James Ziegler Martin Nelson United States Naval Academy




























- Slides: 32

James Ziegler Martin Nelson United States Naval Academy 1 UNCLASSIFIED

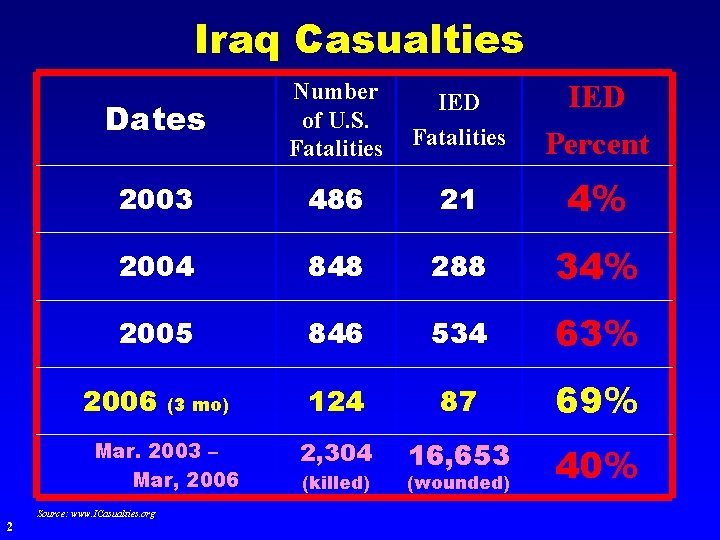
Iraq Casualties Dates Number of U. S. Fatalities IED Percent 2003 486 21 4% 2004 848 288 34% 2005 846 534 63% 124 87 69% 2, 304 16, 653 40% 2006 (3 mo) Mar. 2003 – Mar, 2006 Source: www. ICasualties. org 2 (killed) (wounded)

• Problem occurred because terrorists are using a new technology that had not been foreseen. • Previous terrorist bombs detonated using timing devices. Difficult to use against defended targets, and could not be used against mobile targets. • Widespread availability of commercial RF switches (car fobs, cell phone, etc. ) allowed precise timing without exposing terrorist to counter-attack. 3

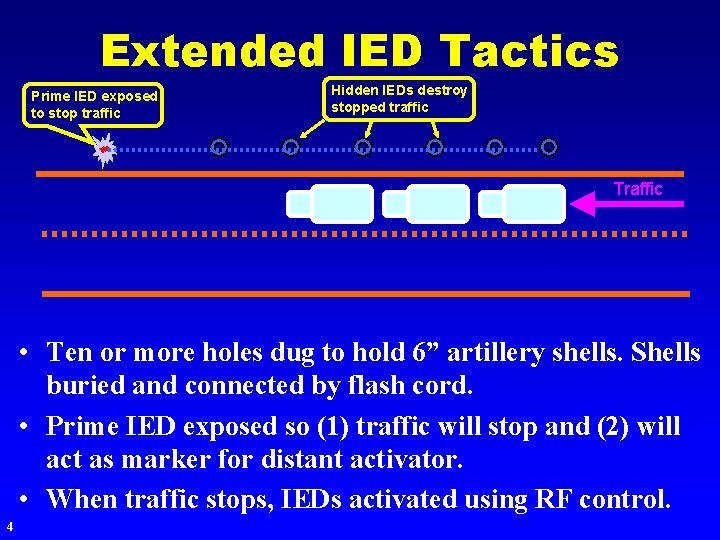
Extended IED Tactics Prime IED exposed to stop traffic Hidden IEDs destroy stopped traffic Traffic • Ten or more holes dug to hold 6” artillery shells. Shells buried and connected by flash cord. • Prime IED exposed so (1) traffic will stop and (2) will act as marker for distant activator. • When traffic stops, IEDs activated using RF control. 4

DAISY CHAINS FEATURING MORE THAN 20 ROUNDS HAVE BEEN DISCOVERED • 22 155 -mm rounds • 380 m kill zone • Daisy chained with det cord • Buried Shells have been excavated 5

Iraq IED Tactics • 2003 -2004 IEDs planted at night using 5 -20 men digging holes next to road. • 2004 Deployment of night -vision Predator UAVs used seek-and-destroy tactics. • By end of 2004, night • 2005 – IEDs planted in deployment of IEDs daylight by men dressed as effectively ended on Road Crews. major highways. • 2005 – Less than 20% of day -light buried IEDs reported by Iraqi civilians. 6

RF - IED INITIATORS: CAR ALARMS / KEYLESS ENTRY SYSTEMS • Most common RF - IED initiator • No modification req’d; output taken to detonator Car alarm receiver • 12 V power • Effective range 100 -150 m Car alarm transmitters (key fobs) 7

