Network Analysis While Preserving Privacy Karl F Lutzen



















- Slides: 50

Network Analysis While Preserving Privacy* Karl F. Lutzen Information Security Officer kfl@mst. edu *meaning contents of transmission 1

Introduction • Privacy concerns today • Analyzing traffic usually is done by examining packets – Deep packet inspection • Looking at “calling information” can reveal much • Can be used as an IDS • Can be use as policy enforcement 2

“Calling Information” • • Source IP address and port Destination IP address and port Protocol Other data – Timestamps – Number of packets – Bytes • Technology used: Netflow 3

Net. Flow Background • Developed by Cisco to: – Characterize traffic – Account for how and where it flows – Help optimize network investment – Traffic engineering/network planning – Provide usage-based billing 4

Net. Flow Background • Three key characteristics: – Be scalable – Be manageable – Be reliable 5

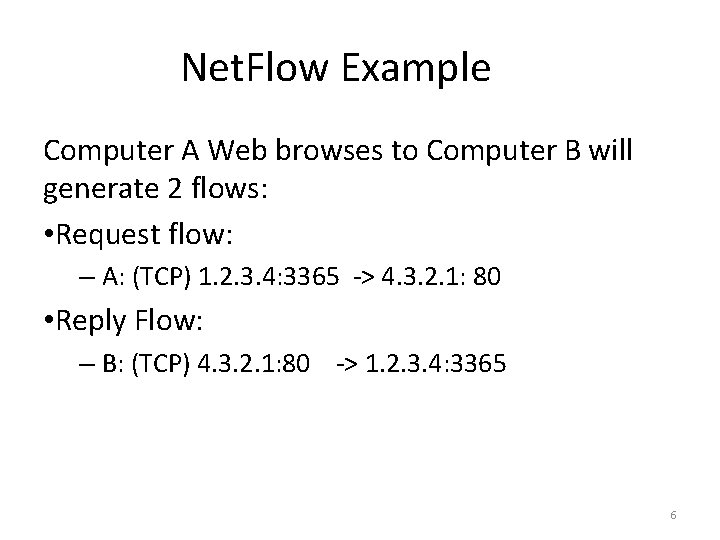
Net. Flow Example Computer A Web browses to Computer B will generate 2 flows: • Request flow: – A: (TCP) 1. 2. 3. 4: 3365 -> 4. 3. 2. 1: 80 • Reply Flow: – B: (TCP) 4. 3. 2. 1: 80 -> 1. 2. 3. 4: 3365 6

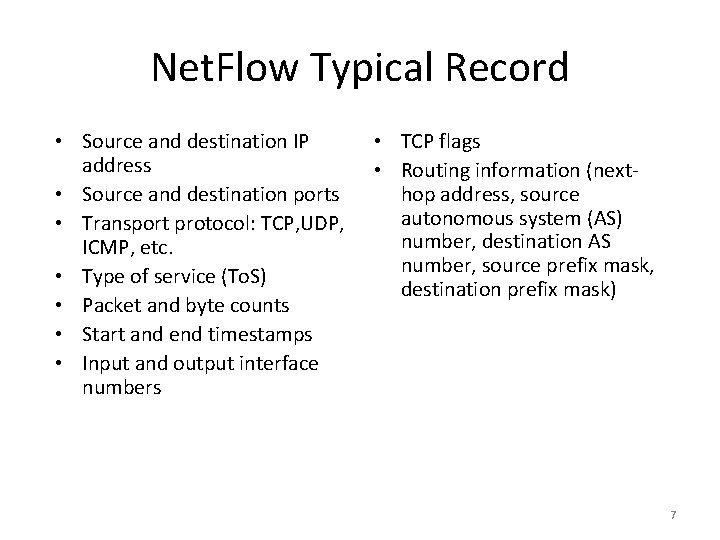
Net. Flow Typical Record • Source and destination IP address • Source and destination ports • Transport protocol: TCP, UDP, ICMP, etc. • Type of service (To. S) • Packet and byte counts • Start and end timestamps • Input and output interface numbers • TCP flags • Routing information (nexthop address, source autonomous system (AS) number, destination AS number, source prefix mask, destination prefix mask) 7

Net. Flow Data Cache • Available on Cisco routers/switches • Available on Juniper routers • Cached on devices • WARNING! Not all devices are Net. Flowenabled! 8

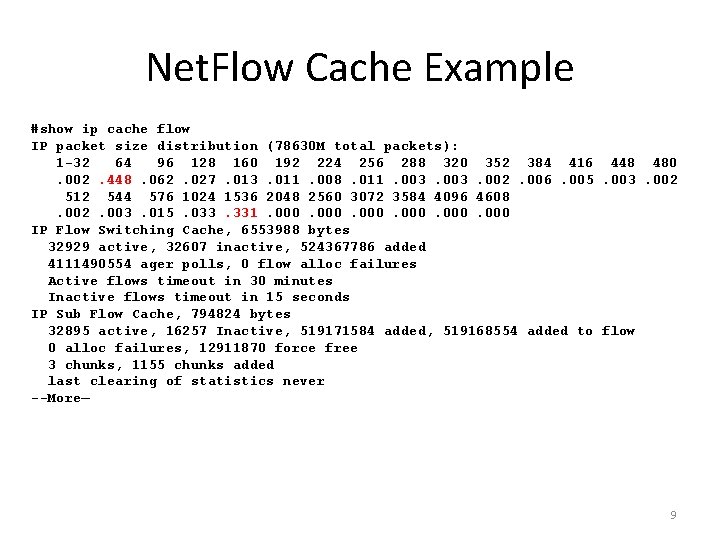
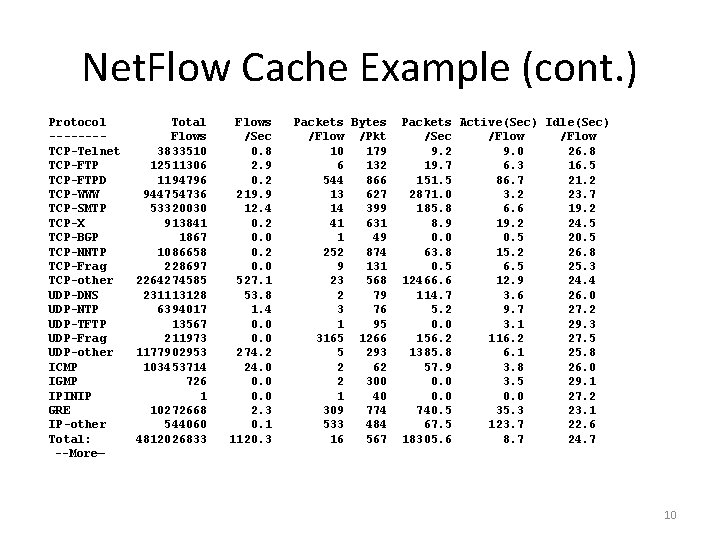
Net. Flow Cache Example #show ip cache flow IP packet size distribution (78630 M total packets): 1 -32 64 96 128 160 192 224 256 288 320 352 384 416 448 480. 002. 448. 062. 027. 013. 011. 008. 011. 003. 002. 006. 005. 003. 002 512 544 576 1024 1536 2048 2560 3072 3584 4096 4608. 002. 003. 015. 033. 331. 000 IP Flow Switching Cache, 6553988 bytes 32929 active, 32607 inactive, 524367786 added 4111490554 ager polls, 0 flow alloc failures Active flows timeout in 30 minutes Inactive flows timeout in 15 seconds IP Sub Flow Cache, 794824 bytes 32895 active, 16257 Inactive, 519171584 added, 519168554 added to flow 0 alloc failures, 12911870 force free 3 chunks, 1155 chunks added last clearing of statistics never --More— 9

