Using Nessus and Nmap to Audit Large Networks
























































- Slides: 92

Using Nessus and Nmap to Audit Large Networks By Greg Johnson Principal Security Analyst University of Missouri – Columbia Johnson. G@missouri. edu Missouri Network Security Symposium December 18, 2001 Updated December 19, 2001

Using Nessus and Nmap to Audit Large Networks This presentation with any additional notes and corrections is at: www. missouri. edu/~johnsong/audit

Using Nessus and Nmap to Audit Large Networks Management Goal: Justify regular use of NMAP, NESSUS, and similar external, network-based security auditing tools in your organization. Technology Goal: Show strategies to effectively use these tools in light of six audit-impeding challenges such as personal firewalls.

Why Audit? • Find problems that need fixing. • Significant security vulnerabilities persist even after best practices. • Pilots, Santa Claus, & quality assurance. “Trust, but verify. ”

Why Audit? • Clustering 1, or, Bugs Have Families: An audit won’t find all vulnerabilities. But fixing the ones the audit does find tends also to fix many that the audit did not identify. • Clustering 2: Work groups that have good security (few problems) are doing something right. Imitate them.

Why Audit? • Be a prophet: “I know 600 machines that will have security incidents. ” • Such measurements support: – Requests for security budget $$ – Requests for security training for your enterprise. – Requests for mitigating measures such as better firewalls, filters—or disaster recovery!

Why Audit? • By-products of frequent, large-scale security auditing: – Inventory of systems and services. “How many `servers’ do we have? ” – Ability to respond quickly to applicationspecific exploitations such as Code Red. – Identification of unauthorized systems & services (intruders, unacceptable use).

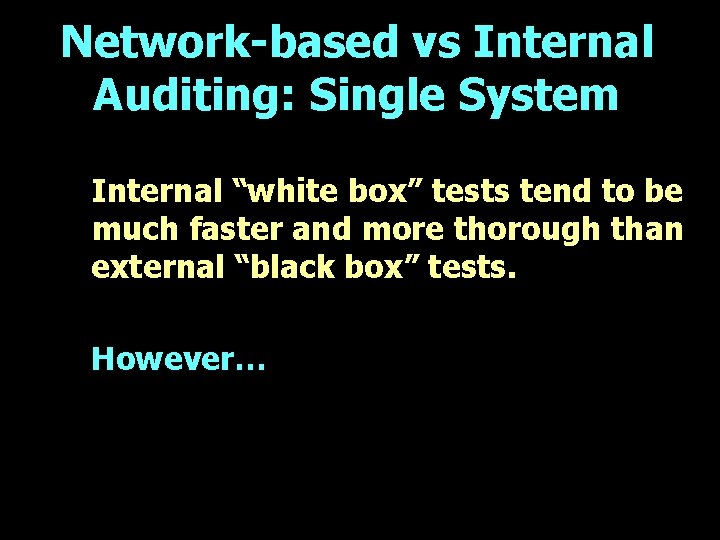
Network-based vs Internal Auditing: Single System Internal “white box” tests tend to be much faster and more thorough than external “black box” tests. However…

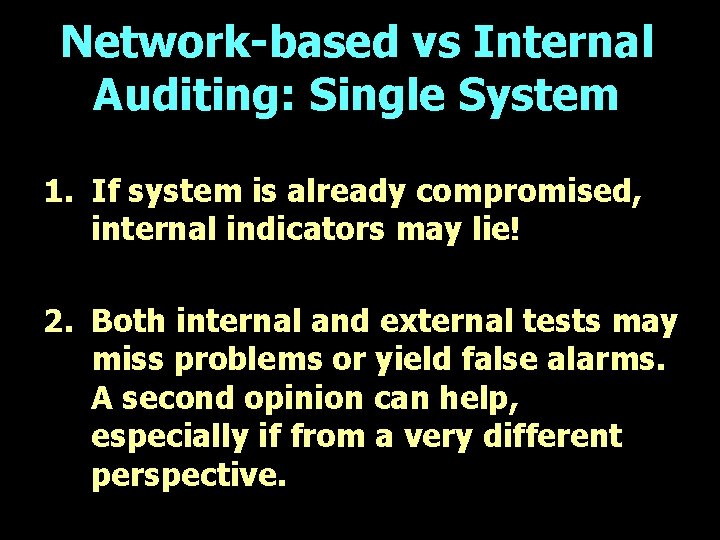
Network-based vs Internal Auditing: Single System 1. If system is already compromised, internal indicators may lie! 2. Both internal and external tests may miss problems or yield false alarms. A second opinion can help, especially if from a very different perspective.

Network-based vs Internal Auditing: Single System 3. Internally installed security tools are subject to attacks, as in recent Goner virus which disabled antivirus and personal firewall.

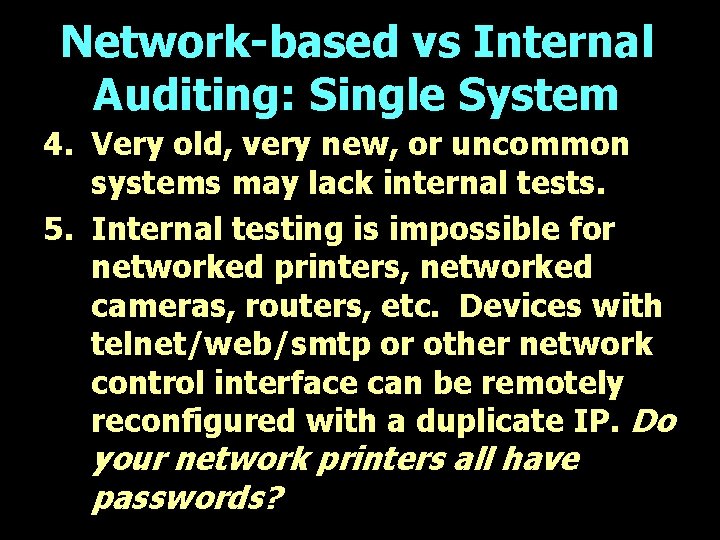
Network-based vs Internal Auditing: Single System 4. Very old, very new, or uncommon systems may lack internal tests. 5. Internal testing is impossible for networked printers, networked cameras, routers, etc. Devices with telnet/web/smtp or other network control interface can be remotely reconfigured with a duplicate IP. Do your network printers all have passwords?

