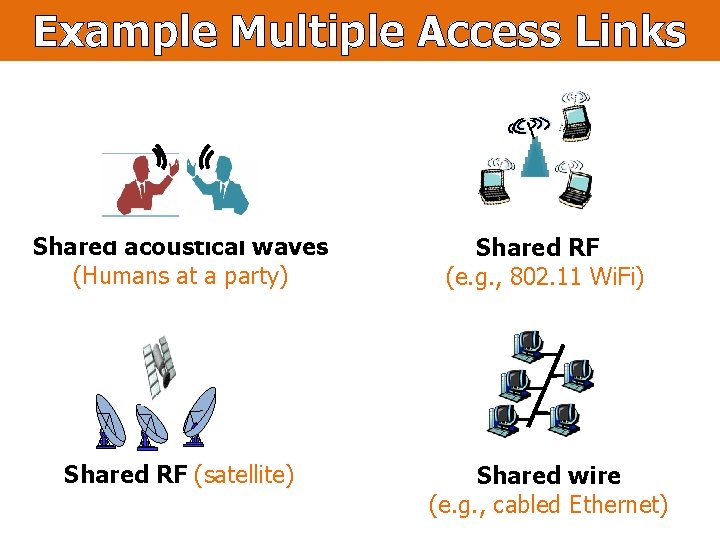
Example Multiple Access Links Shared acoustical waves (Humans at a party) Shared RF (e. g. , 802. 11 Wi. Fi) Shared RF (satellite) Shared wire (e. g. , cabled Ethernet)

Different approaches to MAC 1 - Channel Partitioning Divide channel into smaller “pieces” (time slots, frequency, code) and allocate for exclusive use 2 - Random-access Channel not divided, allow (and recover from) collisions 3 - Round-robin or “taking turns” Nodes use tokens to share the media deterministically; for bursty data traffic, performs better than channel partitioning

Random Access Protocol • Random access MAC protocol specifies: – how to detect collisions – how to recover from collisions • Examples of random access MAC protocols: – ALOHA; CSMA/CD, CSMA/CA

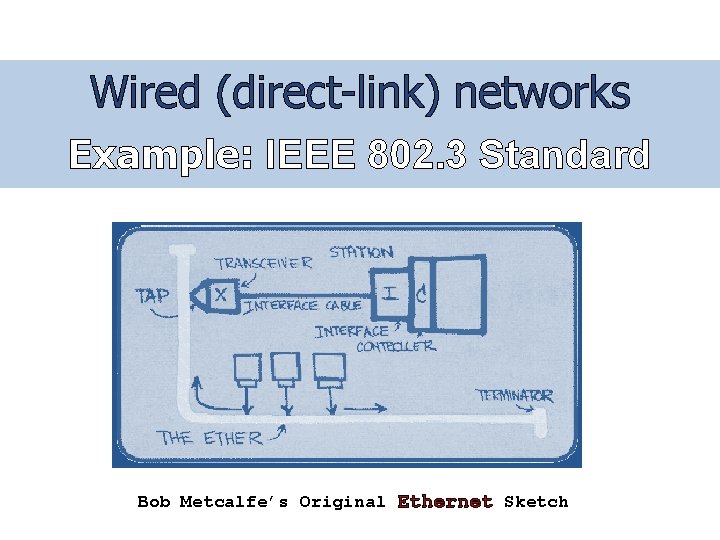
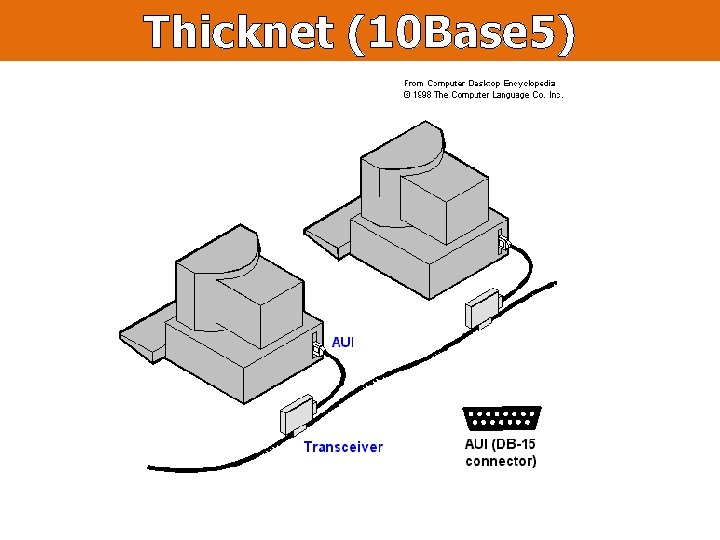
Wired (direct-link) networks Example: IEEE 802. 3 Standard Bob Metcalfe’s Original Ethernet Sketch

