CHAPTER 1 Introduction to Computer Security 1 c













- Slides: 25

CHAPTER 1 Introduction to Computer Security 1 (c) by Syed Ardi Syed Yahya Kamal, UTM 2004

Objectives Define the computer security concept Explain the difference between computer intrusion, computer threats, vulnerabilities and controls Differentiate threats to security computing: interception, interruption, fabrication and modification Explain the goals of secure computing i. e confidentiality, integrity, availability and non repudiation Discuss controls available to address these security threats 2

‘’SECURE” mean… Protecting Valuables. Computer-related assets, not gold & money. Protecting Money vs. Protecting Information. 3

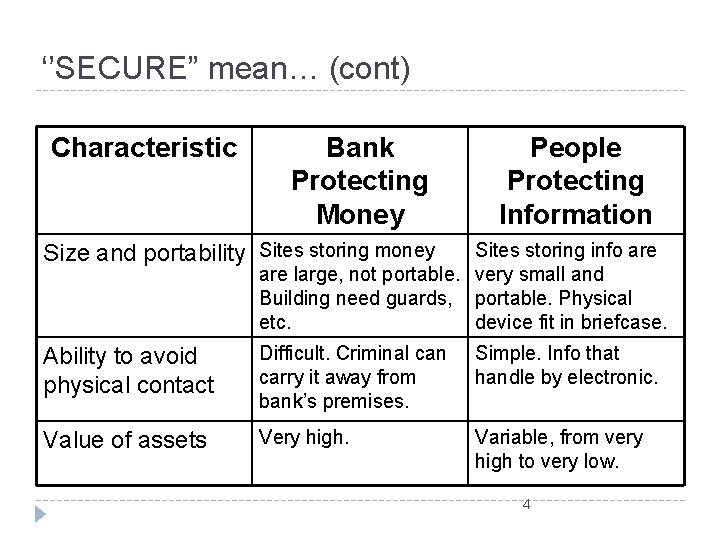
‘’SECURE” mean… (cont) Characteristic Bank Protecting Money People Protecting Information Size and portability Sites storing money Sites storing info are large, not portable. very small and Building need guards, portable. Physical etc. device fit in briefcase. Ability to avoid physical contact Difficult. Criminal can carry it away from bank’s premises. Simple. Info that handle by electronic. Value of assets Very high. Variable, from very high to very low. 4

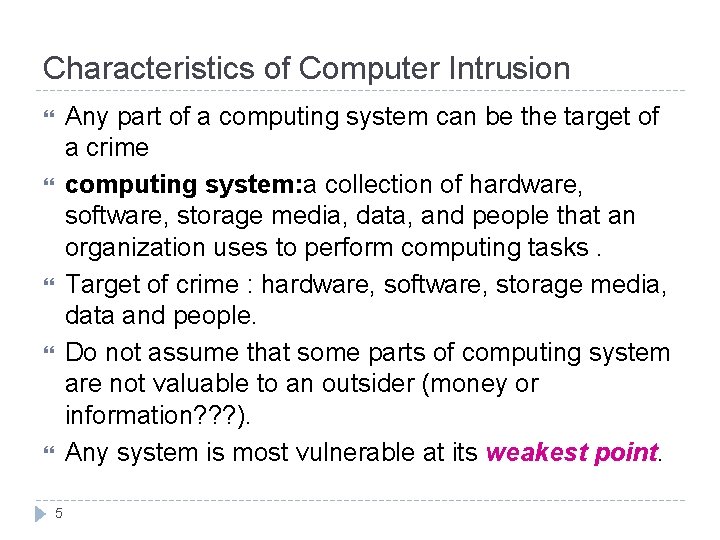
Characteristics of Computer Intrusion Any part of a computing system can be the target of a crime computing system: a collection of hardware, software, storage media, data, and people that an organization uses to perform computing tasks. Target of crime : hardware, software, storage media, data and people. Do not assume that some parts of computing system are not valuable to an outsider (money or information? ? ? ). Any system is most vulnerable at its weakest point. 5

