Payments technology and security Mercury Confidential and Proprietary










- Slides: 24

Payments technology and security Mercury Confidential and Proprietary - For Recipient's Internal Use Only

Agenda • • • Introduction End-to-end encryption (E 2 E) Tokenization E 2 E + Tokenization EMV Summary Mercury Confidential and Proprietary - For Recipient's Internal Use Only

Introduction • This is an exciting time for the payments industry. There is a steady stream of disruptive technologies and security conformance being injected into the industry. From End-to-end encryption to EMV. • Today, we will discuss end-to-end encyption, tokenization and EMV technologies and how they impact the small to medium sized merchants. Mercury Confidential and Proprietary - For Recipient's Internal Use Only

End-to-end Encryption

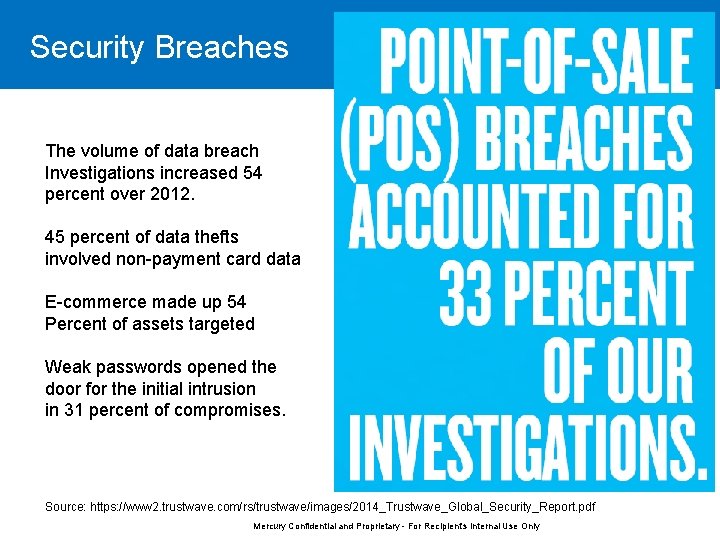
Security Breaches The volume of data breach Investigations increased 54 percent over 2012. 45 percent of data thefts involved non-payment card data E-commerce made up 54 Percent of assets targeted Weak passwords opened the door for the initial intrusion in 31 percent of compromises. Source: https: //www 2. trustwave. com/rs/trustwave/images/2014_Trustwave_Global_Security_Report. pdf Mercury Confidential and Proprietary - For Recipient's Internal Use Only

Security Breaches Every year that we produce the Trustwave Global Security Report, retail, food and beverage and hospitality jostle for position as the most frequently compromised industries. Retail once again led the pack in 2013 at 35 percent, a decrease of 10 percent over 2012. Food and beverage industry breaches counted for 18 percent of the total, 35% a five percent decrease from 2012. Source: https: //www 2. trustwave. com/rs/trustwave/images/2014_Trustwave_Global_Security_Report. pdf Mercury Confidential and Proprietary - For Recipient's Internal Use Only

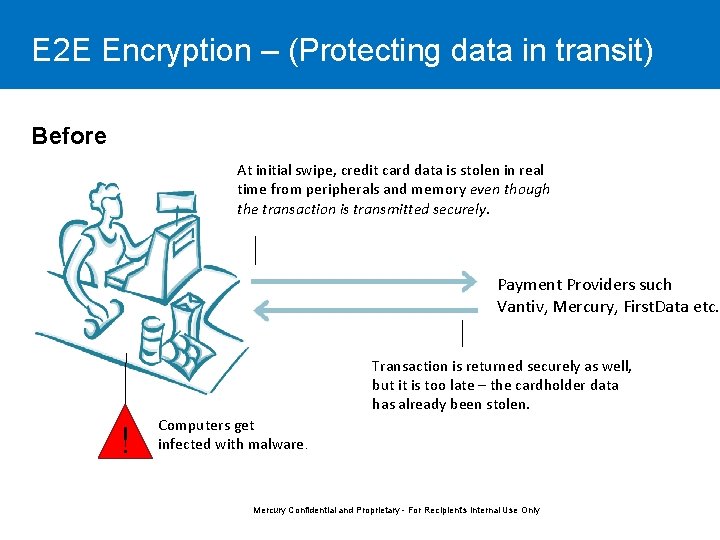
E 2 E Encryption – (Protecting data in transit) Before At initial swipe, credit card data is stolen in real time from peripherals and memory even though the transaction is transmitted securely. Payment Providers such Vantiv, Mercury, First. Data etc. Transaction is returned securely as well, but it is too late – the cardholder data has already been stolen. ! Computers get infected with malware. Mercury Confidential and Proprietary - For Recipient's Internal Use Only

