Internetworking and Network Layer in Internet Lecture 33






- Slides: 34

Internetworking and Network Layer in Internet Lecture -33 -35 1. Tunneling, Internetwork Routing 2. Fragmentation 3. IP-Protocol 4. IP-Address Classes(A, B, C, D, E), Broadcast address , Multicast address, Network Mask, Subnetting 5. Internet control Protocol-ICMP, IGMP 6. OSPF-Interior Gateway Routing Protocol 7. BGP-Exterior Gateway Routing Protocol 8. Internet Multicasting 9. Mobile-IP 10. IPv 6

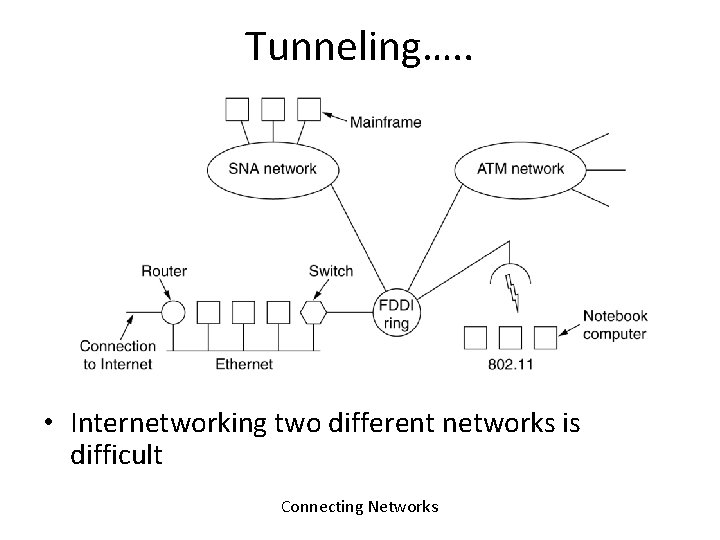
Tunneling…. . • Internetworking two different networks is difficult Connecting Networks

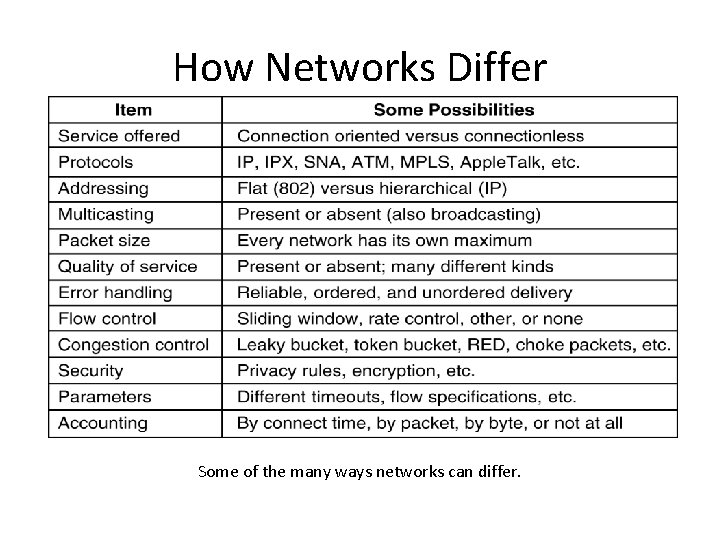
How Networks Differ Some of the many ways networks can differ.

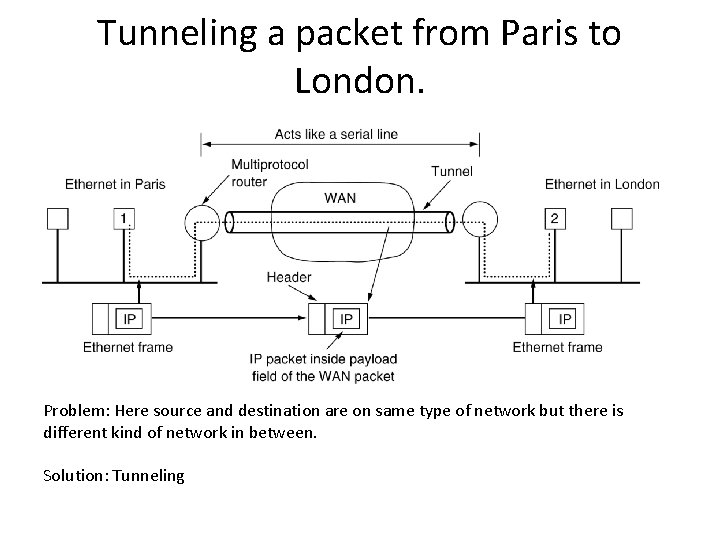
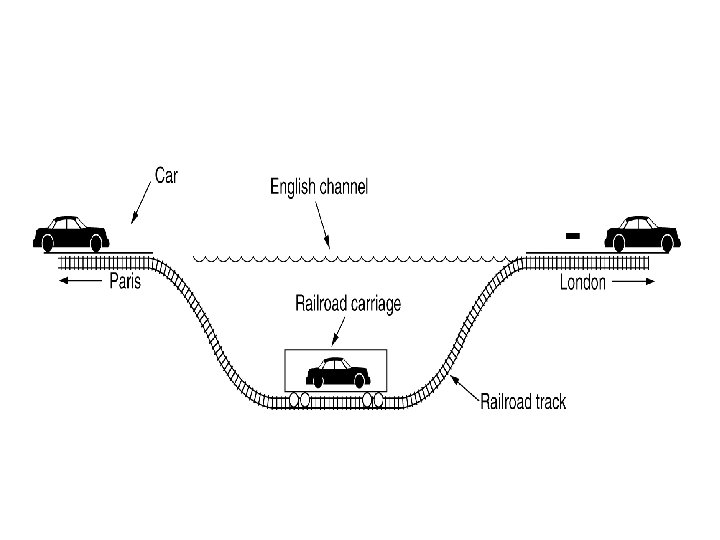
Tunneling a packet from Paris to London. Problem: Here source and destination are on same type of network but there is different kind of network in between. Solution: Tunneling


