Net Defend UTM Firewall DFL870 Agenda Security Trend




- Slides: 23

Net. Defend UTM Firewall DFL-870

Agenda • • Security Trend on Firewall Product Introduction Functionality and Technology Deployment Scenario

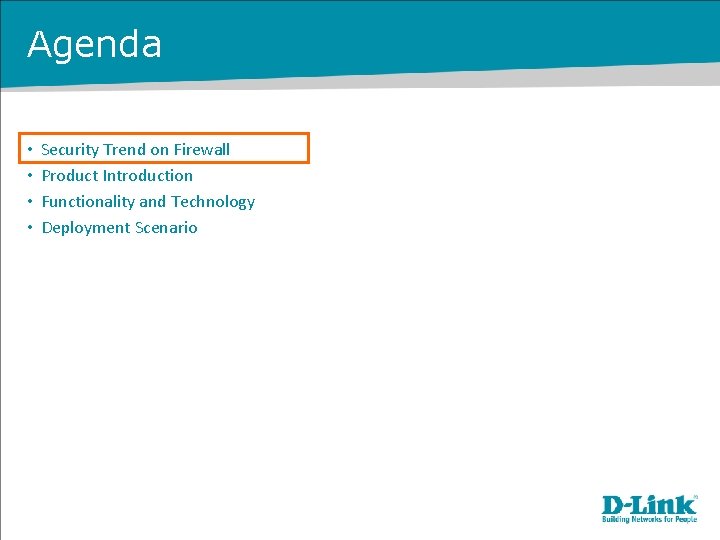
Security Trend on Firewall • Traditional Multiple Point Solutions in Network ISP 1 Load Balancing IPS/IDP Appliance Firewall/VPN Anti-Virus ISP 2 Anti-Spam Web URL filtering Disadvantage § Complex network architecture. § Multiple vendors & appliances. § Higher appliance operation and maintenance cost. § Increases management effort. Switch Users Server Farm

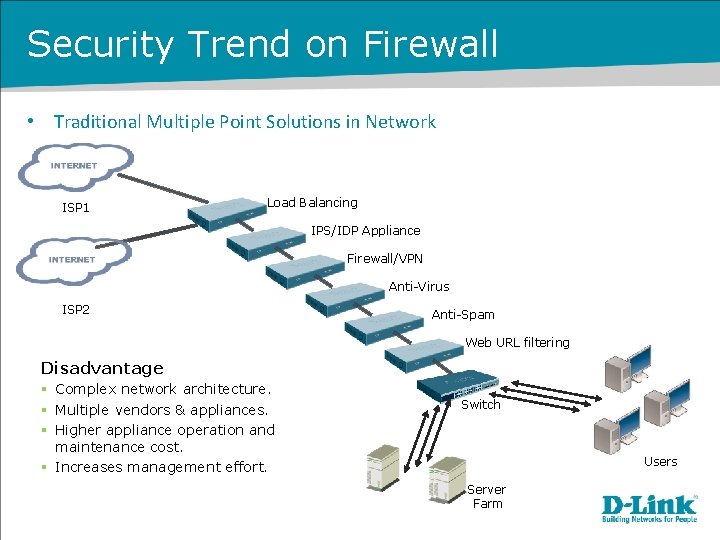
Security Trend on Firewall • Net. Defend Multi-Layered Security Solutions in Network ISP 1 Multi-Layered Security ISP 2 Load Balancing Traffic Shaping IPS/IDP Anti-Virus Web Content Filtering Anti-Spam Firewall IPSec/PPTP/L 2 TP Network/Content Processing Advantage § Provide comprehensive security approach. § Minimizes down time from individual threats. § Reduces number of vendors and appliances. § Simplifies security management. § Improves detection capabilities. UTM Firewall Switch Users Server Farm

Agenda • • Security Trend on Firewall Product Introduction Functionality and Technology Deployment Scenario

