NSX Introduzione e casi dUso Luca Morelli Sr









- Slides: 40

NSX – Introduzione e casi d’Uso Luca Morelli – Sr Sales Engineer - NSX lmorelli@vmware. com © 2014 VMware Inc. All rights reserved.

Agenda 1 Il Software Defined Data Center 2 Introduzione alla Virtualizzazione di Rete con NSX 3 Il Paradigma della Micro-Segmentazione 4 Principali Casi d’Uso 2

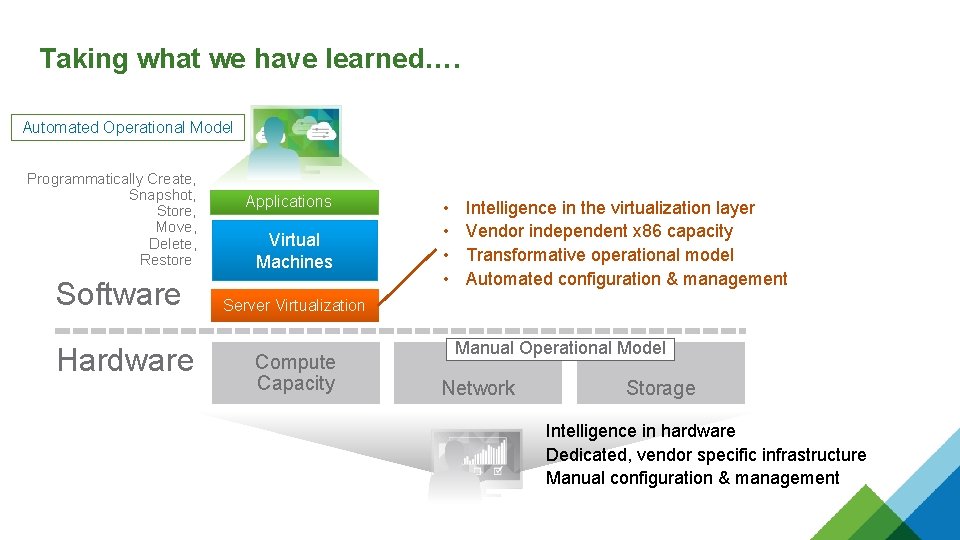
Taking what we have learned…. Automated Operational Model Programmatically Create, Snapshot, Store, Move, Delete, Restore Software Hardware Applications Virtual Machines • • Intelligence in the virtualization layer Vendor independent x 86 capacity Transformative operational model Automated configuration & management Server Virtualization Compute Capacity Manual Operational Model Network Storage Intelligence in hardware Dedicated, vendor specific infrastructure Manual configuration & management

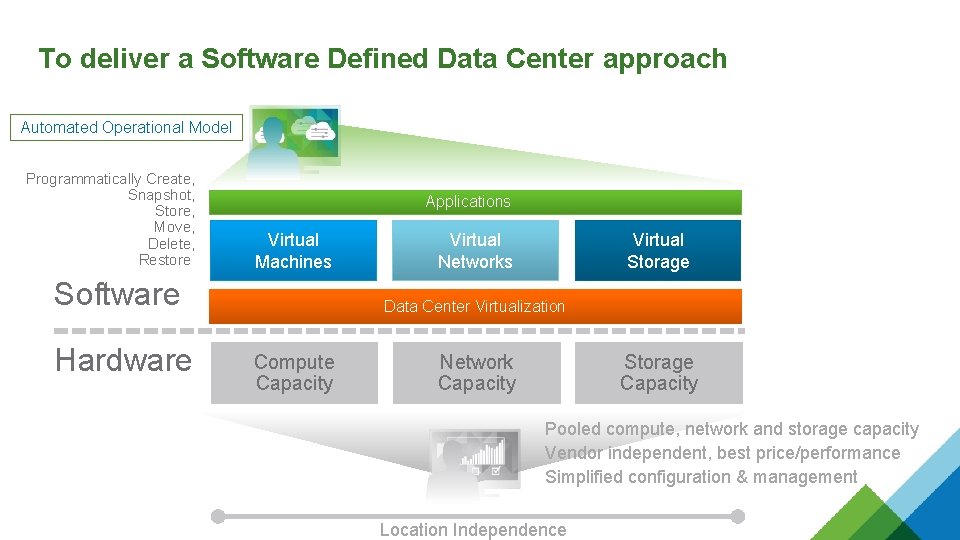
To deliver a Software Defined Data Center approach Automated Operational Model Programmatically Create, Snapshot, Store, Move, Delete, Restore Applications Virtual Machines Software Hardware Virtual Networks Virtual Storage Data Center Virtualization Compute Capacity Network Capacity Storage Capacity Pooled compute, network and storage capacity Vendor independent, best price/performance Simplified configuration & management Location Independence

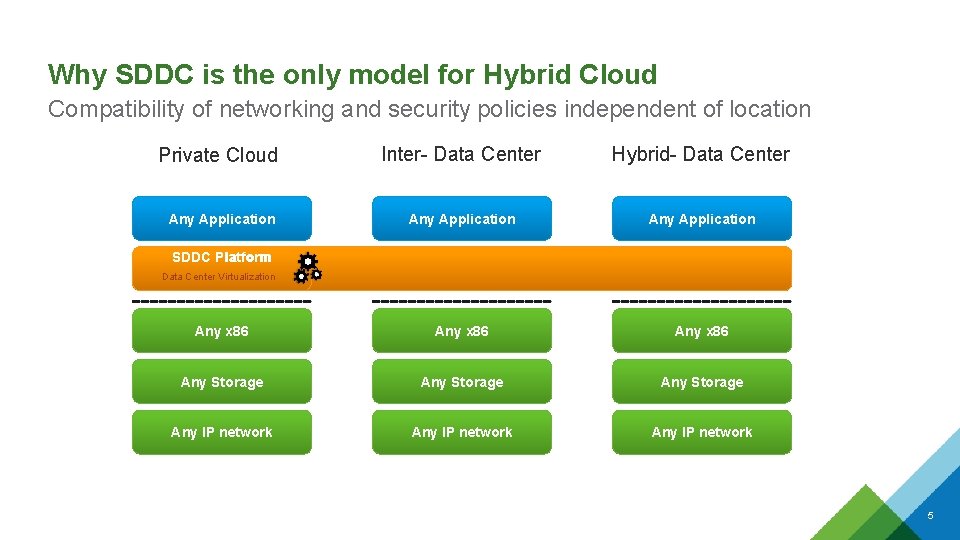
Why SDDC is the only model for Hybrid Cloud Compatibility of networking and security policies independent of location Private Cloud Inter- Data Center Hybrid- Data Center Any Application Any x 86 Any Storage Any IP network SDDC Platform Data Center Virtualization 5

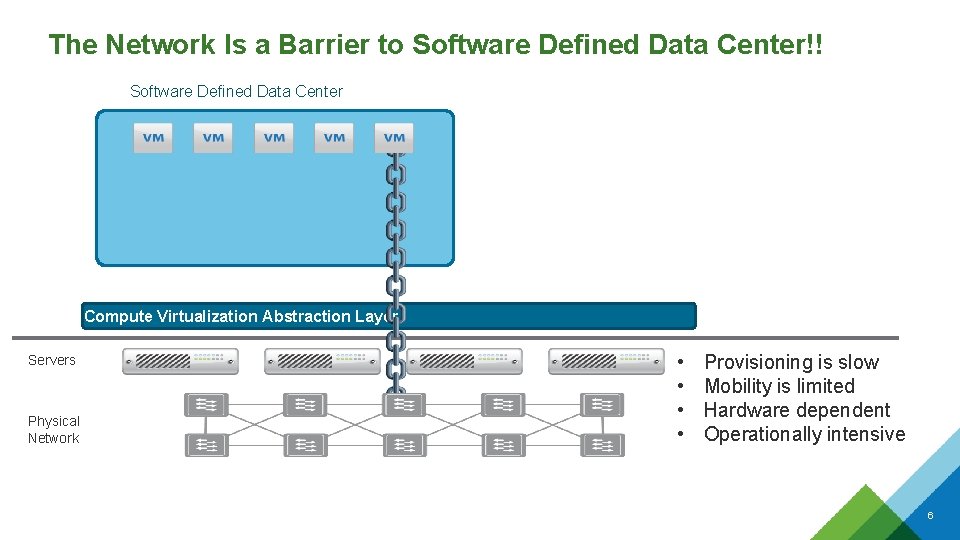
The Network Is a Barrier to Software Defined Data Center!! Software Defined Data Center Compute Virtualization Abstraction Layer Servers Physical Network • • Provisioning is slow Mobility is limited Hardware dependent Operationally intensive 6

