Digital Identities for Networks and Convergence Joao Girao

- Slides: 17

Digital Identities for Networks and Convergence Joao Girao, Amardeo Sarma

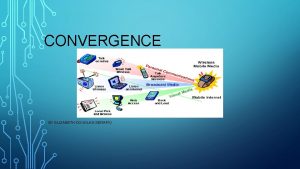
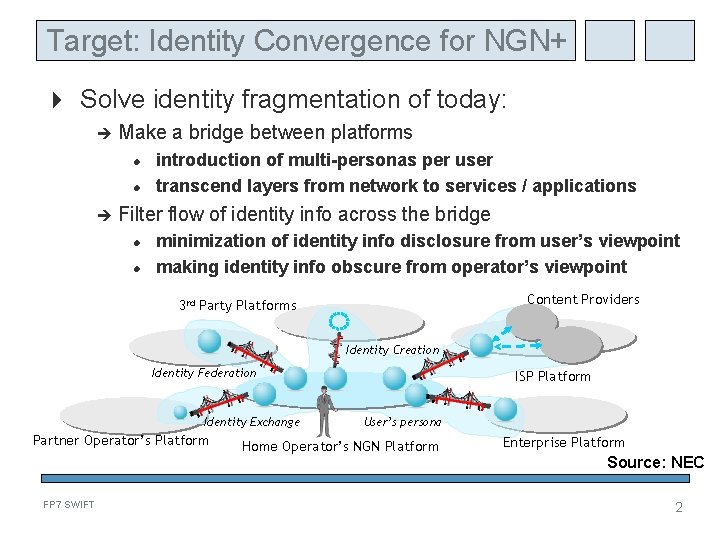
Target: Identity Convergence for NGN+ Solve identity fragmentation of today: Make a bridge between platforms introduction of multi-personas per user transcend layers from network to services / applications Filter flow of identity info across the bridge minimization of identity info disclosure from user’s viewpoint making identity info obscure from operator’s viewpoint Content Providers 3 rd Party Platforms Identity Creation Identity Federation Identity Exchange Partner Operator’s Platform FP 7 SWIFT ISP Platform User’s persona Home Operator’s NGN Platform Enterprise Platform Source: NEC 2

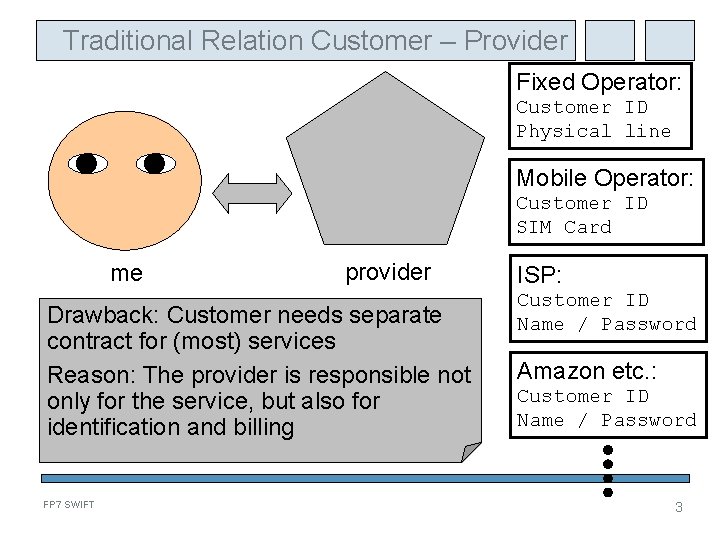
Traditional Relation Customer – Provider Fixed Operator: Customer ID Physical line Mobile Operator: Customer ID SIM Card me provider Drawback: Customer needs separate contract for (most) services Reason: The provider is responsible not only for the service, but also for identification and billing FP 7 SWIFT ISP: Customer ID Name / Password Amazon etc. : Customer ID Name / Password 3

