HopCount Filtering An Effective Defense Against Spoofed DDos






- Slides: 36

Hop-Count Filtering: An Effective Defense Against Spoofed DDos Traffic Cheng Jin CS Department Caltech Pasadena Haining Wang CS Department College of William and Mary Williamsburg Kang G. Shin EECS Department University of Michigan Ann Arbor CCS’ 03, October 27– 31, 2003 1

Outline Introduction Hop-count inspection Feasibility of hop-count filtering Effectiveness of HCF Construction of HCF table Running states of HCF Resource Savings Related work Conclusion and future work 1

INTRODUCTION IP spoofing makes DDo. S attack more difficult to defend against. Conceal flooding sources and localities in flooding traffic Coax legitimate hosts into becoming reflectors Two approaches to thwart DDo. S attack Router-based Victim-based 1

INTRODUCTION Router-based : improve routing infrastructure Off-line analysis of flooding traffic On-line filtering of DDo. S traffic inside routers Off-line IP traceback Rely on IP router enhancement Victim-based : enhances the resilience of Internet servers against attacks Advantage of being immediately deployable Current approach : resource management 1

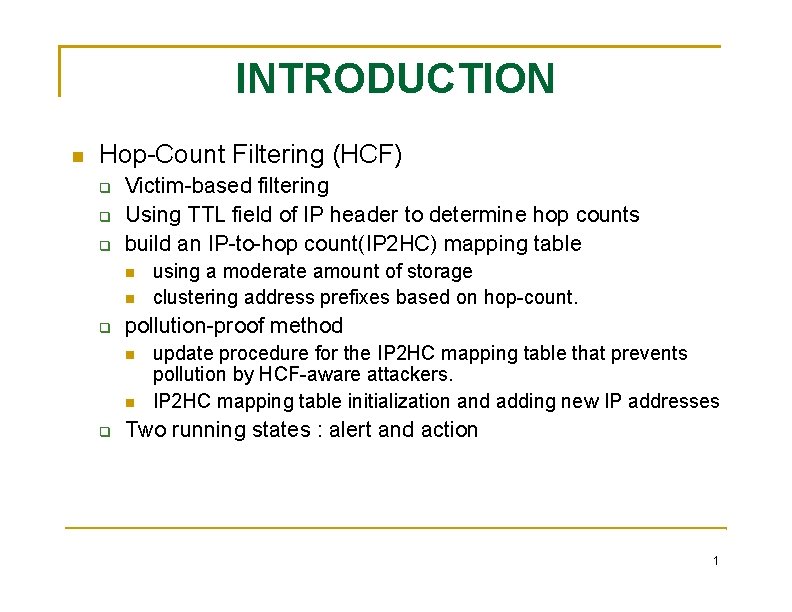
INTRODUCTION Hop-Count Filtering (HCF) Victim-based filtering Using TTL field of IP header to determine hop counts build an IP-to-hop count(IP 2 HC) mapping table pollution-proof method using a moderate amount of storage clustering address prefixes based on hop-count. update procedure for the IP 2 HC mapping table that prevents pollution by HCF-aware attackers. IP 2 HC mapping table initialization and adding new IP addresses Two running states : alert and action 1

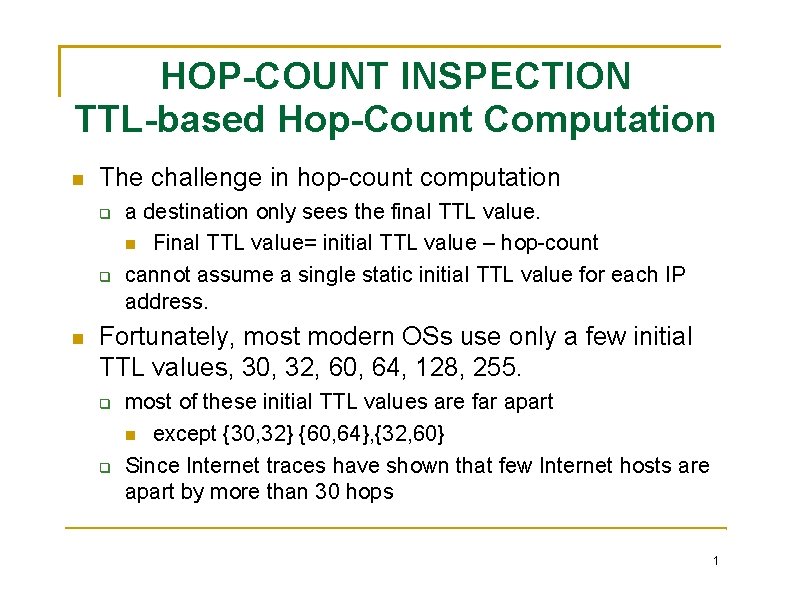
HOP-COUNT INSPECTION TTL-based Hop-Count Computation The challenge in hop-count computation a destination only sees the final TTL value. Final TTL value= initial TTL value – hop-count cannot assume a single static initial TTL value for each IP address. Fortunately, most modern OSs use only a few initial TTL values, 30, 32, 60, 64, 128, 255. most of these initial TTL values are far apart except {30, 32} {60, 64}, {32, 60} Since Internet traces have shown that few Internet hosts are apart by more than 30 hops 1

