Efficiency Effectiveness Productivity Dell Connected Security in Action












- Slides: 31

Efficiency, Effectiveness, Productivity: Dell Connected Security in Action Florian Malecki, EMEA Product & Solution Marketing Director Network security

Connected Security

Out-Connect the Threats Efficiency, Effectiveness, Productivity: Out-Connect the Threats Dell Connected Security in Action Dell Connected Joanne. Security Moretti Joanne Moretti, Vice President, Software Marketing Ramses Gallego, Security Strategist & Evangelist, Dell Software

Unfortunately, the bad guys are more connected too. They have many names Spear-Phishers, BOTnets, DDo. S, Zero-Day Threats, Insider threats & former employees They’re determined to exploit “disconnected security” Security tools, processes, user profiles and information, separated in siloes that leave dangerous gaps in-between

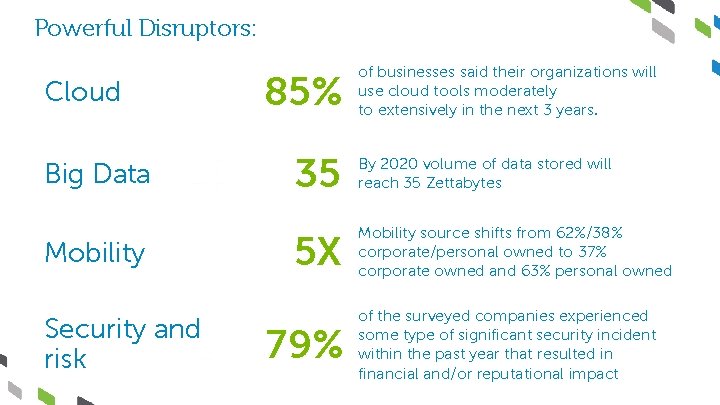
Powerful Disruptors: Cloud Big Data Mobility Security and risk 85% of businesses said their organizations will use cloud tools moderately to extensively in the next 3 years. 35 By 2020 volume of data stored will reach 35 Zettabytes 5 X Mobility source shifts from 62%/38% corporate/personal owned to 37% corporate owned and 63% personal owned 79% of the surveyed companies experienced some type of significant security incident within the past year that resulted in financial and/or reputational impact

The IT Journey From mainframe to client server to distributed to risk everywhere

Security should enable the business… and not inhibit it A more effective and Business efficient way needs are to solve your challenges not starts with an adequately understandin g of how Dell addressed leverages our bycollective security assets. solutions Complex issue • Threats are everywhere and constantly changing • Many technology options to mitigate threats A major pain • Security is identified in the top 3 as the single greatest obstacle to realizing the full benefits of IT Barrier to realizing full IT benefits Top 3

Business can’t stop to wait for security Cloud Saa. S Data growth BYOD How secure Desire: is your To embrace environment business trends with all these new initiatives Challenge: coming into Security often play? gets in the way Web 2. 0 Virtualization Compliance

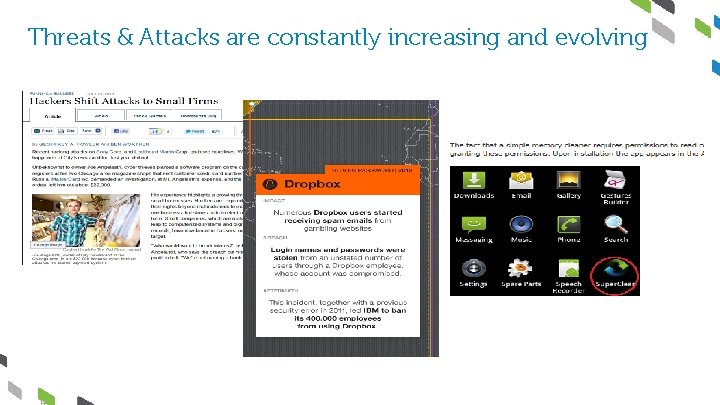
Threats & Attacks are constantly increasing and evolving

