CSC 482582 Computer Security Transport Layer Security CSC


















- Slides: 36

CSC 482/582: Computer Security Transport Layer Security CSC 482/582: Computer Security Slide #1

Topics 1. 2. 3. 4. 5. HTTPS The TLS Protocol Public Key Infrastructure (PKI) Attacks on TLS Defenses (Pinning, HSTS) CSC 482/582: Computer Security Slide #2

HTTPS (HTTP over SSL) HTTPS differences �Default port is 443. �Connection: close HTTP header ends session. �RFC 2818: HTTP over TLS Encrypts �URL of requested document �HTTP headers �HTTP bodies, including response documents �All form parameters, as they are either in the URL or the HTTP body. CSC 482/582: Computer Security Slide #3

Transport Layer Security (TLS) TLS protocol provides security features for other protocols, such as HTTP, IMAP, etc. 1. 2. 3. 4. Authentication of server to client. Optional authentication of client to server. Confidentiality of communication. Integrity of communication. TLS 1. 0 was published in 1999. �SSL 2. 0 was first released in 1995 (insecure) �TLS 1. 2 is most recent, defined in 2008. �TLS 1. 3 draft being developed. CSC 482/582: Computer Security Slide #4

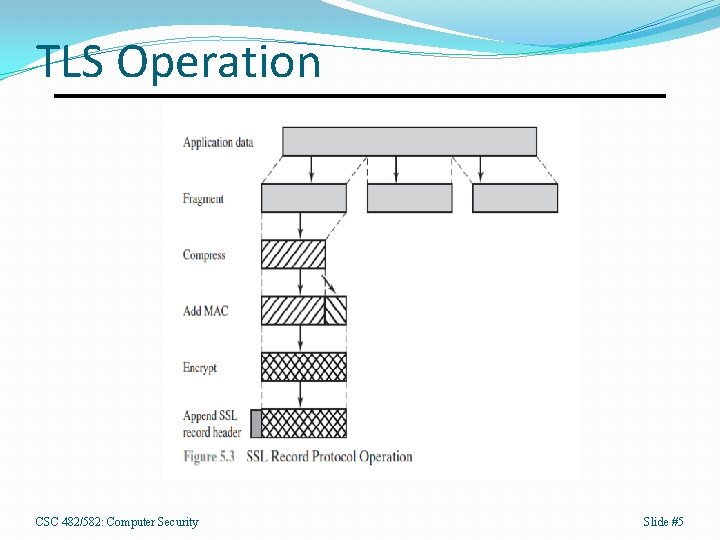
TLS Operation CSC 482/582: Computer Security Slide #5

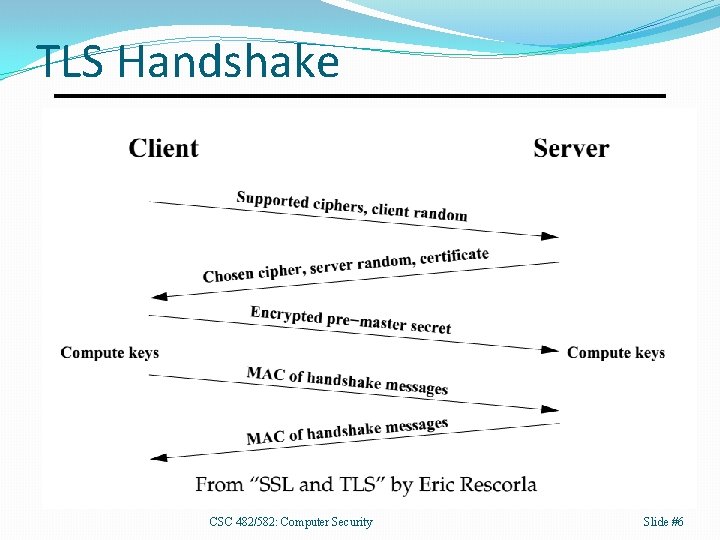
TLS Handshake CSC 482/582: Computer Security Slide #6