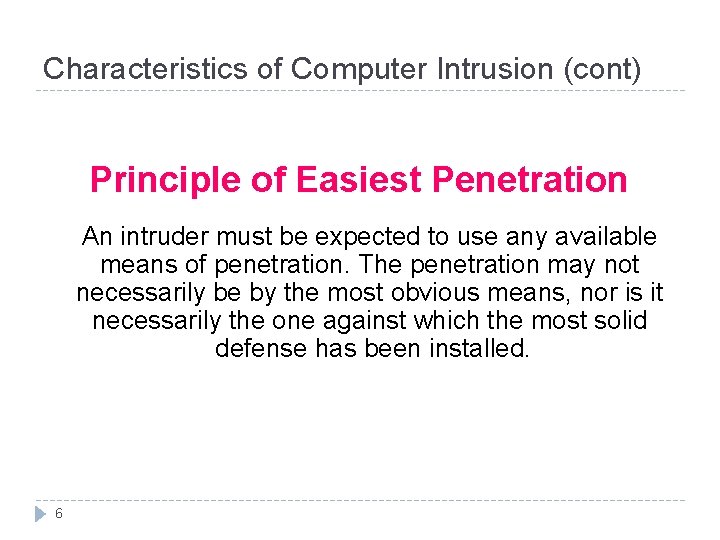
Characteristics of Computer Intrusion (cont) Principle of Easiest Penetration An intruder must be expected to use any available means of penetration. The penetration may not necessarily be by the most obvious means, nor is it necessarily the one against which the most solid defense has been installed. 6

ATTACKS When we test any computer system, we need to imagine how the system could malfunction. Then we improve the system’s design so that the system can withstand any of the problems that we have identified. 7

Threats, Vulnerabilities and Control Three valuable components: hardware, software and data. Vulnerability : weakness in the security system, for example in procedures, design or implementation that might be exploited to cause loss or harm. Data manipulation – system does not verify a user 's identity before allowing data access. 8

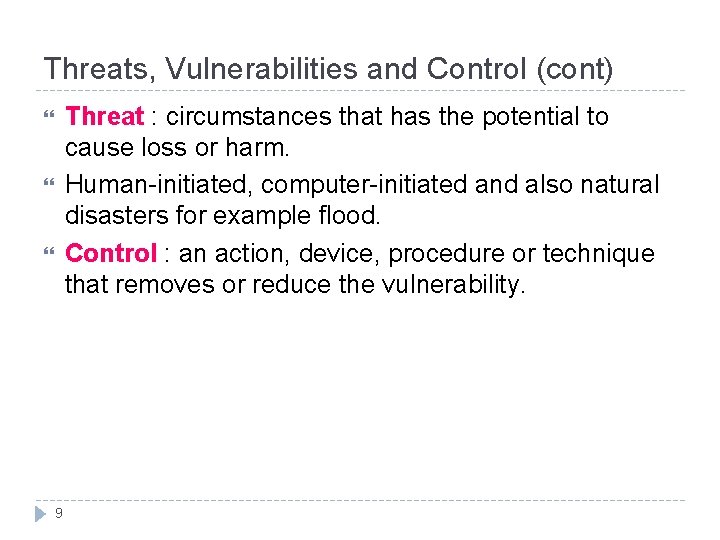
Threats, Vulnerabilities and Control (cont) Threat : circumstances that has the potential to cause loss or harm. Human-initiated, computer-initiated and also natural disasters for example flood. Control : an action, device, procedure or technique that removes or reduce the vulnerability. 9

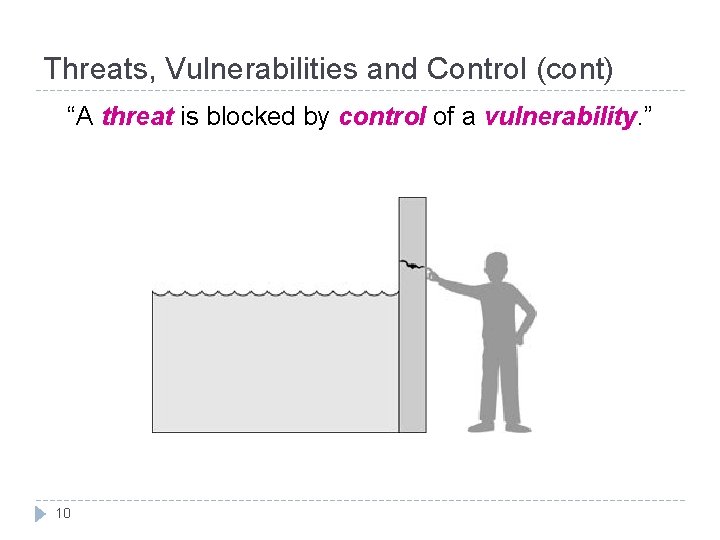
Threats, Vulnerabilities and Control (cont) “A threat is blocked by control of a vulnerability. ” 10

