Network Kernel Architectures and Implementation 01204423 Medium Access














- Slides: 43

Network Kernel Architectures and Implementation (01204423) ) Medium Access Control and WPAN Technologies Chaiporn Jaikaeo chaiporn. j@ku. ac. th Department of Computer Engineering Kasetsart University Materials taken from lecture slides by Karl and Willig

Overview l l Principal options and difficulties Contention-based protocols Schedule-based protocols Wireless Personal Area Networks Technologies 2

Difficulties l Medium access in wireless networks is difficult, mainly because of Ø Ø l Half-duplex communication High error rates Requirements Ø Ø As usual: high throughput, low overhead, low error rates, … Additionally: energy-efficient, handle switched off devices! 3

Requirements for Energy-Efficient MAC Protocols l Recall Ø Ø Ø l Energy problems Ø Ø l Transmissions are costly Receiving about as expensive as transmitting Idling can be cheaper but is still expensive Collisions Overhearing Idle listening Protocol overhead Always wanted: Low complexity solution 4

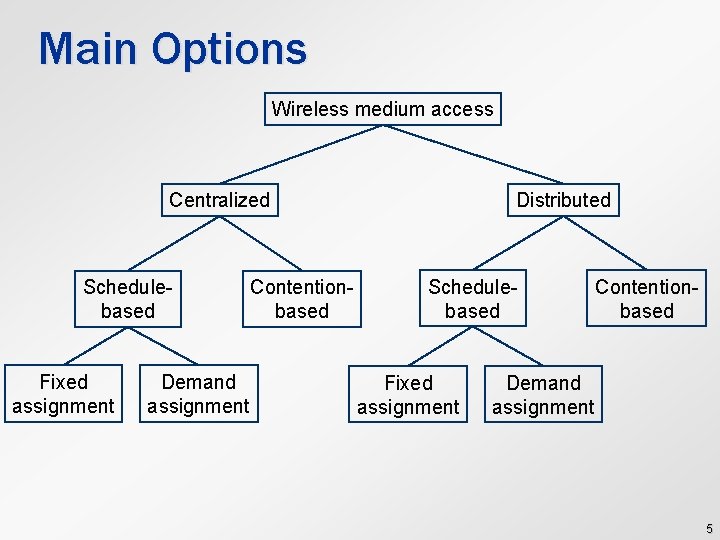
Main Options Wireless medium access Centralized Schedulebased Fixed assignment Demand assignment Contentionbased Distributed Schedulebased Fixed assignment Contentionbased Demand assignment 5

Centralized Medium Access l A central station controls when a node may access the medium Ø Ø l l l E. g. , Polling, computing TDMA schedules Advantage: Simple, efficient Not directly feasible for non-trivial wireless network sizes But: Can be quite useful when network is somehow divided into smaller groups Distributed approach still preferable 6

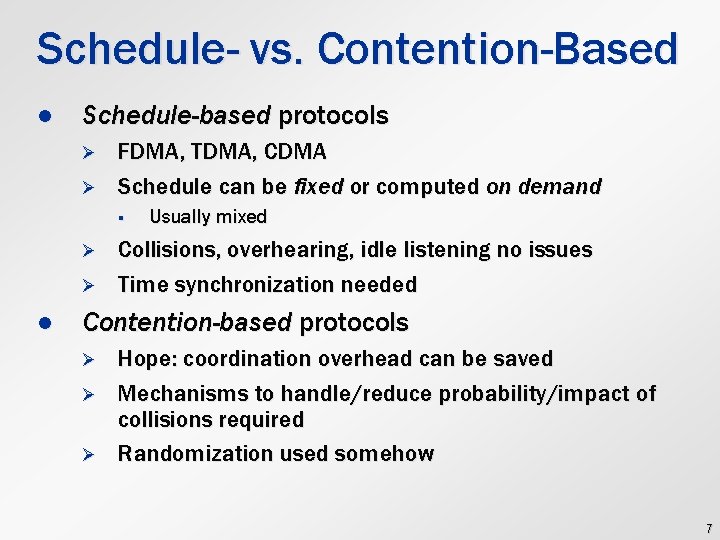
Schedule- vs. Contention-Based l Schedule-based protocols Ø Ø FDMA, TDMA, CDMA Schedule can be fixed or computed on demand § Ø Ø l Usually mixed Collisions, overhearing, idle listening no issues Time synchronization needed Contention-based protocols Ø Ø Ø Hope: coordination overhead can be saved Mechanisms to handle/reduce probability/impact of collisions required Randomization used somehow 7

Overview l l Principal options and difficulties Contention-based protocols Schedule-based protocols Wireless Personal Area Networks Technologies 8

