Internet Introduction Overview Internetworking Concept and protocol Layering






- Slides: 70

Internet: Introduction, Overview, Internetworking Concept and protocol Layering Reference: Internetworking with TCP/IP: Principles, Protocol, and Architecture, Douglas E. Comer 6 th Edition, 2017, , Pearson, ISBN 978 -93325 -5010 -0 Asst. Prof. Dr. Anilkumar K. G 1

Motivation of Internetworking • Today without Internet; – There is no social networks (such as Face Book, whats. Apps, etc). – There is no online transaction (including Ecommerce, voice/video chat etc). • Move towards cloud computing will put more information and services online. Asst. Prof. Dr. Anilkumar K. G 2

What Does Internet Mean? • The Internet is a globally connected network system that uses TCP/IP to transmit data via various types of media. – The Internet is a network of global exchanges – including private, public, academic and government networks – connected by guided, wireless and fiber-optic technologies. • The terms Internet and world wide web (www) are often used interchangeably, but they are not exactly the same thing; – the Internet refers to the global communication system, including HW and infrastructure, while the www is one of the services communicated over the Internet. Asst. Prof. Dr. Anilkumar K. G 3

Motivation of Internetworking • The Internet technology hides the details of network HW, and permits computers to communicate independent of their physical network connections. • Internet technology is an example of open system interconnection, because its specifications are publicly available. • Uses any packet switched HW to accommodate a wide variety of applications. Asst. Prof. Dr. Anilkumar K. G 4

The TCP/IP Internet • The Internet protocol suit is named as TCP/IP (Transmission Control Protocol/Internet Protocol). • It can be used to communicate across any set of interconnected networks. – Interconnection network generally refers to data transportation among computers. • networks refers to interconnected nodes using network equipments, such as switches/routers and communication channels. – The Internet demonstrates the viability of the TCP/IP technology and shows how it can accommodate a wide variety of underlying HW technologies. Asst. Prof. Dr. Anilkumar K. G 5

Internet Services - Protocol • The term protocol defines the syntactic and semantic rules for communication: – Protocols give the details of message formats, describes how a computer responds when a message arrives, and specify how a computer handles error or other abnormal conditions. – Protocols allow us to discuss computer communication independent of any particular vender’s network HW. • A protocol is just like an algorithm: • An algorithm allows one to specify or understand a computation without knowing the details of a particular programming language or ISA. Asst. Prof. Dr. Anilkumar K. G 6

Internet Services - Protocol • Hiding the low level details of communication helps to improve productivity in several ways: – People can use high-level protocol abstractions. – Programmers do not need to learn or remember details about a given HW configuration/ISA. • Thus people/user/developer can create various new network applications quickly. – The applications do not need to be changed when computers or networks are replaced or reconfigured. Asst. Prof. Dr. Anilkumar K. G 7

Internet Services - Interoperability • The term interoperability refers to the ability of computing systems to cooperate in solving various computational problems. • The Internet was designed to accommodate heterogeneous networks and computers, and hence interoperability was a key requirement. – Most users access Internet via cable modem, or Wi-Fi, or from a mobile phone hotspot service without understanding the types of computers or networks being used. Asst. Prof. Dr. Anilkumar K. G 8

Internet application services • The most popular and widespread Internet application services include: – World wide web(www): www became the largest source of traffic on the global Internet. – Cloud access and remote desktop: Cloud access, computing and storage facilities through cloud data centers are the services arranged over the internet. – File Transfer: The file transfer protocols allows users to send or receive a copy of a data file. – email: Many users now access email through a web (based on an email transfer protocol). – Voice and video services: Both streaming video and audio bits transported across the global internet. Asst. Prof. Dr. Anilkumar K. G 9

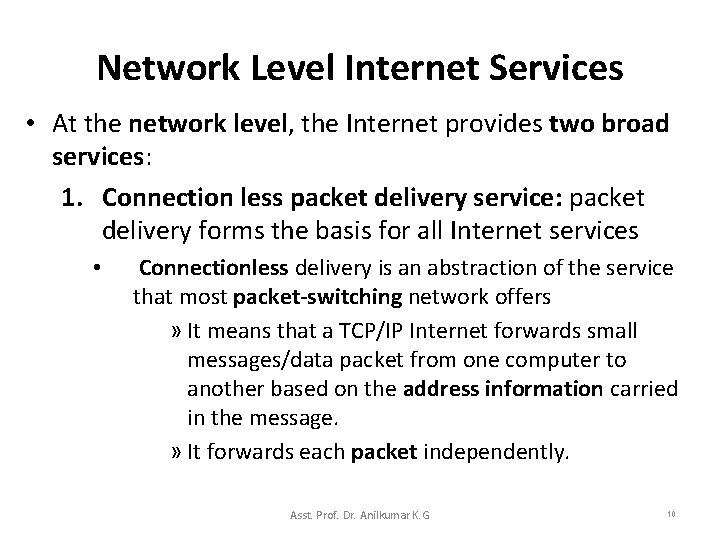
Network Level Internet Services • At the network level, the Internet provides two broad services: 1. Connection less packet delivery service: packet delivery forms the basis for all Internet services • Connectionless delivery is an abstraction of the service that most packet-switching network offers » It means that a TCP/IP Internet forwards small messages/data packet from one computer to another based on the address information carried in the message. » It forwards each packet independently. Asst. Prof. Dr. Anilkumar K. G 10

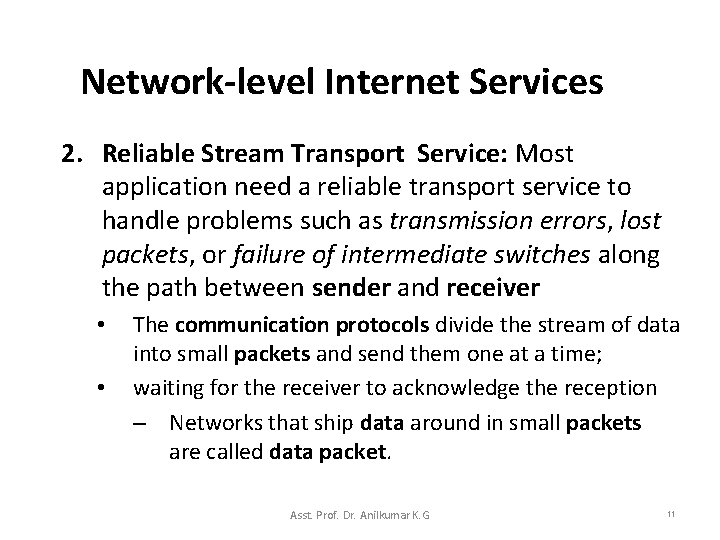
Network-level Internet Services 2. Reliable Stream Transport Service: Most application need a reliable transport service to handle problems such as transmission errors, lost packets, or failure of intermediate switches along the path between sender and receiver • • The communication protocols divide the stream of data into small packets and send them one at a time; waiting for the receiver to acknowledge the reception – Networks that ship data around in small packets are called data packet. Asst. Prof. Dr. Anilkumar K. G 11

