CSC 482582 Computer Security Electronic Voting Security CSC

























- Slides: 46

CSC 482/582: Computer Security Electronic Voting Security CSC 482/582: Computer Security

Topics 1. 2. 3. 4. Do we have a right to vote? History of voting Voting fraud techniques Electronic voting CSC 482/582: Computer Security

Voting Rights Do we have a right to vote? CSC 482/582: Computer Security

Voting Rights Non-discrimination is protected � 15 th (race) � 19 th (sex) � 26 th (age) But the SCOTUS majority concluded: "the individual citizen has no federal constitutional right to vote for electors for the President of the United States. " (Bush v. Gore, 531 U. S. 98, 104 (2000)) CSC 482/582: Computer Security

Election Requirements 1. 2. 3. 4. 5. Privacy—voters have the right to keep their ballots secret. Incoercibility—voters cannot prove contents of their ballots. Accuracy—final tally is sum of all ballots. Availability—voters should be able to vote when they reach the polling place. Verifiability—voters can prove to themselves that their ballots were cast as intended and counted and that everyone can prove final tally is accurate.

History of Voting Voice Voting �Observers can record votes. �So can others, leading to bribery and coercion. Ballots �Clay or stone tokens to represent vote. �Black balls used for negative, white for positive. Paper Ballots �Used in Rome as early as 139 BCE. �Originally supplied by voters, later by parties. �Difficult to ensure privacy while avoiding fraud. CSC 482/582: Computer Security

History of Voting Australian Paper Ballot 1858 �Standardized paper ballot distributed at polls. �Marked in secret. �Adopted in US after fraud in 1884. �Problem: how to interpret marks � What type of mark (X, check)? � In-box vs. out of box? � Multiple selections? �Problem: spoiling votes � Counters can spoil votes with stray marks. CSC 482/582: Computer Security

Punched Card Systems 1964 Flaws �Hanging Chads �Dimpled Chads �Chad Jams HAVA 2002 �Reaction to 2000 Florida. �$3. 8 B to replace punch card + lever machines. �Accessibility requirements. �No security requirements.

Types of Electronic Voting Optical scan �Voter marks paper ballots, which are counted based on darkness of mark like scan-tron tests. Direct-recording electronic (DRE) �Records vote count electronically. Networked DRE �Uploads vote count electronically. �Includes Internet voting. e. Slate made by Hart. IC CSC 482/582: Computer Security

Advantages of e-voting �Accessibility �Cheaper election costs due to no paper �Multi-lingual ballots �Speed of tabulation �Remote voting CSC 482/582: Computer Security

Disadvantages of e-voting �Voters could be tracked �Lack of reliability �Lack of verification �Lack of transparency �Undetectable fraud (Rice’s theorem) �Wholesale fraud �More expensive due to voting machines CSC 482/582: Computer Security

Are Voting Machines Reliable? Columbus, OH – An error while a Danaher / Guardian ELECTronic 1242 was plugged into a laptop to download results gave President Bush 3, 893 extra votes. : http: //www. usatoday. com/tech/news/techpolicy/evoting/2004 -11 -06 -ohio-evotetrouble_x. htm Carteret Co. , NC – More early voters voted on Unilect Inc. ’s Patriot voting system than the system could handle resulting in the loss of more than 4, 500 votes. : http: //www. usatoday. com/news/politicselections/vote 2004/2004 -11 -04 -voteslost_x. htm Broward Co. , FL – ES&S software on their machines only reads 32, 000 votes at a precinct then it starts counting backwards (see this update): http: //www. news 4 jax. com/politics/3890292/detail. html Habersham Co. , GA – Reported 243% turnout in one precinct in 2018 election. https: //arstechnica. com/tech-policy/2018/08/georgia-defends-voting-systemdespite-243 -percent-turnout-in-one-precinct/ Mecklenburg Co. , NC – More votes registered than voters: http: //www. charlotte. com/mld/charlotte/news/politics/10094165. htm La. Porte County, IN - A bug in ES&S’ software causes each precinct to be reported as only having (exactly) 300 voters each; all reports add up to 22, 000 voters in a county that has more than 79, 000 registered voters. : http: //www. heraldargus. com/content/story. php? storyid=5304 Utah County, UT - 33, 000 straight-party ballots are not counted due to a programming error in punchcard counting equipment. : http: //deseretnews. com/dn/view/0, 1249, 595105309, 00. html CSC 482/582: Computer Security