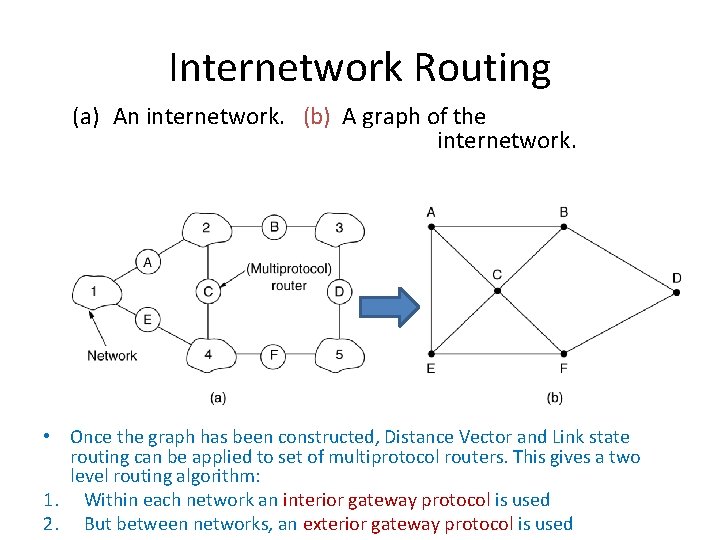
Internetwork Routing (a) An internetwork. (b) A graph of the internetwork. • Once the graph has been constructed, Distance Vector and Link state routing can be applied to set of multiprotocol routers. This gives a two level routing algorithm: 1. Within each network an interior gateway protocol is used 2. But between networks, an exterior gateway protocol is used

Internetwork routing • Requires crossing international boundaries • COST: within a network only one algorithm applies but different networks may be under different managements , so there will be different routes with different cost and quality of service • Within a big internetwork it is difficult to choose best route as it is time consuming. 1. Various laws come in to play like : sweden’s privacy law about exporting personal data about swedish citizen from sweden 2. Canadian law saying data originated from can add and destined in canada may not leave the country.

Fragmentation • Network designers are not free to chose any maximum packet size they wish. ( hardware, od, protocols, error handling) • Problem: when a large packet wants to travel through a network whose max packet size is too small. 1. Solution 1: use routing algorithm that avoid sending packets to route that support small packet size. 2. Fragmentation: divide the big packet into small But reverse process is not easy. ( 2 nd law of thermodynamic) There are two schemes to combine the packets again: a) Transparent b) Non- transparent

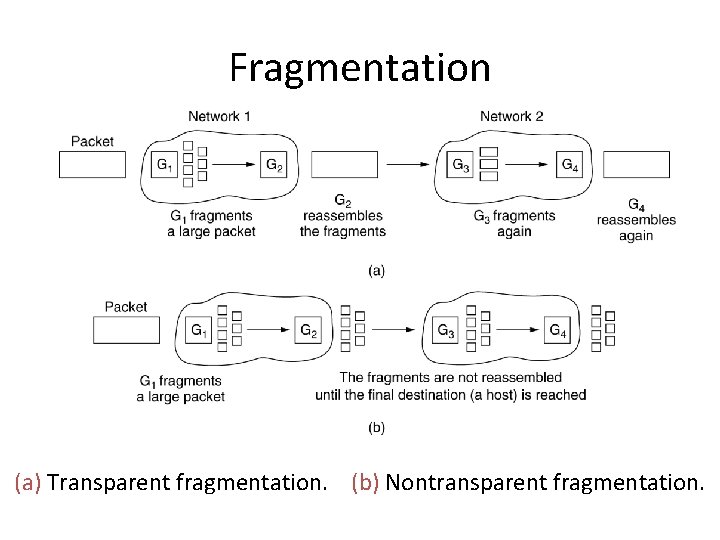
Fragmentation (a) Transparent fragmentation. (b) Nontransparent fragmentation.