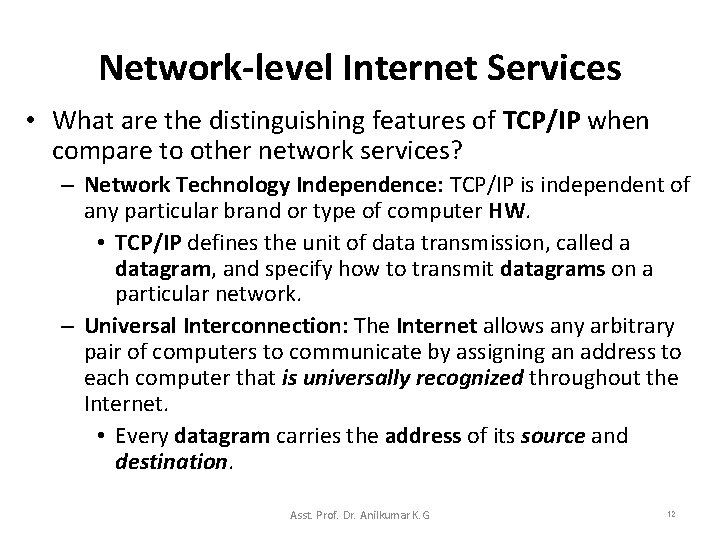
Network-level Internet Services • What are the distinguishing features of TCP/IP when compare to other network services? – Network Technology Independence: TCP/IP is independent of any particular brand or type of computer HW. • TCP/IP defines the unit of data transmission, called a datagram, and specify how to transmit datagrams on a particular network. – Universal Interconnection: The Internet allows any arbitrary pair of computers to communicate by assigning an address to each computer that is universally recognized throughout the Internet. • Every datagram carries the address of its source and destination. Asst. Prof. Dr. Anilkumar K. G 12

Network-level Internet Services – End-to-End Acknowledgement: The TCP/IP Internet protocols provide acknowledgements between the original source and ultimate destination. – Application Protocol Standards: The TCP/IP Internet protocol include protocols specifies how to access a web page, transfer file, send/receive email, etc. Asst. Prof. Dr. Anilkumar K. G 13

Transition from IPv 4 To IPv 6 • The Internet Protocol (IP), IPv 4 was the first working version for internet since 1970. – Since the time IPv 4 was designed, processor performance has increased. • Despite the success of IPv 4, it was insufficient for new applications such as voice and video. • The new IP is called IPv 6 and is inherited some of the features of the IPv 4. Asst. Prof. Dr. Anilkumar K. G 14

Transition from IPv 4 To IPv 6 • Both IPv 4 and IPv 6 use a connectionless delivery paradigm, allow the sender to choose the size of data being sent. – connectionless describes communication between two network end points in which a message/packet can be sent from one end point to another without prior arrangement. • IPv 6 retains many of the IPv 4 facilities such a fragmentation. • IPv 6 changes most of the protocol details: – IPV 6 uses larger address and it completely revises the IPv 4 packet format. Asst. Prof. Dr. Anilkumar K. G 15

Transition from IPv 4 To IPv 6 • The changes introduced by IPv 6 can be grouped into seven categories: 1. Larger address: IPv 6 quadruples the size of an IPv 4 address from 32 bits to 128 bits. 2. Extended Address Hierarchy: IPv 6 uses the larger address space to create additional levels of addressing hierarchy. 3. New Header Format: IPv 6 uses an entirely new packet format that includes a set of optional headers. 4. Improved options: IPv 6 allows a packet to include optional control information that is not available in IPv 4. Asst. Prof. Dr. Anilkumar K. G 16

Transition from IPv 4 To IPv 6 5. Provision for Protocol Extension: The IPv 6 extension capability allows to adapt the protocol to new network HW and applications. 6. Support for Auto configuration and Renumbering: IPv 6 allows a site to change from one Internet Service Provider(ISP) to another by automating the requisite address changes. 7. Support for Resource Allocation: IPv 6 includes a flow abstraction and allows differentiated services. Asst. Prof. Dr. Anilkumar K. G 17

Protocol Stack • Operating Systems such as Linux, Windows, and OS-X are already classified as dual stack systems: – Means in addition to all the SW needed for IPv 4, the OS contains all the SW needed for IPv 6. – In most OS, the two versions do not interact, • that is each side has an IP address and can send and receive packets. • The dual stack idea is closely related to the parallel internet approach. – Dual Stack systems allow applications to choose whether they will use IPv 4, IPv 6 or both. Asst. Prof. Dr. Anilkumar K. G 18

Protocol Stack • A dual stack mechanism allows an application to choose dynamically making the IP migration automatic: – if a given Uniform Resource Locator (URL or a web address) maps to both an IPv 4 address and an IPv 6 address: • the browser might try to communicate using IPv 6 first • If the attempt fails, the browser can try IPv 4 • If the computer is connected to an IPv 6 network that reaches the destination, IPv 6 communication will succeed. • If not, the browser automatically falls back to using IPv 4. Asst. Prof. Dr. Anilkumar K. G 19

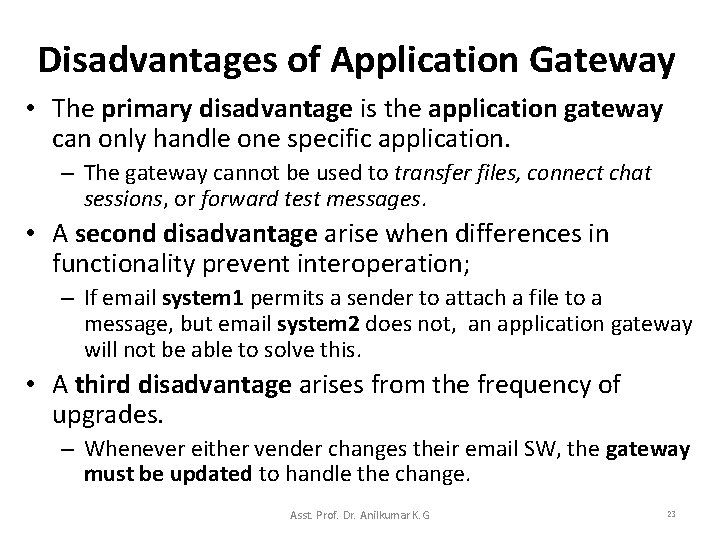
Application Level Interconnection • When faced with heterogeneous systems, early designers relied on special application programs, called application gateways to hide the underlying differences and provide the appearance of uniformity. – For example, consider early versions of different email systems. – When a connection between such email systems was needed, an application gateway was used. – The gateway SW runs on a computer that connects to both email systems as shown in Figure 3. 1. Asst. Prof. Dr. Anilkumar K. G 20

