ICOM 6115 Computer Networks and the WWW Manuel




- Slides: 34

ICOM 6115 – Computer Networks and the WWW Manuel Rodriguez-Martinez, Ph. D. Lecture 19 ICOM 6115 ©Manuel Rodriguez-Martinez

Lecture Objectives • Finish Loose end on 802. 11 b • Present Local Internetworking – Bridges – VLANs • Introduction to Global Internetworking – Layer 3 – The Network Layer – IP Protocol ICOM 6115 ©Manuel Rodriguez-Martinez

Collisions and IEEE 802. 11 • 802. 11 is a collision avoidance system – Sender A and receiver B first negotiate and agree to start a session – Nearby hosts notice this and refrain themselves from speaking • Also they won’t talk to either A or B until getting “permission” – Collisions are avoided hosts first ask permission to speak – Details on book … ICOM 6115 ©Manuel Rodriguez-Martinez

Local Internetworking • Problem: – LANs can quickly grow to 100 s or 1000 s of hosts – Switches, hubs and lines cannot handle this – Too much traffic going around • Increase chance of collisions • Solution: – Segment the LAN into regions – Each region has related hosts • i. e. Department, floor, laboratory – Isolate and filter traffic for better performance ICOM 6115 ©Manuel Rodriguez-Martinez

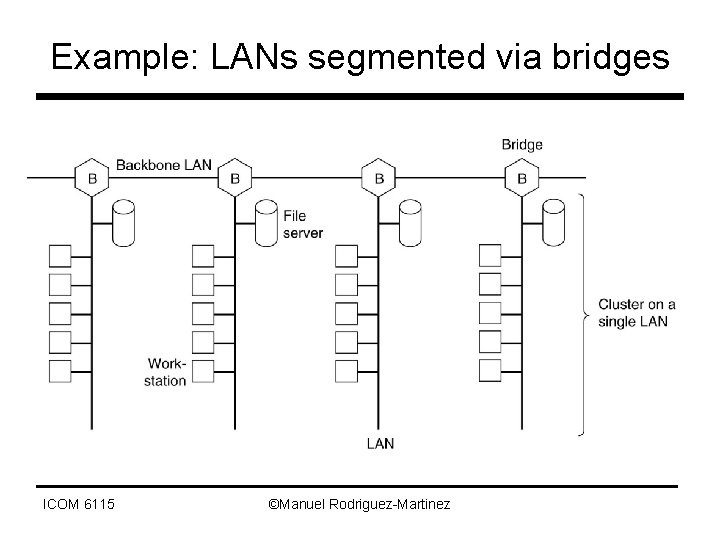
How is this done? • Bridges and Switches – Devices that do forwarding at Layer 2 • Recall that routers do forwarding at Layer 3 • Bridges – Devices that connect different LAN segments • Switches – Connect computers and create virtual LANs (VLANs) inside the switch • Coloring scheme to identify hosts on a VLAN ICOM 6115 ©Manuel Rodriguez-Martinez

Example: LANs segmented via bridges ICOM 6115 ©Manuel Rodriguez-Martinez

Benefits of bridges • Transparency – Hosts need not be aware of bridges • Scalability – Limits collisions and control traffic • Reliability – Isolate hardware and link failures to a segment • Security – Control what frames can be seen • Put all sensitive machine on a given segment • Ease of Management – Organize staff by segments ICOM 6115 ©Manuel Rodriguez-Martinez

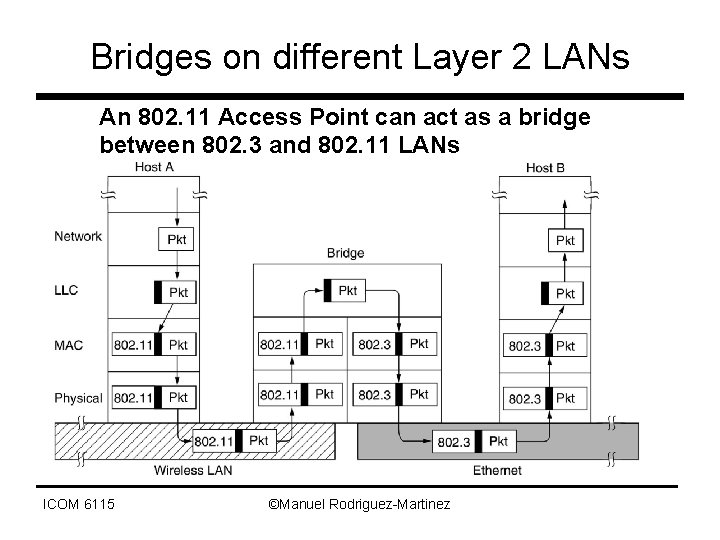
Bridges on different Layer 2 LANs An 802. 11 Access Point can act as a bridge between 802. 3 and 802. 11 LANs ICOM 6115 ©Manuel Rodriguez-Martinez