Are Voting Machines Secure? “As long as I count the votes, what are you going to do about it? ” -- William Marcy “Boss” Tweed, 1871

Voting Fraud History Altering voter lists �Register false voters. �Remove voters of groups unlikely to support you. Voter coercion and social engineering �Intimidate voters from going to polling place. �Threaten to fire employees. Physical tampering �Ballot stuffing �Destruction of ballot boxes CSC 482/582: Computer Security

Voting Fraud Social Engineering �“Helping” blind or elderly people vote. �Voting in multiple precincts. �Impersonating another voter. �Selling votes. Control the counting of votes �Spoiling votes (making extra marks) �Subverting election officials. �Alter software that tallies votes. CSC 482/582: Computer Security

Election Process Targets 1. 2. 3. 4. 5. 6. Registration Nomination Polling Place Access Voter Manipulation Ballot Manipulation Tabulation CSC 482/582: Computer Security

Threats 1. 2. 3. 4. 5. 6. 7. Individual Voters Outside Attackers Poll Workers Election Officials Equipment Vendors Policy Makers Foreign governments CSC 482/582: Computer Security

Registration Age (lowered to 18, 26 th amendment, 1971) Race (15 th amendment, 1870) Gender (20 th amendment, 1920) Residency DC given presidential vote 23 rd amendment, 1961. Property Ownership Poll taxes prohibited by 24 th amendment, 1964. Criminal Record Most states disallow felons to vote in jail. Many states disallowing voting during parole. Only 2 states (KY, VA) permanently disallow. CSC 482/582: Computer Security

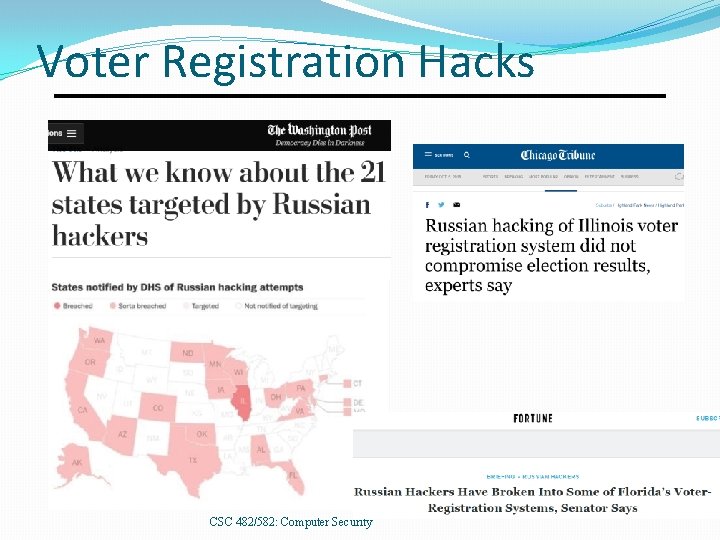
Voter Registration Hacks CSC 482/582: Computer Security

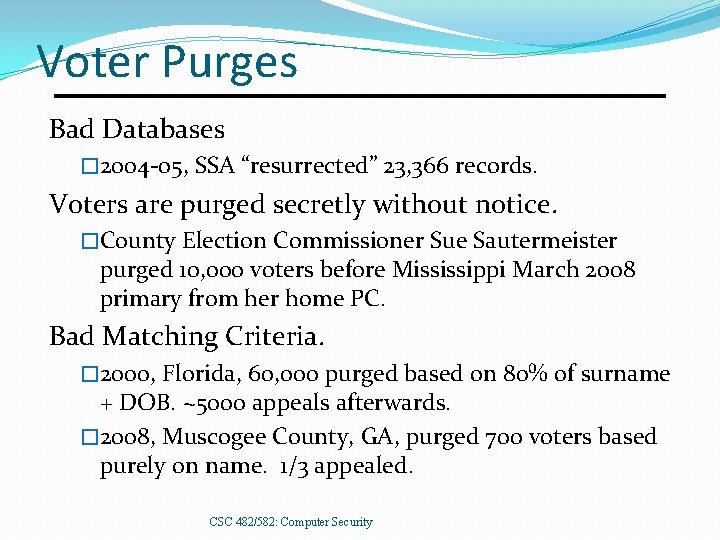
Voter Purges Bad Databases � 2004 -05, SSA “resurrected” 23, 366 records. Voters are purged secretly without notice. �County Election Commissioner Sue Sautermeister purged 10, 000 voters before Mississippi March 2008 primary from her home PC. Bad Matching Criteria. � 2000, Florida, 60, 000 purged based on 80% of surname + DOB. ~5000 appeals afterwards. � 2008, Muscogee County, GA, purged 700 voters based purely on name. 1/3 appealed. CSC 482/582: Computer Security