Application-level Interconnection Asst. Prof. Dr. Anilkumar K. G 21

Application Gateway • The application gateway must understand the details of the network connections, the message protocols and the email message formats used by the email systems (see the Figure 3. 1): – When user 1 sends an email message to user 2, user 1’s email is configured to send the message to the application gateway. – The application gateway translates the message and the email address used by the email systems, and then forward the message to the users. – Using the application gateway , the original email systems on the users’ computers remain unchanged. Asst. Prof. Dr. Anilkumar K. G 22

Disadvantages of Application Gateway • The primary disadvantage is the application gateway can only handle one specific application. – The gateway cannot be used to transfer files, connect chat sessions, or forward test messages. • A second disadvantage arise when differences in functionality prevent interoperation; – If email system 1 permits a sender to attach a file to a message, but email system 2 does not, an application gateway will not be able to solve this. • A third disadvantage arises from the frequency of upgrades. – Whenever either vender changes their email SW, the gateway must be updated to handle the change. Asst. Prof. Dr. Anilkumar K. G 23

Network-level Connections • An alternative to application gateway is the application of network-level interconnection (Internet): – A system that allowed to transfer data packets from their original source to their ultimate destination without using any intermediate application programs. • Advantages of network-level interconnection: 1. The scheme maps directly onto the underlying network HW, making it extremely efficient. 2. It separates data communication activities from application programs. Asst. Prof. Dr. Anilkumar K. G 24

Network-level Connections 3. Making it possible to build general purpose communication facilities that are not limited to specific use. 4. The scheme allows network manages to add or change network technologies while application programs remain unchanged. • The key to designing universal level interconnection can be found in an abstract communication system concept known as internetworking or Internet. • One of the first principles in the Internet design focuses on encapsulation: – Hiding the underlying internet architecture from users, and permit communication without requiring knowledge of the internet’s structure. Asst. Prof. Dr. Anilkumar K. G 25

Internet Architecture • How are networks connected to form an internetwork? • The answer has two parts: 1. Physically, two networks cannot be plugged together directly. Special HW needed to connect to each network. 2. A physical attachment does not provide the interconnection. Because such a connection does not guarantee that a computer will corporate with other machines that wish to communicate. Asst. Prof. Dr. Anilkumar K. G 26

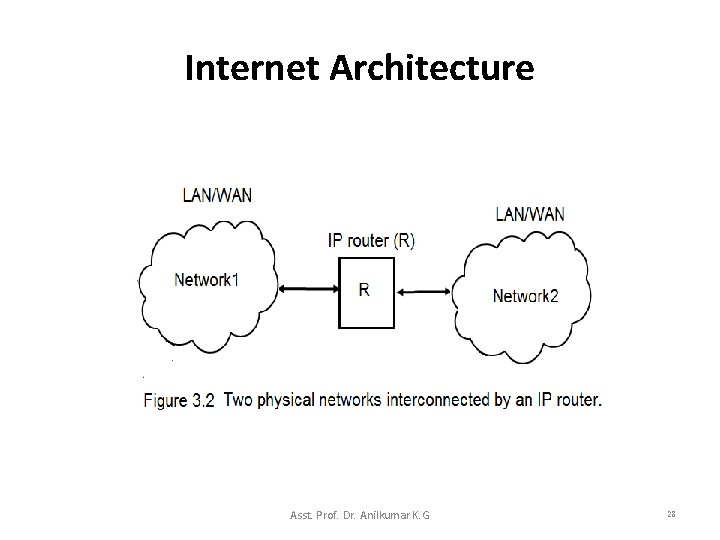
Internet Architecture • To have a viable Internet, we need computers that are willing to transfer data packets from one network to another. • Computers that interconnect two networks and pass packets from one to the other are called Internet routers (or IP routers). – IP routing is the field of routing methodologies of Internet Protocol packets within and across IP networks. • The two physical networks interconnected by an IP router is shown in Figure 3. 2. Asst. Prof. Dr. Anilkumar K. G 27

Internet Architecture Asst. Prof. Dr. Anilkumar K. G 28

Internet Architecture • In Figure 3. 2, the router R connects to both Network 1 and Network 2. – R must capture packets on Network 1 that are destined for machines on Network 2 and transfer them. – Similarly, R must capture packets on Network 2 that are destined for machines on Network 1 and transfer them. • Each network can either be a LAN or WAN. Asst. Prof. Dr. Anilkumar K. G 29

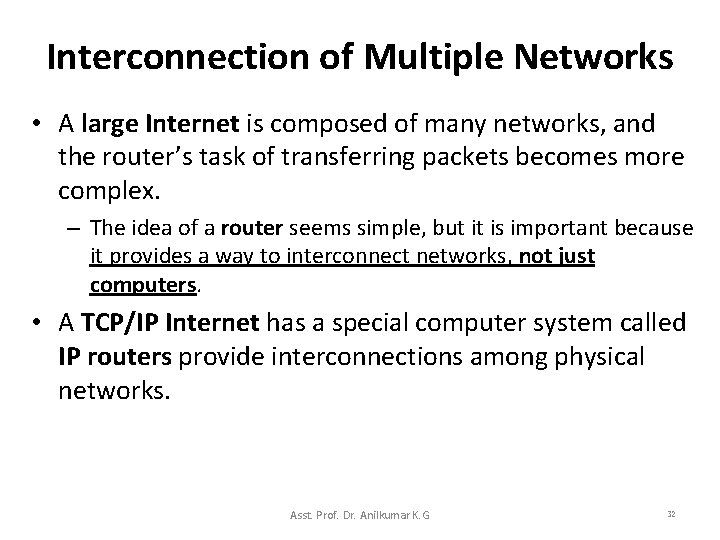
Interconnection of Multiple Networks • A realistic Internet will include multiple networks and routers. – In Figure 3. 3, router R 1 must transfer from Network 1 to Network 2 all packets destined for computers on either Network 2 or Network 3. – Similarly, router R 2 must transfer packets from Network 3 that are destined for either Network 2 or Network 1. • The important point is that a router must handle packets for networks to which the router does not attach. Asst. Prof. Dr. Anilkumar K. G 30