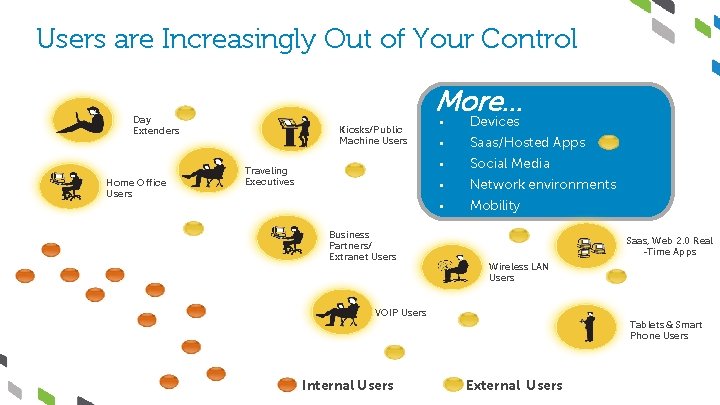
Users are Increasingly Out of Your Control More… Day Extenders Home Office Users Kiosks/Public Machine Users § Devices § Saas/Hosted Apps Social Media § Traveling Executives § § Business Partners/ Extranet Users Network environments Mobility Saas, Web 2. 0 Real -Time Apps Wireless LAN Users VOIP Users Tablets & Smart Phone Users Internal Users External Users

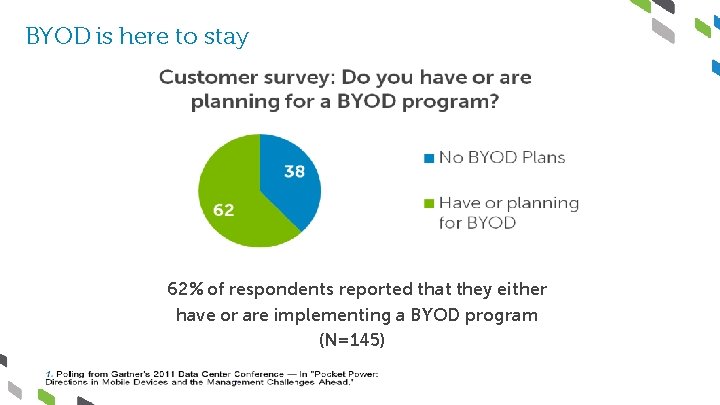
BYOD is here to stay 62% of respondents reported that they either have or are implementing a BYOD program (N=145)

End users don’t get the complexity & could even create security issues… • “I just got a tablet. Let me see if I can connect it to my office network. ” • “I can’t find a secure network at Starbucks. I’m sure the open Wi. Fi is fine for a few hours. ” • “If my office isn’t going to supply me with productivity apps for my phone – I’m just going to download and configure them myself. ” • “If I accidentally lose my phone, I’ll just buy another one. No harm done. ”

Why Mobile Devices Could Be Risky? 13

Every 53 Seconds a laptop is stolen $49, 246 Average value of lost laptop 1 57% Were not protected with mobile security features 1 46% Of lost laptops contained confidential data 1 • Intellectual Property • Customer and employee data • Competitive information IT managers are looking for ways to: $5. 5 M Average organizational cost of a data breach 2 Source: 1. Poneman Institute Study Source: 2 Symantec & Poneman Institute Study: US cost of a Data Breach, 2011 Dell Solutions Tour Data is the most important asset companies own: • Fully protect data wherever it goes without disrupting end users • Save time deploying and managing security • Ensure they remain in compliance • Flexible scale to ensure they meet the requirements of different users