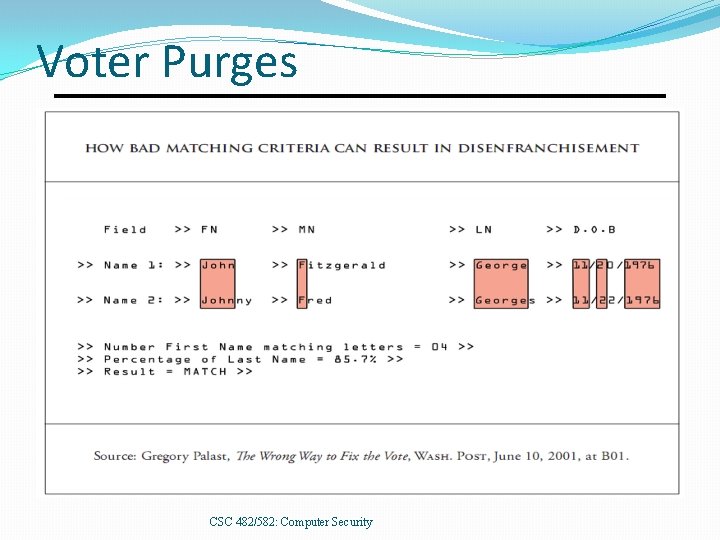
Voter Purges CSC 482/582: Computer Security

Who Will Vote Robo-calls �Claim that voter can vote by phone. �Claim that voter is ineligible to vote. �Incorrect precinct or polling place. �Incorrect date. �Annoying calls appear to be from other party. Mandatory voting �Australia, Brazil, Greece, GA (1777), etc. �Shifts campaign from motivating base to convincing undecideds. CSC 482/582: Computer Security

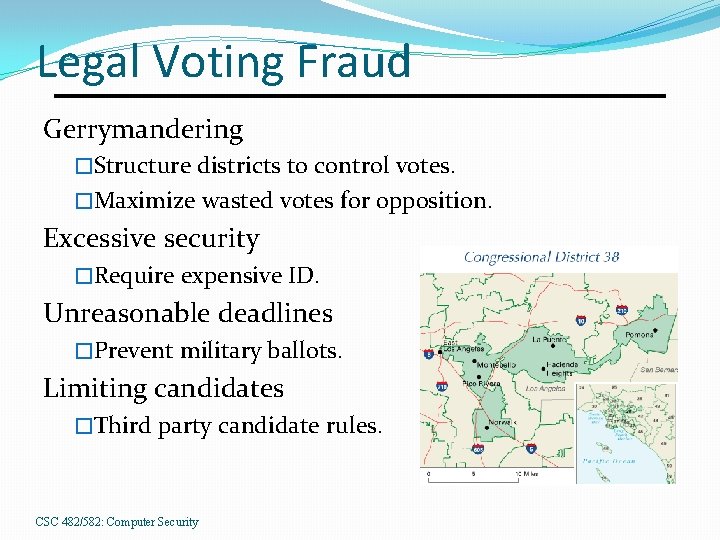
Legal Voting Fraud Gerrymandering �Structure districts to control votes. �Maximize wasted votes for opposition. Excessive security �Require expensive ID. Unreasonable deadlines �Prevent military ballots. Limiting candidates �Third party candidate rules. CSC 482/582: Computer Security

Shortest Splitline Algorithm CSC 482/582: Computer Security

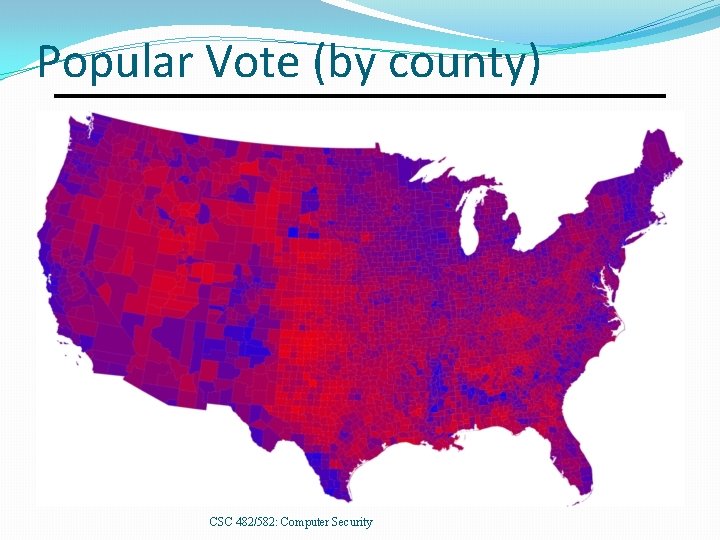
Popular Vote (by county) CSC 482/582: Computer Security