8

RF - IED INITIATORS: WIRELESS DOORBELLS • • Inexpensive Readily available Simple to modify for IED use Output taken from chime speaker Doorbell receiver Doorbell transmitters 9

RF - IED INITIATORS: TWO-WAY RADIOS Two-way radio hidden in a wooden box • Large choice of frequencies • Ranges of up to 5 km • Some homemade decoder boards encountered • Requires some degree of skill 10

RF - IED INITIATORS: CORDLESS PHONES Long-range handset and base station (12 V power) HOUSEHOLD handset and base station (12 V power) 11

RF - IED INITIATORS: MODEL TOYS Model receiver in box 12 Trigger controller Futaba Model 6 XA-FM Toy car modified as RF - IED

GENERAL OBSERVATIONS: IEDs IN IRAQ 70% of attacks in the Sunni Triangle occur during morning 0900 -1200 RC DEVICES ENCOUNTERED DEVICE RANGE Car alarm/keyless entry 200 m Wireless doorbell 200 m Cordless phone 100 m Nokia phone 1 -2 km+ Model car/toy receivers 1 -150 m Transceivers/decoder 5 km VEHICLE CONVOYS ARE PRIME TARGETS FOR IEDs 13

14

IED - MAIN CHARGES • Majority are ordnance items: artillery shells and mortar rounds • Bulk TNT, PE-4, and PE-4 A also used (PE-4 and PE-4 A are RDXbased) • No homemade explosives encountered 15

IED - CONCEALMENT • • • 16 Cast in concrete Hidden in roadside trash Placed in burlap or plastic bags Concealed in tires Hidden in trees

IED - Detonation • Primarily commercial electric blasting caps: several foreign designs • Detonating cord also used • Standard procedure: fuze wells potted with PE-4 A; blasting caps or detonating cord then inserted 17

18

What Countermeasures for Simple RF-IEDs? Bradley Fighting Vehicle (22 tons) fitted with RF Jamming. >1, 000 units, “Warlock”, being produced by Raytheon (based on Univ. New Mexico design). Effectiveness is moderate because BFV is slow (< 30 mph). RF Jamming is indiscriminate and requires guessing as to frequency band. Also interferes with military communications and civilian RF applications. 19

20

IED Countermeasures • Some experts believe that a more effective IED countermeasure might be achieved through technology that can detect IEDs from afar, and then create a pulse of electromagnetic energy to prematurely detonate them, or burn out and destroy their circuitry. One device is the Neutralizing Improvised Explosive Devices with Radio Frequency (NIRF). The device produces a high-frequency field at very short range that can neutralize electronics. The Pentagon reportedly will deploy NIRF in Iraq later this year. • Other devices create a protective area around moving convoys. A Pentagon microwave project, code-named PING, is already deployed in Iraq, and reportedly has been successful at helping locate insurgent weapons caches. The machine, which fits inside a Humvee, sends out electromagnetic waves that can penetrate a building’s interior to detect IEDs. • Other sensors, such as the Laser-Induced Breakdown Spectroscopy system (LIBS), are being developed to detect traces of explosives used for IEDs from as far away as 30 meters. • The “Talon” is a bomb-disposal Unmanned Ground Vehicle (UGV), or robot, that comes equipped with a mechanical arm to pick up and inspect dangerous objects, such as suspected IEDs. More than a hundred of the remote-control robots are now being used in Iraq and Afghanistan, with an equal amount on order. Another robot, called the “Pack. Bot” has also been used by the Army to clear bombs and explore suspected terrorist hideouts. http: //www. usembassy. it/pdf/other/RS 22330. pdf 21

Funding for IED Countermeasures • 2002 Funding ~ $ 30 M • 2004 Funding ~ $ 85 M • 2006 Funding ~ $ 3, 320 M 22

Causing Electronics to Lock-Up Using Particle Beams in Air • Irradiation with Neutrons has no effect (doses exceeding 1012/cm 2 (2 hour irradiation). • Irradiation with high energy protons (capable of going 100’) has no effect (doses exceeding 1010/cm 2 (1 hour irradiation). • Electron beams – Total lock-up within 1 second for a beam of < 1μA. 23 Note: An e- beam of 18 Me. V might go 230’ in air (theory).