Interconnection of Multiple Networks Asst. Prof. Dr. Anilkumar K. G 31

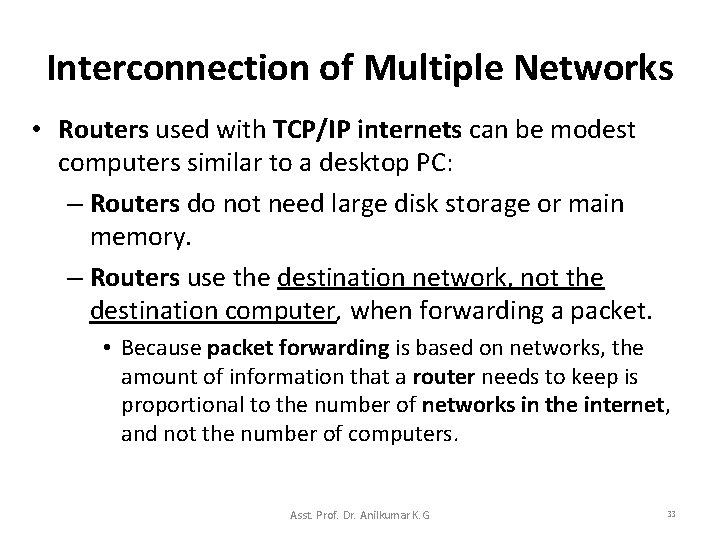
Interconnection of Multiple Networks • A large Internet is composed of many networks, and the router’s task of transferring packets becomes more complex. – The idea of a router seems simple, but it is important because it provides a way to interconnect networks, not just computers. • A TCP/IP Internet has a special computer system called IP routers provide interconnections among physical networks. Asst. Prof. Dr. Anilkumar K. G 32

Interconnection of Multiple Networks • Routers used with TCP/IP internets can be modest computers similar to a desktop PC: – Routers do not need large disk storage or main memory. – Routers use the destination network, not the destination computer, when forwarding a packet. • Because packet forwarding is based on networks, the amount of information that a router needs to keep is proportional to the number of networks in the internet, and not the number of computers. Asst. Prof. Dr. Anilkumar K. G 33

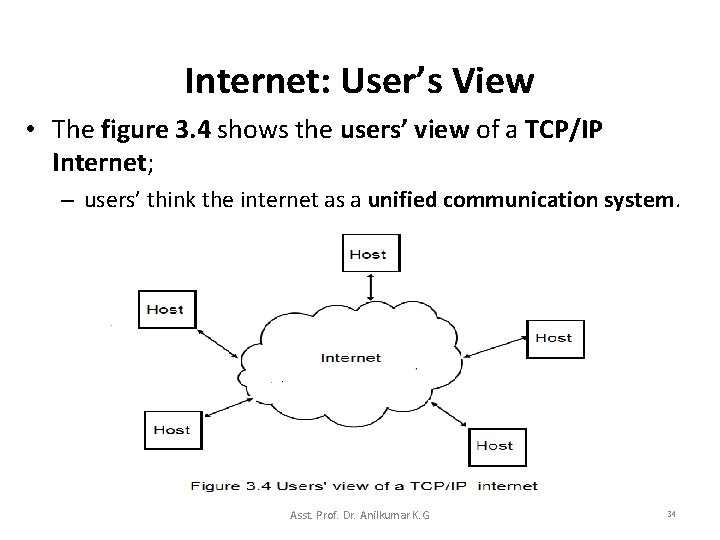
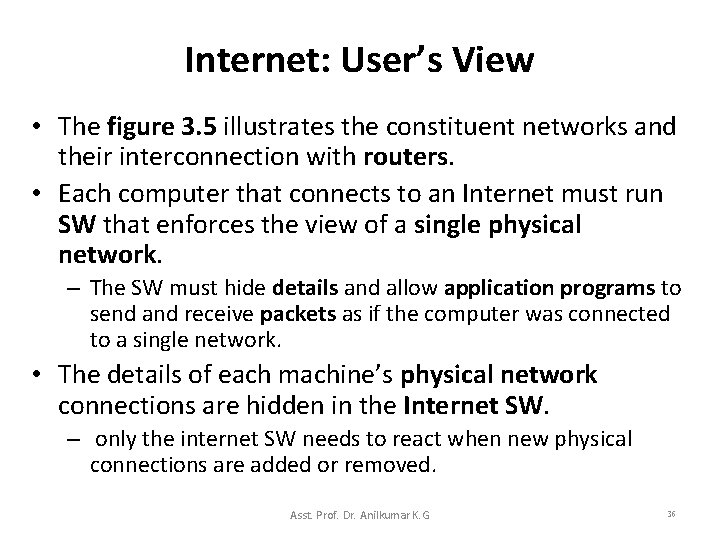
Internet: User’s View • The figure 3. 4 shows the users’ view of a TCP/IP Internet; – users’ think the internet as a unified communication system. Asst. Prof. Dr. Anilkumar K. G 34

Internet: User’s View Asst. Prof. Dr. Anilkumar K. G 35

Internet: User’s View • The figure 3. 5 illustrates the constituent networks and their interconnection with routers. • Each computer that connects to an Internet must run SW that enforces the view of a single physical network. – The SW must hide details and allow application programs to send and receive packets as if the computer was connected to a single network. • The details of each machine’s physical network connections are hidden in the Internet SW. – only the internet SW needs to react when new physical connections are added or removed. Asst. Prof. Dr. Anilkumar K. G 36

Internet: User’s View • Advantage of having communication at the network level is more subtle: – user do not have to understand, remember, or specify how network connect, what application they support, etc. • Internal networks do not know about applications, they merely transport packets. – As a result, programmers who do not know about the Internet structure can create applications, and – the internet does not need to be modified when new applications are created. Asst. Prof. Dr. Anilkumar K. G 37

Internet: User’s View • The networks participating in an Internet are analogous to a system of roads. – Local networks feed traffic into larger networks, just as local roads connect to highways. • Here is the Internet point of view: – any communication system capable of transferring packets counts as a single network independent of its delay and throughput characteristics, packet size or geographic scale. • The TCP/IP treat all networks equally: • A LAN such as an Ethernet, a WAN used as a backbone, a wireless network such as Wi-Fi hotspot, and a point-to-point link between two computers each count as one network. Asst. Prof. Dr. Anilkumar K. G 38

Protocol Layering • Protocols allow one to specify or understand communication without knowing the details of a particular network HW: – To understand the complexity a network communication, the problems that can arise when computers communicate over a data network need to be noticed: I. III. IV. V. – HW failure Network congestion Packet delay or loss Data corruption Data duplication It is impossible to write a single protocol specification that will handle them all! Asst. Prof. Dr. Anilkumar K. G 39

Protocol Layering • A programming language normally has 4 partitions : compiler, Assembler, Link-editor and Loader. • From this analogy, we can clarify the organization of a communication protocol: – It should be clear that communication translation SW must agree on the exact format of data passed between them. – • For ex: , the data passed from a compiler to an assembler consists of a program defined by the assembly language. The four parts of the programming language translator form a linear sequence in which output from the Compiler becomes input to the Assembler and so on. – Similarly , a communication protocol SW also uses a linear sequence. Asst. Prof. Dr. Anilkumar K. G 40