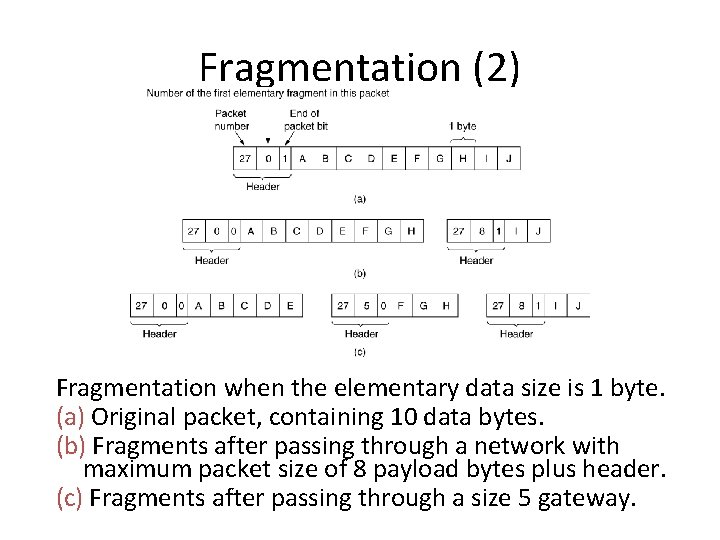
Fragmentation (2) Fragmentation when the elementary data size is 1 byte. (a) Original packet, containing 10 data bytes. (b) Fragments after passing through a network with maximum packet size of 8 payload bytes plus header. (c) Fragments after passing through a size 5 gateway.

The Network Layer in the Internet • • The IP Protocol IP Addresses Internet Control Protocols OSPF – The Interior Gateway Routing Protocol BGP – The Exterior Gateway Routing Protocol Internet Multicasting Mobile IP IPv 6

Design Principles for Internet 1. Make sure it works. 2. Keep it simple. 3. Make clear choices. 4. Exploit modularity. 5. Expect heterogeneity. 6. Avoid static options and parameters. 7. Look for a good design; it need not be perfect. 8. Be strict when sending and tolerant when receiving. 9. Think about scalability. 10. Consider performance and cost.

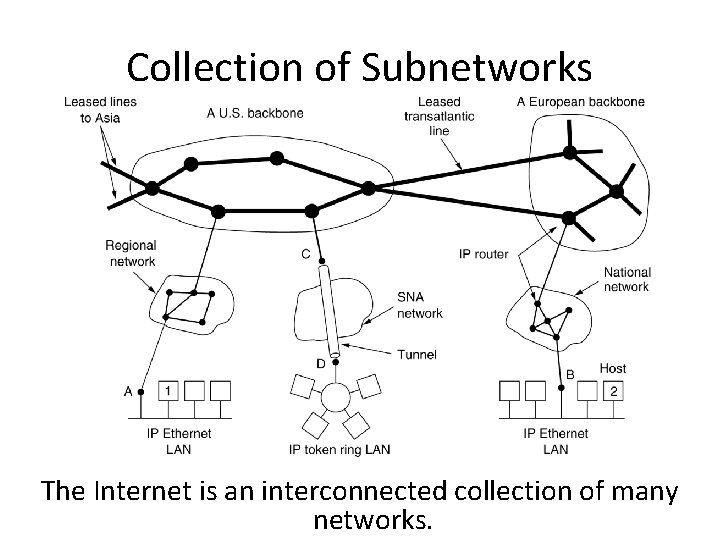
Collection of Subnetworks The Internet is an interconnected collection of many networks.

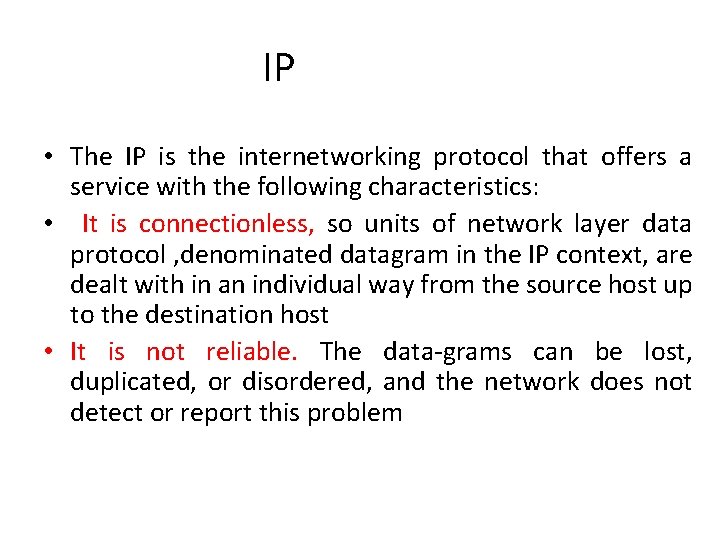
IP • The IP is the internetworking protocol that offers a service with the following characteristics: • It is connectionless, so units of network layer data protocol , denominated datagram in the IP context, are dealt with in an individual way from the source host up to the destination host • It is not reliable. The data-grams can be lost, duplicated, or disordered, and the network does not detect or report this problem