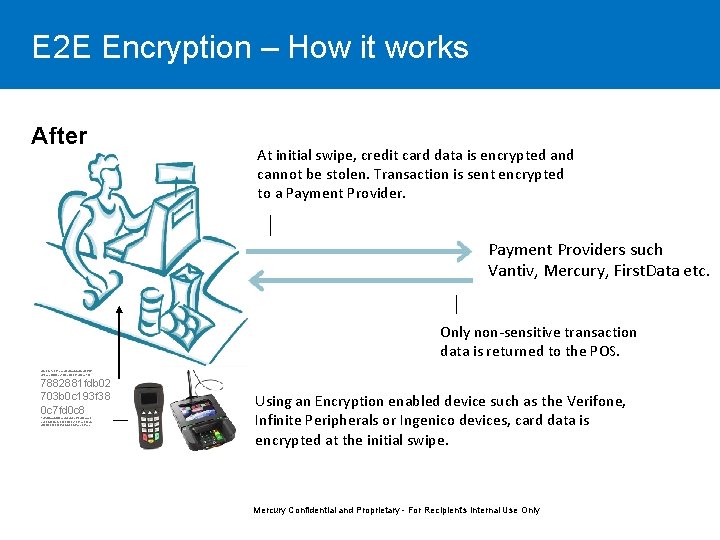
E 2 E Encryption – How it works After At initial swipe, credit card data is encrypted and cannot be stolen. Transaction is sent encrypted to a Payment Providers such Vantiv, Mercury, First. Data etc. Only non-sensitive transaction data is returned to the POS. d 5 e 35 c 1 e 081 cec 7 f 5 dbaddad 3 e 4 f 5628 c 65 c 7 e 8 df 63 ec 1 fb 275 f 3231490 c 716 e 7882881 fdb 02 703 b 0 c 193 f 38 0 c 7 fd 0 c 8 1784 bfac 4 d 5 f 0 a 74 e 3 d 457 f 12 d 82 ac 7 f ea 3 b 9 d 29 feb 72299 fbbb 710 b 1 ce 0674 e dbbf 952022528 abfd 72 bfa 8 e 7 cf 08777 Using an Encryption enabled device such as the Verifone, Infinite Peripherals or Ingenico devices, card data is encrypted at the initial swipe. Mercury Confidential and Proprietary - For Recipient's Internal Use Only

E 2 E enabled device examples Mercury Confidential and Proprietary - For Recipient's Internal Use Only

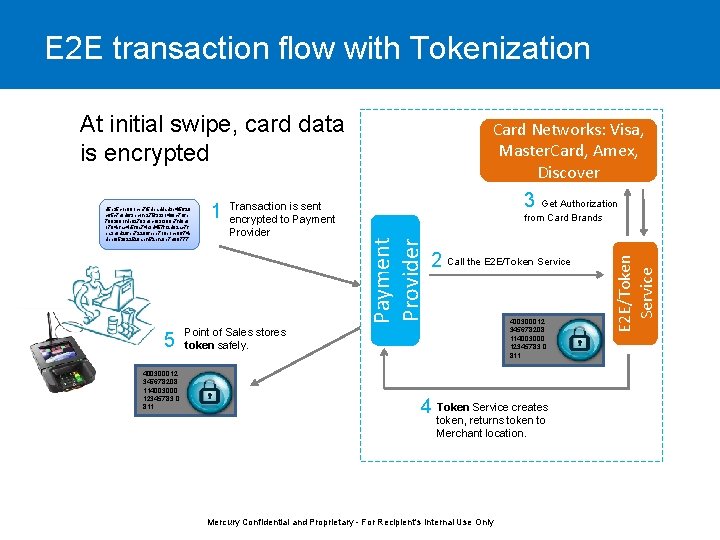
E 2 E transaction flow with Tokenization At initial swipe, card data is encrypted 400300012 345678208 114003000 12345783, 0 811 Transaction is sent encrypted to Payment Provider 3 Get Authorization from Card Brands 2 Call the E 2 E/Token Service 400300012 345678208 114003000 12345783, 0 811 Point of Sales stores token safely. 4 Token Service creates token, returns token to Merchant location. Mercury Confidential and Proprietary - For Recipient's Internal Use Only E 2 E/Token Service 5 1 Payment Provider d 5 e 35 c 1 e 081 cec 7 f 5 dbaddad 3 e 4 f 5628 c 65 c 7 e 8 df 63 ec 1 fb 275 f 3231490 c 716 e 7882881 fdb 02703 b 0 c 193 f 380 c 7 fd 0 c 8 1784 bfac 4 d 5 f 0 a 74 e 3 d 457 f 12 d 82 ac 7 f ea 3 b 9 d 29 feb 72299 fbbb 710 b 1 ce 0674 e dbbf 952022528 abfd 72 bfa 8 e 7 cf 08777 Card Networks: Visa, Master. Card, Amex, Discover

