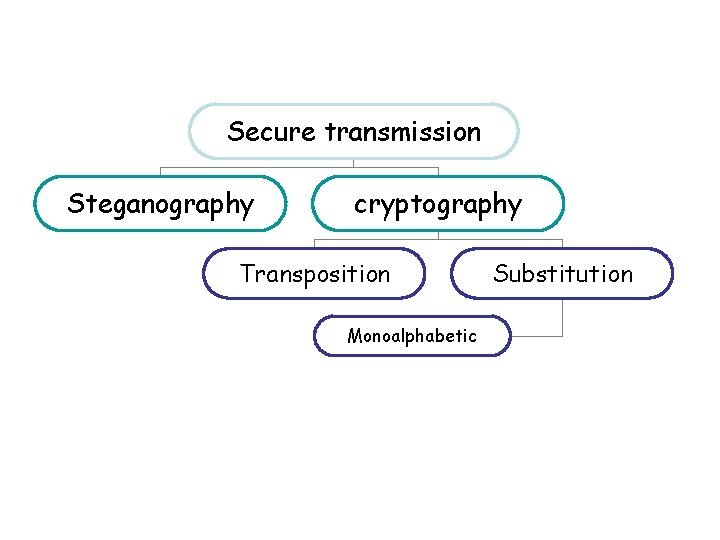
CRYPTOGRAPHY lecture 3 Wednesday Secure transmission Steganography cryptography


















- Slides: 24

CRYPTOGRAPHY lecture 3 Wednesday

Secure transmission Steganography cryptography Transposition Monoalphabetic Substitution

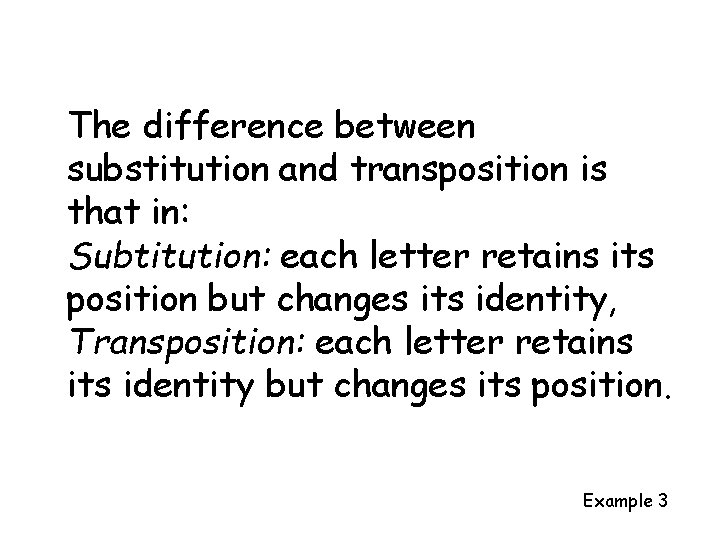
The difference between substitution and transposition is that in: Subtitution: each letter retains its position but changes its identity, Transposition: each letter retains its identity but changes its position. Example 3

HW #2: Caesar shift problems 2. KENKMOC PYBDEXK TEFKD 3. MHILYLZAZBHLXBPZXBLMVYABUHLHW WPBZJSHBKPBZJHLJBZKPJABTHYJHUB TLZAULBAYVU

• QK MEJXNEJJ ZMEVTJ Q YVNGEZ VNHKE KVMMHY JXMEEXJ HB FHWWNEJXHKE WEKEVXP XPE PVNH HB V JXMEEX NVTI Q XRMK TA FHNNVM XH XPE FHNZ VKZ ZVTI YPEK TA EAEJ YEME JXVWWEZ WA XPE BNVJP HB V KEHK NQDPX XPVX JINQX XPE KQDPX VKZ XHRFPEZ XPE JHRKZ HB JQNEKFE

new ciphers 1. MPV DIZ DFF EPUQH D WZIM QUSZ NPY EZSUBJZIUQH GZTTDHZT UT UC KVQ 2. HGJUBQPU V HY H CVP AHT BA DHQG ZVYBT V KB GVZJRT JB BJURW YQZVE JBB CQJ ZVTER VJ VZ YBZJGS EGHZZVEHG VJ KBRZ TBJ VTZDVWR HTS EVDURWR

new ciphers 1. HGJUBQPU V HY H CVP AHT BA DHQG ZVYBT V KB GVZJRT JB BJURW YQZVE JBB CQJ ZVTER VJ VZ YBZJGS EGHZZVEHG VJ KBRZ TBJ VTZDVWR HTS EVDURWR

Mono-alphabetic Substitution Cipher • Allow any permutation of the alphabet • Each letter is replaced by a different letter or symbol • Key = permutation (still need to decide on a key and exchange this information in a secure way). • 26! Possibilities – What does this mean?

