Network Security Essentials Chapter 7 Malicious Software Fourth













- Slides: 17

Network Security Essentials Chapter 7 Malicious Software Fourth Edition by William Stallings Dr. Bremnavas Ismail Mohideen

Key Objectives of Chapter – 7 • To learn about the types of malicious software • To understand the virus and virus countermeasures • To learn about the worms and distributed denial of service attacks

Malicious Software: The most sophisticated types of threats of computer system are presented by a program that exploit vulnerabilities in computer system. Divided in to two categories: Those that need a host program Those that are independent

Terminology for Malicious Software

Multiple – Threat malware • Can be classified into two broad categories: A Multipartite virus infect multiways, capable of infecting multiple types of files A blended attack uses multiple methods of infection or transmission, to maximize the speed of contagion and the severity of the attach • Nimda uses four distribution blended attack methods: • Email: A user on vulnerable host opens an infected email attachment • Windows shares: Nimda scans hosts for unsecured windows file shares • Web Server: Nimda scans Webservers, looking for known vulnerabilities in microsoft IIS • Web Clients: If a vulnerable web clients visits a web server that has been infected by Nimda

Viruses • A computer virus is a piece of software that can “infect” other programs by modify them • The modification includes injecting the original code with a routine to make copies of the virus code, which can then go on to infect other content

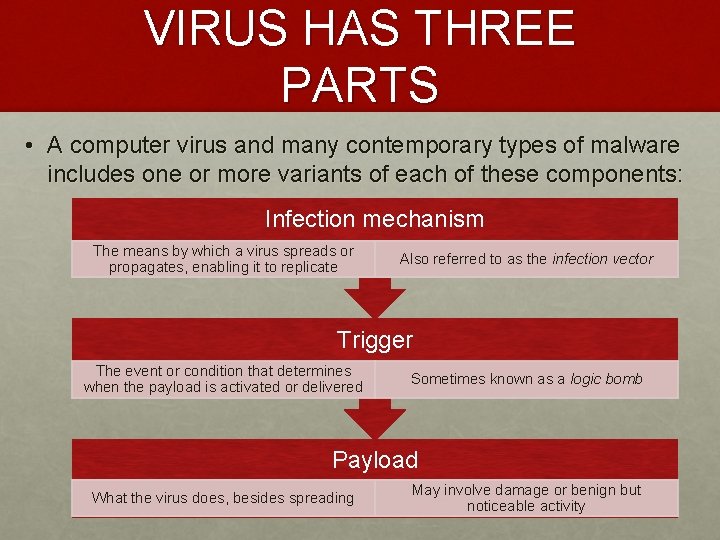
VIRUS HAS THREE PARTS • A computer virus and many contemporary types of malware includes one or more variants of each of these components: Infection mechanism The means by which a virus spreads or propagates, enabling it to replicate Also referred to as the infection vector Trigger The event or condition that determines when the payload is activated or delivered Sometimes known as a logic bomb Payload What the virus does, besides spreading May involve damage or benign but noticeable activity

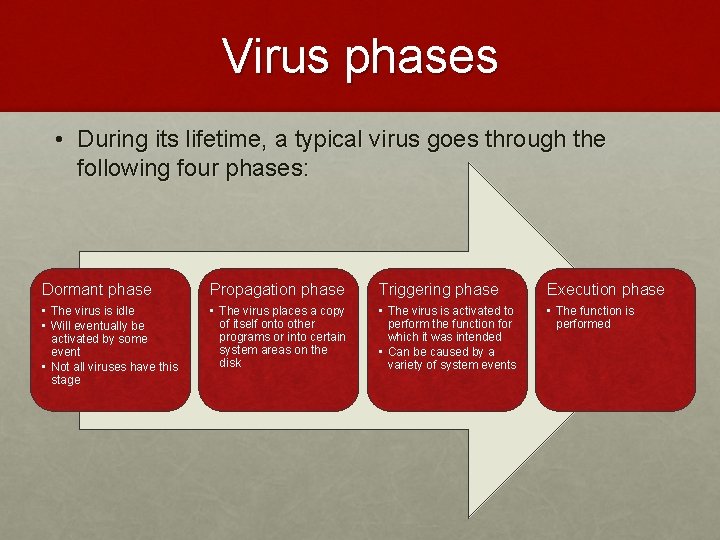
Virus phases • During its lifetime, a typical virus goes through the following four phases: Dormant phase Propagation phase Triggering phase Execution phase • The virus is idle • Will eventually be activated by some event • Not all viruses have this stage • The virus places a copy of itself onto other programs or into certain system areas on the disk • The virus is activated to perform the function for which it was intended • Can be caused by a variety of system events • The function is performed