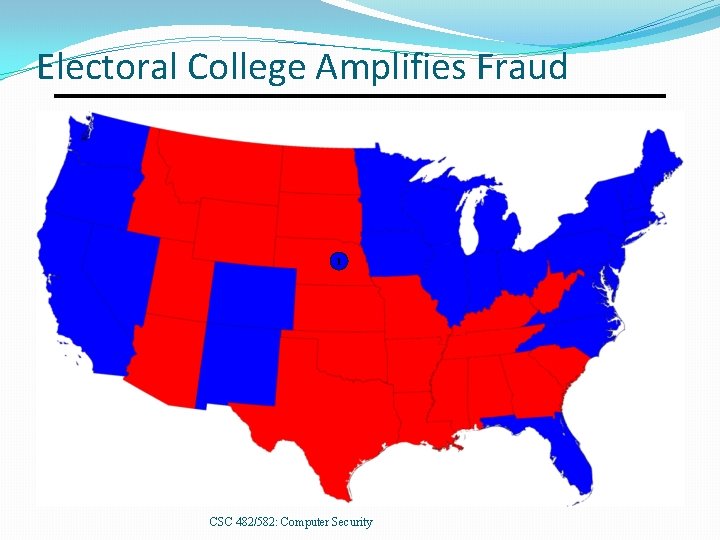
Electoral College Amplifies Fraud 1 CSC 482/582: Computer Security

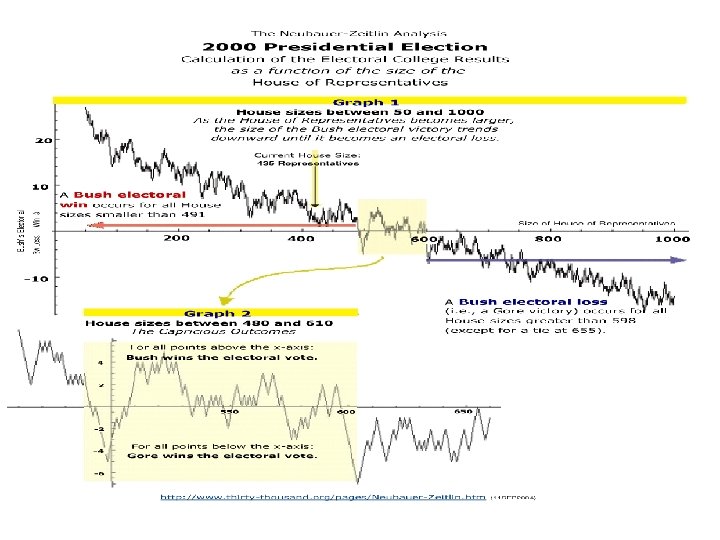
Electoral College Size

Electronic Voting (DRE) Reliability �History of inaccuracy. �Hardware failures (10% fail each election). Security �Designed like a PC. �Most use Windows CE. �Impossible to audit without paper trail. Usability �Support for disabilities, multiple ballots, languages. �Touch screen problems. �Hart double-selection ‘bug’ CSC 482/582: Computer Security e. Slate made by Hart. IC