• Part of TCP/IP – Used by the Internet • Specifies interface with higher layer – e. g. TCP • Specifies protocol format and mechanisms • IPv 4 – addresses are 32 bits wide – Its header is 20 bytes at minimum – Uses doted-decimal notation (e. g. 43. 23. 43. 56) • IPv 6 – – Provides larges address domain; addresses are 128 bits wide Multiple separate headers are supported Handles audio and video; providing high quality paths Supports unicast, multicast, anycast


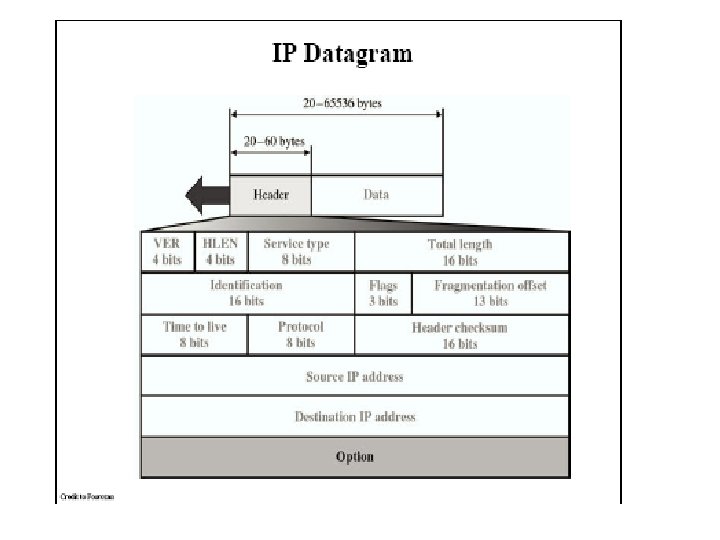
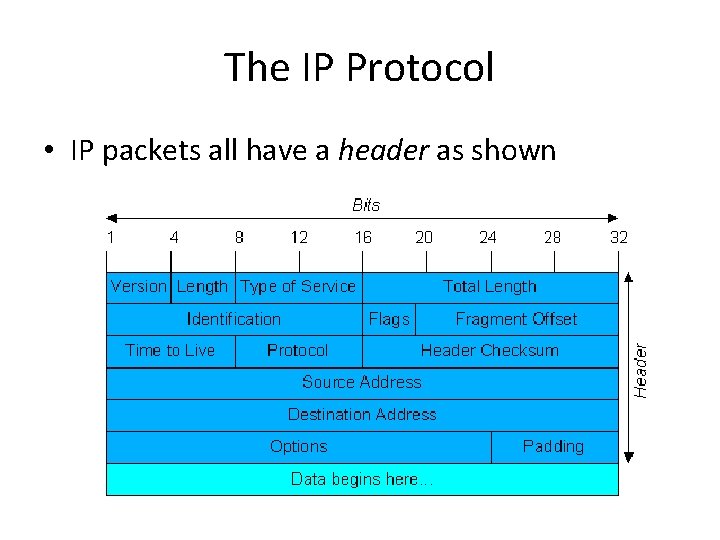
The IP Protocol • IP packets all have a header as shown

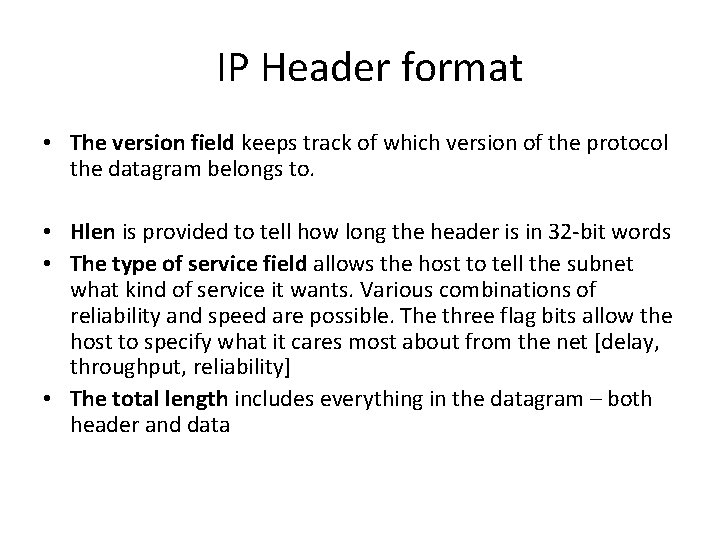
IP Header format • The version field keeps track of which version of the protocol the datagram belongs to. • Hlen is provided to tell how long the header is in 32 -bit words • The type of service field allows the host to tell the subnet what kind of service it wants. Various combinations of reliability and speed are possible. The three flag bits allow the host to specify what it cares most about from the net [delay, throughput, reliability] • The total length includes everything in the datagram – both header and data