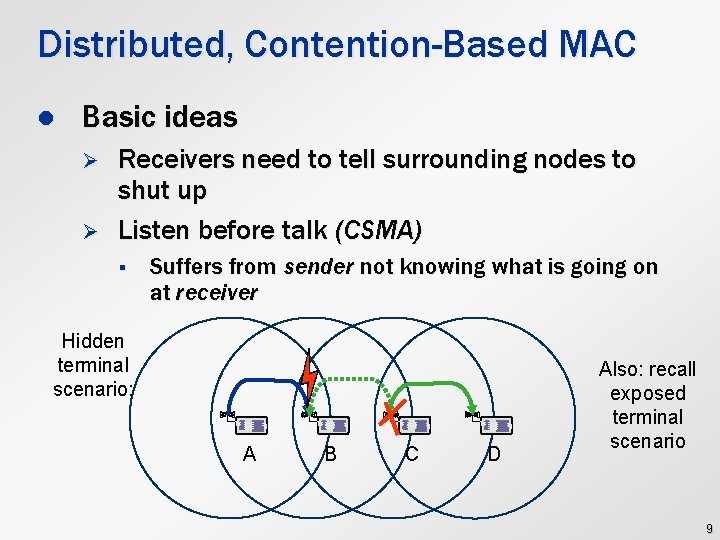
Distributed, Contention-Based MAC l Basic ideas Ø Ø Receivers need to tell surrounding nodes to shut up Listen before talk (CSMA) § Suffers from sender not knowing what is going on at receiver Hidden terminal scenario: A B C D Also: recall exposed terminal scenario 9

How To Shut Up Senders l Inform potential interferers during reception Ø Ø Cannot use the same channel So use a different one § l Busy tone protocol Inform potential interferers before reception Ø Ø Ø Can use same channel Receiver itself needs to be informed, by sender, about impending transmission Potential interferers need to be aware of such information, need to store it 10

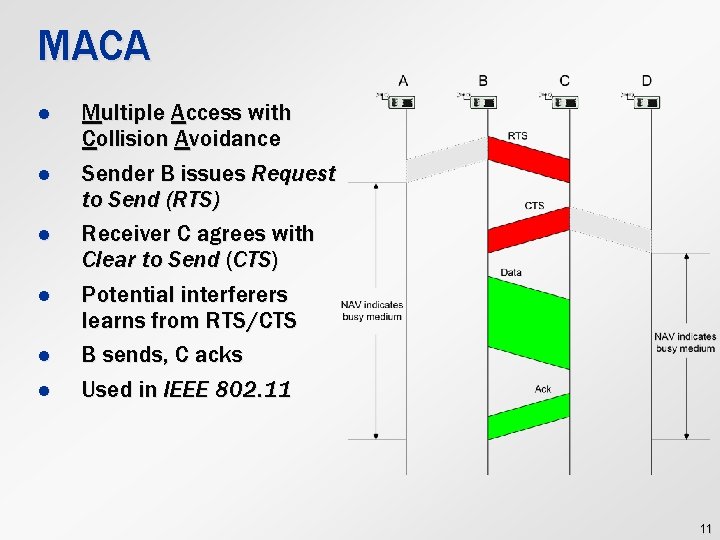
MACA l l l Multiple Access with Collision Avoidance Sender B issues Request to Send (RTS) Receiver C agrees with Clear to Send (CTS) Potential interferers learns from RTS/CTS B sends, C acks Used in IEEE 802. 11 11

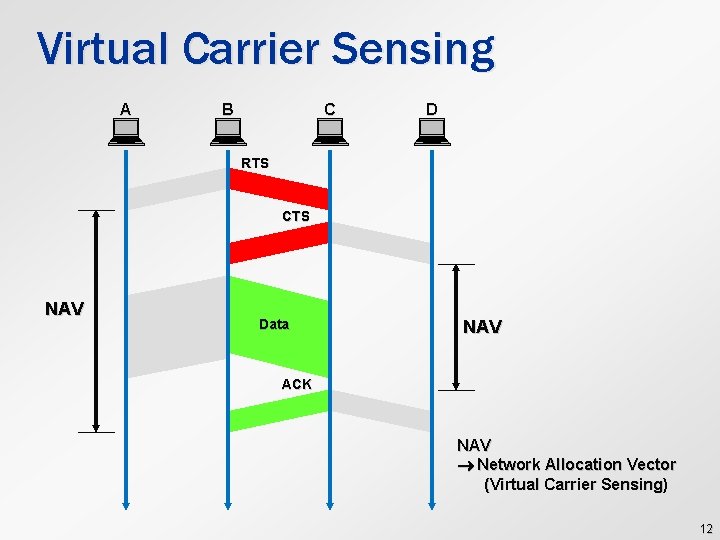
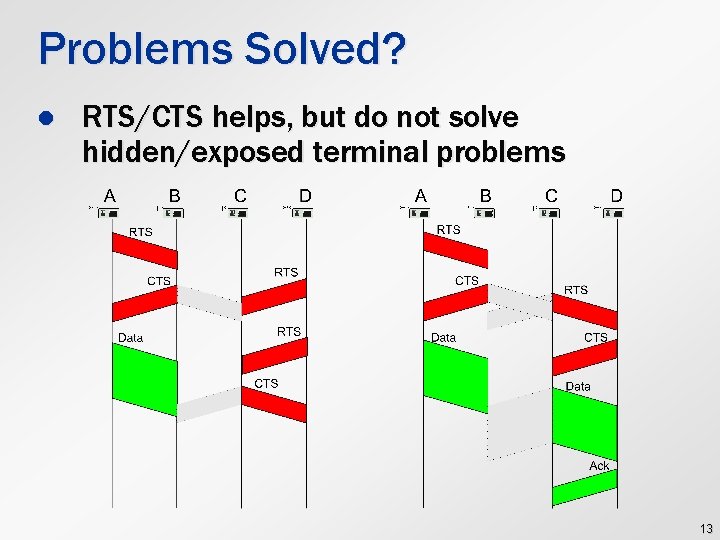
Virtual Carrier Sensing A B C D RTS CTS NAV Data NAV ACK NAV Network Allocation Vector (Virtual Carrier Sensing) 12

