IP Network Scanning Outline n What is IP













- Slides: 27

IP Network Scanning

Outline n What is IP network scanning? n n Example Tool n n Concepts, motivation nmap Scanning types n n Host discovery port scanning Version detection OS detection 2

What is Scanning? n Method to gather information regarding the devices running on the network n Typically to discover services or servers on a network n n n Which hosts are up? Which services are offering? Do not confuse with “host vulnerability scanner” which further explore a computer by testing for common vulnerabilities (nessus, SAINT) common vulnerabilities 3

Why Scanning? n Network Security assessment n Evaluation and Auditing the security n n Firewall Penetration Test (Policy auditing) IDS proof/evaluation Identifying unexpected new servers Identifying open ports for n n proactively protect the network (Network and security admin) attacking it (Hackers) 4

nmap n A well known and free security scanner written by Fyodor (http: //insecure. org/nmap/) n n First released Sept 1, 1997 in Phrack 51 “The Art of Port Scanning” (http: //www. phrack. org/issues. html? issue=51 Many updates since then: n n n OS Detection (http: //www. phrack. org/issues. html? issue=54&id=9#article) Version scanning ARP Scanning Version 5. 00 as of this doc Usage: nmap [scan types] [options] <host or net …> 5

Why nmap n An excellent tool n n n Long history of development and support Continuous development and improvements “Industry Standard” port scanner 6

nmap features n Host Discovery: Which host is alive? n n Port Scanning : What services are available? n n Enumerating the open ports on one or more target computers Service and Version Detection : Which version is running? n n Identifying computers on a network, for example listing the computers which respond to pings (Ping Sweeps) Determine the application name and version number OS Detection: What platforms are served? n Remotely determining the OS and some hardware characteristics of network devices 7

Host Discovery n Querying multiple hosts using this method is referred to as ping sweeps n The most basic step in mapping out a network. n Several Sweeps technique n n n ICMP Sweeps Broadcast ICMP NON Echo ICMP TCP sweep UDP sweep 8

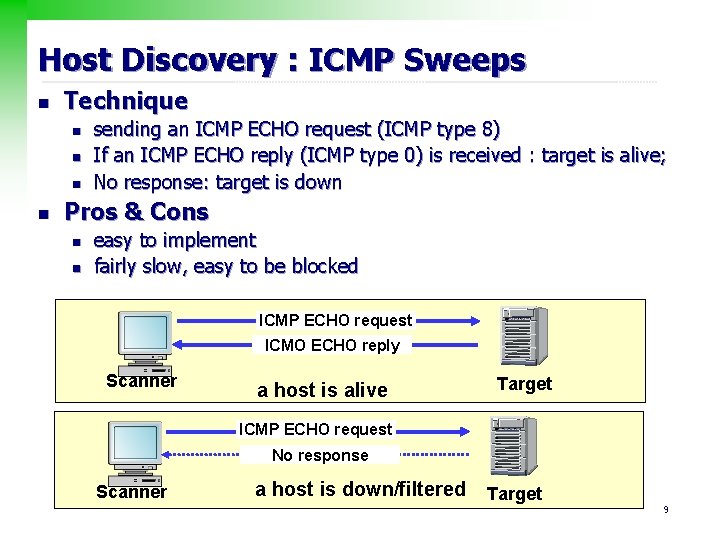
Host Discovery : ICMP Sweeps n Technique n n sending an ICMP ECHO request (ICMP type 8) If an ICMP ECHO reply (ICMP type 0) is received : target is alive; No response: target is down Pros & Cons n n easy to implement fairly slow, easy to be blocked ICMP ECHO request ICMO ECHO reply Scanner a host is alive Target ICMP ECHO request No response Scanner a host is down/filtered Target 9

Host Discovery : Broadcast ICMP n Sending ICMP ECHO request to the network and/or broadcast addresses n n Windows ignored this Most routers blocked this 10