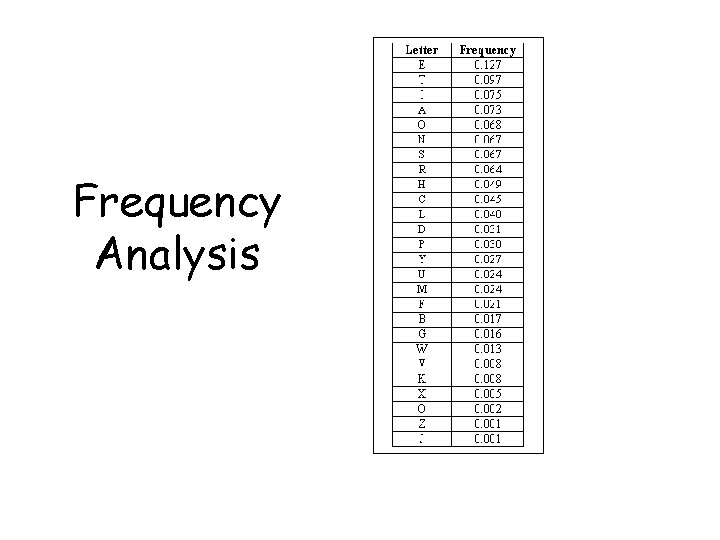
Frequency Analysis

HW # 3: Reading §Review: The Code Book chapter 1 & read chapter 2 p. 45 -51 §Find websites on substitution ciphers and frequency analysis §Begin research for a 5 -7 page essay on “Why are substitution and transposition ciphers obsolete, and when did they become so. ” Due on Monday in class.

(in class): Substitution cipher SK BKGKC FBTKCHZWBT W ZXUBA HM SKOO, WBT EWQK UZ MFC MSB, WH SXKB SK XWGK TUHJMGKCKT UZ DMC MFCHKOGKH

(in class): Substitution cipher CGXTOUNZL NQ UDOU HDNTD BCJONLQ HDCL ZLC DOQ WZBMZUUCL CACBEUDNLM DC KCOBLCG NL QTDZZK.

HW # 3: Substitution cipher UWZEZ VTPUW ZBEIK WVRWT UPUZT UWPUV YZFZE PAIQB SISVT RBFZE TZJPR UNIKW PUUWZ GAVFZ ETZVT YBEPA SKWIV UVTWZ EZVUK VNNVA TUPAU NISVT PCCZP EPASQ ZEZCN PRZSQ ITBOZ UWVAX ZFZAO BEZQV HPEEZ PASVA ZJCNV RPQNZ UWZEZ VTPAB UWZEU WZBEI KWVRW TUPUZ TUWPU UWVTW PTPNE ZPSIW PCCZA ZS

HW # 3: Substitution cipher VBIPA IJPIE IGDLA IRVAM IFJDT MADPM FIJKD IDGAP BDQLN MDMBI PMBIE IJJWF MAEWL BWPDM MBIIW DVBAE NIPMA ADPJD NIELW JIGWF DQFJI YTDFD HWPNJ BIFWP FMBMB BMBIL MLIMB TRWPO FIMBI WMADP DTBQR PIGID VBAEB NMDWJ IJIGW WVJDT IRWNI APNFI EWQJI WPIUI GLIMD BWUIE JQRIW FWMIW PWMQF EIPMF SQAFI JVBAE PMJAM NAJJD DPPIE RDPKM PNISQ IWPND IJGIE JMBWM BARGI HIEDR LUIMB MINMB BIGDV WLJMW TPWMQ MMDMB MBIYJ LMBIR

HW # 3: Substitution cipher NBSQF VLMVE LSNRH QSRMN SHZMC HLDMR LFMCQ RHDLF HLHSR FQSRM GVZQS VKLUV LQSGV HSGVQ VPVVO HVMHV XGVQR VXVRU MCVCG KKNVS SGRHX ZMCRG GZSGN LSGVQ VMVUV HNVZM HTFRC HGGRH VCEQL VZQSE GLFTG GZMTV ZUVGR BGVZQ TRUVM QDZHZ CGRNR VHGVK AVXZF NNBHR LQZHE SRMNV HLFTG H SZMCR RGLKC AZQTZ MLMVN LUVHN HVRMN TGSNB QLNNV GRHGF SLFQA GZUVG GRHCV RMAVS BGVZQ VRSAR GVZQS LMGRN QSCRC KRHHN RHABI ZQZMC SVQCQ SRMGR SELQL CVHGR DZHDL GRHGF HNZQS BSQFV FHSVW NRMVG RUVMG NGRHS MXVRS HGVZQ FMCVC QSCRC ALSGV KLUVG XGZMT VXZMM RHGVZ GLFTG DZHGR SGRHD DRSGG KRTGS JFZKG ZSGNB

