In the Name of the Most High SNMPv





- Slides: 30

In the Name of the Most High SNMPv 3 by Behzad Akbari Fall 2008 1

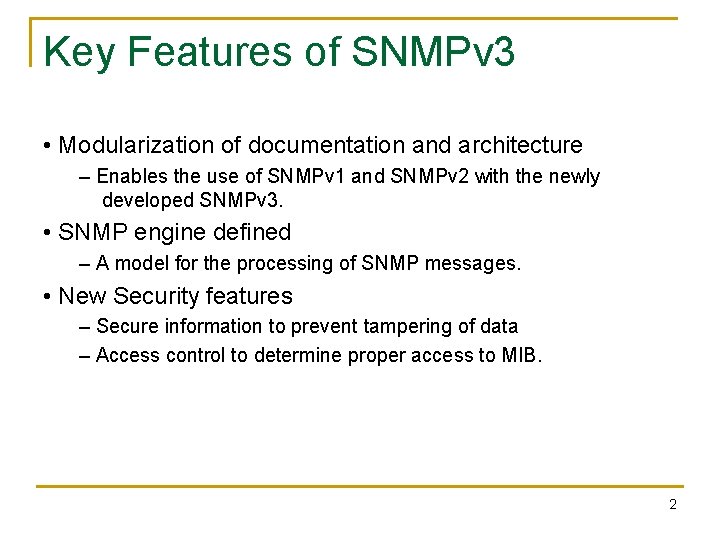
Key Features of SNMPv 3 • Modularization of documentation and architecture – Enables the use of SNMPv 1 and SNMPv 2 with the newly developed SNMPv 3. • SNMP engine defined – A model for the processing of SNMP messages. • New Security features – Secure information to prevent tampering of data – Access control to determine proper access to MIB. 2

Documentation 3

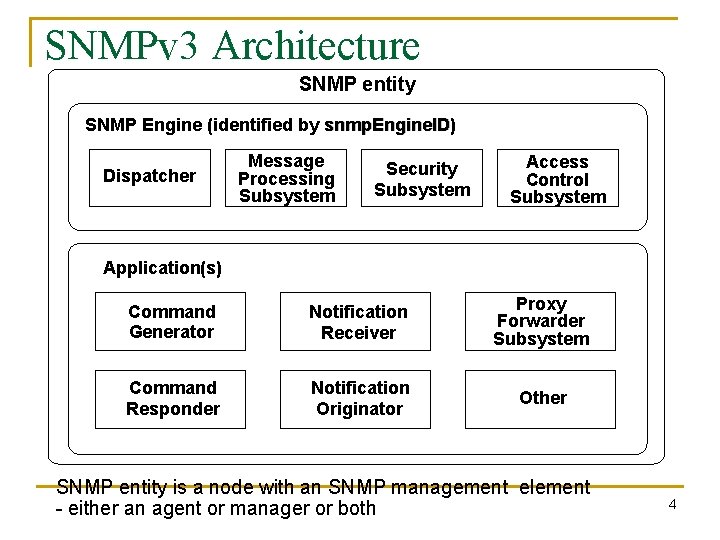
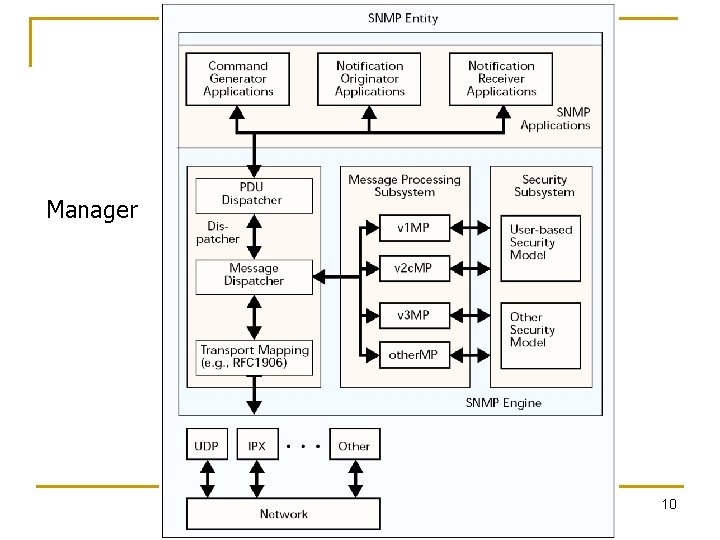
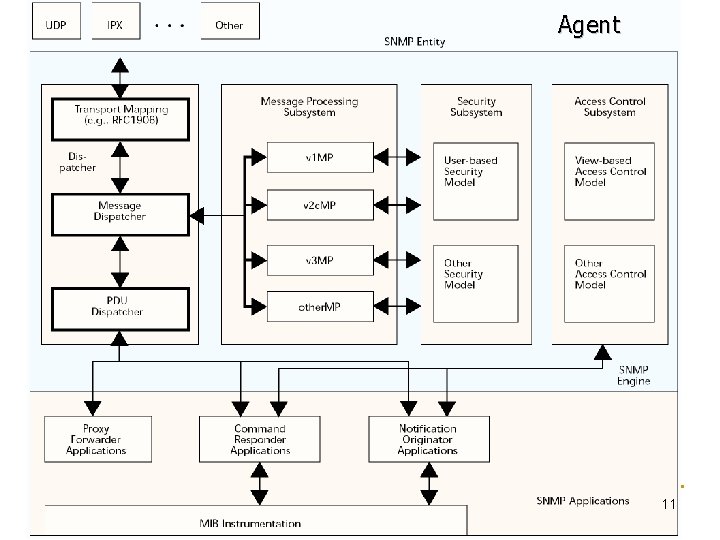
SNMPv 3 Architecture SNMP entity SNMP Engine (identified by snmp. Engine. ID) snmp. Engine. ID Dispatcher Message Processing Subsystem Security Subsystem Access Control Subsystem Application(s) Command Generator Notification Receiver Proxy Forwarder Subsystem Command Responder Notification Originator Other SNMP entity is a node with an SNMP management element - either an agent or manager or both 4