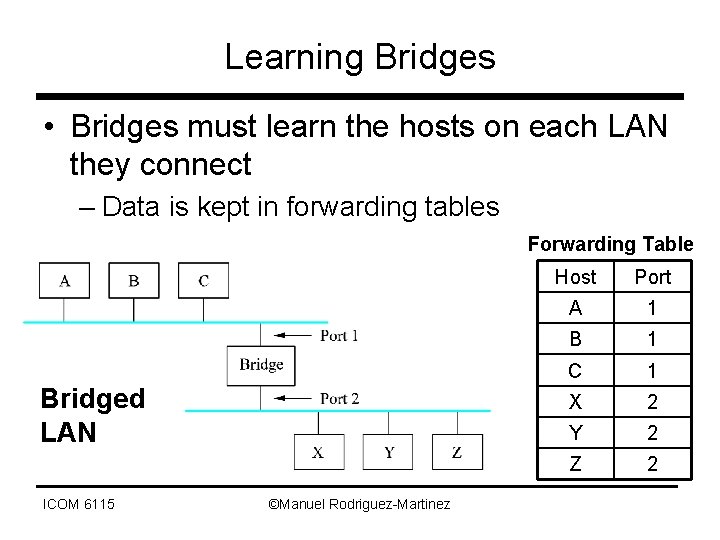
Learning Bridges • Bridges must learn the hosts on each LAN they connect – Data is kept in forwarding tables Forwarding Table Bridged LAN ICOM 6115 ©Manuel Rodriguez-Martinez Host Port A 1 B 1 C 1 X 2 Y 2 Z 2

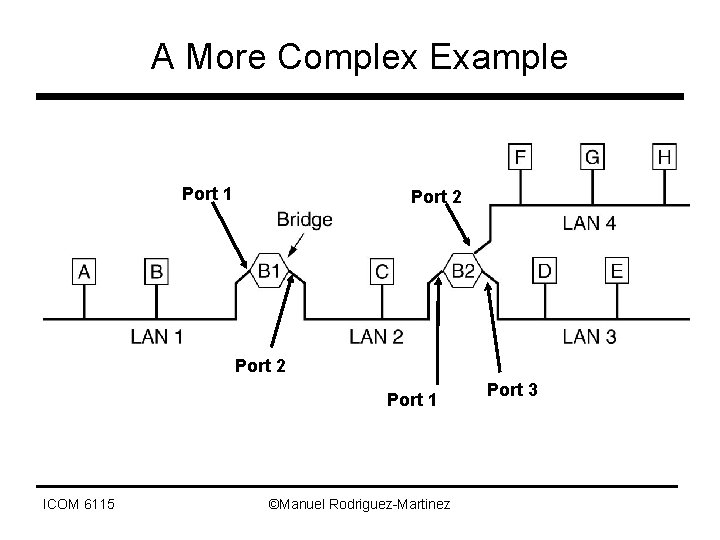
A More Complex Example Port 1 Port 2 Port 1 ICOM 6115 ©Manuel Rodriguez-Martinez Port 3

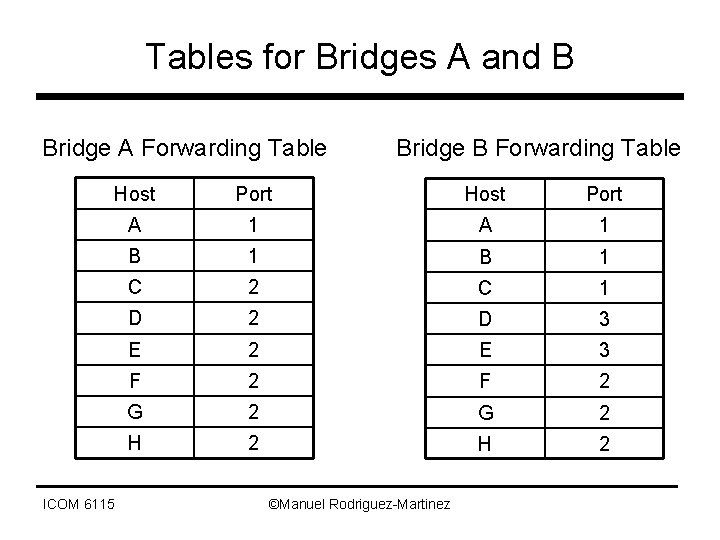
Tables for Bridges A and B Bridge A Forwarding Table Bridge B Forwarding Table Host Port A 1 B 1 C 2 C 1 D 2 D 3 E 2 E 3 F 2 G 2 H 2 ICOM 6115 ©Manuel Rodriguez-Martinez