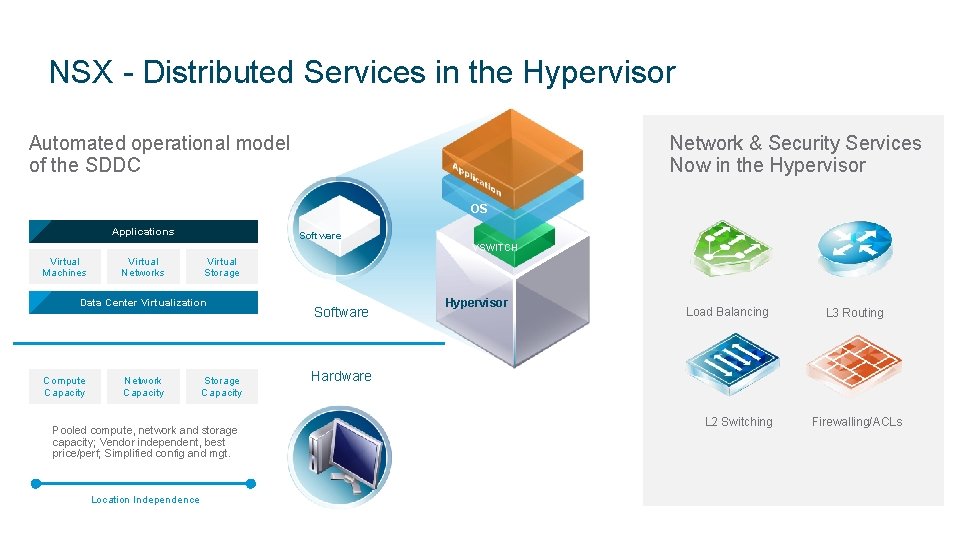
NSX - Distributed Services in the Hypervisor Automated operational model of the SDDC Network & Security Services Now in the Hypervisor OS Applications Software VSWITCH Virtual Machines Virtual Networks Virtual Storage Data Center Virtualization Compute Capacity Network Capacity Storage Capacity Pooled compute, network and storage capacity; Vendor independent, best price/perf; Simplified config and mgt. Location Independence Software Hypervisor Load Balancing L 3 Routing Hardware L 2 Switching Firewalling/ACLs

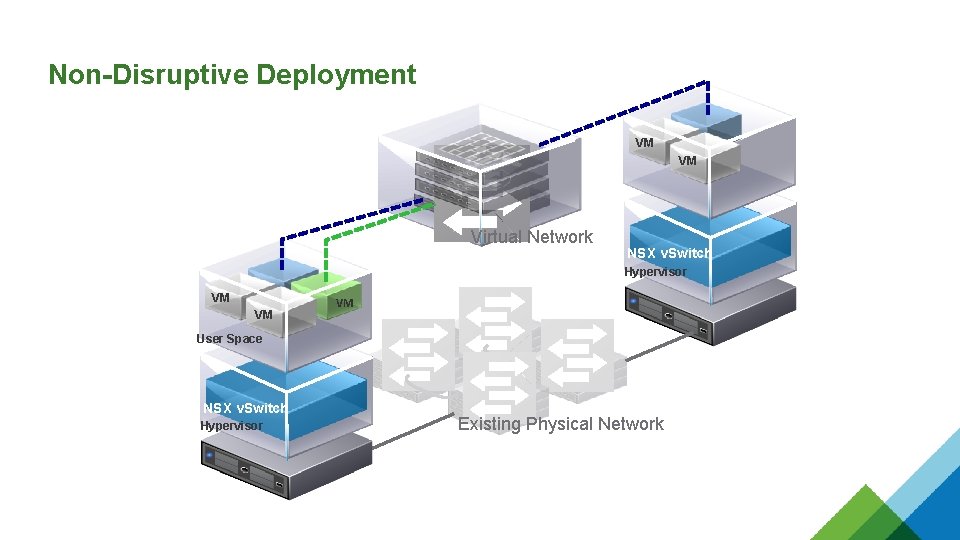
Non-Disruptive Deployment VM VM Virtual Network NSX v. Switch Hypervisor VM VM VM User Space NSX v. Switch Hypervisor Existing Physical Network

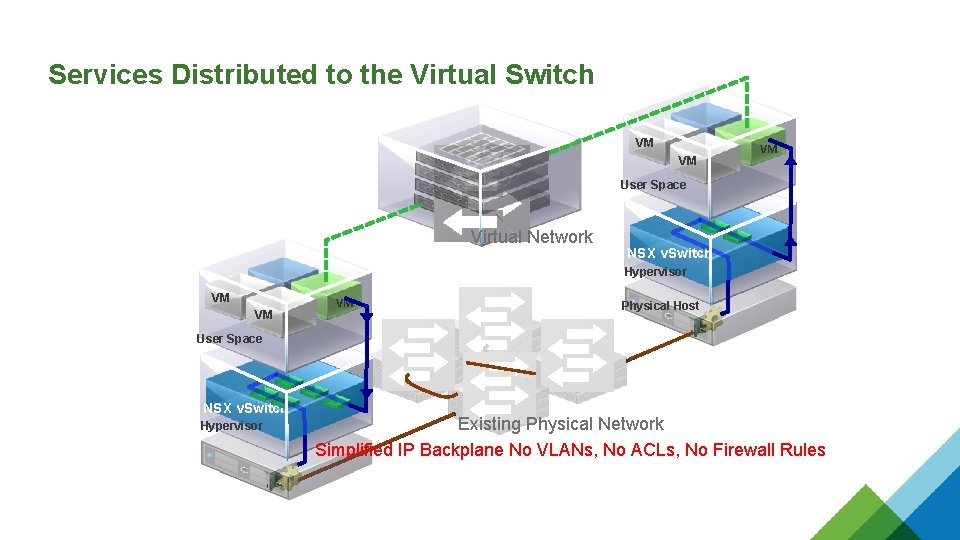
Services Distributed to the Virtual Switch VM VM VM User Space Virtual Network NSX v. Switch Hypervisor VM VM VM Physical Host User Space NSX v. Switch Hypervisor Existing Physical Network Simplified IP Backplane No VLANs, No ACLs, No Firewall Rules

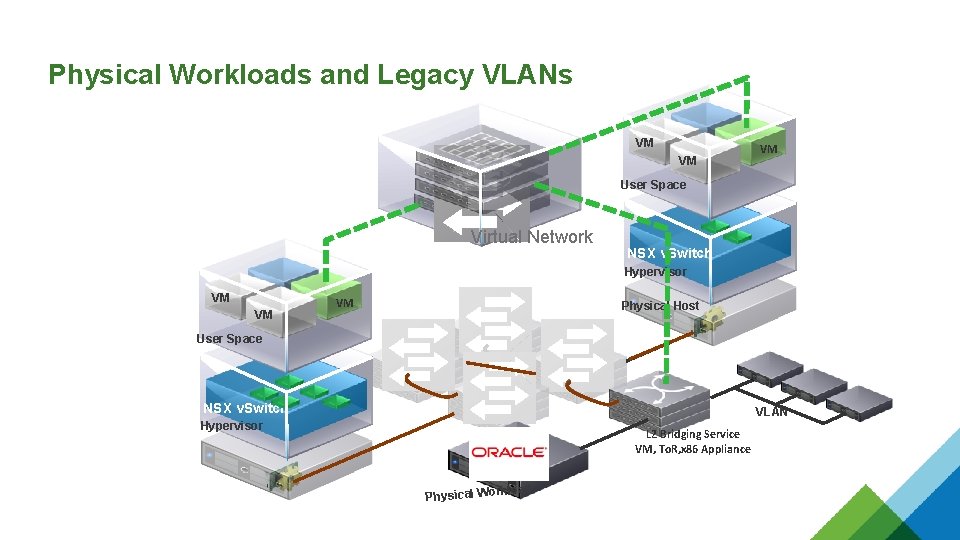
Physical Workloads and Legacy VLANs VM VM VM User Space Virtual Network NSX v. Switch Hypervisor VM VM VM Physical Host User Space NSX v. Switch VLAN Hypervisor L 2 Bridging Service VM, To. R, x 86 Appliance load Physical Work

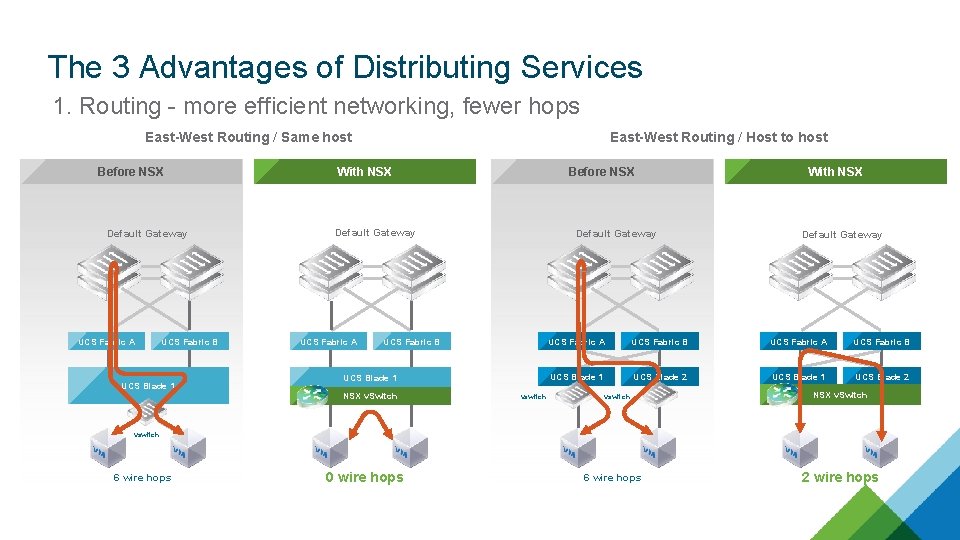
The 3 Advantages of Distributing Services 1. Routing - more efficient networking, fewer hops East-West Routing / Same host Before NSX Default Gateway UCS Fabric A UCS Fabric B UCS Blade 1 East-West Routing / Host to host With NSX Before NSX Default Gateway UCS Fabric A Default Gateway UCS Fabric B UCS Blade 1 NSX v. Switch vswitch With NSX Default Gateway UCS Fabric A UCS Fabric B UCS Blade 1 UCS Blade 2 vswitch NSX v. Switch vswitch 6 wire hops 0 wire hops 6 wire hops 2 wire hops

