Systems Architecture Seventh Edition Chapter 9 Computer Networks













- Slides: 53

Systems Architecture, Seventh Edition Chapter 9 Computer Networks © 2016. Cengage Learning. All rights reserved.

Chapter Objectives • In this chapter, you will learn to: – Describe logical and physical network topologies – Explain message forwarding across local and wide area networks – Describe media access control protocols – Describe network hardware devices – Summarize the OSI network layers – Describe the Internet architecture and network protocols – Describe IEEE physical network standards, including Ethernet © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

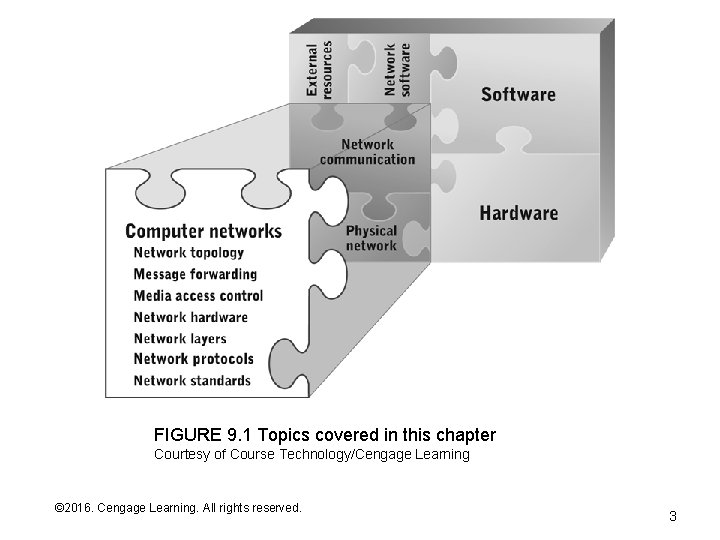
FIGURE 9. 1 Topics covered in this chapter Courtesy of Course Technology/Cengage Learning © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition 3

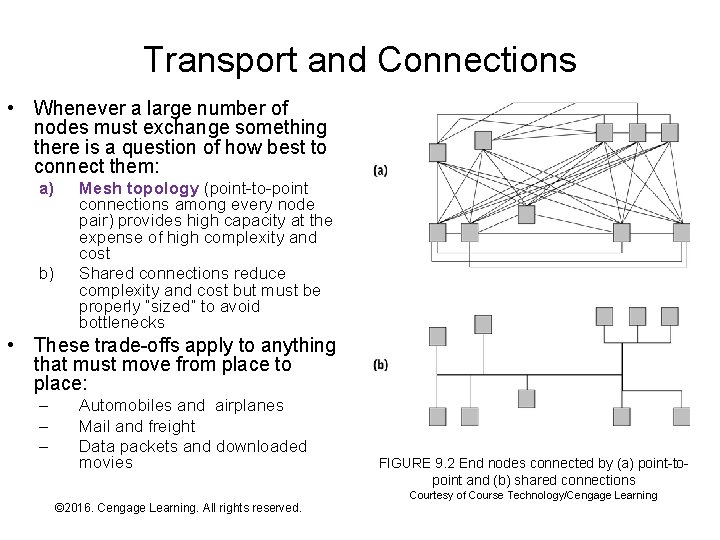
Transport and Connections • Whenever a large number of nodes must exchange something there is a question of how best to connect them: a) b) Mesh topology (point-to-point connections among every node pair) provides high capacity at the expense of high complexity and cost Shared connections reduce complexity and cost but must be properly “sized” to avoid bottlenecks • These trade-offs apply to anything that must move from place to place: – – – Automobiles and airplanes Mail and freight Data packets and downloaded movies © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition FIGURE 9. 2 End nodes connected by (a) point-topoint and (b) shared connections Courtesy of Course Technology/Cengage Learning

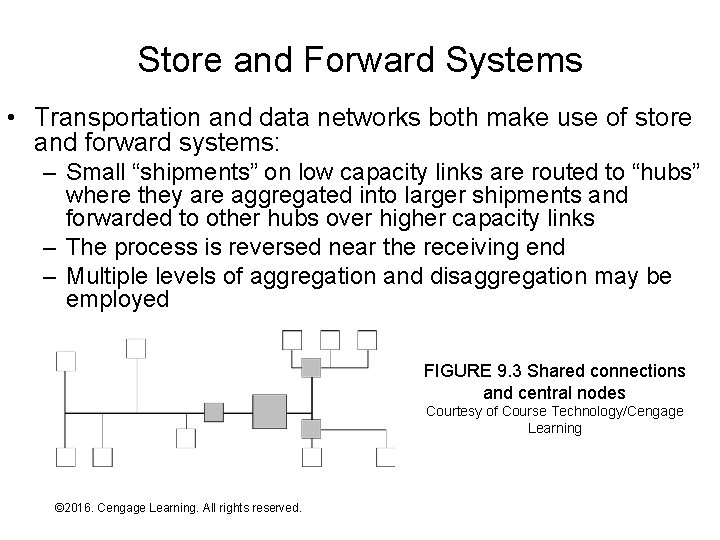
Store and Forward Systems • Transportation and data networks both make use of store and forward systems: – Small “shipments” on low capacity links are routed to “hubs” where they are aggregated into larger shipments and forwarded to other hubs over higher capacity links – The process is reversed near the receiving end – Multiple levels of aggregation and disaggregation may be employed FIGURE 9. 3 Shared connections and central nodes Courtesy of Course Technology/Cengage Learning © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Network Topology • Network topology is the organization of nodes and communication channels for message transport: – Physical topology – how are the nodes and connections physically arranged – what is connected to what? – Logical topology – how do messages traverse the physical network? • Network topologies: – – Mesh – rarely used (see previous slide) Star Bus Ring © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