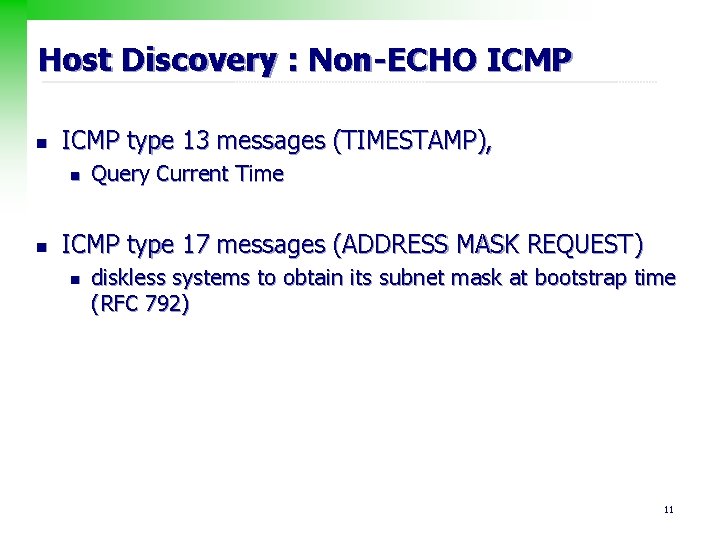
Host Discovery : Non-ECHO ICMP n ICMP type 13 messages (TIMESTAMP), n n Query Current Time ICMP type 17 messages (ADDRESS MASK REQUEST) n diskless systems to obtain its subnet mask at bootstrap time (RFC 792) 11

Host Discovery : TCP Sweeps n n Sending TCP ACK or TCK SYN packets The port number can be selected to avoid blocking by firewall n n Usually a good pick would be 21 / 22 / 23 / 25 / 80 But. . firewalls can spoof a RESET packet for an IP address, so TCP Sweeps may not be reliable. 12

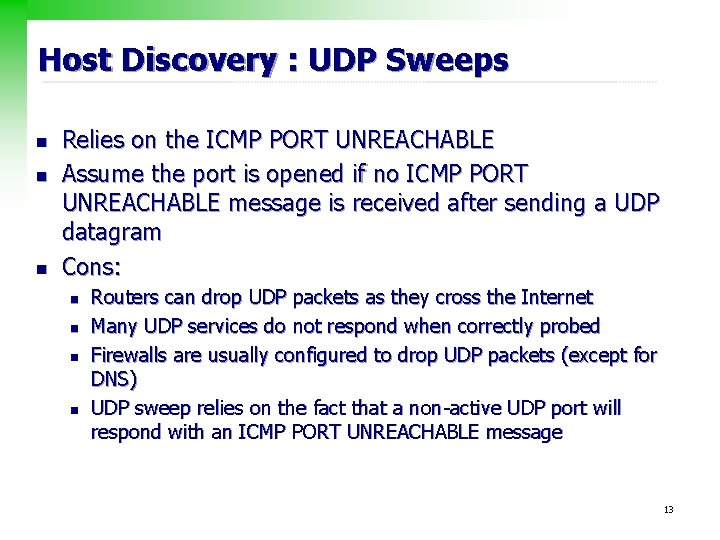
Host Discovery : UDP Sweeps n n n Relies on the ICMP PORT UNREACHABLE Assume the port is opened if no ICMP PORT UNREACHABLE message is received after sending a UDP datagram Cons: n n Routers can drop UDP packets as they cross the Internet Many UDP services do not respond when correctly probed Firewalls are usually configured to drop UDP packets (except for DNS) UDP sweep relies on the fact that a non-active UDP port will respond with an ICMP PORT UNREACHABLE message 13

nmap Host Discovery summary n n n n n s. L: List Scan - simply list targets to scan -s. P: Ping Scan - go no further than determining if host is online -PN: Treat all hosts as online -- skip host discovery -PS/PA/PU [portlist]: TCP SYN/ACK or UDP discovery to given ports -PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes -PO [protocol list]: IP Protocol Ping -n/-R: Never do DNS resolution/Always resolve [default: sometimes] --dns-servers <serv 1[, serv 2], . . . >: Specify custom DNS servers --system-dns: Use OS's DNS resolver -s. U: UDP Scan 14