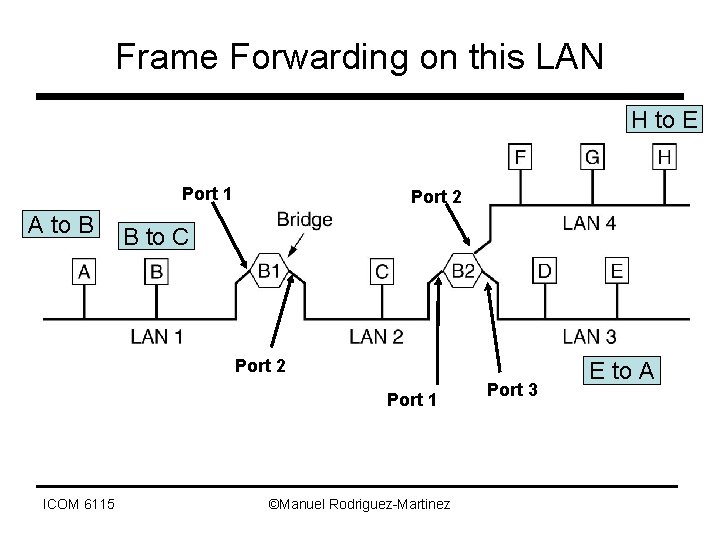
Frame Forwarding on this LAN H to E Port 1 A to B Port 2 B to C Port 2 Port 1 ICOM 6115 ©Manuel Rodriguez-Martinez Port 3 E to A

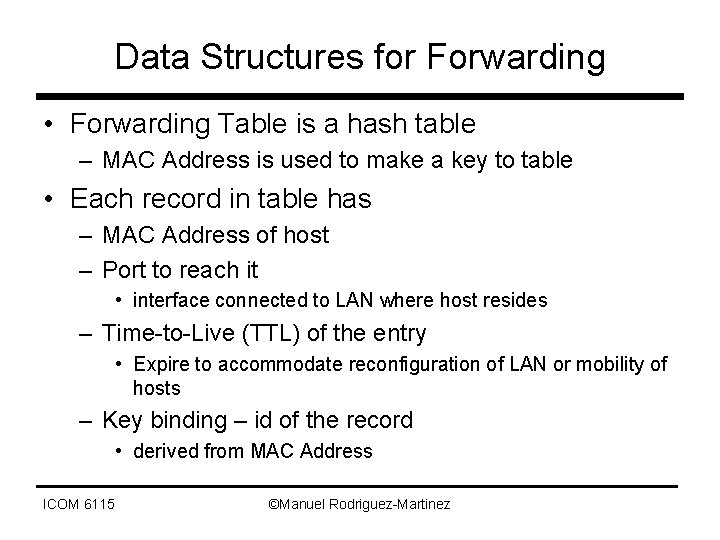
Data Structures for Forwarding • Forwarding Table is a hash table – MAC Address is used to make a key to table • Each record in table has – MAC Address of host – Port to reach it • interface connected to LAN where host resides – Time-to-Live (TTL) of the entry • Expire to accommodate reconfiguration of LAN or mobility of hosts – Key binding – id of the record • derived from MAC Address ICOM 6115 ©Manuel Rodriguez-Martinez

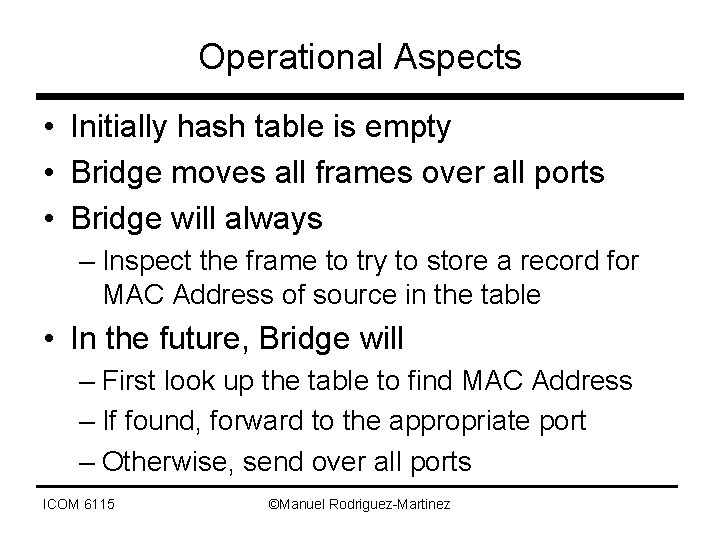
Operational Aspects • Initially hash table is empty • Bridge moves all frames over all ports • Bridge will always – Inspect the frame to try to store a record for MAC Address of source in the table • In the future, Bridge will – First look up the table to find MAC Address – If found, forward to the appropriate port – Otherwise, send over all ports ICOM 6115 ©Manuel Rodriguez-Martinez