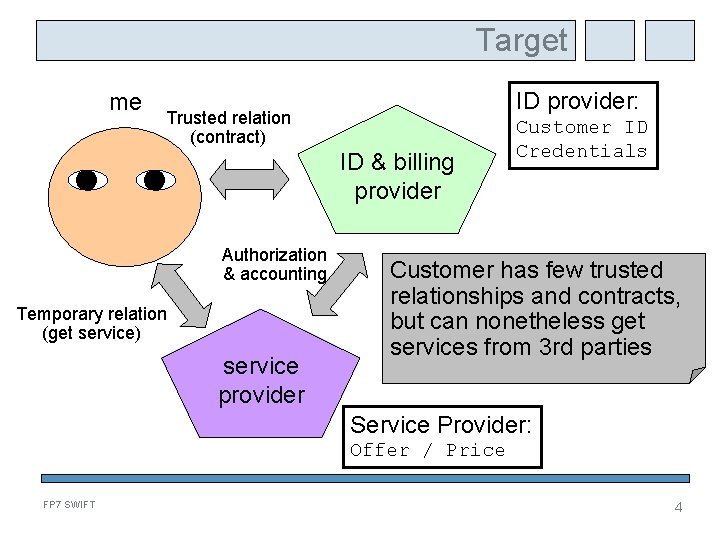
Target me ID provider: Trusted relation (contract) ID & billing provider Authorization & accounting Temporary relation (get service) service provider Customer ID Credentials Customer has few trusted relationships and contracts, but can nonetheless get services from 3 rd parties Service Provider: Offer / Price FP 7 SWIFT 4

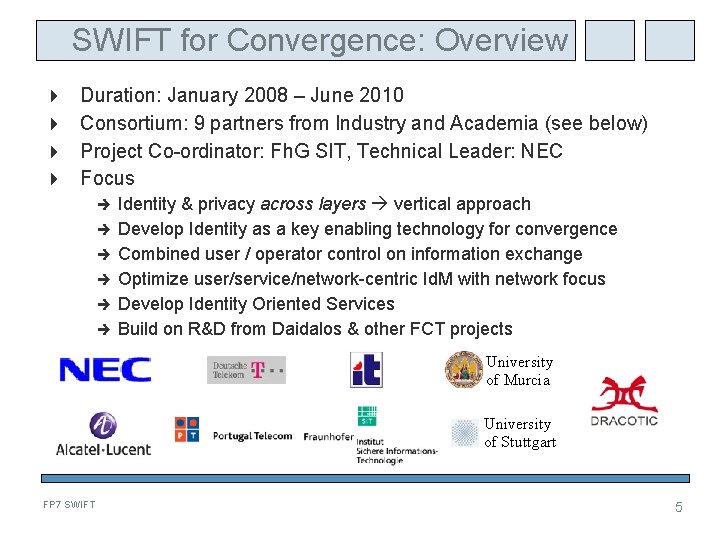
SWIFT for Convergence: Overview Duration: January 2008 – June 2010 Consortium: 9 partners from Industry and Academia (see below) Project Co-ordinator: Fh. G SIT, Technical Leader: NEC Focus Identity & privacy across layers vertical approach Develop Identity as a key enabling technology for convergence Combined user / operator control on information exchange Optimize user/service/network-centric Id. M with network focus Develop Identity Oriented Services Build on R&D from Daidalos & other FCT projects University of Murcia University of Stuttgart FP 7 SWIFT 5

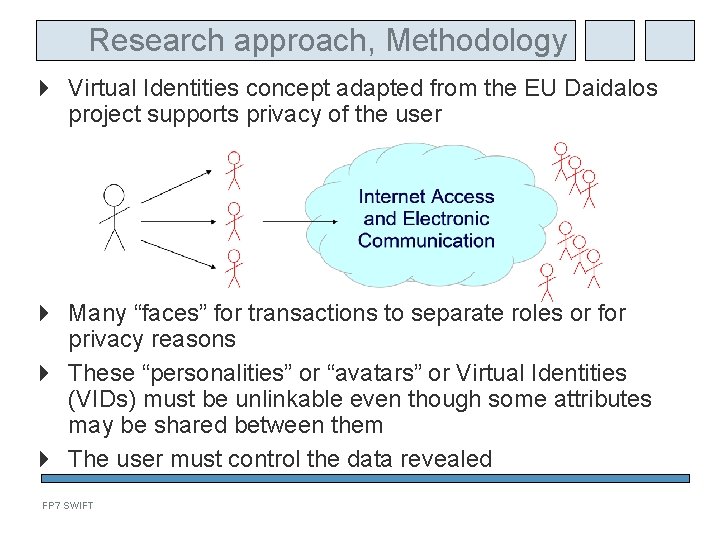
Research approach, Methodology Virtual Identities concept adapted from the EU Daidalos project supports privacy of the user Many “faces” for transactions to separate roles or for privacy reasons These “personalities” or “avatars” or Virtual Identities (VIDs) must be unlinkable even though some attributes may be shared between them The user must control the data revealed FP 7 SWIFT

