Introduction Definitions Steganography means literally Covered Writing in




![Simple Example Original RGB Pixel [150 25 255] MSB LSB 1111 1 00011001 0 Simple Example Original RGB Pixel [150 25 255] MSB LSB 1111 1 00011001 0](https://slidetodoc.com/presentation_image_h/c47ceb278c4fa245bb6c0ea31c942072/image-10.jpg)




- Slides: 18


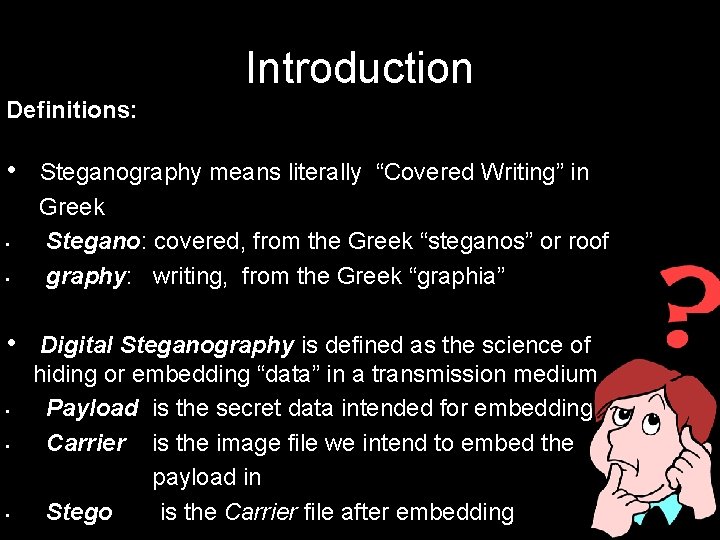
Introduction Definitions: • • Steganography means literally “Covered Writing” in Greek Stegano: covered, from the Greek “steganos” or roof graphy: writing, from the Greek “graphia” Digital Steganography is defined as the science of hiding or embedding “data” in a transmission medium Payload is the secret data intended for embedding Carrier is the image file we intend to embed the payload in Stego is the Carrier file after embedding

Introduction • Ancient Steganography è 5 th century BC (the tattooed head) è 500 years ago, Cardan reinvented the Cardan Grille House BT 48 3 R Figure: Cardan Grille, this is just an illustration - keeping in mind that the Grill has no fixed pattern

Different Disciplines

Applications • Copyright control • Human rights organizations (Encryption prohibited in many countries) • Enhancing image search engines • Smart IDs where individuals’ details are embedded in their photographs • Video-audio synchronization / Companies’ secret data safe circulation • TV broadcasting and TCP/IP packets (e. g. , TTL, etc) • Embedding Checksum • Medical Imaging Systems where a separation is considered necessary for confidentiality between patients’ images and their captions e. g. , Physician, Patient’s name, address and other particulars

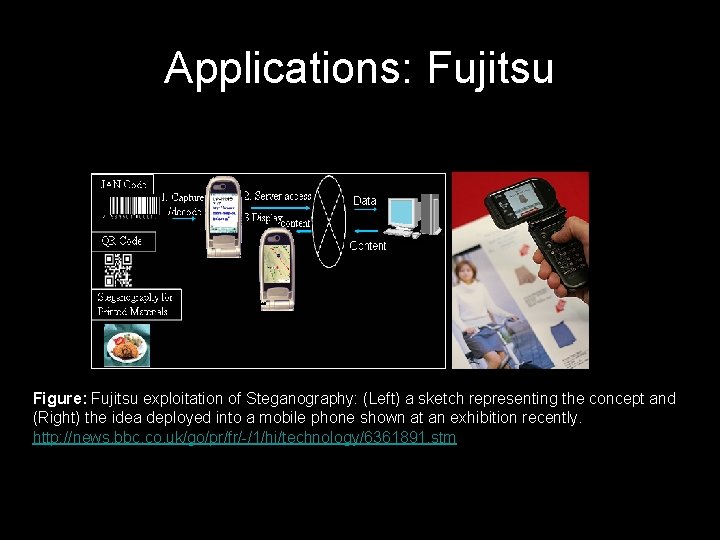
Applications: Fujitsu Figure: Fujitsu exploitation of Steganography: (Left) a sketch representing the concept and (Right) the idea deployed into a mobile phone shown at an exhibition recently. http: //news. bbc. co. uk/go/pr/fr/-/1/hi/technology/6361891. stm