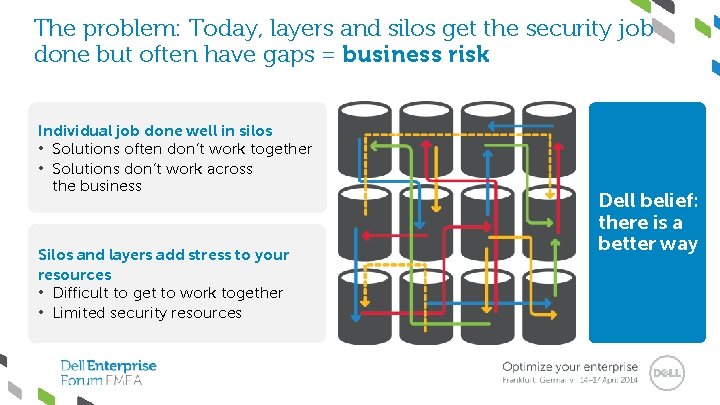
The problem: Today, layers and silos get the security job done but often have gaps = business risk Individual job done well in silos • Solutions often don’t work together • Solutions don’t work across the business Silos and layers add stress to your resources • Difficult to get to work together • Limited security resources Dell belief: there is a better way

Connected Securityfor a connected world Effective Security to enable business while also meeting the needs of security Connected Security is security that… • • Shares and applies intelligence Works with the business, end-to-end Maintains flexibility and open architecture Enables broad contextual awareness with dynamic control Protect information everywhere Efficient Work with the business

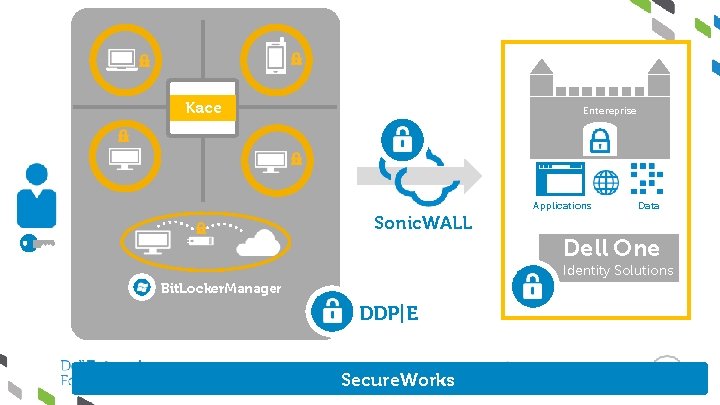
Kace Entereprise Applications Sonic. WALL Data Dell One Identity Solutions Bit. Locker. Manager DDP|E Secure. Works

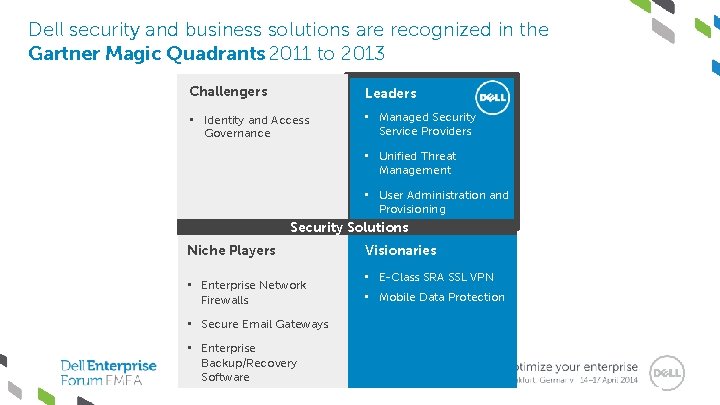
Dell security and business solutions are recognized in the Gartner Magic Quadrants 2011 to 2013 Challengers Leaders • Identity and Access Governance • Managed Security Service Providers • Unified Threat Management • User Administration and Provisioning Security Solutions Niche Players • Enterprise Network Firewalls • Secure Email Gateways • Enterprise Backup/Recovery Software Visionaries • E-Class SRA SSL VPN • Mobile Data Protection