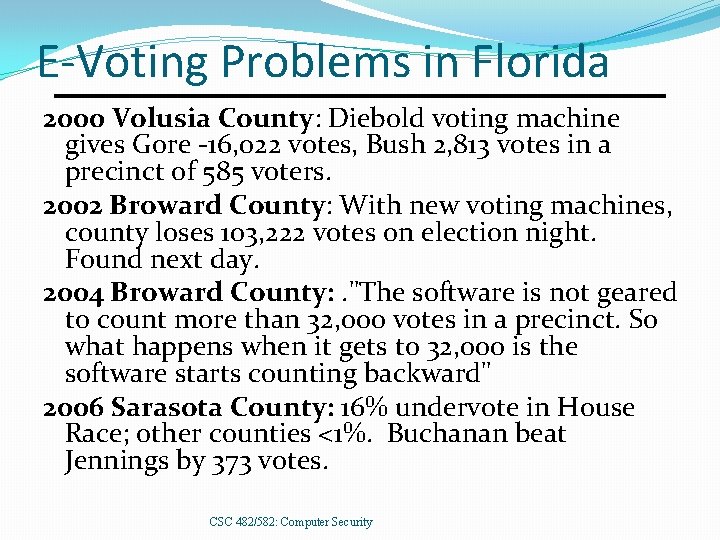
E-Voting Problems in Florida 2000 Volusia County: Diebold voting machine gives Gore -16, 022 votes, Bush 2, 813 votes in a precinct of 585 voters. 2002 Broward County: With new voting machines, county loses 103, 222 votes on election night. Found next day. 2004 Broward County: . "The software is not geared to count more than 32, 000 votes in a precinct. So what happens when it gets to 32, 000 is the software starts counting backward" 2006 Sarasota County: 16% undervote in House Race; other counties <1%. Buchanan beat Jennings by 373 votes. CSC 482/582: Computer Security

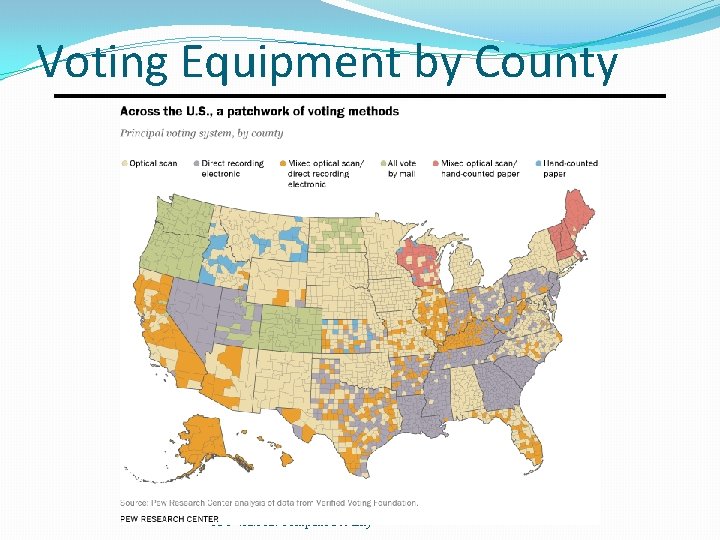
Voting Equipment by County CSC 482/582: Computer Security

Diebold Ballot. Station 1. Setup D/L ballot setup 2. Pre-Election L&A testing 3. Election Voting 4. Post-Election Print result tape Transfer votes CSC 482/582: Computer Security

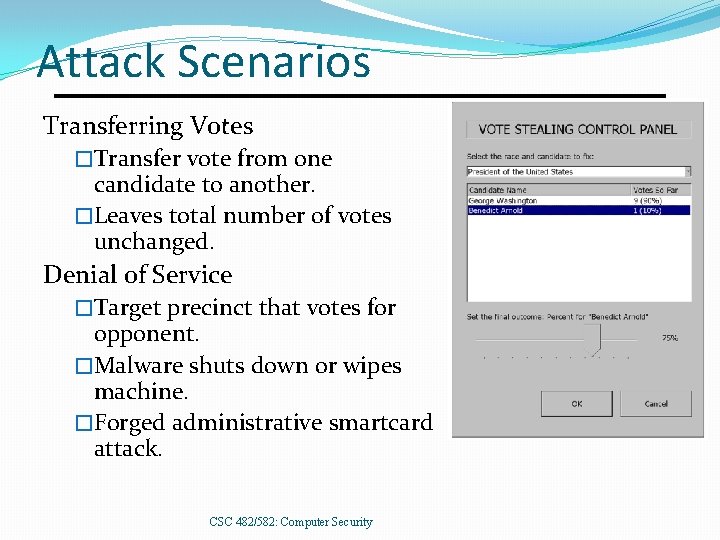
Attack Scenarios Transferring Votes �Transfer vote from one candidate to another. �Leaves total number of votes unchanged. Denial of Service �Target precinct that votes for opponent. �Malware shuts down or wipes machine. �Forged administrative smartcard attack. CSC 482/582: Computer Security