Problems Solved? l RTS/CTS helps, but do not solve hidden/exposed terminal problems 13

MACA Problem: Idle listening l Need to sense carrier for RTS or CTS packets Ø l Simple sleeping will break the protocol IEEE 802. 11 solution Ø Ø Ø Idea: Nodes that have data buffered for receivers send traffic indicators at prearranged points in time ATIM - Announcement Traffic Indication Message Receivers need to wake up at these points, but can sleep otherwise 14

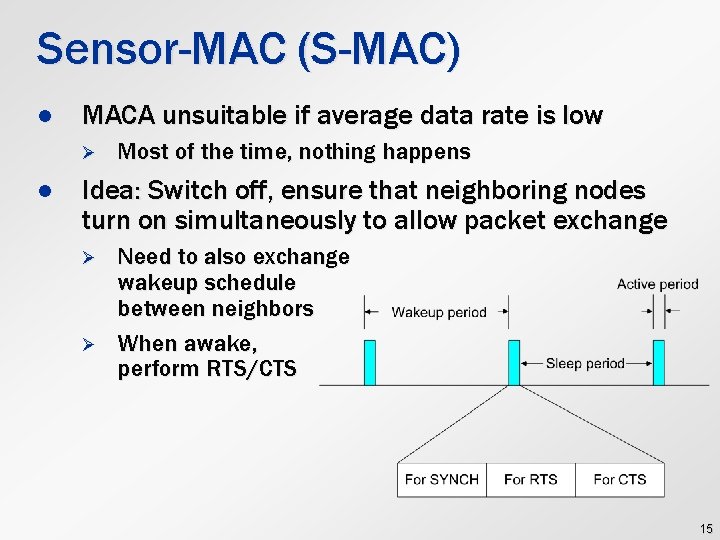
Sensor-MAC (S-MAC) l MACA unsuitable if average data rate is low Ø l Most of the time, nothing happens Idea: Switch off, ensure that neighboring nodes turn on simultaneously to allow packet exchange Ø Ø Need to also exchange wakeup schedule between neighbors When awake, perform RTS/CTS 15

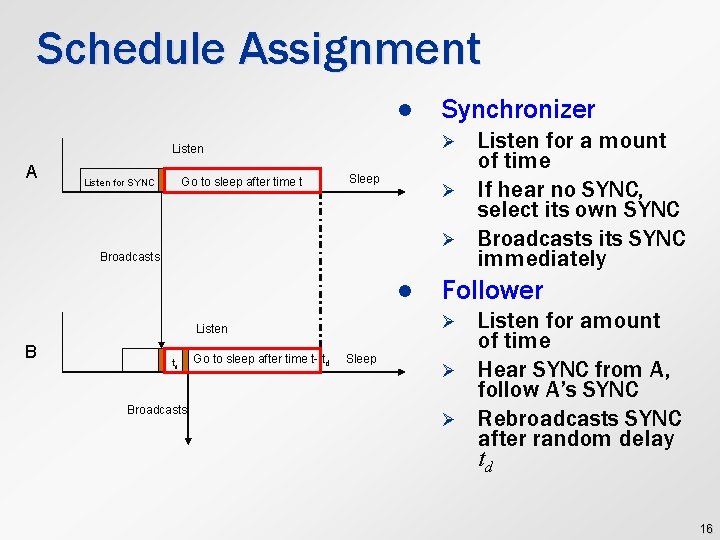
Schedule Assignment l Ø Listen A Go to sleep after time t Listen for SYNC Synchronizer Sleep Ø Ø Broadcasts l B td Broadcasts Go to sleep after time t- td Follower Ø Listen Sleep Listen for a mount of time If hear no SYNC, select its own SYNC Broadcasts its SYNC immediately Ø Ø Listen for amount of time Hear SYNC from A, follow A’s SYNC Rebroadcasts SYNC after random delay td 16