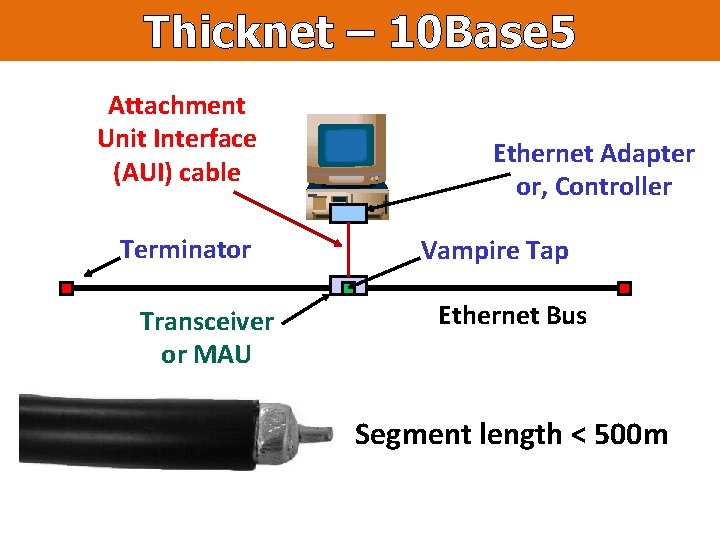
Thicknet – 10 Base 5 Attachment Unit Interface (AUI) cable Terminator Transceiver or MAU Ethernet Adapter or, Controller Vampire Tap Ethernet Bus Segment length < 500 m

Thicknet (10 Base 5)

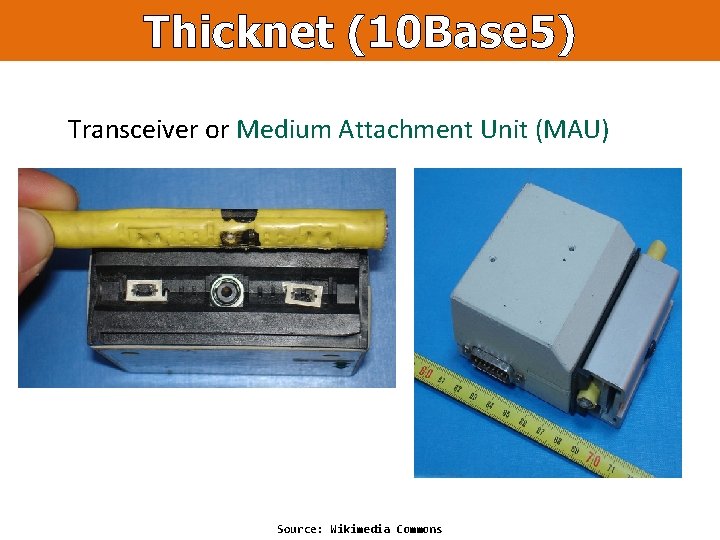
Thicknet (10 Base 5) Transceiver or Medium Attachment Unit (MAU) Source: Wikimedia Commons