Injecting Attack Code Direct installation �Reboot using smartcard with fboot. nbo. �Reboot using smartcard with explorer. glb. �Replace EPROM. �Voting machines use standard minibar keys. Virus �Infects memory cards. �Memory cards infect machines on boot. �Upgrades delivered via memory cards. CSC 482/582: Computer Security

Concealing Voting Malware Timing �Software only active in Election mode. �Software only active on certain dates / times. Knock �Activates only after secret “knock” given. Hiding processes and files �Rootkit techniques �Virtualization CSC 482/582: Computer Security

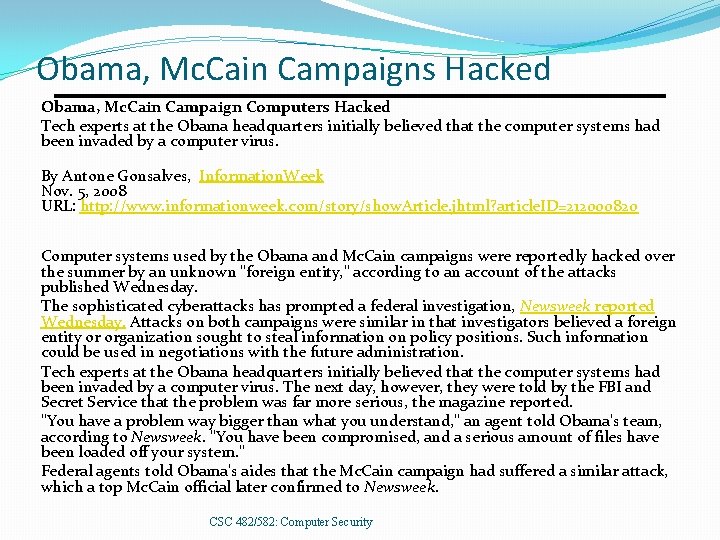
Obama, Mc. Cain Campaigns Hacked Obama, Mc. Cain Campaign Computers Hacked Tech experts at the Obama headquarters initially believed that the computer systems had been invaded by a computer virus. By Antone Gonsalves, Information. Week Nov. 5, 2008 URL: http: //www. informationweek. com/story/show. Article. jhtml? article. ID=212000820 Computer systems used by the Obama and Mc. Cain campaigns were reportedly hacked over the summer by an unknown "foreign entity, " according to an account of the attacks published Wednesday. The sophisticated cyberattacks has prompted a federal investigation, Newsweek reported Wednesday. Attacks on both campaigns were similar in that investigators believed a foreign entity or organization sought to steal information on policy positions. Such information could be used in negotiations with the future administration. Tech experts at the Obama headquarters initially believed that the computer systems had been invaded by a computer virus. The next day, however, they were told by the FBI and Secret Service that the problem was far more serious, the magazine reported. "You have a problem way bigger than what you understand, " an agent told Obama's team, according to Newsweek. "You have been compromised, and a serious amount of files have been loaded off your system. " Federal agents told Obama's aides that the Mc. Cain campaign had suffered a similar attack, which a top Mc. Cain official later confirmed to Newsweek. CSC 482/582: Computer Security

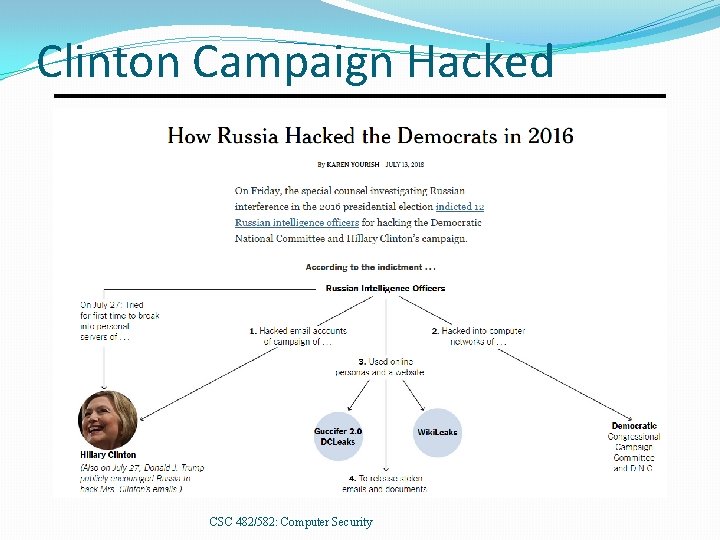
Clinton Campaign Hacked CSC 482/582: Computer Security