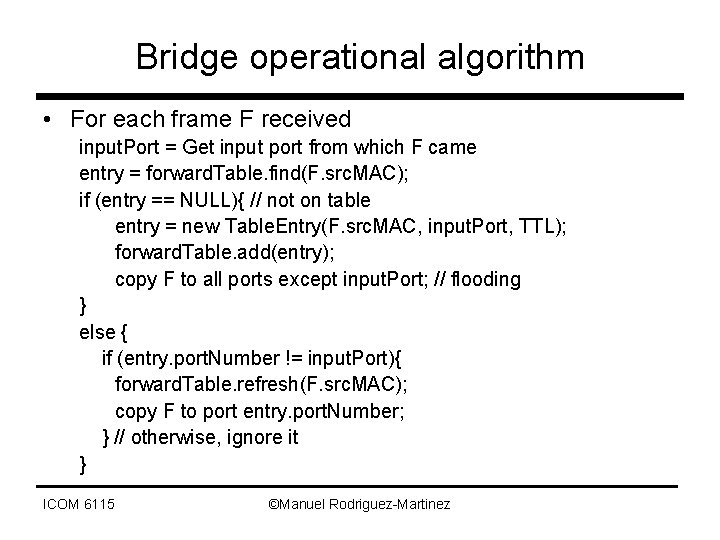
Bridge operational algorithm • For each frame F received input. Port = Get input port from which F came entry = forward. Table. find(F. src. MAC); if (entry == NULL){ // not on table entry = new Table. Entry(F. src. MAC, input. Port, TTL); forward. Table. add(entry); copy F to all ports except input. Port; // flooding } else { if (entry. port. Number != input. Port){ forward. Table. refresh(F. src. MAC); copy F to port entry. port. Number; } // otherwise, ignore it } ICOM 6115 ©Manuel Rodriguez-Martinez

Other Issues • If source and destination are on same segment, bridge will not forward frame – destination will get frame anyway! • Periodically, a routine will be run by bridge to purge forwarding table – All entries get TTL reduced by amount X – If TTL of an entry gets to 0, the entry is removed • Keep the table up to date • Bridge is constantly learning what is out there ICOM 6115 ©Manuel Rodriguez-Martinez

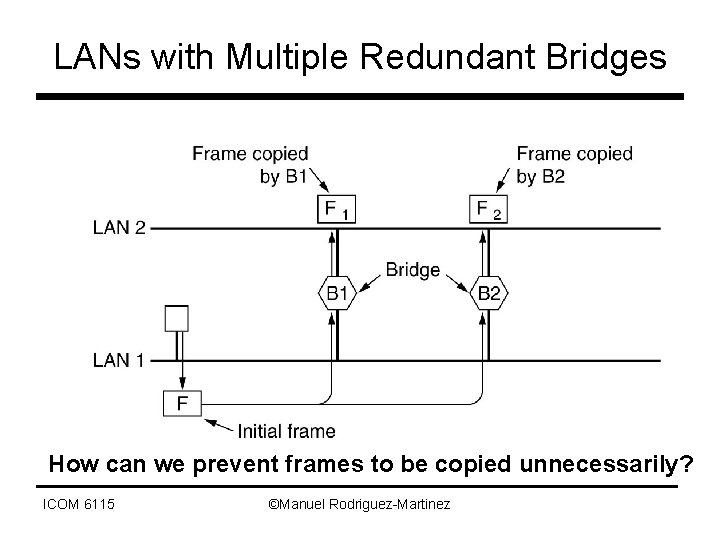
LANs with Multiple Redundant Bridges How can we prevent frames to be copied unnecessarily? ICOM 6115 ©Manuel Rodriguez-Martinez

Spanning Tree Bridges ICOM 6115 ©Manuel Rodriguez-Martinez

Traffic Management on LANs • Problem – Originally hosts got assigned a particular segment of a LAN based on location – Host on same building or floor are on same segment – What happens when people on same department work at different buildings? • They got connected to different LAN segments • Makes it hard to isolate and filter traffic ICOM 6115 ©Manuel Rodriguez-Martinez

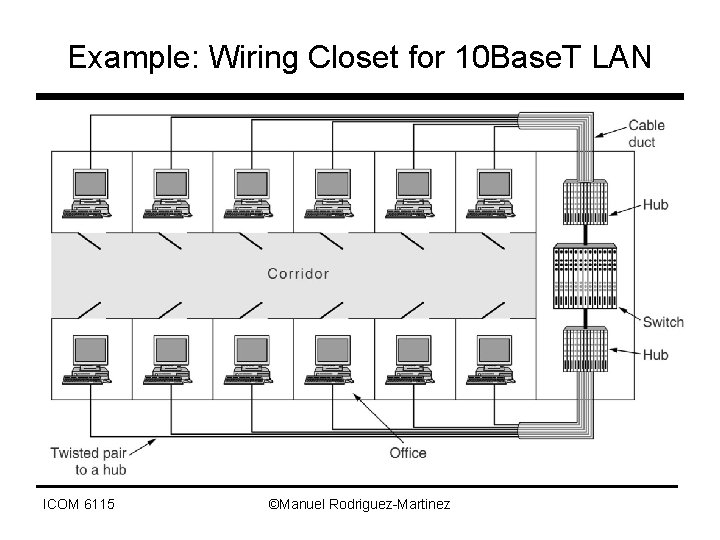
Example: Wiring Closet for 10 Base. T LAN ICOM 6115 ©Manuel Rodriguez-Martinez

