CSC 382582 Computer Security Denial of Service CSC





















- Slides: 29

CSC 382/582: Computer Security Denial of Service CSC 382/582: Computer Security 1

Topics 1. 2. 3. 4. 5. 6. 7. Introduction History of Do. S Modes of Attack Technical Attacks Distributed DOS (DDOS) Computational Attacks Defending against Do. S CSC 382/582: Computer Security 2

Denial of Service • Attacks against availability of services. • Common attacks: – CAIDA conservatively estimated 4000/week. – Attacks have increased since 2001 estimate. • Most Do. S vs. small site for short duration. • However, Do. S attacks can be very big – Millions of packets/second. – Many thousands of hosts involved. • Do. S attacks are very difficult to stop. CSC 382/582: Computer Security 3

Denial of Service Motives • Attacker Competitions – Take over IRC channels. – Fame: take down a well-known target. – Revenge for being Do. Sed. • Political – Take down computers of political opponents. • Financial – Take down competitor web site. – Extortion: pay attacker or be Do. Sed. CSC 382/582: Computer Security 4

History of Denial of Service 1988: Morris Worm brings down most of Internet. 1996: SYN flood attacks take out IRC networks. 1997: Fragment attacks used to Do. S Windows systems. 1998: Distributed Do. S attack tools appear. 1999: Heavy use of DDo. S tools. 2000: DDo. S attacks takes down Amazon, e. Bay, Yahoo. 2001: Reflected DDo. S attacks appear. 2002: DDo. S takes down 9 of 13 root DNS servers. 2003: DDo. S takes down Al-Jazeera after broadcasting pictures of captured American soldiers. 2003 -: Financially motivated DDo. S. Spammers DDo. S antispam organizations. Extortionists DDo. S small sites. CSC 382/582: Computer Security 5

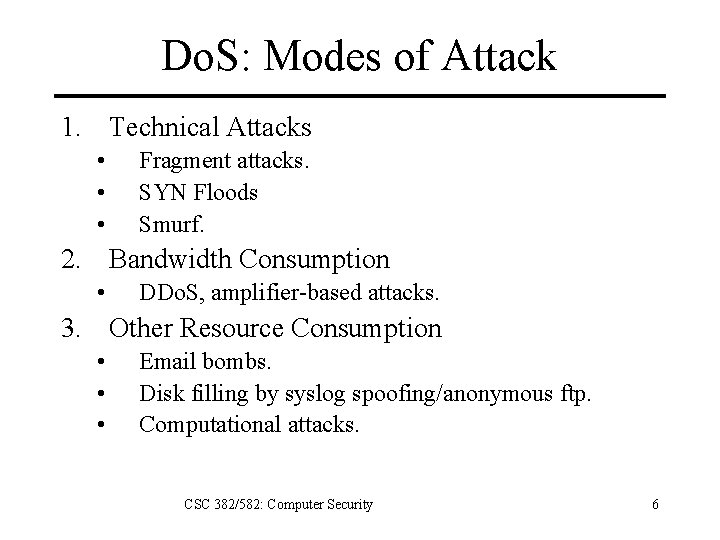
Do. S: Modes of Attack 1. Technical Attacks • • • Fragment attacks. SYN Floods Smurf. 2. Bandwidth Consumption • DDo. S, amplifier-based attacks. 3. Other Resource Consumption • • • Email bombs. Disk filling by syslog spoofing/anonymous ftp. Computational attacks. CSC 382/582: Computer Security 6

Packet Fragmentation Occurs at IP layer Each fragment has own IP header Characteristics: – Each fragment of a packet has same identification field. – More Fragments flag set (except on final frag). – Fragment Offset is offset (8 -byte units) of fragment from beginning of original datagram. – Total Length field is length of fragment. CSC 382/582: Computer Security 7

Fragment Security Issues Large Datagrams – Use multiple fragments that will be re-assembled into a packet larger than the maximum IP packet size of 64 KB. – example: ping of death Incomplete Datagrams – Jolt 2: stream of fragments, with no first fragment. Overlapping Fragments – Fragment offsets overlap, so during reassembly, second packet is copied over part of TCP header, allowing true header to be hidden in second packet while firewall reads misleading header data from first packet. – Denial of Service: Teardrop attack uses overlapping fragments to overflow integer in memory copy to crash Windows 95/NT and Linux <2. 0. 32 hosts. CSC 382/582: Computer Security 8