® Tokenization

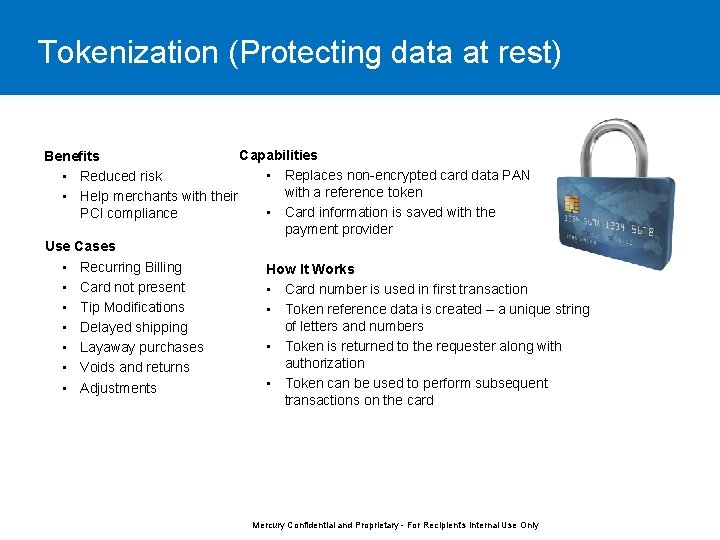
Tokenization (Protecting data at rest) Capabilities Benefits • Replaces non-encrypted card data PAN • Reduced risk with a reference token • Help merchants with their • Card information is saved with the PCI compliance payment provider Use Cases • Recurring Billing How It Works • Card not present • Card number is used in first transaction • Tip Modifications • Token reference data is created – a unique string of letters and numbers • Delayed shipping • Token is returned to the requester along with • Layaway purchases authorization • Voids and returns • Token can be used to perform subsequent • Adjustments transactions on the card Mercury Confidential and Proprietary - For Recipient's Internal Use Only

Tokenization – How it works The transaction response is sent back securely with a token. 40030001234567820811 4003000123456783, 0811 4003000123456784, 0811 4003000123456785, 0811 4003000123456786, 0811 4003000123456787, 0811 Payment Providers such Vantiv, Mercury, First. Data etc. Credit card is initially swiped or keyed, then transmitted securely. ! Computers can still get infected with malware. Mercury Confidential and Proprietary - For Recipient's Internal Use Only