Net. Flow Cache Example (cont. ) Protocol -------TCP-Telnet TCP-FTPD TCP-WWW TCP-SMTP TCP-X TCP-BGP TCP-NNTP TCP-Frag TCP-other UDP-DNS UDP-NTP UDP-TFTP UDP-Frag UDP-other ICMP IGMP IPINIP GRE IP-other Total: --More— Total Flows 3833510 12511306 1194796 944754736 53320030 913841 1867 1086658 228697 2264274585 231113128 6394017 13567 211973 1177902953 103453714 726 1 10272668 544060 4812026833 Flows /Sec 0. 8 2. 9 0. 2 219. 9 12. 4 0. 2 0. 0 527. 1 53. 8 1. 4 0. 0 274. 2 24. 0 0. 0 2. 3 0. 1 1120. 3 Packets Bytes /Flow /Pkt 10 179 6 132 544 866 13 627 14 399 41 631 1 49 252 874 9 131 23 568 2 79 3 76 1 95 3165 1266 5 293 2 62 2 300 1 40 309 774 533 484 16 567 Packets Active(Sec) Idle(Sec) /Sec /Flow 9. 2 9. 0 26. 8 19. 7 6. 3 16. 5 151. 5 86. 7 21. 2 2871. 0 3. 2 23. 7 185. 8 6. 6 19. 2 8. 9 19. 2 24. 5 0. 0 0. 5 20. 5 63. 8 15. 2 26. 8 0. 5 6. 5 25. 3 12466. 6 12. 9 24. 4 114. 7 3. 6 26. 0 5. 2 9. 7 27. 2 0. 0 3. 1 29. 3 156. 2 116. 2 27. 5 1385. 8 6. 1 25. 8 57. 9 3. 8 26. 0 0. 0 3. 5 29. 1 0. 0 27. 2 740. 5 35. 3 23. 1 67. 5 123. 7 22. 6 18305. 6 8. 7 24. 7 10

Net. Flow Limitations of Cache • • Difficult to read Only shows recent activity No automation on devices for analysis No accounting of flows (besides overall totals) 11

Net. Flow Export of Data • Greatly enhances Net. Flow and turns the technology into a analysis tool! • Data sent to external collector(s) • Analyzed by one or more systems • Archived for other concerns • Efficient: Uses multiple records per UDP packet 12

Net. Flow Export: Establish Policies! • Ensure policies are in place before deploying covering: – Retention of network usage statistics – Establish a retention policy. – Privacy protection of the data, who is authorized, no offloading without sanitizing personal data (the host portion) 13

Privacy • While the contents of the packet are not recorded, the calling information can still be a concern. • However, with virtual servers, it is impossible to know the true destination • Mostly it can only be used as verification that something occurred. 14

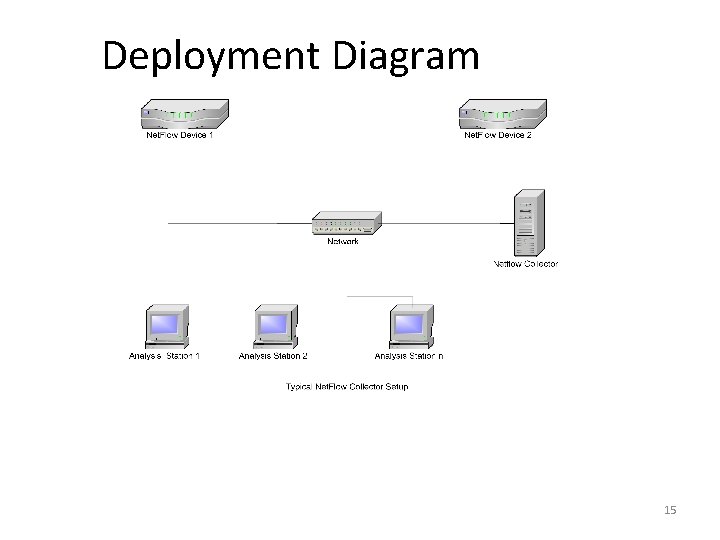
Deployment Diagram 15

Securing The Data Stream • Hmm, hold on there! • Using UDP, any Security in the transmission? – Nope! • Most deployments use a private, maintenance network that only admins can touch. 16

Introduction to flow-tools • Full featured Net. Flow tool set • Open-source software • Available from: http: //www. splintered. net/sw/flow-tools/ • Entire package compiles on most Linux, Free. BSD, etc. systems 17

Flow-tools Contains • • • flow-capture flow-cat flow-dscan flow-expire flow-export flow-fanout flow-filter flow-gen flow-header flow-import flow-mask • • • flow-merge flow-nfilter flow-print flow-receive flow-report flow-send flow-split flow-stat flow-tag flow-xlate 18

Single Source to Many Collectors flow-fanout • Inline replacement for flow-capture • Replicates a Net. Flow stream to multiple locations • Ideal for simultaneous: – Replicated storage – Multiple systems for near real time analysis 19