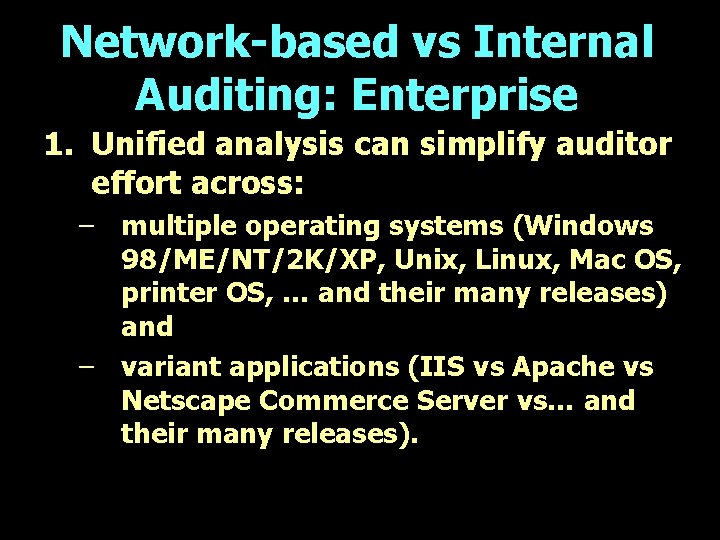
Network-based vs Internal Auditing: Enterprise 1. Unified analysis can simplify auditor effort across: – multiple operating systems (Windows 98/ME/NT/2 K/XP, Unix, Linux, Mac OS, printer OS, … and their many releases) and – variant applications (IIS vs Apache vs Netscape Commerce Server vs… and their many releases).

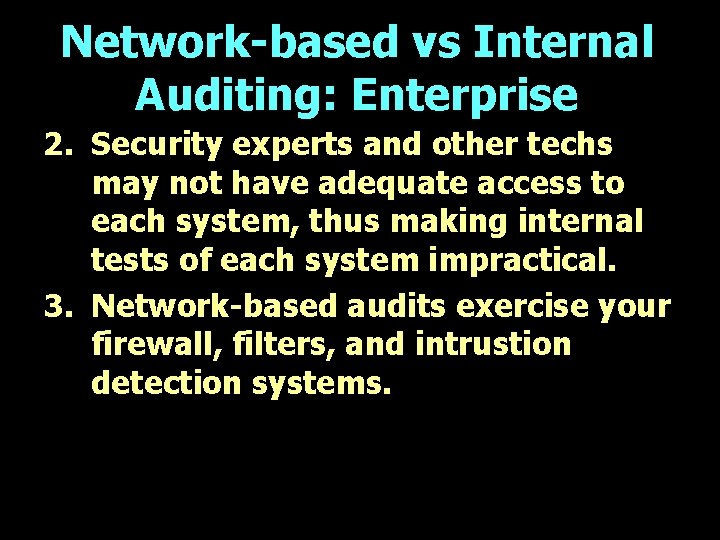
Network-based vs Internal Auditing: Enterprise 2. Security experts and other techs may not have adequate access to each system, thus making internal tests of each system impractical. 3. Network-based audits exercise your firewall, filters, and intrustion detection systems.

Network-based vs Internal Auditing: Perspective As Robert Burns wrote: Wad a gift The giftie gie us, To see ourselves As others see us. Intruders use network-based auditing!

Background: TCP & UDP Internet Protocol supports two major transport protocols: TCP: Transmission Control Protocol – Verifies that packets reach destination intact. UDP: User Datagram Protocol - No delivery guarantee. Ok for video and audio, or where application checks valid delivery.

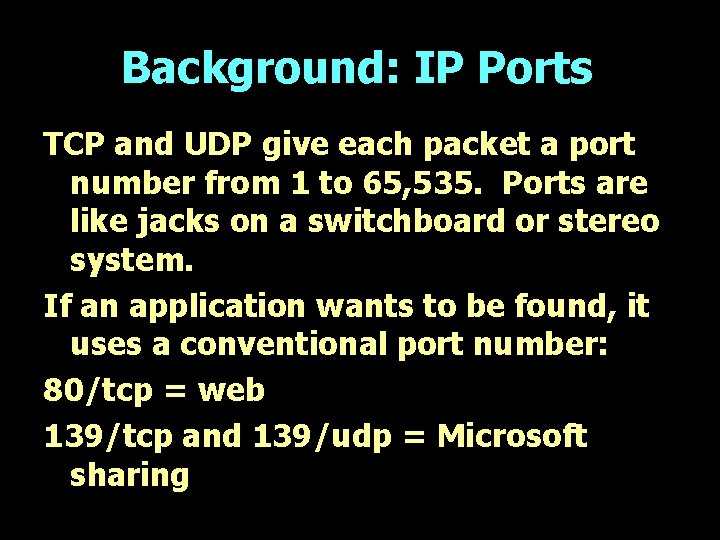
Background: IP Ports TCP and UDP give each packet a port number from 1 to 65, 535. Ports are like jacks on a switchboard or stereo system. If an application wants to be found, it uses a conventional port number: 80/tcp = web 139/tcp and 139/udp = Microsoft sharing

Background: Hide & Seek • If an application wants to be found, it can also use a local mechanism like RPC or a broker like Napster, Aimster, etc to locate port number by name. • Some applications don’t want to be found! Subseven, Netbus, …. To find these, you must search all 65, 535 ports or else sniff traffic while the application is communicating (Intrusion Detection System. )

Background: Port Status A port can be: • Closed (not in use), • Open (listening), or • Filtered (the client computer asked for open or closed status report, and the target computer did not reply, usually due to a firewall. )

NMAP is one of many port-scanning programs. Relative to other tools, NMAP is particularly efficient in scanning simultaneously testing multiple ports and multiple hosts. NMAP is free, open source, from www. insecure. org.

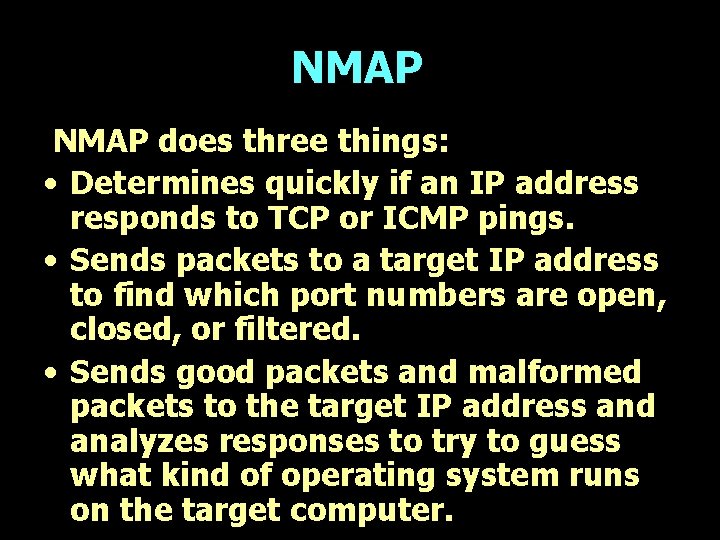
NMAP does three things: • Determines quickly if an IP address responds to TCP or ICMP pings. • Sends packets to a target IP address to find which port numbers are open, closed, or filtered. • Sends good packets and malformed packets to the target IP address and analyzes responses to try to guess what kind of operating system runs on the target computer.