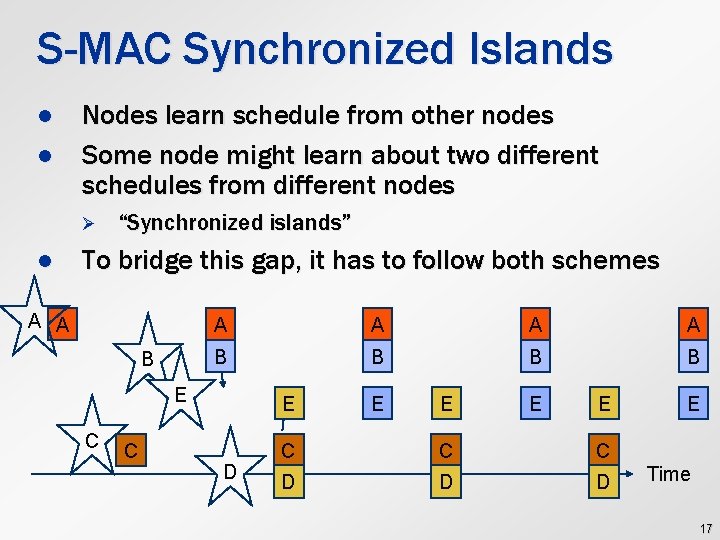
S-MAC Synchronized Islands l l Nodes learn schedule from other nodes Some node might learn about two different schedules from different nodes Ø l “Synchronized islands” To bridge this gap, it has to follow both schemes A A B B E C C E D E E C C C D D D E Time 17

Preamble Sampling l Alternative option: Don’t try to explicitly synchronize nodes Ø l Have receiver sleep and only periodically sample the channel Use long preambles to ensure that receiver stays awake to catch actual packet Ø Example: B-MAC, Wise. MAC Start transmission: Check channel Long preamble Actual packet Check channel Stay awake! Check channel 18

B-MAC l l Very simple MAC protocol Employs Ø Ø Ø Clear Channel Assessment (CCA) and backoffs for channel arbitration Link-layer acknowledgement for reliability Low-power listening (LPL) § l I. e. , preamble sampling Currently: Often considered as the default WSN MAC protocol 19

B-MAC l B-MAC does not have Ø Ø Synchronization RTS/CTS Results in simpler, leaner implementation Clean and simple interface 20

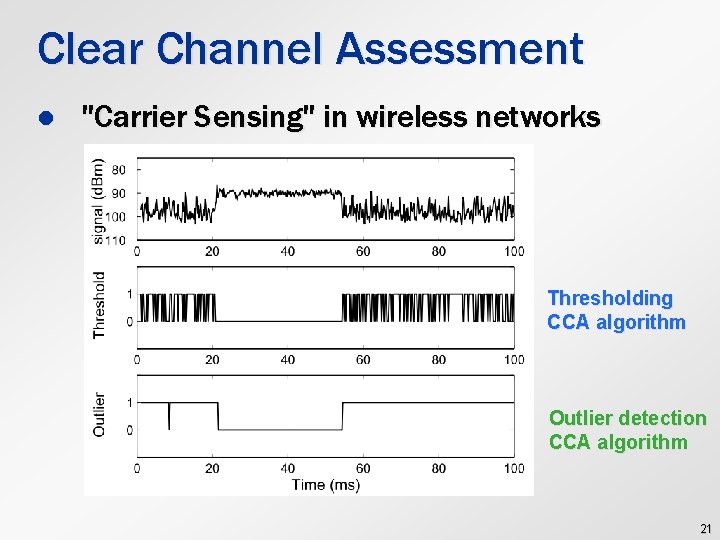
Clear Channel Assessment l "Carrier Sensing" in wireless networks Thresholding CCA algorithm Outlier detection CCA algorithm 21

Contiki LPL and LPP l Low-Power Listening (LPL) Ø Ø l Also known as Contiki. MAC Similar to B-MAC, but allowing packet-based MAC such as IEEE 802. 15. 4 Low-Power Probing (LPP) Ø Ø Receivers periodically broadcast a probe Sender listens for probes from receivers before transmitting 22

Overview l l Principal options and difficulties Contention-based protocols Schedule-based protocols Wireless Personal Area Networks Technologies 23