HW # 3: Substitution cipher 826821526251162515231172625148114 14826232621111161411615142623722526 14826168262326172213262514826232621111 1122161423125221214222161827182625 8262326116252026232671782152625148114 14826232621111161411615142623722526 252610711112512011

Websites which help http: //www. geocities. com/cryptogramcorner/ http: //cs. colgate. edu/faculty/nevison/Core 139 Web/tools/substitution. html

What can we do to improve the substitution cipher? In 1460 Battista Alberti wrote an essay on what he believed to be a new form of cipher: use two or more cipher alphabets alternately to encrypt a message. ABCDEFGHIJKLMNOPQRSTUVWXYZABCDEF RSTUVWXYZABCDEFGHIJKLMNOPQ plain text cipher 1 cipher 2 Let’s encrypt the statement IT IS WAY TOO EARLY IN THE DAY TO BE DOING THIS OK OJ CRE KUF KRXCE ZT KNV JRE KU SK UUZTX ZYOJ 12 34 567 890 12345 67 890 123 45 67 89012 3456

What can we do to improve the substitution cipher? Alberti was followed by Johannes Trithemius (born 1462) and Giovanni Porta (born 1535) who developed his ideas. Finally, Vigenere put all these ideas together. Let’s take a whole table of Caesar shift alphabets. The first row will have a Caesar shift of 1, the second of 2, etc. Each letter in the plaintext message can be enciphered by a different row.

Vigenere cipher: Start with a table of Caesar shift alphabets. A B C D E F G H I J K L M N O P Q R S T U V W X Y Z A B C E F G H I J K L M N O P Q R S T U V W X Y Z A B C D E F G I J K L M N O P Q R S T U V W X Y Z A B C D E F G H I J K M N O P Q R S T U V W X Y Z A B C D E F G H I J K L M N O Q R S T U V W X Y Z A B C D E F G H I J K L M N O P Q R S U V W X Y Z A B C D E F G H I J K L M N O P Q R S T U V W Y Z A B C D E F G H I J K L M N O P Q R S T U V W X Y

A B C D E F G H I J K L M N O P Q R S T U V W X Y Z A B E F G H I J K L M N O P Q R S T U V W X Y Z A B C D E F I J K L M N O P Q R S T U V W X Y Z A B C D E F G H I J M N O P Q R S T U V W X Y Z A B C D E F G H I J K L M N Q R S T U V W X Y Z A B C D E F G H I J K L M N O P Q R U V W X Y Z A B C D E F G H I J K L M N O P Q R S T U V Y Z A B C D E F G H I J K L M N O P Q R S T U V W X SAVEMEPLEASE CRYPTOGRAMCR URTTFSVCEMUV plain text keyword enciphered The first letter, S is encrypted using the row beginning with C The second letter, A is encryted using the row beginning with R The third letter, V is encrypted using the row beginning with Y The fourth letter, E, is encrypted using the row beginning with P. And so on. . . Z A B C D E F G H I J K L M N O P Q R S T U V W X Y You can use http: //www. simonsingh. net/The_Black_Chamber/v_square. html

Vigenere cipher • Frequency analysis does not apply. • Enormous number of possible keys • The Vigenere cipher is a polyalphabetic cipher. • It was then neglected for 2 centuries – it is hard to break but also hard to encrypt.

Vigenere cipher: the unbreakable code • At first glance the Vigenère Cipher appears to be unbreakable, due to its use of up to 26 different cipher alphabets. Ciphers like this, which use more than one cipher alphabet are known as Polyalphabetic Ciphers. These can be incredibly difficult to decipher, because of their resistance to letter frequency analysis. Indeed, over time, the Vigenère cipher became known as 'Le Chiffre Undechiffrable', or 'The Unbreakable Cipher'. This slide and the next few copied directly from Simon Singh’s website.

Ciphers • Monoalphabetic ciphers: each letter in the plaintext is encoded by only one letter from the cipher alphabet, and each letter in the cipher alphabet represents only one letter in the plaintext. • Polyalphabetic ciphers: each letter in the plaintext can be encoded by any letter in the cipher alphabet, and each letter in the cipher alphabet may represent different letters from the plaintext each time it appears.