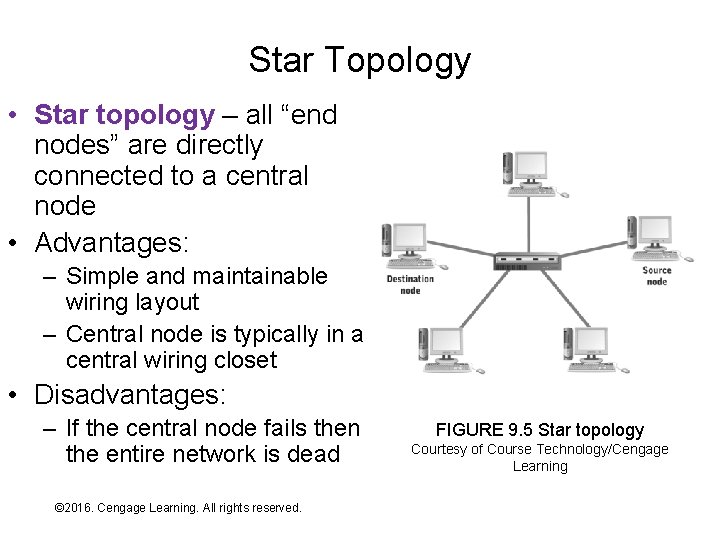
Star Topology • Star topology – all “end nodes” are directly connected to a central node • Advantages: – Simple and maintainable wiring layout – Central node is typically in a central wiring closet • Disadvantages: – If the central node fails then the entire network is dead © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition FIGURE 9. 5 Star topology Courtesy of Course Technology/Cengage Learning

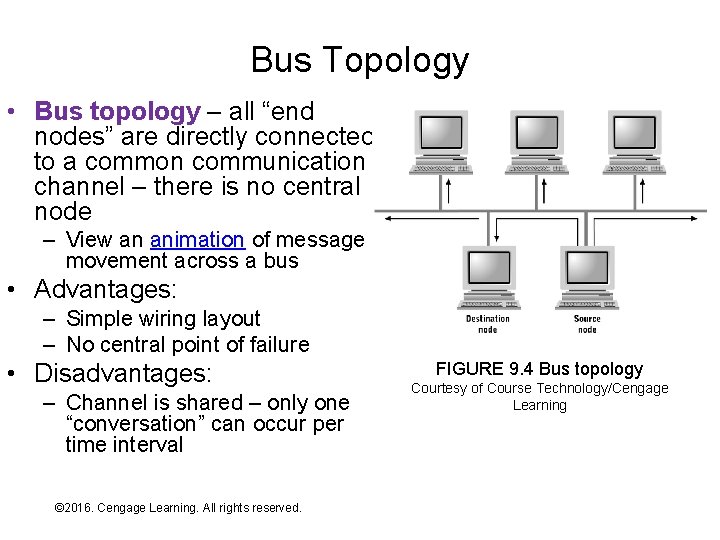
Bus Topology • Bus topology – all “end nodes” are directly connected to a common communication channel – there is no central node – View an animation of message movement across a bus • Advantages: – Simple wiring layout – No central point of failure • Disadvantages: – Channel is shared – only one “conversation” can occur per time interval © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition FIGURE 9. 4 Bus topology Courtesy of Course Technology/Cengage Learning

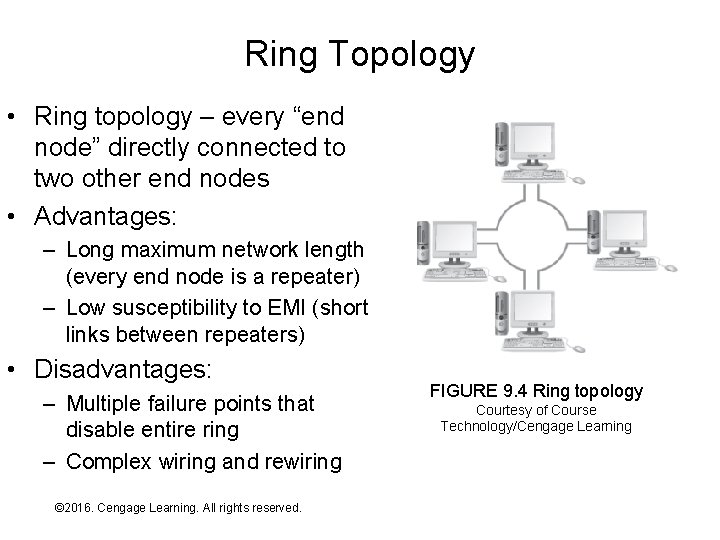
Ring Topology • Ring topology – every “end node” directly connected to two other end nodes • Advantages: – Long maximum network length (every end node is a repeater) – Low susceptibility to EMI (short links between repeaters) • Disadvantages: – Multiple failure points that disable entire ring – Complex wiring and rewiring © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition FIGURE 9. 4 Ring topology Courtesy of Course Technology/Cengage Learning