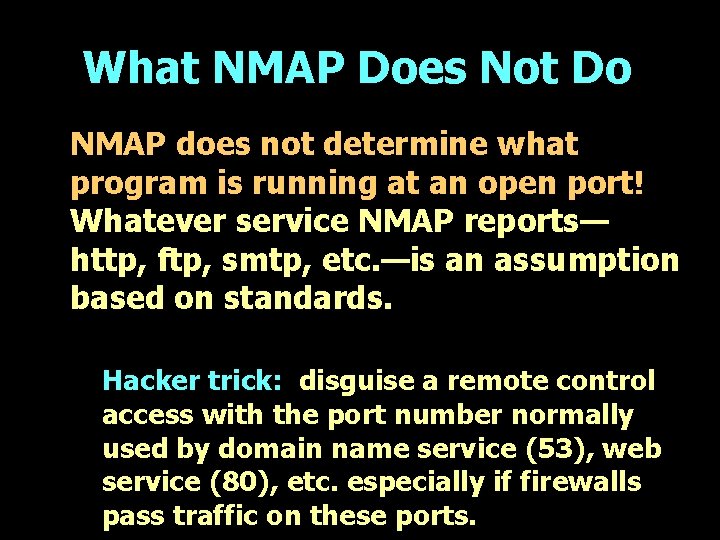
What NMAP Does Not Do NMAP does not determine what program is running at an open port! Whatever service NMAP reports— http, ftp, smtp, etc. —is an assumption based on standards. Hacker trick: disguise a remote control access with the port number normally used by domain name service (53), web service (80), etc. especially if firewalls pass traffic on these ports.

Parlez HTTP? Habla DNS? NESSUS takes over where NMAP leaves off. 1. NESSUS first calls NMAP or uses previous NMAP results to find open ports. NESSUS can also check specified ports without a prior NMAP. 2. NESSUS then can check an open port for dozens of known protocols, such as HTTP, FTP, SMTP (e-mail), Subseven (remote control)…. 3. NESSUS, having determined what service runs on a port, sends data to that service to exploit known security vulnerabilties.

Is Scanning Dangerous? Both NMAP and NESSUS aim to never damage data. In MU’s NMAP and NESSUS scanning of 13, 000 connections in its network, no data has ever been lost through scanning.

Is Scanning Dangerous? HOWEVER! • NMAP and especially NESSUS can freeze scanning targets. The network application may freeze. The entire system may require restarting. Some devices such as printers or routers may reset themselves—or not.

Is Scanning Dangerous? • In MU’s scanning, freezes are rare: about one in six hundred general purpose systems for tests that are not explicitly dangerous. • NESSUS designates about 10% of its tests as dangerous, denial of service attacks such as oversize data or flooding. In tests of 200 diverse systems, around one third eventually fell to a denial of service attack.

Is Scanning Dangerous? A full 65, 535 TCP port scan and service check generates – at least 5 MB of traffic to the target – and at least 6 MB in reply. – Most of this traffic is small packets. Hence…

Is Scanning Dangerous? • Typical testing over a 10 or 100 Mbps connection will noticeably but not painfully slow target system performance for around 15 minutes. • Scanning multiple targets through one network device can slow that subnet’s performance. • NMAP and NESSUS offer options to scan slowly or aggressively, and to randomize target sequence.

Safe Scans • Hence, scan critical infrastructure systems with someone ready to restart systems. Performance monitoring may yield insights. • For extra safety, move NESSUS denial of service tests out of their normal directory.

Safe Scans ‘Tis better to find exposures • from a friend who can desist and heal, • than from adversaries who repeatedly attack whenever they want.

Anti-Scan Measures • Testing is a stimulus/response match. If no response arrives in a specified time, the test may be inconclusive.

Anti-Scan Measures One way to resist attacks is to limit rate of responses to certain requests such as “is this port open? ”. That excellent strategy slows down tests by both the bad guys and the good guys. webmail. cotse. com/CIE/RFC/ 1812/74. htm “Requirements for IP Version 4 Routers” section on rate-limiting

Scanning Tools • Commercial: ISS, • Freeware: NMAP, NESSUS, NBTSCAN, LEGION, . . . • Network service: Mix of Unix, NT implementations

For-Free Scans Via Web Useful as yet another perspective. See how enterprise gateway/firewall affects vulnerability scan. Not comprehensive. • • • www. dslreports. com/scan security 2. norton. com hackerwhacker. com: 4000/startdemo. dyn www. securitylogics. com/portscan. adp www. securityspace. com/sspace A variety of companies offer for a fee comprehensive and regularly-scheduled vulnerability scanning services.

NMAP • • www. insecure. org Unix support; NT version promised. NT port via e-eye Performance determined mainly by presence of personal firewalls and other mechanisms designed to impede scanning.

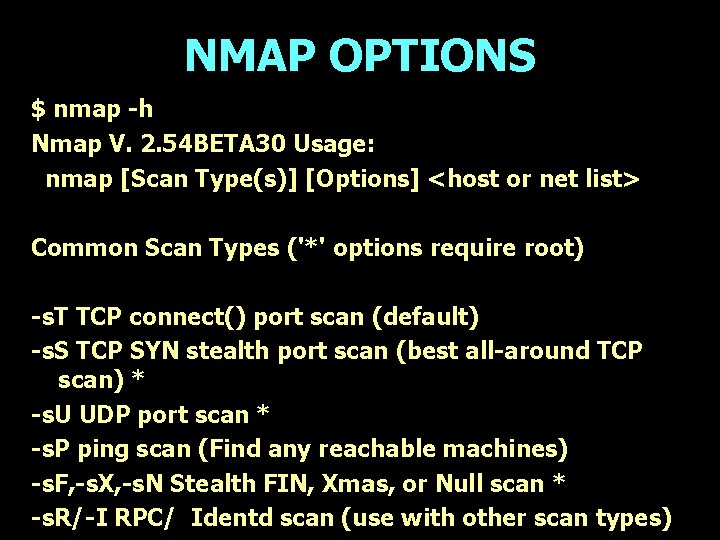
NMAP OPTIONS $ nmap -h Nmap V. 2. 54 BETA 30 Usage: nmap [Scan Type(s)] [Options] <host or net list> Common Scan Types ('*' options require root) -s. T TCP connect() port scan (default) -s. S TCP SYN stealth port scan (best all-around TCP scan) * -s. U UDP port scan * -s. P ping scan (Find any reachable machines) -s. F, -s. X, -s. N Stealth FIN, Xmas, or Null scan * -s. R/-I RPC/ Identd scan (use with other scan types)