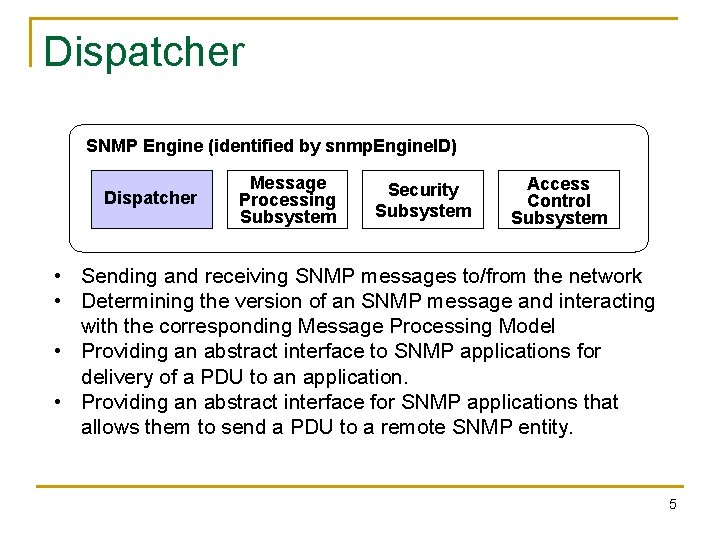
Dispatcher SNMP Engine (identified by snmp. Engine. ID) Dispatcher Message Processing Subsystem Security Subsystem Access Control Subsystem • Sending and receiving SNMP messages to/from the network • Determining the version of an SNMP message and interacting with the corresponding Message Processing Model • Providing an abstract interface to SNMP applications for delivery of a PDU to an application. • Providing an abstract interface for SNMP applications that allows them to send a PDU to a remote SNMP entity. 5

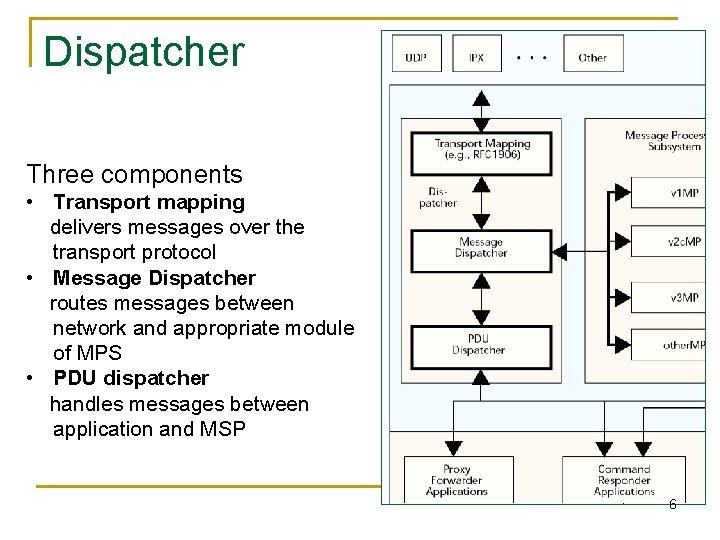
Dispatcher Three components • Transport mapping delivers messages over the transport protocol • Message Dispatcher routes messages between network and appropriate module of MPS • PDU dispatcher handles messages between application and MSP 6