Cipher Suites 1. Key Exchange Algorithm � Used to exchange session keys for bulk encryption algorithm. � Examples: RSA, Diffie-Hellmann, Elliptic Curve Diffie-Hellman 2. Bulk Encryption Algorithm � Used to encrypt message stream. � Examples: RC 4 -128, Triple-DES, AES-128, AES-256 3. Message Authentication Code � MAC is keyed hash function to ensure integrity. � Based on MD 5, SHA-1, or SHA-2, key based on master secret. 4. Pseudorandom Function � Used to create master secret, a 48 -byte secret shared with both parties. Used to create session keys. Slide #7

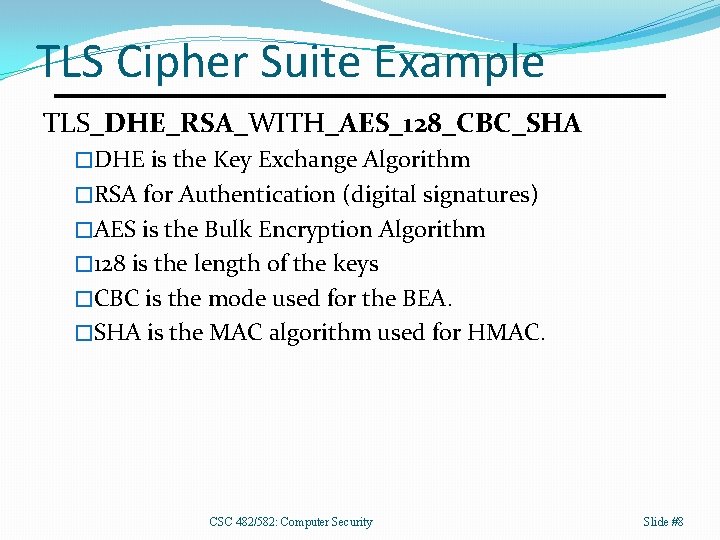
TLS Cipher Suite Example TLS_DHE_RSA_WITH_AES_128_CBC_SHA �DHE is the Key Exchange Algorithm �RSA for Authentication (digital signatures) �AES is the Bulk Encryption Algorithm � 128 is the length of the keys �CBC is the mode used for the BEA. �SHA is the MAC algorithm used for HMAC. CSC 482/582: Computer Security Slide #8

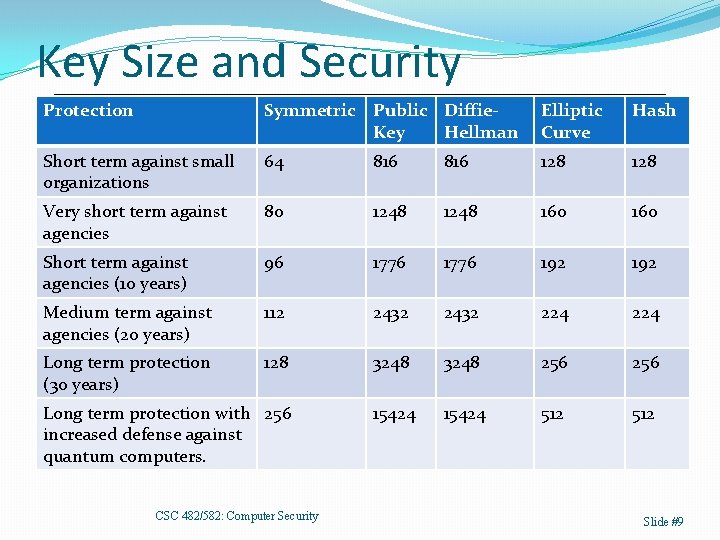
Key Size and Security Protection Symmetric Public Diffie. Key Hellman Elliptic Curve Hash Short term against small organizations 64 816 128 Very short term against agencies 80 1248 160 Short term against agencies (10 years) 96 1776 192 Medium term against agencies (20 years) 112 2432 224 Long term protection (30 years) 128 3248 256 15424 512 Long term protection with 256 increased defense against quantum computers. CSC 482/582: Computer Security Slide #9