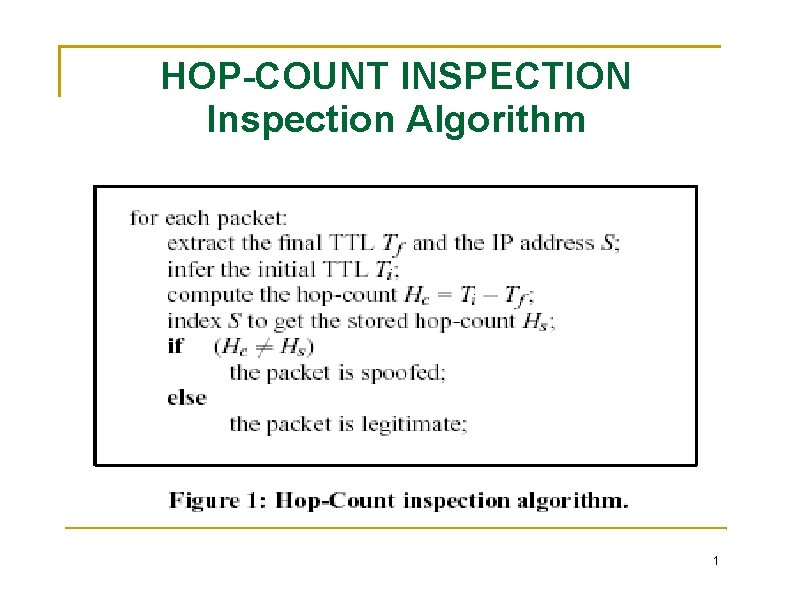
HOP-COUNT INSPECTION Inspection Algorithm 1

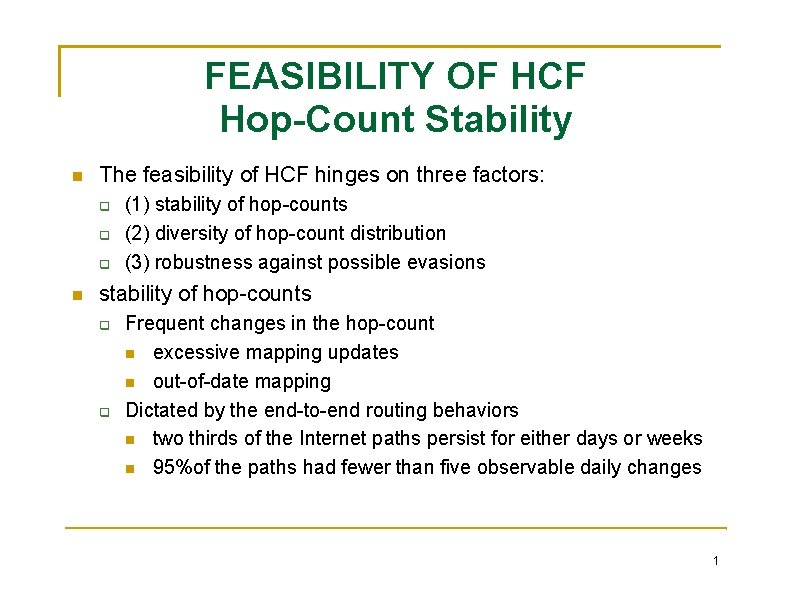
FEASIBILITY OF HCF Hop-Count Stability The feasibility of HCF hinges on three factors: (1) stability of hop-counts (2) diversity of hop-count distribution (3) robustness against possible evasions stability of hop-counts Frequent changes in the hop-count excessive mapping updates out-of-date mapping Dictated by the end-to-end routing behaviors two thirds of the Internet paths persist for either days or weeks 95%of the paths had fewer than five observable daily changes 1