Port Scanning n n To determine what services are running or in a LISTENING Some well known types n n TCP Connect Scan TCP SYN scan Stealth scan FTP bounce scan 15

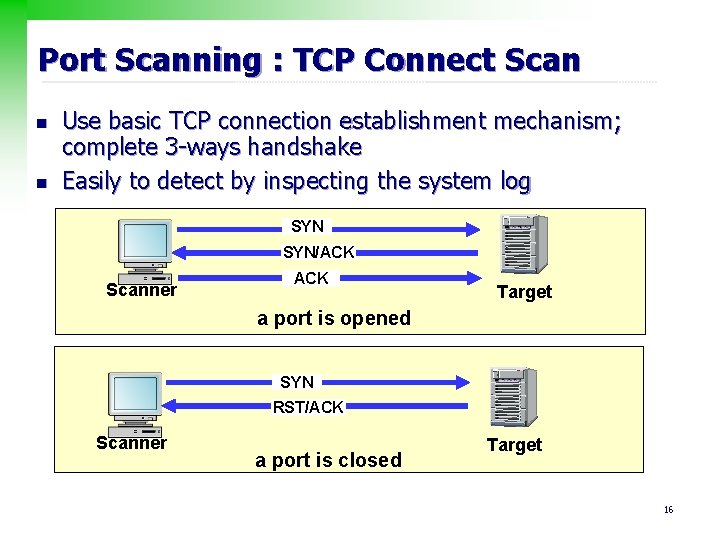
Port Scanning : TCP Connect Scan n n Use basic TCP connection establishment mechanism; complete 3 -ways handshake Easily to detect by inspecting the system log SYN/ACK Scanner ACK Target a port is opened SYN RST/ACK Scanner a port is closed Target 16

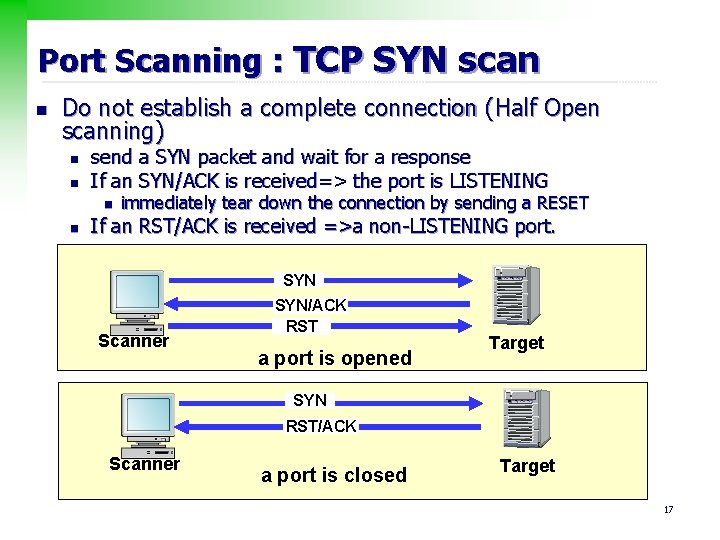
Port Scanning : TCP SYN scan n Do not establish a complete connection (Half Open scanning) n n send a SYN packet and wait for a response If an SYN/ACK is received=> the port is LISTENING n n immediately tear down the connection by sending a RESET If an RST/ACK is received =>a non-LISTENING port. SYN Scanner SYN/ACK RST a port is opened Target SYN RST/ACK Scanner a port is closed Target 17