TLS Client Test browser TLS by going to �https: //www. ssllabs. com/ssltest/view. My. Client. html �Does your browser support latest TLS version? �Does your browser support weak cipher suites? Check other clients by going to �https: //www. ssllabs. com/ssltest/clients. html �Are you or your customers using any of the clients that are missing secure TLS versions and features? CSC 482/582: Computer Security Slide #10

TLS Server Test �Go to https: //www. ssllabs. com/ssltest/ �Test the following servers �www. nku. edu �www. google. com �A server of your own choice. �Compare configurations with top servers at https: //www. trustworthyinternet. org/ssl-pulse/ �Discuss server configurations. CSC 482/582: Computer Security Slide #11

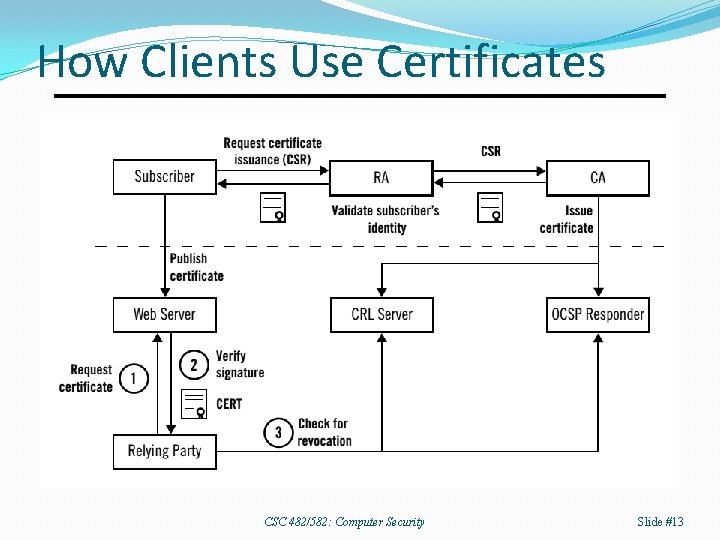
X. 509 Digital Certificates Certificate contains � Serial number � Identity of issuer, who produced certificate. � Identity of subject. � Public key of subject. � Range of dates for which certificate is valid. � Digital signature from issuer. Signature means that issuer vouches that � Public key belongs to subject, e. g. � You really are connected to example. com. Client has list of trusted certificate authorities (CAs) � Client will trust certificate if it is signed by one of those CAs or if issuer has a certificate that was signed by CA. CSC 482/582: Computer Security Slide #12

How Clients Use Certificates CSC 482/582: Computer Security Slide #13

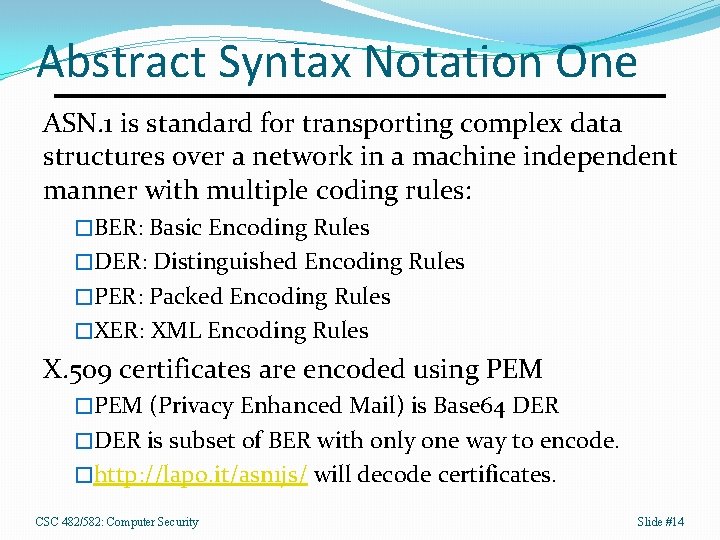
Abstract Syntax Notation One ASN. 1 is standard for transporting complex data structures over a network in a machine independent manner with multiple coding rules: �BER: Basic Encoding Rules �DER: Distinguished Encoding Rules �PER: Packed Encoding Rules �XER: XML Encoding Rules X. 509 certificates are encoded using PEM �PEM (Privacy Enhanced Mail) is Base 64 DER �DER is subset of BER with only one way to encode. �http: //lapo. it/asn 1 js/ will decode certificates. CSC 482/582: Computer Security Slide #14