Exercise • What are the physical topologies of the following common “networks”? – City streets – Cable TV – Wireless computer network within a home © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Addressing and Forwarding • When a network is large it must be segmented into smaller networks that are interconnected in a store and forward system – The larger the network, the more levels of interconnection • Messages must be “tagged” with sender (source) and recipient (target) addresses • A central node must examine the recipient address to forward a message to its destination, for example: – To another node in the same local network – To another interconnection point © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

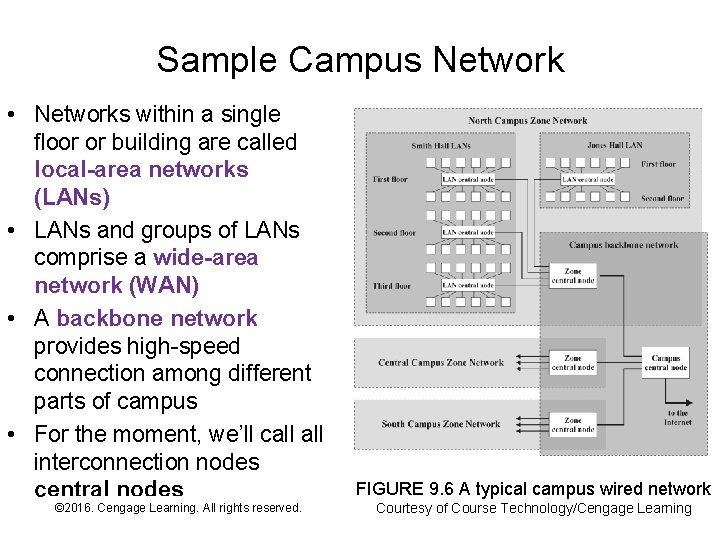
Sample Campus Network • Networks within a single floor or building are called local-area networks (LANs) • LANs and groups of LANs comprise a wide-area network (WAN) • A backbone network provides high-speed connection among different parts of campus • For the moment, we’ll call interconnection nodes central nodes © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition FIGURE 9. 6 A typical campus wired network Courtesy of Course Technology/Cengage Learning

Routing • Central nodes must examine each packet address and determine: – Is the address that of a directly-connected node (local)? – If not local, to where should it be sent? • If the address is: – Local - the central node forwards it to the corresponding directly-connected node – Not local - the central must decide to which other directlyconnected node the message should be forwarded: • This is a trivial decision if a central node is only connected to one other central node (e. g. , the LAN central nodes in the previous figure) • The decision is more complex if a central node is connected to multiple other central nodes (e. g. , the zone and campus central nodes in the previous figure) © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Routing - Continued • A forwarding table is a list of addresses (or groups of addresses) and the node to which they should be sent: – The forwarding table for an end node often contains only one entry – packets to any address are routed to the nearest central node – The forwarding table of a LAN central node generally contains n+1 entries: • N local end nodes • 1 “upstream” central node – The forwarding table of a WAN central node generally contains multiple entries – all of which map groups of addresses to an interconnected central node • For example, the north campus zone central node knows which north campus endpoints are connected to which LAN central nodes and routes all other addresses to the central campus central node – A default gateway is the address of a central node to which messages to “unknown” addresses are sent © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Exercise • Assume that your campus network is organized like Figure 9. 6 • How will a message sent from a desktop computer at one end of campus get to a desktop computer at the other end of campus? • How will a message sent from a desktop computer at another university get to your instructor’s office computer? © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Why Not Use a Centralized Directory • Things to consider when using a centralized directory of nodes? – How big is the directory? – How rapidly does the directory content change? – How big of a computer is required to store the directory and answer queries? – How big must be the network connections to/from the directory server? • Consider the answers for a typical university campus – Tens or hundreds of thousands of entries – Rapid content change (e. g. , due to wired nodes being added/moved/deleted and personal devices entering/leaving campus) – A single directory server would be a large-scale computer, it’s network connections would be clogged with directory-related messages, and it would be a single point of failure in the network • Distributing directory content across many computers with a relatively small amount of information stored in each directory server is the only feasible solution – Though, that requires solving the problem of how multiple copies of directory information are updated and synchronized © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Media Access Control • When multiple nodes share a common transmission medium they must coordinate their communication to avoid interfering with one another • When two nodes “speak” at the same time on the same media their message combine resulting in noise (called a collision) • Any coordination method that ensures that no more than one node “speaks” at a time is called a media access control (MAC) protocol • In a physical classroom, one possible MAC protocol is that students can only speak when they raise their hand the instructor grants them permission to speak © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Computer Network MAC Protocols • Modern wired star topology networks don’t need a MAC protocol because each node connects to a central node with two dedicated transmission wires (one for messages sent in each direction) – Collision are impossible because each transmission wire has only one possible sender • Earlier generations of wired bus networks (e. g. , 10 MBps Ethernet) use a MAC protocol called Carrier Sense Multiple Access / Collision Detection (CSMA/CD) – A sending node listens (carrier sense) until no traffic is detected before attempting to transmit – The sending node transmits message – The sending node listens for a collision during and immediately after transmitting (collision detection) – If the sending node detects a collision, it waits for a random number of clock ticks, then restarts then retransmits – View a CSMA/CD animation © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