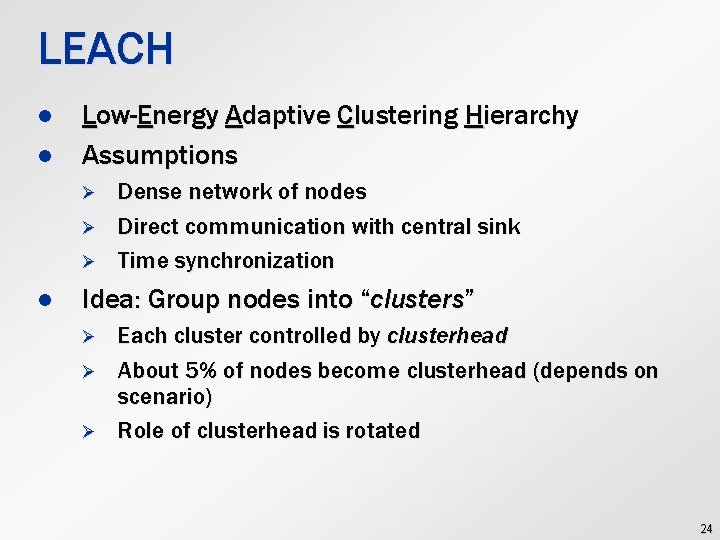
LEACH l l Low-Energy Adaptive Clustering Hierarchy Assumptions Ø Ø Ø l Dense network of nodes Direct communication with central sink Time synchronization Idea: Group nodes into “clusters” Ø Ø Ø Each cluster controlled by clusterhead About 5% of nodes become clusterhead (depends on scenario) Role of clusterhead is rotated 24

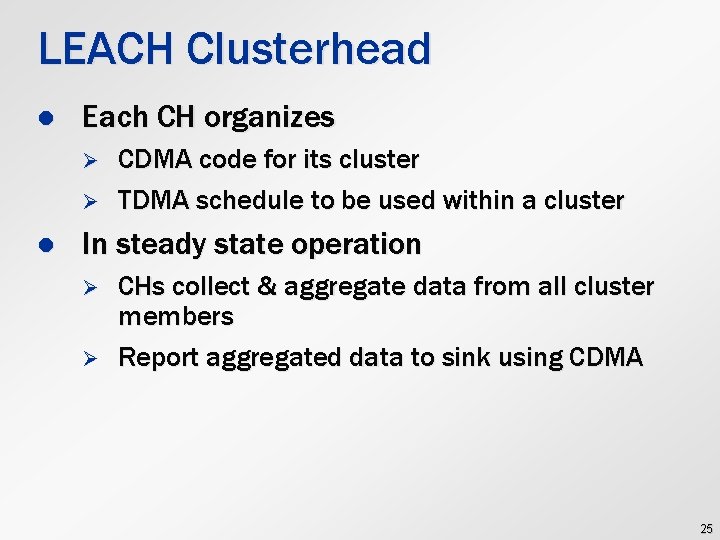
LEACH Clusterhead l Each CH organizes Ø Ø l CDMA code for its cluster TDMA schedule to be used within a cluster In steady state operation Ø Ø CHs collect & aggregate data from all cluster members Report aggregated data to sink using CDMA 25