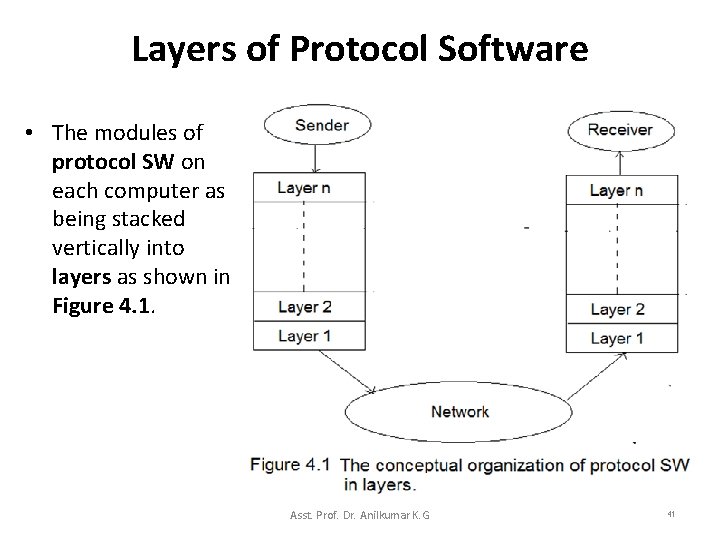
Layers of Protocol Software • The modules of protocol SW on each computer as being stacked vertically into layers as shown in Figure 4. 1. Asst. Prof. Dr. Anilkumar K. G 41

Layers of Protocol Software • Sending a message from an application on one computer to an application on another computer means; – transferring the message down through successive layers of protocol SW on the sender’s machine, forwarding the message across the network, and transferring the message up through successive layers of protocol SW on the receiver’s machine. • The network architecture and the layered organization of the protocol SW are interrelated; one cannot be designed without the other. Asst. Prof. Dr. Anilkumar K. G 42

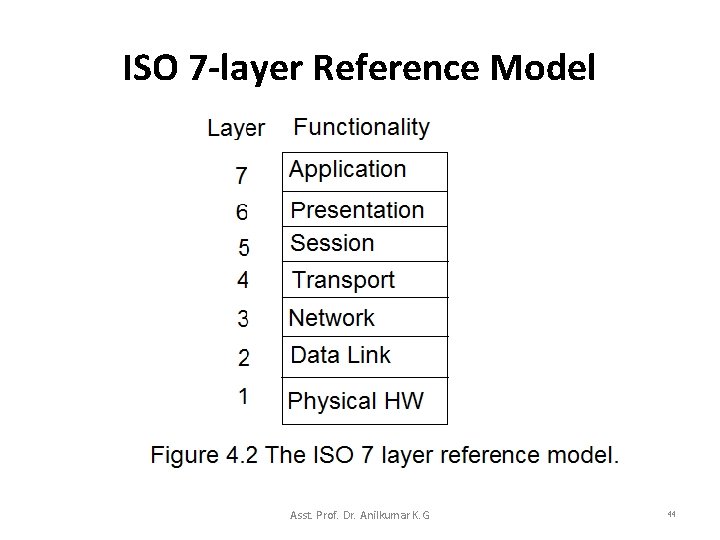
ISO 7 -layer Reference Model • The first layering network protocol model was based on early work done by International Organization for Standardization (ISO). – It is often referred to as the ISO 7 -layer model (shown in Figure 4. 1). • The ISO model does not describe the Internet protocols well and its layers are not used by TCP/IP. • The ISO 7 -layer reference model was designed only to describe protocols in a single network and not for TCP/IP. Asst. Prof. Dr. Anilkumar K. G 43

ISO 7 -layer Reference Model Asst. Prof. Dr. Anilkumar K. G 44

The TCP/IP 5 -layer Reference Model • The original ISO 7 -layer model did not provide an Internet layer and instead defined session and presentation layers that are not related to TCP/IP. • The ISO model was prescriptive but the Internet model is descriptive. – Researchers spent years for understanding how to structure the protocols, building prototype implementations and documenting the results for the Internet. Asst. Prof. Dr. Anilkumar K. G 45

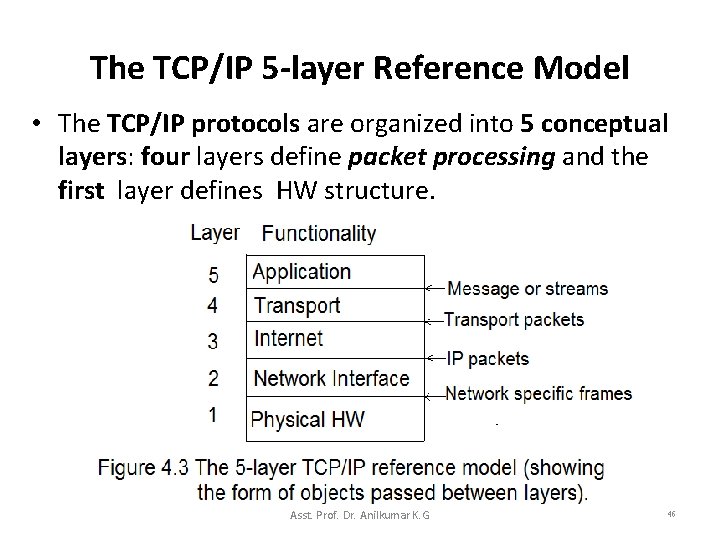
The TCP/IP 5 -layer Reference Model • The TCP/IP protocols are organized into 5 conceptual layers: four layers define packet processing and the first layer defines HW structure. Asst. Prof. Dr. Anilkumar K. G 46

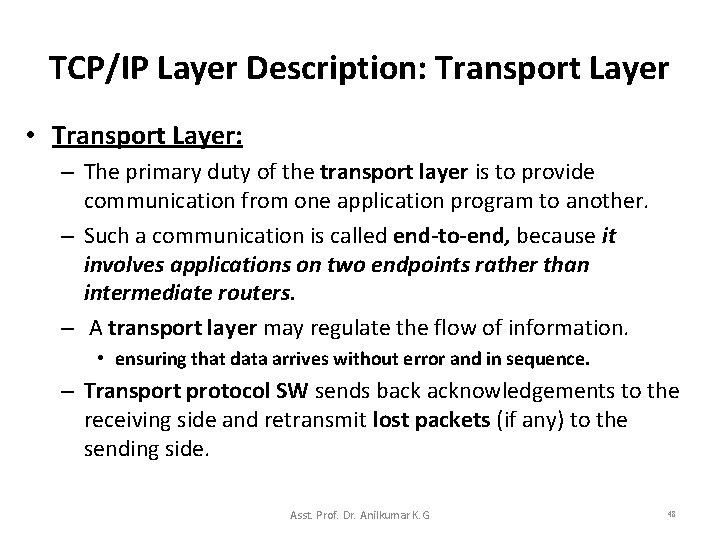
TCP/IP Layer Description: Application Layer • Application layer: – At the application layer, users invoke application programs that access services available across a TCP/IP network. – An application interacts with one of the transport layer protocols send/receive data packets: • • Which can be either a sequence of individual messages or a continuous stream of bytes The application program passes data in the required form to the transport layer for delivery. Asst. Prof. Dr. Anilkumar K. G 47

