Dimensions of E Commerce Security l l l















- Slides: 17

Dimensions of E – Commerce Security l l l Integrity Non – Repudiation Authenticity Confidentiality Privacy Availability

One Line explanation l l l INTEGRITY: prevention against unauthorized data modification NON-REPUDIATION: prevention against any one party from denying on an agreement after the fact AUTHENTICITY: authentication of data source CONFIDENTIALITY: protection against unauthorized data disclosure PRIVACY: provision of data control and disclosure AVAILABILITY: prevention against data delays or removal

Integrity: prevention against unauthorized data modification This is the ability to ensure that information being displayed on a Web site or being transmitted/received over the Internet has not been altered in any way by an unauthorized party. Integrity ensures data remains as is from the sender to the receiver. Example 1: One type of integrity security breach would be an unauthorized person intercepting and redirecting a bank wire transfer into a different account. Example 2: If someone added an extra bill to the envelope, which contained your credit card bill, he has violated the integrity of the mail.

Bank Wire & Bank Wire Transfer (just concept) An electronic message system allowing major banks to communicate various actions or occurrences regarding client accounts. l For example, the purpose of a bank wire would be to notify a bank if a client has deposited funds into its account. Bank Wire Transfer l l l A wire transfer is a transfer of money from one bank account to another. The actual transfer is done by the bank, and neither the sender nor the recipient of the money sees or touches the actual funds. http: //www. ehow. com/how_2817_conduct-wiretransfer. html (more info)

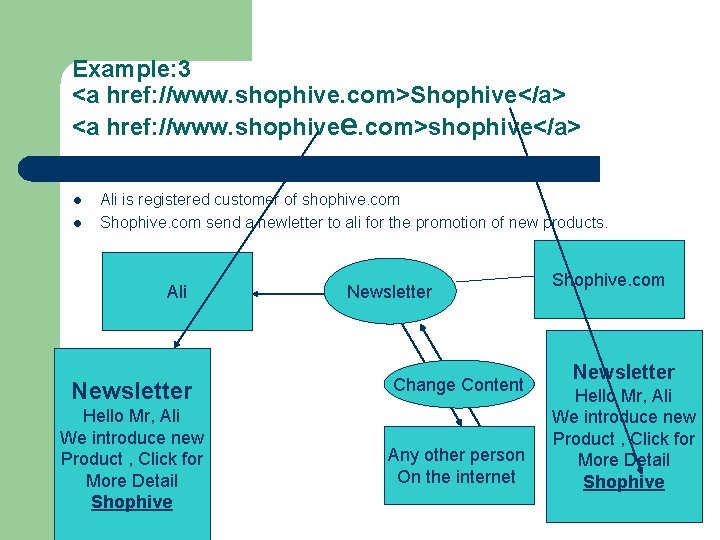
Example: 3 <a href: //www. shophive. com>Shophive</a> <a href: //www. shophivee. com>shophive</a> l l Ali is registered customer of shophive. com Shophive. com send a newletter to ali for the promotion of new products. Ali Newsletter Change Content Hello Mr, Ali We introduce new Product , Click for More Detail Shophive Any other person On the internet Shophive. com Newsletter Hello Mr, Ali We introduce new Product , Click for More Detail Shophive

Customer & Merchant prospective on Integrity dimension of e-commerce Customer’s Prospective: Has information I transmit or receive been altered? Merchant’s Prospective: Has data on the site been altered without authorization? Is data being received from customers valid?

Nonrepudiation: prevention against any one party from reneging on an agreement after the fact the ability to ensure that e-commerce participants do not deny their online actions. Example 1: An example of a repudiation incident would be a customer ordering merchandise online and later denying that he or she had done so. The credit card issuer will usually side with the customer because the merchant has no legally valid proof that the customer ordered the merchandise.

Customer & Merchant prospective on Non – Repudiation dimension of e-commerce Customer’s Prospective: Can a party to an action with me later deny taking the action? Merchant’s Prospective: l Can a customer deny ordering products?