Port Scanning : Stealth Scan n To gather information about target sites while avoiding detection n Try to hide themselves among normal network traffic Not to be logged by logging mechanism (stealth) Techniques n Flag Probe packets (Also called “Inverse mapping”) n n n Response is sent back only by closed port By determining what services do not exist, an intruder can infer what service do exist Slow scans rate n difficult to detect =>need long history log CERT reported this technique in CERT® Incident Note IN-98. 04 http: //www. cert. org/incident_notes/IN-98. 04. html 18

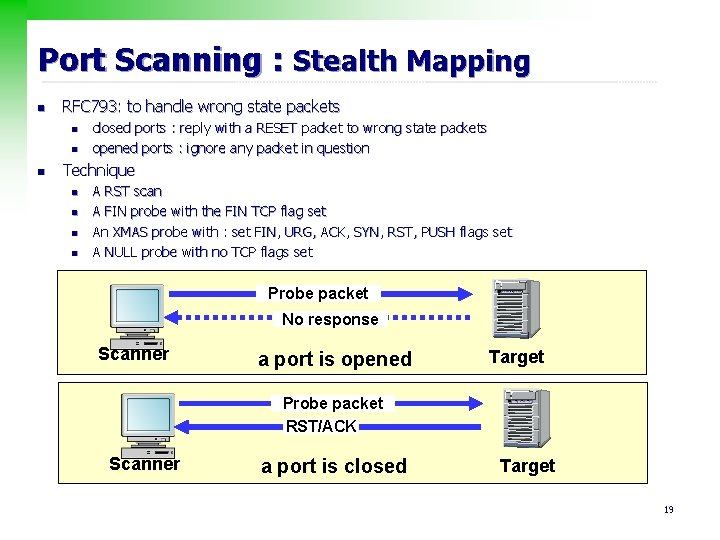
Port Scanning : Stealth Mapping n RFC 793: to handle wrong state packets n n n closed ports : reply with a RESET packet to wrong state packets opened ports : ignore any packet in question Technique n n A RST scan A FIN probe with the FIN TCP flag set An XMAS probe with : set FIN, URG, ACK, SYN, RST, PUSH flags set A NULL probe with no TCP flags set Probe packet No response Scanner a port is opened Target Probe packet RST/ACK Scanner a port is closed Target 19

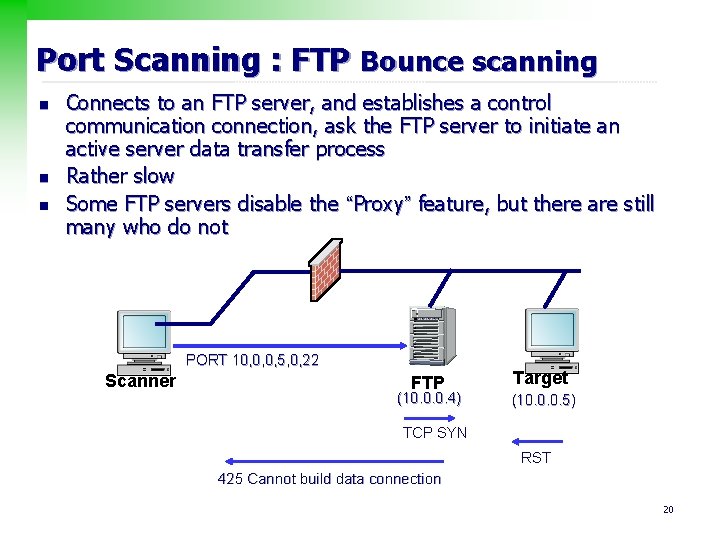
Port Scanning : FTP Bounce scanning n n n Connects to an FTP server, and establishes a control communication connection, ask the FTP server to initiate an active server data transfer process Rather slow Some FTP servers disable the “Proxy” feature, but there are still many who do not Scanner PORT 10, 0, 0, 5, 0, 22 FTP (10. 0. 0. 4) Target (10. 0. 0. 5) TCP SYN RST 425 Cannot build data connection 20