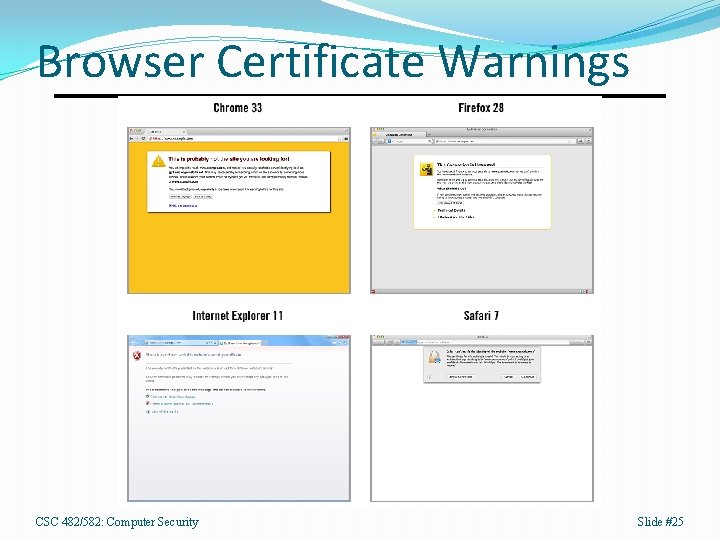
View Certificate Exercise Steps to View 1. 2. 3. Pick a HTTPS URL. Click on padlock icon. Select View Certificate or Certificate Info. Questions 1. 2. 3. Who is the owner of the certificate? Who signed the certificate? When does the certificate expire? CSC 482/582: Computer Security Slide #15

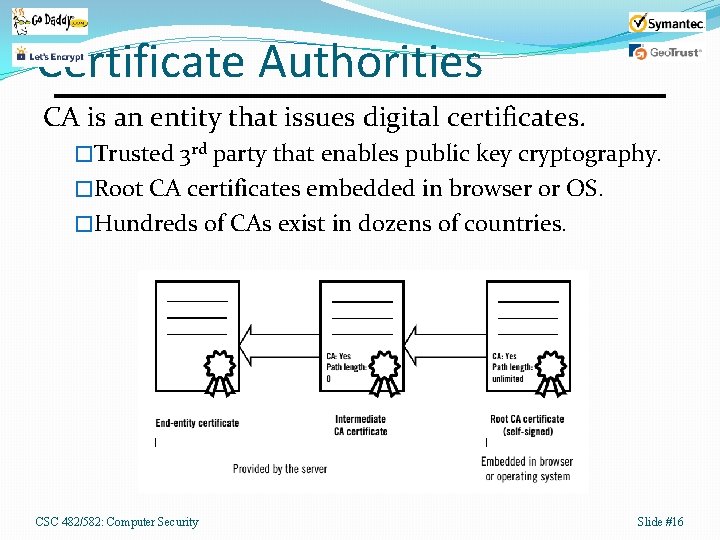
Certificate Authorities CA is an entity that issues digital certificates. �Trusted 3 rd party that enables public key cryptography. �Root CA certificates embedded in browser or OS. �Hundreds of CAs exist in dozens of countries. CSC 482/582: Computer Security Slide #16

Obtaining a Certificate 1. Create a public/private key pair. � Choose appropriate algorithm and key size. 2. Create Certificate Signing Request (CSR) � Contains public key and identity information. � Sign CSR with applicant’s private key. 3. Send CSR to CA. 4. CA validates CSR. � Checks that applicant matches identity. 5. CA sends certificate to applicant. CSC 482/582: Computer Security Slide #17