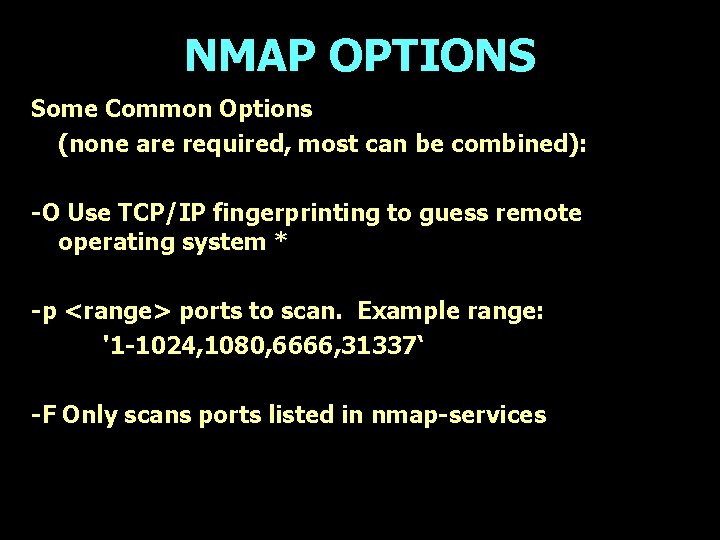
NMAP OPTIONS Some Common Options (none are required, most can be combined): -O Use TCP/IP fingerprinting to guess remote operating system * -p <range> ports to scan. Example range: '1 -1024, 1080, 6666, 31337‘ -F Only scans ports listed in nmap-services

NMAP OPTIONS -P 0 Don't ping hosts (needed to scan www. microsoft. com and others) -Ddecoy_host 1, decoy 2[, . . . ] Hide scan using many decoys -T <Paranoid|Sneaky|Polite|Normal| Aggressive|Insane> General timing policy -n/-R Never do DNS resolution/Always resolve [default: sometimes resolve]

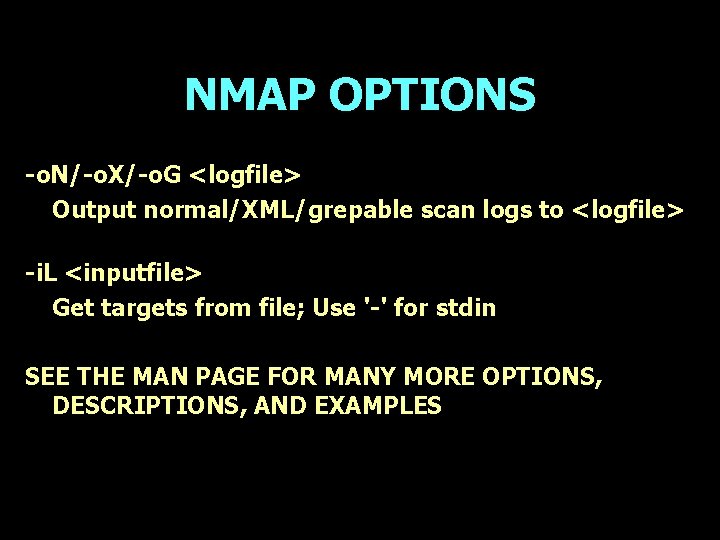
NMAP OPTIONS -o. N/-o. X/-o. G <logfile> Output normal/XML/grepable scan logs to <logfile> -i. L <inputfile> Get targets from file; Use '-' for stdin SEE THE MAN PAGE FOR MANY MORE OPTIONS, DESCRIPTIONS, AND EXAMPLES

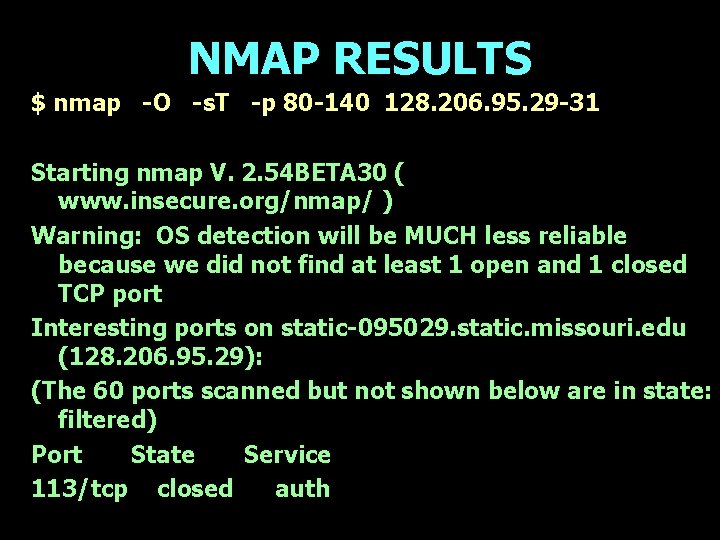
NMAP RESULTS $ nmap -O -s. T -p 80 -140 128. 206. 95. 29 -31 Starting nmap V. 2. 54 BETA 30 ( www. insecure. org/nmap/ ) Warning: OS detection will be MUCH less reliable because we did not find at least 1 open and 1 closed TCP port Interesting ports on static-095029. static. missouri. edu (128. 206. 95. 29): (The 60 ports scanned but not shown below are in state: filtered) Port State Service 113/tcp closed auth

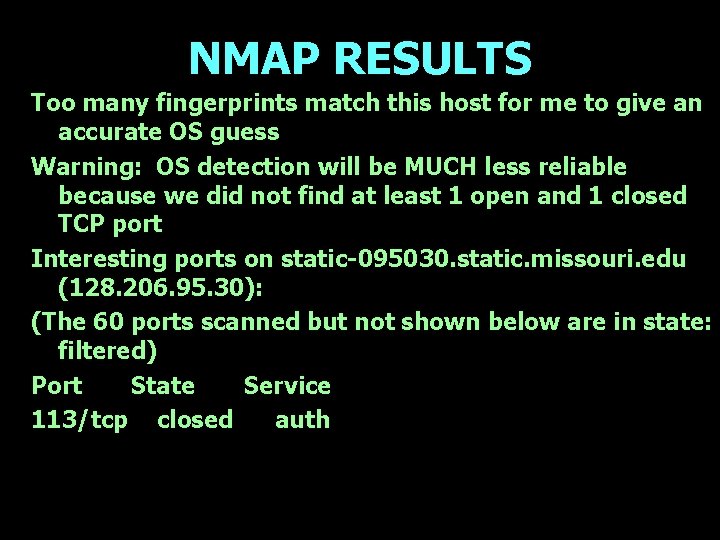
NMAP RESULTS Too many fingerprints match this host for me to give an accurate OS guess Warning: OS detection will be MUCH less reliable because we did not find at least 1 open and 1 closed TCP port Interesting ports on static-095030. static. missouri. edu (128. 206. 95. 30): (The 60 ports scanned but not shown below are in state: filtered) Port State Service 113/tcp closed auth