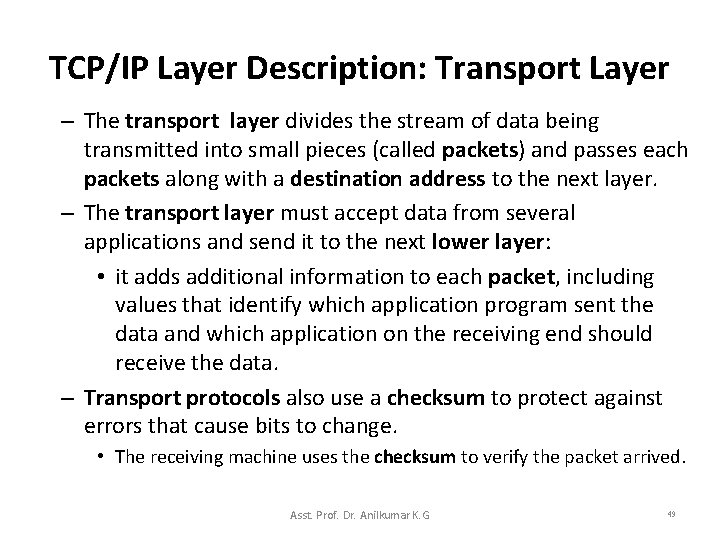
TCP/IP Layer Description: Transport Layer • Transport Layer: – The primary duty of the transport layer is to provide communication from one application program to another. – Such a communication is called end-to-end, because it involves applications on two endpoints rather than intermediate routers. – A transport layer may regulate the flow of information. • ensuring that data arrives without error and in sequence. – Transport protocol SW sends back acknowledgements to the receiving side and retransmit lost packets (if any) to the sending side. Asst. Prof. Dr. Anilkumar K. G 48

TCP/IP Layer Description: Transport Layer – The transport layer divides the stream of data being transmitted into small pieces (called packets) and passes each packets along with a destination address to the next layer. – The transport layer must accept data from several applications and send it to the next lower layer: • it adds additional information to each packet, including values that identify which application program sent the data and which application on the receiving end should receive the data. – Transport protocols also use a checksum to protect against errors that cause bits to change. • The receiving machine uses the checksum to verify the packet arrived. Asst. Prof. Dr. Anilkumar K. G 49

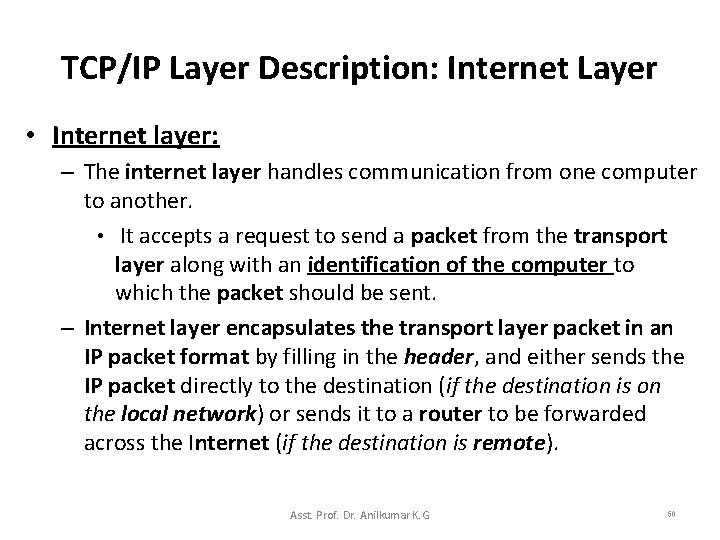
TCP/IP Layer Description: Internet Layer • Internet layer: – The internet layer handles communication from one computer to another. • It accepts a request to send a packet from the transport layer along with an identification of the computer to which the packet should be sent. – Internet layer encapsulates the transport layer packet in an IP packet format by filling in the header, and either sends the IP packet directly to the destination (if the destination is on the local network) or sends it to a router to be forwarded across the Internet (if the destination is remote). Asst. Prof. Dr. Anilkumar K. G 50

TCP/IP Layer Description: Internet Layer – Internet layer SW also handles incoming IP packets, checking their validity and using the forwarding algorithm to decide whether the packet should be processed locally or forwarded : • For packets destined to the local machines, SW in the internet layer choose the transport protocol that will handle the packet. Asst. Prof. Dr. Anilkumar K. G 51

TCP/IP Layer Description: Network Interface Layer • Network Layer: – The lowest layer of TCP/IP comprises a network interface layer, responsible for accepting IP packets and transmitting them over a specific network. – The network layer may consists of a device driver or a complex subsystem that implements a data link protocol. • In practice, the TCP/IP is much more complex than the simple 5 layer model which is just described. – The conceptual diagram in Figure 4. 4 shows the network complexity in a real internet system. Asst. Prof. Dr. Anilkumar K. G 52

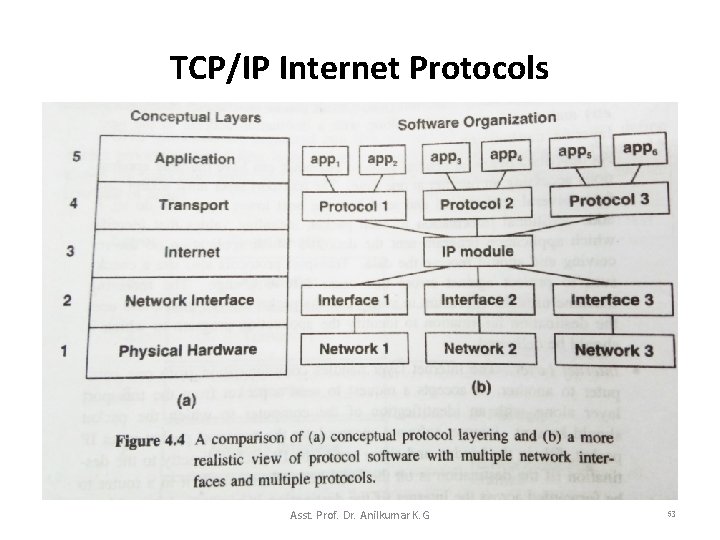
TCP/IP Internet Protocols Asst. Prof. Dr. Anilkumar K. G 53

TCP/IP Internet Protocols • The conceptual diagram Figure 4. 4 a shows five layers of TCP/IP with a depiction each layer. • But Figure 4. 4 b shows more realistic illustration of the five layers of the TCP/IP: – Figure 4. 4 b shows that there may indeed be a layer with one protocol (Layer 3). – There can be multiple applications at Layer 5, and more than one application can use a given transport protocol at a time. – It can be seen that multiple transport protocols at Layer 4, multiple physical networks at Layer 1, and multiple network interface modules at Layer 2. Asst. Prof. Dr. Anilkumar K. G 54

