Protocol Layering Chapter 11 Protocol Layering Why is











- Slides: 19

Protocol Layering Chapter 11

Protocol Layering • Why is software broken into modules? • Why is program translation done in steps with distinct functions and output? – Why must those functions expect a precise format of data?

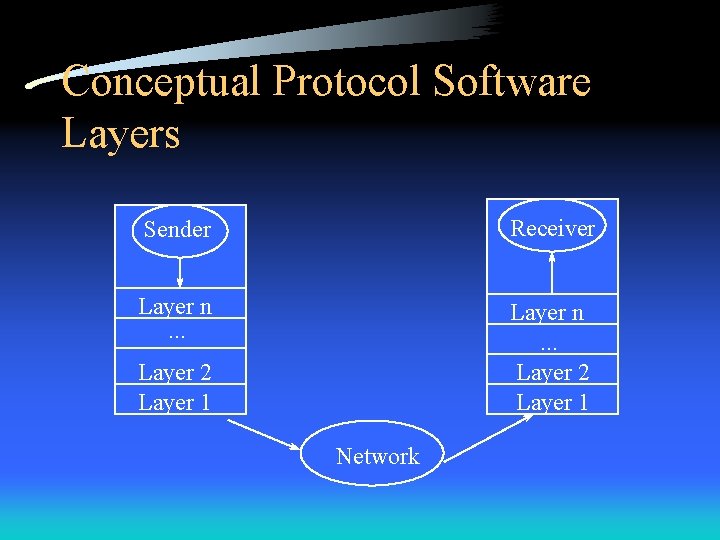
Conceptual Protocol Software Layers Sender Receiver Layer n. . . Layer 2 Layer 1 Network

Conceptual Protocol Software Layers • Sending a message from an application program on one machine to an application program on another machine means: – Transferring a message down through successive layers on the sender’s machine – Forwarding the message across the network – Transferring the message up through successive layers on the receiver’s machine

Conceptual Protocol Software Layers • Each layer makes decisions about the correctness of the message and chooses an appropriate action based on the message type or destination address – Keep the message or forward it to another machine? – Which application program should receive the message? • A more realistic picture is in Figure 11. 2 b, which shows that IP software may deal with multiple high level protocols or multiple network interfaces

ISO Model of Layering • ISO’s 7 layer model – X. 25 had a suite of protocols based on ISO and was widely used – The network operates much like the telephone system • Packet switches have intelligence to route packets • Hosts attach directly to the packet switches by a serial communication line

ISO Model of Layering • ISO Layers – Physical Layer - specifies physical interconnection including specifics on voltage and current – Data Link Layer - defines the format of frames and frame boundaries, error detection, acknowledgements – Network Layer - destination addressing and routing – Transport Layer - end to end reliability, checks that machines in the middle did not fail in transmission – Session Layer - describe how protocol software can be organized to provide functionality for applications

ISO Model of Layering – Presentation Layer - provides functions needed by application programs, such as text compression, graphics conversion into streams – Application Layer - electronic mail, file transfer, etc.

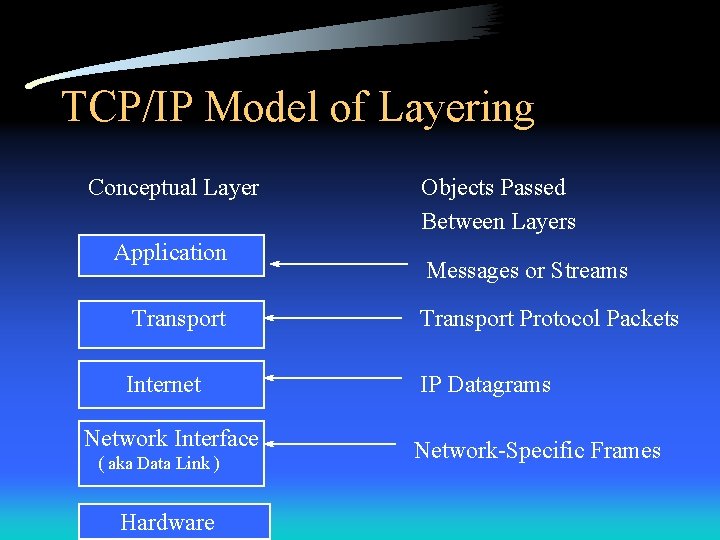
TCP/IP Model of Layering Conceptual Layer Application Objects Passed Between Layers Messages or Streams Transport Protocol Packets Internet IP Datagrams Network Interface ( aka Data Link ) Hardware Network-Specific Frames

TCP/IP Model of Layering • TCP/IP Layers – Network Interface - accepts IP datagrams and transmits them over a network (device driver or specific data link protocol) – Internet - routing and delivery of datagrams – Transport - provides communication from one application program on one machine to another (end-toend communication), adds codes to header indicating the application involved – Application - individual messages or continuous stream of bytes

Differences between ISO and Internet Layering • The ISO model handles errors at all layers, checksums, acknowledgments (including timeout and retransmission) are used • TCP/IP assumes that reliability is an end-to-end problem and handles it in the transport layer – the internet is built to handle expected load, but data may be lost along the way – this assumption makes the software simpler to understand implement – detection and recovery of datagram loss is handled by source and destination hosts

Differences between ISO and Internet Layering • Networks using X. 25 assume that the network vendor provides a transport service – the network controls network access, monitors traffic for billing, handles routing, flow control, acknowledgements, etc. – the network is complex • TCP/IP expects the hosts to implement those types of functions – routing (they choose a router), handling ICMP traffic – the network is simple, intelligence is in the hosts

The Protocol Layering Principle • Layered protocols are designed so that layer n at the destination receives exactly the same object sent by layer n at the source • This allows the protocol designer to focus on one layer at a time • See Figures 11. 6 and 11. 7 • In the higher layers, the layering principle applies across end-to-end transfers • At the lowest layer, it applies to transfer from one machine to a directly connected machine

Point-to-Point Connections • Recall the ARPANET design in which each host was connected to one of 22 ports on a PSN • The set of such point-to-point connections can function like a single network or like a set of networks • Acting like a single network – use a single IP address for and provide new functionality to provide for intranetwork routing • Acting like a set of networks

Boundaries in TCP/IP Model • Boundary between the network interface layer and the Internet layer – above the boundary only IP addresses are used – below the boundary only hardware addresses are used • Boundary between the application layer and the transport layer – the application layer is considered outside the operating system – the transport layer is considered part of the operating system

The Disadvantage of Layering • Software can be inefficient – the transport layer may not know what the Internet layer is doing, so instead of choosing the largest possible packet size from the beginning, it will not know what that size is • The strict layering scheme can be relaxed – information like route selection and network MTU can be made known

Multiplexing and Demultiplexing • The source sends a message and includes extra bits indicating message type, originating program and protocols used • Eventually, all messages are placed into frames and multiplexed, or combined into a stream • The destination network interface decodes, or demultiplexes, the messages as seen in Figure 11. 10 • Both occur at almost every protocol layer

Summary • Protocols – are the standards that specify how data is represented when transferred from one machine to another – specify how the transfer occurs, how errors are detected, how acknowledgements are passed • Communication problems are segregated into subproblems that can be solved independently • Witha layered approach, each subproblem is handled by a separate layer

For Next Time • Read Chapter 12