No Net. Flow? Use fprobe http: //sourceforge. net/projects/fprobe Open source Net. Flow probe Linux, Free. BSD, etc. Uses a SPAN port or network tap Consider libpcap-ring kernel or MMAPed pcap for high-speed collections (over 100 Mbits) • Can match CPU to traffic load • Downside: loss of interface on reports • • • 20

Portable Probe Build a couple of portable probes to have on hand for remote probes for network analysis. Install flow-tools, fprobe, tcpdump on a system with a large hard drive. When a problem occurs, you can deploy it on a SPAN port or with a hub or network TAP. 21

Traffic Analysis: Know Thy Network! • Net. Flow records the communication between systems • Quickly tells you what is happening on your network at a high level • Can be used to spot anomalies • Simple IDS capabilities • Locate all stations doing the same thing on the network • Policy enforcement 22

Knowing Where to Look • Deploy Net. Flow on devices at keys location – Border of network(s) – Core points • Deploy probes where needed – Specific problem areas – Network aggregation points without Net. Flow capabilities. 23

Planning/Policies Make for Success • Establish policies as to what traffic is allowed • Establish specific pathways or gateways for traffic like SMTP, IRC, HTTP, etc. • Any traffic not flowing through these gateways are your indicator for problems • Segregate servers and workstations with subnets. 24

Analysis: Finding the Needles • • • Which State? Which County? Which Field? Which haystack? What part of the haystack? How many needles? 25

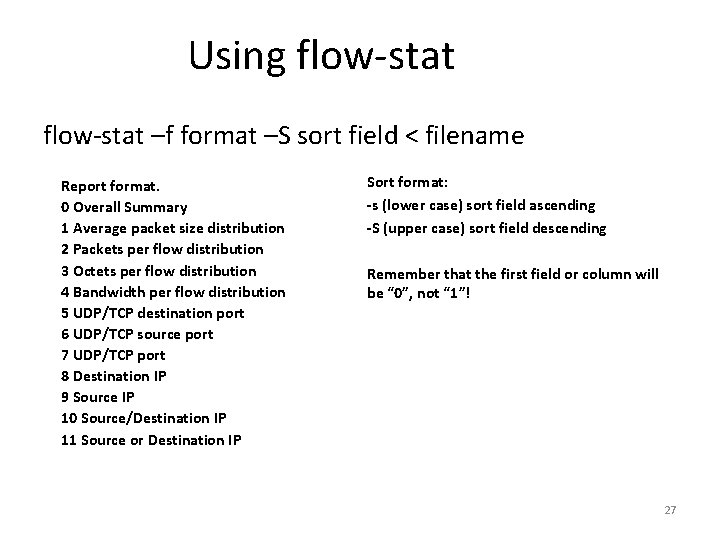
Finding the Needle(s): flow-stat • The flow-stat command provides quick statistics • Can provide reports on SRC/DST IP’s or ports, as well as others • Can sort by flows, octets or packets in ascending or descending order • Coupled with flow-nfilter removes known good traffic or look known problem traffic 26

Using flow-stat –f format –S sort field < filename Report format. 0 Overall Summary 1 Average packet size distribution 2 Packets per flow distribution 3 Octets per flow distribution 4 Bandwidth per flow distribution 5 UDP/TCP destination port 6 UDP/TCP source port 7 UDP/TCP port 8 Destination IP 9 Source IP 10 Source/Destination IP 11 Source or Destination IP Sort format: -s (lower case) sort field ascending -S (upper case) sort field descending Remember that the first field or column will be “ 0”, not “ 1”! 27

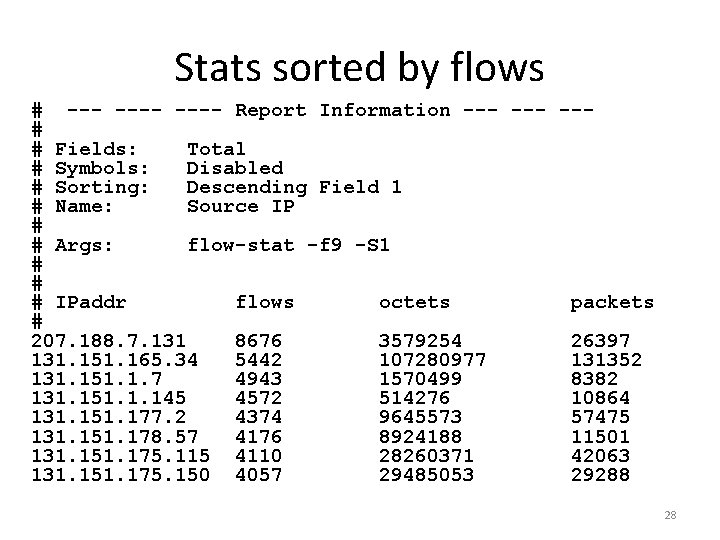
Stats sorted by flows # ---- Report Information --- --# # Fields: Total # Symbols: Disabled # Sorting: Descending Field 1 # Name: Source IP # # Args: flow-stat -f 9 -S 1 # # # IPaddr flows octets packets # 207. 188. 7. 131 8676 3579254 26397 131. 151. 165. 34 5442 107280977 131352 131. 151. 1. 7 4943 1570499 8382 131. 151. 1. 145 4572 514276 10864 131. 151. 177. 2 4374 9645573 57475 131. 151. 178. 57 4176 8924188 11501 131. 151. 175. 115 4110 28260371 42063 131. 151. 175. 150 4057 29485053 29288 28

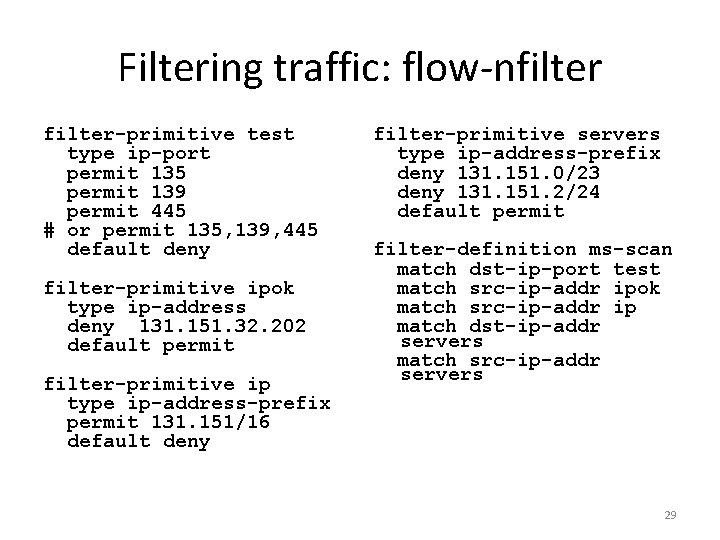
Filtering traffic: flow-nfilter-primitive test type ip-port permit 135 permit 139 permit 445 # or permit 135, 139, 445 default deny filter-primitive ipok type ip-address deny 131. 151. 32. 202 default permit filter-primitive ip type ip-address-prefix permit 131. 151/16 default deny filter-primitive servers type ip-address-prefix deny 131. 151. 0/23 deny 131. 151. 2/24 default permit filter-definition ms-scan match dst-ip-port test match src-ip-addr ipok match src-ip-addr ip match dst-ip-addr servers match src-ip-addr servers 29

