How advanced are Advanced Persistent Threats really Dimitrios
















- Slides: 22

How advanced are Advanced Persistent Threats, really? Dimitrios Petropoulos 1 19 April 2012

$ cut -f 5 -d: /etc/passwd | grep -i petropoulos • Dimitrios Petropoulos • Twenty five years of IT experience; last twenty in Info. Sec • Cryptographer by education (nobody’s perfect) • Have been designing ‘undetectable’ (? ) reverse access trojans all this decade 2

Defining Advanced Persistent Threats (APT) What are they? • Advanced persistent threat (APT) usually refers to a group (such as a foreign nation state government, organised crime, etc. ) with both the capability and means as well as the intent to persistently and effectively target a specific entity. – The term is commonly used to refer to cyber threats, in particular that of cyber espionage, orchestrated advanced cyber-attacks, etc. • 99% of the time they are Client-side, Exfiltration Attacks: – – – 3 Targeted attacks Attack the client/user Malware, Trojans, Web-born attacks Covert Channels, Evasion techniques… Results: Data leakage, Sabotage, Fraud…you name it

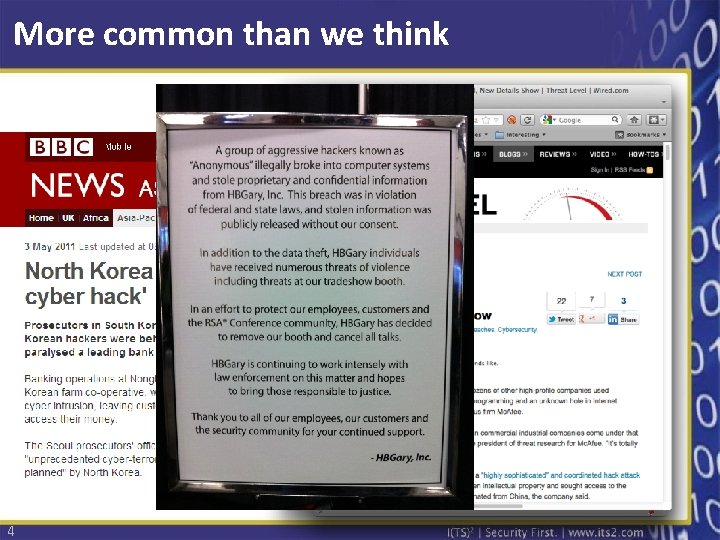
More common than we think 4

APTs go mainstream… Products 5

APTs…Revisited Advanced Persistent Threat • is not a matter of Who • is a matter of When! 6

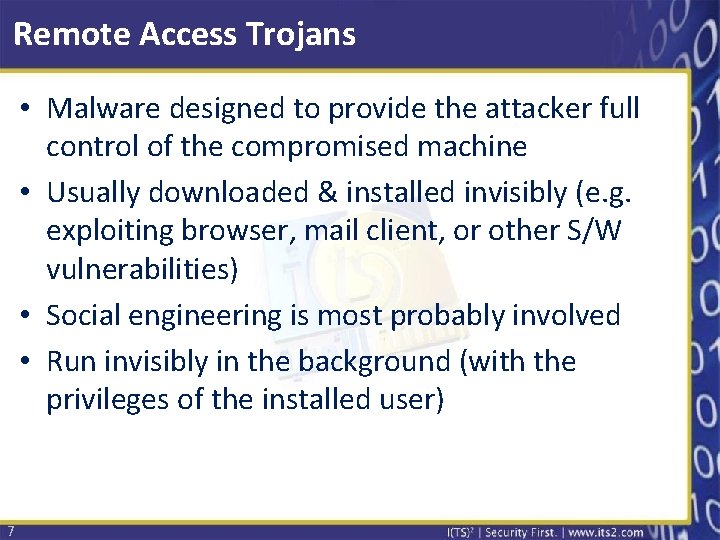
Remote Access Trojans • Malware designed to provide the attacker full control of the compromised machine • Usually downloaded & installed invisibly (e. g. exploiting browser, mail client, or other S/W vulnerabilities) • Social engineering is most probably involved • Run invisibly in the background (with the privileges of the installed user) 7

