In Confidence Putting In Place A Trade Secret






















- Slides: 32

In Confidence: Putting In Place A Trade Secret Protection Program Najmia Rahimi Innovation Division Kingston, Jamaica 4 – 6 June 2012

What are trade secrets? Do-it-yourself form of IP Idea: By keeping valuable information secret, you can prevent competitors from learning about and using it and thereby enjoy a competitive advantage in the marketplace.

General principles: Information that has commercial value. and that has been kept confidential will be considered a trade secret (TS). Owner will be entitled to court relief against those who have stolen or divulged it in an illegal manner.

Question What kind of information qualifies as a trade secret?

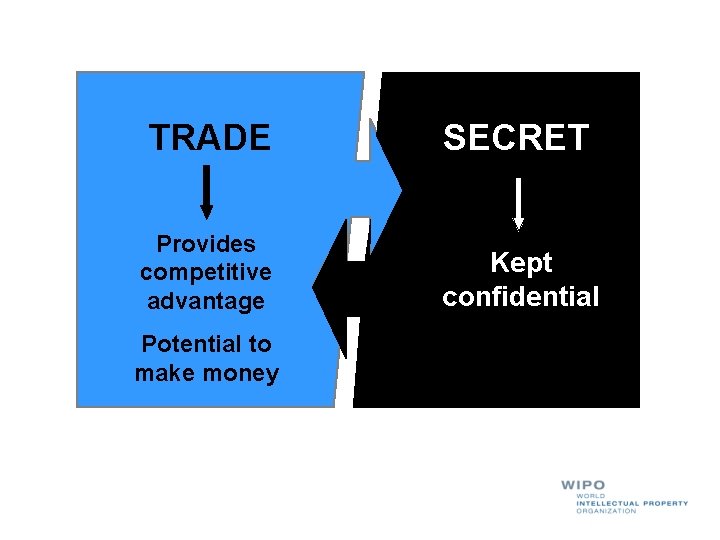
TRADE SECRET Provides competitive advantage Kept confidential Potential to make money

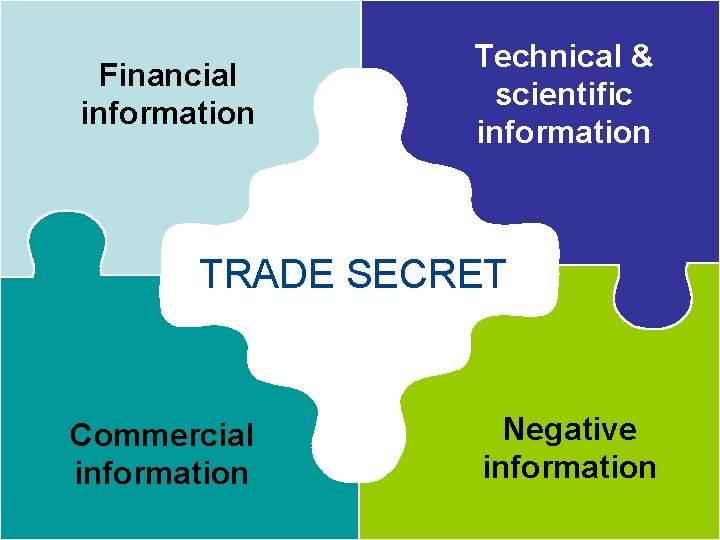
Financial information Technical & scientific information TRADE SECRET Commercial information Negative information