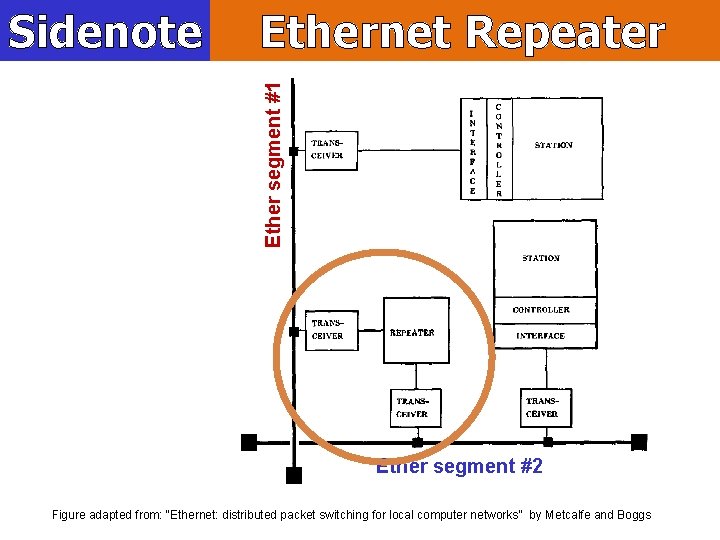
Ethernet Repeater Ether segment #1 Sidenote Ether segment #2 Figure adapted from: “Ethernet: distributed packet switching for local computer networks” by Metcalfe and Boggs

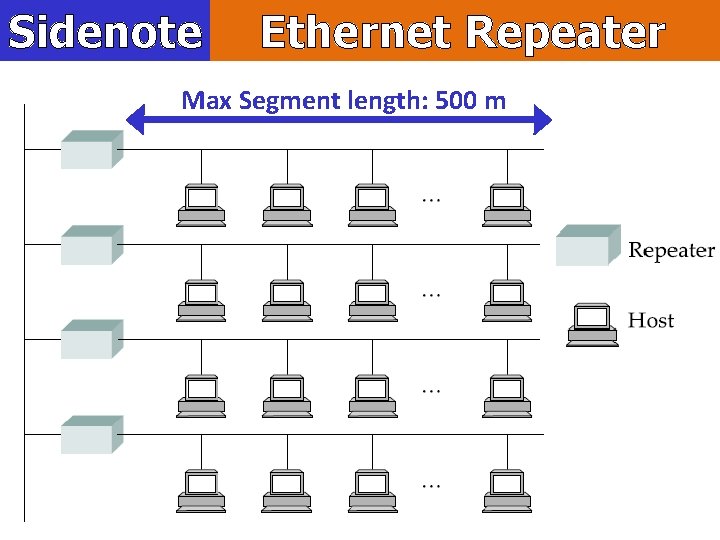
Sidenote Ethernet Repeater Max Segment length: 500 m

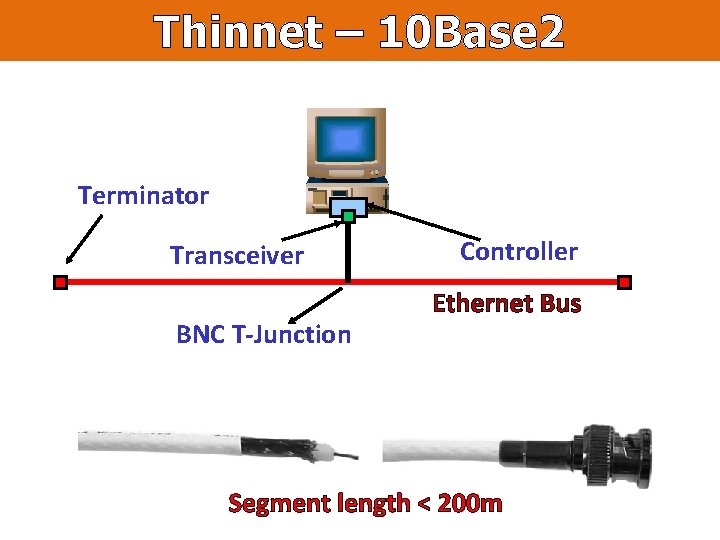
Thinnet – 10 Base 2 Terminator Transceiver BNC T-Junction Controller Ethernet Bus Segment length < 200 m