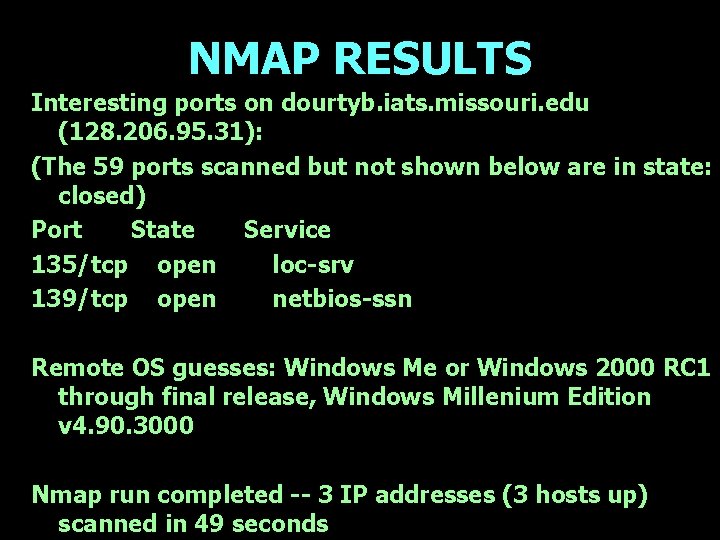
NMAP RESULTS Interesting ports on dourtyb. iats. missouri. edu (128. 206. 95. 31): (The 59 ports scanned but not shown below are in state: closed) Port State Service 135/tcp open loc-srv 139/tcp open netbios-ssn Remote OS guesses: Windows Me or Windows 2000 RC 1 through final release, Windows Millenium Edition v 4. 90. 3000 Nmap run completed -- 3 IP addresses (3 hosts up) scanned in 49 seconds

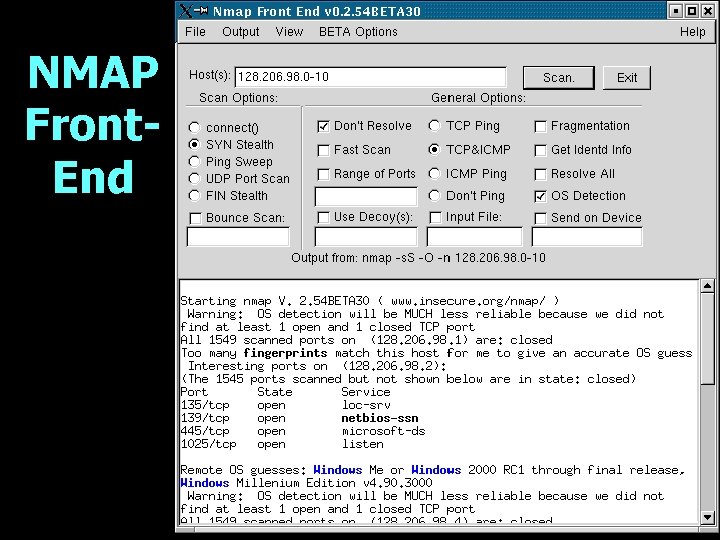
NMAP Front. End

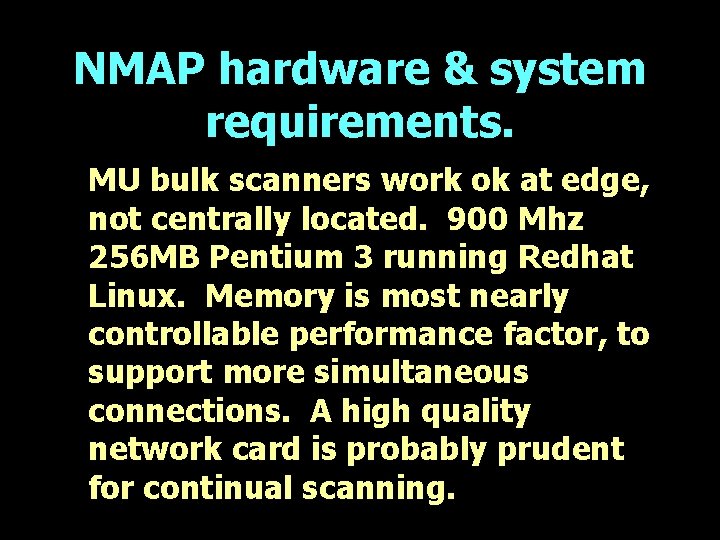
NMAP hardware & system requirements. • MU experience. Scan of 13, 000 connections in Class B network (128. 206. *. *, 65, 535 addresses) for one port over mostly 100 Mbps edge network from one source takes about 40 minutes. Dividing the network between two source systems even in the same subnet halves elapsed time.

NMAP PERFORMANCE DOESN’T ALWAYS SCALE Scanning 1 port on 10, 000 computers can be faster than scanning 10, 000 ports on one computer

NMAP PERFORMANCE DOESN’T ALWAYS SCALE An unauthorized remote control program such as Subseven likes to hide out on an arbitrary UDP port. • Scanning all 65, 535 UDP ports of a Windows 98 system can take as little as 2 minutes. • The same scan of a Solaris system can take eleven hours due to RFC 1812 error-reply rate-limiting.

NMAP hardware & system requirements. MU bulk scanners work ok at edge, not centrally located. 900 Mhz 256 MB Pentium 3 running Redhat Linux. Memory is most nearly controllable performance factor, to support more simultaneous connections. A high quality network card is probably prudent for continual scanning.

NMAP as front end • NMAP and NESSUS can output results in formats that can, with typically a three line Perl or VB script, load into a spreadsheet or database. Besides NESSUS, other tools can utilize or add value to NMAP’s inventory of open ports. Here are some Unix tools:

After NMAP • sdig (www. exploits. org/sdig) obtain IP address' MAC address from its router. • nbtscan - obtain IP address' Netbios name, Netbios user, Netbios report of MAC address. Breathtakingly fast scanner if you're looking only for Netbios/NMB services.