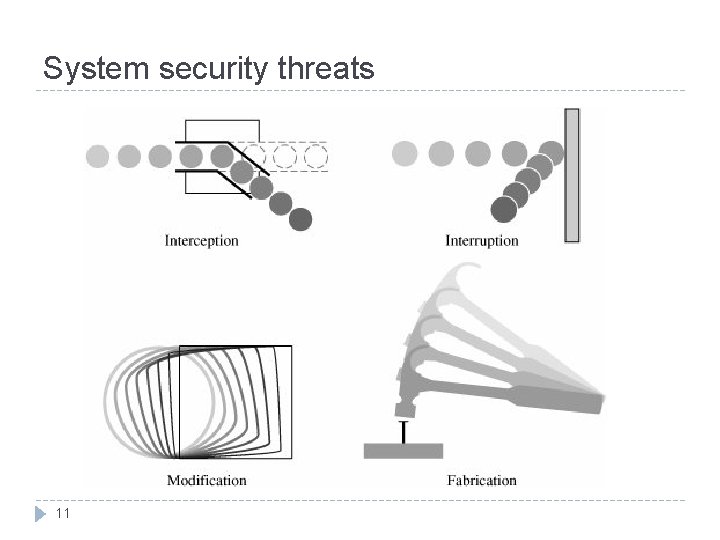
System security threats 11

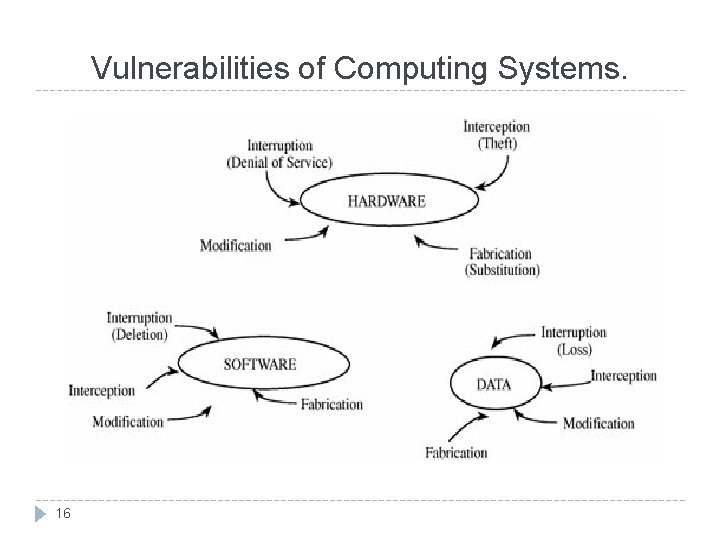
Threats, Vulnerabilities and Control (cont) 4 kinds of threat : 12 Interception : some unauthorized party has gained access to an asset. – illicit copying of program or a computing system. Interruption : an asset of the system becomes lost, unavailable or unusable. – erasure of a data file or malfunction of an operating system. Modification : unauthorized party not only accesses but tampers with an asset. – changes the values in a database. Fabrication : intruder insert spurious transaction to an existing computing system. – forgeries.

Attacker syndrome A malicious attacker must have three things (MOM syndrome): 13 Method : the skills, knowledge, tools and other things with which to be able to pull of the attack. Opportunity : the time and access to accomplish the attack. Motive : a reason to want to perform this attack against this system.