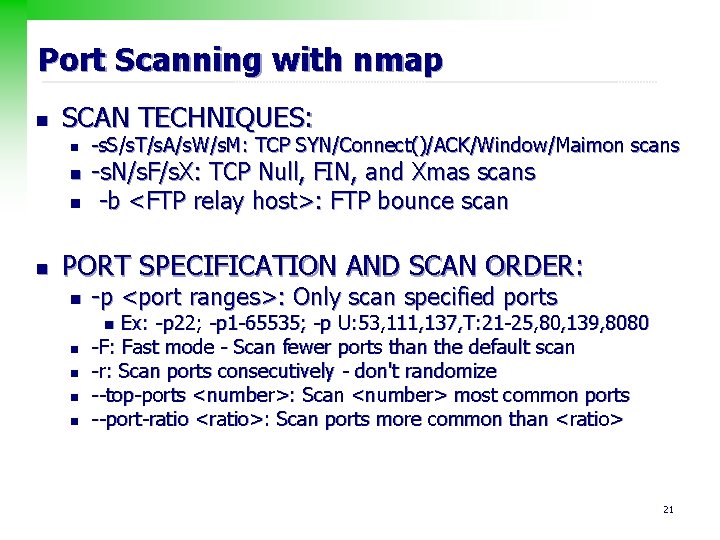
Port Scanning with nmap n SCAN TECHNIQUES: n n -s. S/s. T/s. A/s. W/s. M: TCP SYN/Connect()/ACK/Window/Maimon scans -s. N/s. F/s. X: TCP Null, FIN, and Xmas scans -b <FTP relay host>: FTP bounce scan PORT SPECIFICATION AND SCAN ORDER: n -p <port ranges>: Only scan specified ports Ex: -p 22; -p 1 -65535; -p U: 53, 111, 137, T: 21 -25, 80, 139, 8080 -F: Fast mode - Scan fewer ports than the default scan -r: Scan ports consecutively - don't randomize --top-ports <number>: Scan <number> most common ports --port-ratio <ratio>: Scan ports more common than <ratio> n n n 21

Services and Versions Detection n The nmap-service-probes database contains probes for querying various services and match expressions to recognize and parse responses 22

Operating System Detection n n Banner, DNS HINFO and … TCP/IP fingerprinting (IP stack implementation will response differently) n n FIN probe, Bogus Flag probe TCP initial sequence number sampling, TCP initial window, ACK value ICMP error quenching, message quoting, ICMP echo integrity IP: DF, TOS, Fragmentation 23

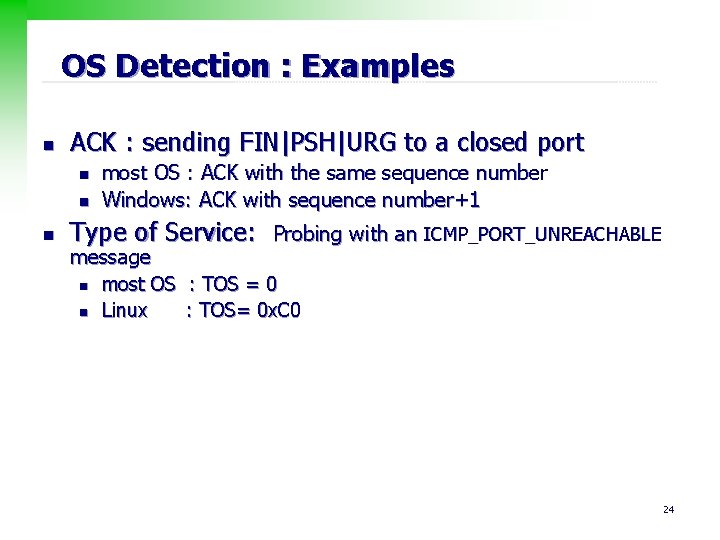
OS Detection : Examples n ACK : sending FIN|PSH|URG to a closed port n n n most OS : ACK with the same sequence number Windows: ACK with sequence number+1 Type of Service: Probing with an ICMP_PORT_UNREACHABLE message n most OS : TOS = 0 n Linux : TOS= 0 x. C 0 24

