CSC 682 Advanced Computer Security Introduction Computer Security




























- Slides: 40

CSC 682: Advanced Computer Security Introduction Computer Security: Art and Science 1

About Me http: //www. nku. edu/~waldenj 1 James Walden – Assistant Professor of Computer Science – waldenj@nku. edu – Interests: • • Software Security Programming Languages Software Engineering Network Security Computer Security: Art and Science 2

Course Administration Web Site – Notes, readings, and assignments on web site. – http: //www. nku. edu/~waldenj 1 Assignment submission – Use submit command on kosh. Contact Information – Email: waldenj@nku. edu – Phone: (859) 572 -5571 Computer Security: Art and Science 3

Topics 1. What is Security? 2. Web Security 3. Evaluating Research Computer Security: Art and Science 4

What is Security? Security is the prevention of certain types of intentional actions from occuring in a system. – These potential actions are threats. – Threats that are carried out are attacks. – Intentional attacks are carried out by an attacker. – Objects of attacks are assets. Computer Security: Art and Science 5

Safety vs Security Adversary: An intelligent attacker who intentionally causes the system to fail. Safety • Home: fire alarm. • Car: crumple zones. • Computer: UPS. Security • Home: door lock. • Car: alarm. • Computer: Login password. Safety and security can interact: Who is watching your computer room after the fire alarm was pulled? Computer Security: Art and Science 6

Goals of Security Prevention – Prevent attackers from violating security policy Detection – Detect attackers’ violation of security policy Recovery – Stop attack, assess and repair damage Survivability – Continue to function correctly even if attack succeeds Computer Security: Art and Science 7

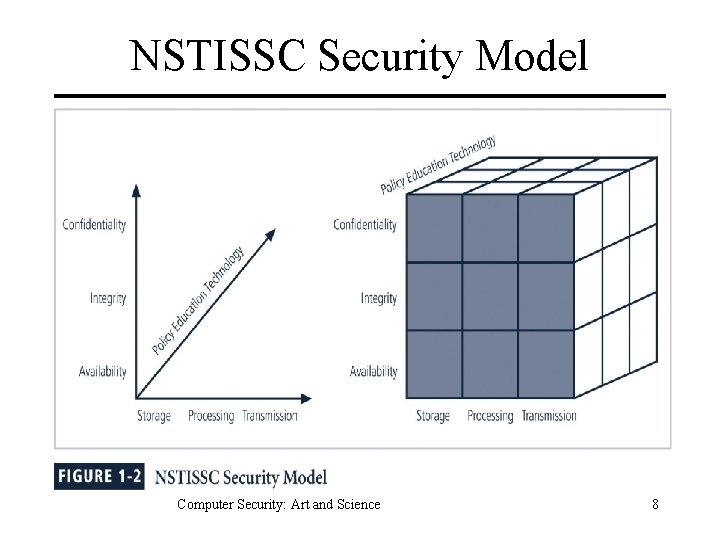
NSTISSC Security Model Computer Security: Art and Science 8

Components of Security Confidentiality – Keeping data and resources hidden. Privacy. Integrity – Preventing unauthorized changes to data or resources. Availability – Enabling access to data and resources Computer Security: Art and Science 9

Confidentiality Authentication Passwords, mother’s maiden name Corporations Trade secrets, e. g. , the formula for Coca Cola. Databases SSN, Driver’s license Governments National security Embarrassing information: www. thememoryhole. org Computer Security: Art and Science 10

Integrity Data Integrity – content of the information. – ex: 2005 Walmart $1. 5 million bar code scam. Origin Integrity (authentication) – source of the information. – ex: 1997 Kurt Vonnegut MIT commencement address email. Vonnegut was not the 1997 speaker and the content wasn’t his. Prevention vs Detection Computer Security: Art and Science 11

Availability Prevent loss of system access. Denial of service attacks common. – Easy to launch, difficult to track down. – Can be just part of another attack Computer Security: Art and Science 12

States of Information 1. Storage Information not currently being accessed. 2. Processing Information currently being used by processor. 3. Transmission Information in transit btw one node and another. Computer Security: Art and Science 13