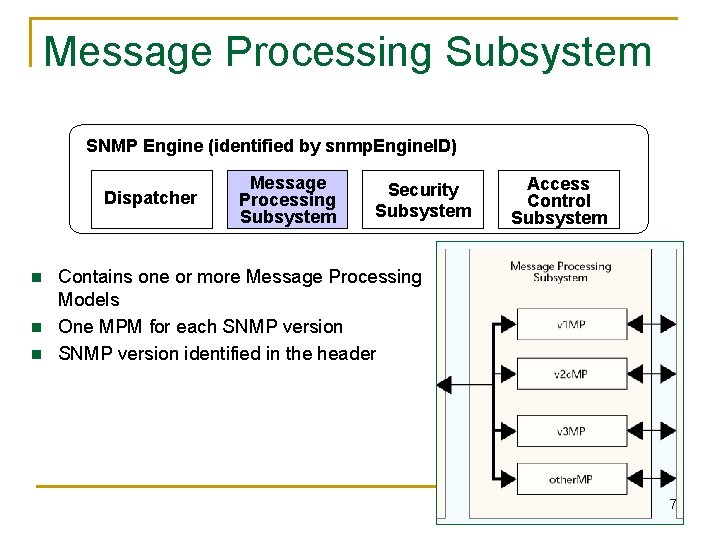
Message Processing Subsystem SNMP Engine (identified by snmp. Engine. ID) Dispatcher n n n Message Processing Subsystem Security Subsystem Access Control Subsystem Contains one or more Message Processing Models One MPM for each SNMP version identified in the header 7

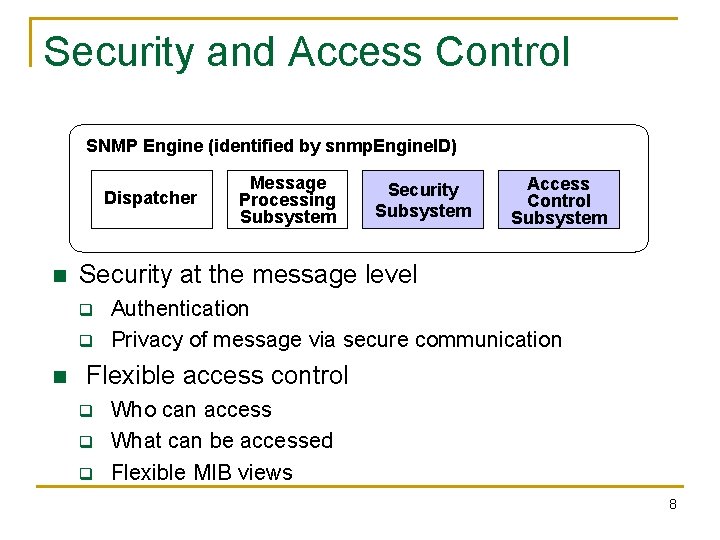
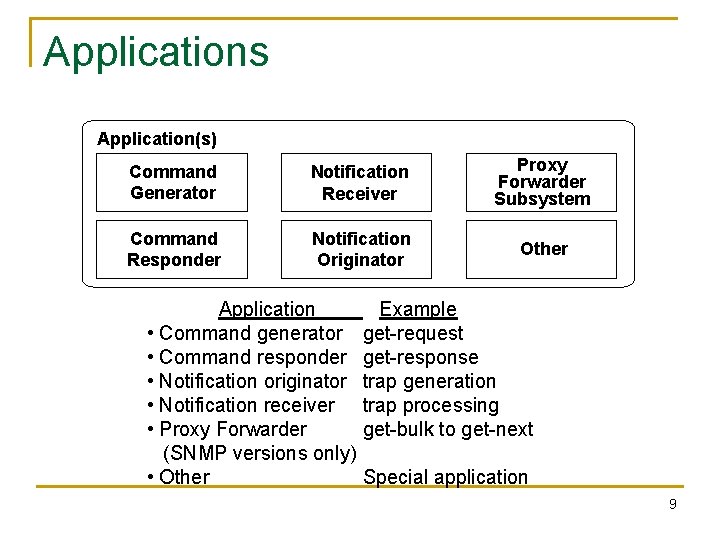
Security and Access Control SNMP Engine (identified by snmp. Engine. ID) Dispatcher n Security Subsystem Access Control Subsystem Security at the message level q q n Message Processing Subsystem Authentication Privacy of message via secure communication Flexible access control q q q Who can access What can be accessed Flexible MIB views 8

Applications Application(s) Command Generator Notification Receiver Proxy Forwarder Subsystem Command Responder Notification Originator Other Application • Command generator • Command responder • Notification originator • Notification receiver • Proxy Forwarder (SNMP versions only) • Other Example get-request get-response trap generation trap processing get-bulk to get-next Special application 9