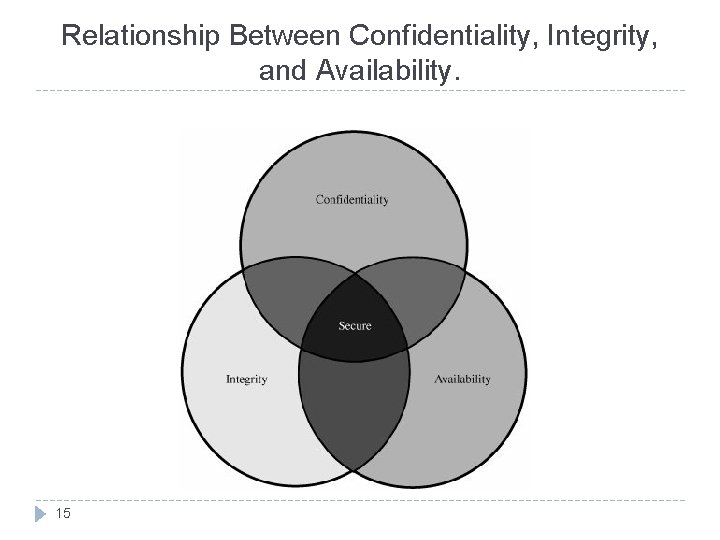
The Meaning of Computer Security The purpose of computer security is to devise ways to prevent the weaknesses from being exploited Security goals: 14 Confidentiality : ensures that computer related assets are accessed only by authorized parties. It is sometime called secrecy or privacy. Integrity : assets can be modified only by authorized parties or only in authorized ways. Availability : assets are accessible to authorized parties at appropriate times. Also known by its opposite, denial of service.

Relationship Between Confidentiality, Integrity, and Availability. 15

Vulnerabilities of Computing Systems. 16

Computer Criminals computer crime is any crime involving a computer or aided by the use of one some of these characteristics: 17 Amateurs : committed most of the computer crimes reported to date. Ordinary computer professionals or users. When they become disgruntled, they vow to ‘get even’ with management by wreaking havoc on a computing installation.

Computer Criminals (cont) Crackers or Malicious Hackers : often high school or university students, attempt to access computing facilities for which they have not been authorized. It is seen as the ultimate victimless crime. They enjoy the simple challenge of trying to log in, just to see whether it can be done. There is no common profile or motivation for these attackers. 18

The security community distinguishes between a "hacker, " someone who (nonmaliciously) programs, manages , or uses computing systems, and a "cracker, " someone who attempts to access computing systems for malicious purposes. Crackers are the " evildoers. " Now, hacker has come to be used outside security to mean both benign and malicious users. 19

Computer Criminals (cont) Career criminals : understand the target of computer crime. There is some evidence that organized crime and international groups are engaging in computer crime. Some companies are reticent to prosecute computer criminals. 20

Terrorists : terrorists using computers in three ways: 21 targets of attack: denial-of-service attacks and web site defacements are popular for any political organization because they attract attention to the cause and bring undesired negative attention to the target of the attack. propaganda vehicles: web sites, web logs, and e-mail lists are effective, fast, and inexpensive ways to get a message to many people. methods of attack: to launch offensive attacks requires use of computers.

Methods of Defense : Concepts We can deal with harm in several ways. 22 Prevent it, by blocking the attack or closing the vulnerability. Deter it, by making the attack harder, but not impossible. Deflect it, by making another target more attractive. Detect it, either as it happens or some time after the fact. Recover from its effects.

Methods of Defense : The Methods Controls : physical security-strong gate or door. Encryption : Scrambling process, so that they are unintelligible to the outside observer Software Controls : program control-OS and development control. Hardware Controls : firewalls, intrusion detecting system. Policies and Procedures : codes of ethics. 23 Physical Control : locks the door, backup.

Effectiveness of Controls several aspects that can enhance the effectiveness of controls. Awareness of Problem- People using controls must be convinced of the need for security. That is, people willingly cooperate with security requirements Likelihood of Use -no control is effective unless it is used Overlapping Controls -several different controls may apply to address a single vulnerability (layered defense) Periodic Review -judging the effectiveness of a control is an ongoing task. 24

Exercise Distinguish among vulnerability, threat, and control. Briefly explain four types of threat. What is the principles of computer security? State the ways to deal with harm. List at least three kinds of harm a company could experience from electronic espionage or unauthorized viewing of confidential company materials. 25