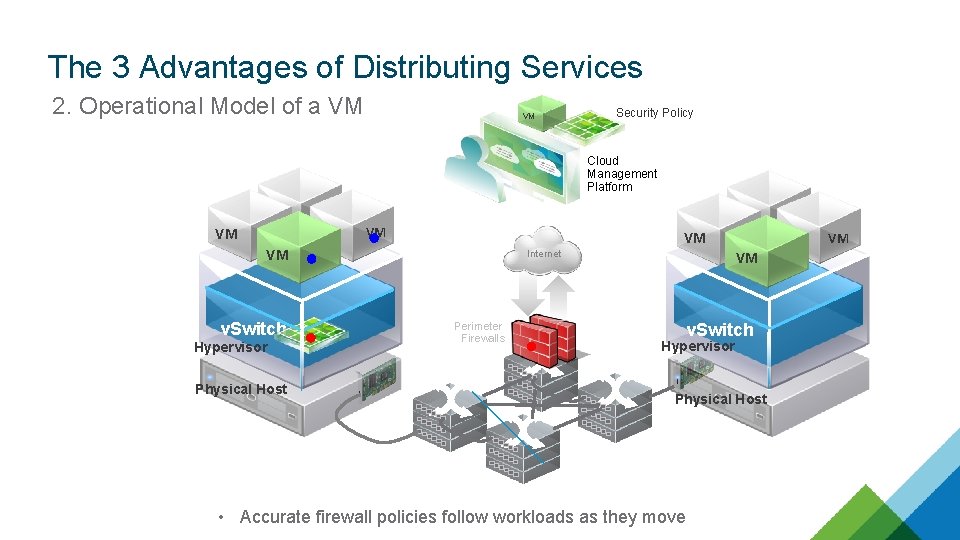
The 3 Advantages of Distributing Services 2. Operational Model of a VM VM Security Policy Cloud Management Platform VM VM VM v. Switch Hypervisor Physical Host VM VM Internet Perimeter Firewalls VM v. Switch Hypervisor Physical Host • Accurate firewall policies follow workloads as they move

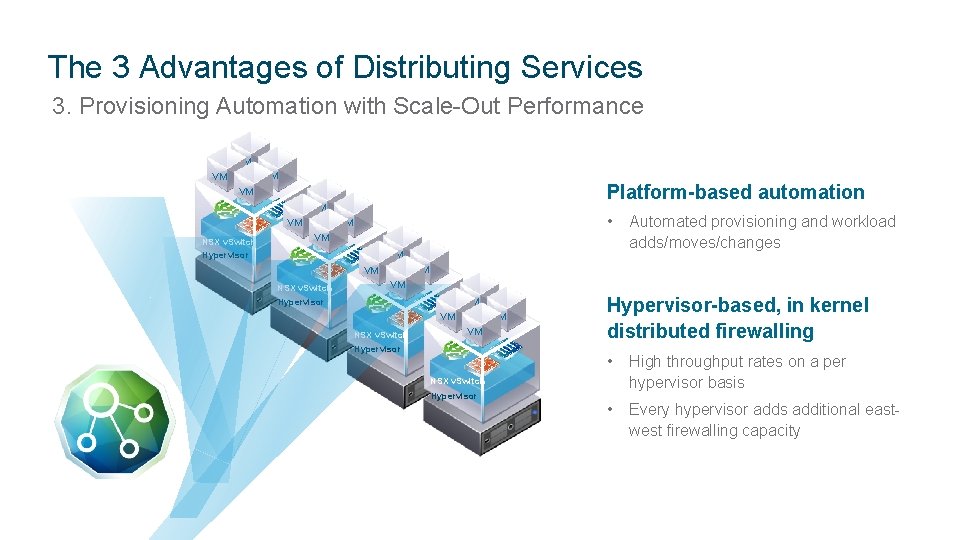
The 3 Advantages of Distributing Services 3. Provisioning Automation with Scale-Out Performance VM VM VM Platform-based automation VM VM NSX v. Switch • VM VM Hypervisor VM VM NSX v. Switch Automated provisioning and workload adds/moves/changes VM VM Hypervisor VM VM NSX v. Switch VM Hypervisor-based, in kernel distributed firewalling • High throughput rates on a per hypervisor basis • Every hypervisor adds additional eastwest firewalling capacity NSX v. Switch Hypervisor CONFIDENTIAL 13

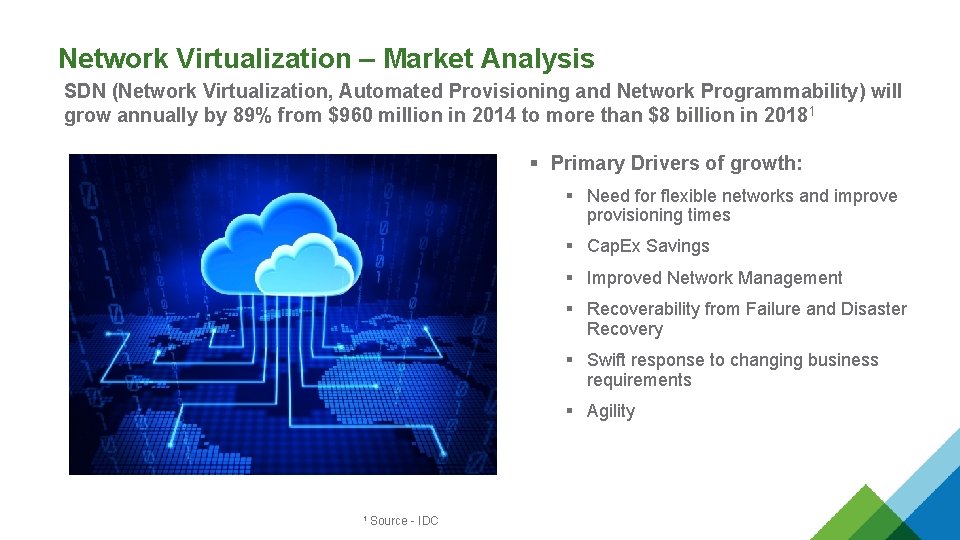
Network Virtualization – Market Analysis SDN (Network Virtualization, Automated Provisioning and Network Programmability) will grow annually by 89% from $960 million in 2014 to more than $8 billion in 20181 § Primary Drivers of growth: § Need for flexible networks and improve provisioning times § Cap. Ex Savings § Improved Network Management § Recoverability from Failure and Disaster Recovery § Swift response to changing business requirements § Agility 1 Source - IDC

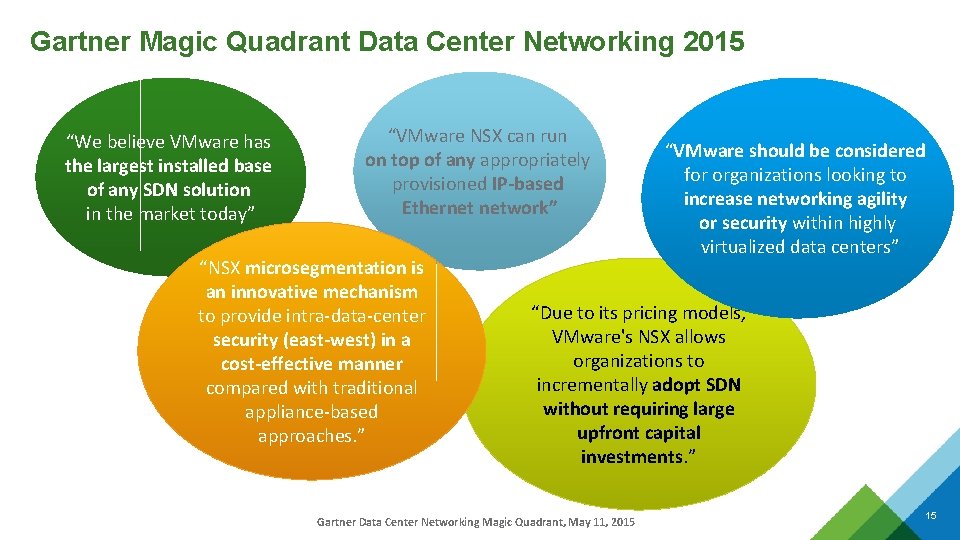
Gartner Magic Quadrant Data Center Networking 2015 “We believe VMware has the largest installed base of any SDN solution in the market today” “VMware NSX can run on top of any appropriately provisioned IP-based Ethernet network” “NSX microsegmentation is an innovative mechanism to provide intra-data-center security (east-west) in a cost-effective manner compared with traditional appliance-based approaches. ” “VMware should be considered for organizations looking to increase networking agility or security within highly virtualized data centers” “Due to its pricing models, VMware's NSX allows organizations to incrementally adopt SDN without requiring large upfront capital investments. ” Gartner Data Center Networking Magic Quadrant, May 11, 2015 15