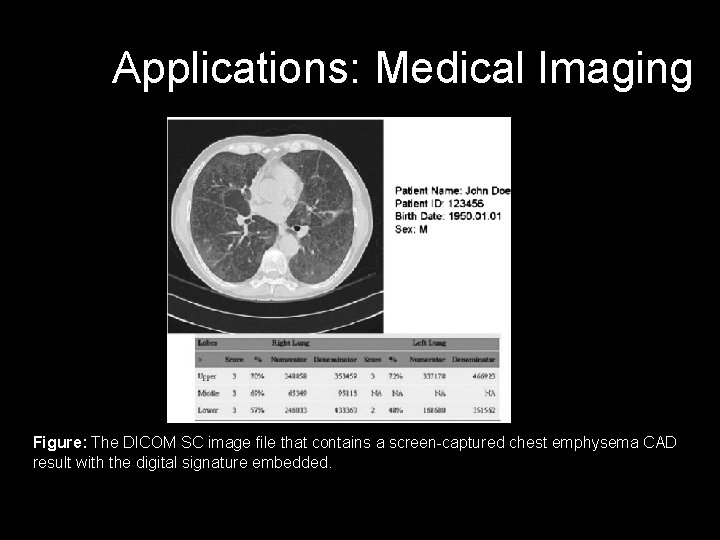
Applications: Medical Imaging Figure: The DICOM SC image file that contains a screen-captured chest emphysema CAD result with the digital signature embedded.

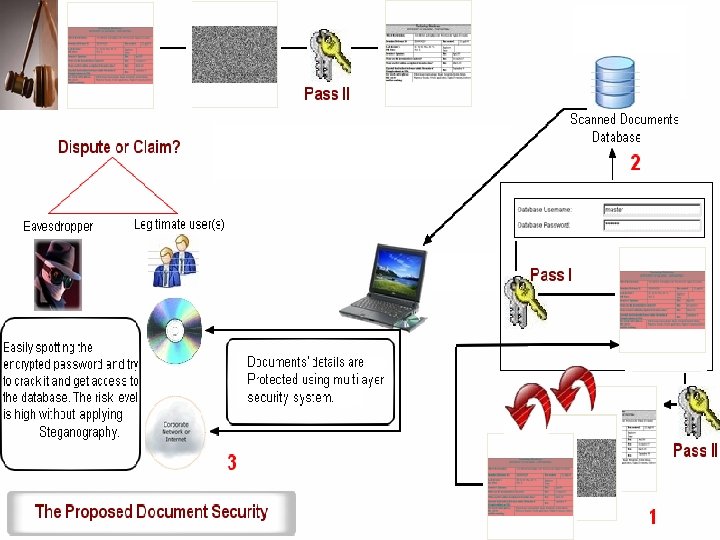
Applications: Secret Sharing Social Network Sender “A” Receiver “B” Clients

How it works? • There are different methods and there is always a trade-off between payload and carrier distortion. § Steganography exploiting image format EOF, EXIF § Steganography in the Image Spatial Domain Direct substitution, Modulus, colour palette, YCb. Cr and HSV transforms etc n Steganography in the Image Frequency Domain JPEG uses discrete cosine transforms (DCT) n Adaptive Steganography or Statistics-aware embedding Edge embedding
![Simple Example Original RGB Pixel 150 25 255 MSB LSB 1111 1 00011001 0 Simple Example Original RGB Pixel [150 25 255] MSB LSB 1111 1 00011001 0](https://slidetodoc.com/presentation_image_h/c47ceb278c4fa245bb6c0ea31c942072/image-10.jpg)
Simple Example Original RGB Pixel [150 25 255] MSB LSB 1111 1 00011001 0 10010110 1 1010101 1101110 1101001 1110110 1100101 1110010 1110011 1101001 1110100 1111001 0100000 1101111 1100110 0100000 1010101 1101100 1110011 1110100 1100101 1110010 Modified RGB Pixel [151 24 255] 1111 00011000 10010111 Binary (‘University of Ulster’);

Hide it in plain site with Steganography! Secret Image Cover Image Stego Image 39. 08