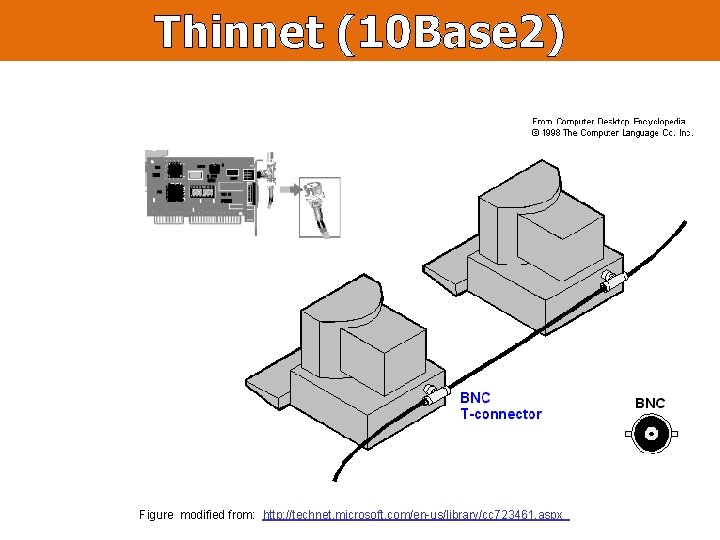
Thinnet (10 Base 2) Figure modified from: http: //technet. microsoft. com/en-us/library/cc 723461. aspx

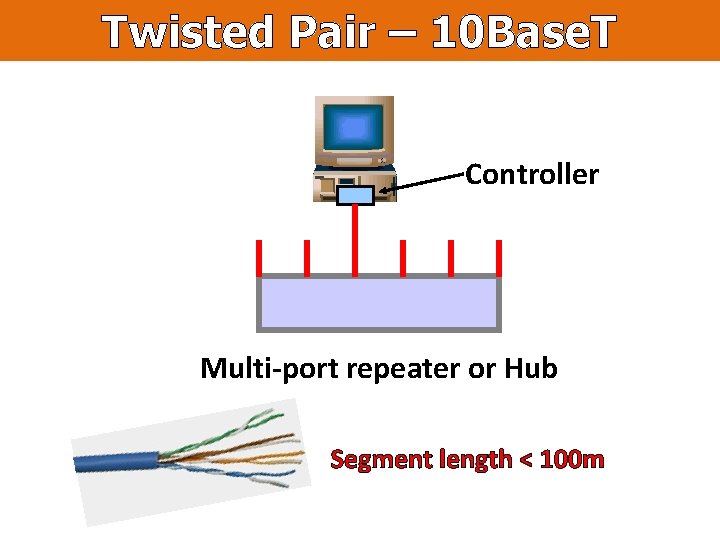
Twisted Pair – 10 Base. T Controller Multi-port repeater or Hub Segment length < 100 m

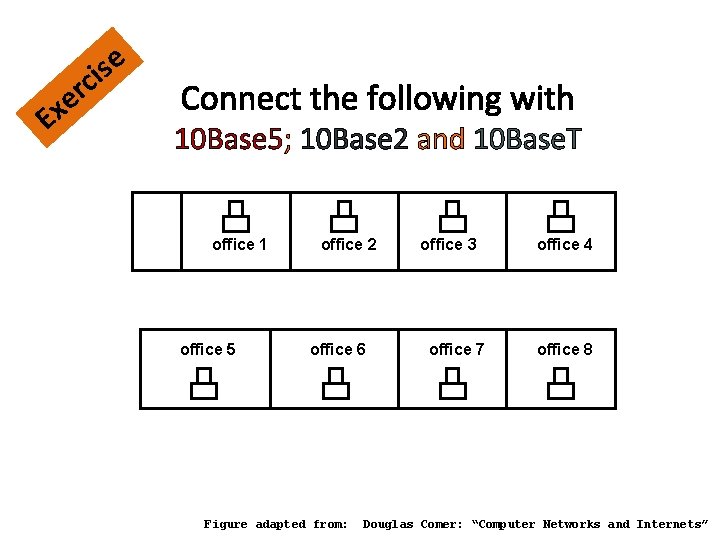
E r e x ic se Connect the following with 10 Base 5; 10 Base 2 and 10 Base. T office 1 office 5 office 2 office 6 Figure adapted from: office 3 office 7 office 4 office 8 Douglas Comer: “Computer Networks and Internets”