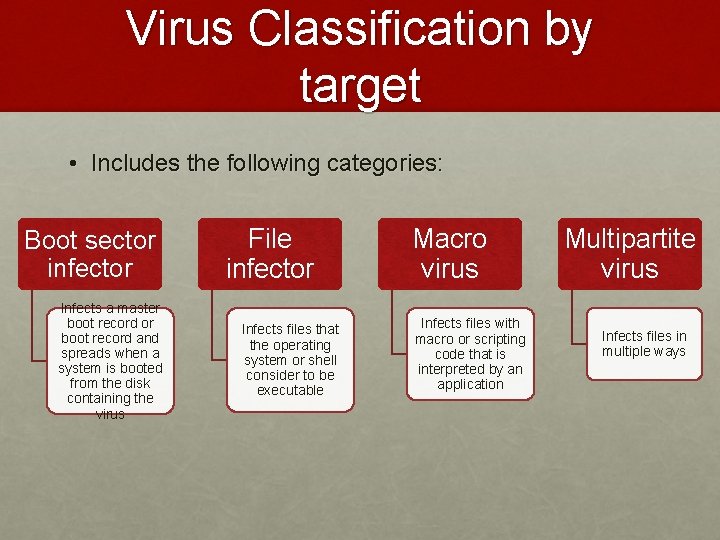
Virus Classification by target • Includes the following categories: Boot sector infector Infects a master boot record or boot record and spreads when a system is booted from the disk containing the virus File infector Infects files that the operating system or shell consider to be executable Macro virus Infects files with macro or scripting code that is interpreted by an application Multipartite virus Infects files in multiple ways

Macro VIRUS • Macro viruses infect scripting code used to support active content in a variety of user document types • Threatening for a number of reasons: • A macro virus is platform independent • Macro viruses infect documents, not executable portions of code • Macro viruses are easily spread, • Because macro viruses infect user documents rather than system programs, traditional file system access controls are of limited use in preventing their spread

E-Mail viruses • A more recent development in malicious software • First spreading email viruses is Melissa, made use of a Microsoft word macro embedded in an attachment. • If the recipient opens the email attachment, the word macro is activated then • The email virus sends itself to everyone on the mailing list • The virus does local damage on the users system

Virus countermeasures • Antivirus Approaches: The idea solution to the threat of viruses is prevention. • Detection : Once the infection has occurred • Identification : Once detection has been achieved • Removal: Once the specific virus has been identified

worms • A Worm is a program that can replicate itself and send copies from computer to computer across network connections. • Upon activation, the worm may replicate and propagate again • To replicate itself, a worm uses some means to access remote systems: • Electronic mail or instant messenger facility • Remote execution capability • Remote login capability

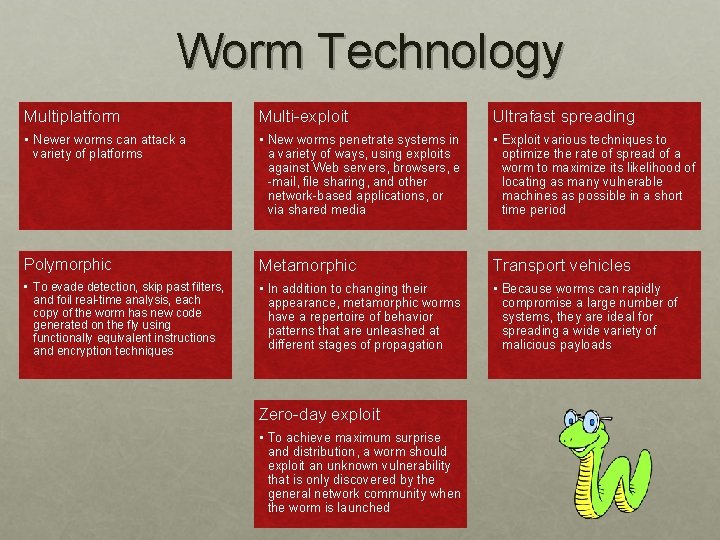
Worm Technology Multiplatform Multi-exploit Ultrafast spreading • Newer worms can attack a variety of platforms • New worms penetrate systems in a variety of ways, using exploits against Web servers, browsers, e -mail, file sharing, and other network-based applications, or via shared media • Exploit various techniques to optimize the rate of spread of a worm to maximize its likelihood of locating as many vulnerable machines as possible in a short time period Polymorphic Metamorphic Transport vehicles • To evade detection, skip past filters, and foil real-time analysis, each copy of the worm has new code generated on the fly using functionally equivalent instructions and encryption techniques • In addition to changing their appearance, metamorphic worms have a repertoire of behavior patterns that are unleashed at different stages of propagation • Because worms can rapidly compromise a large number of systems, they are ideal for spreading a wide variety of malicious payloads Zero-day exploit • To achieve maximum surprise and distribution, a worm should exploit an unknown vulnerability that is only discovered by the general network community when the worm is launched

Mobile phone warms • Worms communicate through bluetooth wireless connections or via the multimedia messaging service(MMS). • The target is the smartphone, which is a mobile phone that permits users to install software applications from sources other than the cellular network operator. • Mobile phone malware can completely disable the phone, delete data on the phone, or force the device to send costly messages to premium priced numbers. • An example of a mobile phone worm is Comm. Warrior, which is launched in 2005

Worm countermeasures • The requirements for an effective worm countermeasures scheme • • • Generality Timeliness Resiliency Minimal denial-of-service costs Transparency Global and local coverage

Distributed Denial of Service Attacks (DDOS) • Attacks that make computer systems inaccessible by flooding servers, networks, or even end-user systems with useless traffic so that legitimate users can no longer gain access to those resources • One way to classify DDo. S attacks is in terms of the type of resources that is consumed • The resource consumed is either an internal host resource on the target system or data transmission capacity in the local network to which the target is attacked