SYN Floods Create many half-open connections to target – Send SYN packet from spoofed, invalid IP address. – Ignore SYN+ACK response Target connection table fills up – all new TCP connections refused SYN a, ACK x SYN b, ACK y SYN c, ACK z SYN x SYN y SYN z SYN_RECV x from IP n SYN_RECV y from IP n SYN_RECV z from IP n Attacker Target CSC 382/582: Computer Security 9

SYN Flood Defences • Micro-connections: Allocate few resources (~16 bytes) micro-record until ACK recv’d • RST Cookies: – Server sends incorrect SYN+ACK to first client connection request, eliciting RST as response. Thereafter, connections from that client are accepted. • SYN Cookies: Store state in ISN, not on server. – Compute ISN using hash of src + dst IP addresses and ports. – Valid clients will respond with ISN+1, allowing server to compute connection table entry. CSC 382/582: Computer Security 10

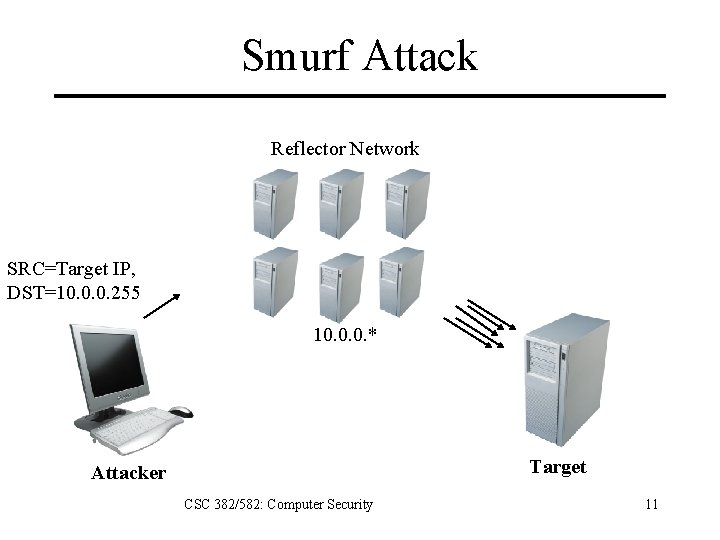
Smurf Attack Reflector Network SRC=Target IP, DST=10. 0. 0. 255 10. 0. 0. * Target Attacker CSC 382/582: Computer Security 11

Smurf Attack Build special ICMP/UDP echo packet Forge IP source address to be that of target. Destination address is a broadcast address. Each host that receives broadcast will respond to the spoofed target address with an echo packet, overwhelming target host. Most current routers refuse to pass on directed broadcast packets. CSC 382/582: Computer Security 12

DDo. S Attacks Attack zombies: • Use valid protocols • Spoof source IP • Massively distributed • Variety of attacks Provider Infrastructure: • DNS, routers, and links Access Line CSC 382/582: Computer Security Entire Data Center: • Servers, security devices, routers 13 • Ecommerce, web, DNS, email, …

Timeline of a DDOS Attack 1. Set up DDOS Network (Botnet) 1. Manual compromise by group of crackers. 2. Automated comprise by a worm. 2. Launch Attack 3. Victim networks become unresponsive Identification difficult due to router/host failures and lack of logging of packets. 4. Third party effects Victim responses sent to spoofed IP addresses. CSC 382/582: Computer Security 14

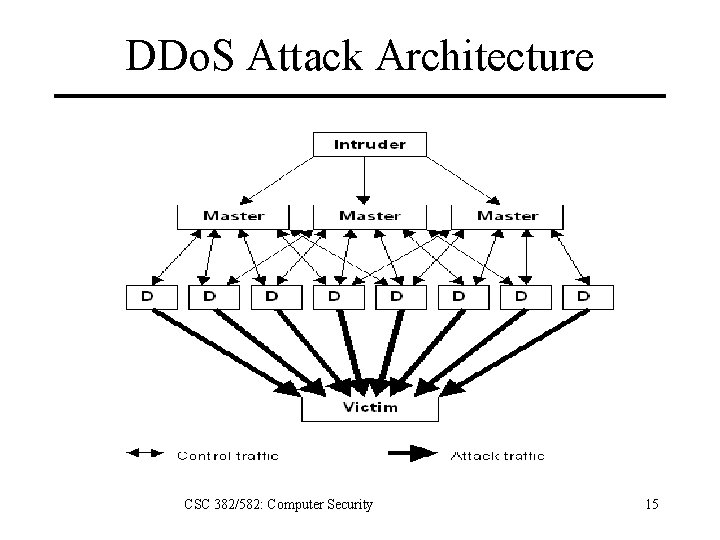
DDo. S Attack Architecture CSC 382/582: Computer Security 15