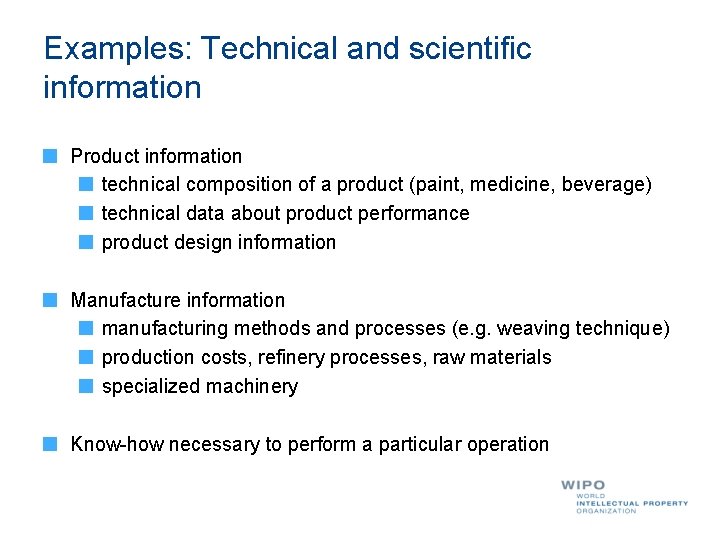
Examples: Technical and scientific information Product information technical composition of a product (paint, medicine, beverage) technical data about product performance product design information Manufacture information manufacturing methods and processes (e. g. weaving technique) production costs, refinery processes, raw materials specialized machinery Know-how necessary to perform a particular operation

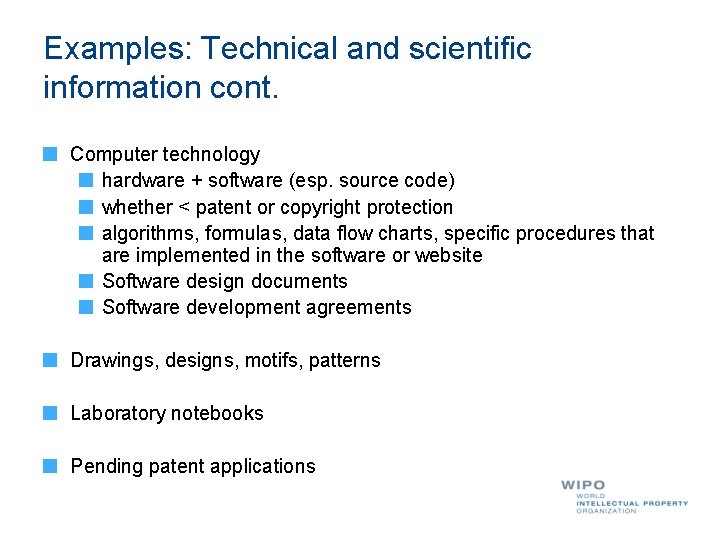
Examples: Technical and scientific information cont. Computer technology hardware + software (esp. source code) whether < patent or copyright protection algorithms, formulas, data flow charts, specific procedures that are implemented in the software or website Software design documents Software development agreements Drawings, designs, motifs, patterns Laboratory notebooks Pending patent applications

Examples: Commercial information Customer lists Customer profiles, buying preferences, requirements Business plans and strategies New product names Supplier arrangements Sales methods Personnel performance Info re: new business opportunities

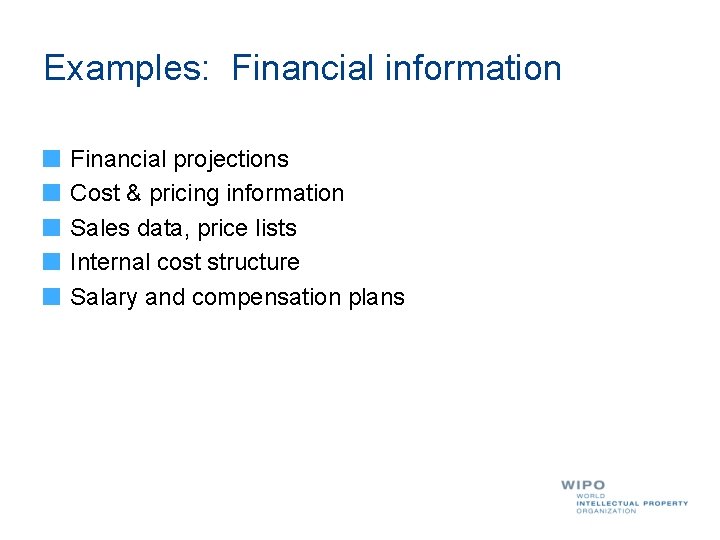
Examples: Financial information Financial projections Cost & pricing information Sales data, price lists Internal cost structure Salary and compensation plans