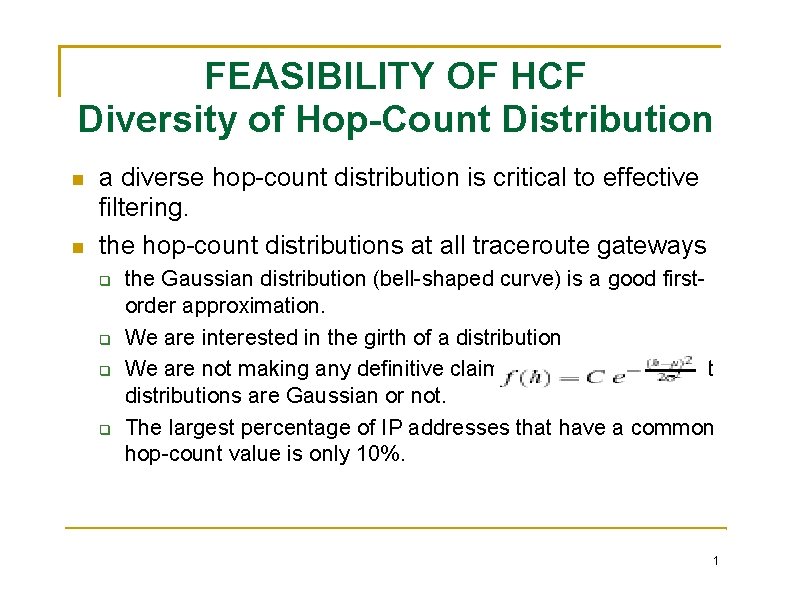
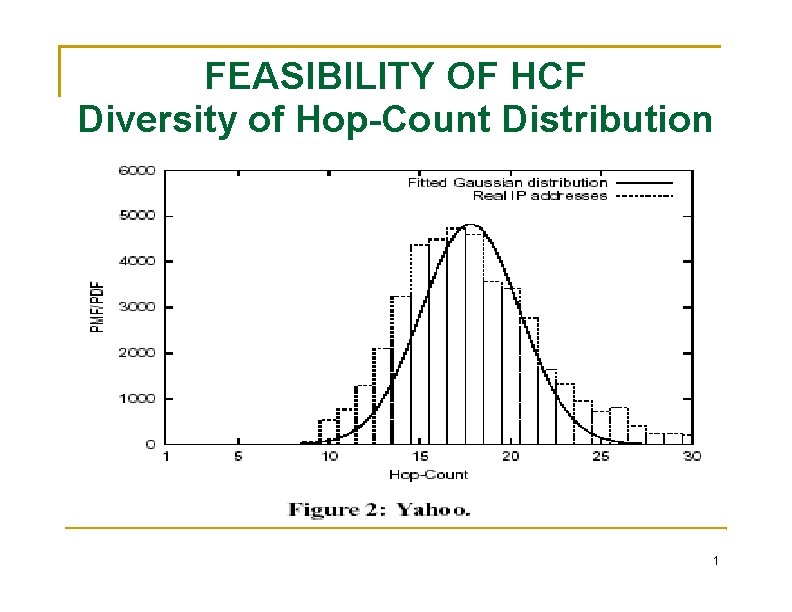
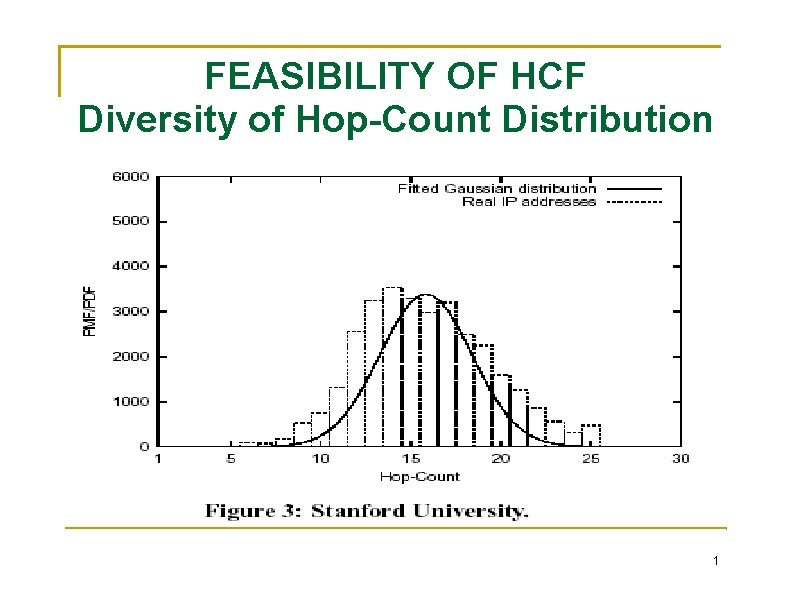
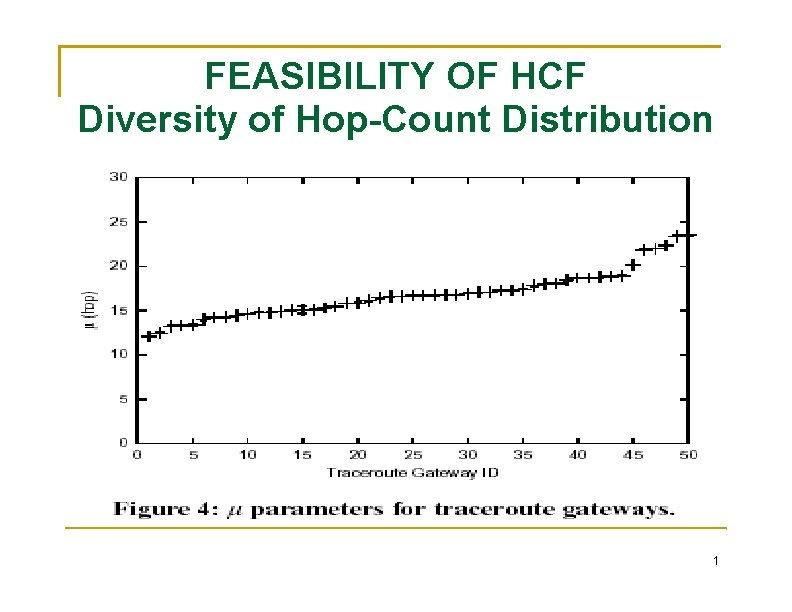
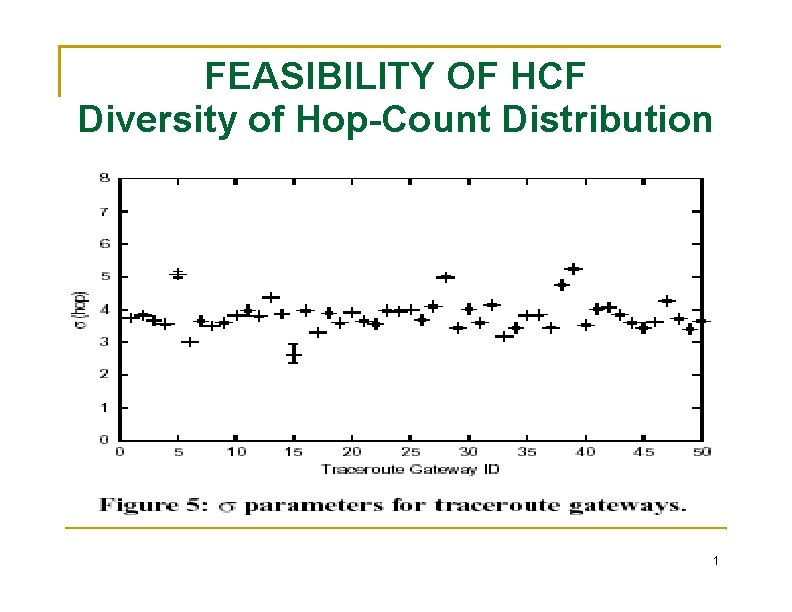
FEASIBILITY OF HCF Diversity of Hop-Count Distribution a diverse hop-count distribution is critical to effective filtering. the hop-count distributions at all traceroute gateways the Gaussian distribution (bell-shaped curve) is a good firstorder approximation. We are interested in the girth of a distribution We are not making any definitive claim of whether hop-count distributions are Gaussian or not. The largest percentage of IP addresses that have a common hop-count value is only 10%. 1