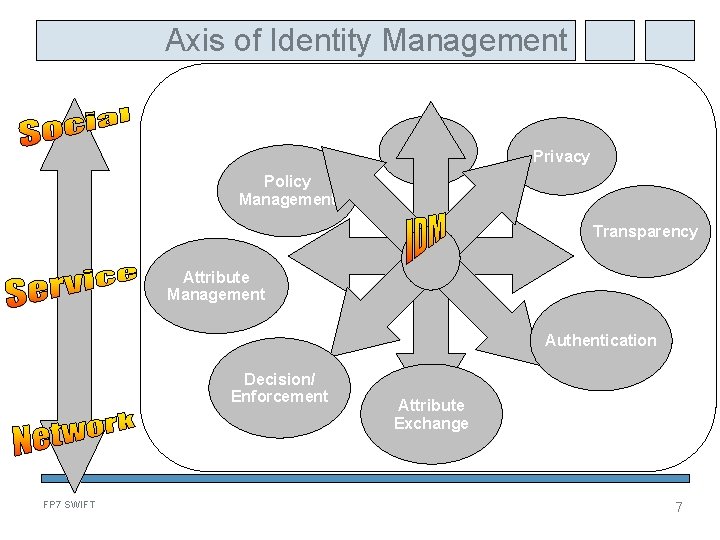
Axis of Identity Management Billing Privacy Policy Management Transparency Attribute Management Authentication Decision/ Enforcement FP 7 SWIFT Attribute Exchange 7