Manager 10

Agent 11

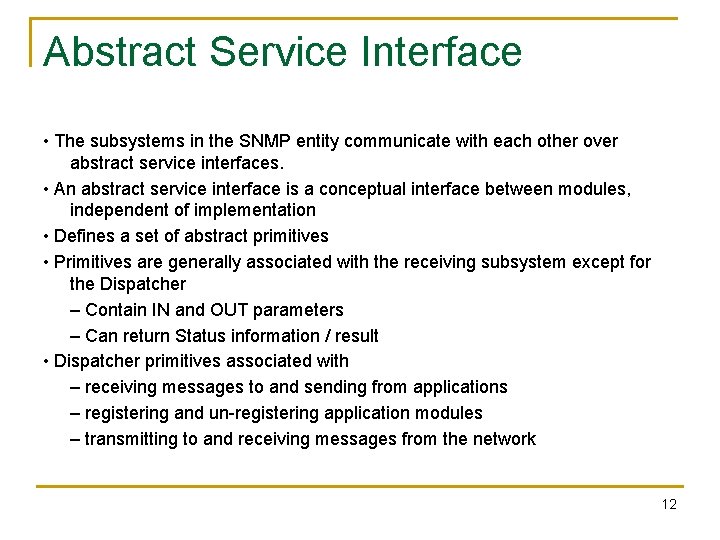
Abstract Service Interface • The subsystems in the SNMP entity communicate with each other over abstract service interfaces. • An abstract service interface is a conceptual interface between modules, independent of implementation • Defines a set of abstract primitives • Primitives are generally associated with the receiving subsystem except for the Dispatcher – Contain IN and OUT parameters – Can return Status information / result • Dispatcher primitives associated with – receiving messages to and sending from applications – registering and un-registering application modules – transmitting to and receiving messages from the network 12