FEASIBILITY OF HCF Diversity of Hop-Count Distribution 1

FEASIBILITY OF HCF Diversity of Hop-Count Distribution 1

FEASIBILITY OF HCF Diversity of Hop-Count Distribution 1

FEASIBILITY OF HCF Diversity of Hop-Count Distribution 1

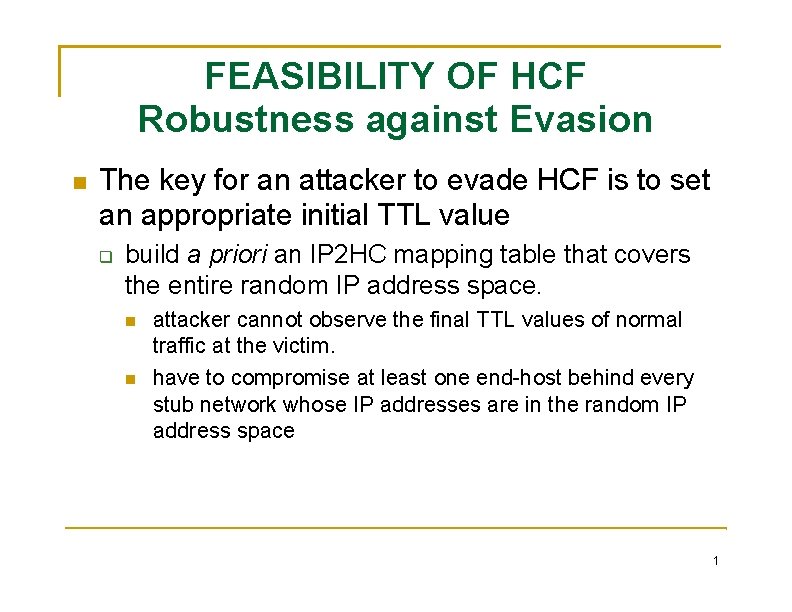
FEASIBILITY OF HCF Robustness against Evasion The key for an attacker to evade HCF is to set an appropriate initial TTL value build a priori an IP 2 HC mapping table that covers the entire random IP address space. attacker cannot observe the final TTL values of normal traffic at the victim. have to compromise at least one end-host behind every stub network whose IP addresses are in the random IP address space 1

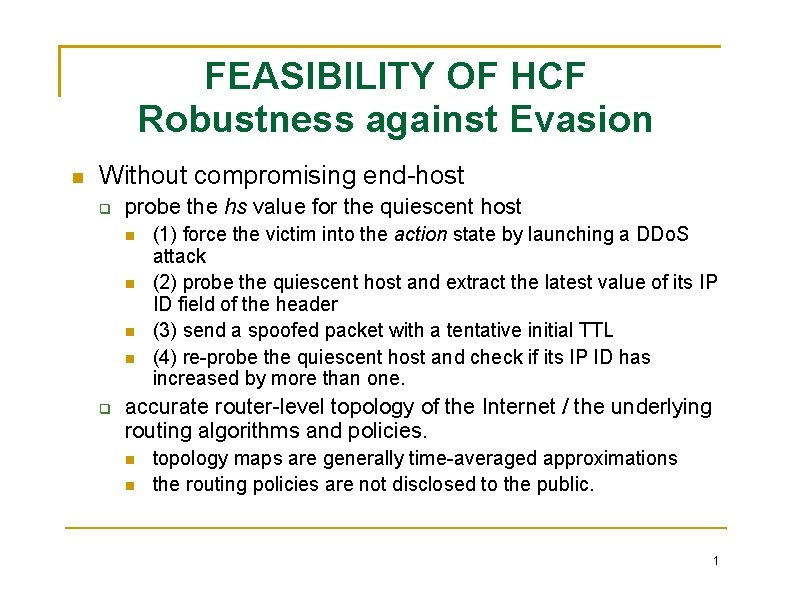
FEASIBILITY OF HCF Robustness against Evasion Without compromising end-host probe the hs value for the quiescent host (1) force the victim into the action state by launching a DDo. S attack (2) probe the quiescent host and extract the latest value of its IP ID field of the header (3) send a spoofed packet with a tentative initial TTL (4) re-probe the quiescent host and check if its IP ID has increased by more than one. accurate router-level topology of the Internet / the underlying routing algorithms and policies. topology maps are generally time-averaged approximations the routing policies are not disclosed to the public. 1