Virtual LANs • Allow switches to implement LAN topology in software – Bridges can also do it • But everybody is going “switched” • VLAN is a logical LAN – All machines are part of the same group • Each port on a switch is associated with a logical LAN (virtual LAN) – Colors are used to identify each VLAN • Each VLAN has its own identifier – Differentiate logical LAN from physical LAN ICOM 6115 ©Manuel Rodriguez-Martinez

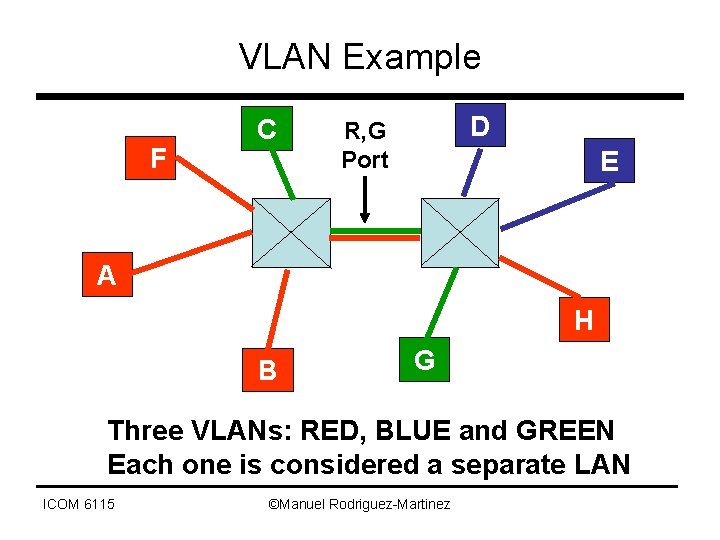
VLAN Example F C D R, G Port E A H B G Three VLANs: RED, BLUE and GREEN Each one is considered a separate LAN ICOM 6115 ©Manuel Rodriguez-Martinez

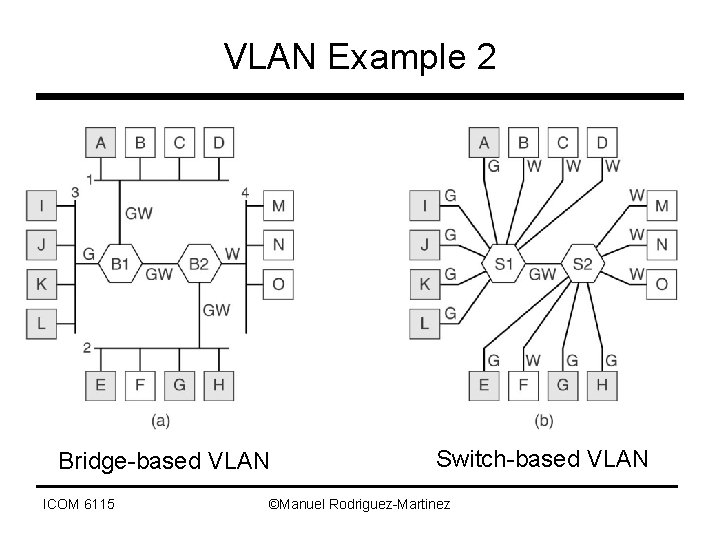
VLAN Example 2 Bridge-based VLAN ICOM 6115 Switch-based VLAN ©Manuel Rodriguez-Martinez

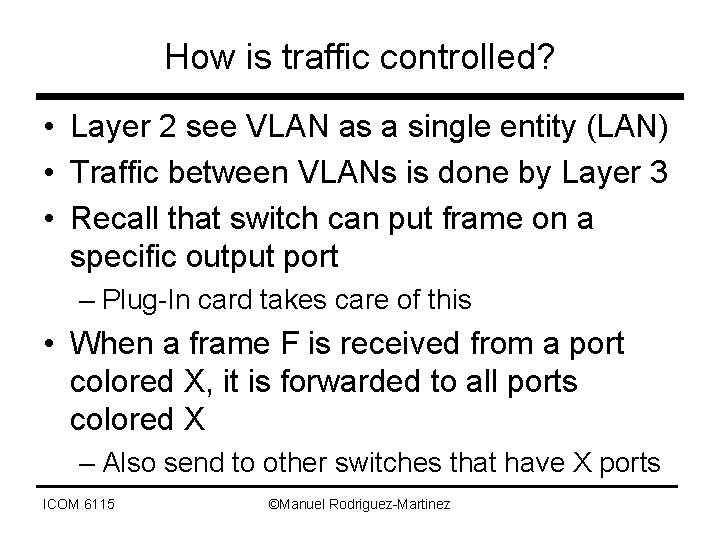
How is traffic controlled? • Layer 2 see VLAN as a single entity (LAN) • Traffic between VLANs is done by Layer 3 • Recall that switch can put frame on a specific output port – Plug-In card takes care of this • When a frame F is received from a port colored X, it is forwarded to all ports colored X – Also send to other switches that have X ports ICOM 6115 ©Manuel Rodriguez-Martinez