DDOS Machines Intruder: One or more intruders access master machines to control network, typically through intermediate proxies. Master: The command control servers that control agents. Multiple masters are used for redundancy and scalability. Often communication is via the IRC protocol. Agent: Infected hosts that launch DDOS attack and recruit more agents, aka zombies or bots. CSC 382/582: Computer Security 16

Level of Automation • Manual – Manual compromise and attack • Semi-automated – Use of automated exploit to compromise hosts, then DDo. S agent (Stacheldraht, TFN 2 k, Trinoo) • Automated – Worm such as W 32/Blaster CSC 382/582: Computer Security 17

Agent Lifecycle 1. 2. 3. 4. 5. 6. 7. Old agent scanner selects target host. Old agent attempts exploit against target. If exploit ok, agent transfers self to target. Agent begins running on target. Agent registers itself with master server. Master accepts agent as member w/ pw. Agent logs into communication channel with provided password. 8. Agent waits for commands from master. CSC 382/582: Computer Security 18

Agent Capabilities • DDOS Attacks – – – SYN floods Smurf UDP floods ICMP floods Mixed • Recruitment – Scanning engine. – Many exploits. – Use other bot backdoors. CSC 382/582: Computer Security • • • File transfer Proxying E-mail harvesting Sniffing Spamming Self-defence – Anti-virus – Polymorphism – Rootkit. 19

Botnet Families • Agobot/Phatbot – Over 500 variants. – Modular structure: easy to add features. – Some use WASTE p 2 p communication. • SDBot – Simpler than Agobot, but common. • m. IRC-based bots – Script m. IRC client for Windows. CSC 382/582: Computer Security 20

Distributed Reflection DOS Combine SYN Flood + DDOS attacks – Forge target’s IP address in SYN flood on multiple reflection servers. – Amplification: most OSes send multiple SYN+ACK responses to SYN packet. – Concealment: packets come from multiple reflection servers, not actual attacker host. – Difficult to block: attacker may rotate attacks from large pool of reflection servers, many of which may be important hosts which you need to receive traffic from. CSC 382/582: Computer Security 21

Computational Attacks • Goal: Exhaust CPU resources of target. • Target: Application Layer • Examples: – 2002. BBCode markup language of php. BB could consume 100% CPU in infinite expansion of multiply nested tags. – 2003. Crosby and Wallach show to select input to reduce hash (O(1) performance) to linked list (O(n) performance). Attacks vs. Bro IDS, perl. – 2005. Tomcat 5. 5 directory listing of large directories could use large amounts of CPU. CSC 382/582: Computer Security 22

Why DDo. S is Hard to Stop 1. Attacker ease of use Attackers can d/l user friendly advanced tools. 2. IP spoofing DDo. S attacks can always be spoofed. 3. Numerous agents Attacker agents spread across networks. 4. Variety of traffic DDo. S attacks can be launched with any protocol. 5. High-volume traffic At DDo. S traffic volumes, firewalls and IDS must analyze each packet quickly, i. e. without deep packet inspection or cross-packet correlations. CSC 382/582: Computer Security 23

Filterable and non-Filterable Attacks – Attack non-essential services (ICMP echo) or ports (random UDP flood. ) Non-filterable Attacks – Attack essential services (email or web. ) – Packets may be partially valid for targeted protocol. CSC 382/582: Computer Security 24

DDOS Prevention • Apply patches against technical attacks. • Firewall rules to drop known attacks at perimeter. • Overprovisioning – Network bandwidth, NICs – Memory, disk – CPU • Load balancing • Caching – Create static page frequently instead of dynamically creating page whenever accessed. CSC 382/582: Computer Security 25