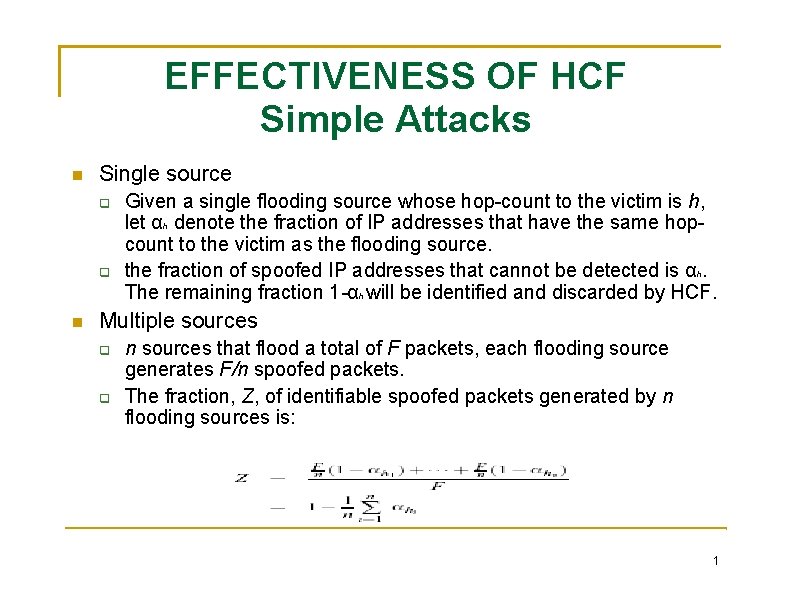
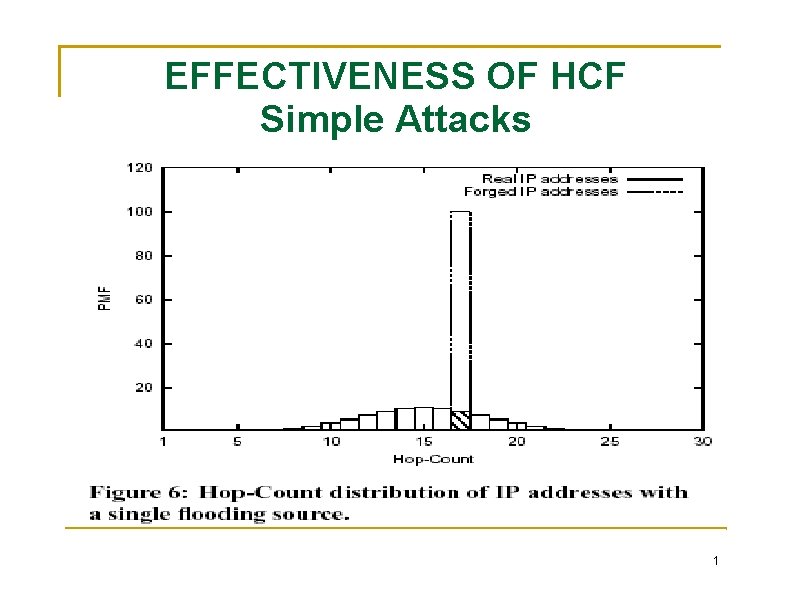
EFFECTIVENESS OF HCF Simple Attacks Single source Given a single flooding source whose hop-count to the victim is h, let αh denote the fraction of IP addresses that have the same hopcount to the victim as the flooding source. the fraction of spoofed IP addresses that cannot be detected is αh. The remaining fraction 1 -αh will be identified and discarded by HCF. Multiple sources n sources that flood a total of F packets, each flooding source generates F/n spoofed packets. The fraction, Z, of identifiable spoofed packets generated by n flooding sources is: 1

EFFECTIVENESS OF HCF Simple Attacks 1

EFFECTIVENESS OF HCF Simple Attacks 1

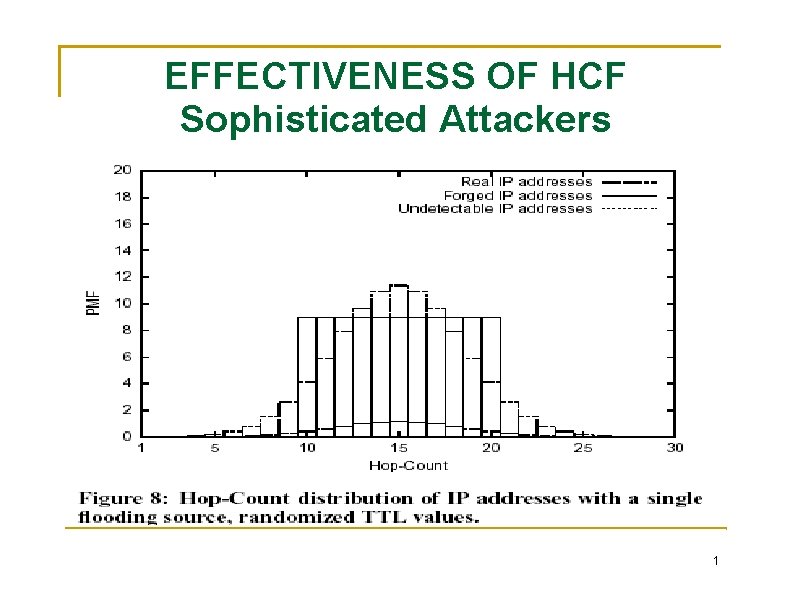
EFFECTIVENESS OF HCF Sophisticated Attackers 1

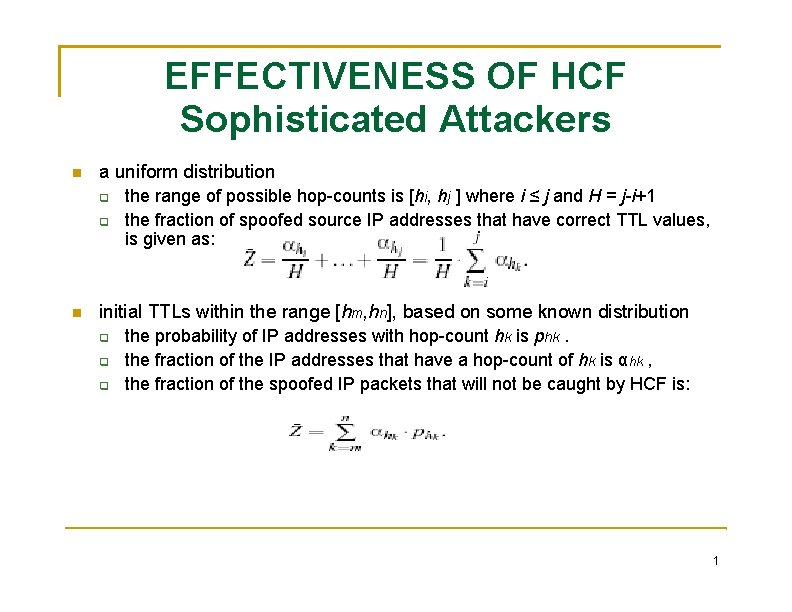
EFFECTIVENESS OF HCF Sophisticated Attackers a uniform distribution the range of possible hop-counts is [hi, hj ] where i ≤ j and H = j-i+1 the fraction of spoofed source IP addresses that have correct TTL values, is given as: initial TTLs within the range [hm, hn], based on some known distribution the probability of IP addresses with hop-count hk is phk. the fraction of the IP addresses that have a hop-count of hk is αhk , the fraction of the spoofed IP packets that will not be caught by HCF is: 1