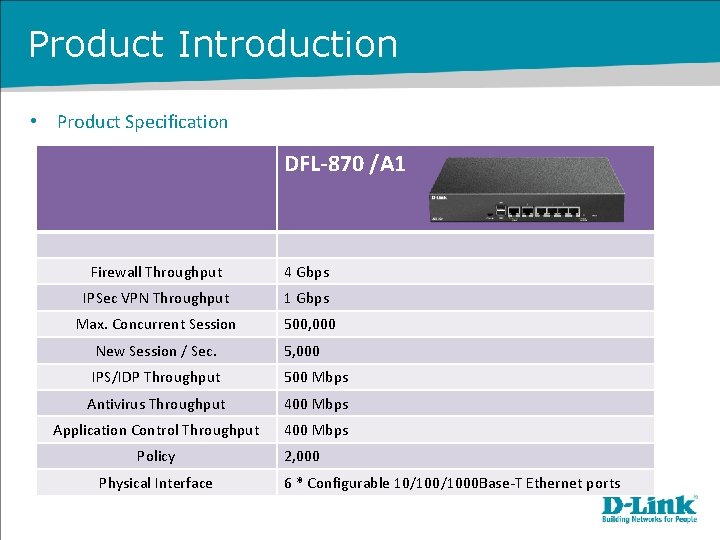
Product Introduction • Product Specification DFL-870 /A 1 Firewall Throughput 4 Gbps IPSec VPN Throughput 1 Gbps Max. Concurrent Session 500, 000 New Session / Sec. 5, 000 IPS/IDP Throughput 500 Mbps Antivirus Throughput 400 Mbps Application Control Throughput 400 Mbps Policy Physical Interface 2, 000 6 * Configurable 10/1000 Base-T Ethernet ports

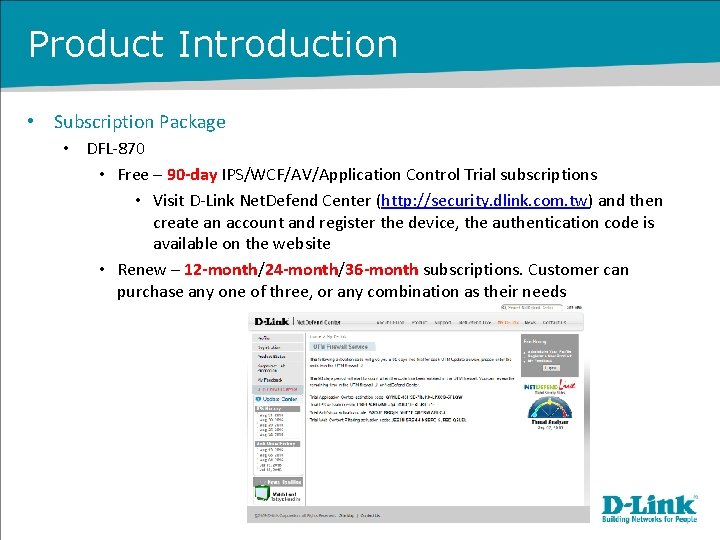
Product Introduction • Subscription Package • DFL-870 • Free – 90 -day IPS/WCF/AV/Application Control Trial subscriptions • Visit D-Link Net. Defend Center (http: //security. dlink. com. tw) and then create an account and register the device, the authentication code is available on the website • Renew – 12 -month/24 -month/36 -month subscriptions. Customer can purchase any one of three, or any combination as their needs

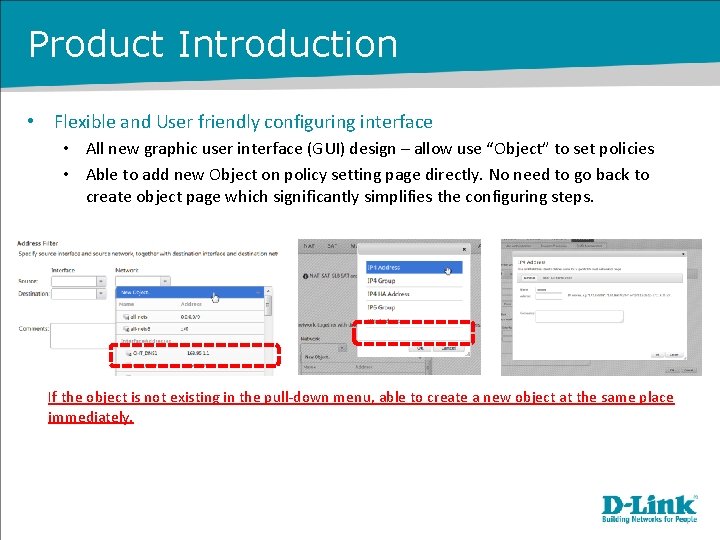
Product Introduction • Flexible and User friendly configuring interface • All new graphic user interface (GUI) design – allow use “Object” to set policies • Able to add new Object on policy setting page directly. No need to go back to create object page which significantly simplifies the configuring steps. If the object is not existing in the pull-down menu, able to create a new object at the same place immediately.