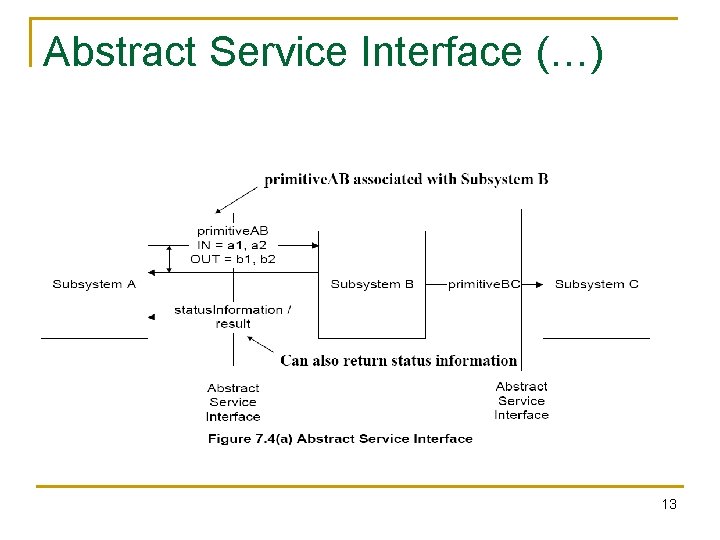
Abstract Service Interface (…) 13

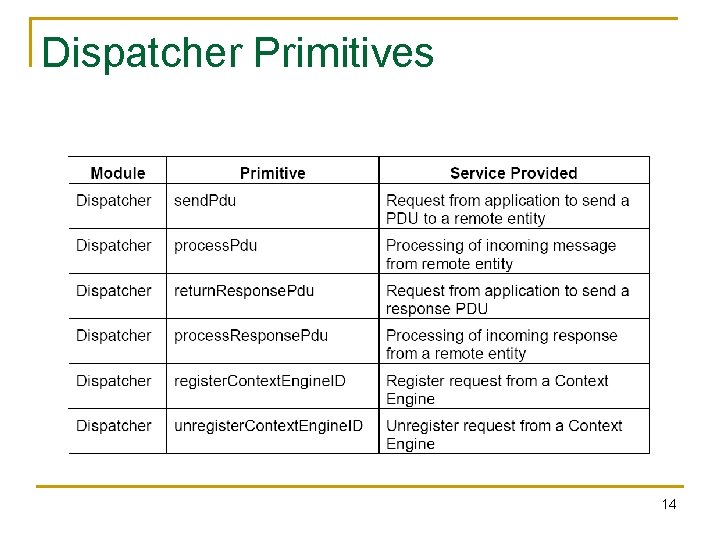
Dispatcher Primitives 14

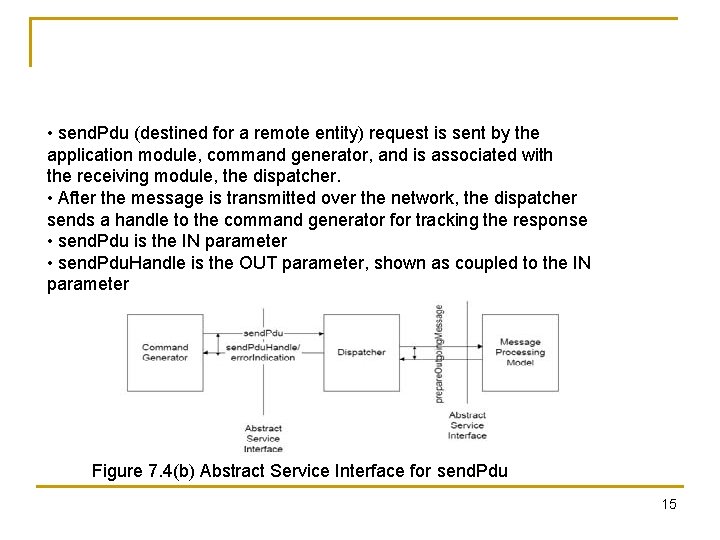
• send. Pdu (destined for a remote entity) request is sent by the application module, command generator, and is associated with the receiving module, the dispatcher. • After the message is transmitted over the network, the dispatcher sends a handle to the command generator for tracking the response • send. Pdu is the IN parameter • send. Pdu. Handle is the OUT parameter, shown as coupled to the IN parameter Figure 7. 4(b) Abstract Service Interface for send. Pdu 15

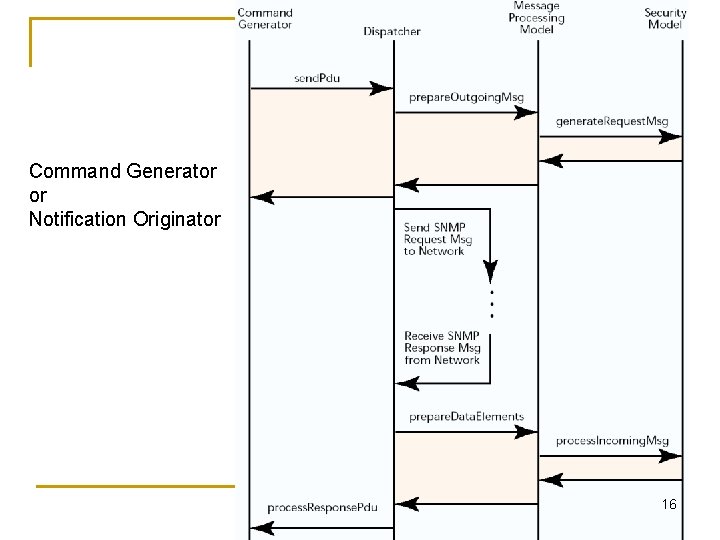
Command Generator or Notification Originator 16

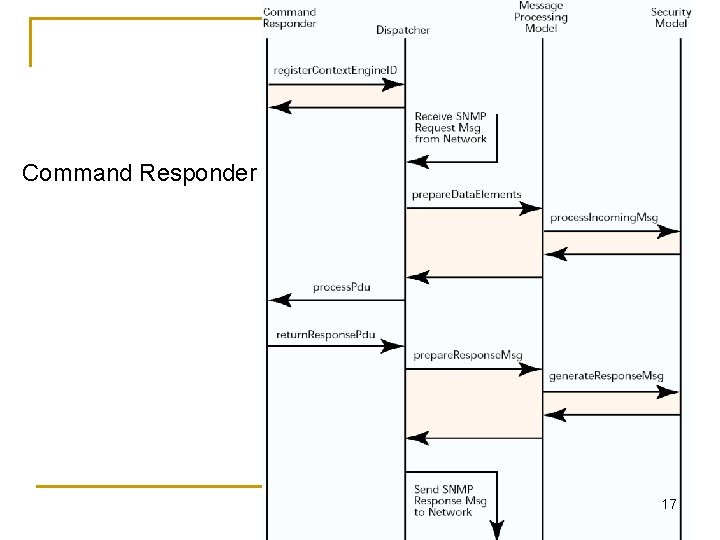
Command Responder 17

Names n n n Entity Engine (snmp. Engine. ID) q Associated with each SNMP entity is a unique snmp. Engine. ID. Context (context. Name) q A context is a collection of management information accessible by an SNMP entity. Context engine (context. Engine. ID) q = snmp. Engine. ID Principal (security. Name) q the "who" on whose behalf services are provided or processing takes place. q may be an individual or an application or a group of individuals or applications. 18