Identifying VLANs • Port Coloring • MAC Address Table • Layer 3 Payload Inspection ICOM 6115 ©Manuel Rodriguez-Martinez

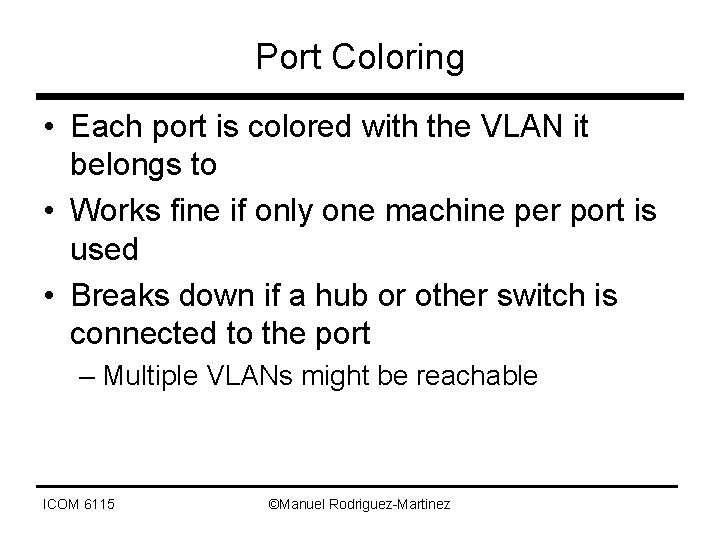
Port Coloring • Each port is colored with the VLAN it belongs to • Works fine if only one machine per port is used • Breaks down if a hub or other switch is connected to the port – Multiple VLANs might be reachable ICOM 6115 ©Manuel Rodriguez-Martinez

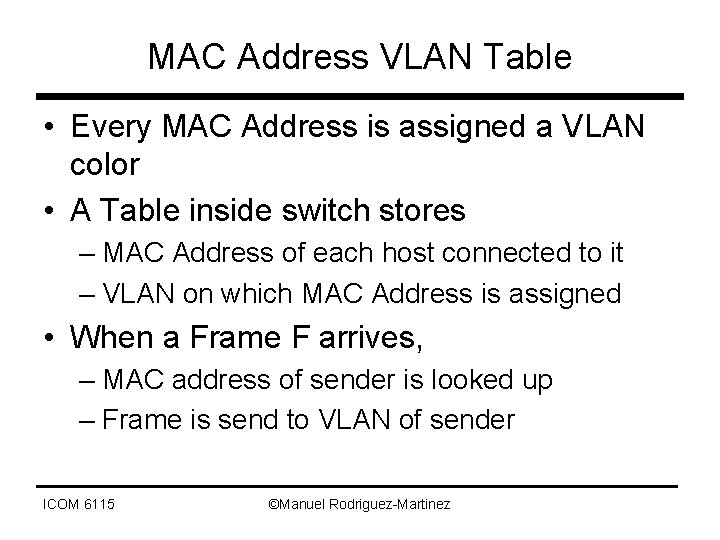
MAC Address VLAN Table • Every MAC Address is assigned a VLAN color • A Table inside switch stores – MAC Address of each host connected to it – VLAN on which MAC Address is assigned • When a Frame F arrives, – MAC address of sender is looked up – Frame is send to VLAN of sender ICOM 6115 ©Manuel Rodriguez-Martinez

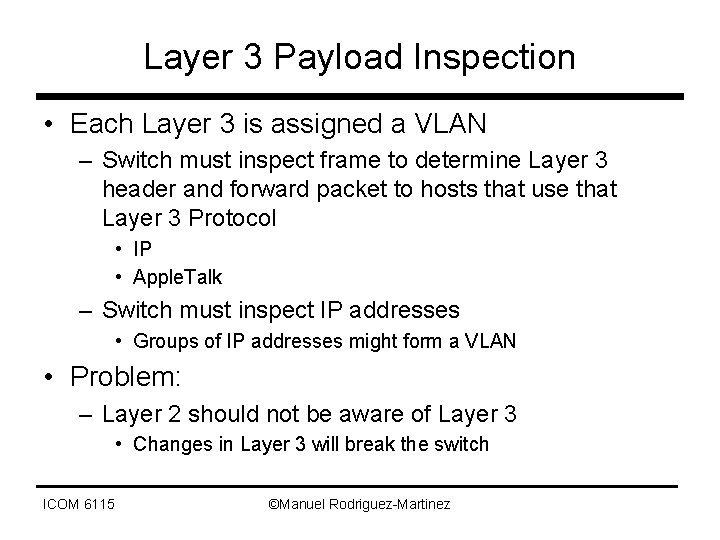
Layer 3 Payload Inspection • Each Layer 3 is assigned a VLAN – Switch must inspect frame to determine Layer 3 header and forward packet to hosts that use that Layer 3 Protocol • IP • Apple. Talk – Switch must inspect IP addresses • Groups of IP addresses might form a VLAN • Problem: – Layer 2 should not be aware of Layer 3 • Changes in Layer 3 will break the switch ICOM 6115 ©Manuel Rodriguez-Martinez