Security Measures Technology. – Hardware/software used to ensure confidentiality, integrity, or availability. Policy and practice. – Security requirements and activities. Education, training, and awareness. – Understanding of threats and vulnerabilities and how to protect against them. Computer Security: Art and Science 14

How to evaluate security solutions? 1. What assets are you trying to protect? 2. What are the risks to those assets? 3. How well does the security solution mitigate those risks? 4. What other risks does the security solution cause? 5. What costs and trade-offs does the security solution impose? Computer Security: Art and Science 15

Aspects of Risks To evaluate a risk, we need to evaluate both: – Probability of risk occurring. – Cost incurred by risk if it occurs. Minimize product of probability and cost. Risks are impacted by environment. – Building a house in a flood plain incurs additional risks beyond that of house itself. – Similarly, installion and configuration options impact risk of software systems. Computer Security: Art and Science 16

Security is a matter of Trade-offs Security is only one of many system goals: • • • Functionality Ease of Use Efficiency Time to market Cost Security Computer Security: Art and Science 17

Cost-Benefit Analysis Is it cheaper to prevent violation or recover? – Cost of good network security: • Money, time, reduced functionality, annoyed users. • Large and ongoing. – Risks of bad network security: • Angry customers, bad press, network downtime. • Small and temporary. Computer Security: Art and Science 18

Airport Security Let’s consider the issue of airport security from the standpoint of what we’ve learned. Develop a solution, keeping the 5 questions in mind: 1. What assets are you trying to protect? 2. What are the risks to those assets? 3. How well does the security solution mitigate those risks? 4. What other risks does the security solution cause? 5. What costs and trade-offs does the security solution impose? Computer Security: Art and Science 19

Human Issues: People Problems Social engineering – Kevin Mitnick testified before Congress “I was so successful in that line of attack that I rarely had to resort to a technical attack. ” Circumvention – Users write down passwords, leave screens unlocked. Insider attacks Computer Security: Art and Science 20

Human Issues: Organizations Low priority – Security costs, but doesn’t produce income. – Lack of liability reduces costs of bad security. Variable impact – Cost of security violation highly variable. – Insurance converts variable risk to fixed cost, but risk too variable for much involvement so far. Power and responsibility – Personnel responsible for security often don’t have power to enforce security. Computer Security: Art and Science 21

Security: Laws and Customs Are desired security measures illegal? – cryptography export before 2000 – is it legal to monitor security breakins? – international commerce Will users circumvent them? – writing down passwords – removing file ACLs Computer Security: Art and Science 22

Security Liability Product liability: – Tires: Continental recalled Ford SUV tires in 2002 due to wire and vibration problems. – Software: Manufacturer not liable for security flaws. Since Microsoft isn’t liable for Windows security failures, why would they want to sacrifice money, time, functionality, and ease of use for security? Computer Security: Art and Science 23

Assumptions • Security rests on assumptions specific to type of security required and environment. • Example: – TCP/IP designed for pre-commercial Internet. • Assumed only legitimate admins had root access. • Trusted IP addresses, since only root can set IP addr. • What happens to network when Windows 95 systems added to network, where desktop user has all privileges? Computer Security: Art and Science 24

Assurance How much can you trust a system? Example: – Purchasing aspirin from a drugstore. – Bases for trust: • Certification of drug by FDA. • Reputation of manufacturer. • Safety seal on bottle. Computer Security: Art and Science 25

How much do you trust? Ken Thompson’s compiler hack from “Reflections on Trusting Trust. ” – Modified C compiler does two things: • If compiling a compiler, inserts the self-replicating code into the executable of the new compiler. • If compiling login, inserts code to allow a backdoor password. – After recompiling and installing old C compiler: • Source code for Trojan horse does not appear anywhere in login or C compiler. • Only method of finding Trojan is analyzing binary. Computer Security: Art and Science 26

What is web application security? The art and science of developing web applications that function correctly even when under attack.