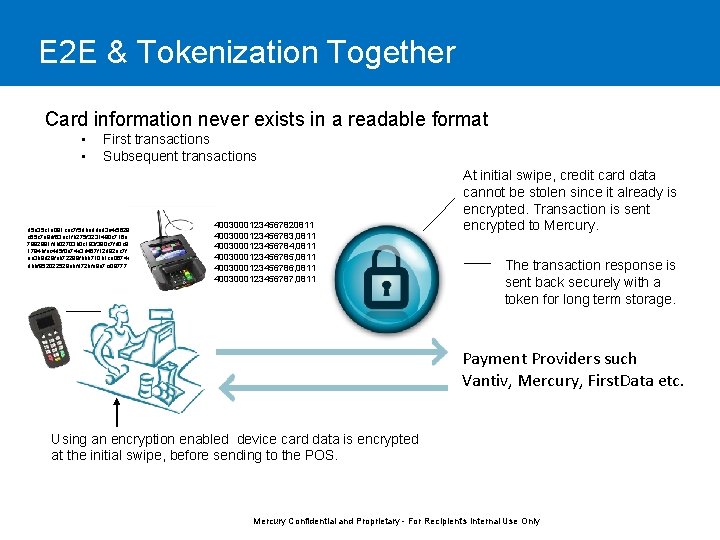
E 2 E & Tokenization Together Card information never exists in a readable format • • First transactions Subsequent transactions d 5 e 35 c 1 e 081 cec 7 f 5 dbaddad 3 e 4 f 5628 c 65 c 7 e 8 df 63 ec 1 fb 275 f 3231490 c 716 e 7882881 fdb 02703 b 0 c 193 f 380 c 7 fd 0 c 8 1784 bfac 4 d 5 f 0 a 74 e 3 d 457 f 12 d 82 ac 7 f ea 3 b 9 d 29 feb 72299 fbbb 710 b 1 ce 0674 e dbbf 952022528 abfd 72 bfa 8 e 7 cf 08777 40030001234567820811 4003000123456783, 0811 4003000123456784, 0811 4003000123456785, 0811 4003000123456786, 0811 4003000123456787, 0811 At initial swipe, credit card data cannot be stolen since it already is encrypted. Transaction is sent encrypted to Mercury. The transaction response is sent back securely with a token for long term storage. Payment Providers such Vantiv, Mercury, First. Data etc. Using an encryption enabled device card data is encrypted at the initial swipe, before sending to the POS. Mercury Confidential and Proprietary - For Recipient's Internal Use Only

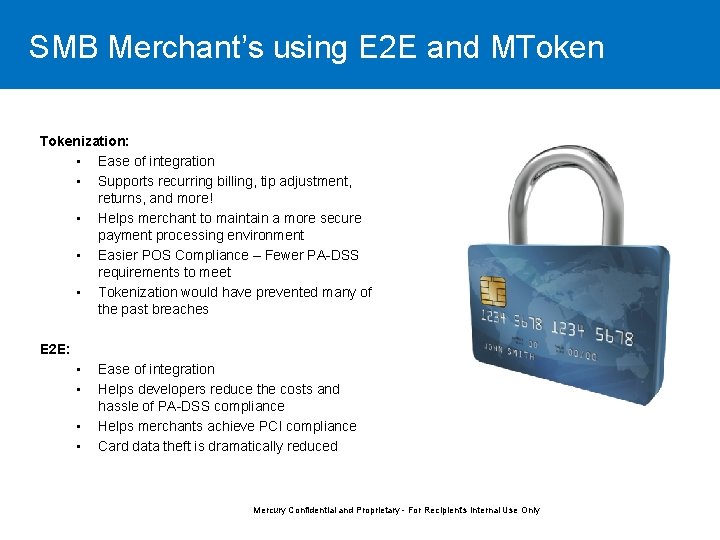
SMB Merchant’s using E 2 E and MTokenization: • Ease of integration • Supports recurring billing, tip adjustment, returns, and more! • Helps merchant to maintain a more secure payment processing environment • Easier POS Compliance – Fewer PA-DSS requirements to meet • Tokenization would have prevented many of the past breaches E 2 E: • • Ease of integration Helps developers reduce the costs and hassle of PA-DSS compliance Helps merchants achieve PCI compliance Card data theft is dramatically reduced Mercury Confidential and Proprietary - For Recipient's Internal Use Only

EMV

What is EMV • EMV is a set of standards that defines interoperability of secure transactions across the international payments landscape. • EMV transactions introduce dynamic-data specific to the card and the transaction, with the goal of reducing the risk of counterfeit fraud. • The computer chip on the card uses cryptography to provide security. In the context of EMV, encryption is only used to protect the PIN. • EMV is a card present schema only. Does not solve for ecommerce transactions Mercury Confidential and Proprietary - For Recipient's Internal Use Only