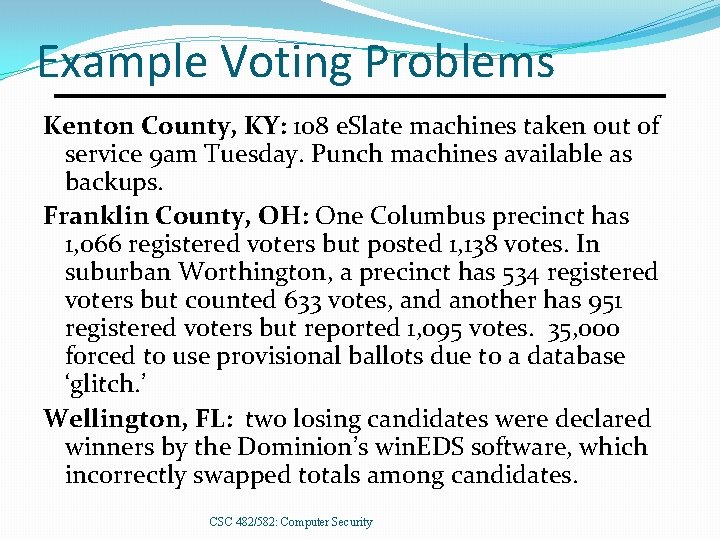
Example Voting Problems Kenton County, KY: 108 e. Slate machines taken out of service 9 am Tuesday. Punch machines available as backups. Franklin County, OH: One Columbus precinct has 1, 066 registered voters but posted 1, 138 votes. In suburban Worthington, a precinct has 534 registered voters but counted 633 votes, and another has 951 registered voters but reported 1, 095 votes. 35, 000 forced to use provisional ballots due to a database ‘glitch. ’ Wellington, FL: two losing candidates were declared winners by the Dominion’s win. EDS software, which incorrectly swapped totals among candidates. CSC 482/582: Computer Security

Alternatives 1. 2. 3. Don’t use electronic voting machines. Use voting machines to print ballots only; don’t use direct electronic counting. Produce a secure electronic voting machine. CSC 482/582: Computer Security

Transparency of Process �Security requirements. �Reference implementations. �Public demonstrations. �Testing guidelines. Transparency of Elections �Transparent registration process. �Publicly viewable logs. CSC 482/582: Computer Security

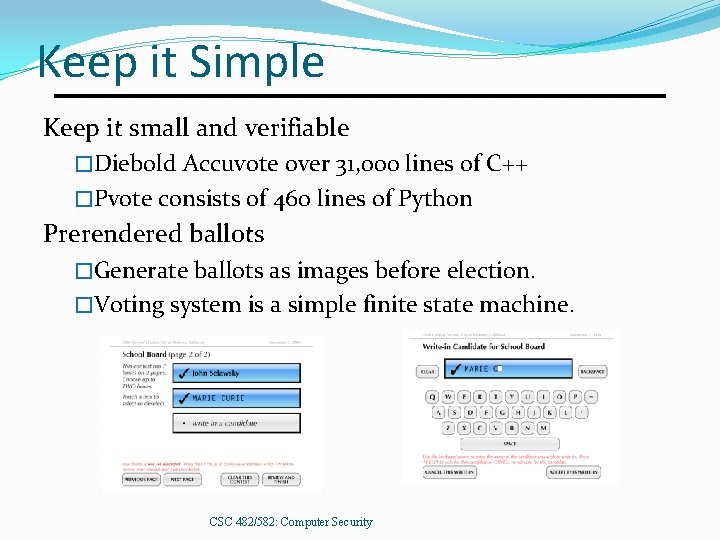
Keep it Simple Keep it small and verifiable �Diebold Accuvote over 31, 000 lines of C++ �Pvote consists of 460 lines of Python Prerendered ballots �Generate ballots as images before election. �Voting system is a simple finite state machine. CSC 482/582: Computer Security