After NMAP • wget - get web or FTP page and headers. • wget http: //whever. blah: 1214 = Morpheus/Kazaa

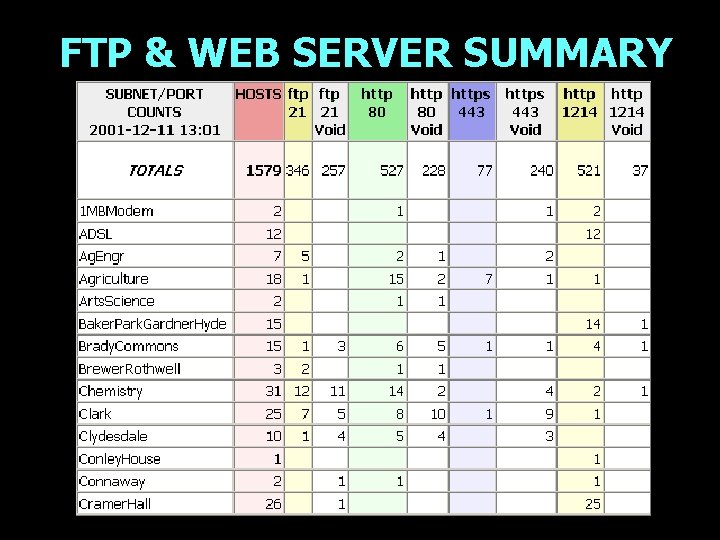
FTP & WEB SERVER SUMMARY

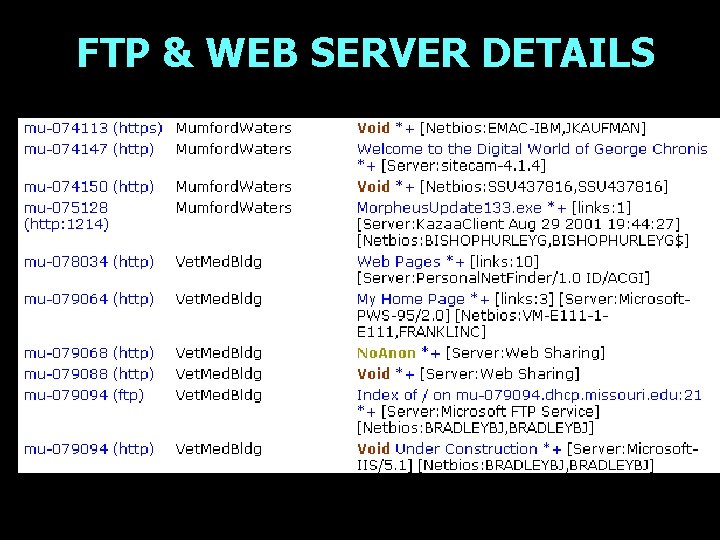
FTP & WEB SERVER DETAILS

After NMAP • coderedscan. pl - posted on UNISOG list, also finds traces of NIMDA. • Open e-mail relay tests - Manually via www. abuse. net

NESSUS • www. nessus. org • Secure client/server architecture • Server must be on Unix system. • Clients for Unix, Windows, Java applets, and command line of server. Client can securely login with ID and password or certificate, and can be restricted to set of IP addresses they can scan.

NESSUS PERFORMANCE • At MU Nessus runs on Linux systems previously described. • NESSUS non-dangerous tests on a typical host, take about 10 minutes more in addition to NMAP scan. Including NMAP reconnaissance, NESSUS rarely takes more than 20 minutes per host.

NESSUS PERFORMANCE • A NESSUS server can handle – simultaneous tests of multiple hosts – multiple tests per host. • MU has settled on 20 hosts per scanner. If NMAP is not mired with a personal firewall, a full NMAP+NESSUS scan process 100 hosts per hour.

NESSUS PERFORMANCE • However, in a hundred targets you will find a few that will occupy NMAP full scan for half a day each unless you take care to separate these slow-movers.

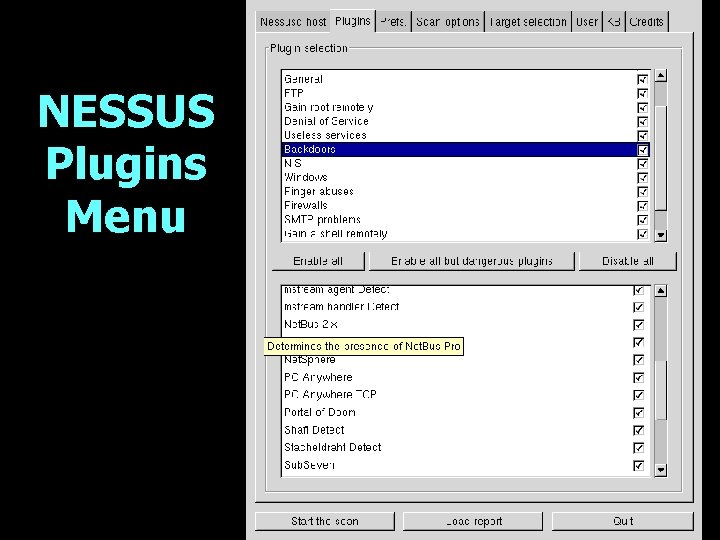
VULNERABILITY TESTS • Plugin architecture - 812 plugins as of Dec 18, 2001, with around 2 new, and a dozen updated plugins every week. Almost all plugins are in a C-like script language, “NASL”. C can also be used for plugins. You can make your own plugins.

VULNERABILITY TESTS • Knowledgebase - test results for an IP can be preserved for specified time, to avoid retesting. • NESSUS applies tests conditionally: web buffer overflows (such as Code Red) are applied only to http ports. You can tell Nessus to respect banners, so if a host claims to use Apache don’t run IIS tests.