Organizations face multiple issues with security Source NSX Security Infographic: http: //vmw. re/1 Ady. TEA 16

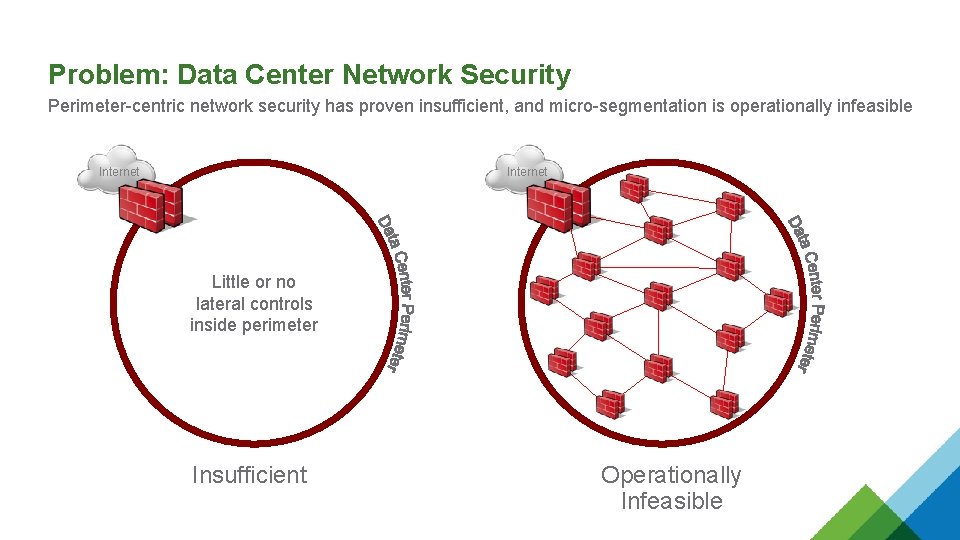
Problem: Data Center Network Security Perimeter-centric network security has proven insufficient, and micro-segmentation is operationally infeasible Internet Little or no lateral controls inside perimeter Insufficient Operationally Infeasible

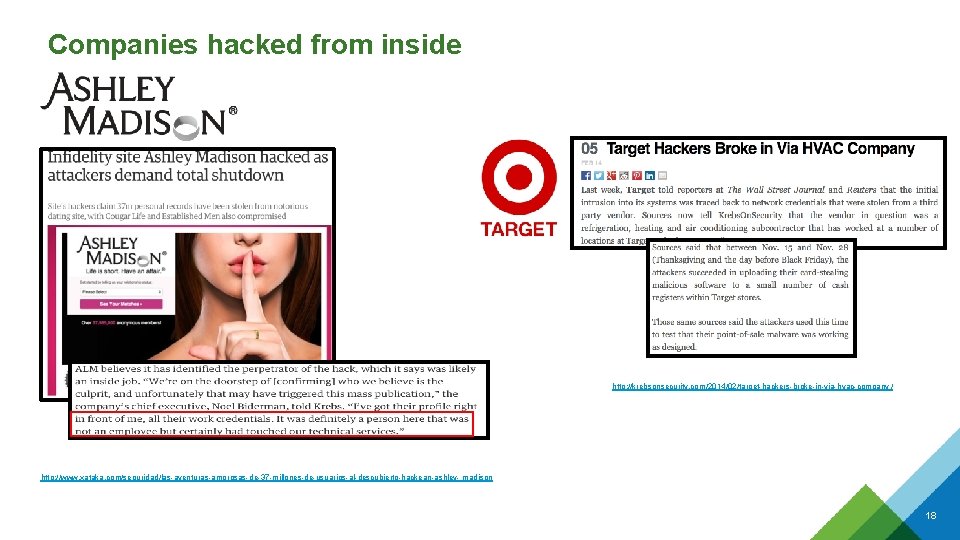
Companies hacked from inside http: //krebsonsecurity. com/2014/02/target-hackers-broke-in-via-hvac-company / http: //www. xataka. com/seguridad/las-aventuras-amorosas-de-37 -millones-de-usuarios-al-descubierto-hackean-ashley- madison 18

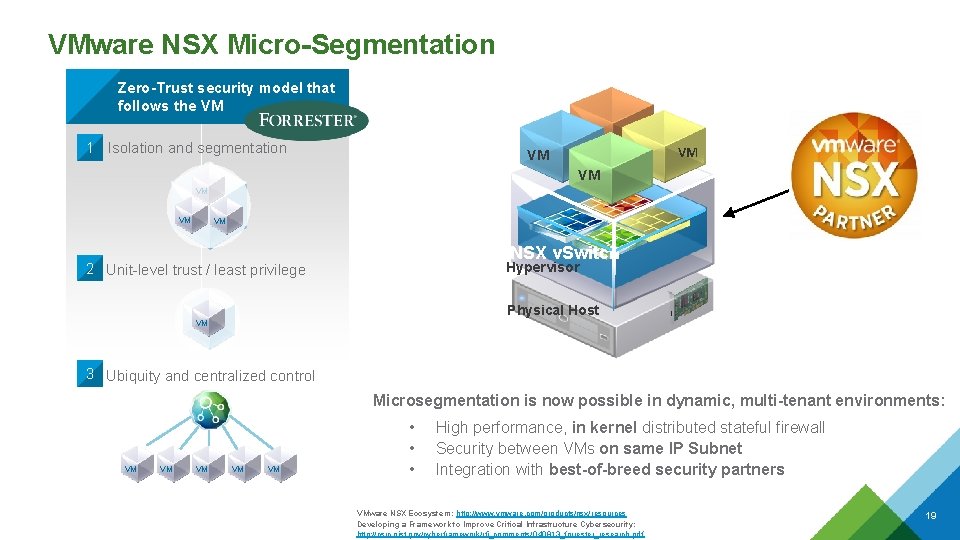
VMware NSX Micro-Segmentation Zero-Trust security model that follows the VM 1 Isolation and segmentation VM VM VM NSX v. Switch Hypervisor 2 Unit-level trust / least privilege Physical Host VM 3 Ubiquity and centralized control Microsegmentation is now possible in dynamic, multi-tenant environments: VM VM VM • • • High performance, in kernel distributed stateful firewall Security between VMs on same IP Subnet Integration with best-of-breed security partners VMware NSX Ecosystem: http: //www. vmware. com/products/nsx/resources Developing a Framework to Improve Critical Infrastructure Cybersecurity: http: //csrc. nist. gov/cyberframework/rfi_comments/ 040813_forrester_research. pdf 19

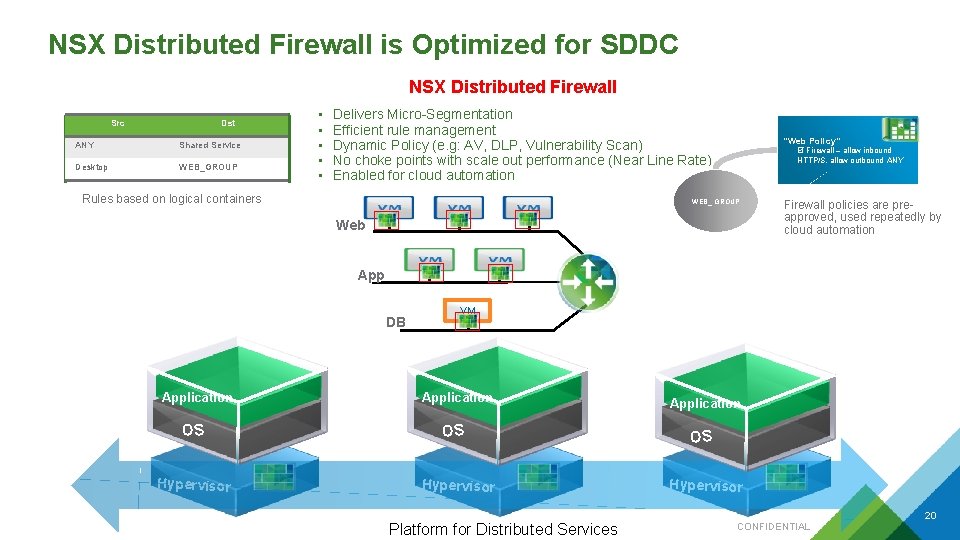
NSX Distributed Firewall is Optimized for SDDC NSX Distributed Firewall Src Dst ANY Shared Service Desktop WEB_GROUP • • • Delivers Micro-Segmentation Efficient rule management Dynamic Policy (e. g: AV, DLP, Vulnerability Scan) No choke points with scale out performance (Near Line Rate) Enabled for cloud automation Rules based on logical containers “Web Policy” Firewall – allow inbound HTTP/S, allow outbound ANY WEB_ GROUP Web Firewall policies are preapproved, used repeatedly by cloud automation App DB VM Application OS OS OS Hypervisor Platform for Distributed Services Hypervisor 20 CONFIDENTIAL