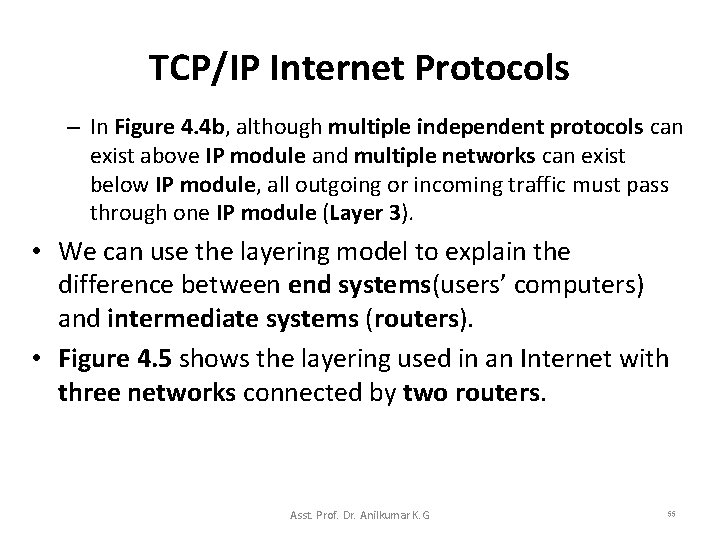
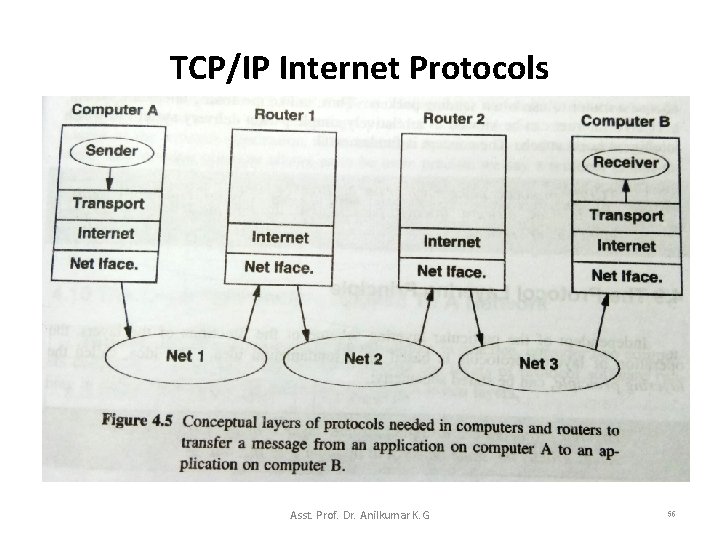
TCP/IP Internet Protocols – In Figure 4. 4 b, although multiple independent protocols can exist above IP module and multiple networks can exist below IP module, all outgoing or incoming traffic must pass through one IP module (Layer 3). • We can use the layering model to explain the difference between end systems(users’ computers) and intermediate systems (routers). • Figure 4. 5 shows the layering used in an Internet with three networks connected by two routers. Asst. Prof. Dr. Anilkumar K. G 55

TCP/IP Internet Protocols Asst. Prof. Dr. Anilkumar K. G 56

TCP/IP Internet Protocols • In the Figure 4. 5, a sending application on computer A uses a transport protocol to send data to a receiving application on computer B. – The message passes down the protocol stack on A, and is transmitted across Net 1 to Router 1. – When it reaches the Router 1, the packet passes up to the internet layer (Layer 3) of the Router 1, which forwards the packet over Net 2 to Router 2. – On Router 2, the message passes up to Layer 3 of the Router 2, and is forwarded over Net 3 to the destination. – When it reaches the destination machine, the message passes up to the Transport Layer, which delivers the messages to the receiving application. Asst. Prof. Dr. Anilkumar K. G 57

Protocol Layering Principle • Independent of a particular layering scheme, the operation of layered protocol is based on a fundamental idea called layering. • Layering principle: – Layered protocols are designed so that layer n at the destination receives exactly the same object sent by layer n at the source. • The layering principle offers: I. Protocol design independence II. Definition of the end-to-end property Asst. Prof. Dr. Anilkumar K. G 58

Protocol Layering Principle • Protocol design independence: – By placing a guarantee on the items passing between each pair of layers, the layering principle allows protocol designers to work on one layer at a time. • A protocol designer can focus on the message exchange for a given layer with the assurance that lower layers will not alter messages: – For example, when creating a file transfer application, a designer only needs to imagine two copies of the file transfer application running on two computers. – The interaction between the two copies can be planned without thinking about the other protocol layers because the designer can assume each message will be delivered exactly as it was sent. Asst. Prof. Dr. Anilkumar K. G 59

Protocol Layering Principle – All a designer has to do is guarantee the layering principle to the next higher layer; • For example, when a protocol designer works on a new transport protocol, the designer can assume the transport protocol module on the destination machine will receive whatever message is sent by the transport protocol module on the sending machine. – The key idea: is that a transport protocol can be designed independent of other protocols. Asst. Prof. Dr. Anilkumar K. G 60

Protocol Layering Principle • Definition of the end-to-end property: • We classify a network technology as end-to-end if the technology provides communication from the original source to the ultimate destination. – A protocol is end-to-end iff the layering principle applies between the original source and ultimate destination. • Other protocols are classified as machine-to-machine because the layering principle only applies across one network hop. Asst. Prof. Dr. Anilkumar K. G 61

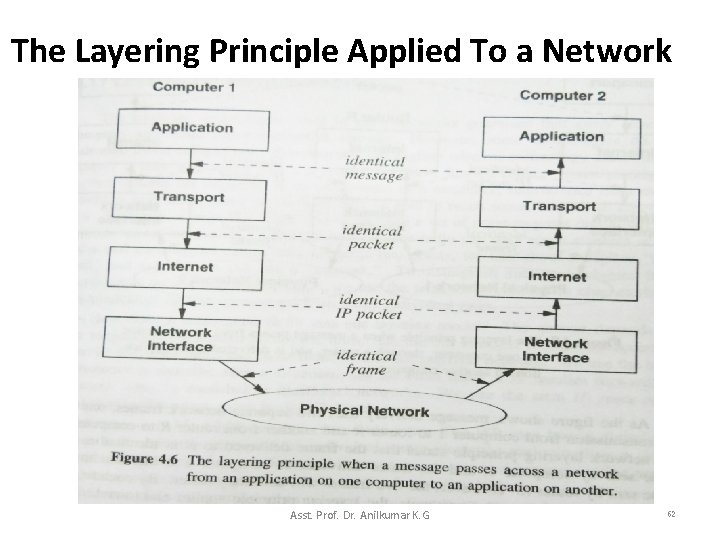
The Layering Principle Applied To a Network Asst. Prof. Dr. Anilkumar K. G 62