NESSUS Plugins Menu

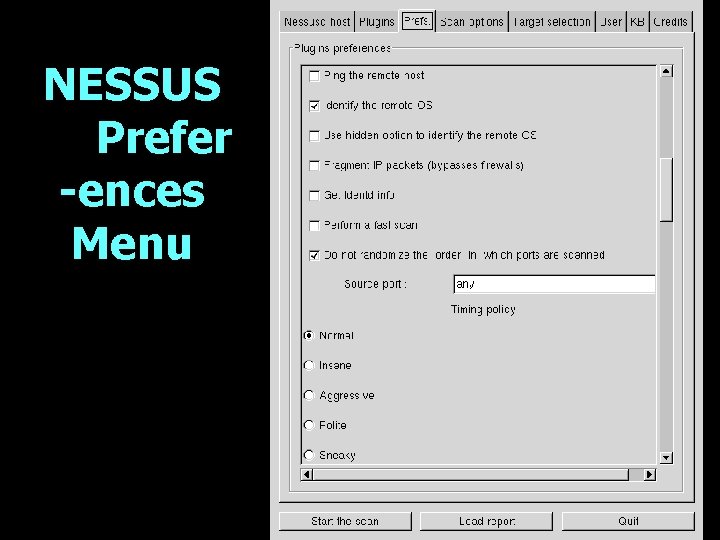
NESSUS Prefer -ences Menu

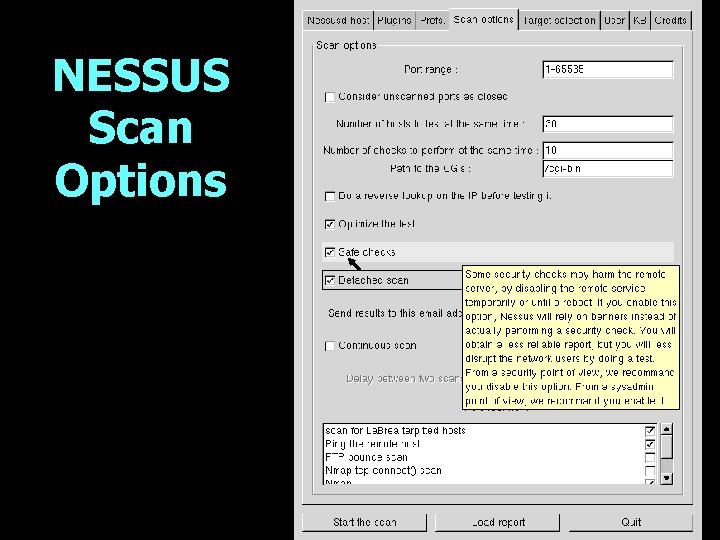
NESSUS Scan Options

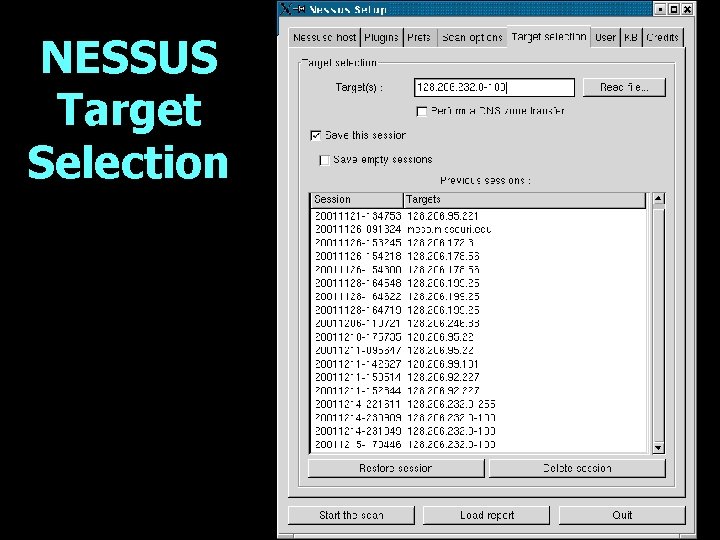
NESSUS Target Selection

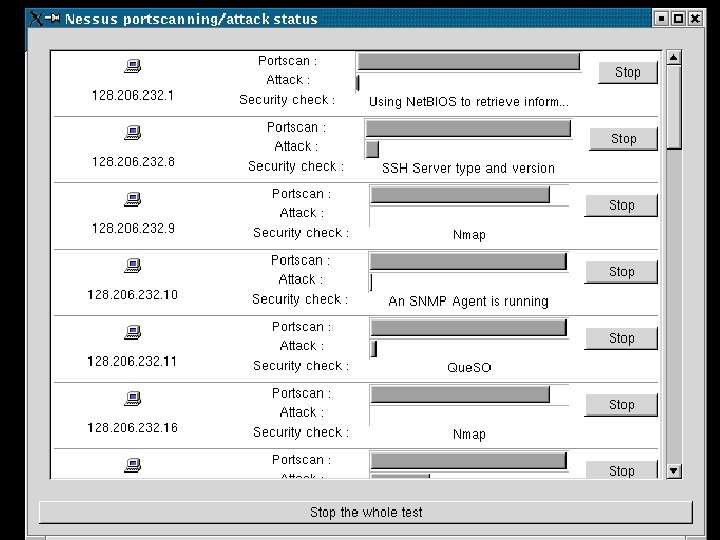
NESSUS Status

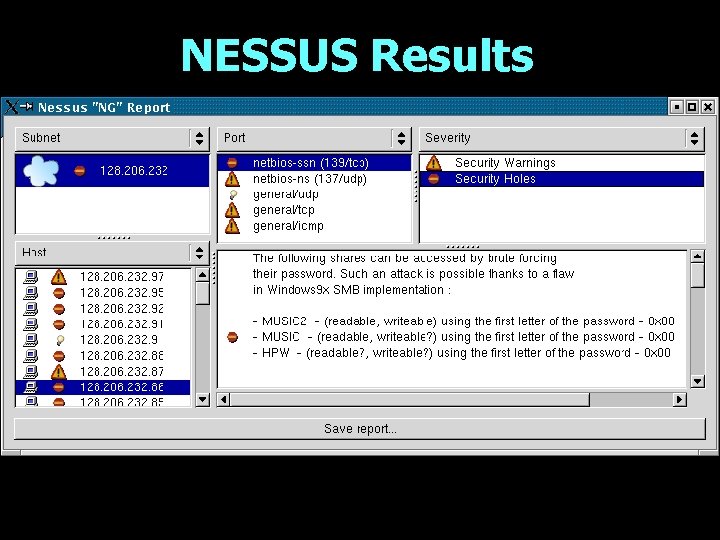
NESSUS Results

NESSUS Results • Reports - Nessus produces reports in several formats including HTML with management-friendly pie charts. Results can be imported into spreadsheet databases to try to understand enterprise issues.

NESSUS RESULTS • Reports offer links or succinct advice for fixing most vulnerabilities. • Relative to other scanning products, NESSUS has exhibited fewer false alarms, finds more vulnerabilities, and produces appropriate levels of advice.

TECHIE ADVICE: Versions 1. NMAP is stable, months between updates to beta. Use latest beta. 2. Currently, Nessus source code is updated a couple of times per week, beta version is updated about monthly. My advice: use latest Nessus beta.

TECHIE ADVICE: Optimization 3. Read the Changelogs and Readme files, if not source and plugins. These contain tips on optimization. 4. NMAP option for timeouts of scan allows –T Aggressive. -T Normal seems in many cases faster apparently due to dynmaic adjustment of timeouts.

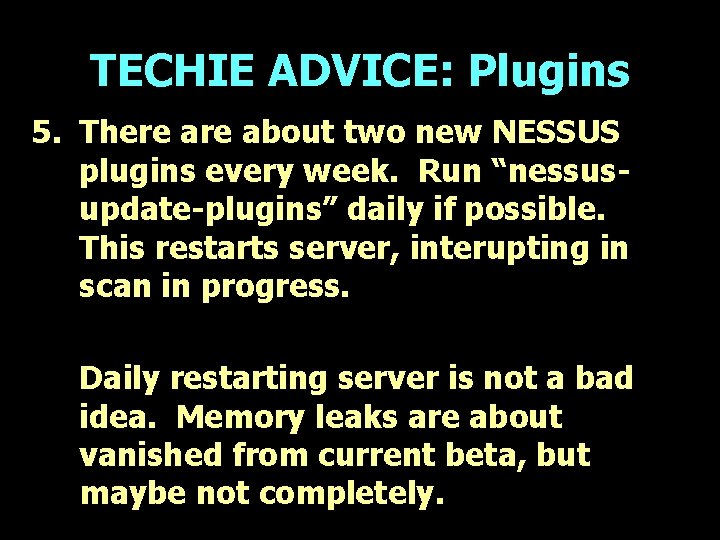
TECHIE ADVICE: Plugins 5. There about two new NESSUS plugins every week. Run “nessusupdate-plugins” daily if possible. This restarts server, interupting in scan in progress. Daily restarting server is not a bad idea. Memory leaks are about vanished from current beta, but maybe not completely.