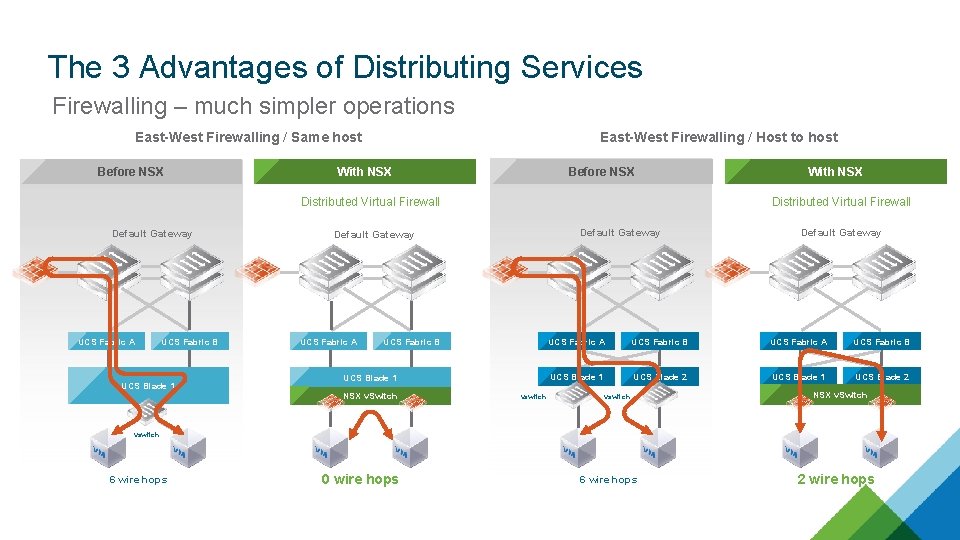
The 3 Advantages of Distributing Services Firewalling – much simpler operations East-West Firewalling / Same host Before NSX East-West Firewalling / Host to host With NSX Before NSX Distributed Virtual Firewall Default Gateway UCS Fabric A UCS Fabric B UCS Blade 1 NSX v. Switch With NSX vswitch Default Gateway UCS Fabric A UCS Fabric B UCS Blade 1 UCS Blade 2 vswitch NSX v. Switch vswitch 6 wire hops 0 wire hops 6 wire hops 2 wire hops

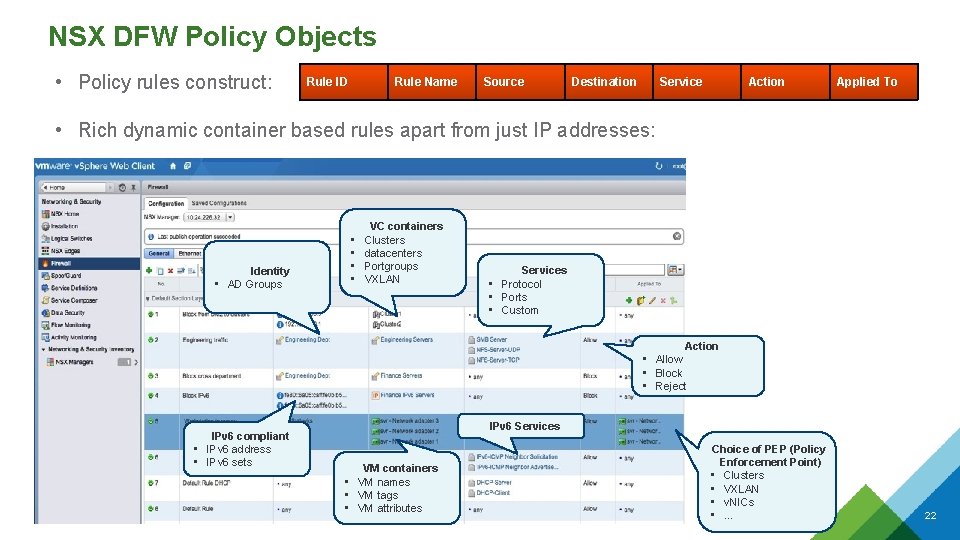
NSX DFW Policy Objects • Policy rules construct: Rule ID Rule Name Source Destination Service Action Applied To • Rich dynamic container based rules apart from just IP addresses: Identity • AD Groups • • VC containers Clusters datacenters Portgroups VXLAN Services • Protocol • Ports • Custom Action • Allow • Block • Reject IPv 6 compliant • IPv 6 address • IPv 6 sets IPv 6 Services VM containers • VM names • VM tags • VM attributes Choice of PEP (Policy Enforcement Point) • Clusters • VXLAN • v. NICs • CONFIDENTIAL … 22

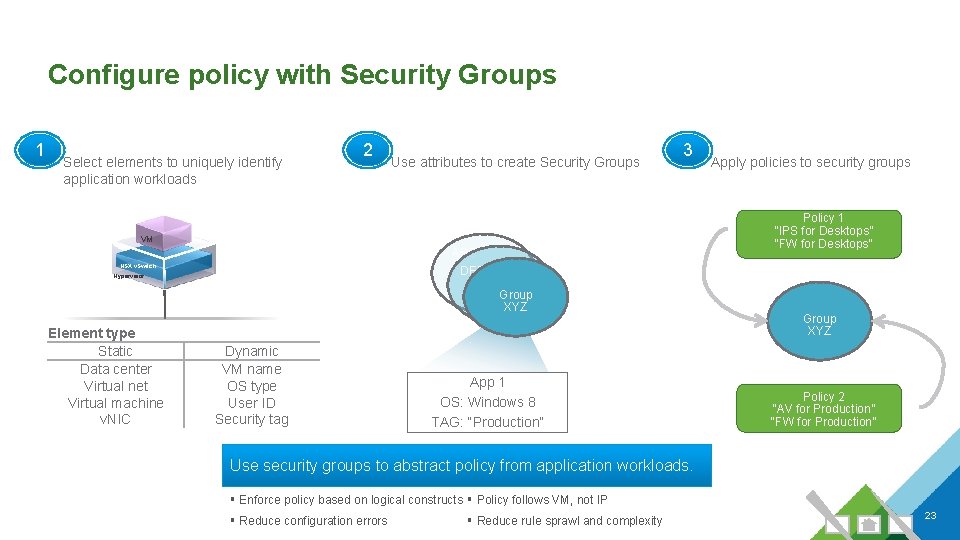
Configure policy with Security Groups 1 Select elements to uniquely identify application workloads 2 Use attributes to create Security Groups 3 Policy 1 “IPS for Desktops” “FW for Desktops” VM ABC DEF NSX v. Switch Hypervisor Group XYZ Element type Static Data center Virtual net Virtual machine v. NIC Dynamic VM name OS type User ID Security tag Apply policies to security groups App 1 OS: Windows 8 TAG: “Production” Group XYZ Policy 2 “AV for Production” “FW for Production” Use security groups to abstract policy from application workloads. § Enforce policy based on logical constructs § Policy follows VM, not IP § Reduce configuration errors § Reduce rule sprawl and complexity 23

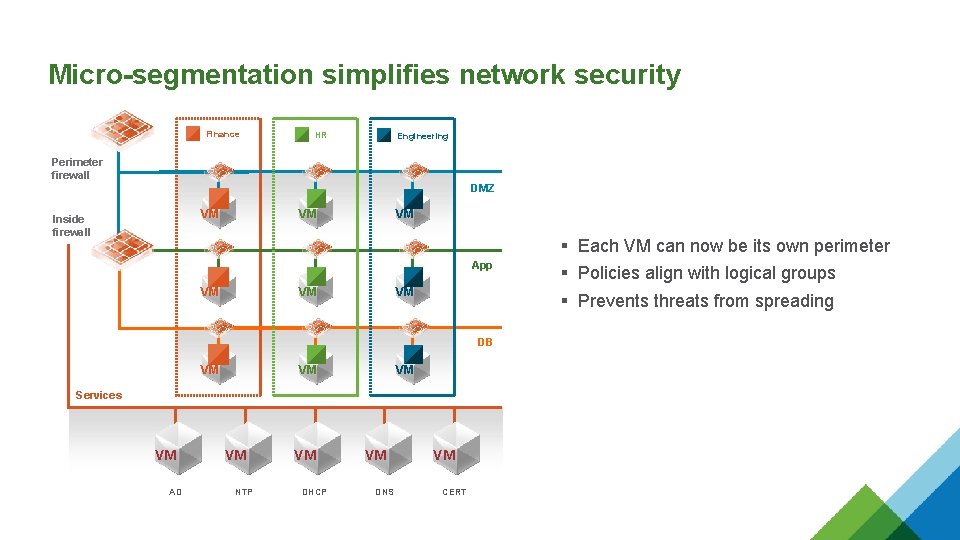
Micro-segmentation simplifies network security Finance HR Engineering Perimeter firewall DMZ VM Inside firewall VM VM App VM VM VM DB VM VM VM Services VM AD VM NTP VM DHCP VM DNS VM CERT § Each VM can now be its own perimeter § Policies align with logical groups § Prevents threats from spreading