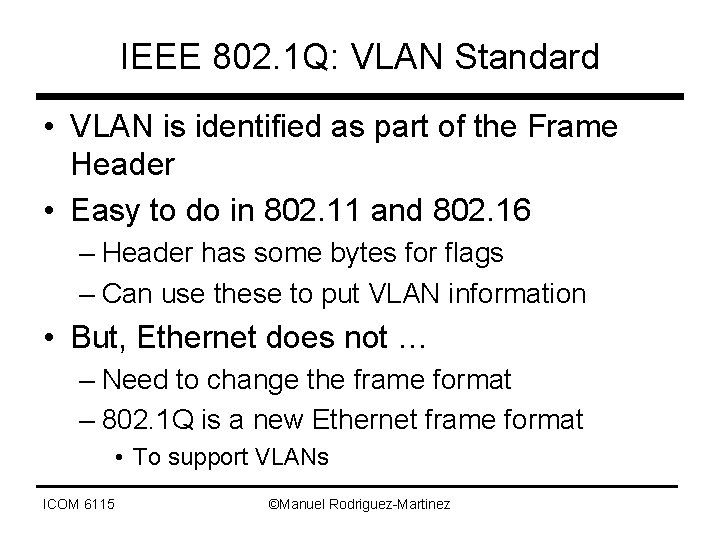
IEEE 802. 1 Q: VLAN Standard • VLAN is identified as part of the Frame Header • Easy to do in 802. 11 and 802. 16 – Header has some bytes for flags – Can use these to put VLAN information • But, Ethernet does not … – Need to change the frame format – 802. 1 Q is a new Ethernet frame format • To support VLANs ICOM 6115 ©Manuel Rodriguez-Martinez

WHAT? ? ? Changing Frames? ? ? • It is scary but – Only switches and bridges are affected • These are the only ones that need to deal with VLANs – New Ethernet cards will have it • Gigabit Ethernet Cards • Thus, VLAN aware bridge or switch will transform original Ethernet frame into a VLAN frame – MAC Address based VLAN or Layer 3 VLAN – If needed (Good hack!) ICOM 6115 ©Manuel Rodriguez-Martinez

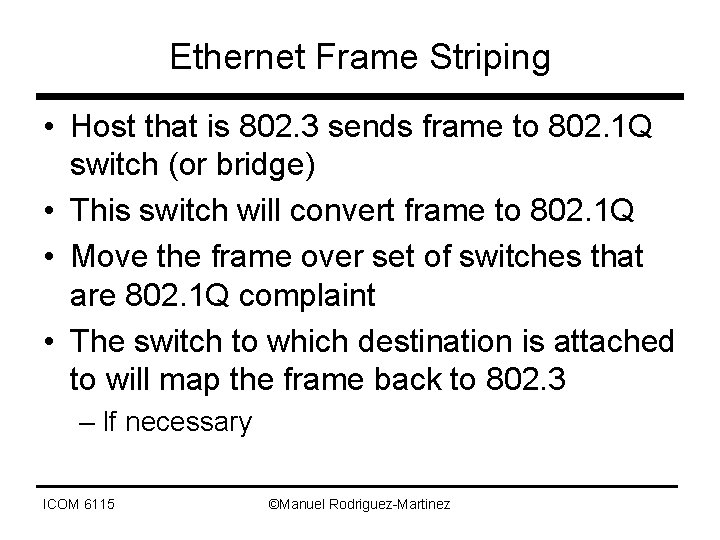
Ethernet Frame Striping • Host that is 802. 3 sends frame to 802. 1 Q switch (or bridge) • This switch will convert frame to 802. 1 Q • Move the frame over set of switches that are 802. 1 Q complaint • The switch to which destination is attached to will map the frame back to 802. 3 – If necessary ICOM 6115 ©Manuel Rodriguez-Martinez