ic se r e x E 10 Base 5 10 Base 2 Figure adapted from: Douglas Comer: “Computer Networks and Internets” 10 Base. T

Carrier Sense on Multiple Access/ Collision Detection (CSMA/ CD) Human analogy: the polite conversationalist

How do collisions occur? Propagation delay: d

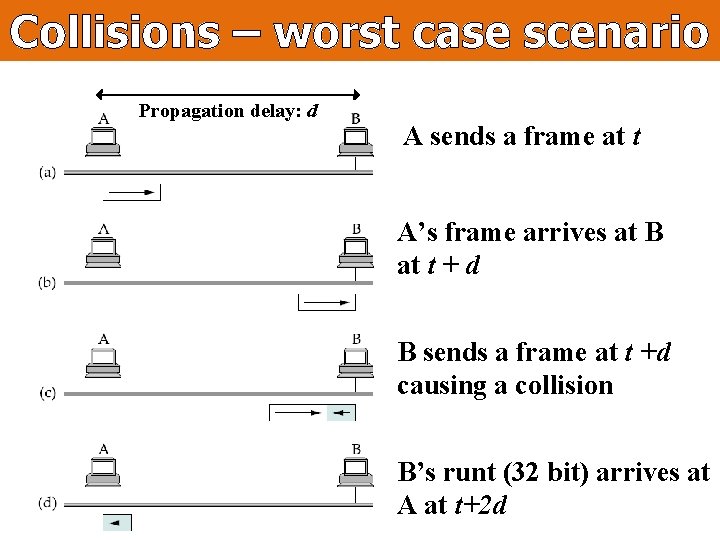
Collisions – worst case scenario Propagation delay: d A sends a frame at t A’s frame arrives at B at t + d B sends a frame at t +d causing a collision B’s runt (32 bit) arrives at A at t+2 d

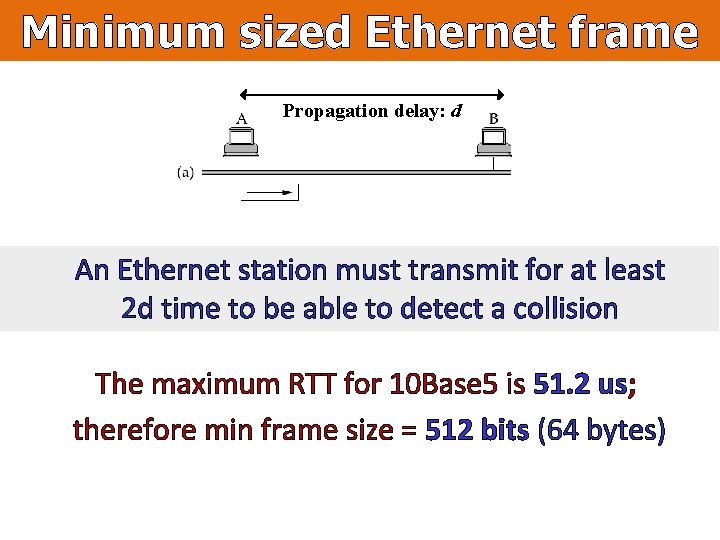
Minimum sized Ethernet frame Propagation delay: d An Ethernet station must transmit for at least 2 d time to be able to detect a collision The maximum RTT for 10 Base 5 is 51. 2 us; therefore min frame size = 512 bits (64 bytes)