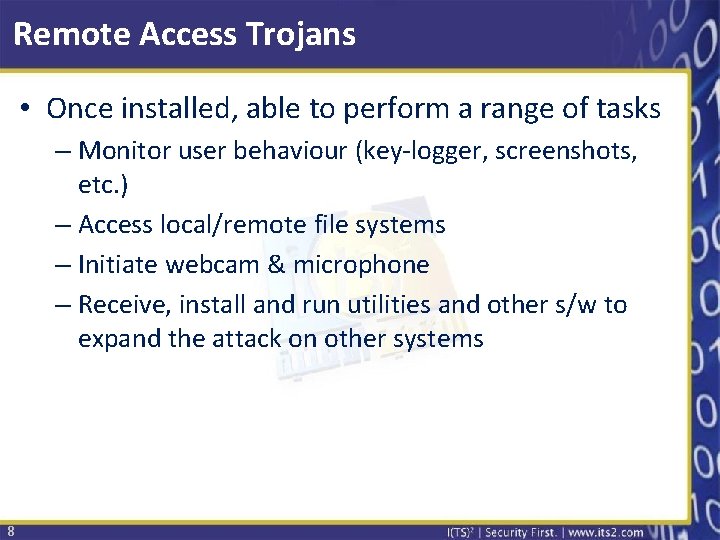
Remote Access Trojans • Once installed, able to perform a range of tasks – Monitor user behaviour (key-logger, screenshots, etc. ) – Access local/remote file systems – Initiate webcam & microphone – Receive, install and run utilities and other s/w to expand the attack on other systems 8

More than data… 9

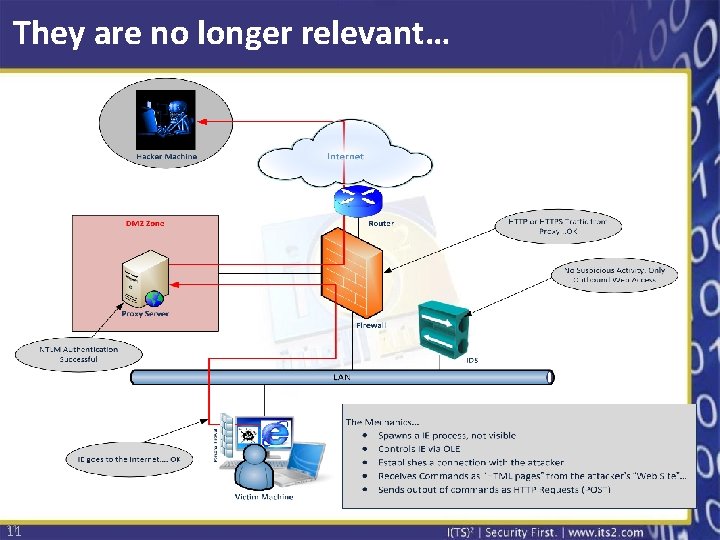
Behind the scenes… • But who controls what the RAT does? Is it programmed logic? • Of course not! • Behind every RAT attack there’s a C&C entity • Behind the C&C entity there’s a human instructing the RAT to execute various tasks • That means RATs can communicate with the outside world from within the secure perimeter? What about all our expensive security controls? 10

They are no longer relevant… 11 11

Are APTs actually “Advanced”? • Not Straight Forward Attacks: YES – Not a pure one-level attack (network, system, application, content…) – Not a single signature/type of attack • Multi-Vector Attacks: YES – Web-born, mail-born, media-born… – Exploits/Vulnerabilities: Browser, PDF, Office files, Active. X, Java. Script, Binders, Object Packagers, API abuse… • Huge Attack Surface Attacks: YES – number of employees/users – The complexity and size of the Internet • Weakest link Attacks: YES – Users = Persons …but “Advanced” ? 12

Why “Advanced” is misleading… Because these attacks: • are actually Advanced for traditional but also for “less traditional” security controls • are also advanced for single-vector specialised security controls • are not advanced enough for some specialised security controls trying to be “very advanced”, missing the simplicity of some APTs 13