Authenticity: authentication of data source Authenticity is the ability to identify the identity of a person or entity you are transacting with on the Internet. Example 1: One instance of an authenticity Example 2: One instance of an authenticity security breach is “spoofing, ” in which someone uses a fake e-mail address, or poses as someone else. This can also involve redirecting a Web link to a different address. security breach in which postman deliver the mail to a wrong address.

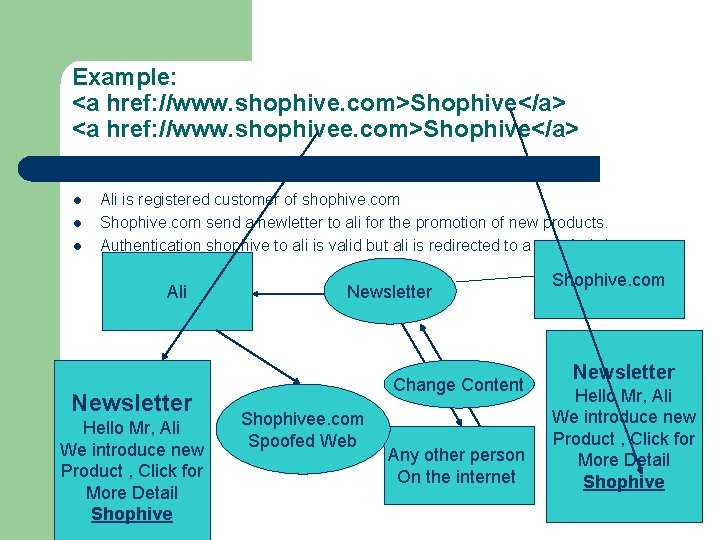
Example: <a href: //www. shophive. com>Shophive</a> <a href: //www. shophivee. com>Shophive</a> l l l Ali is registered customer of shophive. com Shophive. com send a newletter to ali for the promotion of new products. Authentication shophive to ali is valid but ali is redirected to a spoofed site. Ali Newsletter Hello Mr, Ali We introduce new Product , Click for More Detail Shophive Newsletter Change Content Shophivee. com Spoofed Web Any other person On the internet Shophive. com Newsletter Hello Mr, Ali We introduce new Product , Click for More Detail Shophive

Customer & Merchant prospective on Authenticity dimension of e-commerce Customer’s Prospective: Who am I dealing with? How can I be assured that the person or entity is who they claim to be? Merchant’s Prospective: l What is the real identity of the customer?

Confidentiality: protection against unauthorized data disclosure Privacy concerns people or control over information, whereas confidentiality concerns data. Confidentiality: The ability to ensure that messages and data are available only to authorized viewers. One type of confidentiality security breach is “sniffing” in which a program is used to steal proprietary information on a network including e-mail messages, company files, or confidential reports. Bank send credit card pin on your address but someone (postman etc) read it. (it is breach of confidentiality)

Customer & Merchant prospective on Confidentiality dimension of e-commerce Customer’s Prospective: Can someone other than the intended recipient read my messages? Merchant’s Prospective: l Are messages or confidential data accessible to anyone other than those authorized to view them?

Privacy: provision of data control and disclosure The ability to control the use of information a customer provides about him or herself to an e-commerce merchant. An example of a privacy security breach is a hacker breaking into an e-commerce site and gaining access to credit card or other customer information. This violates the confidentiality of the data and also the privacy of the people who supplied the data.

Customer & Merchant prospective on Privacy dimension of e-commerce Customer’s Prospective: Can I control the use of information about myself transmitted to an e-commerce merchant? Merchant’s Prospective: What use , if any, can be made of personal data collected as part of an e-commerce transaction? Is the personal information of customers being used in an unauthorized manner?

Availability: prevention against data delays or removal This is the ability to ensure that an e-commerce site continues to function as intended. Availability ensures you have access and are authorized to resources. Example 1 : One availability security breach is a Do. S (Denial of Service) attack in which hackers flood a Web site with useless traffic that causes it to shut down, making it impossible for users to access the site. Example 2: If the post office destroys your mail or the postman takes one year to deliver your mail, he has impacted the availability of your mail.

Customer & Merchant prospective on Availability dimension of e-commerce Customer’s Prospective: Can I get access to the site? Merchant’s Prospective: Is the site Operational?