EFFECTIVENESS OF HCF Sophisticated Attackers 1

EFFECTIVENESS OF HCF Sophisticated Attackers 1

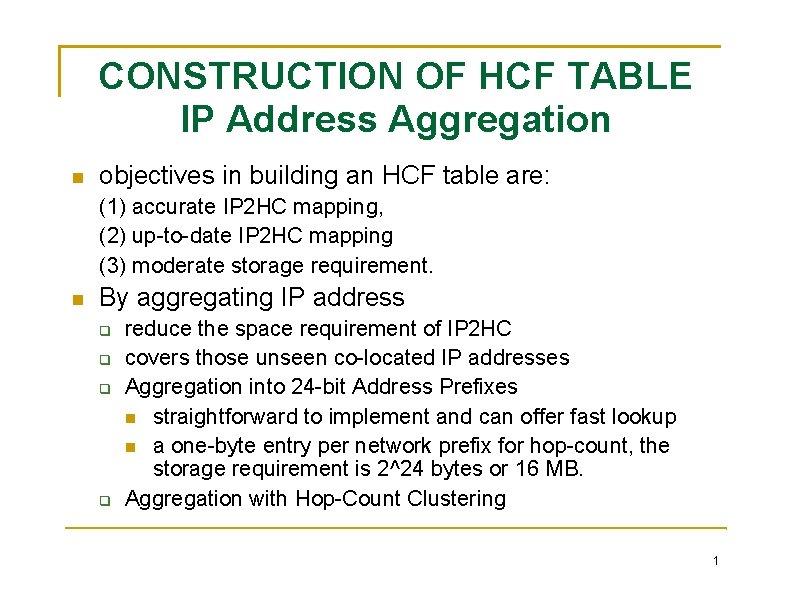
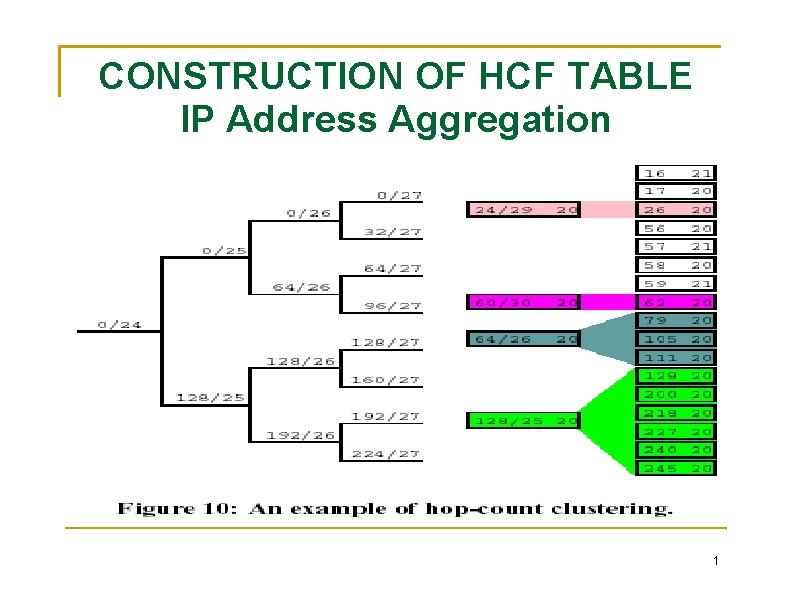
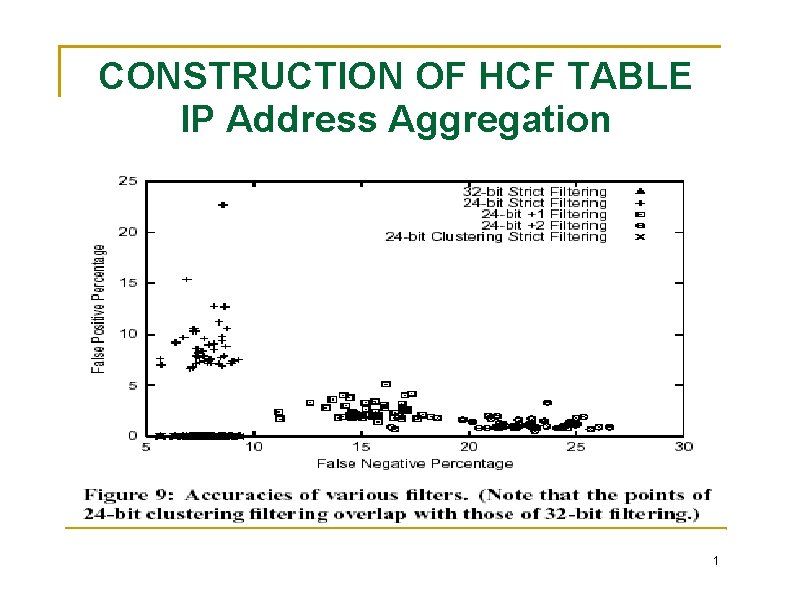
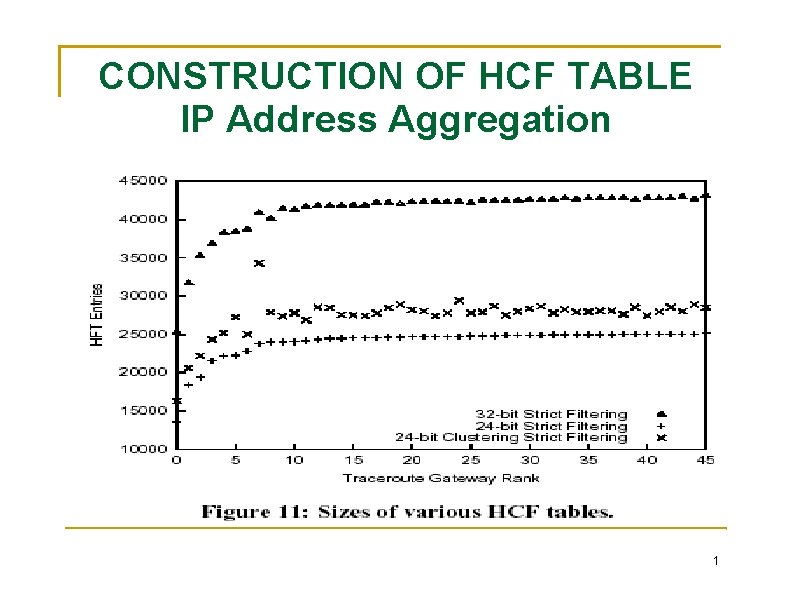
CONSTRUCTION OF HCF TABLE IP Address Aggregation objectives in building an HCF table are: (1) accurate IP 2 HC mapping, (2) up-to-date IP 2 HC mapping (3) moderate storage requirement. By aggregating IP address reduce the space requirement of IP 2 HC covers those unseen co-located IP addresses Aggregation into 24 -bit Address Prefixes straightforward to implement and can offer fast lookup a one-byte entry per network prefix for hop-count, the storage requirement is 2^24 bytes or 16 MB. Aggregation with Hop-Count Clustering 1