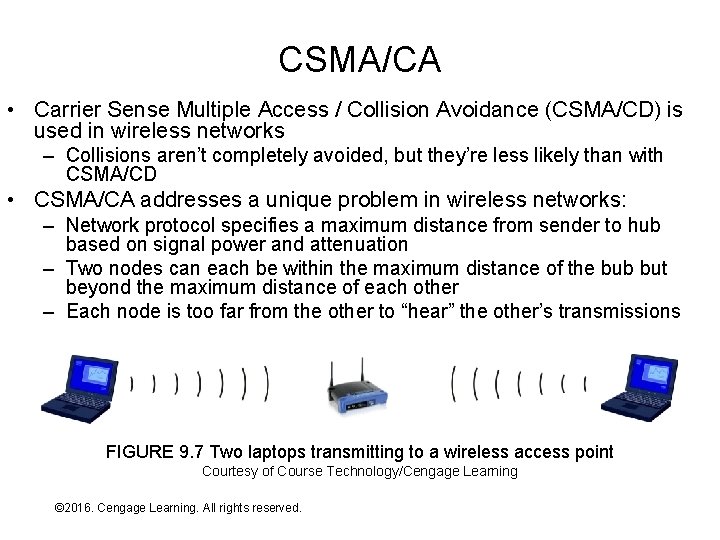
CSMA/CA • Carrier Sense Multiple Access / Collision Avoidance (CSMA/CD) is used in wireless networks – Collisions aren’t completely avoided, but they’re less likely than with CSMA/CD • CSMA/CA addresses a unique problem in wireless networks: – Network protocol specifies a maximum distance from sender to hub based on signal power and attenuation – Two nodes can each be within the maximum distance of the bub but beyond the maximum distance of each other – Each node is too far from the other to “hear” the other’s transmissions FIGURE 9. 7 Two laptops transmitting to a wireless access point Courtesy of Course Technology/Cengage Learning © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

CSMA/CA - Continued • CSMA/CA uses a three-step sequence 1. A node that wants to transmit a message first transmits a ready-to-send (RTS) signal 2. If the wireless central node detects: a) A collision (two nodes transmitted RTS at the same time), it ignores the RTS signals - Lacking a response from the central node, each node waits a random interval before sending another RTS b) No collision, it transmits a clear-to-send (CTS) signal 3. After receiving the CTS signal in response to its own RTS signal, the node transmits message © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Network (Inter)Connection Devices • Types of network interconnection devices include: – Network interface card – Hub – Switch – Router – Wireless access point © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Network Adapters • Network interface card (NIC) or network adapter – Device that connects a single node (usually a workstation or server) to a single network (usually a LAN) – Acts as a bridge between the network and the node’s system bus – Sample device on right would “plug into” an expansion slot of a desktop computer bus (see Figure 6. 4) – Many computers have the network adapter integrated into the motherboard. © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Hubs • Hub – Central connection point for LAN wiring – May implement a logical topology internally • Internal functions of 10 Mbps Ethernet hub on right would match those in Figure 9. 8 10 Mbps Ethernet hub – Few or no “brains” – no routing – Rarely used today except for patch panels Network patch panel © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Switches and Routers • Switch – Connects each node to a full-duplex dedicated port – Forms virtual two-port networks on a per-packet basis – Larger switches can form many twonode networks at the same time • Router Network switch or router – Connects two or more networks – Actively forwards packets as needed – Maintains a routing table and makes “intelligent” routing choices • Multifunction devices – Some devices perform both switching and routing functions (and perhaps other functions) – You can’t tell whether a device is a switch, router, or both, based on physical appearance © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition A multifunction device for home networking that combines switching, routing, and wireless access point functions

Wireless Access points • A wireless access point (WAP): – Connects a wireless network to a wired network – Implements one or more IEEE wireless networking standards (for example, 802. 11 n) – Divides allocated RF bandwidth into subchannels to support multiple transmission paths and assigns nodes to specific subchannels – Implements CSMA/CA or another MAC protocol for each subchannel – Implements protocols for error detection/correction and security – WAP functions can be combined with routing and wired network switching functions in the same device (see previous slide) © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Application Layer • Includes communication protocols used by programs that make and respond to high-level requests for network services – End-user network utilities – Network services embedded in the OS – Network service providers © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Presentation Layer • Converts and formats data • Ensures correct interpretation of transmitted data • Other layered network models usually collapse Presentation-layer functions into the Application layer © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Session Layer • Establishes and manages communication sessions • Negotiates protocol parameters • Monitors communication to detect and deal with problems © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Transport Layer • Formats messages into packets suitable for transmission over the network • Places messages within a packet data area and adds header/trailer information (network addresses, error detection data, packet sequencing data) • Gives packets to Network layer for delivery • Examines packets for errors; requests retransmission if necessary (when receiving packets) © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Network Layer • Forwards messages to their correct destinations • Those within central node interact with one another to exchange routing information and update internal tables © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Data Link Layer • Interface between network software and hardware • Device drivers perform functions such as media access control and conversion of messages and addresses from one format to another © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Physical Layer • Where communication between devices actually takes place • Includes hardware devices that encode and decode bit streams and the transmission lines that transport them © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

