Snort Nmap Mike OConnor Eric Tallman Matt Yasiejko






























- Slides: 34

Snort & Nmap Mike O’Connor Eric Tallman Matt Yasiejko

Overview n Snort What is it? n What does it do? n Features n n Nmap What is it? n What does it do? n Features n

What is Snort? n n n IDS Can also be configured to be an IPS Software solution to IDS/IPS To be IPS, the sniffing machine needs 2 interfaces Network based n n Switch – port mirroring Hub – sniff all

Snort Network intrusion detection system n Real-time traffic analysis n Packet logging n Detects OS fingerprinting attempts n n Protocol implementation details

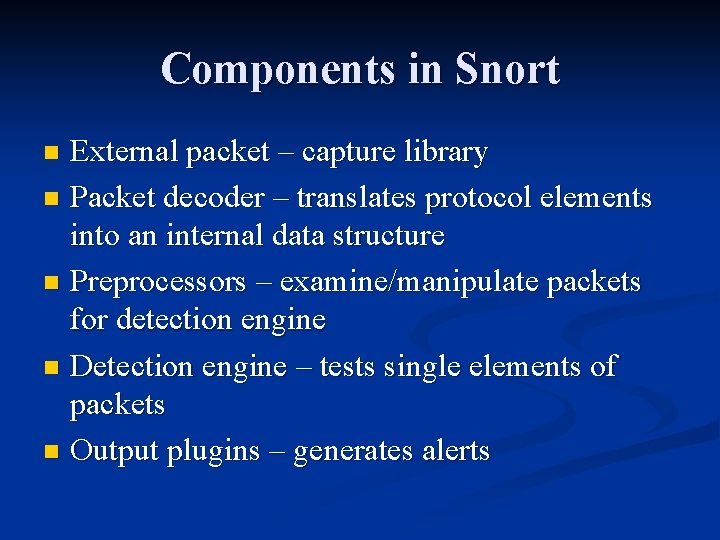
Components in Snort External packet – capture library n Packet decoder – translates protocol elements into an internal data structure n Preprocessors – examine/manipulate packets for detection engine n Detection engine – tests single elements of packets n Output plugins – generates alerts n


1. Capturing traffic (libpcap/Win. Pcap) Sniffs line and gets raw packets off the network n Raw packets needed to detect various attacks n Can only process one packet at a time n n We use Win. Pcap Windows Packet Capturing n Captures packets traveling across a network

2. Packet decoder Series of decoders that each decode specific protocol elements n Data structure is filled up with decoded packet data n Data structures passed to preprocessors and the detection engine n

3 a. Preprocessors n Two types n Examine packets -Used for non-signature based attacks n Modify packets in preparation for detection engine -Normalize traffic n Packets cycle through all preprocessors Keeps attackers from hiding other traffic n Multiple violations may be seen this way n

3 b. Preprocessors n Fragmentation n Malicious traffic n Modify packet headers n Do. S – Ping of Death Stateful inspections n Stateless connections n n n SYN-ACK (connection not complete) IP protocol checks – beyond TCP

4. Detection engine n Uses a decision tree Eg) if the packet is TCP, the packet is passed to the portion that deals with TCP n The first signature that matches is applied, the next packet is analyzed n n Priority is very important n High level attacks must be prioritized currently

5. Output plugins Dumps alert data to a file/resource n Unified format n One of many options n Fastest possible n n Alert file – Attack summary, IPs, protocol used, etc listed n Packet file – actual packet info n Database, file dumps, external applications

snort_inline turns Snort into IPS Set up rules to drop packets n Set up alerts to log attacks n Set up rules to cut connection n TCP reset for example drop tcp any -> any 80 (classtype: attempted-user; msg: "Port 80 connection initiated"; )

General rule structure n _action _protocol _ip 1 _direction _ip 2 (options)

_action options n _action _protocol _ip 1 _direction _ip 2 (options) n alert - generate an alert using the selected alert method, and then log the packet log - log the packet pass - ignore the packet activate - alert and then turn on another dynamic rule dynamic - remain idle until activated by an activate rule , then act as a log rule n n

_protocol options _action _protocol _ip 1 _direction _ip 2 (options) n TCP, IP, UDP, ICMP (, ARP, IGRP, GRE, OSPF, RIP, IPX) n

_ip options _action _protocol _ip 1 _direction _ip 2 (options) n IP address/netmask, port, ! to negate n n n Any, individual ip alert tcp any -> 192. 168. 1. 0/24 111 port IP address netmask

_direction options n _action _protocol _ip 1 _direction _ip 2 (options) -> is from source to destination n <> is from source to destination and destination to source n

Rule options _action _protocol _ip 1 _direction _ip 2 (options) n alert tcp any -> $HOME_NET 31337 (msg: "BLEEDING-EDGE ATTACK RESPONSE Potential root shell connection detected!"; flow: established, to_server; tag: session, 20, packets; classtype: bad-unknown; sid: 2001545; rev: 2; ) n

Rule structure for wireless <action> wifi <mac> <direction> <mac> (<rule options>)