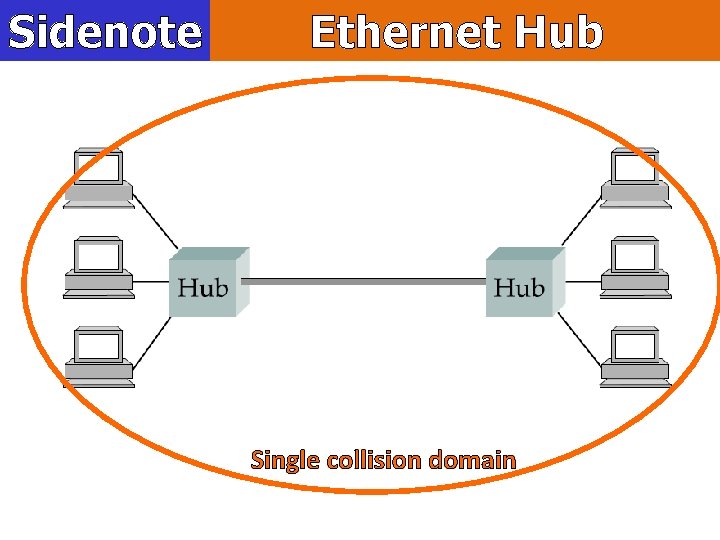
Sidenote Ethernet Hub Single collision domain

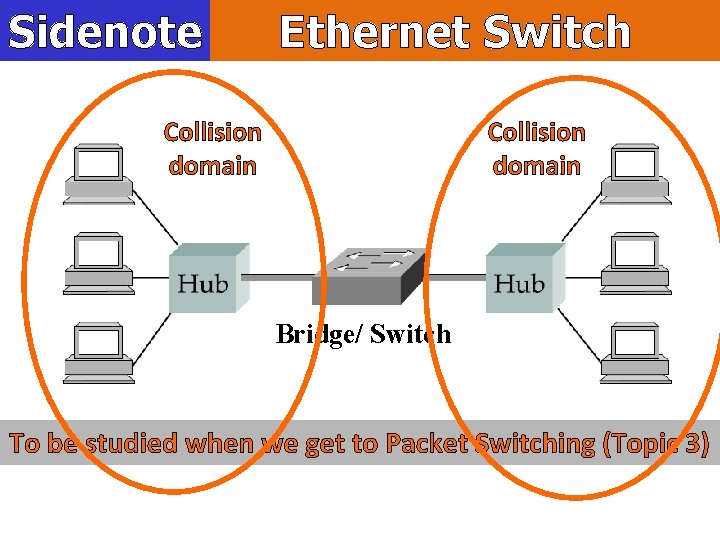
Sidenote Ethernet Switch Collision domain Bridge/ Switch To be studied when we get to Packet Switching (Topic 3)

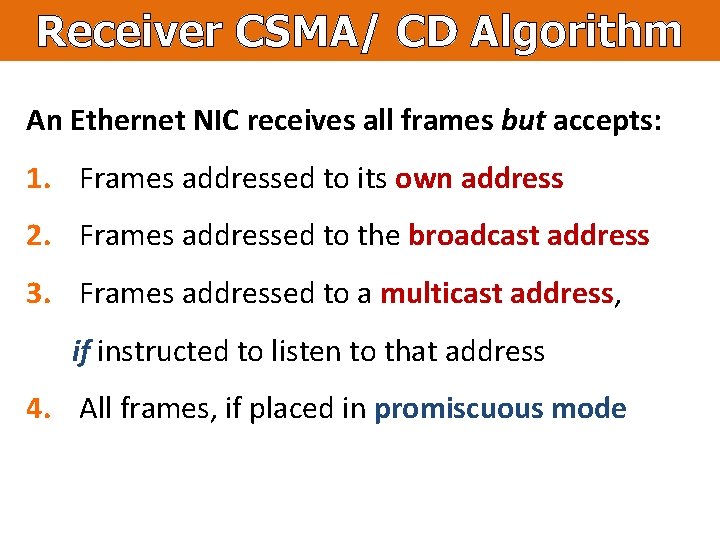
Receiver CSMA/ CD Algorithm An Ethernet NIC receives all frames but accepts: 1. Frames addressed to its own address 2. Frames addressed to the broadcast address 3. Frames addressed to a multicast address, if instructed to listen to that address 4. All frames, if placed in promiscuous mode