The Internet • The U. S. Department of Defense sponsored the development of a peer-to-peer inter-networking standard (ARPANET) in the late 1960 s • The protocol was designed for large multiple-vendor networks operating under “wartime” conditions: – Independent of vendor-specific protocols (e. g. , Ethernet) – Avoids centralized information stores, services, and infrastructure to improve fault tolerance – Network should provide some functionality even in the event of significant loss of network resources • In other words, we should still be able to fire a retaliatory strike if the Russians wipe out 90% of the network in a first strike • With surprisingly few changes, ARPANET evolved into the modern Internet © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Core Internet Protocols • Internet Protocol (IP) – a packet format that defines the content of a datagram, including: – – Data content Sequencing of multiple-packet messages Addressing and routing information View an animation • Transmission Control Protocol (TCP) – a “connection” protocol layered over IP that enables: – Detection of transmission errors – Retransmission of missing or corrupted packets • Internet Control Message Protocol (ICMP) – A set of messages/responses used to report and diagnose errors • Routing Information Protocol (RIP) – Defines how datagrams are routed from sender to receiver – Defines how routers exchange routing information • ARP/RARP – covered later © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

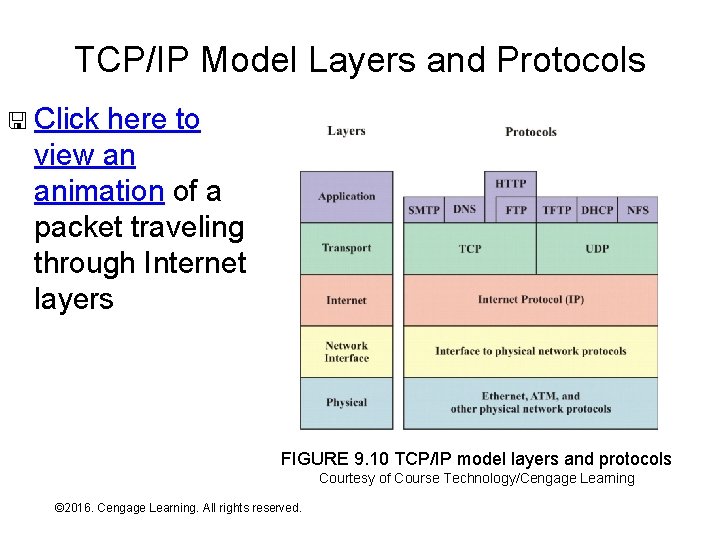
TCP/IP Model Layers and Protocols < Click here to view an animation of a packet traveling through Internet layers FIGURE 9. 10 TCP/IP model layers and protocols Courtesy of Course Technology/Cengage Learning © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

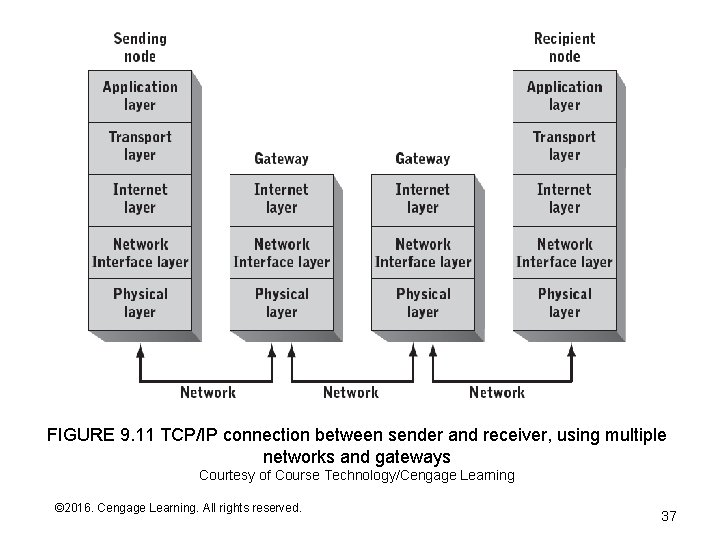
Internet Routing • All nodes store a routing table (execute ‘arp –a’ from a command prompt to view the table). • The routing table stores the IP and physical (e. g. , Ethernet) addresses of known local nodes and routers – Some IP addresses are “wild cards” – patterns that match multiple addresses (e. g. , all addresses at UNM) • A sending node’s IP layer looks up a destination address in its routing table and sends it to the most appropriate gateway • Subsequent gateways continue the process until the datagram reaches its destination • View an animation © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

FIGURE 9. 11 TCP/IP connection between sender and receiver, using multiple networks and gateways Courtesy of Course Technology/Cengage Learning © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition 37

Connectionless and Connection-Oriented Protocols • A connection-oriented protocol: – Contacts a recipient before sending data to “let it know that messages are coming” – Negotiates communication parameters such as error detection/correction, data encoding, and security – The process is similar to what happens when you dial a telephone number • A connection-oriented protocol enables: – A recipient to know if data is lost or mangled during transmission • View an animation of packet loss and retransmission – “Optimization” of the data transmission to match desired service or data characteristics (e. g. , secure vs. insecure) • But, a connection-oriented protocol requires “extra work” before and during transmission • A connection-less protocol doesn’t establish or use connections: – Little/no ability to detect lost datagrams – Relies on default methods for routing, data encoding, security, … © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