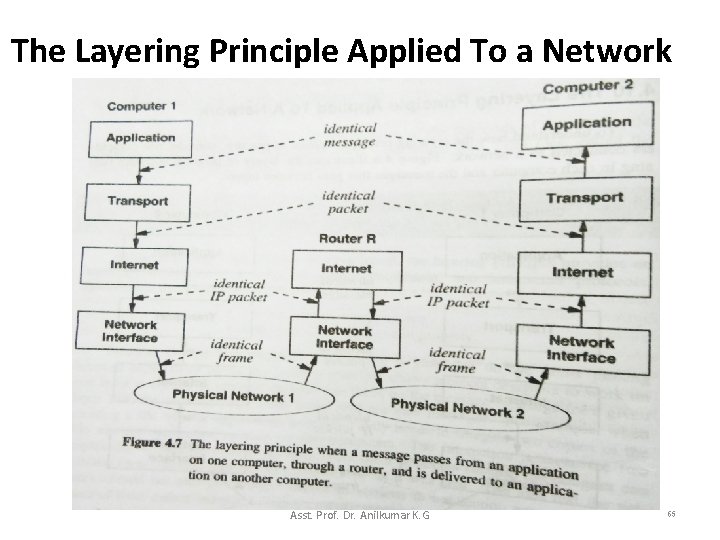
The Layering Principle Applied To a Network • The Figure 4. 6 only shows layering for two computers connected to a single network. • How does the layering principle apply to an Internet that can transfer messages across multiple networks? – Figure 4. 7 answers the question by showing an example where a message from an application on one computer is sent through a router. – Message delivery uses two separate network frames, one for the transmission from computer 1 to router R and another from R to computer 2. Asst. Prof. Dr. Anilkumar K. G 63

The Layering Principle Applied To a Network – The network layering principle states that the frame delivered to router R is identical to the frame sent by Computer 1, and the frame delivered to computer 2 is identical to the frame sent by R. • For the application and transport protocols, the layering principle applies end-to end. – That is, the message delivered on computer 2 is exactly the same message that peer protocol sent on computer 1. Asst. Prof. Dr. Anilkumar K. G 64

The Layering Principle Applied To a Network Asst. Prof. Dr. Anilkumar K. G 65

The Layering Principle Applied To a Network • For higher layers, the layering principle applies end-to end and that at the lowest layer, it applies to a single machine transfer. • The goal of the Internet design is to present a large virtual network, with the internet layer sending packets across the virtual internet analogous to the way network HW sends frames across a single network: – Imagine an IP packet being sent from the source to the ultimate destination, the layering principle guaranteeing that the ultimate destination receives exactly the same IP packet. Asst. Prof. Dr. Anilkumar K. G 66

The Layering Principle Applied To a Network • An IP packet contains fields such as a time to live counter that must be changed each time the packet passes through routers. • Thus, the ultimate destination will not receive exactly the same IP packet as the source sent. – Although most of the IP packet stays intact as it passes across a TCP/IP internet, the layering principle only applies to packets across single machine transfers. • Therefore Figure 4. 7 shows the internet layer providing a machine-to-machine service rather than end-to-end service. Asst. Prof. Dr. Anilkumar K. G 67

Layering in a Mesh Network • Nowadays, an ISP might choose to lease a set of pointto-point digital circuits to interconnects many sites. • How does a mesh network fit into this leased ISP model? – The answer depends on how packets are forwarded across the network links. – If forwarding occurs at layer 2, the entire mesh can be modeled as a single physical network (this situation can be termed as “mesh-under”). – On the other hand, if IP module (layer 3) handles forwarding, the mesh must be modeled as individual networks (referred as IP route-over). Asst. Prof. Dr. Anilkumar K. G 68

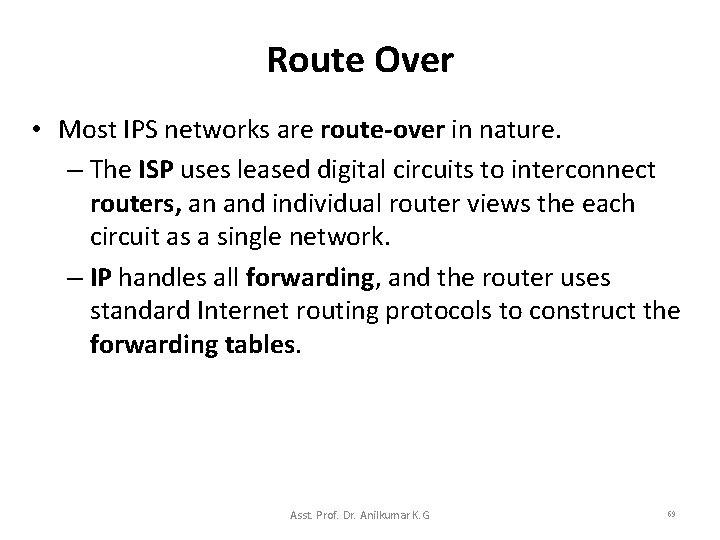
Route Over • Most IPS networks are route-over in nature. – The ISP uses leased digital circuits to interconnect routers, an and individual router views the each circuit as a single network. – IP handles all forwarding, and the router uses standard Internet routing protocols to construct the forwarding tables. Asst. Prof. Dr. Anilkumar K. G 69

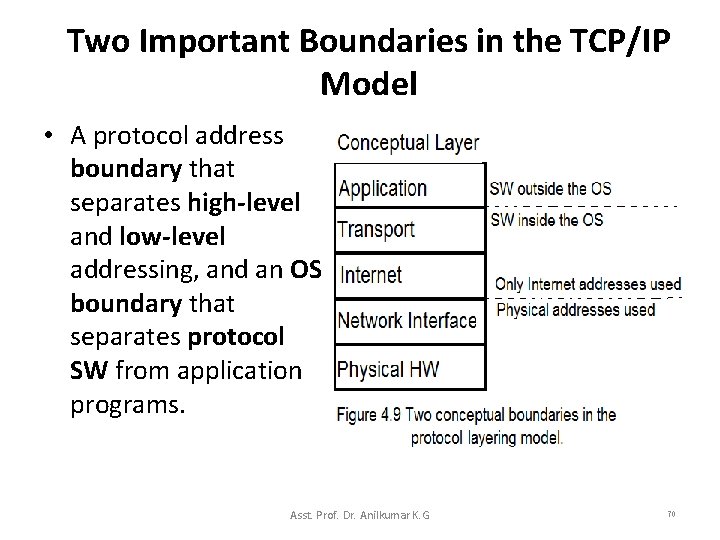
Two Important Boundaries in the TCP/IP Model • A protocol address boundary that separates high-level and low-level addressing, and an OS boundary that separates protocol SW from application programs. Asst. Prof. Dr. Anilkumar K. G 70