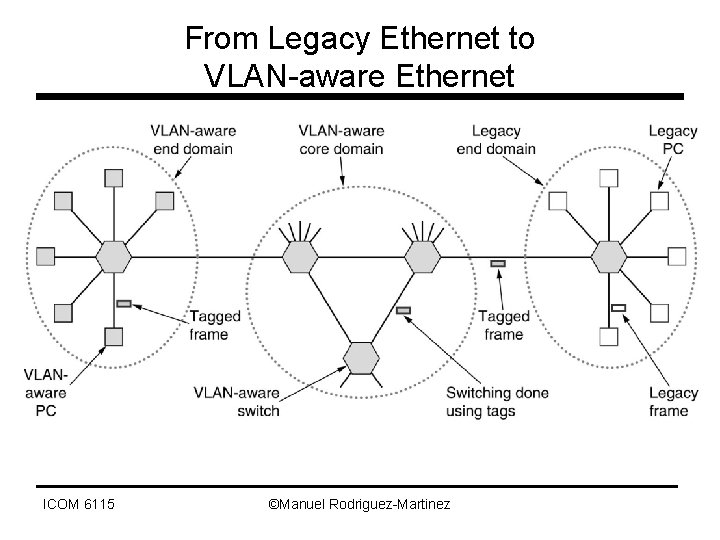
From Legacy Ethernet to VLAN-aware Ethernet ICOM 6115 ©Manuel Rodriguez-Martinez

Comparison of frame formats • • VLAN Protocol Id – value of 0 x 8100 used to identify frame as 802. 1 Q – Tells that frame is not 802. 3 (2 -bytes long) Pri – priority field used to specify Qo. S (3 -bit long) CFI – Format indicator for MAC Address (Big vs Little Endian) (1 -bit) VLAN Identifier – id of the VLAN, used by switched to index forwarding Table (12 -bit long) ICOM 6115 ©Manuel Rodriguez-Martinez

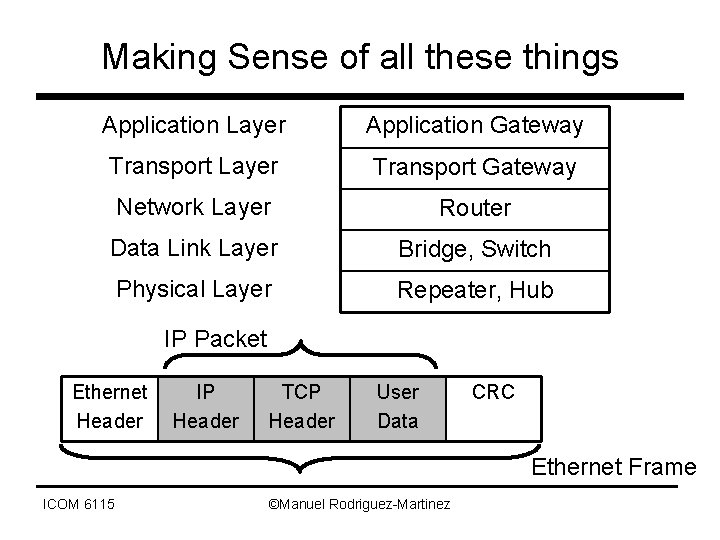
Making Sense of all these things Application Layer Application Gateway Transport Layer Transport Gateway Network Layer Router Data Link Layer Bridge, Switch Physical Layer Repeater, Hub IP Packet Ethernet Header IP Header TCP Header User Data CRC Ethernet Frame ICOM 6115 ©Manuel Rodriguez-Martinez
 Comparison of virtual circuit and datagram network
Comparison of virtual circuit and datagram network Backbone networks in computer networks
Backbone networks in computer networks Icom ic-2730a vs kenwood tm-v71a
Icom ic-2730a vs kenwood tm-v71a Icom dstar
Icom dstar ämaps
ämaps Icom
Icom Integrated and differentiated services in computer networks
Integrated and differentiated services in computer networks Error detection in computer networks
Error detection in computer networks What is bit and byte stuffing
What is bit and byte stuffing Bit stuffing and byte stuffing
Bit stuffing and byte stuffing What is the reverse request protocol?
What is the reverse request protocol? Analogue and digital transmission in computer networks
Analogue and digital transmission in computer networks Web and http in computer networks
Web and http in computer networks Computer networks and internets with internet applications
Computer networks and internets with internet applications Error detection and correction in networking
Error detection and correction in networking Protocols and standards in computer networks
Protocols and standards in computer networks Error detection computer networks
Error detection computer networks Computer networks and internets
Computer networks and internets Crc in computer networks
Crc in computer networks Crc in computer networks
Crc in computer networks Traffic management in computer networks
Traffic management in computer networks Tpdu in computer networks
Tpdu in computer networks What is optimality principle in computer networks
What is optimality principle in computer networks Snmp model in computer networks
Snmp model in computer networks What is optimality principle in computer networks
What is optimality principle in computer networks Uses of computer in business
Uses of computer in business Classify computer networks based of transmission technology
Classify computer networks based of transmission technology Dns in computer networks
Dns in computer networks Icmp in computer networks
Icmp in computer networks Framing in computer network
Framing in computer network Dns in computer networks
Dns in computer networks Computer networks assignment
Computer networks assignment Difference between computer network and distributed system
Difference between computer network and distributed system Computer networks routing algorithms
Computer networks routing algorithms Internet transport protocol in computer networks
Internet transport protocol in computer networks