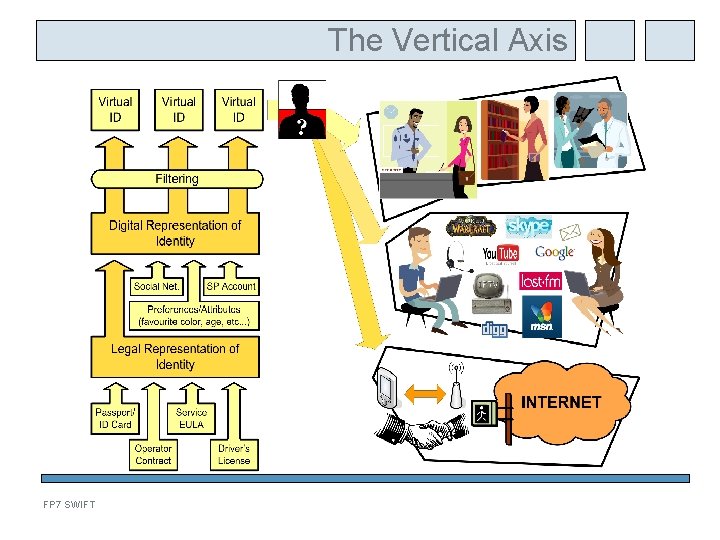
The Vertical Axis FP 7 SWIFT

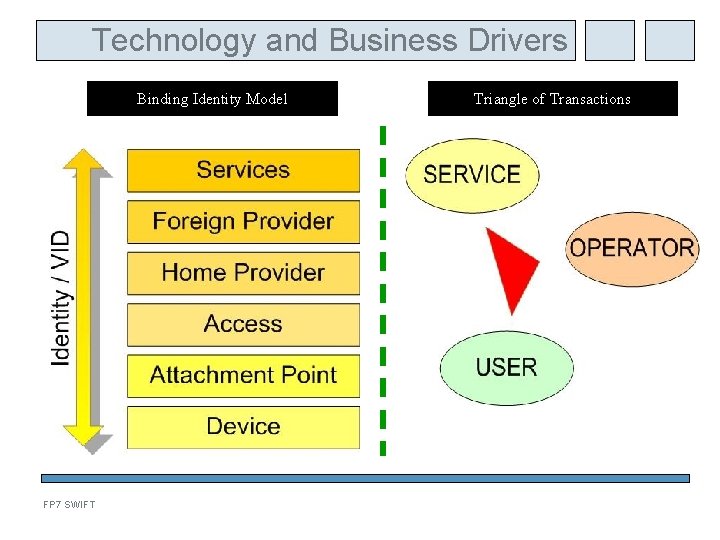
Technology and Business Drivers Binding Identity Model FP 7 SWIFT Triangle of Transactions

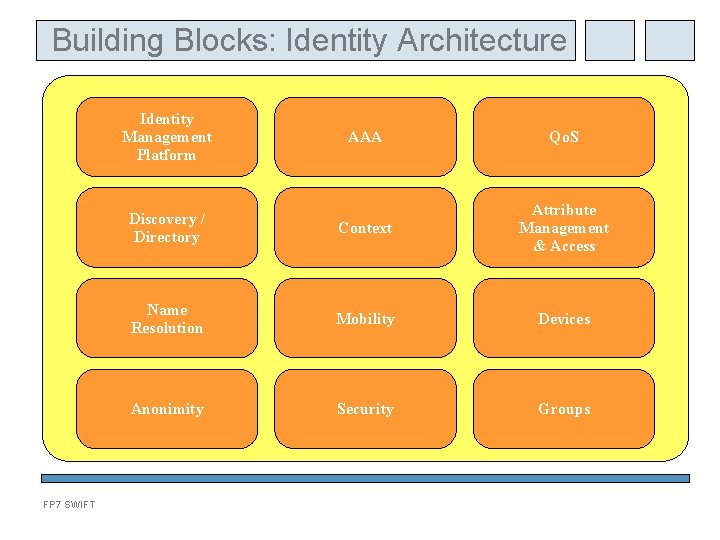
Building Blocks: Identity Architecture Identity Management Platform FP 7 SWIFT AAA Qo. S Discovery / Directory Context Attribute Management & Access Name Resolution Mobility Devices Anonimity Security Groups

Goal 1: Enhance Ubiquity and Experience Liberate user from device(s) by enabling use of several interchangeable devices Ownership of the device should be independent of who uses it hiring (embedded) devices becomes part of the model Facilitate discovery and service usage respecting the user's privacy options Network access is automatically made available based on service requested Invisible co-ordination of network and resources Supported by the Identity Backbone

Goal 2: Enable Convergence Identity can form the bridge between networks, services, content and arbitrary offerings it becomes a convergence technology Currently a vast range of solutions exist that need to be brought together This includes SIM and USIM solutions Central will be to also impact emerging NGN architectures 3 GPP, ITU-T, ETSI A key problem to solve will be to bridge the independently existing Identity solutions (SAML, Open. ID, Card. Space, . . . ) SWIFT will develop solutions for this Identity as the convergence enabler

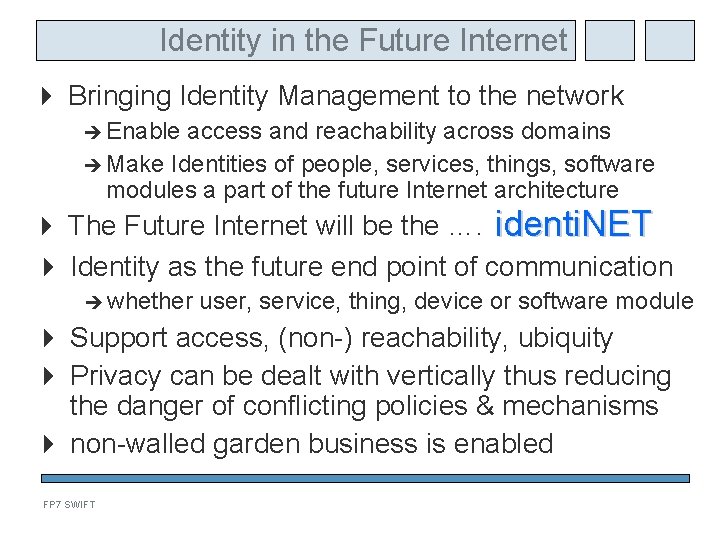
Identity in the Future Internet Bringing Identity Management to the network Enable access and reachability across domains Make Identities of people, services, things, software modules a part of the future Internet architecture The Future Internet will be the …. identi. NET Identity as the future end point of communication whether user, service, thing, device or software module Support access, (non-) reachability, ubiquity Privacy can be dealt with vertically thus reducing the danger of conflicting policies & mechanisms non-walled garden business is enabled FP 7 SWIFT