Certificate Validation �Domain Validation (DV) certificates are issued based on proof of control over a domain name. �Send confirmation e-mail to one of the standard approved e-mail addresses. �If applicant follows link in e-mail, cert is validated. �Organization Validation (OV) certificates require identity and authenticity validation but validation requirements are not consistent. �Extended Validation (EV) certificates are issued with standard identity and authenticity validation procedures documented by the CA/Browser Forum (https: //cabforum. org/) CSC 482/582: Computer Security Slide #18

Certificate Revocation Certificates are revoked when �Private key is compromised or no longer in use. �Certificate was issued to wrong entity (faulty validation). Certificate Revocation List (CRL) �List of serial numbers of revoked certificates that have not yet expired. �Can be large, so lookup can be slow. Online Certificate Status Protocol (OCSP) �Check revocation status of a single certificate. �CA specifies their OCSP servers in issued certificates. CSC 482/582: Computer Security Slide #19

Revocation Problems Revocation is slow �Revocation status data is valid for 10 days. Revocation is a blacklist technology �CRLs were designed as a blacklist. �OCSP was implemented as a blacklist, using CRL data and interpreting no response as not revoked. Libraries and command line tools don’t check �Default configuration is not to check for revocation. OCSP leaks information about browsing habits �Monitor small # of OCSP servers vs entire Internet. �OCSP stapling fixes by allowing servers to do OCSP. CSC 482/582: Computer Security Slide #20

PKI Incidents § § § 2001: Veri. Sign tricked into issuing two code-signing certificates to someone claiming to represent Microsoft. Certificates not trusted by Windows, but GUI asks user to accept certificate from Microsoft. 2008: Security researcher Mike Zusman obtained certificate for login. live. com by using a personal live. com e-mail address, sslcertificates@live. com. 2008: Cert. Star (a Comodo branch) is found to issue certificates without any domain name validation. Tester got mozilla. org cert. 2011: Comodo resellers issue certificates for login. yahoo. com, mail. google. com, login. skype. com, etc. 2011: Dutch CA Digi. Notar totally compromised; hundreds of certificates issue, including *. *. com and *. *. org. Could not revoke because did not know which certificates issued. Company’s root certificates were revoked and Digit. Notar declared bankruptcy. CSC 482/582: Computer Security Slide #21

PKI Weaknesses Domain owner permission not required �Any CA can issue a certificate for any domain. �Do CAs issue certificates for surveillance? Weak domain validation �DV relies on domain ownership information from insecure WHOIS protocol. �Relatively easy to hijack e-mail accounts. Some CAs have become too big to fail �Only small CAs have been removed from root stores. Revocation is slow and unreliable �Revocation status data is valid for 10 days. �Browsers interpret no OCSP response as no revocation. CSC 482/582: Computer Security Slide #22

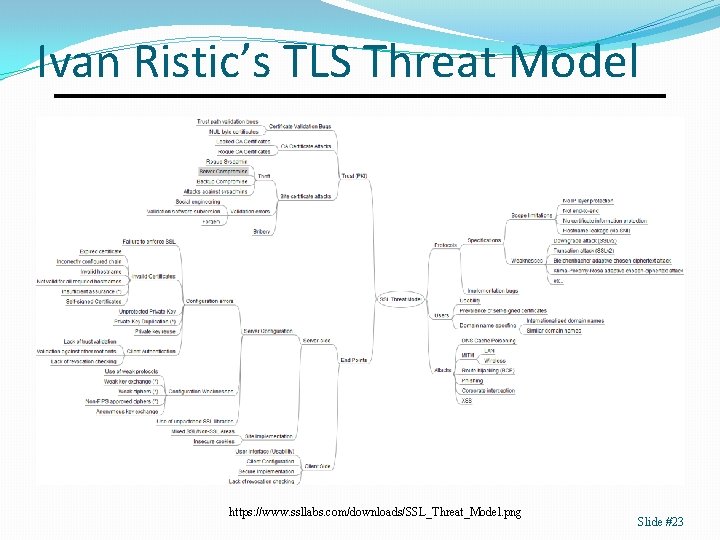
Ivan Ristic’s TLS Threat Model https: //www. ssllabs. com/downloads/SSL_Threat_Model. png Slide #23