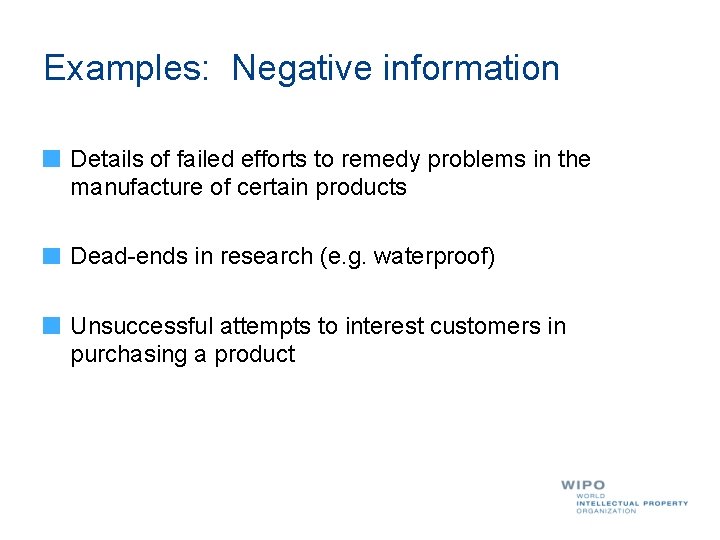
Examples: Negative information Details of failed efforts to remedy problems in the manufacture of certain products Dead-ends in research (e. g. waterproof) Unsuccessful attempts to interest customers in purchasing a product

What’s a Trade Secret? Let’s start with the Norden Case! Past ten years the IT specialist A was working in a company A in high-tech designs application business. Starting this year, A was hired by the company Norden which produces T-Shirts and another apparel. During the first weeks of his work in Norden, A developed a new very efficient process of application 3 D images on Tshirts. The manager of Norden asked A how he made such invention which worked perfectly. The specialist A said that he had gotten certain knowledge from the previous company he used to work at. The manager of Norden was surprised and asked if such information was not secret. A said that he did not hear about anything ‘secret’ in the previous company…

What’s a Trade Secret? Going back to the Norden Case… Past ten years the IT specialist A was working in a company A in high-tech designs application business. Starting this year, A was hired by the company Norden which produces T-Shirts and another apparel. During the first weeks of his work in Norden, A developed a new very efficient process of application 3 D images on Tshirts. The manager of Norden asked A how he made such invention which worked perfectly. The specialist A said that he had gotten certain knowledge from the previous company he used to work at. The manager of Norden was surprised and asked if such information was not secret. A said that he did not hear about anything ‘secret’ in the previous company…

One of the most famous examples: formula of Coca-Cola drink

Pros and Cons of Trade Secret Protection Advantages No registration, therefore, no registration costs Immediate effect No other substantive requirements to be met (e. g. of novelty or originality) No disclosure requirement No written description requirement Unlimited period of protection

Pros and Cons of Trade Secret Protection Disadvantages Difficult to maintain for a longer period Limited scope of protection, more difficult enforcement of rights No protection against legitimate discovery of the same information, invention, etc. by others (e. g. through ‘reverse engineering’) No possibility to stop others from developing the same invention by legitimate means (protection against improper acquisition, use or disclosure of confidential information only)

How to build up a trade secret management program in a company? Going back to the Norden Case… What should have been done by the company A (where the IT specialist A was previously working) in order he, later hired by Norden, did not take ‘secret’ information from the company A? What steps should the company A have taken?