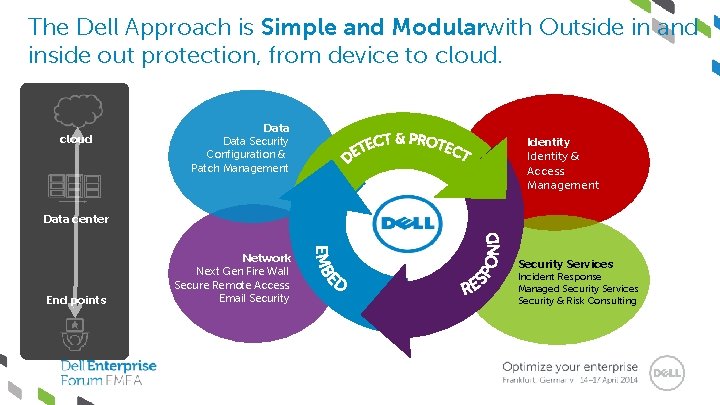
The Dell Approach is Simple and Modularwith Outside in and inside out protection, from device to cloud Data Security Configuration & Patch Management Identity & Access Management Data center Network End points Next Gen Fire Wall Secure Remote Access Email Security Services Incident Response Managed Security Services Security & Risk Consulting

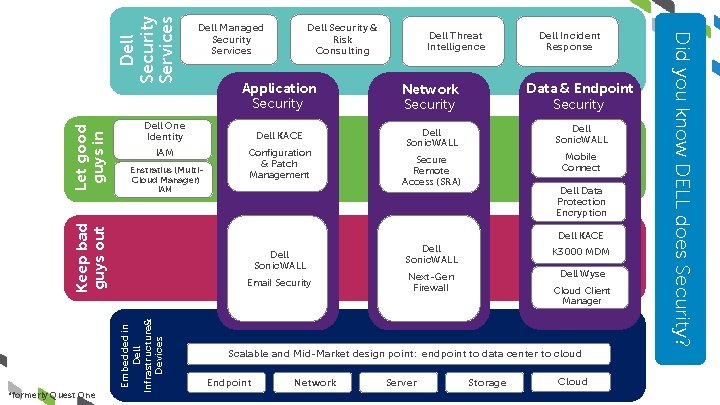
Dell Security Services Dell Incident Response Network Security Data & Endpoint Security Dell KACE Dell Sonic. WALL Secure Remote Access (SRA) Mobile Connect Configuration & Patch Management IAM Keep bad guys out Let good guys in Enstratius (Multi. Cloud Manager) Dell Threat Intelligence Application Security Dell One Identity IAM Dell Security & Risk Consulting Dell Data Protection Encryption Dell KACE Dell Sonic. WALL Embedded in Dell Infrastructure& Devices Email Security Dell Sonic. WALL K 3000 MDM Next-Gen Firewall Dell Wyse Cloud Client Manager Scalable and Mid-Market design point: endpoint to data center to cloud Endpoint Network Server Storage Cloud Did you know DELL does Security? *formerly Quest One Dell Managed Security Services

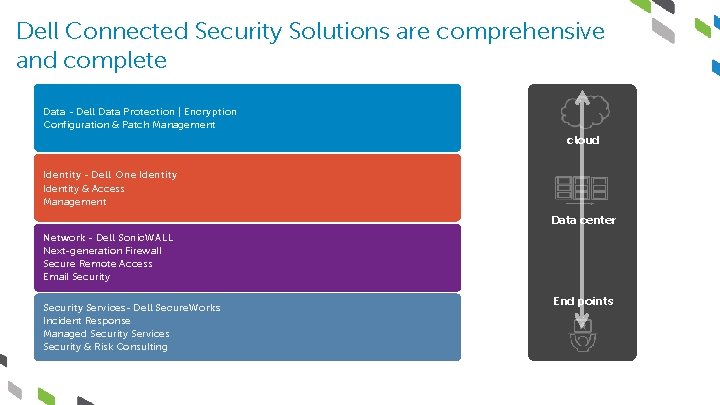
Dell Connected Security Solutions are comprehensive and complete Data - Dell Data Protection | Encryption Configuration & Patch Management cloud Identity - Dell One Identity & Access Management Data center Network - Dell Sonic. WALL Next-generation Firewall Secure Remote Access Email Security Services- Dell Secure. Works Incident Response Managed Security Services Security & Risk Consulting End points