IP vs. TCP vs. UDP • IP is a connection-less protocol – Datagrams are “launched” toward their destination with no advance warning or explicit receipt acknowledgement – IP’s simplicity is both a virtue and shortcoming • Simple and flexible to implement • Lacks many features needed for reliable and/guaranteed communication • TCP is a connection-oriented protocol – Connection is established so receiver “knows” data is coming – Error detection for datagram content and tracking of individual packets so loss can be detected – Recipient explicitly acknowledges datagram receipt – Sender retransmits unacknowledged datagrams • UDP is a connection-oriented protocol – – “Lighter” than TCP Less error detection No retransmission of lost/garbled datagrams Intended for streaming multimedia © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

IP Addresses • An IP address is a unique 32 bit number, generally written in “dotted decimal notation” as: nnn • Client nodes can have IP addresses assigned: – Statically – the address is “programmed into” the device and doesn’t change unless reprogrammed – Dynamically – the address is assigned by a server, typically using Dynamic Host Control Protocol (DHCP) © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

IP Versions 4 & 6 • Internet protocol version 4 (IPv 4) has been used for over 30 years • IPv 6 was developed in the late 1990 s because: – The number of Internet-connected hosts was expected to exceed 4 billion (maximum possible number of unique IPv 4 addresses) – IPv 4 implementation of multicasting is too inefficient • IPv 6 addresses are: – 128 bits long – Written in colon hexadecimal notation (hhhh: hhhh: hhhh) where h is a hexadecimal digit • IPv 6 requires updating the IP layer in EVERY Internet device! – Full conversion won’t be complete for several more years • Multicasting – data transmission among multiple senders and receivers – Typical scenario is 1 sender to multiple receivers, for example: • Internet radio • Software update distributed from one server to multiple clients – More complex scenarios are possible (e. g. , Internet video-conferencing) – IPv 6 provides much more efficient support for multicasting © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

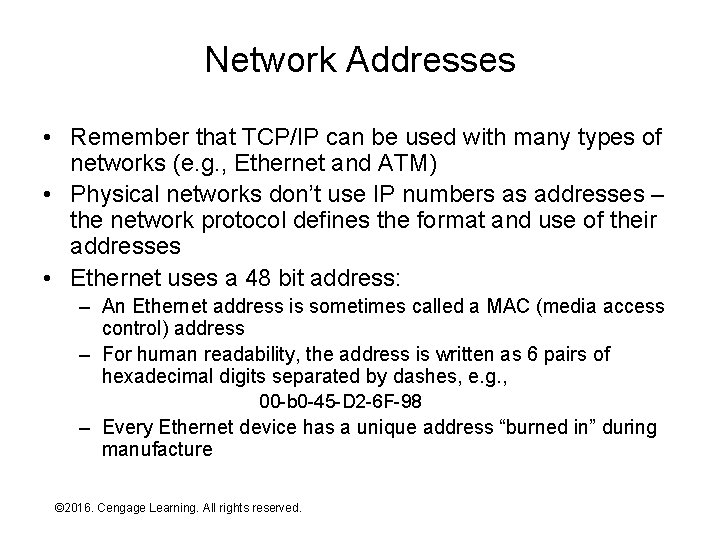
Network Addresses • Remember that TCP/IP can be used with many types of networks (e. g. , Ethernet and ATM) • Physical networks don’t use IP numbers as addresses – the network protocol defines the format and use of their addresses • Ethernet uses a 48 bit address: – An Ethernet address is sometimes called a MAC (media access control) address – For human readability, the address is written as 6 pairs of hexadecimal digits separated by dashes, e. g. , 00 -b 0 -45 -D 2 -6 F-98 – Every Ethernet device has a unique address “burned in” during manufacture © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Address Resolution Protocol • The Address Resolution Protocol (ARP) describes queries that convert IP addresses into network addresses (e. g. , Ethernet MAC addresses) • An IP capable device can send an ARP broadcast message (e. g. , “Is 129. 24. 8. 78 on this LAN and, if so, tell me your MAC address? ”) • The Reverse Address Resolution Protocol (RARP) describes broadcast messages that inform routers and other devices of network addresses and their corresponding IP addresses • An IP capable device sends a RARP broadcast message when it boots up. “Interested” devices, such as routers, update internal ARP tables when they see RARP message • ARP tables can be displayed with the command “arp -a” © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

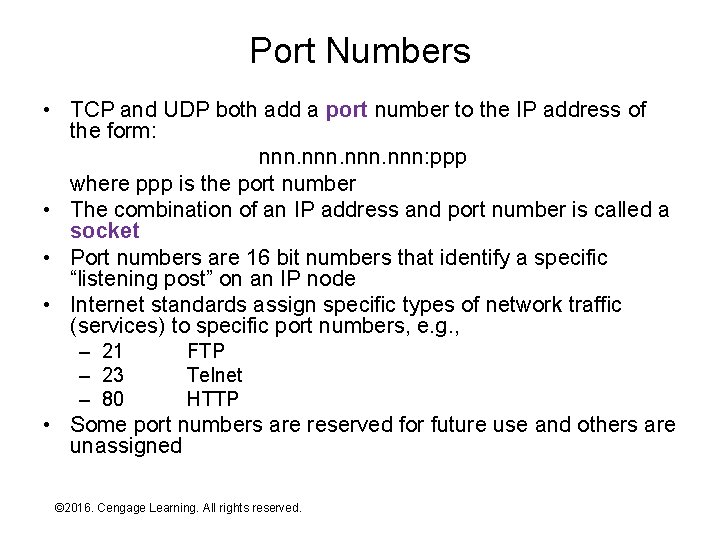
Port Numbers • TCP and UDP both add a port number to the IP address of the form: nnn: ppp where ppp is the port number • The combination of an IP address and port number is called a socket • Port numbers are 16 bit numbers that identify a specific “listening post” on an IP node • Internet standards assign specific types of network traffic (services) to specific port numbers, e. g. , – 21 – 23 – 80 FTP Telnet HTTP • Some port numbers are reserved for future use and others are unassigned © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Voice over IP (Vo. IP) • Technologies/standards that carry voice messages and data over single packet-switched network • Lower cost than traditional public switched telephone network (PSTN) • Complex and competing standards • Transmission quality problems (packet loss, latency, jitter) © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