Cause “Traditional” controls fail • Firewalls, IPS, Secure Web Gateways, AV/Endpoint Security… – They are blind: • Single-level controls • Signature based – They try to be preventive: • Black-listing or white-listing approach • The 1 st is futile against APTs (and most other attacks) • The 2 nd is difficult/impossible to implement for all possible attack vectors, or it would definitely impair business – Single-Vector Approach: • e. g. SWGs: they are focusing on a single vector of attack (Web Access) • And they are not even effective for this single vector 14

…but also “less traditional” controls • Most DLP systems are designed to: – Detect (and try to prevent) unintentional leakages, or even some times intentional leakages – But by normal users, over common methods! (e. g. web upload, mail, webmail, removable media, etc. ) 15

…while Security Programs • Are focused around Compliance – Many standards/regulations to comply with – Huge investments/efforts towards compliance – The Security Objectives/Metrics have been replaced by one: “How quickly can I provide Auditors with answers? ” • However: Compliant ≠Secure 16

Lessons Learned • We need our “traditional” security controls • We need also our “less traditional” ones – Security as a Business enabler – Fit for purpose for collaborative enterprise environments, especially in the era of Enterprise 2. 0 • We need to be Compliant • We definitely need Specialized Controls What we don’t need is to expect the attacker to play by the rules and attack us ‘nobly’ 17

Focus on APT Let’s first find the right security paradigm for Addressing APT • As Complexity increases the good old “Preventive” controls get increasingly less effective or impair Business : – Complex IT environments & business process – Complex threat landscape • Proactive Security ≠ Preventive Controls alone – Early Warning & Response is the “preventive” control of choice for complex environments and threats 18

Focus on APT If Early Warning is what we need, let’s think “What cannot be evaded” • Behavior – An IT environment under attack does not behaves as normal – Each attack, APT included, has its own signs in behaviour change • True Visibility – at all (relevant) Levels – Network: Internet Access (incoming/outgoing) – Endpoint: System state & Data Access/Use • Expertise – the human factor – Rules…Rulz! – Expert view and analysis 19

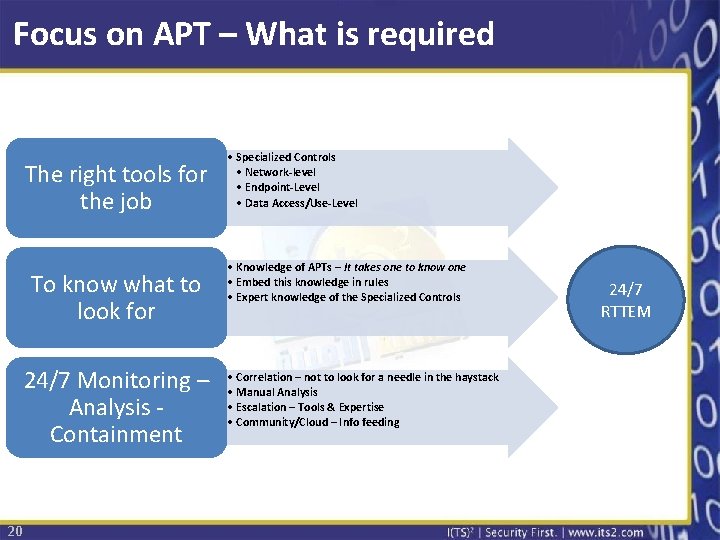
Focus on APT – What is required The right tools for the job To know what to look for 24/7 Monitoring – Analysis Containment 20 • Specialized Controls • Network-level • Endpoint-Level • Data Access/Use-Level • Knowledge of APTs – It takes one to know one • Embed this knowledge in rules • Expert knowledge of the Specialized Controls • Correlation – not to look for a needle in the haystack • Manual Analysis • Escalation – Tools & Expertise • Community/Cloud – Info feeding 24/7 RTTEM

APTs & RATs – my conclusions • These attacks cannot be prevented – Undetermined attack vector – No established attack signatures or patterns – Attack characteristics can be changed in both their physical and logical manifestation • Over reliance on anti-virus is a fallacy • One can only detect, contain & eradicate – Any intrusion -regardless of its stealthiness- leaves marks; it’s just a matter of looking closely & looking for the right things… 21

Security First. 22