Evidence of Advanced Persistent Threat A Case Study






- Slides: 9

Evidence of Advanced Persistent Threat: A Case Study of Malware for Political Espionage Frankie Li, Anthony Lai, Ddl Valkyrie-X Security Research Group 2011 6 th International Conference on Malicious and Unwanted Software Presenter: 劉力瑋 國立清華大學高速通訊與計算實驗室 NTHU High-Speed Communication & Computing Laboratory 1/9

Outline APT n A case in Hong Kong n Analysis n Conclusion n 國立清華大學高速通訊與計算實驗室 NTHU High-Speed Communication & Computing Laboratory 2/9

Advanced Persistent Threats (APT) n This paper consider an APT as a cyber attack launched by a group of sophisticated, determined, and coordinated attackers who systematically compromise the network of a specific target machine or entity for a prolonged period. 國立清華大學高速通訊與計算實驗室 NTHU High-Speed Communication & Computing Laboratory 3/9

A case in Hong Kong n n A well design email (2011/7/7) l Title : Democracy Depot meeting l Sender : first_name. p 0 on@<org_name>. org. hk l Attachments : Democracy Depot meeting Second email was received on 2011/7/14 l It is sent by a political group about the news of a riot in 廣州 國立清華大學高速通訊與計算實驗室 NTHU High-Speed Communication & Computing Laboratory 4/9

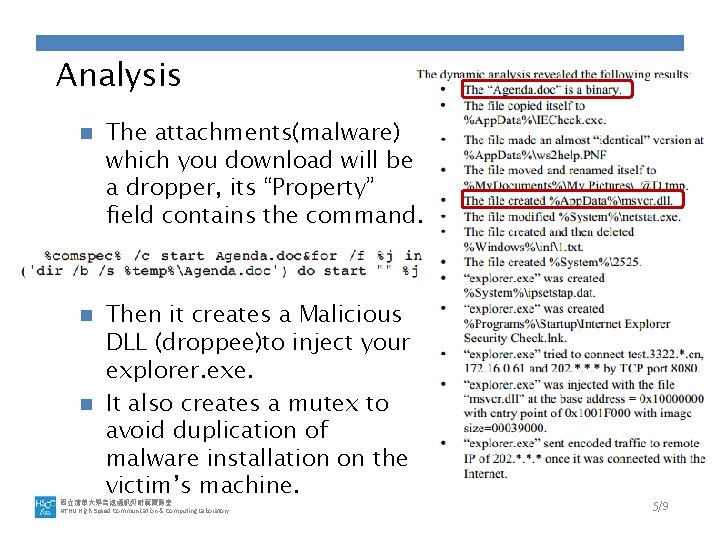
Analysis n The attachments(malware) which you download will be a dropper, its “Property” field contains the command. Then it creates a Malicious DLL (droppee)to inject your explorer. exe. n It also creates a mutex to avoid duplication of malware installation on the victim’s machine. n 國立清華大學高速通訊與計算實驗室 NTHU High-Speed Communication & Computing Laboratory 5/9

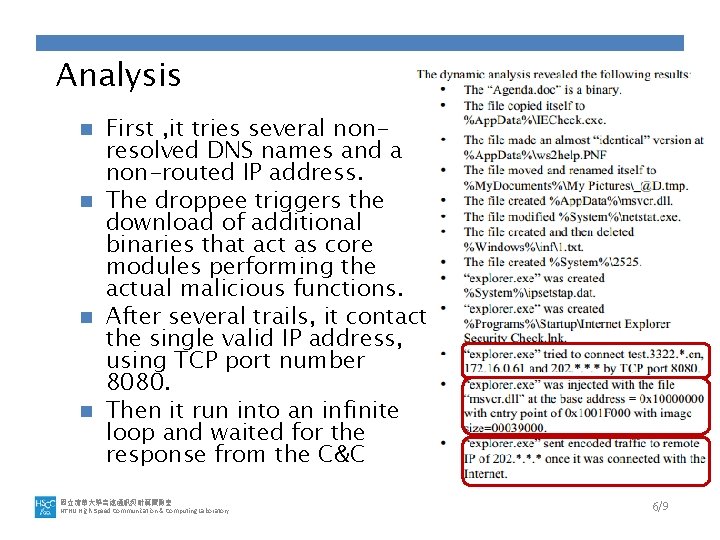
Analysis First , it tries several nonresolved DNS names and a non-routed IP address. n The droppee triggers the download of additional binaries that act as core modules performing the actual malicious functions. n After several trails, it contact the single valid IP address, using TCP port number 8080. n Then it run into an infinite loop and waited for the response from the C&C n 國立清華大學高速通訊與計算實驗室 NTHU High-Speed Communication & Computing Laboratory 6/9

Analysis Additional binaries downloaded by droppee perform the actual malicious functions. n All passwords from “foxmail, ” “outlook express, ” “IE Form Storage, ” “MSN, ” “Passport Dot. Net, ” and “protected storage, ” were collected from the infected machine. n The screen captures will also be collected and uploaded to the C&C. n 國立清華大學高速通訊與計算實驗室 NTHU High-Speed Communication & Computing Laboratory 7/9

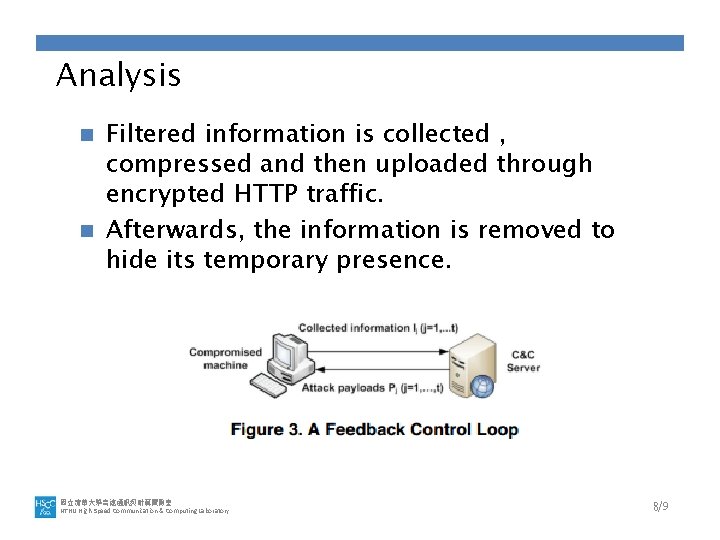
Analysis Filtered information is collected , compressed and then uploaded through encrypted HTTP traffic. n Afterwards, the information is removed to hide its temporary presence. n 國立清華大學高速通訊與計算實驗室 NTHU High-Speed Communication & Computing Laboratory 8/9

Discussion and Conclusion APT-type malware does not carry obvious malicious functions. n Unlike the other malware it seldom changes the infected system as a zombie machine. n n How to avoid it NEVER OPEN SPEARPHISHING EMAILS !! 國立清華大學高速通訊與計算實驗室 NTHU High-Speed Communication & Computing Laboratory 9/9