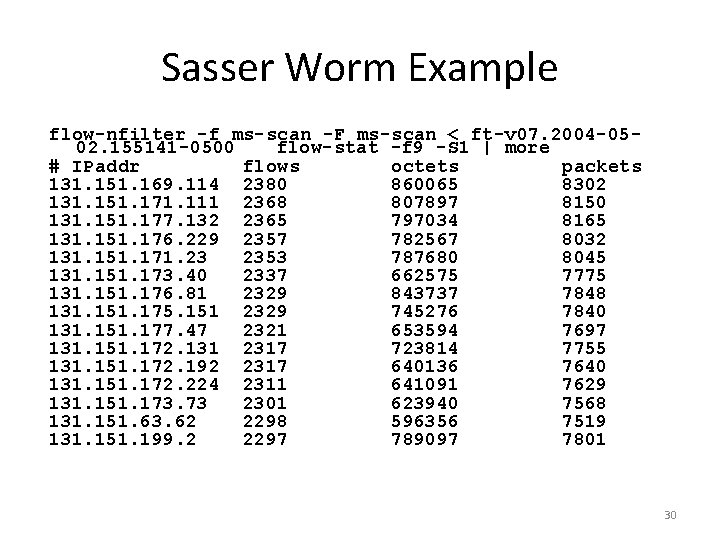
Sasser Worm Example flow-nfilter -f ms-scan -F ms-scan < ft-v 07. 2004 -0502. 155141 -0500 flow-stat -f 9 -S 1 | more # IPaddr flows octets packets 131. 151. 169. 114 2380 860065 8302 131. 151. 171. 111 2368 807897 8150 131. 151. 177. 132 2365 797034 8165 131. 151. 176. 229 2357 782567 8032 131. 151. 171. 23 2353 787680 8045 131. 151. 173. 40 2337 662575 7775 131. 151. 176. 81 2329 843737 7848 131. 151. 175. 151 2329 745276 7840 131. 151. 177. 47 2321 653594 7697 131. 151. 172. 131 2317 723814 7755 131. 151. 172. 192 2317 640136 7640 131. 151. 172. 224 2311 641091 7629 131. 151. 173. 73 2301 623940 7568 131. 151. 63. 62 2298 596356 7519 131. 151. 199. 2 2297 789097 7801 30

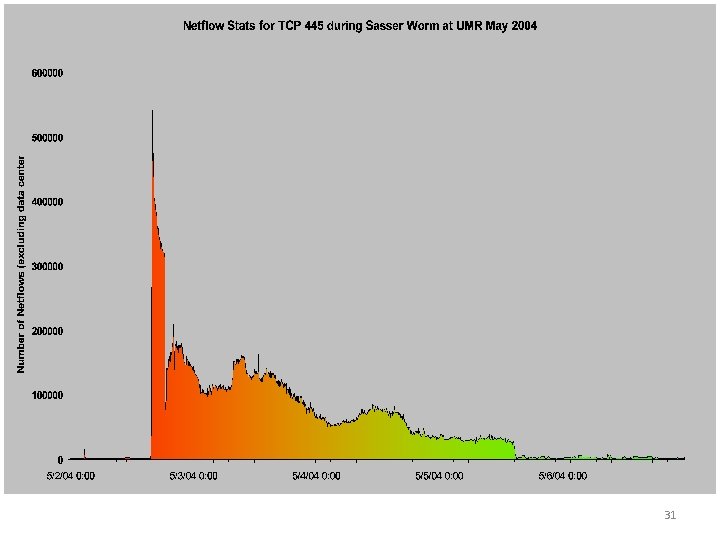
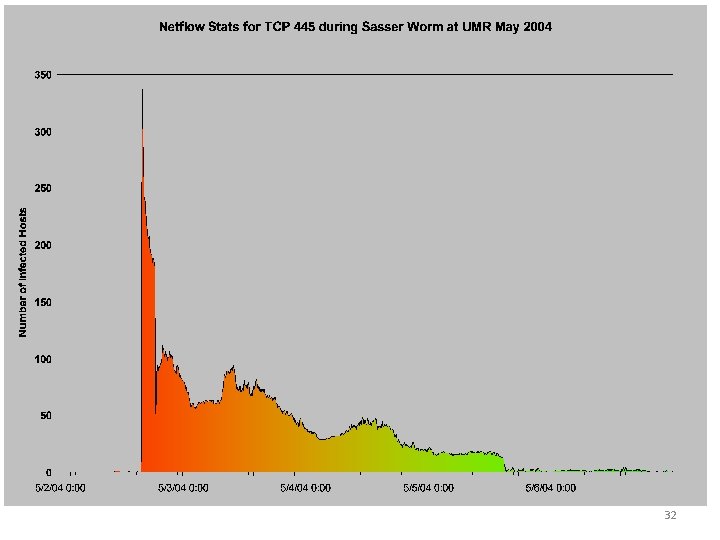
31

32

Profile of a Worm in Net. Flow • • Can use different protocols High flow count Low packet count – 3 packets or less per flow Use flow-stat or flow-report to spot them Downside: If the stations generate other traffic, it can obscure the worm activity 33

Flow File Size Can Tell a Story • Always keep an eye on the Net. Flow file sizes • Works best after a baseline of a few days or weeks of observation. • General fluctuations are normal traffic patterns, but a sudden surge indicates something new is going on. • Sudden drops could indicate network problems. 34