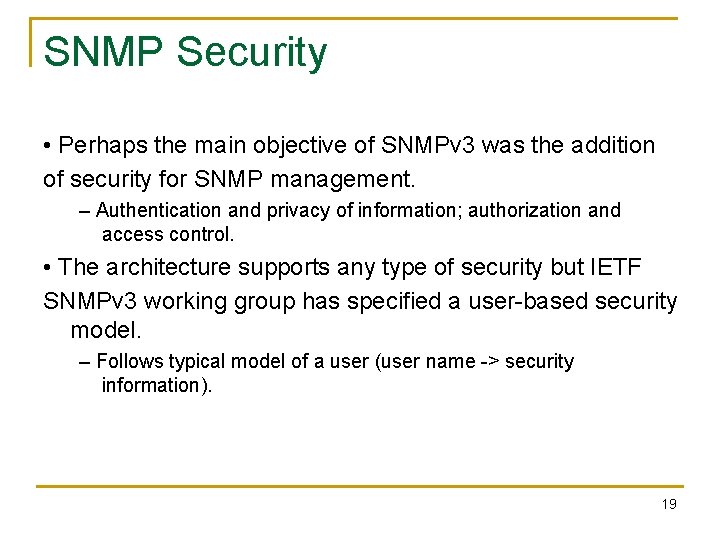
SNMP Security • Perhaps the main objective of SNMPv 3 was the addition of security for SNMP management. – Authentication and privacy of information; authorization and access control. • The architecture supports any type of security but IETF SNMPv 3 working group has specified a user-based security model. – Follows typical model of a user (user name -> security information). 19

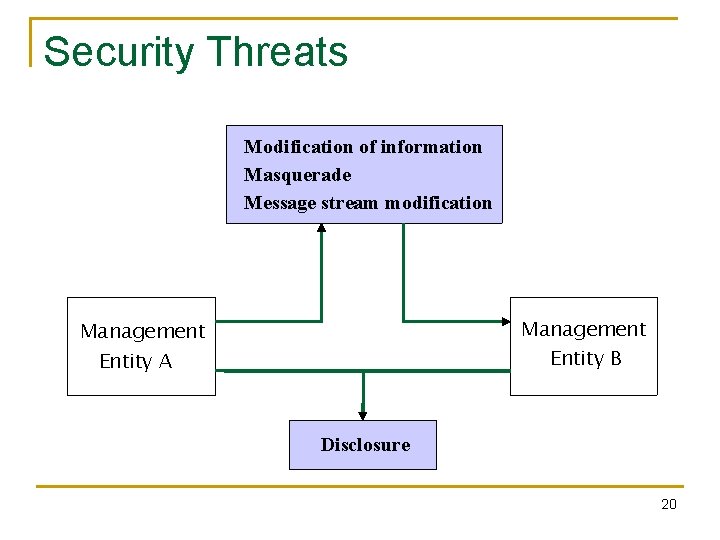
Security Threats Modification of information Masquerade Message stream modification Management Entity B Management Entity A Disclosure 20

Security Threats n SNMPv 3 security model is developed to protect the following security threats: q Modification of information n Contents modified by unauthorized user q Masquerade n change of originating address by unauthorized user q Message Stream Modification n Re-ordering, delay or replay of messages q Disclosure n Eavesdropping 21

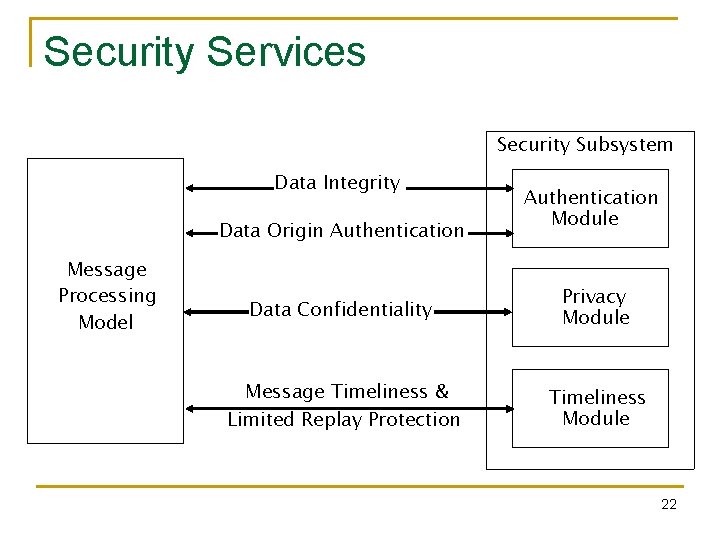
Security Services Security Subsystem Data Integrity Data Origin Authentication Message Processing Model Authentication Module Data Confidentiality Privacy Module Message Timeliness & Limited Replay Protection Timeliness Module 22