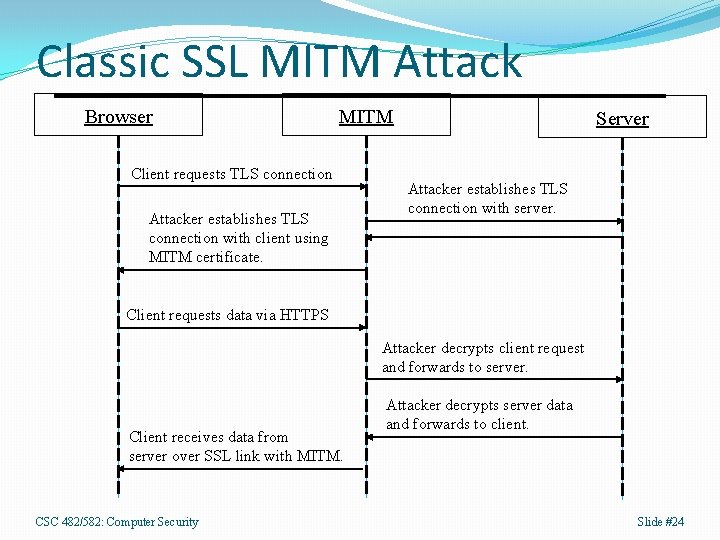
Classic SSL MITM Attack Browser MITM Client requests TLS connection Attacker establishes TLS connection with client using MITM certificate. Server Attacker establishes TLS connection with server. Client requests data via HTTPS Attacker decrypts client request and forwards to server. Client receives data from server over SSL link with MITM. CSC 482/582: Computer Security Attacker decrypts server data and forwards to client. Slide #24

Browser Certificate Warnings CSC 482/582: Computer Security Slide #25

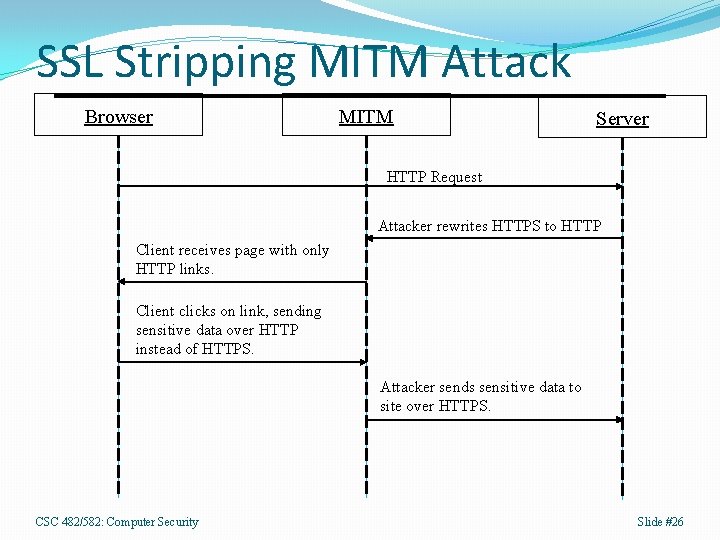
SSL Stripping MITM Attack Browser MITM Server HTTP Request Attacker rewrites HTTPS to HTTP Client receives page with only HTTP links. Client clicks on link, sending sensitive data over HTTP instead of HTTPS. Attacker sends sensitive data to site over HTTPS. CSC 482/582: Computer Security Slide #26

FREAK Attack �Factoring RSA Export Keys (FREAK) �Export restrictions relaxed in 2000, but �Export-grade cryptography still supported. �Export cipher suite names begin with EXP-. �FREAK MITM Attack Process �Client requests standard RSA cipher suite. �MITM modifies message to request export RSA. �Server responds with 512 -bit RSA key. �Vulnerable browsers accept weak key. �Attacker factors RSA modulus to recover decryption key in seconds. CSC 482/582: Computer Security Slide #27