Pig in the Python -rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r-- 1 1 1 1 1 1 netflow netflow netflow netflow netflow netflow afsuser afsuser afsuser afsuser afsuser afsuser 2019685 2031767 2032419 2072933 2062822 2120842 7013906 11331622 15607255 15748046 14216272 12008287 9972353 8973700 9042363 8017690 8109288 7301829 7175834 7029650 7063063 May May May May May May 2 2 2 2 2 2 15: 21 15: 26 15: 31 15: 36 15: 41 15: 46 15: 51 15: 56 16: 01 16: 06 16: 11 16: 16 16: 21 16: 26 16: 31 16: 36 16: 41 16: 46 16: 51 16: 56 17: 01 ft-v 07. 2004 -10 -02. 151649 -0500 ft-v 07. 2004 -10 -02. 152148 -0500 ft-v 07. 2004 -10 -02. 152647 -0500 ft-v 07. 2004 -10 -02. 153145 -0500 ft-v 07. 2004 -10 -02. 153645 -0500 ft-v 07. 2004 -10 -02. 154144 -0500 ft-v 07. 2004 -10 -02. 154643 -0500 ft-v 07. 2004 -05 -02. 155141 -0500 ft-v 07. 2004 -05 -02. 155640 -0500 ft-v 07. 2004 -05 -02. 160139 -0500 ft-v 07. 2004 -05 -02. 160638 -0500 ft-v 07. 2004 -05 -02. 161137 -0500 ft-v 07. 2004 -05 -02. 161636 -0500 ft-v 07. 2004 -05 -02. 162135 -0500 ft-v 07. 2004 -05 -02. 162635 -0500 ft-v 07. 2004 -05 -02. 163133 -0500 ft-v 07. 2004 -05 -02. 163632 -0500 ft-v 07. 2004 -05 -02. 164131 -0500 ft-v 07. 2004 -05 -02. 164630 -0500 ft-v 07. 2004 -05 -02. 165129 -0500 ft-v 07. 2004 -05 -02. 165628 -0500 35

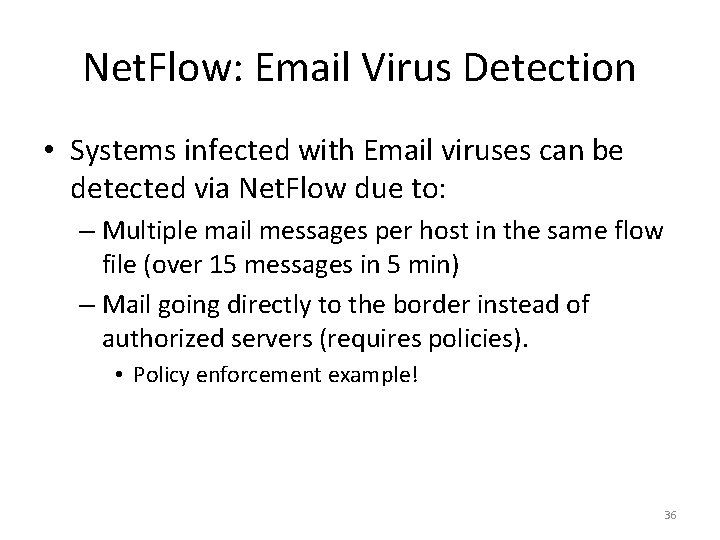
Net. Flow: Email Virus Detection • Systems infected with Email viruses can be detected via Net. Flow due to: – Multiple mail messages per host in the same flow file (over 15 messages in 5 min) – Mail going directly to the border instead of authorized servers (requires policies). • Policy enforcement example! 36

Typical Email Virus flow-cat ft-v 07. 2004 -11 -18. 190* | Femail | flow-print -f 3|more src. IP dst. IP packets 131. 151. 148. 26 64. 12. 138. 152 131. 151. 148. 26 64. 12. 138. 57 131. 151. 148. 26 64. 12. 138. 89 131. 151. 148. 26 64. 12. 137. 249 131. 151. 148. 26 67. 28. 113. 11 131. 151. 148. 26 67. 28. 114. 36 131. 151. 148. 26 64. 156. 215. 7 131. 151. 148. 26 206. 190. 36. 245 131. 151. 148. 26 66. 135. 195. 181 131. 151. 148. 26 66. 135. 195. 180 131. 151. 148. 26 195. 245. 231. 83 131. 151. 148. 26 195. 245. 230. 131. 151. 148. 26 207. 251. 96. 22 131. 151. 148. 26 65. 125. 54. 22 flow-nfilter -f ~/kfl/emailblocked prot src. Port dst. Port octets 6 6 6 6 6 1148 1150 1152 1154 1156 1158 1160 1162 1165 1167 1169 1171 1174 1176 1179 1181 1184 1186 1189 1191 25 25 25 25 25 144 144 144 144 144 3 3 3 3 3 37

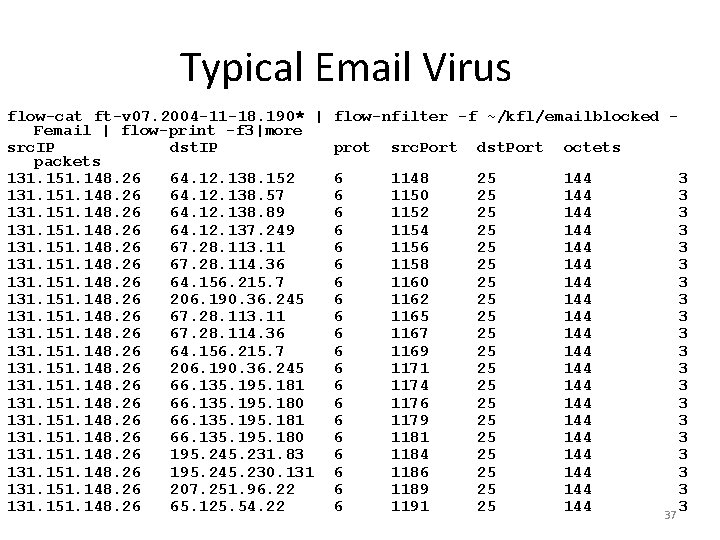
Email checks: Not all are bad flow-print –f 3 < last | grep 131. 151. 65. 124 | grep " 25 src. IP dst. IP prot src. Port dst. Port 131. 151. 65. 124 65. 54. 252. 230 6 3828 25 131. 151. 65. 124 65. 54. 252. 99 6 3842 25 131. 151. 65. 124 65. 54. 252. 230 6 3852 25 131. 151. 65. 124 64. 4. 50. 239 6 3867 25 131. 151. 65. 124 65. 54. 167. 230 6 3879 25 131. 151. 65. 124 65. 54. 252. 99 6 3897 25 131. 151. 65. 124 65. 54. 252. 230 6 3912 25 131. 151. 65. 124 64. 4. 50. 239 6 3922 25 131. 151. 65. 124 65. 54. 167. 230 6 3934 25 131. 151. 65. 124 65. 54. 252. 99 6 3943 25 131. 151. 65. 124 65. 54. 252. 230 6 3957 25 131. 151. 65. 124 64. 4. 50. 239 6 3972 25 131. 151. 65. 124 65. 54. 167. 230 6 4003 25 131. 151. 65. 124 65. 54. 252. 99 6 4018 25 131. 151. 65. 124 65. 54. 252. 230 6 4035 25 131. 151. 65. 124 64. 4. 50. 239 6 4053 25 131. 151. 65. 124 65. 54. 167. 230 6 4072 25 131. 151. 65. 124 65. 54. 252. 99 6 4091 25 131. 151. 65. 124 65. 54. 252. 230 6 4105 25 6 “ octets 96 96 96 96 96 packets 2 2 2 2 2 All destinations are Hotmail addresses: configuration issue 38