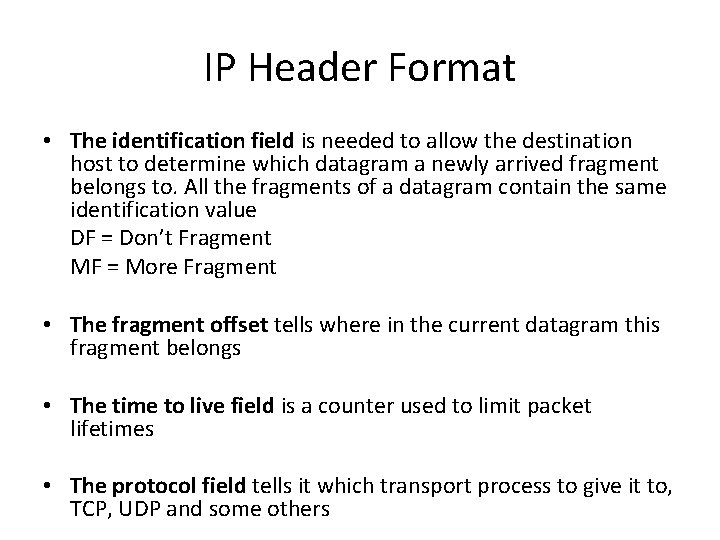
IP Header Format • The identification field is needed to allow the destination host to determine which datagram a newly arrived fragment belongs to. All the fragments of a datagram contain the same identification value DF = Don’t Fragment MF = More Fragment • The fragment offset tells where in the current datagram this fragment belongs • The time to live field is a counter used to limit packet lifetimes • The protocol field tells it which transport process to give it to, TCP, UDP and some others

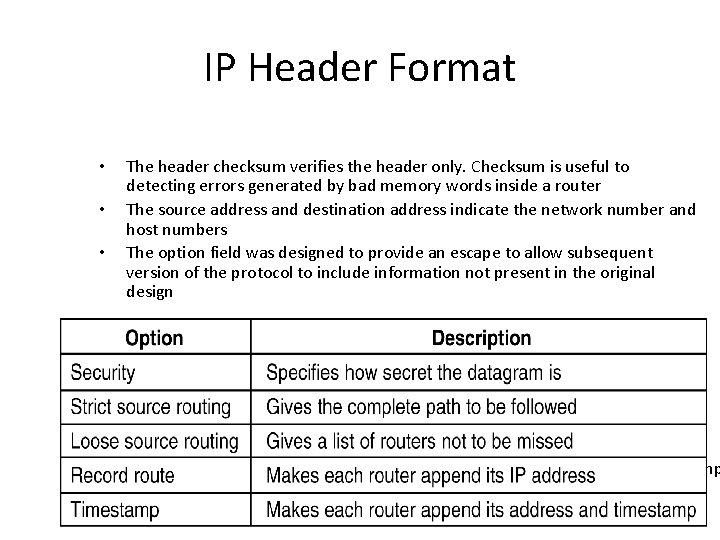
IP Header Format • • • The header checksum verifies the header only. Checksum is useful to detecting errors generated by bad memory words inside a router The source address and destination address indicate the network number and host numbers The option field was designed to provide an escape to allow subsequent version of the protocol to include information not present in the original design Option Security Description Specifies how secret the datagram is Strict source routing Loose source routing Record route Timestamp Gives the complete path to be followed Gives a list of routers not to be missed Makes each router append its IP address Makes each router append its address and timestamp






Internet Control Protocols • IP protocol only deal with the data transfer • We need control protocol to check the network – ICMP, ARP, RARP, BOOTP, HDCP

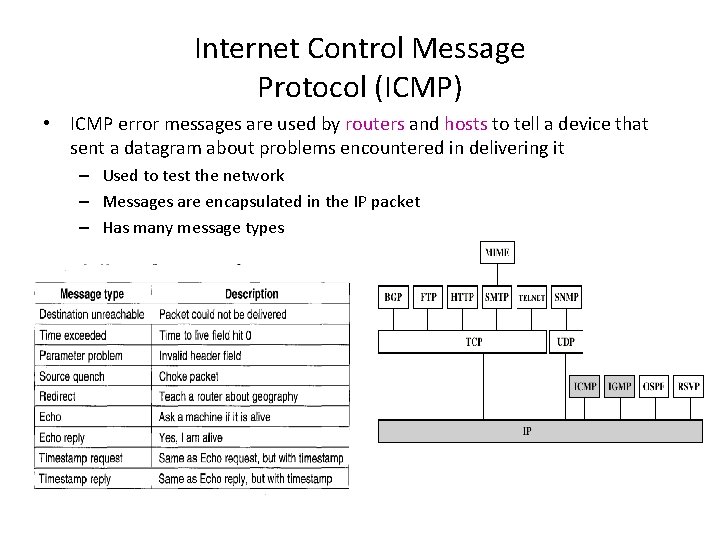
Internet Control Message Protocol (ICMP) • ICMP error messages are used by routers and hosts to tell a device that sent a datagram about problems encountered in delivering it – Used to test the network – Messages are encapsulated in the IP packet – Has many message types