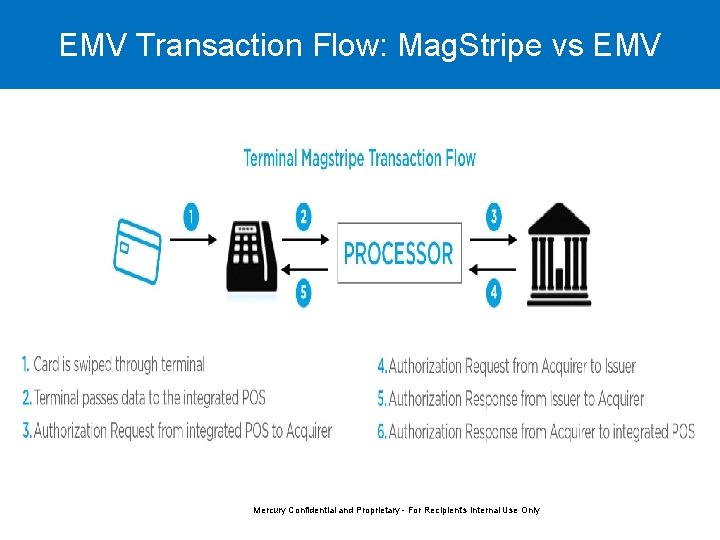
EMV Transaction Flow: Mag. Stripe vs EMV Mercury Confidential and Proprietary - For Recipient's Internal Use Only

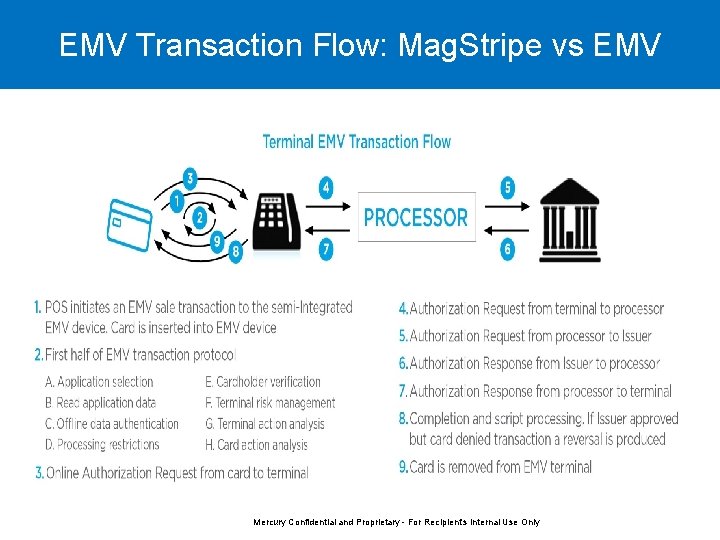
EMV Transaction Flow: Mag. Stripe vs EMV Mercury Confidential and Proprietary - For Recipient's Internal Use Only

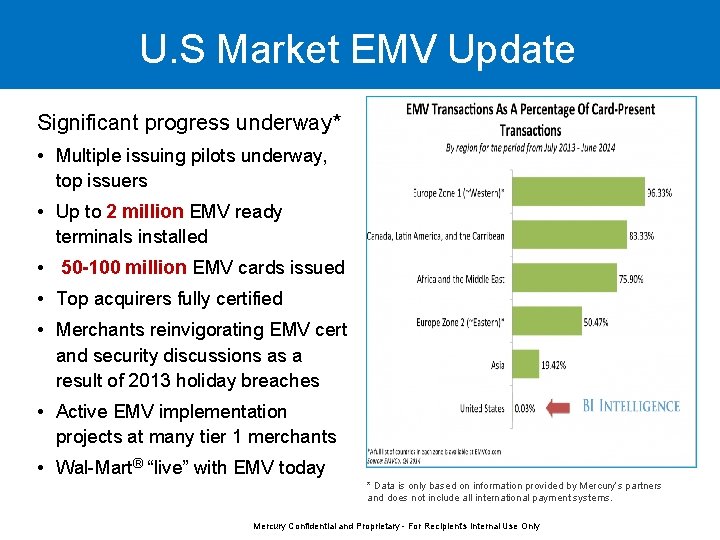
U. S Market EMV Update Significant progress underway* • Multiple issuing pilots underway, top issuers • Up to 2 million EMV ready terminals installed • 50 -100 million EMV cards issued • Top acquirers fully certified • Merchants reinvigorating EMV cert and security discussions as a result of 2013 holiday breaches • Active EMV implementation projects at many tier 1 merchants • Wal-Mart® “live” with EMV today * Data is only based on information provided by Mercury’s partners and does not include all international payment systems. Mercury Confidential and Proprietary - For Recipient's Internal Use Only