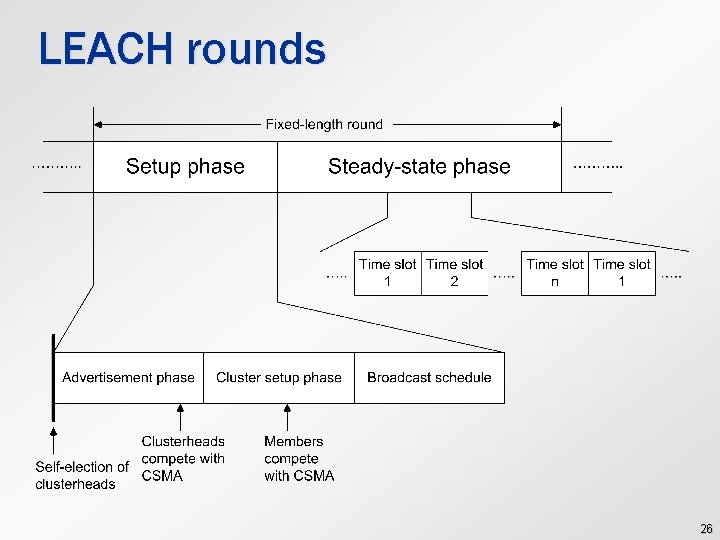
LEACH rounds 26

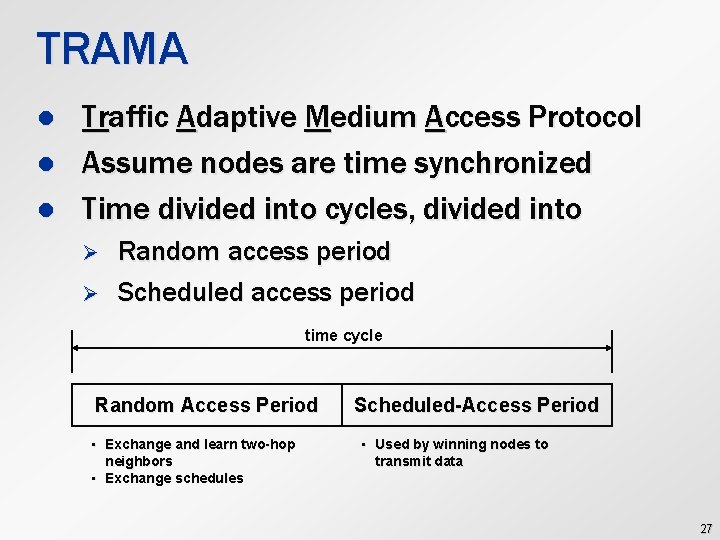
TRAMA l l l Traffic Adaptive Medium Access Protocol Assume nodes are time synchronized Time divided into cycles, divided into Ø Ø Random access period Scheduled access period time cycle Random Access Period • Exchange and learn two-hop neighbors • Exchange schedules Scheduled-Access Period • Used by winning nodes to transmit data 27

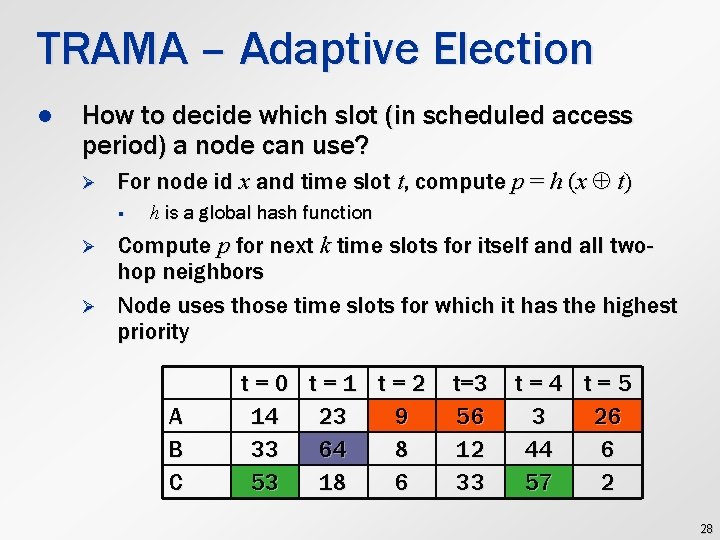
TRAMA – Adaptive Election l How to decide which slot (in scheduled access period) a node can use? Ø For node id x and time slot t, compute p = h (x t) § Ø Ø h is a global hash function Compute p for next k time slots for itself and all twohop neighbors Node uses those time slots for which it has the highest priority A B C t=0 t=1 t=2 14 23 9 33 64 8 53 18 6 t=3 56 12 33 t=4 t=5 3 26 44 6 57 2 28

Overview l l Principal options and difficulties Contention-based protocols Schedule-based protocols Wireless Personal Area Networks Technologies 29

IEEE 802. 15. 4 l IEEE standard for low-rate WPAN (LR-WPAN) applications Ø Ø Ø l Physical layer Ø Ø Ø l Low-to-medium bit rates Moderate delays without too strict requirements Low energy consumption 20 kbps over 1 channel @ 868 -868. 6 MHz 40 kbps over 10 channels @ 905 – 928 MHz 250 kbps over 16 channels @ 2. 4 GHz MAC protocol Ø Ø Ø Single channel at any one time Combines contention-based and schedule-based schemes Asymmetric: nodes can assume different roles 30

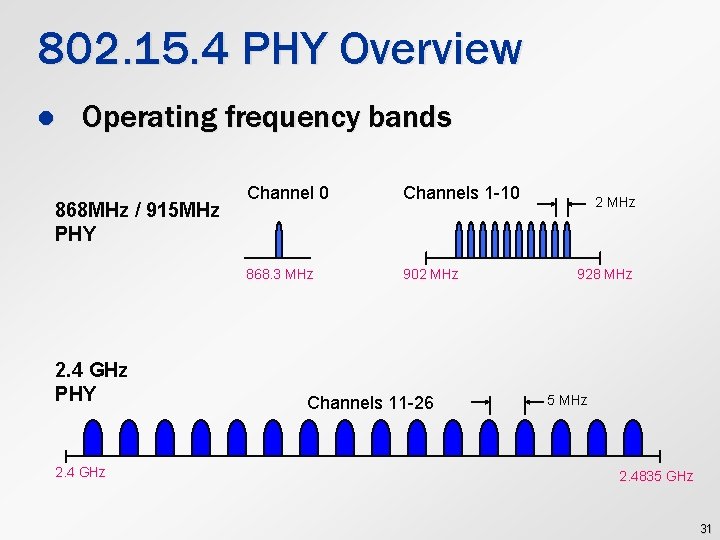
802. 15. 4 PHY Overview l Operating frequency bands 868 MHz / 915 MHz PHY 2. 4 GHz Channel 0 Channels 1 -10 868. 3 MHz 902 MHz Channels 11 -26 2 MHz 928 MHz 5 MHz 2. 4835 GHz 31