CONSTRUCTION OF HCF TABLE IP Address Aggregation 1

CONSTRUCTION OF HCF TABLE IP Address Aggregation 1

CONSTRUCTION OF HCF TABLE IP Address Aggregation 1

CONSTRUCTION OF HCF TABLE Pollution-Proof Initialization and Update Keeping the IP 2 HC mapping up-to-date is necessary initialization and dynamic update is through TCP connection establishment One way to ensure that only legitimate packets are used attacker cannot slowly pollute an HCF table by spoofing source IP addresses. may be too expensive to inspect and update with each newlyestablished TCP connection user-configurable parameter to adjust the frequency of update. a counter p that records the number of established TCP connections p can also be a function of system load and hence, updates are made more frequently when the system is lightly-loaded. mapping updates may require re-clustering hop-count changes are not a frequent event, the overhead incurred by re-clustering is negligible. 1

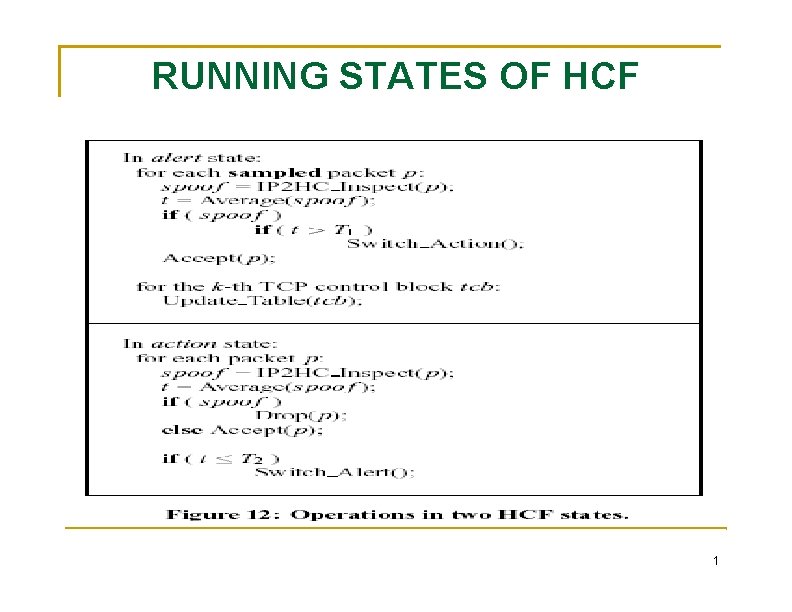
RUNNING STATES OF HCF 1

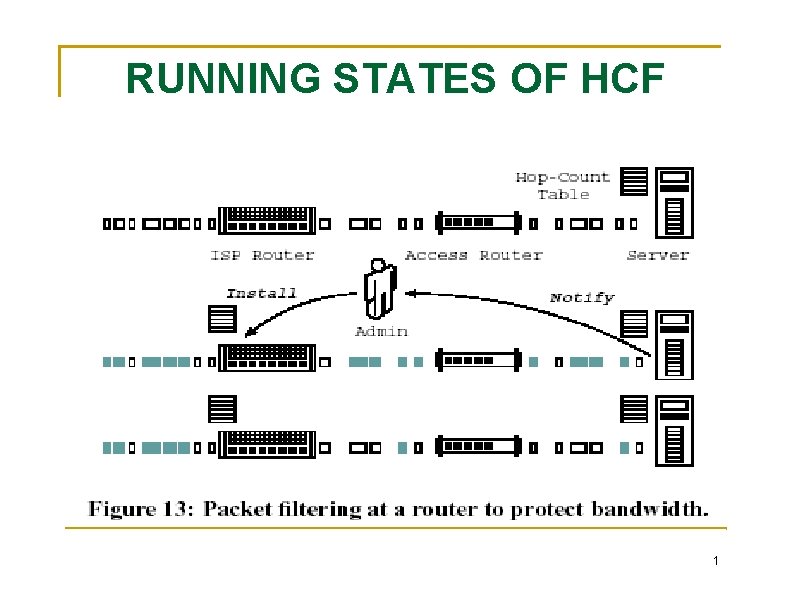
RUNNING STATES OF HCF Introduction of the alert state lowers the overhead of HCF stop DRDo. S HCF specifically looks for IP spoofing, so it will be able to detect attempts to fool servers into acting as reflectors. Blocking Bandwidth Attacks detection and filtering (at the ISP’s edge router) of spoofed packets must be separated One or more machines inside the stub network and the access router must run HCF at least one machine inside the stub network maintain an updated HCF table 1