Certification Standards EMVCo™ • Level 1: Certification of the device’s electrical, mechanical, and communication protocol characteristics • Level 2: Certification of application software that supports specified EMV functionality Card Networks • Brand/“Level 3”: Approval of end-to-end solution • Brand-by-brand testing requirements Mercury Confidential and Proprietary - For Recipient's Internal Use Only

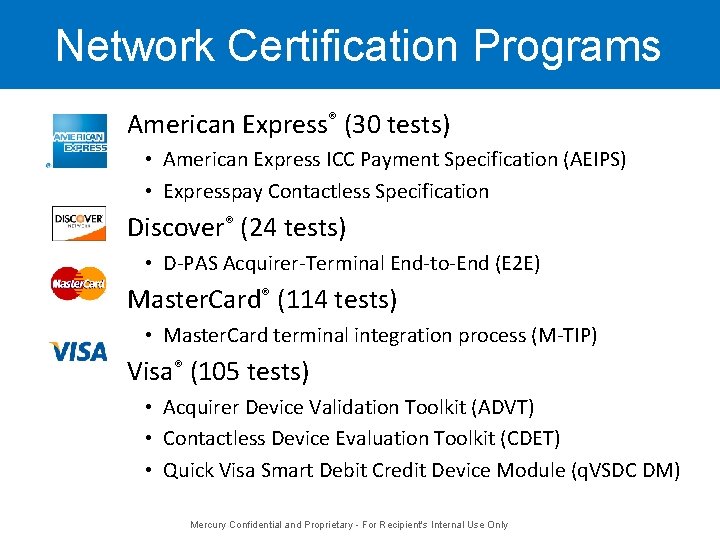
Network Certification Programs American Express® (30 tests) • American Express ICC Payment Specification (AEIPS) • Expresspay Contactless Specification Discover® (24 tests) • D-PAS Acquirer-Terminal End-to-End (E 2 E) Master. Card® (114 tests) • Master. Card terminal integration process (M-TIP) Visa® (105 tests) • Acquirer Device Validation Toolkit (ADVT) • Contactless Device Evaluation Toolkit (CDET) • Quick Visa Smart Debit Credit Device Module (q. VSDC DM) Mercury Confidential and Proprietary - For Recipient's Internal Use Only

Points of pain for Merchants Cardholders EMV card never leaves the cardholder’s hand Contact EMV – dipping Contactless EMV – tapping Chip and Signature vs Chip and Pin Restaurant environments Merchant and consumer payment process flow will change Varied merchant impacts by vertical: pizza delivery, fine dining, unattended kiosk(Car washes) Cost for new EMV enabled hardware/software Liability Shift: charge back Line-busting will change Cost vs. Customer impact 5 Mercury Confidential and Proprietary - For Recipient's Internal Use Only

Thank you!
 Proprietary and confidential do not distribute
Proprietary and confidential do not distribute Confidential & proprietary
Confidential & proprietary Performance based payment
Performance based payment Privat security
Privat security Disadvantages of open source software
Disadvantages of open source software Proprietary freeware
Proprietary freeware Proprietary grief
Proprietary grief Proprietary format
Proprietary format Define proprietary colony
Define proprietary colony Proprietary theory
Proprietary theory Wireless security in cryptography
Wireless security in cryptography Electronic commerce security
Electronic commerce security Special amount column definition
Special amount column definition Receipt and payment rules 1983
Receipt and payment rules 1983 Cycle based testing audit
Cycle based testing audit Audit of the capital acquisition and repayment cycle
Audit of the capital acquisition and repayment cycle Williams fudge inc
Williams fudge inc Televax
Televax Difference between mercury cell and diaphragm cell
Difference between mercury cell and diaphragm cell Mercury and apollo
Mercury and apollo Does mercury have more protons and electrons than tin
Does mercury have more protons and electrons than tin What is the osi security architecture
What is the osi security architecture Security guide to network security fundamentals
Security guide to network security fundamentals Explain about visa international security mode
Explain about visa international security mode Electronic mail security in network security
Electronic mail security in network security