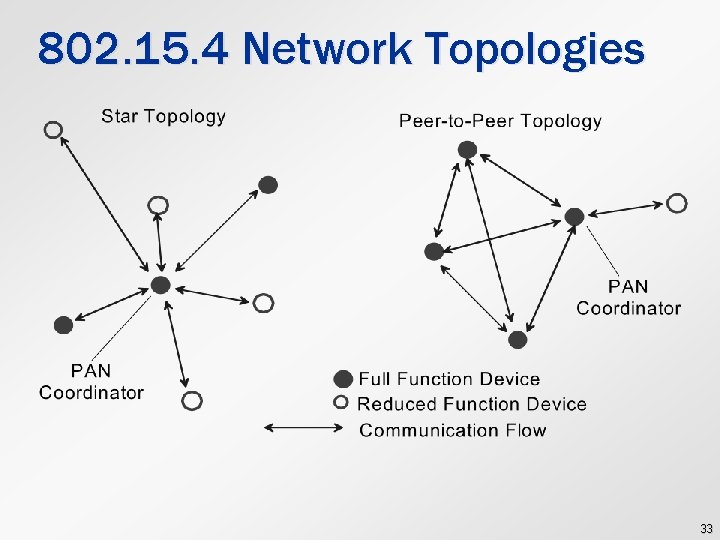
802. 15. 4 Device Classes l Full function device (FFD) § § § l Any topology Network coordinator capable Talks to any other device Reduced function device (RFD) § § Limited to star topology Cannot become a network coordinator Talks only to a network coordinator Very simplementation 32

802. 15. 4 Network Topologies 33

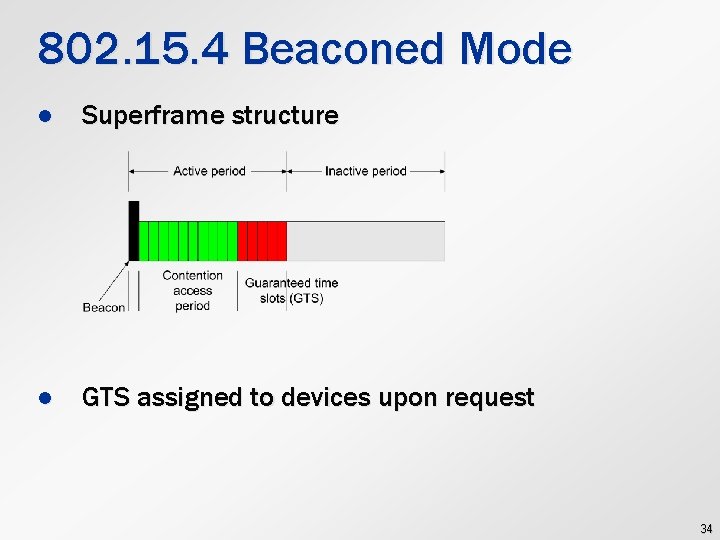
802. 15. 4 Beaconed Mode l Superframe structure l GTS assigned to devices upon request 34

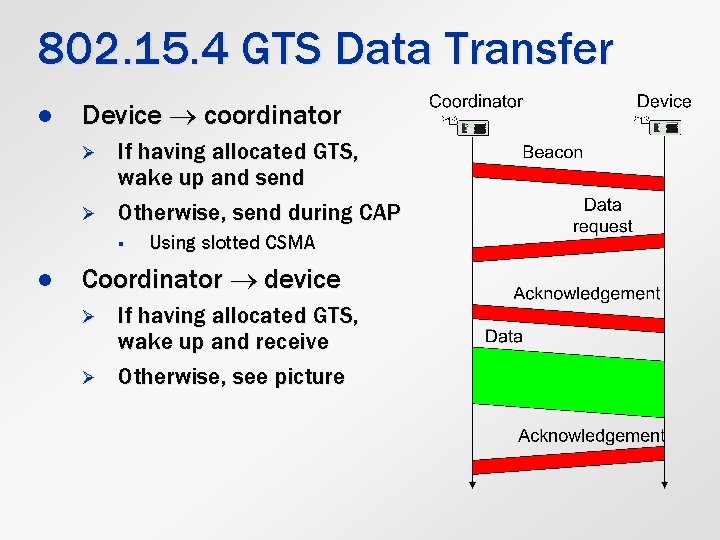
802. 15. 4 GTS Data Transfer l Device coordinator Ø Ø If having allocated GTS, wake up and send Otherwise, send during CAP § l Using slotted CSMA Coordinator device Ø Ø If having allocated GTS, wake up and receive Otherwise, see picture