RUNNING STATES OF HCF 1

RESOURCE SAVINGS Building the Hop-Count Filter The test module resides in the IP packet receive function, ip_rcv. insert the filtering function before the expensive checksum verification. The hop-count mapping 4096 -bucket hash table with chaining to resolve collisions. Each entry in the hash table represents a 24 -bit address prefix. A binary tree is used to cluster hosts within each 24 -bit address prefix. This tree can then be implemented as a linear array of 127 elements. Each element in the array stores the hop-count value of a particular clustering. the HCF-table update insert the function call into the kernel TCP code 1

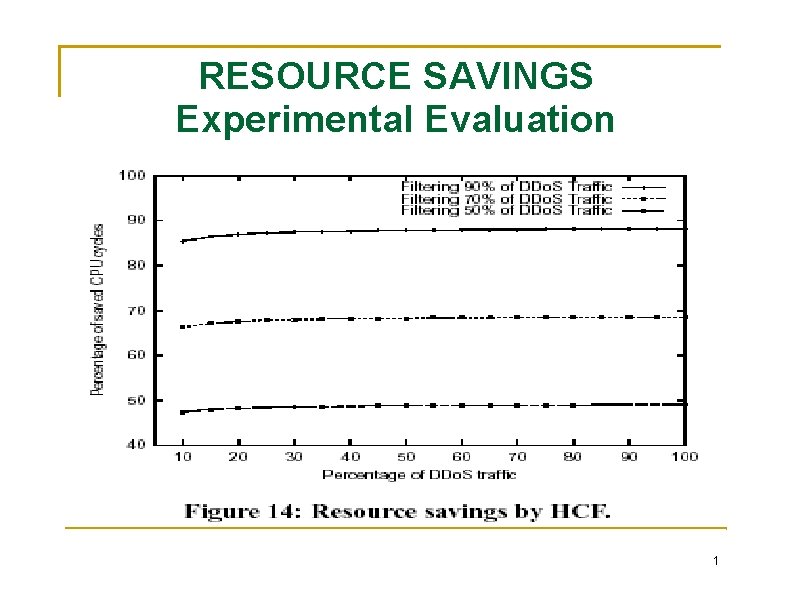
RESOURCE SAVINGS Experimental Evaluation 1

RESOURCE SAVINGS Experimental Evaluation 1

RELATED WORK Despoof Detecting spoofed packets. S. Templeton/K. Levitt. using TTL for detecting spoofed packet ingress filtering compares the TTL of a received packet with the actual TTL of a test packet sent to the source IP address Requires the administrator to determine , and manually verify. High overhead blocks spoofed packets at edge routers, Rely on wide-eployment in IP routers. route-based distributed packet filtering (DPF) Given the reachability constraints 1

RELATED WORK SAVE builds a table of incoming source IP addresses at each router associates each of its incoming interfaces with a set of valid incoming network Path Identifier (Pi) IP traceback marking a path fingerprint in each packet 1

CONCLUSION FUTURE WORK HCF NAT (Network Address Translator) Can detect and discard spoofed IP Without router support Using moderate storage each of which may connect multiple stub networks, could make a single IP address appear to have multiple valid hop-counts at the same time install the HCF system at a victim site for practical use 1
 Ingress filtering vs egress filtering
Ingress filtering vs egress filtering Riorey ddos
Riorey ddos Riorey
Riorey Ddos tabletop exercise
Ddos tabletop exercise Ddos
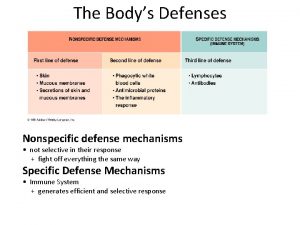
Ddos Nonspecific defense mechanisms
Nonspecific defense mechanisms Control hijacking
Control hijacking Safe internet service
Safe internet service Stateless packet filtering
Stateless packet filtering Doterra taiwan
Doterra taiwan Intensity transformation and spatial filtering
Intensity transformation and spatial filtering Theory of filtration
Theory of filtration Fwps_callout
Fwps_callout Filtering self-rescue respirator
Filtering self-rescue respirator Image filtering
Image filtering Matlab
Matlab Risk ranking and filtering
Risk ranking and filtering Collaborative filtering medium
Collaborative filtering medium Recursive bilateral filtering
Recursive bilateral filtering Band pass filtering in biomedical instrumentation
Band pass filtering in biomedical instrumentation Matched filtering gravitational waves
Matched filtering gravitational waves Frequency filtering
Frequency filtering Filtering organizational behavior
Filtering organizational behavior Restoration in the presence of noise only-spatial filtering
Restoration in the presence of noise only-spatial filtering Collaborative filtering
Collaborative filtering What is stateless packet filtering
What is stateless packet filtering Intensity transformations and spatial filtering
Intensity transformations and spatial filtering Collaborative filtering with temporal dynamics
Collaborative filtering with temporal dynamics Filtering mode
Filtering mode Digital image processing
Digital image processing Frequency filtering
Frequency filtering Spatial filtering
Spatial filtering Post filtering in computer graphics
Post filtering in computer graphics Content filtering trusts
Content filtering trusts Knapp's relationship model
Knapp's relationship model Bragg filtering
Bragg filtering Intensity transformations and spatial filtering
Intensity transformations and spatial filtering