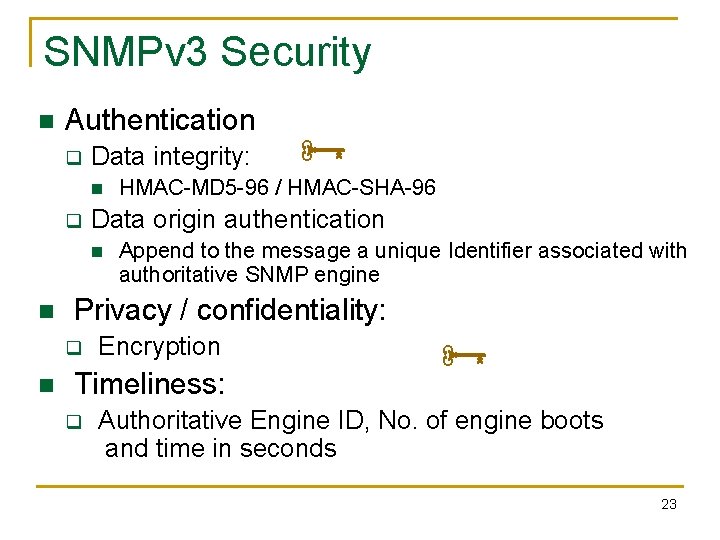
SNMPv 3 Security n Authentication q Data integrity: n q Append to the message a unique Identifier associated with authoritative SNMP engine Privacy / confidentiality: q n HMAC-MD 5 -96 / HMAC-SHA-96 Data origin authentication n n Encryption Timeliness: q Authoritative Engine ID, No. of engine boots and time in seconds 23

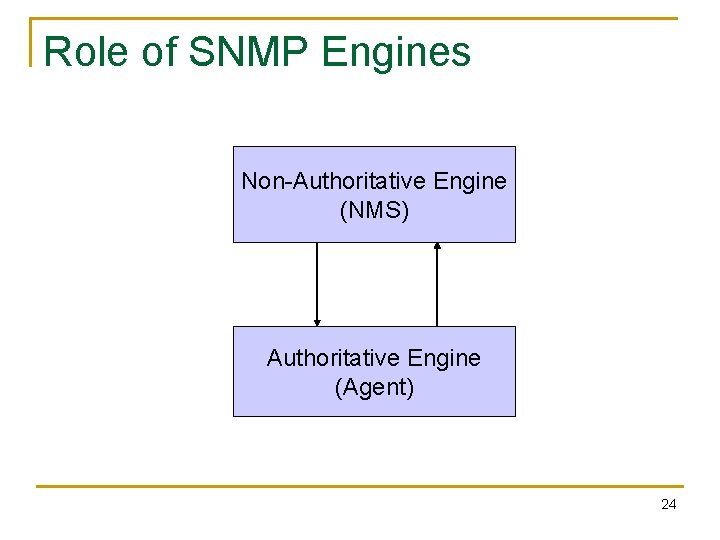
Role of SNMP Engines Non-Authoritative Engine (NMS) Authoritative Engine (Agent) 24

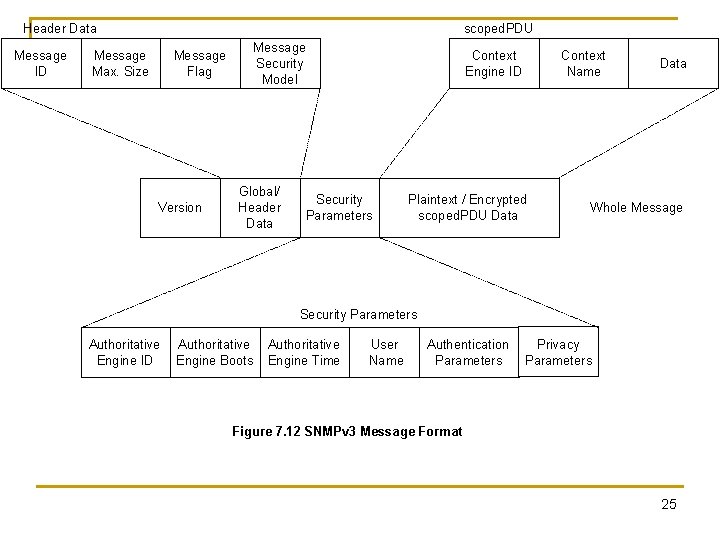
Header Data Message ID scoped. PDU Message Max. Size Message Security Model Message Flag Version Global/ Header Data Context Engine ID Security Parameters Context Name Plaintext / Encrypted scoped. PDU Data Whole Message Security Parameters Authoritative Engine ID Authoritative Engine Boots Authoritative Engine Time User Name Authentication Parameters Privacy Parameters Figure 7. 12 SNMPv 3 Message Format 25