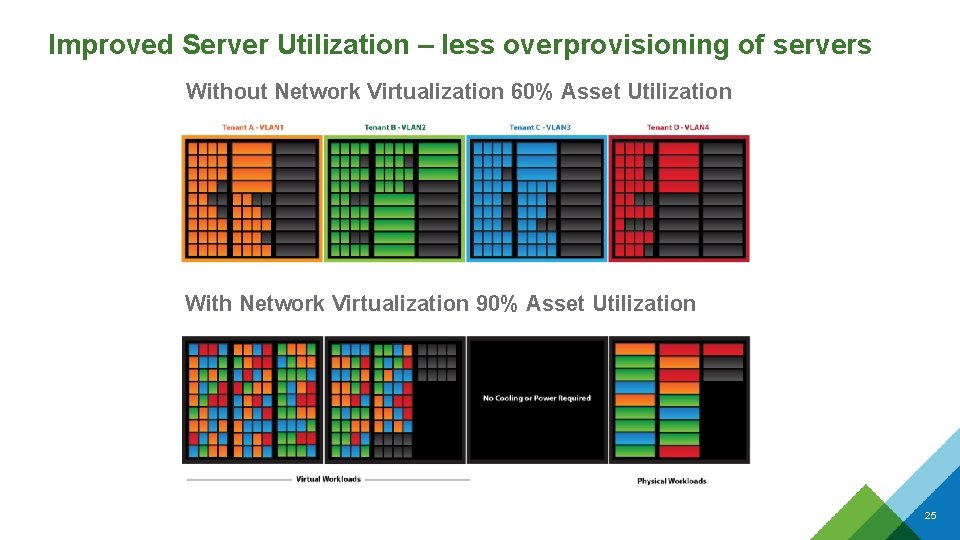
Improved Server Utilization – less overprovisioning of servers Without Network Virtualization 60% Asset Utilization With Network Virtualization 90% Asset Utilization 25

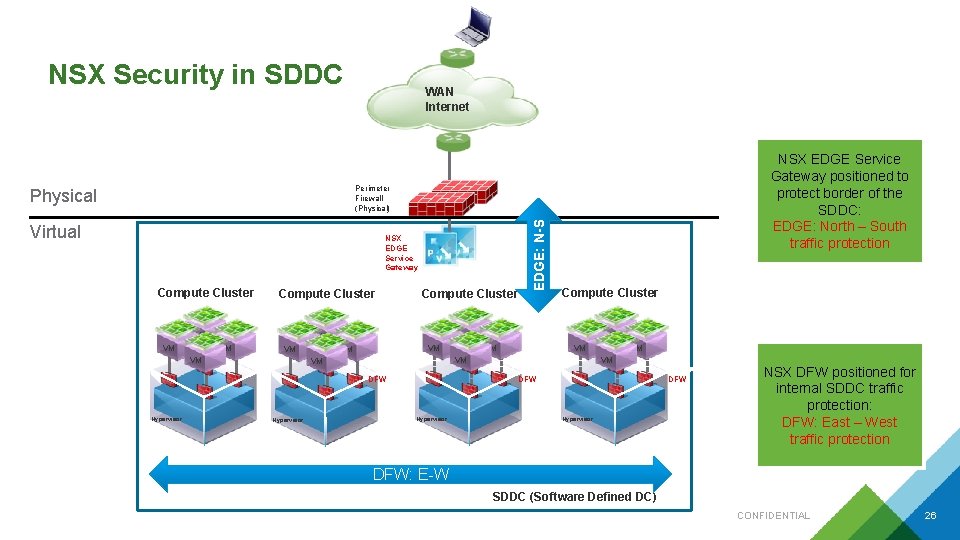
NSX Security in SDDC WAN Internet NSX EDGE Service Gateway positioned to protect border of the SDDC: EDGE: North – South traffic protection Virtual NSX EDGE Service Gateway Compute Cluster VM VM Hypervisor VM VM VM DFW Hypervisor Compute Cluster VM VM VM EDGE: N-S Perimeter Firewall (Physical) Physical VM VM DFW Hypervisor NSX DFW positioned for internal SDDC traffic protection: DFW: East – West traffic protection DFW: E-W SDDC (Software Defined DC) CONFIDENTIAL 26

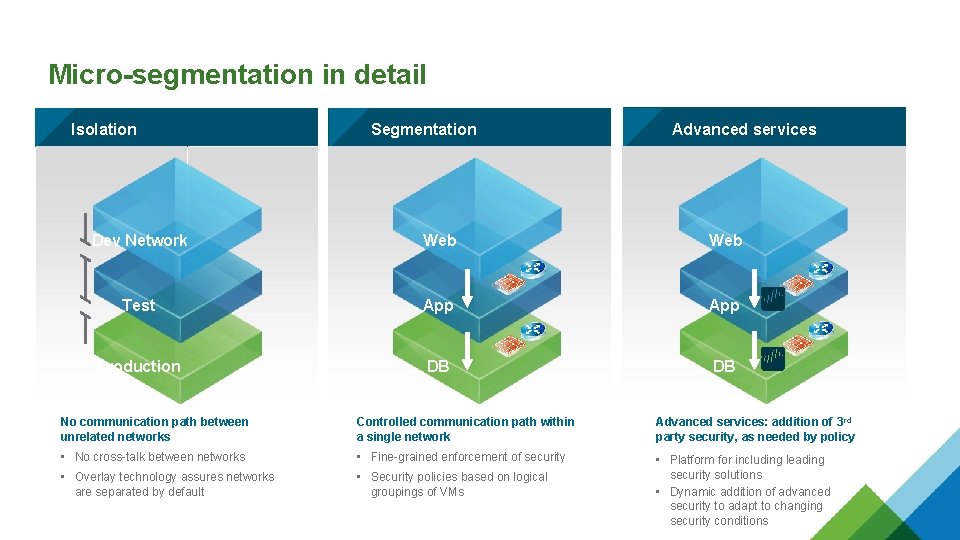
Micro-segmentation in detail Isolation Segmentation Advanced services Dev Network Web Test App Production DB DB No communication path between unrelated networks Controlled communication path within a single network Advanced services: addition of 3 rd party security, as needed by policy • No cross-talk between networks • Fine-grained enforcement of security • Overlay technology assures networks are separated by default • Security policies based on logical groupings of VMs • Platform for including leading security solutions • Dynamic addition of advanced security to adapt to changing security conditions

NSX Partners and Service Categories NSX Partner Extensions Physical-to-Virtual Services Operations and Visibility Security http: //www. vmware. com/products/nsx/resources. html Application Delivery Services

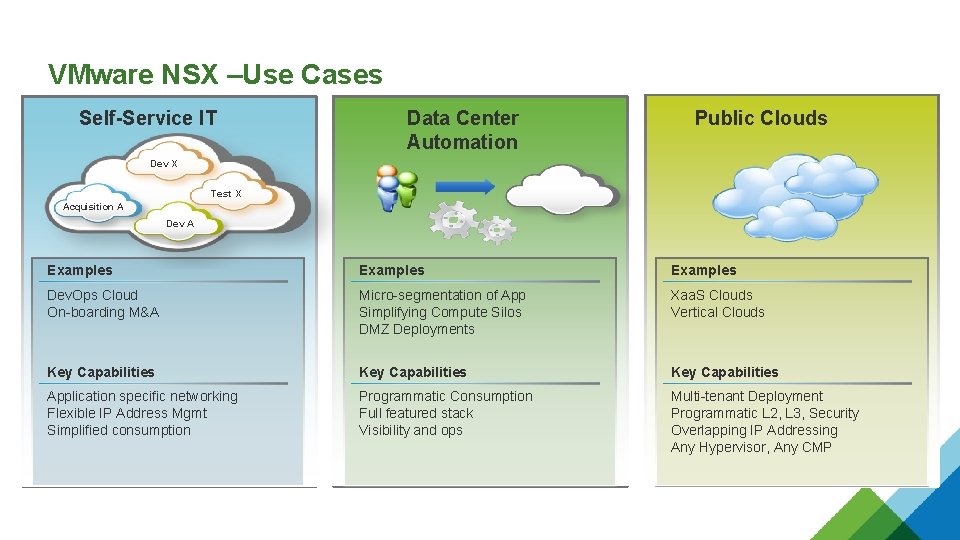
VMware NSX –Use Cases Self-Service IT Data Center Automation Public Clouds Dev X Test X Acquisition A Dev A Examples Dev. Ops Cloud On-boarding M&A Micro-segmentation of App Simplifying Compute Silos DMZ Deployments Xaa. S Clouds Vertical Clouds Key Capabilities Application specific networking Flexible IP Address Mgmt Simplified consumption Programmatic Consumption Full featured stack Visibility and ops Multi-tenant Deployment Programmatic L 2, L 3, Security Overlapping IP Addressing Any Hypervisor, Any CMP