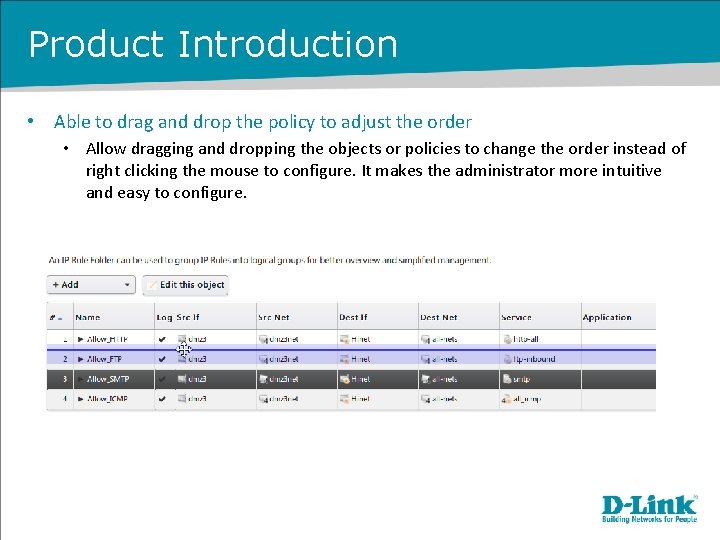
Product Introduction • Able to drag and drop the policy to adjust the order • Allow dragging and dropping the objects or policies to change the order instead of right clicking the mouse to configure. It makes the administrator more intuitive and easy to configure.

Agenda • • Security Trend on Firewall Product Introduction Functionality and Technology Deployment Scenario

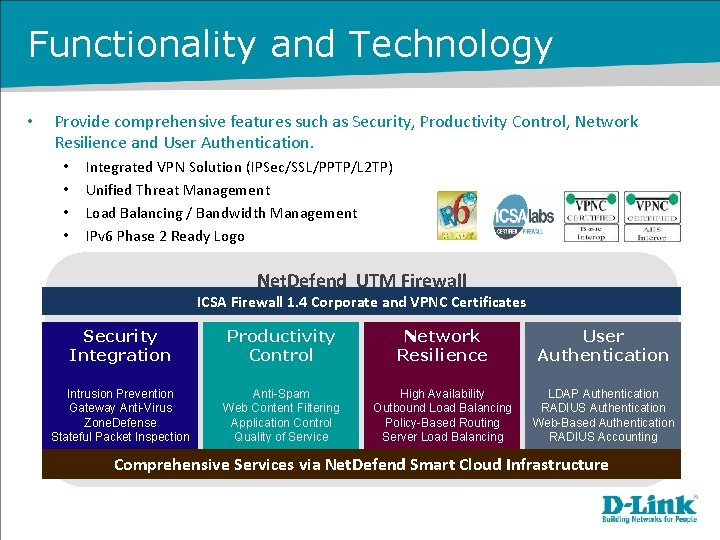
Functionality and Technology • Provide comprehensive features such as Security, Productivity Control, Network Resilience and User Authentication. • • Integrated VPN Solution (IPSec/SSL/PPTP/L 2 TP) Unified Threat Management Load Balancing / Bandwidth Management IPv 6 Phase 2 Ready Logo Net. Defend UTM Firewall ICSA Firewall 1. 4 Corporate and VPNC Certificates Security Integration Productivity Control Network Resilience User Authentication Intrusion Prevention Gateway Anti-Virus Zone. Defense Stateful Packet Inspection Anti-Spam Web Content Filtering Application Control Quality of Service High Availability Outbound Load Balancing Policy-Based Routing Server Load Balancing LDAP Authentication RADIUS Authentication Web-Based Authentication RADIUS Accounting Comprehensive Services via Net. Defend Smart Cloud Infrastructure