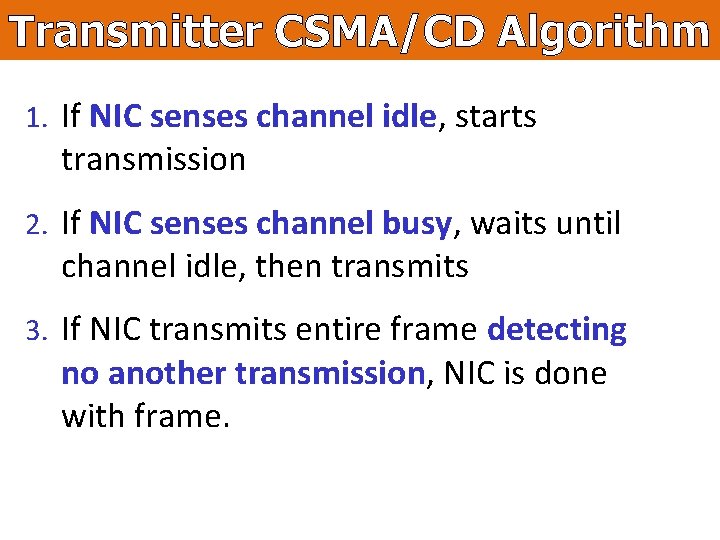
Transmitter CSMA/CD Algorithm 1. If NIC senses channel idle, starts transmission 2. If NIC senses channel busy, waits until channel idle, then transmits 3. If NIC transmits entire frame detecting no another transmission, NIC is done with frame.

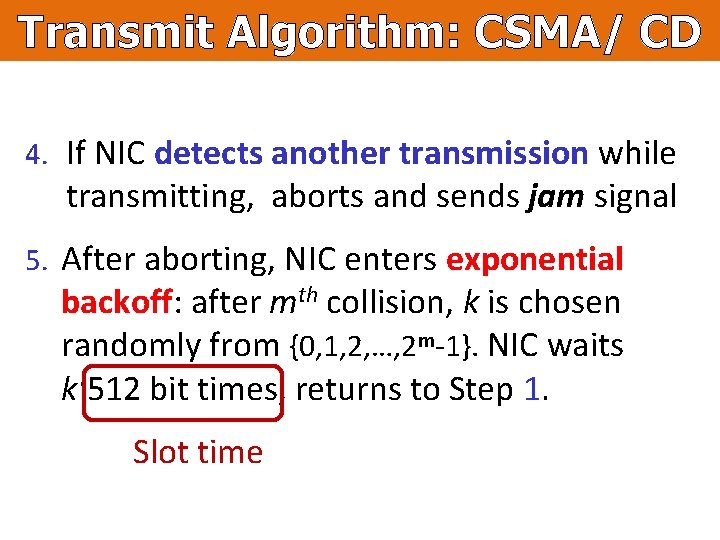
Transmit Algorithm: CSMA/ CD 4. If NIC detects another transmission while transmitting, aborts and sends jam signal 5. After aborting, NIC enters exponential backoff: after mth collision, k is chosen randomly from {0, 1, 2, …, 2 m-1}. NIC waits k·512 bit times, returns to Step 1. Slot time

Experience with Ethernet 1. Simple decentralized and cheap methodology 2. In practice: nodes < 200; distance << 2500 m; dprop is as low as 5 us 3. In such condition, Ethernet performs very well. 4. Very versatile; started with 3 Mbps and has now reached 10 Gbps
![References Section 2 6 Direct Link Networks PD References Section 2. 6: Direct Link Networks [P&D]](https://slidetodoc.com/presentation_image/0de861b22020993306b156f96f680810/image-29.jpg)
References Section 2. 6: Direct Link Networks [P&D]

? ? ? Questions/ Confusions?