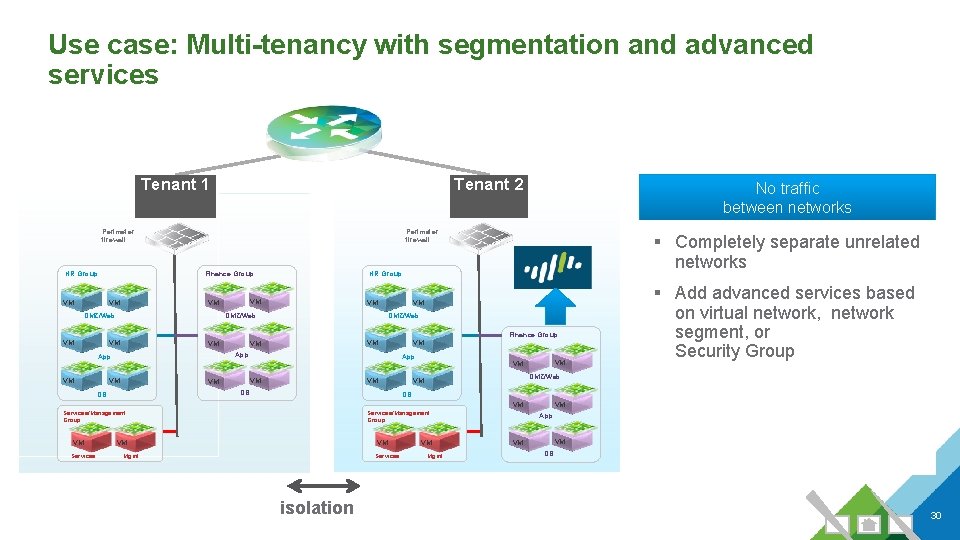
Use case: Multi-tenancy with segmentation and advanced services Tenant 1 Tenant 2 Perimeter firewall HR Group VM Perimeter firewall VM VM DMZ/Web § Completely separate unrelated networks HR Group Finance Group VM No traffic between networks VM VM DMZ/Web Finance Group VM VM App VM VM VM DB DB VM VM VM DMZ/Web VM DB VM VM Services/Management Group VM Services § Add advanced services based on virtual network, network segment, or Security Group Services/Management Group VM VM Mgmt Services isolation VM Mgmt App VM VM DB 30

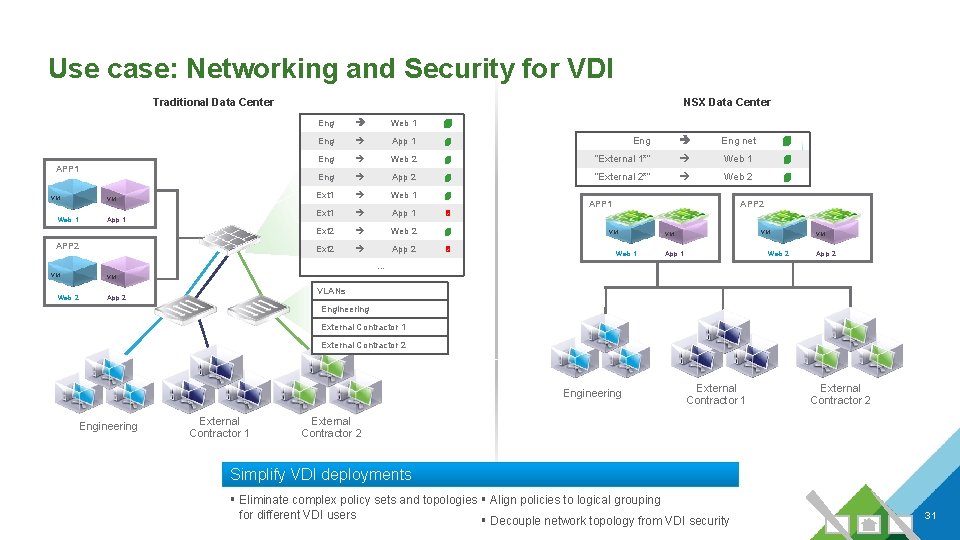
Use case: Networking and Security for VDI Traditional Data Center APP 1 VM Web 1 VM App 1 APP 2 NSX Data Center Eng Web 1 4 Eng App 1 4 Eng net 4 Eng Web 2 4 “External 1*” Web 1 4 Eng App 2 4 “External 2*” Web 2 4 Ext 1 Web 1 4 Ext 1 App 1 5 Ext 2 Web 2 4 Ext 2 App 2 5 APP 1 APP 2 VM Web 1 VM VM App 1 Web 2 VM App 2 … VM Web 2 VM VLANs App 2 Engineering External Contractor 1 External Contractor 2 Simplify VDI deployments § Eliminate complex policy sets and topologies § Align policies to logical grouping for different VDI users § Decouple network topology from VDI security 31

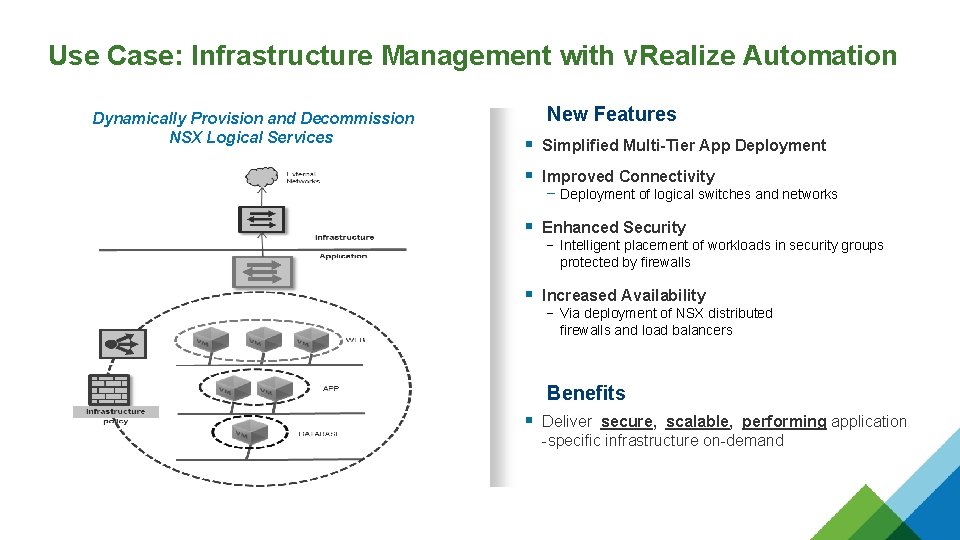
Use Case: Infrastructure Management with v. Realize Automation Dynamically Provision and Decommission NSX Logical Services New Features § Simplified Multi-Tier App Deployment § Improved Connectivity − Deployment of logical switches and networks § Enhanced Security − Intelligent placement of workloads in security groups protected by firewalls § Increased Availability − Via deployment of NSX distributed firewalls and load balancers Benefits § Deliver secure, scalable, performing application -specific infrastructure on-demand

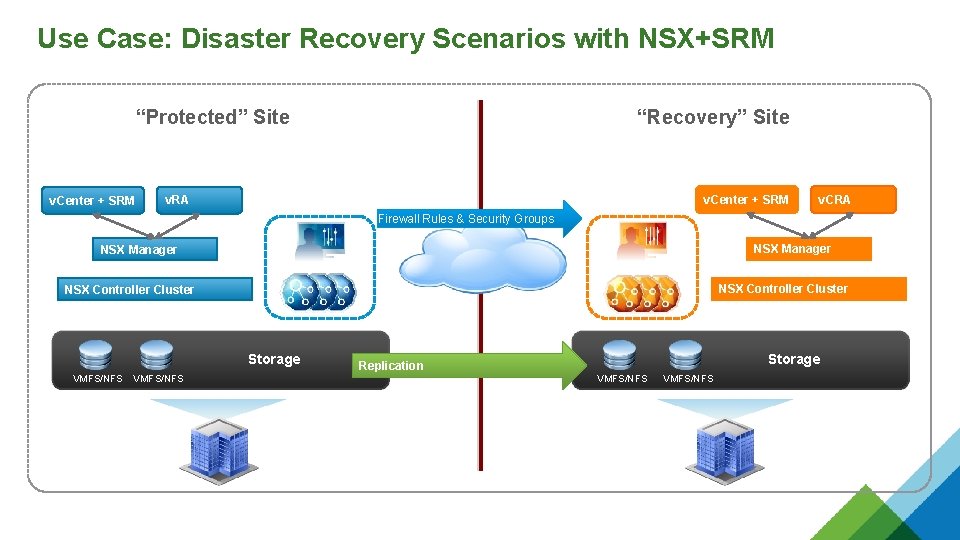
Use Case: Disaster Recovery Scenarios with NSX+SRM “Protected” Site v. Center + SRM “Recovery” Site v. Center + SRM v. RA v. CRA Firewall Rules & Security Groups NSX Manager NSX Controller Cluster Storage VMFS/NFS Replication Storage VMFS/NFS