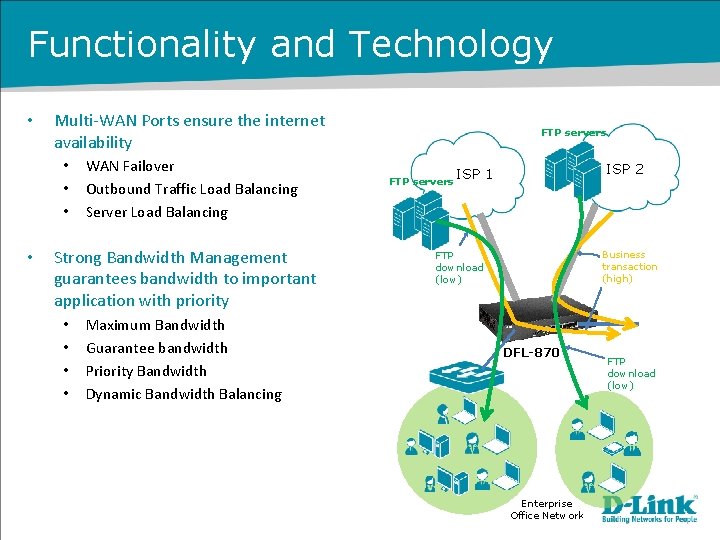
Functionality and Technology • Multi-WAN Ports ensure the internet availability • • WAN Failover Outbound Traffic Load Balancing Server Load Balancing Strong Bandwidth Management guarantees bandwidth to important application with priority • • Maximum Bandwidth Guarantee bandwidth Priority Bandwidth Dynamic Bandwidth Balancing FTP servers ISP 2 ISP 1 Business transaction (high) FTP download (low) DFL-870 Enterprise Office Network FTP download (low)

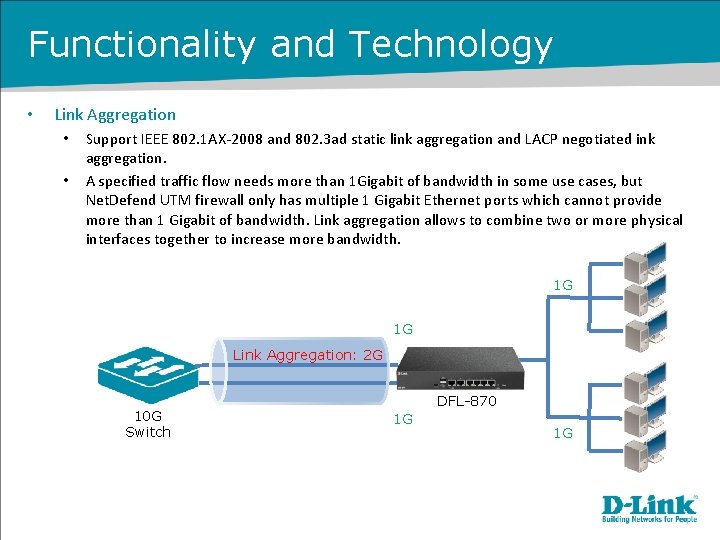
Functionality and Technology • Link Aggregation • • Support IEEE 802. 1 AX-2008 and 802. 3 ad static link aggregation and LACP negotiated ink aggregation. A specified traffic flow needs more than 1 Gigabit of bandwidth in some use cases, but Net. Defend UTM firewall only has multiple 1 Gigabit Ethernet ports which cannot provide more than 1 Gigabit of bandwidth. Link aggregation allows to combine two or more physical interfaces together to increase more bandwidth. 1 G 1 G Link Aggregation: 2 G 10 G Switch DFL-870 1 G 1 G