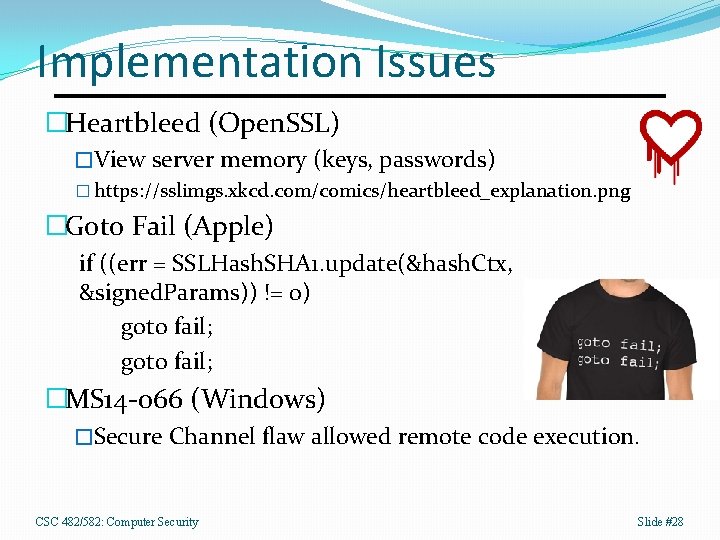
Implementation Issues �Heartbleed (Open. SSL) �View server memory (keys, passwords) � https: //sslimgs. xkcd. com/comics/heartbleed_explanation. png �Goto Fail (Apple) if ((err = SSLHash. SHA 1. update(&hash. Ctx, &signed. Params)) != 0) goto fail; �MS 14 -066 (Windows) �Secure Channel flaw allowed remote code execution. CSC 482/582: Computer Security Slide #28

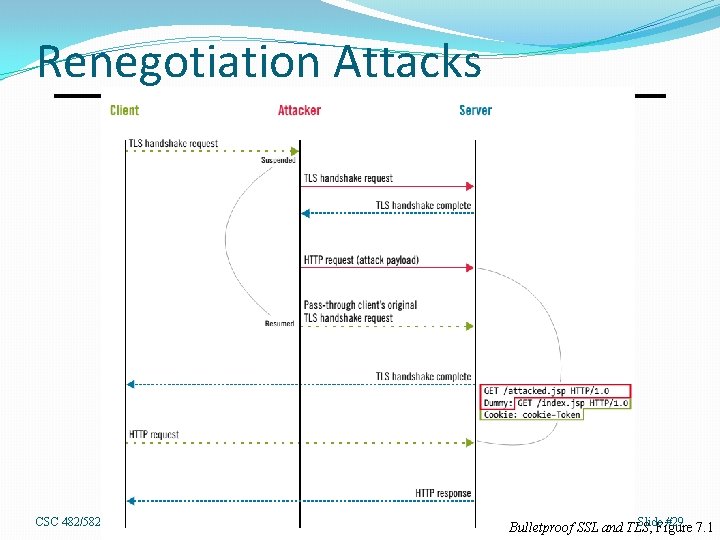
Renegotiation Attacks CSC 482/582: Computer Security Slide #29 7. 1 Bulletproof SSL and TLS, Figure

Side Channel Attacks Compression Side Channel Attacks �CRIME, TIME, BREACH attacks. �Insert Java. Script malware into browser. �Manipulate data to change compression result, then observe diffs in compressed encrypted output. �Allows recovery of cookies, CSRF tokens. Lucky 13 Padding Oracle Attack �Exploits lack of integrity protection for padding. �Insert Java. Script malware into browser. �Guess bytes, modify padding to include. � 8192 HTTP requests to get 1 byte of plaintext. CSC 482/582: Computer Security Slide #30

Certificate Pinning �Clients pin certificates (or public keys) by � Storing certificates for certain hosts, and � When connecting to those hosts, validating the certificate sent by the server by comparing it with the stored certificate instead of by following the digital signature chain via PKI. �Preloaded pins � Client developer stores pinned certificate with client software. � Valid until certificate expires. � Must update app or browser when certificate is replaced. �Uses of Certificate Pinning � Browsers preload certificates of their creators and certain widely used web sites. � Mobile apps preload certificates of the sites that they are associated with. CSC 482/582: Computer Security Slide #31