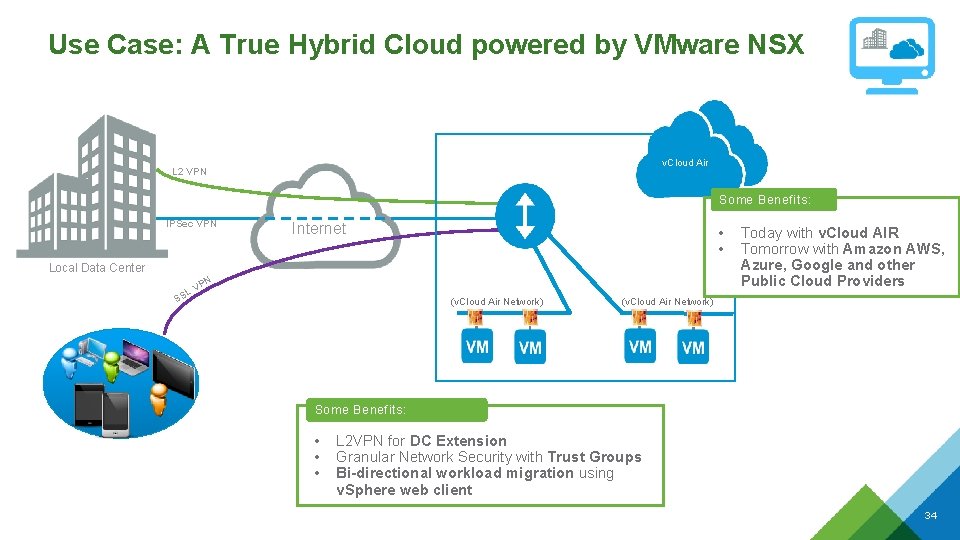
Use Case: A True Hybrid Cloud powered by VMware NSX v. Cloud Air L 2 VPN Some Benefits: IPSec VPN Internet • • Local Data Center N VP L SS (v. Cloud Air Network) Today with v. Cloud AIR Tomorrow with Amazon AWS, Azure, Google and other Public Cloud Providers (v. Cloud Air Network) Some Benefits: • • • L 2 VPN for DC Extension Granular Network Security with Trust Groups Bi-directional workload migration using v. Sphere web client 34

What You’ve Done with NSX What You’re Doing Next 900+ EXPANDED SECURITY New security partners, integrations, and projects and applications of NSX Customers DEEPER INTEGRATION 100+ New infrastructure and operations partners, integrations, and frameworks for IT organizations Production Deployments (adding 25 -50 per quarter) APPLICATION CONTINUITY √ 65+ Organizations invested US$1 M+ in NSX New functionality to scale deployments across v. Center instances, with the ability to: • • • Pool resources from multiple data centers Recover from disasters faster Deploy a hybrid cloud architecture NSX 6. 2 contains over 20 new features Tested against over 1000 new scenarios 35

VMware NSX Momentum Top investment banks Enterprises, public & service providers 36

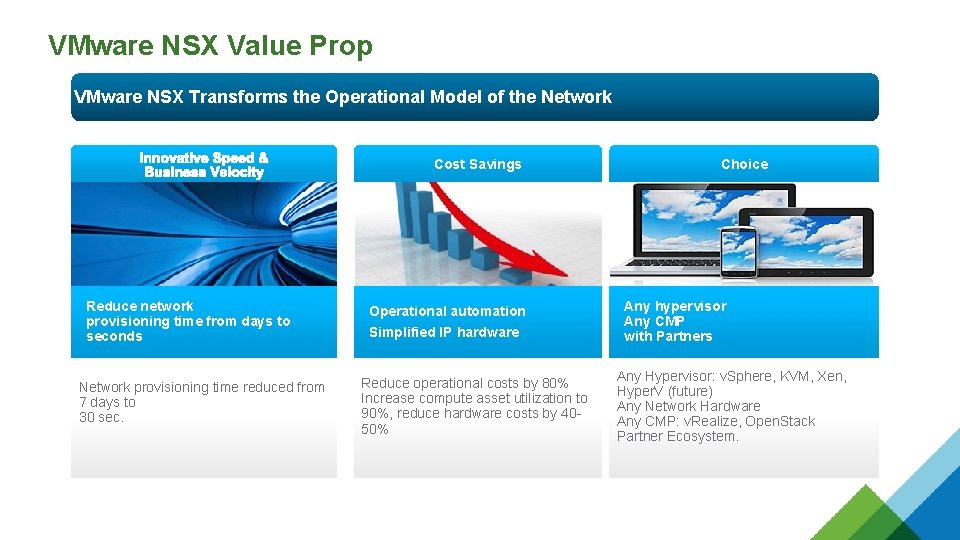
VMware NSX Value Prop VMware NSX Transforms the Operational Model of the Network Cost Savings Reduce network provisioning time from days to seconds Network provisioning time reduced from 7 days to 30 sec. Operational automation Simplified IP hardware Reduce operational costs by 80% Increase compute asset utilization to 90%, reduce hardware costs by 4050% Choice Any hypervisor Any CMP with Partners Any Hypervisor: v. Sphere, KVM, Xen, Hyper. V (future) Any Network Hardware Any CMP: v. Realize, Open. Stack Partner Ecosystem.

What’s Next… Play VMware NSX Hands-on Labs labs. hol. vmware. com Learn Explore, Engage, Evolve virtualizeyournetwork. com Deploy NSX Technical Resources Reference Designs vmware. com/products/nsx/resources Network Virtualization Blog blogs. vmware. com/networkvirtualization VMware NSX You. Tube Channel youtube. com/user/vmwarensx NSX Product Page vmware. com/go/nsx VMware NSX Community communities. vmware. com/community/vmtn/nsx NSX Training & Certification www. vmware. com/go/NVtraining 38

Q&A 39

Thank you. § Luca Morelli § Network Virtualization Platform Sr System Engineer
 Madonna costantinopolitana padova
Madonna costantinopolitana padova Srs
Srs Wwwaaaddd
Wwwaaaddd Nsx-t ssl passthrough
Nsx-t ssl passthrough Ralph morelli
Ralph morelli Sonorenses famosos
Sonorenses famosos Deambulación temprana
Deambulación temprana Marc morelli
Marc morelli Dani su čovjekovi kao sijeno
Dani su čovjekovi kao sijeno Dušo kristova posveti me note
Dušo kristova posveti me note Slatka dušo mom životu analiza
Slatka dušo mom životu analiza Introduzione ai database
Introduzione ai database Riggettato
Riggettato Introduzione al calcolo letterale
Introduzione al calcolo letterale Tesina sulle donne introduzione
Tesina sulle donne introduzione Manuale di pedagogia pdf
Manuale di pedagogia pdf Introduzione alla psicologia della comunicazione
Introduzione alla psicologia della comunicazione Introduzione alle criptovalute
Introduzione alle criptovalute Enti primitivi
Enti primitivi Introduzione tesina sfruttamento minorile
Introduzione tesina sfruttamento minorile Introduzione cap
Introduzione cap Tesi sul linguaggio giovanile
Tesi sul linguaggio giovanile Introduzione al pensiero complesso
Introduzione al pensiero complesso Violazione dei diritti umani tesina
Violazione dei diritti umani tesina Introduzione alle basi di dati
Introduzione alle basi di dati Introduzione alla sociologia ritzer
Introduzione alla sociologia ritzer Introduzione alla finanza
Introduzione alla finanza Alla sera ugo foscolo divisione in sillabe
Alla sera ugo foscolo divisione in sillabe Introduzione agli algoritmi e strutture dati
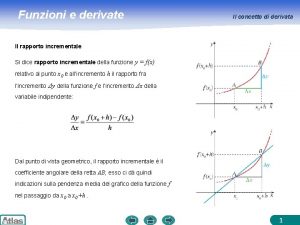
Introduzione agli algoritmi e strutture dati Derivata definizione
Derivata definizione Struttura della lettera
Struttura della lettera Introduzione alla psicometria
Introduzione alla psicometria Potenza di monomi
Potenza di monomi Java introduzione
Java introduzione I promessi sposi autore
I promessi sposi autore Cos'è il romanzo storico per manzoni
Cos'è il romanzo storico per manzoni Introduzione a python
Introduzione a python Sinalefe
Sinalefe Introduzione caccia al tesoro
Introduzione caccia al tesoro Cosa sono le frazioni complementari
Cosa sono le frazioni complementari Equazioni di maxwell in forma integrale
Equazioni di maxwell in forma integrale