DDOS Detection • Detecting zombie hosts – DDOSPing – Zombie Zapper • Detecting a DDOS attack – Performance monitoring: network and host – Network intrusion detection systems CSC 382/582: Computer Security 26

DDOS Reaction • Filter out identifiable DDOS traffic. • Contact ISP for help with – Filtering and rate limiting. – Tracking down source of attack. • Move the target – White House avoided by changing IP address. • Use Alternate Infrastructure – Use caching to decrease server load. – Use anti-ddos provider like Akamai, Prolexic. CSC 382/582: Computer Security 27

Key Points • Types of denial of service attack – Technical attacks (SYN flood, smurfing) – Bandwidth attacks (DDOS) • DOS attacks are a serious threat – Can take down large sites (often for money. ) – Difficult to prevent and react to. • Botnets make DDOS easy and effective – Agents evolve rapidly, offer auto-updating. CSC 382/582: Computer Security 28

References 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. “Al-Jazeera Hobbled by DDOS Attack, ” Info. World, http: //www. infoworld. com/article/03/03/26/HNjazeera_1. html, March 26, 2003. Scott Berinato, “How a Bookmaker and a Whiz Kid Took On an Extortionist—and Won, ” CSO Online, http: //www. csoonline. com/read/050105/extortion_pf. html, Nov 22 2003. CERT Coordination Center, “Results of the Distributed-Systems Intruder Tools Workshop, ” December 1999, http: //www. cert. org/reports/dsit_workshop-final. html David Dittrich, DDOS Archives, http: //staff. washington. edu/dittrich/misc/ddos/, 2006. Greene, “ISP Security 101 Primer, ” http: //www. nanog. org/mtg-0602/greene. html, 2003. The Honeynet Project, “Know Your Enemy: Tracking Botnets, ” http: //www. honeynet. org/papers/bots/, 2005. Steve Gibson, “Distributed Reflection Denial of Service, ” http: //www. grc. com/dos/drdos. htm, Feb 22 2002. Stuart Mc. Clure, Joel Scambray, and George Kurtz, Hacking Exposed, 5/e, Mc. Graw-Hill, 2005. Jelena Mirkovic, Sven Dietrich, David Dittrich, and Peter Reiher, Internet Denial of Service: Attack and Defense Mechanisms, Prentice Hall, 2005. C. Nuttall, “Crime Gangs Extort Money with Hacking Threat, ” The Financial Times, 11 Dec 2003, http: //www. rense. com/general 44/hack. htm Joel Scambray, Mike Shema, Caleb Sima, Hacking Exposed Web Applications, Second Edition, Mc. Graw-Hill, 2006. Ed Skoudis, Counter Hack Reloaded, Prentice Hall, 2006. Scott A Crosby and Dan S Wallach, “Denial of Service via Algorithmic Complexity Attacks, ” USENIX Security 2003, http: //www. cs. rice. edu/~scrosby/hash/, 2003. CSC 382/582: Computer Security 29
 382582
382582 Csc
Csc Memory performance attacks
Memory performance attacks Provate security
Provate security Stage one denial stage two
Stage one denial stage two Deniability
Deniability Vv dina
Vv dina Equation of emotion
Equation of emotion Displacement defense mechanism
Displacement defense mechanism Co227 denial code
Co227 denial code Hermes denial of receipt form download
Hermes denial of receipt form download Indirect denial method example
Indirect denial method example Adaptive denial dbt
Adaptive denial dbt Prayer and self denial 2021
Prayer and self denial 2021 Doubt denial subjunctive
Doubt denial subjunctive Subjunctive with doubt disbelief and denial
Subjunctive with doubt disbelief and denial Operation haven denial
Operation haven denial The osi security architecture
The osi security architecture Security guide to network security fundamentals
Security guide to network security fundamentals Wireless security in cryptography
Wireless security in cryptography Visa international security model
Visa international security model Electronic mail security in network security
Electronic mail security in network security Cnss security model คือ
Cnss security model คือ E commerce security policy
E commerce security policy Building security software
Building security software Security guide to network security fundamentals
Security guide to network security fundamentals Security guide to network security fundamentals
Security guide to network security fundamentals X.800 architecture
X.800 architecture What is the osi security architecture?
What is the osi security architecture? Web service security standards
Web service security standards