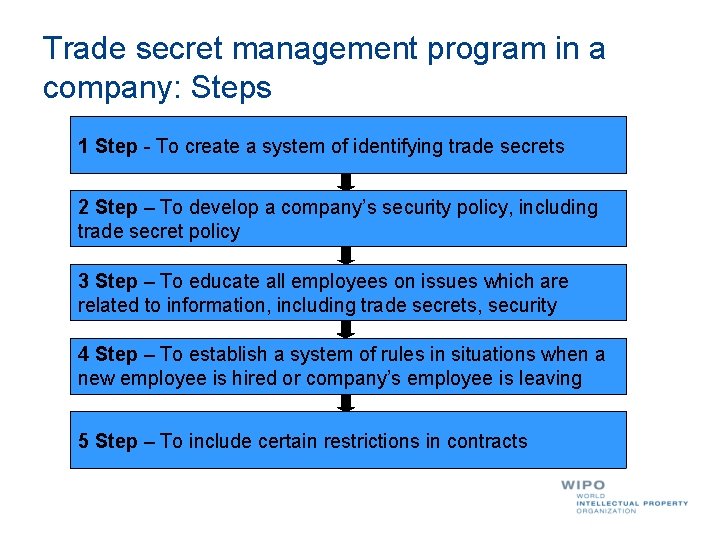
Trade secret management program in a company: Steps 1 Step - To create a system of identifying trade secrets 2 Step – To develop a company’s security policy, including trade secret policy 3 Step – To educate all employees on issues which are related to information, including trade secrets, security 4 Step – To establish a system of rules in situations when a new employee is hired or company’s employee is leaving 5 Step – To include certain restrictions in contracts

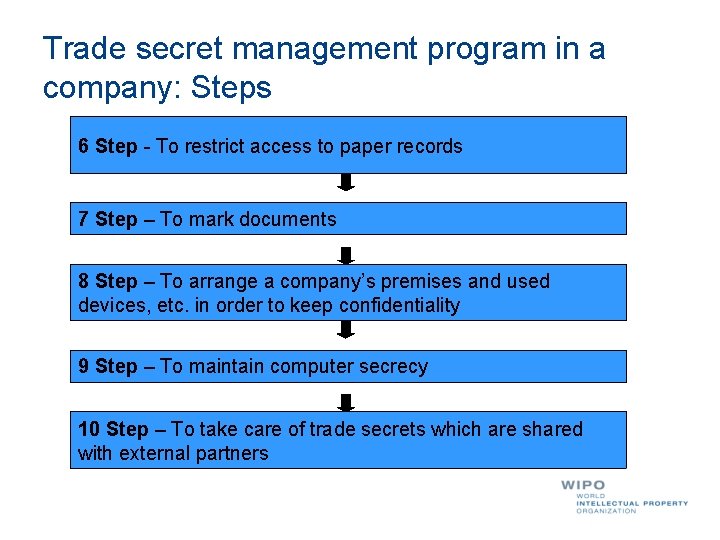
Trade secret management program in a company: Steps 6 Step - To restrict access to paper records 7 Step – To mark documents 8 Step – To arrange a company’s premises and used devices, etc. in order to keep confidentiality 9 Step – To maintain computer secrecy 10 Step – To take care of trade secrets which are shared with external partners

How trade secrets get stolen? Further in the Norden Case… The employee A explained to the manager of Norden that he had found a description of an improved chemical composition of the glue and specific printing material in a waste-paper basket in the company A. He said he had compared that information with the information he could find in the confidential documents’ folder saved on the company’s A servers. The manager of Norden was very much surprised how the employee A could have had an access to such documents, as it usually requires a password. A explained that he took that password from his colleague who had actually ‘hacked’ it.

Misappropriation of trade secrets 1. Unfair acquisition of trade secret That is, theft, fraud, coercion, industrial espionage or other unlawful or dishonest acts.

Misappropriation of trade secrets 2. Acquisition of a trade secret with knowledge about its prior illegal acquisition, or without such knowledge, but being grossly negligent in falling to know such previous illegal act, and, in any case, using or disclosing trade secret acquired in such a way.

Misappropriation of trade secrets 3. After a trade secret was acquired innocently, using or disclosing it after learning about its prior illegal acquisition by another person.

Misappropriation of trade secrets 4. Using or disclosing a trade secret in breach of contractual obligations to maintain the trade secret. 4. 1. Acquisition of a trade secret that was disclosed while breaching contractual obligations (knowing or with gross negligence about this fact), and using or disclosing such trade secret. 4. 2. After a trade secret was acquired by innocently breaching contractual obligations, using or disclosing it after learning about the breach of contractual obligations or being grossly negligent in falling to learn about such illegal act.

How trade secrets get stolen: What would be your comments on the Norden Case? The employee A explained to the manager of Norden that he had found a description of an improved chemical composition of glue and materials for printing on textile in a waste-paper basket in the company A. He said he had compared that information with the information he could find in the internal documents folder saved on the company’s A servers. The manager of Norden was very much surprised how the employee A could have had an easy access to such documents, as it usually requires a password. A explained that he took that password from his colleague who had actually ‘hacked’ it.