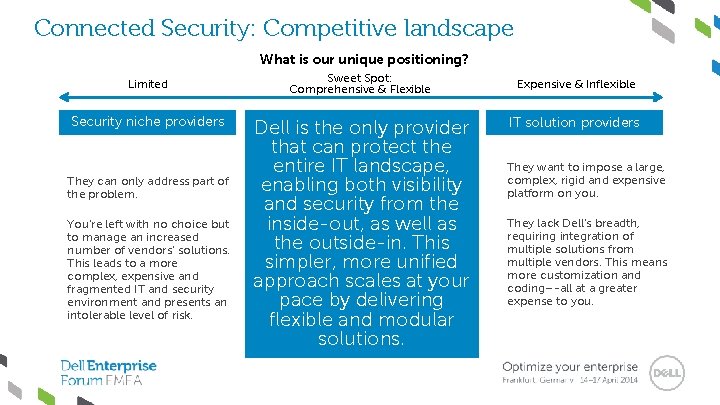
Connected Security: Competitive landscape What is our unique positioning? Limited Security niche providers They can only address part of the problem. You’re left with no choice but to manage an increased number of vendors’ solutions. This leads to a more complex, expensive and fragmented IT and security environment and presents an intolerable level of risk. Sweet Spot: Comprehensive & Flexible Dell is the only provider that can protect the entire IT landscape, enabling both visibility and security from the inside-out, as well as the outside-in. This simpler, more unified approach scales at your pace by delivering flexible and modular solutions. Expensive & Inflexible IT solution providers They want to impose a large, complex, rigid and expensive platform on you. They lack Dell’s breadth, requiring integration of multiple solutions from multiple vendors. This means more customization and coding–-all at a greater expense to you.

Cross sell opps

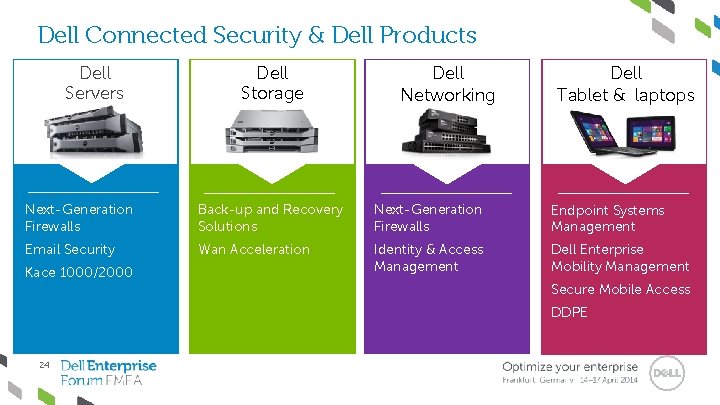
Dell Connected Security & Dell Products Dell Servers Dell Storage Dell Networking Dell Tablet & laptops Next-Generation Firewalls Back-up and Recovery Solutions Next-Generation Firewalls Endpoint Systems Management Email Security Wan Acceleration Identity & Access Management Dell Enterprise Mobility Management Kace 1000/2000 Secure Mobile Access DDPE 24

