CS 591 C 3 S Cryptography Steganography Secure














- Slides: 16

CS 591 C 3 S Cryptography & Steganography Secure System By: Osama Khaleel

. Quick Intro • Nowadays, information is rapidly available through the Internet. Companies have the ability to communicate with a worldwide audience through the World Wide Web. • So Information hiding techniques are received a. b. increasing attention due to : the availability of multimedia and digital form objects. and the need to present solutions to criminal copying and copyright problems.

Motivation: As we know, cryptography and steganography have been known for many years. We can encrypt data, but it will be exposed while transferring. On the other hand, we can hide data into a common object, but if someone extracts it, he/she can get the information easily. Therefore, my idea is to apply both of them, so in case one gets the embedded stuff, s/he will face an encrypted data.

Project Idea • To combine two security techniques 1. Cryptography (For Encryption & Decryption) Steganography Data hiding in a multimedia object) (For 2.

? Why to do so • Hiding data is better than moving it shown and encrypted. • To hide data in a popular object that will not attract any attention. • In case the data is extracted, it will be encrypted.

Cryptography: The science of using mathematics to encrypt and decrypt data. It enables you to send sensitive information across insecure networks (such as the Internet). • Advanced Encryption Standard. (AES) • Benefits: 1. Very Secure. 2. Reasonable Cost. 3. Main Characteristics: I. Flexibility. II. Simplicity.

: Algorithm Steps • Sub-Bytes. • Shift rows. • Mix columns. • Add round key.

Steganography: Hiding a secret message within a larger object in such a way that others can not discern the presence of the hidden message. • In this project, I use a PNG image as a cover object. • Why “Image”? • It can contain enough information to hide, while not appearing to be modified. • It is common enough to not attract any attention.

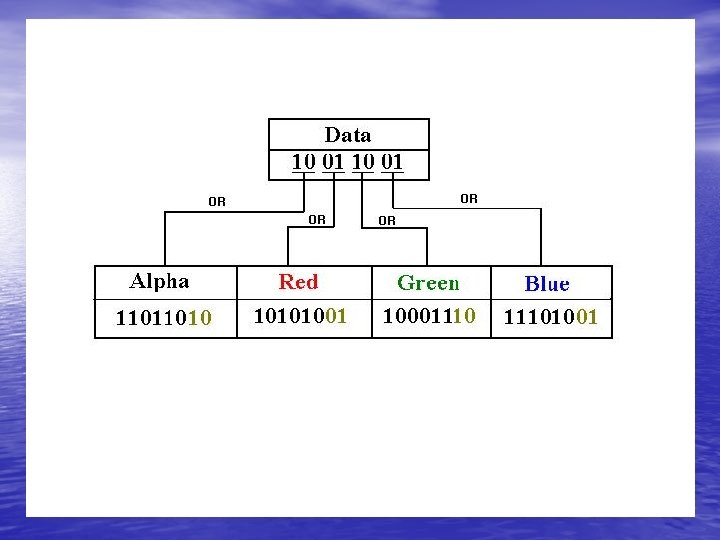
The used Steganographic : Techniques • The Least Significant Bit (LSB): modifying the rightmost bit in each byte by replacing it with a bit from the secret message. • Why “LSB”? • Designed for images that have 3 or 4 bytes per pixel. • When changing 4 bits in a 4 -byte pixel, the change is about 1 / billion.

: The improvements on simple LSB 1) I have added an option that allows the user to insert data into the two “least significant bits”. It is a little bit less secure, because there will be more modification. On the other hand, we can double the secret message size. [it’s up to the user]


: The improvements on simple LSB 2) Randomization of inserting the secret message bits into the image. Developed a function that generates a random offset from the set {2, 4, 6}, then spreads the message bits according to that offset. e. g. Suppose that the offset is “ 4”, then the program will insert the first bit in byte 1, the second bit in byte 5, the third in byte 9 and so on. After reaching certain end, loop back starting from byte 2 then 6, 10, … and so on… This will add a huge security level.

: The improvements on simple LSB 3) Adding SHA-1 hash for the secret message. The program calculates an sha-hash for the secret message in the hiding stage, and checks this value when retrieving the hidden message. Therefore, it can detect any attempt to modify the message content. This will also add a security plus a confidentiality levels.

Now, if you are asking about how the recipient will know what the used variables are; (the random offset, the LSB method, the SHA-hash, the message length, …) : ? ? ? The program creates a header for these variables, and reserves the first 70 bytes for that header to insert it after encrypting it. Then it inserts the encrypted message starting from byte 71. On the recipient side, the program reads the first 70 bytes, decrypts them, and gets the variables values to use them to extract the hidden message.

Program Sequence Hiding • Select a PNG image. • Enter a message and a • • cipher key Encrypting message. Hiding it in the selected image. Revealing • Select a PNG image • • • (Stego object). Enter the cipher key. Extracting encrypted data from the image. Decrypting and showing the message.