TECHIE ADVICE: Plugins 5. Spread scan. For example, scan addresses ending in “. 0”, then addresses ending in “. 1”, then addresses ending in “. 2”, etc. 6. Generate a fresh list of hosts to scan, iterating as above but skipping unallocated subnets, broadcast addresses, network devices, and things like printers that don’t merit frequent testing.

SIX AUDIT CHALLENGES AND STRATEGIC RESPONSES TO THEM 1. 2. 3. 4. 5. 6. First, Do No Harm Time Scan-Resistant Computers Identifying People Prioritizing Response to Audit Results

Challenge 1: First Do No Harm • Strategy: Get permission, and buyin from highest levels. "The difference between a hacker and a security analyst is permission. " John Greene, in SANS Institute Auditing With NMAP • Have your business case in order: mandates for security, risk analysis, "you can't manage what you don't measure", …

Challenge 1: First Do No Harm • Strategy: Start small • Strategy: Initial scan series run from 7 a. m. to 3 p. m. or whenever someone is available to restart systems. • Strategy: Maintain exception lists: infrastructure devices to be tested only by arrangement, delicate devices.

Challenge 2: Time • Strategy: More exception lists. Don't waste time scanning free subnets, broadcast addresses, rarely-changed devices such as routers and printers.

Challenge 2: Time • Strategy: Divide and conquer. Use multiple computers to speed throughput. Try to NMAP one port on many computers simultaneously rather than many ports on one computer.

Challenge 2: Time Recognize bottlenecks such as hubs, wireless, and firewalls where many computers funnel through the same network connection.

Challenge 2: Time Strategy: Test only for a few key vulnerabilities, not all 812+. A few vulnerabilities account for a disproportionate number of breakins and mischief.

Challenge 2: Time Sources of "top ten" current exploits: – www. incidents. org – aris. securityfocus. com – mynetwatchmn. com/mynetwatchman /topports. asp – your own records

Challenge 2: Time • Strategy: Detect new and updated systems, and scan these thoroughly. • Strategy: Offer self-service scanning.

Challenge 2: Time • Strategy: Avoid diminishing returns. Some tests consume much more time than others, but rarely find a host with this vulnerability, or the vulnerability is not severe. For example, detecting the PGP service was the 4 th most time-consuming scan in recent MU tests, but found no PGP hosts.

Challenge 2: Time • Strategy: Maintain OS inventory. • Strategy: Maintain network services inventory.

Challenge 3: Scan. Resistant Computers • Net good news for security, but a challenge for independently verifying security. • Symptoms: No reply to pings or other unexpected traffic. Rate limits on error replies or status requests. Teergruben - tar pits. Complete block of scan source that triggers some threshold. VPN.

Challenge 3: Scan. Resistant Computers • Strategy: Use SNMP, not ping, to find connected devices. • Strategy: Identify scan-resistant computers for special treatment. • Strategy: Use network IDS to identify open ports for priority attention.

Challenge 3: Scan. Resistant Computers • Strategy: Encourage users to configure firewall or intrusion detection software to accept traffic from authorized source(s). • Strategy: Self-service scanning. User can temporarily turn off personal firewall at least with respect to scan source.

Challenge 3: Scan. Resistant Computers Footnote: Conscientious people running personal firewalls, intrusion detection systems, access monitoring, etc. will notice your scanning and complain. Have written explanation and permission ready.

Challenge 4: Identifying Computers • IP address identifies connection, not computer. • Strategy: Use SNMP to identify systems by MAC and physical port.

Challenge 5: Identifying People • Strategy: Improved logging of use of central services. • Strategy: Create incentives to register computers with people (user and any support staff): – Access to scan results – theft tracing via MAC address – disconnection if problem and no registered support.

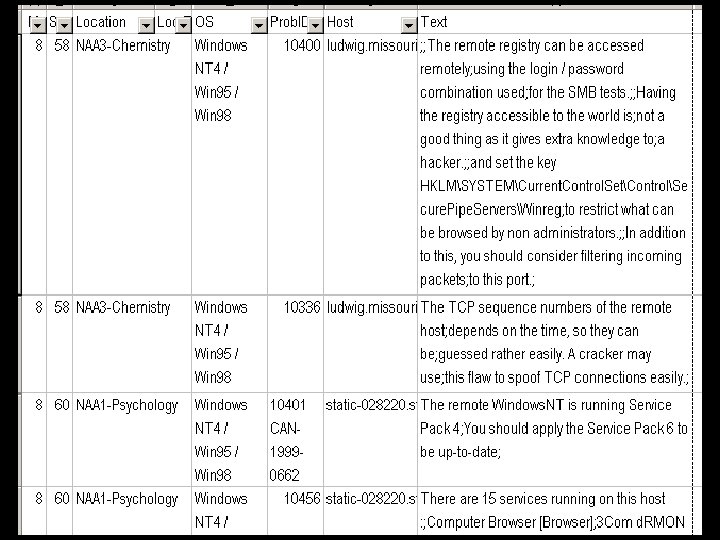
Challenge 6: Prioritizing Response • Strategy: Get the big picture by putting Nessus results in a spreadsheet. Use this to find: – Which extreme vulnerabilities do we have? – Which extreme vulnerabilities have lowcost solutions? – Are there any correlations with extreme vulnerabilities, such as department or operating system type?

Spreadsheet

POINTS TO REMEMBER • Vulnerability scanning can uncover security disasters before they happen. • Vulnerability scanning increases defense in depth. • Get permission and administrative buyin for scanning. • Phase in audits.

POINTS TO REMEMBER • Personal firewalls and kindred tar pits are highly desirable defenses. Authorized scanning must arrange to bypass these or else deal with them separately from hosts that scan much more quickly. • Don’t waste time detecting vulnerabilities that are relatively minor or that cost too much to fix.

POINTS TO REMEMBER • In scanning, the security analyst can have advantages over the intruder: – Permission to intensively scan. – Higher-speed access. – Access to SNMP identification or other means of identifying stealth targets, moving targets, and valuable targets. – Long term records. USE YOUR ADVANTAGES!