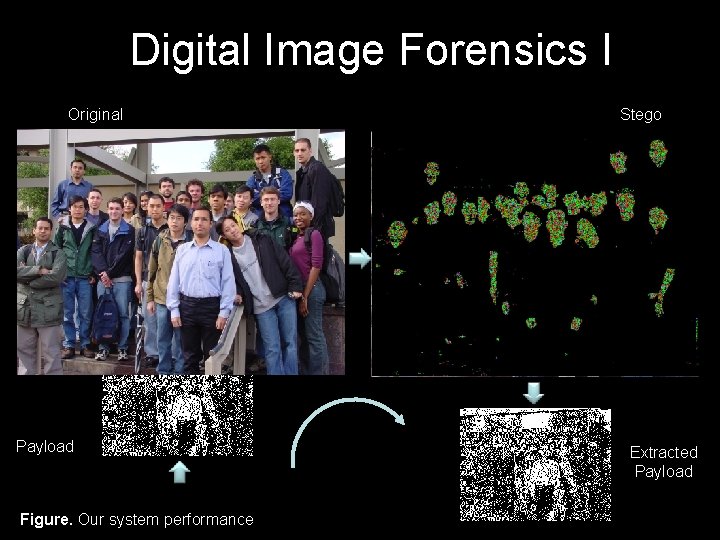
Digital Image Forensics I Original Payload Figure. Our system performance Stego Extracted Payload

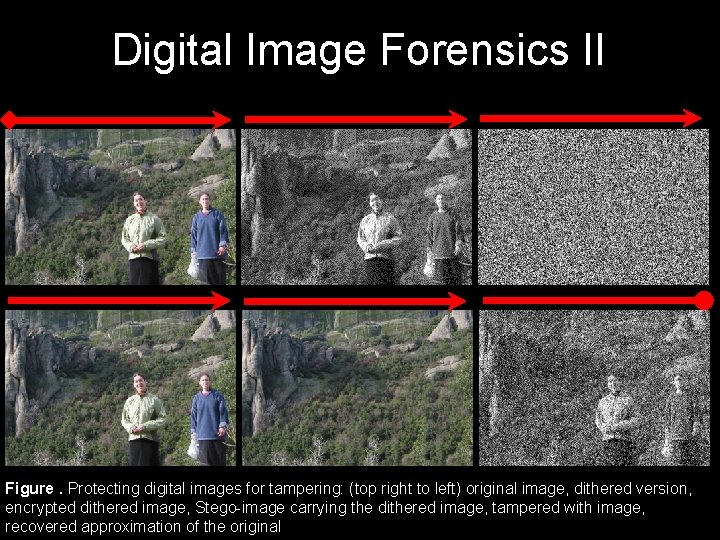
Digital Image Forensics II Figure. Protecting digital images for tampering: (top right to left) original image, dithered version, encrypted dithered image, Stego-image carrying the dithered image, tampered with image, recovered approximation of the original

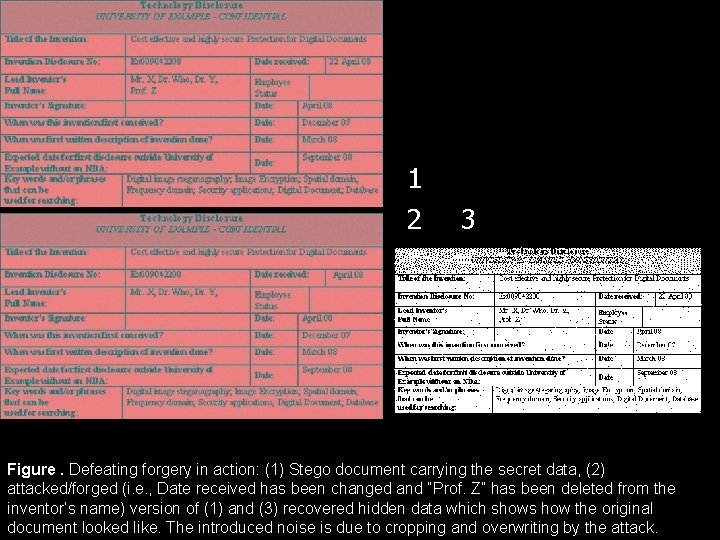
1 2 3 Figure. Defeating forgery in action: (1) Stego document carrying the secret data, (2) attacked/forged (i. e. , Date received has been changed and “Prof. Z” has been deleted from the inventor’s name) version of (1) and (3) recovered hidden data which shows how the original document looked like. The introduced noise is due to cropping and overwriting by the attack.


Attacks • Steganography, like Cryptography, has its counterpart enemy namely Steganalysis which deals with counter attacking Steganographic algorithms • Applying different statistical measurements and image processing techniques

Conclusion • Steganography is an ancient art • With the boost of computer power and with the development of information theory, Steganography was shaped in its current digital form • Attributes itself to security and forensics systems • Defined as the science and art of hiding data within data in an inconspicuous way

Still Interested? • • Virtual Place: http: //www. infm. ulst. ac. uk/~abbasc/ Physical Place: Room MG 212 (B) Email: cheddad-a [AT] email. ulster. ac. uk Tel: 02871375156 (ext: 75156) Thank you for listening Questions?