ARP (address resolution protocol) • Exploits broadcast property of a LAN • Each host on LAN maintains a a table of IP subnetwork addresses • If the address can not be found ARP broadcasts a request – Shouting: Who know about this IP address? • Other hosts listen and reply – The reply includes IP address and MAC – Any interested host can learn about the new information

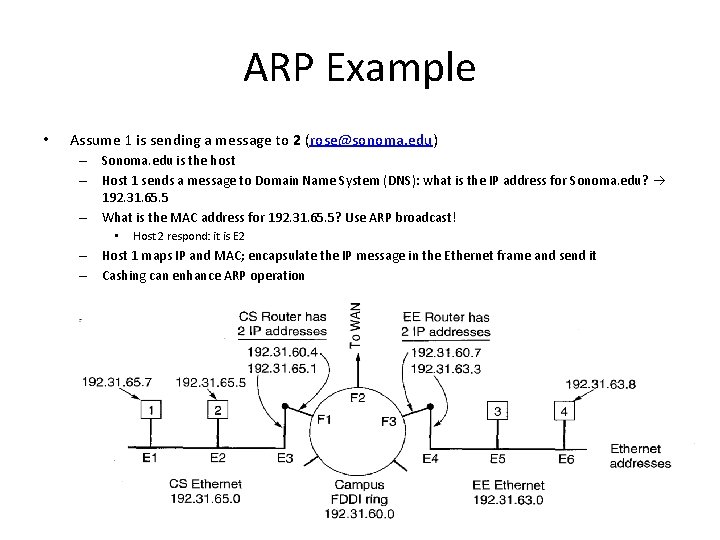
ARP Example • Assume 1 is sending a message to 2 (rose@sonoma. edu) – Sonoma. edu is the host – Host 1 sends a message to Domain Name System (DNS): what is the IP address for Sonoma. edu? 192. 31. 65. 5 – What is the MAC address for 192. 31. 65. 5? Use ARP broadcast! • Host 2 respond: it is E 2 – Host 1 maps IP and MAC; encapsulate the IP message in the Ethernet frame and send it – Cashing can enhance ARP operation

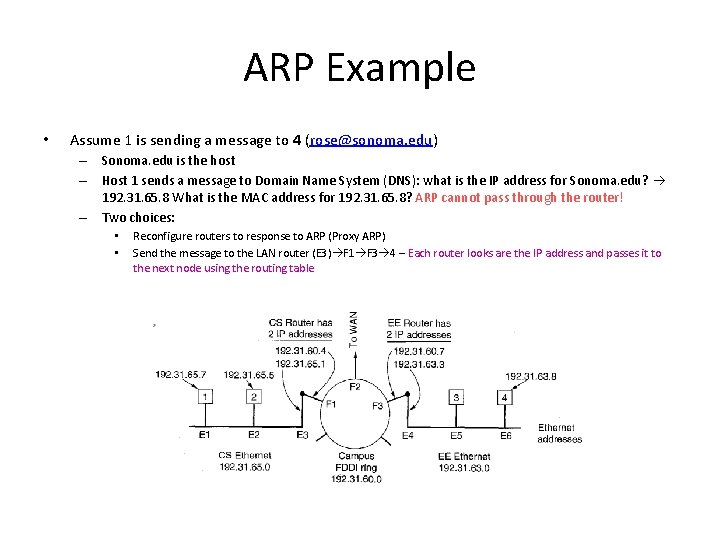
ARP Example • Assume 1 is sending a message to 4 (rose@sonoma. edu) – Sonoma. edu is the host – Host 1 sends a message to Domain Name System (DNS): what is the IP address for Sonoma. edu? 192. 31. 65. 8 What is the MAC address for 192. 31. 65. 8? ARP cannot pass through the router! – Two choices: • • Reconfigure routers to response to ARP (Proxy ARP) Send the message to the LAN router (E 3) F 1 F 3 4 – Each router looks are the IP address and passes it to the next node using the routing table

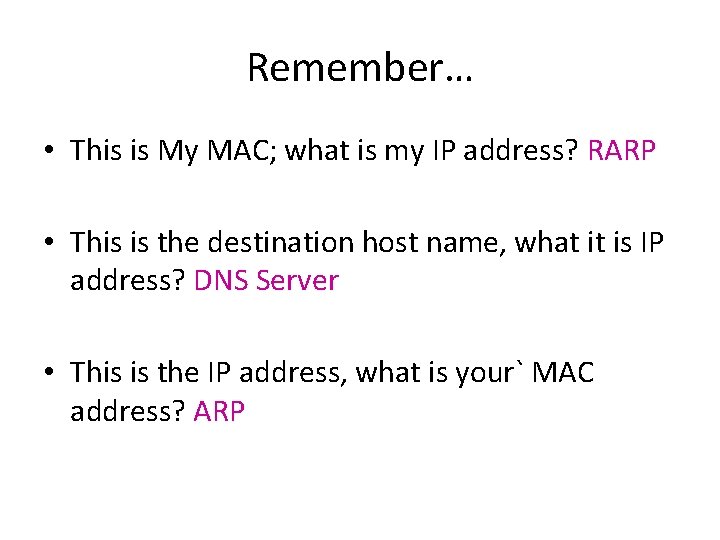
Reverse Address Resolution Protocol (RARP) • Allows a station to determine its IP address from its hardware address • A server can be configured to respond to RARP request automatically allocating IP address across the network • Not used much nowadays, replaced instead by more powerful auto configuration protocols such as DHCP (Dynamic Host Configuration Protocol) [1] A. S. Tanen. Baum, "Computer Networks, " Pearson Education, 2003, pp. 453 -454.