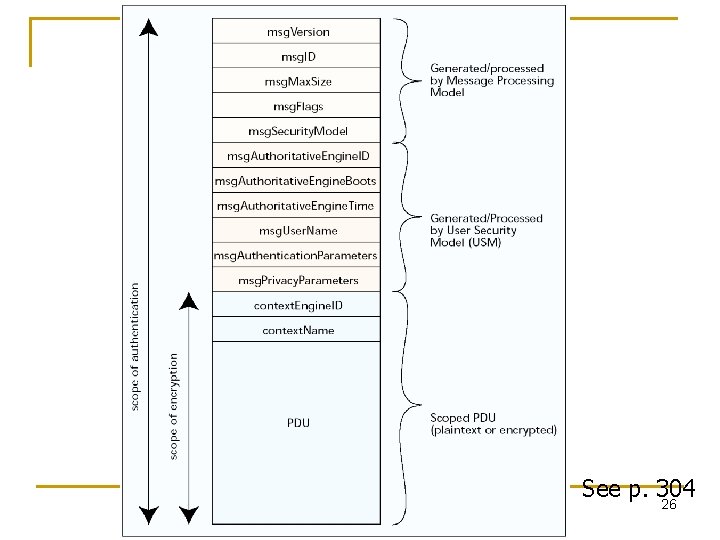
See p. 304 26

User-Based Security Model n n Based on traditional user name concept Authentication service primitives q q n authenticate. Outgoing. Msg authenticate. Incoming. Msg Privacy Services q q encrypt. Data decrypt. Data 27

28

29

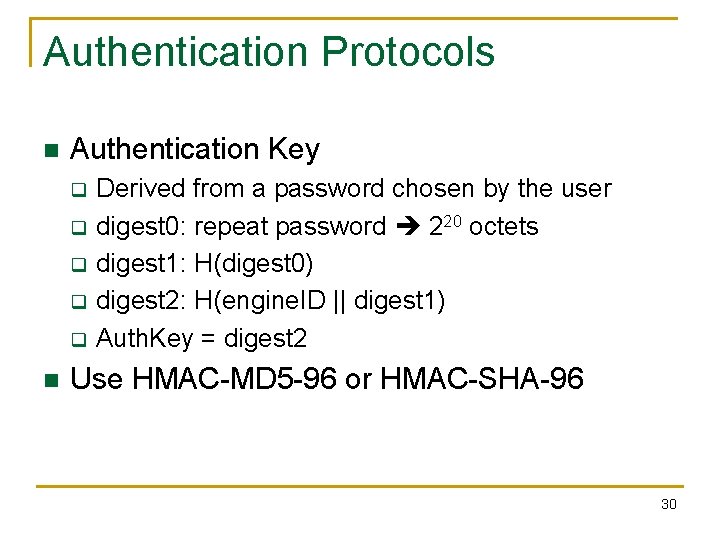
Authentication Protocols n Authentication Key q q q n Derived from a password chosen by the user digest 0: repeat password 220 octets digest 1: H(digest 0) digest 2: H(engine. ID || digest 1) Auth. Key = digest 2 Use HMAC-MD 5 -96 or HMAC-SHA-96 30
 Snmp 2 vs 3
Snmp 2 vs 3 Cisco arp table
Cisco arp table Snmpv
Snmpv Snmpv
Snmpv Snmpv
Snmpv Arquitectura snmp
Arquitectura snmp Snmpv
Snmpv Snmpv
Snmpv Network management principles
Network management principles Snmpv
Snmpv In the name of allah the most gracious
In the name of allah the most gracious In the name of allah the most beneficent the most merciful
In the name of allah the most beneficent the most merciful سsh
سsh In the name of allah the most beneficent the most merciful
In the name of allah the most beneficent the most merciful In the name of god most gracious prayer
In the name of god most gracious prayer In the name of allah the most gracious the most merciful
In the name of allah the most gracious the most merciful In the name of allah the most
In the name of allah the most The most gracious
The most gracious Aqeedah
Aqeedah In the name of god most gracious prayer
In the name of god most gracious prayer In the name of allah the most beneficent
In the name of allah the most beneficent Lord most high be magnified
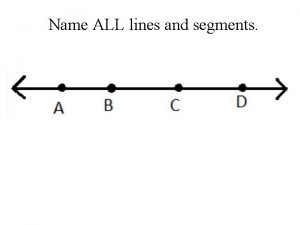
Lord most high be magnified Name all the lines
Name all the lines Most general to most specific classification
Most general to most specific classification Most general to most specific classification
Most general to most specific classification Organisms taxonomy
Organisms taxonomy Arrangement of organisms
Arrangement of organisms Most high glorious god
Most high glorious god Most colonists placed a high value on education
Most colonists placed a high value on education When the most high divided the nations
When the most high divided the nations High precision vs high recall
High precision vs high recall