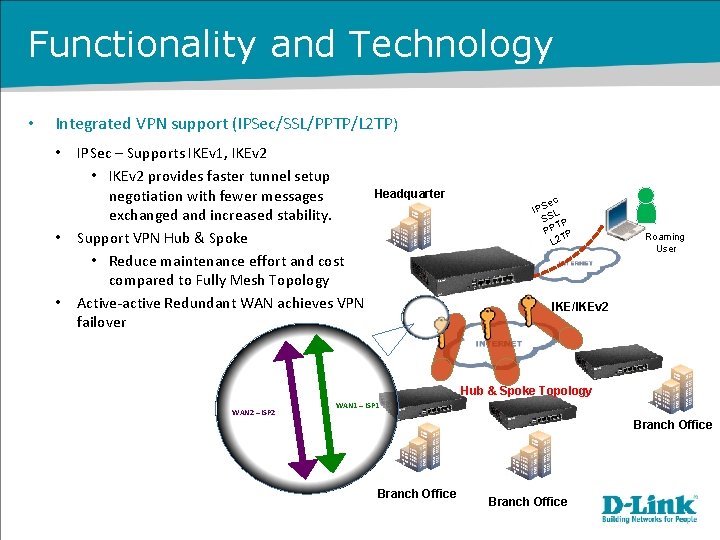
Functionality and Technology • Integrated VPN support (IPSec/SSL/PPTP/L 2 TP) • • • IPSec – Supports IKEv 1, IKEv 2 • IKEv 2 provides faster tunnel setup negotiation with fewer messages exchanged and increased stability. Support VPN Hub & Spoke • Reduce maintenance effort and cost compared to Fully Mesh Topology Active-active Redundant WAN achieves VPN failover Headquarter ec IPS L SS P T PP P T 2 L Roaming User IKE/IKEv 2 Hub & Spoke Topology WAN 2 – ISP 2 WAN 1 – ISP 1 Branch Office

Functionality and Technology • Intrusion Prevention System / Intrusion Detection and Prevention System, IPS/IDP • • • Supports Routing mode & Transparent mode In-Depth inspection from Layer 2 to Layer 7 Unique Signature Set – Powered by Recognizes and protects against all varieties of known and unknown attacks based on signature and behavior Automatic update of IPS signatures Advanced Protection Mechanisms • Protocol Anomaly – Catches unknown attacks • Re-Assembly – Catches fragmented attacks • Backdoor detection mechanisms • Insertion / Evasion Protection

Functionality and Technology • Anti-Virus Highlight • • Powered by Extremely high performance in combination with Stream-Based virus scanning technology. Supported Protocol: HTTP, FTP, SMTP, POP 3 and IMAP Supports Anti-virus over VPN tunnel Support to scan not only ZIP file but also 10 levels of ZIP-in-ZIP file Scanning of all MIME types including i. Phone applications (. ipa file) Zone. Defense Feature triggered by Anti-Virus Signature Database Support block page when virus is found in files

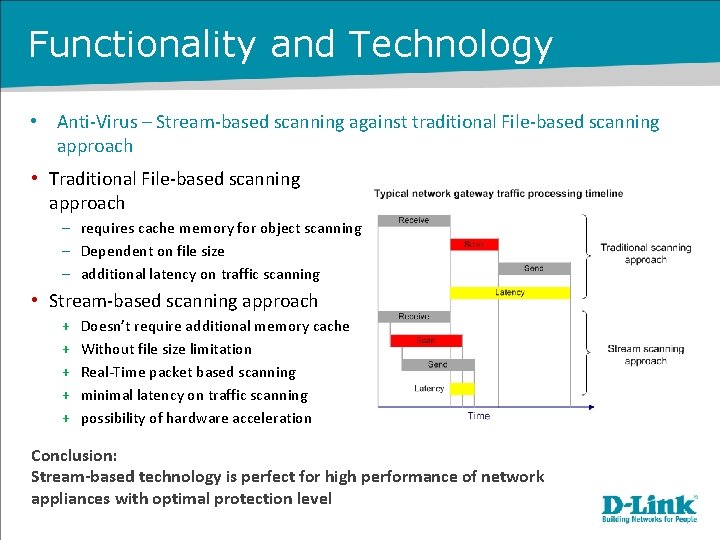
Functionality and Technology • Anti-Virus – Stream-based scanning against traditional File-based scanning approach • Traditional File-based scanning approach – requires cache memory for object scanning – Dependent on file size – additional latency on traffic scanning • Stream-based scanning approach + + + Doesn’t require additional memory cache Without file size limitation Real-Time packet based scanning minimal latency on traffic scanning possibility of hardware acceleration Conclusion: Stream-based technology is perfect for high performance of network appliances with optimal protection level