Remember… • This is My MAC; what is my IP address? RARP • This is the destination host name, what it is IP address? DNS Server • This is the IP address, what is your` MAC address? ARP

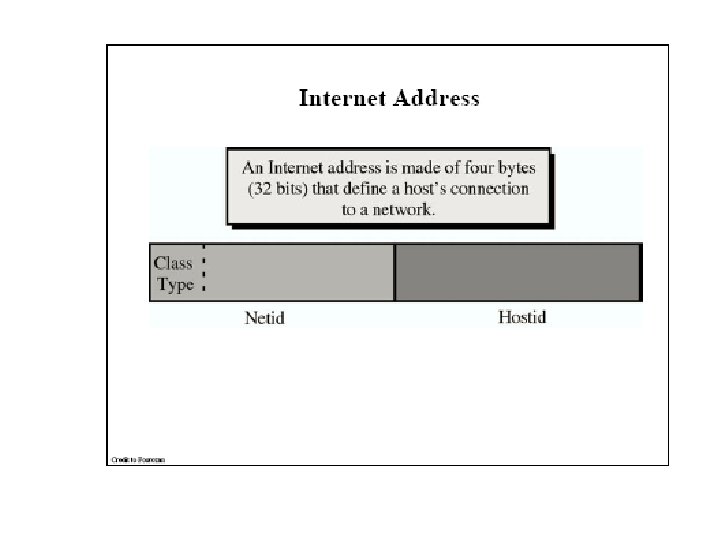
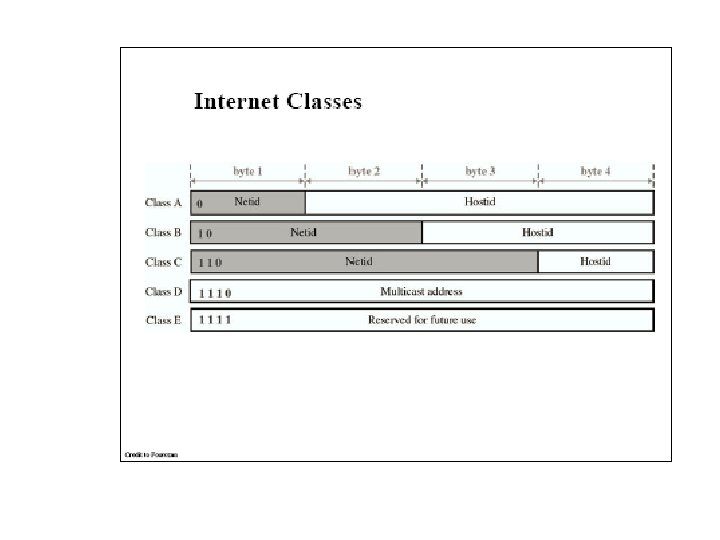
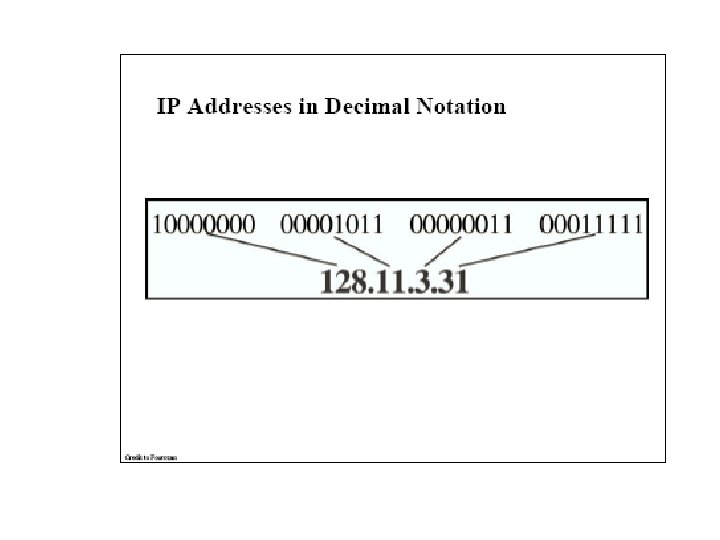
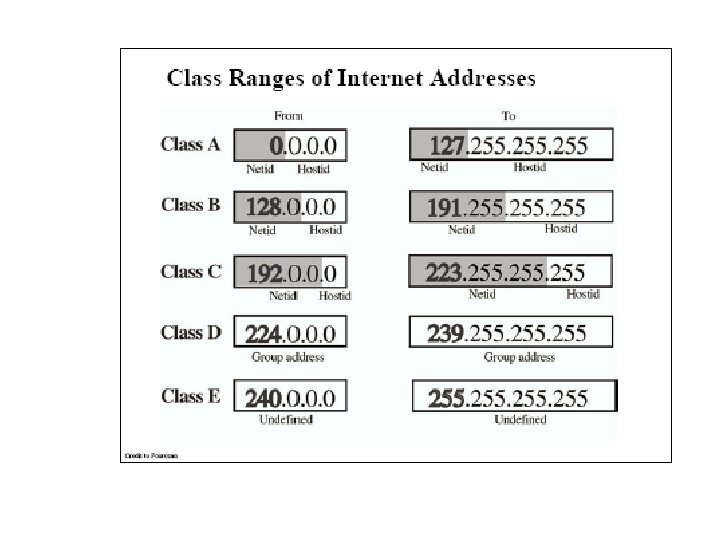
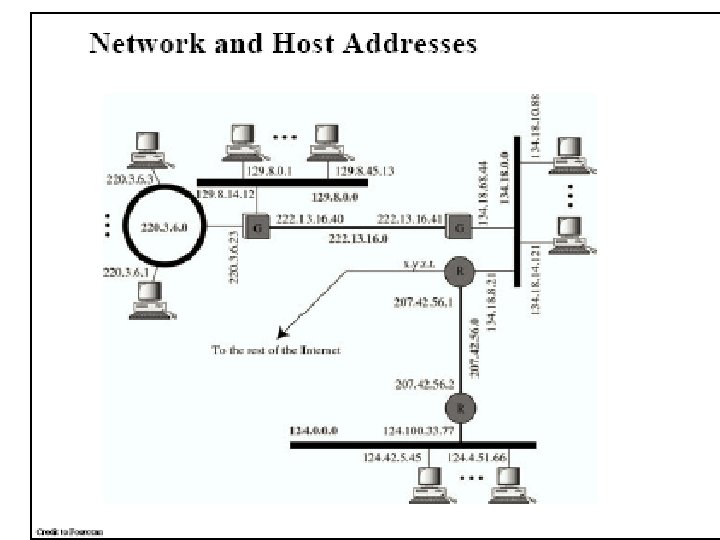
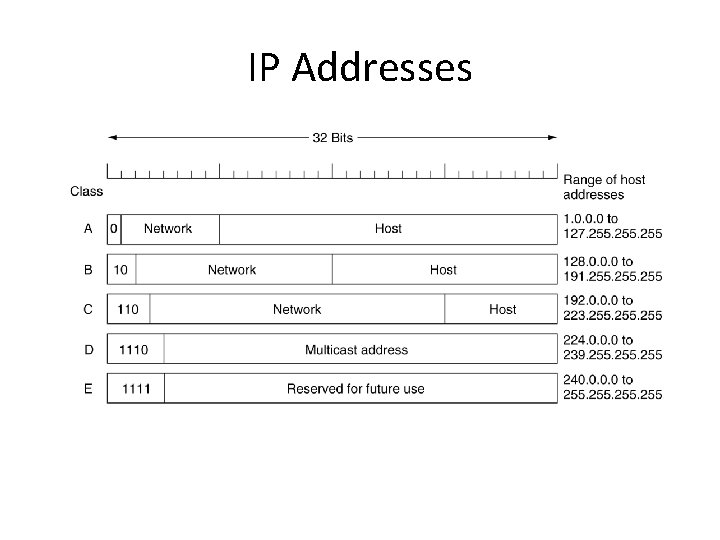
IP Addresses IP address formats.