23 Me. V e- Accelerators Widely Available Johns Hopkins Medical Center 23 Me. V Varian Therapy Tool 24

Electron accelerator (18 Me. V) used in current e-Zapper tests The electron accelerator used in the tests described in this report. It creates an electron beam with energies up to 18 Me. V, which exit from the 3 mm tube at the left. The accelerator is an RF linac, capable of producing more than 10 m. A (DC equivalent) of electrons at the maximum energy. 25

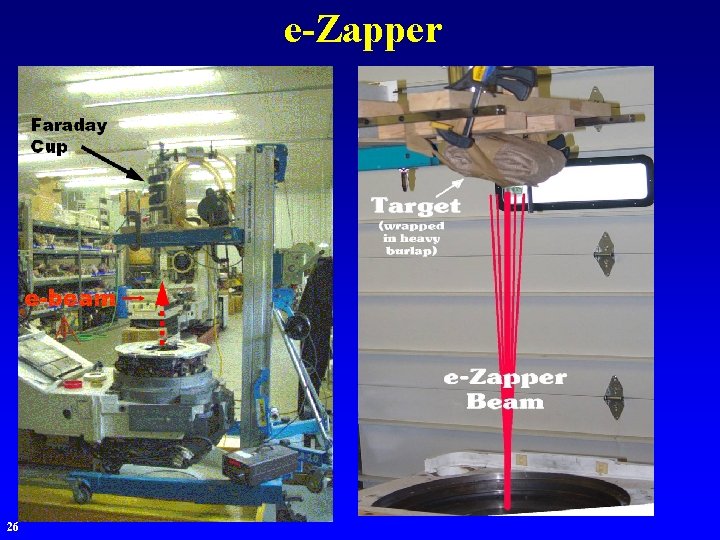
e-Zapper 26

Typical e-Zapper Target A typical e-Zapper target used in the experiments. This is a walkie-talkie with a quoted range of 2 miles. It has both a bell alarm and a LED alarm, either of which could be rewired to activate a micro-relay connecting a battery to a detonator. The walkie-talkie has three primary chips, any of which could disable it. The walkie-talkies were killed in <5 seconds using about 50 n. A/cm 2 of e-beam intensity. 27

Intensity of e-Zapper One target was placed about 1’ from the e-beam exit aperture during initial setup, and the beam instantly drilled a hole in the plastic housing. The melted plastic hole measured slightly less than 1 cm, indicating both the beam size and the potential beam power. 28 (Noted on the case are the positions of three chips inside the ringer case, which are required to activate the bell chimes. )

Deactivation without Detonation Experimental paper (1966) showed explosives only detonated by heat. Can not be set off by radiation. Typically, need >220 C. 29 Experiment: Surrounded RF device with shot-gun shells and bullets. Deactivation occurred in 2 seconds, with no detonation.

E-Zapper Status - 2006 30

e-Zapper Original Equipment and Essential Equipment 31

James Ziegler Martin Nelson United States Naval Academy 33 UNCLASSIFIED
 Naval academy forum
Naval academy forum Feiws
Feiws Royal norwegian naval academy
Royal norwegian naval academy James fraser naval aviator
James fraser naval aviator James fraser naval aviator
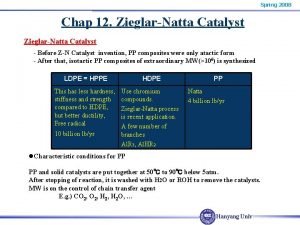
James fraser naval aviator Ziegler natta catalyst is
Ziegler natta catalyst is Pia ziegler
Pia ziegler Ziegler family tree
Ziegler family tree Ziegler-natta coordination polymerization
Ziegler-natta coordination polymerization Pia ziegler
Pia ziegler Polimeri esempi
Polimeri esempi Ziegler
Ziegler Jeffrey ziegler,
Jeffrey ziegler, Carolin ziegler rp stuttgart
Carolin ziegler rp stuttgart Ziegler
Ziegler Belle ziegler
Belle ziegler Andrea ziegler
Andrea ziegler Adolf ziegler
Adolf ziegler Traditions and encounters chapter 20
Traditions and encounters chapter 20 Was the united states on the axis powers or allied powers?
Was the united states on the axis powers or allied powers? Many _____ people have settled in this megalopolis.
Many _____ people have settled in this megalopolis. 36 30 line
36 30 line Us pro soccer organization
Us pro soccer organization United states v. nixon significance
United states v. nixon significance United states student association
United states student association The united states ought to provide a universal basic income
The united states ought to provide a universal basic income The preamble of the constitution
The preamble of the constitution The united states in the caribbean 1776-1985
The united states in the caribbean 1776-1985 Products of the southeast
Products of the southeast Expansion of the united states of america 1607 to 1853 map
Expansion of the united states of america 1607 to 1853 map When did nicholas novikov write the telegram
When did nicholas novikov write the telegram Louisiana purchase previous owner
Louisiana purchase previous owner Author of awake united states
Author of awake united states