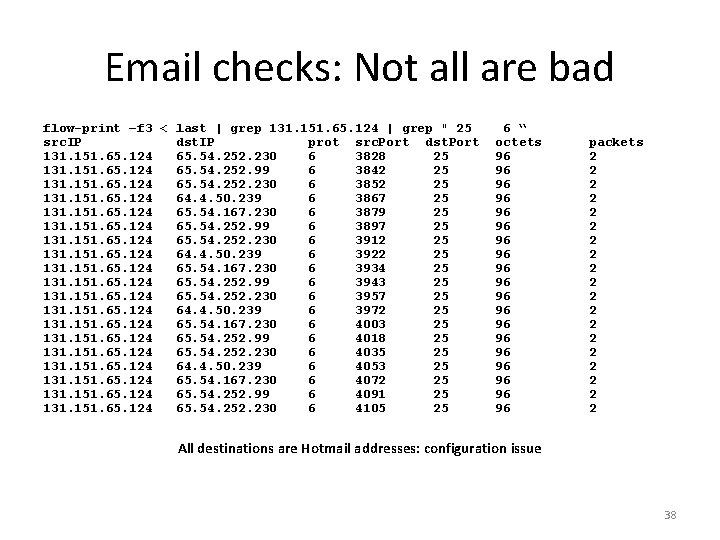
Controlled Mass Mailer flow-nfilter -f ~/kfl/emailblocked -F email < ft-v 07. 2004 -11 -17. 220025 -0600 | flow-print -f 3 src. IP dst. IP prot src. Port dst. Port octets packets 131. 151. 173. 197 64. 48. 9. 3 6 3281 25 144 3 131. 151. 173. 197 32. 97. 166. 40 6 3282 25 144 3 131. 151. 173. 197 216. 200. 145. 10 6 3283 25 144 3 131. 151. 173. 197 208. 36. 123. 68 6 3284 25 144 3 131. 151. 173. 197 66. 126. 156. 4 6 3285 25 144 3 131. 151. 173. 197 61. 9. 0. 109 6 3286 25 144 3 131. 151. 173. 197 211. 233. 37. 232 6 3287 25 144 3 131. 151. 173. 197 200. 217. 215. 90 6 3288 25 144 3 131. 151. 173. 197 216. 213. 21. 13 6 3289 25 144 3 131. 151. 173. 197 202. 138. 96. 6 6 3290 25 144 3 131. 151. 173. 197 207. 55. 105. 2 6 3291 25 144 3 131. 151. 173. 197 216. 86. 113. 228 6 3292 25 144 3 131. 151. 173. 197 194. 158. 37. 140 6 3293 25 144 3 131. 151. 173. 197 209. 242. 224. 42 6 3294 25 144 3 131. 151. 173. 197 67. 65. 226. 82 6 3295 25 144 3 131. 151. 173. 197 64. 18. 4. 10 6 3296 25 144 3 131. 151. 173. 197 64. 27. 95. 41 6 3297 25 144 3 131. 151. 173. 197 67. 28. 113. 13 6 3298 25 144 3 131. 151. 173. 197 65. 54. 190. 179 6 3299 25 144 3 131. 151. 173. 197 195. 7. 224. 41 6 3300 25 144 3 131. 151. 173. 197 64. 18. 4. 10 6 3301 25 144 3 131. 151. 173. 197 195. 238. 3. 129 6 3302 25 144 3 39

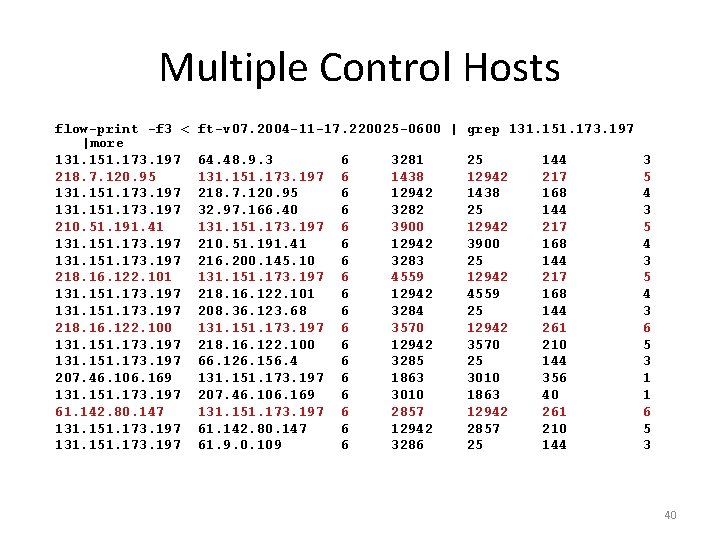
Multiple Control Hosts flow-print -f 3 < |more 131. 151. 173. 197 218. 7. 120. 95 131. 151. 173. 197 210. 51. 191. 41 131. 151. 173. 197 218. 16. 122. 100 131. 151. 173. 197 207. 46. 106. 169 131. 151. 173. 197 61. 142. 80. 147 131. 151. 173. 197 ft-v 07. 2004 -11 -17. 220025 -0600 | grep 131. 151. 173. 197 64. 48. 9. 3 131. 151. 173. 197 218. 7. 120. 95 32. 97. 166. 40 131. 151. 173. 197 210. 51. 191. 41 216. 200. 145. 10 131. 151. 173. 197 218. 16. 122. 101 208. 36. 123. 68 131. 151. 173. 197 218. 16. 122. 100 66. 126. 156. 4 131. 151. 173. 197 207. 46. 106. 169 131. 151. 173. 197 61. 142. 80. 147 61. 9. 0. 109 6 6 6 6 6 3281 1438 12942 3282 3900 12942 3283 4559 12942 3284 3570 12942 3285 1863 3010 2857 12942 3286 25 12942 1438 25 12942 3900 25 12942 4559 25 12942 3570 25 3010 1863 12942 2857 25 144 217 168 144 261 210 144 356 40 261 210 144 3 5 4 3 6 5 3 1 1 6 5 3 40