SWIFT results so far Kick off in 01/08 with Public Web Page in January Work well progressed on Scenario definition Requirements Initial architecture Deliverables done and mid-term Work Methods Internal Report on Dissemmination Scenarios Gap Analysis and Architecture Requirements Initial Architecture FP 7 SWIFT

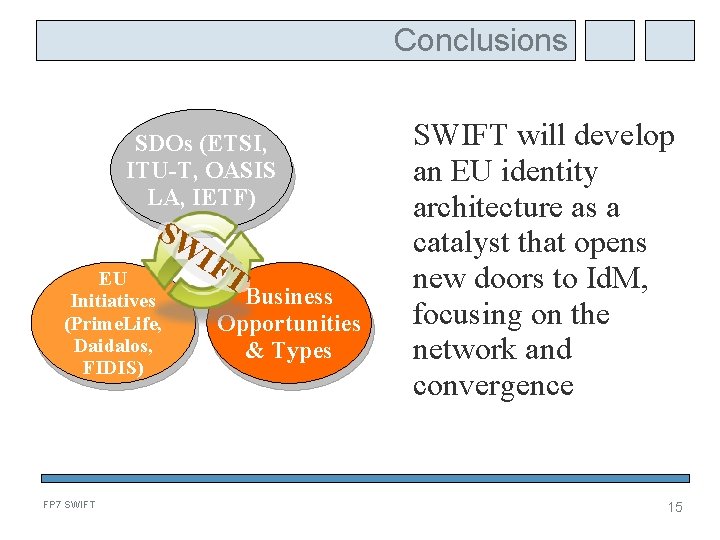
Conclusions SDOs (ETSI, ITU-T, OASIS LA, IETF) SW EU Initiatives (Prime. Life, Daidalos, FIDIS) FP 7 SWIFT IF T Business Opportunities & Types SWIFT will develop an EU identity architecture as a catalyst that opens new doors to Id. M, focusing on the network and convergence 15

SWIFT Website http: //www. ist-swift. org

End Thank You
 Define absolute convergence
Define absolute convergence Svenskt ramverk för digital samverkan
Svenskt ramverk för digital samverkan Comparison of virtual circuit and datagram network
Comparison of virtual circuit and datagram network Hyper convergence définition
Hyper convergence définition Backbone networks in computer networks
Backbone networks in computer networks Precedence of logic gates
Precedence of logic gates Digital communications and networks
Digital communications and networks Analogue and digital transmission in computer networks
Analogue and digital transmission in computer networks Bozel são joão del rei
Bozel são joão del rei João e andré empurram caixas idênticas e de mesma massa
João e andré empurram caixas idênticas e de mesma massa Brandao filho
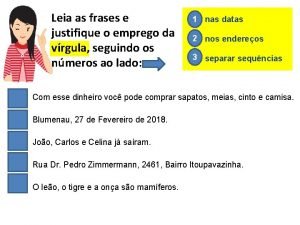
Brandao filho Leia e pontue corretamente usando
Leia e pontue corretamente usando Frases de joão batista scalabrini
Frases de joão batista scalabrini João leite da silva ortiz
João leite da silva ortiz João 10, 22-30
João 10, 22-30 João candido
João candido Porm
Porm Crónica de d joão i resumo capítulo 115
Crónica de d joão i resumo capítulo 115