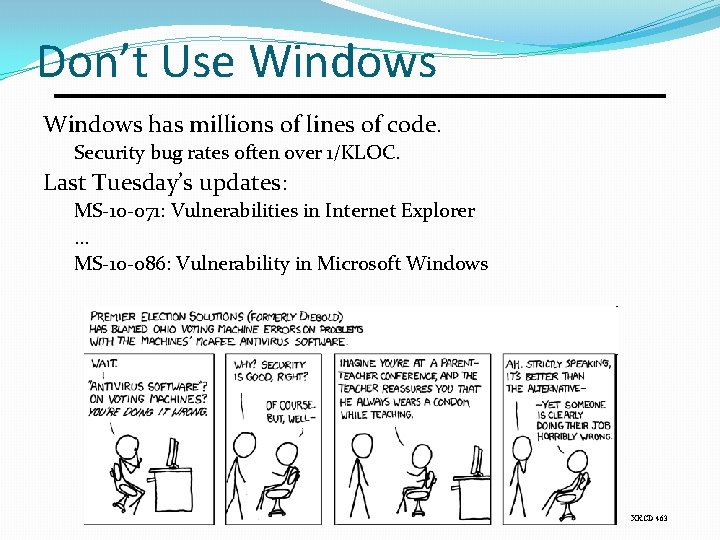
Don’t Use Windows has millions of lines of code. Security bug rates often over 1/KLOC. Last Tuesday’s updates: MS-10 -071: Vulnerabilities in Internet Explorer … MS-10 -086: Vulnerability in Microsoft Windows XKCD 463

VVPAT �Humans can’t read digital storage, so �Visually verified paper. PROBLEMS �Voters don’t verify. �Cuyahoga 2006: 9. 6% of VVPAT destroyed, blank, or compromised. �Could print extra records if unattended. CSC 482/582: Computer Security

Risk Limiting Audits https: //www. stat. berkeley. edu/~stark/Vote/audit. Tools. htm CSC 482/582: Computer Security

Physical Security Memory cards are easily stolen, modified. Tamper-evident Tape �Record serial numbers. �Check for tampering. Chain of custody �Serial numbers for each memory card. �Track chain of custody like evidence. CSC 482/582: Computer Security

Key Points Election Requirements 1. 1. 2. 3. 4. 5. Privacy Incoercibility Accuracy Availability Verifiability Direct Electronic Voting (DRE) 2. 1. 2. Lack of reliability, verifiability, and security. Possibility of undetectable wholesale fraud. Alternatives 3. 1. 2. Use e-voting to mark ballots only. Use simple pre-rendered systems with appropriate software and physical security. CSC 482/582: Computer Security

References 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. Matt Blaze et. Al. DEFCON-25 Voting Machine Hacking Village Report. http: //cs. brown. edu/people/jsavage/Voting. Project/2017_09_DEF_CON_25_Voting_Vil lage_Report. pdf. 2017. Caltech/MIT Voting Project, “Residual Votes Attributable to Technology, ” http: //www. hss. caltech. edu/~voting/Cal. Tech_MIT_Report_Version 2. pdf#search=%22 mit%20 caltech%20 uncounted%20 ballots%22, 2001. “More e-voting problems, ” http: //www. evoting-experts. com/, December 12, 2004. Ariel J. Feldman, J. Alex Halderman, Edward W. Felten, “Security Analysis of the Diebold Accu. Vote-TS Voting Machine, ” http: //itpolicy. princeton. edu/voting, Sep 13, 2006. Susan Hennessey. Cybersecurity of Voting Machines [Congressional Testimony]. https: //www. brookings. edu/testimonies/cybersecurity-of-voting-machines/. 2017. Douglas Jones, “Illustrated Voting Machine History, ” http: //www. cs. uiowa. edu/~jones/voting/pictures/, 2003. Douglas Jones, “Four ways to defend democracy and protect every voter's ballot”, https: //phys. org/news/2018 -09 -ways-defend-democracy-voter-ballot. html, 2018. Tadayoshi Kohno, Adam Stubblefield, Aviel D. Rubin, Dan S. Wallach, “Analysis of an Electronic Voting System, ” IEEE Symposium on Security and Privacy, Oakland, CA, May, 2004 National Academies of Science, Engineering, and Medicine. Securing the Vote. https: //www. nap. edu/catalog/25120/securing-the-vote-protecting-americandemocracy. 2018. Mark Newman, “Election Result Maps, ” http: //wwwpersonal. umich. edu/~mejn/election/, 2004. Avi Rubin, Brave New Ballot, Morgan Road Books, 2006. Verfied Voting, Key Facts 2012, https: //www. verifiedvoting. org/key-facts-2012/. Kim Zetter, “House Dems seek Election Inquiry, ” http: //www. wired. com/news/evote/0, 2645, 65623, 00. html, Nov 5, 2004. CSC 482/582: Computer Security