Functionality and Technology • Web Content Filtering D-Link’s Web Content Filtering Service provides various mechanisms for ensuring organizations infrastructure being used in an appropriated way. Before every web access established, Net. Defend firewall verifies website contents by matching database of the dynamic Web Service Cloud. D-Link’s Web Content Filtering service features include: Active Content Filtering • Object Removal • Active X • Flash • Java Applets • Jscript/VBStript • Cookies • Invalid UTF-8 Characters Static Content Filtering • Blacklists/Whitelists • Use of wildcards Dynamic Content Filtering • Managed Service • Per Device Service Licensing • Internal URL Cashe • Audit/ Blocking Mode • Override Options • Re-Categorization Options • Customizable Block Pages • Hourly Database Update • 31 Content Categories • Block Access to peer-to-peer (P 2 P), Phishing and Spyware Sites

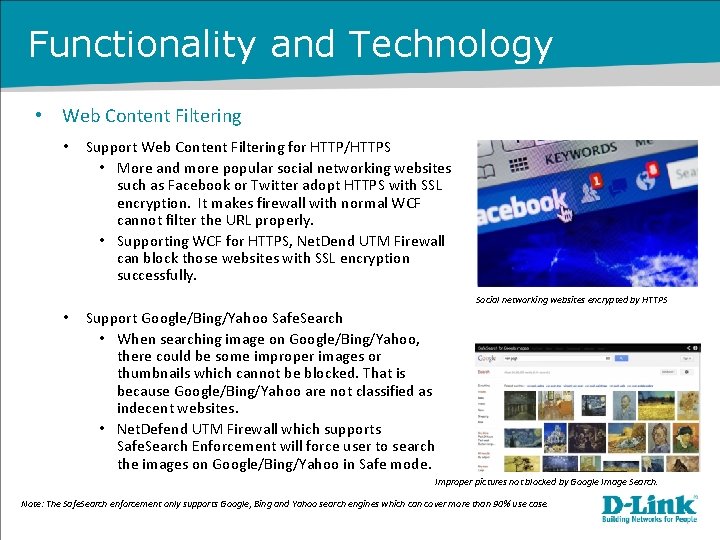
Functionality and Technology • Web Content Filtering • Support Web Content Filtering for HTTP/HTTPS • More and more popular social networking websites such as Facebook or Twitter adopt HTTPS with SSL encryption. It makes firewall with normal WCF cannot filter the URL properly. • Supporting WCF for HTTPS, Net. Dend UTM Firewall can block those websites with SSL encryption successfully. Social networking websites encrypted by HTTPS • Support Google/Bing/Yahoo Safe. Search • When searching image on Google/Bing/Yahoo, there could be some improper images or thumbnails which cannot be blocked. That is because Google/Bing/Yahoo are not classified as indecent websites. • Net. Defend UTM Firewall which supports Safe. Search Enforcement will force user to search the images on Google/Bing/Yahoo in Safe mode. Improper pictures not blocked by Google Image Search. Note: The Safe. Search enforcement only supports Google, Bing and Yahoo search engines which can cover more than 90% use case.

Functionality and Technology • Application Control • • • The feature provides to control the application used behind the UTM firewall. The administrator is able to select which application is allowed and monitor the data transfer. Able to set granular policies to control the content of the data stream with application attributes, such as restricting certain usage of the application, blocking DNS queries for certain domains or blocking mail transfer with certain keywords in the subject field. D-Link Net. Defend UTM Firewall’s Application Control can filter all traffic on layer 1 to layer 7 with inspecting the protocols. More than 1, 000 applications and protocols can be recognized. Furthermore, the application uses HTTPS protocol can be bandwidth managed, blocked or logged as well. Application Recognizable & manageable behavior attributes Social Networking (Facebook, Twitter etc. ) IM (LINE, Yahoo, Skype, QQ etc. ) P 2 P (Bit. Torrent, Winny etc. ) Web APPs (You. Tube, Flickr, Drop. Box etc. ) User login, Application URL/activity, posting activity, search engine queries, Chat, Video Stream, File attachments Email and Webmail (Gmail, QQ Mail, Ymail etc. ) Sender, Receiver, Login, Subject, Message, Attachments, date and time Business Applications (CRM, ERP, Citrix, MS Exchange etc. ) User Login, data transfer sessions (content, type and time), login/logoff date and time Signature powered by