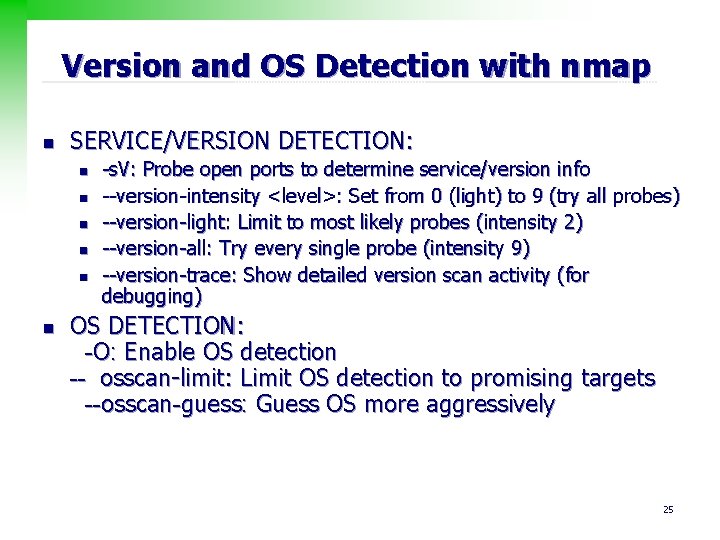
Version and OS Detection with nmap n SERVICE/VERSION DETECTION: n n n -s. V: Probe open ports to determine service/version info --version-intensity <level>: Set from 0 (light) to 9 (try all probes) --version-light: Limit to most likely probes (intensity 2) --version-all: Try every single probe (intensity 9) --version-trace: Show detailed version scan activity (for debugging) OS DETECTION: -O: Enable OS detection -- osscan-limit: Limit OS detection to promising targets --osscan-guess: Guess OS more aggressively 25

Port Scanning Detection n For Administrators to detect scanning n n n Logs suspicious packets Identifies connections not properly terminated Records ports usage 26

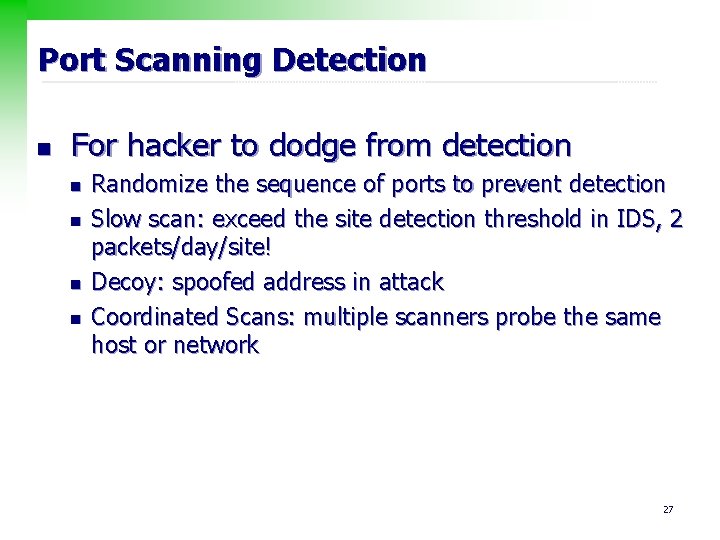
Port Scanning Detection n For hacker to dodge from detection n n Randomize the sequence of ports to prevent detection Slow scan: exceed the site detection threshold in IDS, 2 packets/day/site! Decoy: spoofed address in attack Coordinated Scans: multiple scanners probe the same host or network 27