Protection of trade secrets Most countries do not have specific laws on trade secrets. Protection of trade secrets is established in: Civil Laws In Unfair Competition Laws (for instance, in Germany) In Contract Law (in many countries) In Criminal Law (for instance, in the EU countries, USA, Russia)

How to establish violation of trade secrets? 1 - To clarify if information was secret 2 – To establish if reasonable steps were taken to maintain this information secret 3 - To show that infringement was made or competitive advantage was gained by misappropriating a trade secret by a person/company 4 – To establish that there was a misuse of a trade secret in violation of honest business practices

Remedies Against Violations of Trade Secrets Court order to stop illegal acts (injunction) Monetary compensation (damages, lost of profits, unjust enrichment, etc. ) Seizure order (to check defendant’s premises, to take evidence, etc. ) Precautionary confiscation/seizure of articles that contain trade secrets or products resulting from their use/misuse Destruction of infringing articles In some countries, imposition of punitive damages

Audit of Trade Secrets Coming back to the Norden Case… The general manager of Norden is planning an audit of information possessed by his company, including also all confidential information. The manager arranged a meeting with his human resources and other departments in order to discuss the main aspects of such audit, but first he wants to know the main steps of an audit procedure. What would be those main steps?

Audit of Trade Secrets: Steps Identification of most important trade secrets Consultations with R&D division Sales, marketing and human resources Information management Contacts with customers, etc. Verification of a company’s ownership over those trade secrets Checking all documents, contracts, assignments, licenses, etc.

Audit of Trade Secrets: Steps Verification that confidentiality procedures are duly followed Contacting human resources, security departments which maintain trade secrets Verification that employees and all third persons do not disclose trade secrets Contacting human resources department in order to establish if contracts include confidentiality clauses To clarify what confidentiality means are taken so far, as far as external persons are concerned

Thank You Najmia. rahimi@wipo. int
 Is worthy a scam
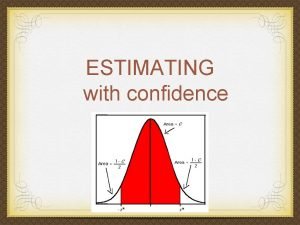
Is worthy a scam Confidence interval z value
Confidence interval z value Confidence interval vs confidence level
Confidence interval vs confidence level Let’s begin our discussion now
Let’s begin our discussion now Trademark and trade secret
Trademark and trade secret Trade secret valuation
Trade secret valuation Draw your secret place
Draw your secret place Trade diversion and trade creation
Trade diversion and trade creation Liner shipping and tramp shipping
Liner shipping and tramp shipping The trade in the trade-to-gdp ratio
The trade in the trade-to-gdp ratio Ted talk atlantic slave trade
Ted talk atlantic slave trade Trade diversion and trade creation
Trade diversion and trade creation Fair trade not free trade
Fair trade not free trade Trade diversion and trade creation
Trade diversion and trade creation Trade diversion and trade creation
Trade diversion and trade creation How did hongwu bring stability to china
How did hongwu bring stability to china Disturbance that transfers energy from place to place
Disturbance that transfers energy from place to place Millions billions trillions chart
Millions billions trillions chart A repeating disturbance that transfers energy
A repeating disturbance that transfers energy Putting the enterprise into the enterprise system
Putting the enterprise into the enterprise system Putting-out system
Putting-out system Putting it all together motion answer key
Putting it all together motion answer key When was the loom invented
When was the loom invented Putting things together is called
Putting things together is called Putting on the new man
Putting on the new man Practice putting it all together part 1 fill in the blank
Practice putting it all together part 1 fill in the blank Sculpture is created by shaping or combining the materials
Sculpture is created by shaping or combining the materials Putting objects in perspective
Putting objects in perspective Putting it all to bed during project closeout includes
Putting it all to bed during project closeout includes Shoulder width stance
Shoulder width stance How to classify a polynomial
How to classify a polynomial Ordering fractions with different denominators
Ordering fractions with different denominators Putting-out system
Putting-out system