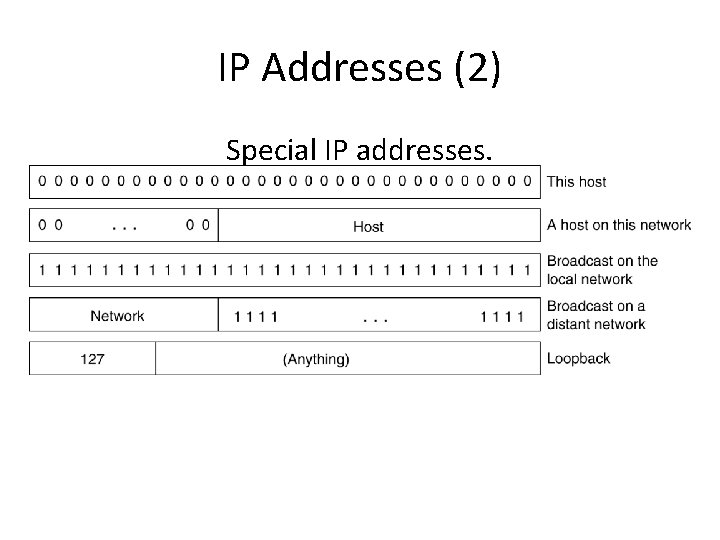
IP Addresses (2) Special IP addresses.