Dynamic Certificate Pinning �Dynamic pinning � Web sites set pins using the HPKP header on a client’s first connection with site. � Valid until max-age header option expires. � Secure if first connection with site or first connection with site after max-age expires not attacked. �HTTP Public Key Pinning (HPKP) header � Public-Key-Pins: pin-sha 256="base 64=="; max-age=expire. Time [; include. Subdomains][; report-uri="report. URI"] � Header can include multiple public keys using multiple pin-sha 256 header options. � If report-uri field specified, clients should send message to specified URI if pinned certificate does not match certificate received from server. CSC 482/582: Computer Security Slide #32

HSTS �HTTP Strict Transport Security (HSTS) �Sets policy to only use HTTPS with site. �All certificate errors are fatal for that site. �Protects against MITM attacks including SSLstrip. �Established via HTTP header on 1 st connection �Strict-Transport-Security: max-age=N; options �max-age is number of seconds policy lasts �include. Sub. Domains enforces policy on subdomains �STS Preloaded List in Browsers �Well known HSTS sites list stored in browser, so even 1 st connection is protected by HSTS for those sites. CSC 482/582: Computer Security Slide #33

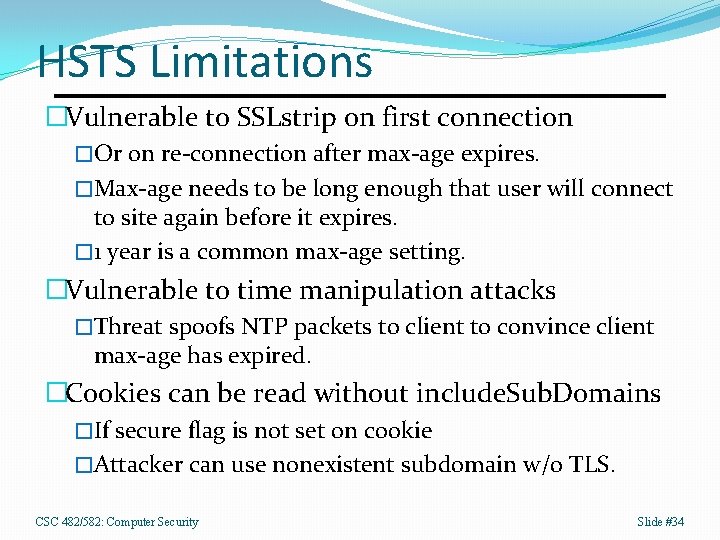
HSTS Limitations �Vulnerable to SSLstrip on first connection �Or on re-connection after max-age expires. �Max-age needs to be long enough that user will connect to site again before it expires. � 1 year is a common max-age setting. �Vulnerable to time manipulation attacks �Threat spoofs NTP packets to client to convince client max-age has expired. �Cookies can be read without include. Sub. Domains �If secure flag is not set on cookie �Attacker can use nonexistent subdomain w/o TLS. CSC 482/582: Computer Security Slide #34

Key Points 1. 2. 3. 4. 5. Security features (C, I, and authentication) Certificates (purpose, validation, revocation) PKI (how it works, weaknesses) Attacks (MITM, implementation, protocol) Defenses (HSTS, certificate pinning) CSC 482/582: Computer Security Slide #35

References 1. 2. 3. 4. 5. 6. Matthew Green, Attack of the week: FREAK, http: //blog. cryptographyengineering. com/2015/03/attac k-of-week-freak-or-factoring-nsa. html, 2015. Dafydd Stuttart and Marcus Pinto, The Web Application Hacker’s Handbook, 2 nd Edition, Wiley, 2011. HTTP/2 Home Page, https: //http 2. github. io/. Ivan Ristic, Bulletproof SSL and TLS, Feisty Duck, 2014. Daniel Stenberg, TLS in HTTP/2, http: //daniel. haxx. se/blog/2015/03/06/tls-in-http 2/, 2015. Michael Zalewski, The Tangled Web: A Guide to Securing Modern Web Applications, No Starch Press, 2011. CSC 482/582: Computer Security Slide #36