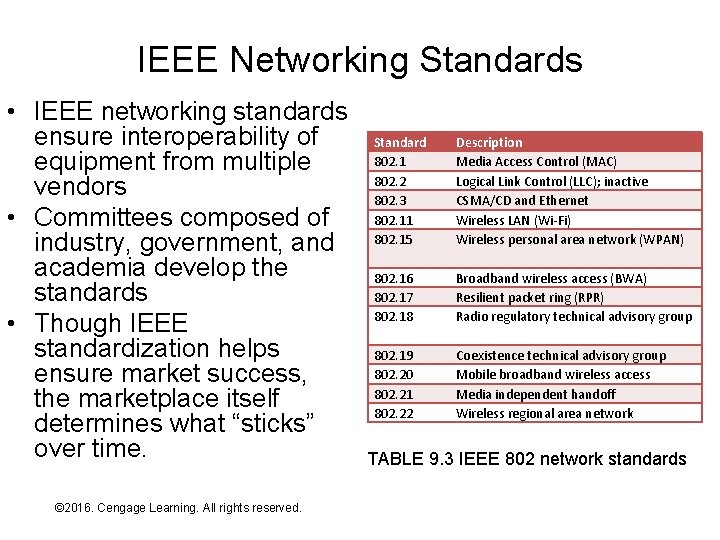
IEEE Networking Standards • IEEE networking standards ensure interoperability of equipment from multiple vendors • Committees composed of industry, government, and academia develop the standards • Though IEEE standardization helps ensure market success, the marketplace itself determines what “sticks” over time. © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition Standard 802. 1 802. 2 802. 3 802. 11 802. 15 Description Media Access Control (MAC) Logical Link Control (LLC); inactive CSMA/CD and Ethernet Wireless LAN (Wi-Fi) Wireless personal area network (WPAN) 802. 16 802. 17 802. 18 Broadband wireless access (BWA) Resilient packet ring (RPR) Radio regulatory technical advisory group 802. 19 802. 20 802. 21 802. 22 Coexistence technical advisory group Mobile broadband wireless access Media independent handoff Wireless regional area network TABLE 9. 3 IEEE 802 network standards

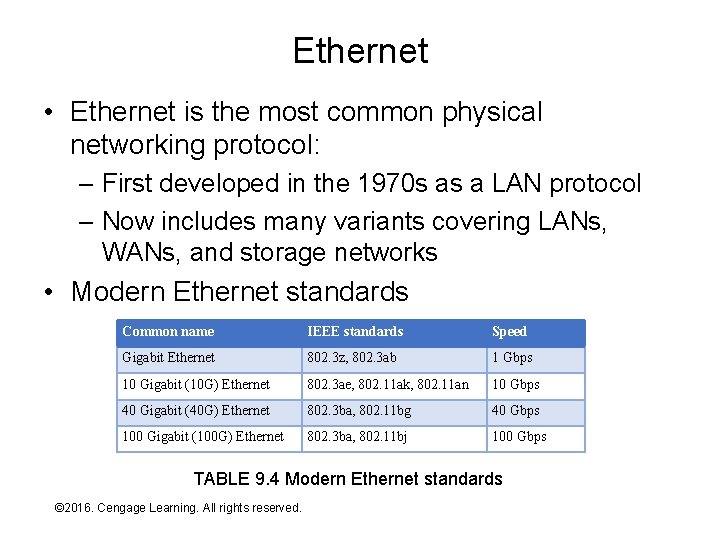
Ethernet • Ethernet is the most common physical networking protocol: – First developed in the 1970 s as a LAN protocol – Now includes many variants covering LANs, WANs, and storage networks • Modern Ethernet standards Common name IEEE standards Speed Gigabit Ethernet 802. 3 z, 802. 3 ab 1 Gbps 10 Gigabit (10 G) Ethernet 802. 3 ae, 802. 11 ak, 802. 11 an 10 Gbps 40 Gigabit (40 G) Ethernet 802. 3 ba, 802. 11 bg 40 Gbps 100 Gigabit (100 G) Ethernet 802. 3 ba, 802. 11 bj 100 Gbps TABLE 9. 4 Modern Ethernet standards © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