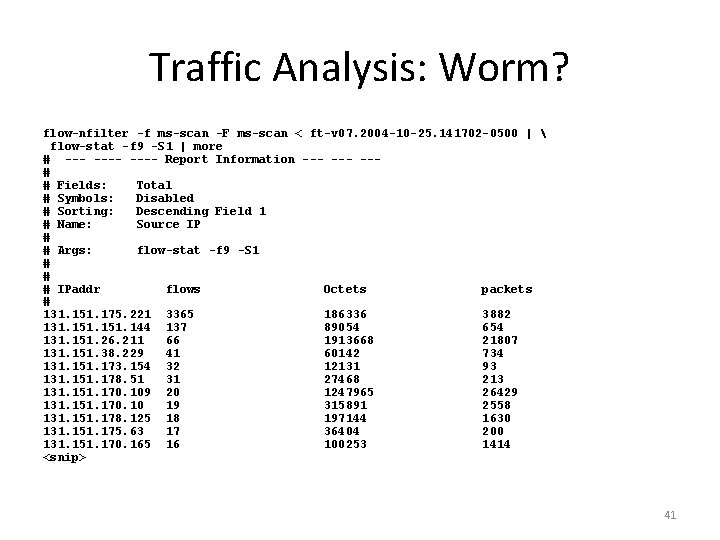
Traffic Analysis: Worm? flow-nfilter -f ms-scan -F ms-scan < ft-v 07. 2004 -10 -25. 141702 -0500 | flow-stat -f 9 -S 1 | more # ---- Report Information --- --# # Fields: Total # Symbols: Disabled # Sorting: Descending Field 1 # Name: Source IP # # Args: flow-stat -f 9 -S 1 # # # IPaddr flows Octets packets # 131. 151. 175. 221 3365 186336 3882 131. 151. 144 137 89054 654 131. 151. 26. 211 66 1913668 21807 131. 151. 38. 229 41 60142 734 131. 151. 173. 154 32 12131 93 131. 151. 178. 51 31 27468 213 131. 151. 170. 109 20 1247965 26429 131. 151. 170. 10 19 315891 2558 131. 151. 178. 125 18 197144 1630 131. 151. 175. 63 17 36404 200 131. 151. 170. 165 16 100253 1414 <snip> 41

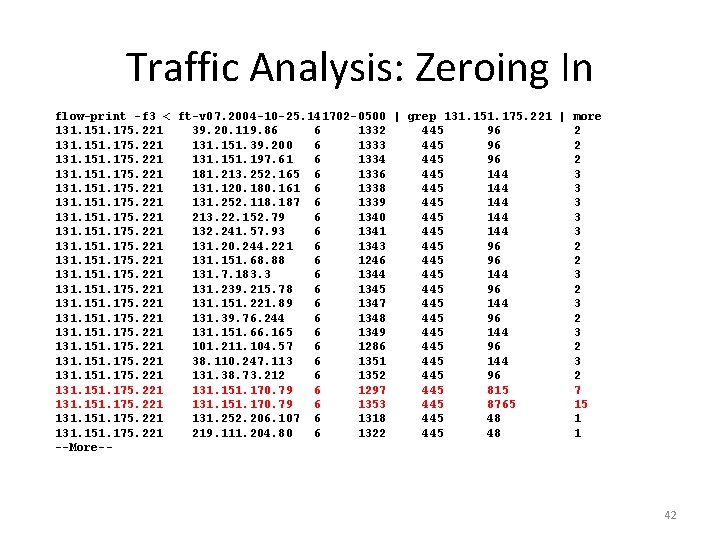
Traffic Analysis: Zeroing In flow-print -f 3 < ft-v 07. 2004 -10 -25. 141702 -0500 | grep 131. 151. 175. 221 | more 131. 151. 175. 221 39. 20. 119. 86 6 1332 445 96 2 131. 151. 175. 221 131. 151. 39. 200 6 1333 445 96 2 131. 151. 175. 221 131. 151. 197. 61 6 1334 445 96 2 131. 151. 175. 221 181. 213. 252. 165 6 1336 445 144 3 131. 151. 175. 221 131. 120. 180. 161 6 1338 445 144 3 131. 151. 175. 221 131. 252. 118. 187 6 1339 445 144 3 131. 151. 175. 221 213. 22. 152. 79 6 1340 445 144 3 131. 151. 175. 221 132. 241. 57. 93 6 1341 445 144 3 131. 151. 175. 221 131. 20. 244. 221 6 1343 445 96 2 131. 151. 175. 221 131. 151. 68. 88 6 1246 445 96 2 131. 151. 175. 221 131. 7. 183. 3 6 1344 445 144 3 131. 151. 175. 221 131. 239. 215. 78 6 1345 445 96 2 131. 151. 175. 221 131. 151. 221. 89 6 1347 445 144 3 131. 151. 175. 221 131. 39. 76. 244 6 1348 445 96 2 131. 151. 175. 221 131. 151. 66. 165 6 1349 445 144 3 131. 151. 175. 221 101. 211. 104. 57 6 1286 445 96 2 131. 151. 175. 221 38. 110. 247. 113 6 1351 445 144 3 131. 151. 175. 221 131. 38. 73. 212 6 1352 445 96 2 131. 151. 175. 221 131. 151. 170. 79 6 1297 445 815 7 131. 151. 175. 221 131. 151. 170. 79 6 1353 445 8765 15 131. 151. 175. 221 131. 252. 206. 107 6 1318 445 48 1 131. 151. 175. 221 219. 111. 204. 80 6 1322 445 48 1 --More-- 42