<MAC address> Rule options # Single MAC Address 00: DE: AD: BE: EF: 00 n # MAC Address List [00: DE: AD: BE: EF: 00, 00: DE: AD: C 0: DE: 00, . . ] n

Logs Using syslog logs n Sawmill n Logs need to be converted to plaintext to be processed n Web interface to analyze traffic n Windump -r _log_ -tt > _txt. File_ n

Snort Status DB connection is problematic for Free. BSD version n Snort currently captures traffic and creates logs based on rules n Lab 3 is now the sniffer box n n n Win. Pcap and Snort Plugged into physical port FA 0/23 n Receiving all switch traffic

NMAP

Nmap Network Mapper n Discovers services available on different hosts in a network n Command line, GUI versions n n Nmap and nmapfe packages in Free. BSD

Features Enumerates ports on target machines n Identify services running on those ports n OS fingerprinting n

Typical uses List services available on a machine n Run network security audit of machines n Identify computers that may be exploited n Audit individual machine security n

nmapfe

Just the beginning… Nmap is one tool in an arsenal for black hat hackers n Prelude to exploitation tools n n Metasploit - used for actual exploitation attempt

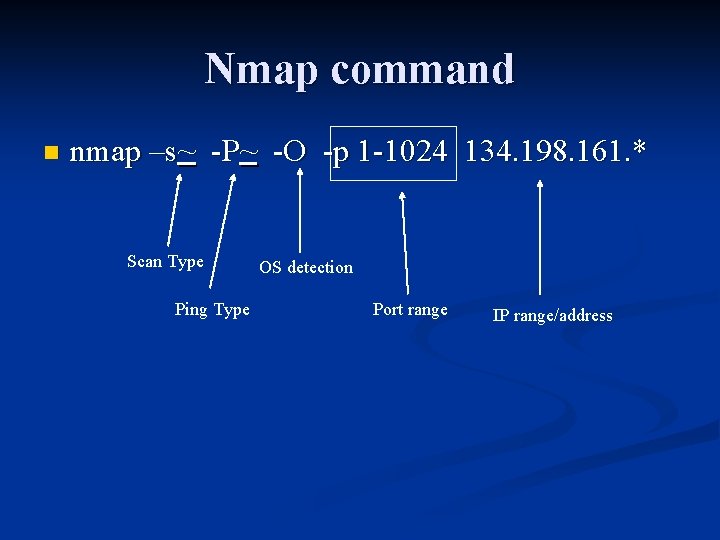
Nmap command n nmap –s~ -P~ -O -p 1 -1024 134. 198. 161. * Scan Type Ping Type OS detection Port range IP range/address

Enumerate ports / services n “Well-known” or “Interesting” ports - 1 -1024 - 65, 535 total TCP & UDP ports n Port/Protocol State Service Name

Types of scans n n http: //www. secguru. com/nmap_cheatsheet s. S (TCP SYN scan) – half open scan; stealthy n n SYN/ACK – listening; RST – non-listener s. T (TCP connect scan) – uses system call to make connection; easily logged s. U (UDP scans) – sends empty UDP header to targeted ports; code returned indicates port state s. N; -s. F; -s. X (TCP Null, FIN, and Xmas scans) n If SYN, RST, ACK bits not set (TCP RFC) n n Any incoming segment not containing RST causes a closed port to respond with an RST No response if port is open

OS detection n Uses TCP/IP fingerprinting OS particular implementation of protocol indicates target host OS n Checked against DB of known DB signatures n n Why hide OS? n Black hat hackers might try OS specific exploits if known

n http: //www. csee. umbc. edu/~krishna/cs 491 n/sn ort_manual. pdf
 5-a-day language review week 17 answer key
5-a-day language review week 17 answer key Maggie oconnor
Maggie oconnor Nancy oconnor
Nancy oconnor Chris oconnor
Chris oconnor Metasploit nmap
Metasploit nmap Nmap http-enum
Nmap http-enum How to scan ports with nmap
How to scan ports with nmap Splunk nmap
Splunk nmap Intro to kali linux
Intro to kali linux Nessus and nmap
Nessus and nmap Seguridad ofensiva
Seguridad ofensiva Pros and cons of nmap
Pros and cons of nmap Veronica kovah
Veronica kovah Snort demo
Snort demo Acid snort
Acid snort Snortsnarf
Snortsnarf Snort proxy
Snort proxy Snort barnyard
Snort barnyard Snort
Snort Snort antivirus
Snort antivirus Snort graphical interface
Snort graphical interface Mysql nn
Mysql nn What is snort preprocessor
What is snort preprocessor Snort ventajas y desventajas
Snort ventajas y desventajas Snort meaning
Snort meaning Acid snort
Acid snort Snort rules examples
Snort rules examples Postech cse
Postech cse Charlie davis motors
Charlie davis motors Matthew moisan
Matthew moisan Matthew 14 22 33
Matthew 14 22 33 Matt hardman
Matt hardman Matt goodfellow poet
Matt goodfellow poet Sanserifer
Sanserifer Matt naish
Matt naish