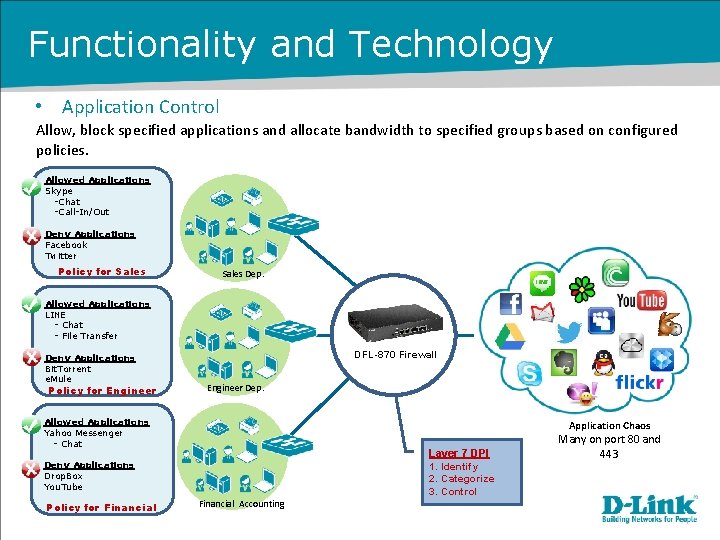
Functionality and Technology • Application Control Allow, block specified applications and allocate bandwidth to specified groups based on configured policies. Allowed Applications Skype -Chat -Call-In/Out Deny Applications Facebook Twitter Policy for Sales Dep. Allowed Applications LINE - Chat - File Transfer Deny Applications Bit. Torrent e. Mule Policy for Engineer DFL-870 Firewall Engineer Dep. Allowed Applications Yahoo Messenger - Chat Application Chaos Layer 7 DPI 1. Identify 2. Categorize 3. Control Deny Applications Drop. Box You. Tube Policy for Financial Accounting Many on port 80 and 443

Agenda • • Security Trend on Firewall Product Introduction Functionality and Technology Deployment Scenario

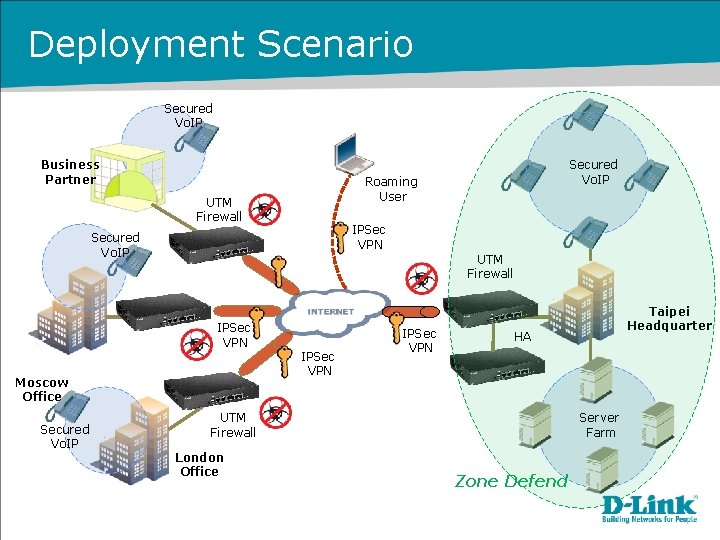
Deployment Scenario Secured Vo. IP Business Partner Roaming User UTM Firewall IPSec VPN Secured Vo. IP UTM Firewall IPSec VPN Moscow Office Secured Vo. IP IPSec VPN HA UTM Firewall London Office Taipei Headquarter Server Farm Zone Defend