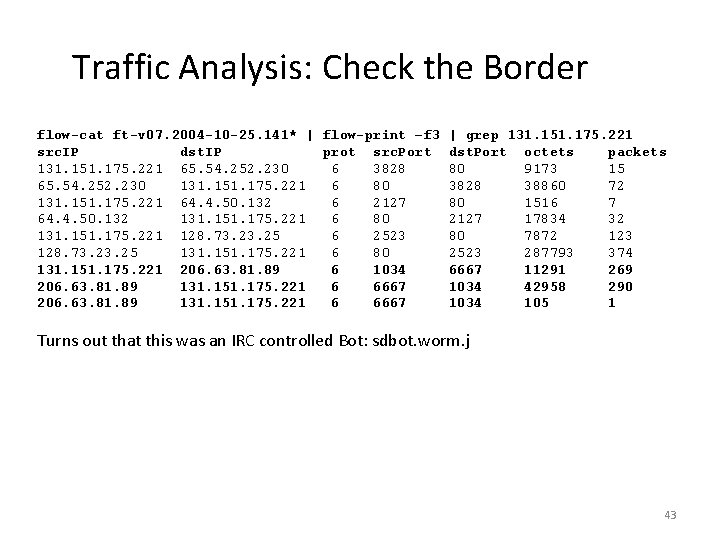
Traffic Analysis: Check the Border flow-cat ft-v 07. 2004 -10 -25. 141* | flow-print –f 3 src. IP dst. IP prot src. Port 131. 151. 175. 221 65. 54. 252. 230 6 3828 65. 54. 252. 230 131. 151. 175. 221 6 80 131. 151. 175. 221 64. 4. 50. 132 6 2127 64. 4. 50. 132 131. 151. 175. 221 6 80 131. 151. 175. 221 128. 73. 25 6 2523 128. 73. 25 131. 151. 175. 221 6 80 131. 151. 175. 221 206. 63. 81. 89 6 1034 206. 63. 81. 89 131. 151. 175. 221 6 6667 | grep 131. 151. 175. 221 dst. Port octets packets 80 9173 15 3828 38860 72 80 1516 7 2127 17834 32 80 7872 123 2523 287793 374 6667 11291 269 1034 42958 290 1034 105 1 Turns out that this was an IRC controlled Bot: sdbot. worm. j 43

Situation: IFRAME Exploit • System suddenly generated a virus warning after visiting a well known, trusted website. • System scan removed the known virus and downloader, but an undetectable trojan was downloaded during the event. • Trojan NOT detectable after virus definition update and full system scan. • System now displays ads and runs very slow • Analysis of system required. Noted traffic involving Netherlands IP address. 44

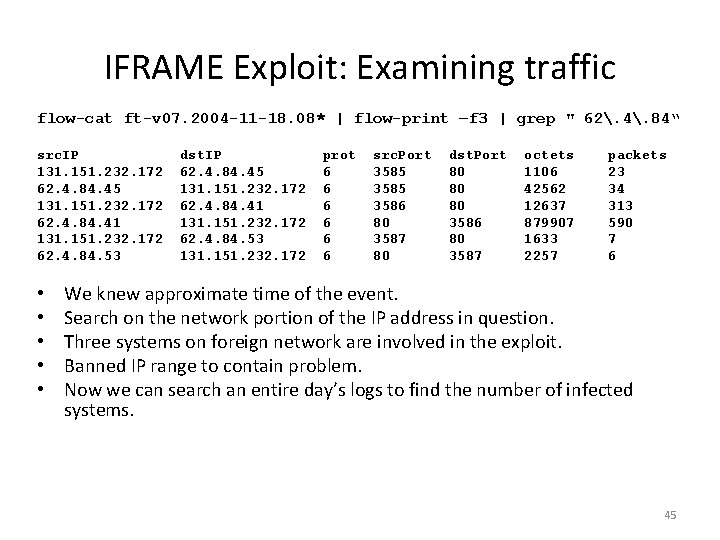
IFRAME Exploit: Examining traffic flow-cat ft-v 07. 2004 -11 -18. 08* | flow-print –f 3 | grep " 62. 4. 84“ src. IP 131. 151. 232. 172 62. 4. 84. 45 131. 151. 232. 172 62. 4. 84. 41 131. 151. 232. 172 62. 4. 84. 53 • • • dst. IP 62. 4. 84. 45 131. 151. 232. 172 62. 4. 84. 41 131. 151. 232. 172 62. 4. 84. 53 131. 151. 232. 172 prot 6 6 6 src. Port 3585 3586 80 3587 80 dst. Port 80 80 80 3586 80 3587 octets 1106 42562 12637 879907 1633 2257 packets 23 34 313 590 7 6 We knew approximate time of the event. Search on the network portion of the IP address in question. Three systems on foreign network are involved in the exploit. Banned IP range to contain problem. Now we can search an entire day’s logs to find the number of infected systems. 45

Create “iframe” Filter filter-primitive test-address type ip-address permit 62. 4. 84. 41 permit 62. 4. 84. 45 permit 62. 4. 84. 53 default deny filter-primitive test-protocol type ip-protocol permit tcp filter-definition iframe match dst-ip-addr test-address match ip-protocol test-protocol 46

Run iframe Filter flow-cat f* | flow-nfilter -f iframe -F iframe | flow-print -f 3 > ~/out Then run this output through awk, sort and grep: awk '{print $1}' ~/out | sort –u | grep 131. 151. 177. 161 131. 151. 178. 45 131. 151. 174. 18 131. 151. 176. 14 131. 151. 177. 44 131. 151. 176. 38 131. 151. 170. 80 131. 151. 174. 10 131. 151. 174. 40 131. 151. 178. 128 131. 151. 169. 181 131. 151. 170. 87 131. 151. 18. 149 131. 151. 18. 8 <snip> 47

Spot Who is Using Services • Netflow is very useful for determining – Who is using various services – Impact on closing down ports – Location of servers 48

Other Types of Detection • Spyware • Verify claims on traffic from your network – DMCA reports – Attacks reports – Scanning reports – Email – spoofed or real • Can aid with determining access controls and Firewall rules – null interface for dropped traffic 49

Other Links • Cisco: http: //www. cisco. com • flow-tools home: http: //www. splintered. net/sw/flow-tools/ • Great selection of links for various Net. Flow tools: http: //www. switch. ch/tf-tant/floma/software. html • Fprobe source: http: //sourceforge. net/projects/fprobe • Libcap-ring, nprobe, ntop: http: //www. ntop. org • Well known IP ports (very good reference for analysis) : http: //www. iana. org/assignments/port-numbers If you ever have any questions of any sort, please email me at kfl@mst. edu. 50