Snapshot - UK Founded in 1916 as a professional organisation for trained nurses, the Royal College of Nursing (RCN) has evolved into a successful professional union. For almost a century, the RCN has pioneered professional standards for nurses in education, practice and working 21 elementary schools, six middle schools and seven high schools RCN has over 400, 000 members and a widespread workforce, many of whom work from home or remote locations. Challenge Improve remote access security and compliance Deliver a cost-effective and scalable solution that can be rolled out to an expanding user base Results • By deploying a Dell Sonic. WALL Aventail EClass SSL VPN solution, RCN has generated real savings in terms of upfront investment and on-going support costs • Mobile device users are authenticated, ensuring secure BYOD

Snapshot - Germany The blue Ravensburger triangle is one of Germany’s best-known trademarks. Based in Ravensburg, near Lake Constance in southern Germany, this 1, 600 employees company is a leader in the European puzzles and games market. It sells over 8, 000 different products internationally, Challenge Company wanted a secure, flexible and scalable solution to make its IT security functionality future-proofed Results • • • Speedy roll-out of the Dell Sonic. WALL EClass NSA 5500, NSA series and TZ series at the international locations Flexible, scalable deployment with Dell Sonic. WALL GMS centralized management Deep Packet Inspection for expanding SSL-encrypted data traffic Software

Snapshot – France (EMEA HQs) Patagonia grew out of a small company that made tools for climbers. Alpinism remains at the heart of a worldwide business that still makes clothes for climbing – as well as for skiing, snowboarding, surfing, fly fishing, paddling and trail running, and employs over 1600 employees worldwide. Challenge The company needed to update its legacy firewalls and implement a centralised management tool to make it easy to deploy and manage. Application Intelligence and Control firewall functionalities and Qo. S were also key requirements. Results • Fast implementation of the Dell Sonic. WALL EClass NSA 5500, TZ series and Wireless Access Points at the EMEA HQs and remote locations • Better bandwidth usage and management • Efficient and cost-effective distributed network implementation • Better work-life balance thanks to secure remote access Software

Snapshot - Switzerland Founded in Switzerland in 1874, the Schindler Group is a leading global provider of elevators, escalators and related services. Behind the company's success are over 45, 000 employees in more than 100 countries. Challenge Schindler Group relied on an infrastructure lacking a central IAM/IAG system that was based on a number of different HR systems and 72 different Active Directory Domains. Results • The company initiated the transition of existing HR systems into one global HR system as a premise. The Dell IAM processes rely on feeds from this system for both employees and external users • Frictionless full visibility and control now in the hands of the right people.

SBB CFF FFS Cargo Switzerland’s major rail operator– plays a central role in transporting thosegoods Challenge SBB Cargo wanted to increase train driver productivity by digitising documents with online devices. It also wanted to lower costs by managing in-house the devices used by train drivers Results • SBB Cargo reduces costs by CHF 2 million a year • IT gains in-depth reports at least 70 % faster • The firm saves around CHF 360, 000 with single pricing • SBB Cargo lowers costs and invests more in the IT network

Thank You

Notices & Disclaimers Copyright © 2014 by Dell, Inc. No part of this document may be reproduced or transmitted in any form without the written permission from Dell, Inc. This document could include technical inaccuracies or typographical errors. Dell may make improvements or changes in the product(s) or program(s) described herein at any time without notice. Any statements regarding Dell’s future direction and intent are subject to change or withdrawal without notice, and represent goals and objectives only. References in this document to Dell products, programs, or services does not imply that Dell intends to make such products, programs or services available in all countries in which Dell operates or does business. Any reference to an Dell Program Product in this document is not intended to state or imply that only that program product may be used. Any functionality equivalent program, that does not infringe Dell’s intellectual property rights, may be used. The information provided in this document is distributed “AS IS” without any warranty, either expressed or implied. Dell EXPRESSLY DISCLAIMS any warranties of merchantability, fitness for a particular purpose OR INFRINGEMENT. Dell shall have no responsibility to update this information. The provision of the information contained herein is not intended to, and does not, grant any right or license under any Dell patents or copyrights. Dell, Inc. 300 Innovative Way Nashua, NH 03063 USA 31 Dell Software