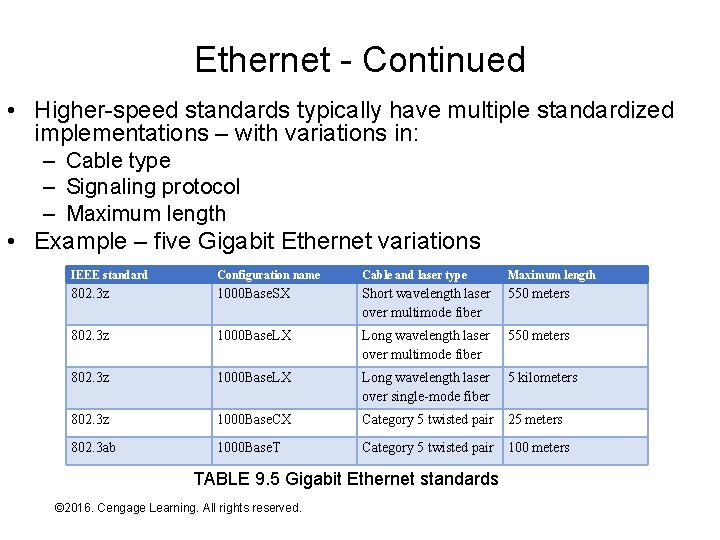
Ethernet - Continued • Higher-speed standards typically have multiple standardized implementations – with variations in: – Cable type – Signaling protocol – Maximum length • Example – five Gigabit Ethernet variations IEEE standard Configuration name Cable and laser type Maximum length 802. 3 z 1000 Base. SX Short wavelength laser over multimode fiber 550 meters 802. 3 z 1000 Base. LX Long wavelength laser over single-mode fiber 5 kilometers 802. 3 z 1000 Base. CX Category 5 twisted pair 25 meters 802. 3 ab 1000 Base. T Category 5 twisted pair 100 meters TABLE 9. 5 Gigabit Ethernet standards © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Wireless Transmission/Networking Standards • Any wireless networking/transmission method is a combination of design choices in: – – Transmission frequency(ies) Bit encoding method(s) Error/detection/correction method(s) Channel organization and sharing method(s) • There are many choices in each category and many possible combinations - without standards, there would be a huge number of competing and incompatible vendor offerings • The Institute of Electrical and Electronics Engineers (IEEE) defines a family of standards for wireless transmission and networking • IEEE works closely with international RF regulating organizations and governments to ensure that its standards are not country- or region-specific © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

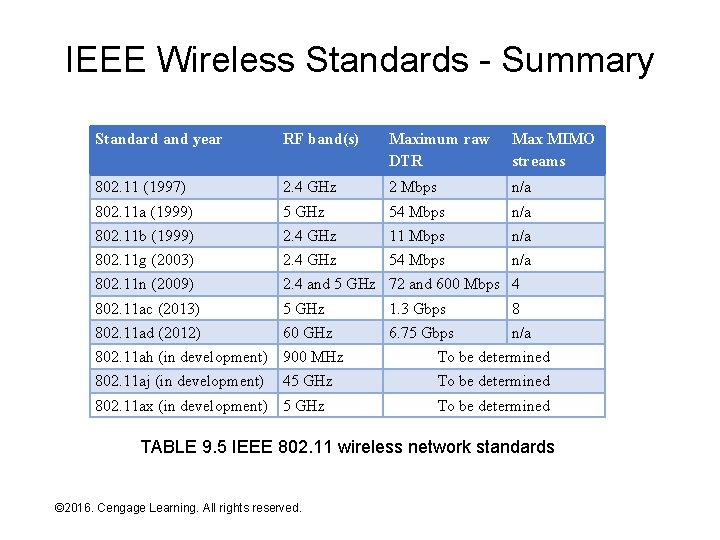
IEEE Wireless Standards - Summary Standard and year RF band(s) Maximum raw DTR Max MIMO streams 802. 11 (1997) 2. 4 GHz 2 Mbps n/a 802. 11 a (1999) 5 GHz 54 Mbps n/a 802. 11 b (1999) 2. 4 GHz 11 Mbps n/a 802. 11 g (2003) 2. 4 GHz 54 Mbps n/a 802. 11 n (2009) 2. 4 and 5 GHz 72 and 600 Mbps 4 802. 11 ac (2013) 5 GHz 1. 3 Gbps 8 802. 11 ad (2012) 60 GHz 6. 75 Gbps n/a 802. 11 ah (in development) 900 MHz To be determined 802. 11 aj (in development) To be determined 45 GHz 802. 11 ax (in development) 5 GHz To be determined TABLE 9. 5 IEEE 802. 11 wireless network standards © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

IEEE Wireless Standards - Continued • Frequency bands – Available unlicensed bands vary from country-to-country – Standards often specify multiple bands so that they’ll have at least one viable implementation in various parts of the world • Data transfer rates – Raw data transfer rates are specified in the standards but typical or effective rates can be much lower due to: • • Competing traffic from nearby users Noise Physical obstacles Fixed vs. mobile transmitters and receivers © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

MIMO • Modern standards and devices typically use multiple-input multiple-output (MIMO) – Multiple antennae used by both transmitters and receivers – For example, 802. 11 n can broadcast and receive on up to 4 channels – requires 4 antennae • MIMO can be used in two different ways: – Diversity • Same info transmitted via different antennae and frequency bands • Receiver selects the stronger received signal • Useful in noisy/crowded environments – Frequency-division multiplexing • Sender transmits different data streams across different bands at the same time to increase throughput • Useful when noise and other traffic isn’t present © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition

Summary • • • Network topology Addressing and routing Media access control Network hardware OSI network layers Network standards © 2016. Cengage Learning. All rights reserved. Systems Architecture, Seventh Edition