IEEE 802. 15. 4 Adopters l Zig. Bee Ø Ø Ø l Requires battery life of at least two years be certified Applications: Industrial control, embedded sensing, home automation Zig. Bee RF 4 CE (Radio Frequency for Consumer Electronics) Nest (acquired by Google) Ø Ø Learning thermostats, Smoke and CO alarms Wi. Fi- and Zig. Bee-enabled https: //nest. com 36

Bluetooth Smart l Formally Bluetooth Low Energy (BLE) Ø l l Part of Bluetooth 4. 0 Specification Based on Nokia's Wibree technology First smartphones to support i. Phone 4 S Ø Now supported by most recent smartphones http: //redbearlab. com/blenano/ 37

Bluetooth: Classic vs. Smart Source: Bluetooth SIG 38

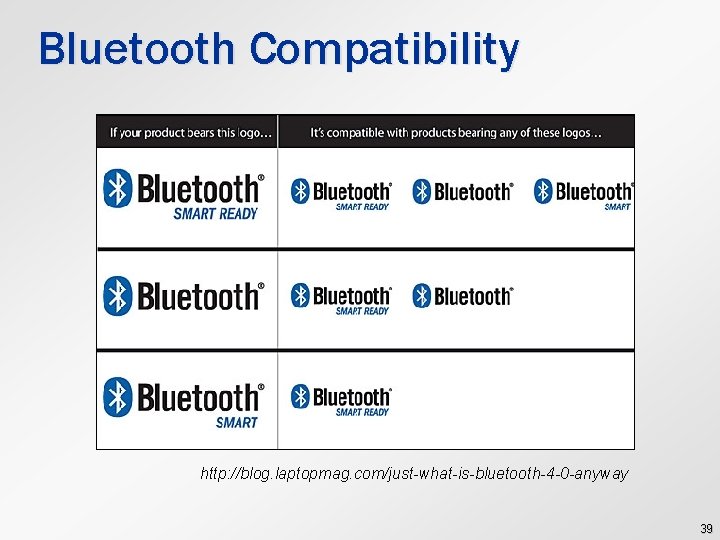
Bluetooth Compatibility http: //blog. laptopmag. com/just-what-is-bluetooth-4 -0 -anyway 39

Bluetooth Smart: Device Roles l Central device Ø Ø Ø l Serves as a hub to one or more peripheral devices Two central devices cannot directly communicate Similar to IEEE 802. 15. 4's FFD Peripheral device Ø Ø Ø Must be connected to a central device Two peripheral devices cannot directly communicate Similar to IEEE 802. 15. 4's RFD 40

ANT / ANT+ / NIKE+ l l Primarily used for fitness monitoring devices ANT / ANT+ Ø l open access multicast wireless sensor network NIKE+ Ø Nike. com Proprietary protocols on 2. 4 GHz band http: //developer. sonymobile. com 41

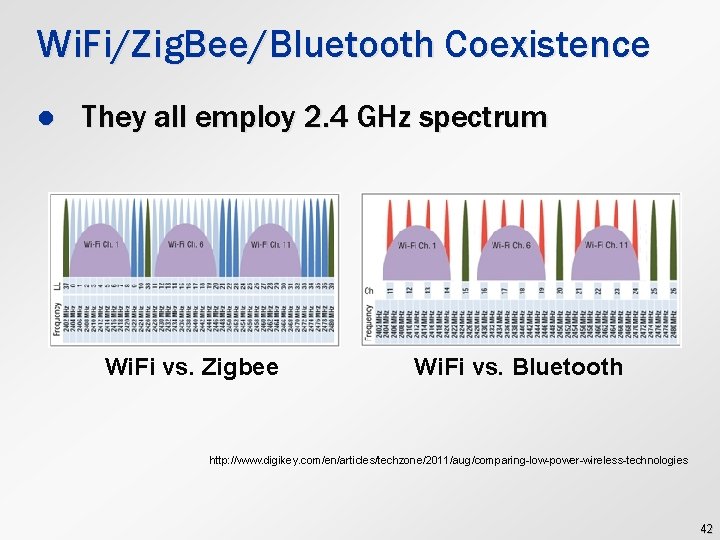
Wi. Fi/Zig. Bee/Bluetooth Coexistence l They all employ 2. 4 GHz spectrum Wi. Fi vs. Zigbee Wi. Fi vs. Bluetooth http: //www. digikey. com/en/articles/techzone/2011/aug/comparing-low-power-wireless-technologies 42

Summary l l l Many different ideas exist for medium access control in MANET/WSN Comparing their performance and suitability is difficult Especially, clearly identifying interdependencies between MAC protocol and other layers/applications is difficult Ø l Which is the best MAC for which application? Nonetheless, certain “common use cases” exist Ø Ø Ø IEEE 802. 11 DCF for MANET IEEE 802. 15. 4 for some early “commercial” WSN variants B-MAC for WSN research not focusing on MAC 43