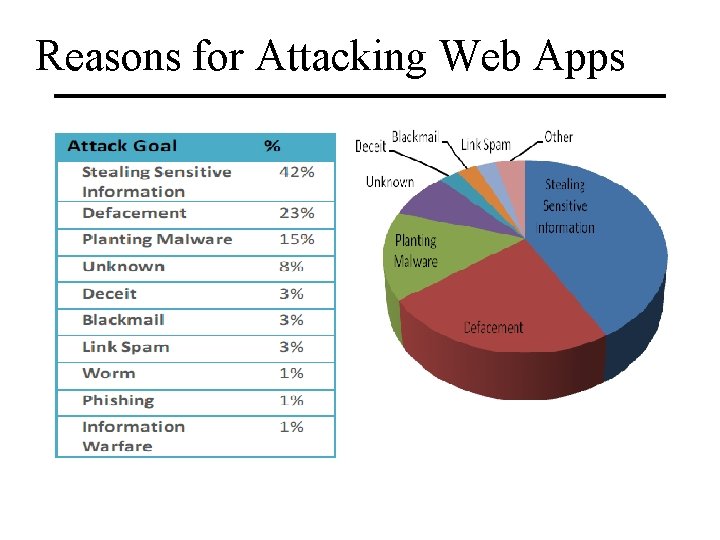
Reasons for Attacking Web Apps

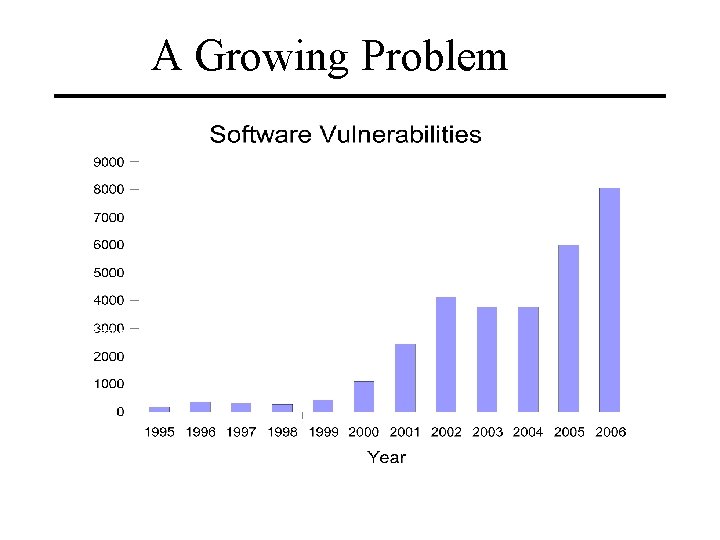
A Growing Problem

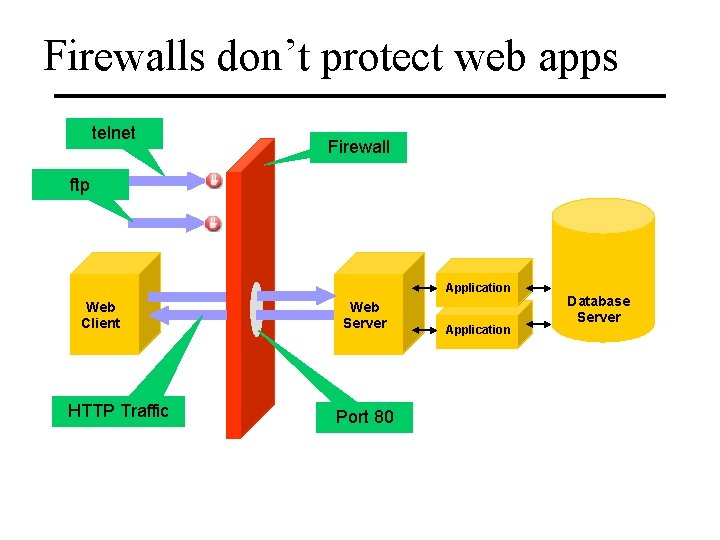
Firewalls don’t protect web apps telnet Firewall ftp Application Web Client HTTP Traffic Web Server Port 80 Application Database Server

HTTP: Hyper. Text Transfer Protocol Simple request/response protocol – Request methods: GET, POST, HEAD, etc. – Stateless: req#2 doesn’t know about req#1 HTTPS – HTTP wrapped in SSL/TLS encryption – Protects data in transit to web server. – Doesn’t protect stored data. – Doesn’t protect server from being hacked.

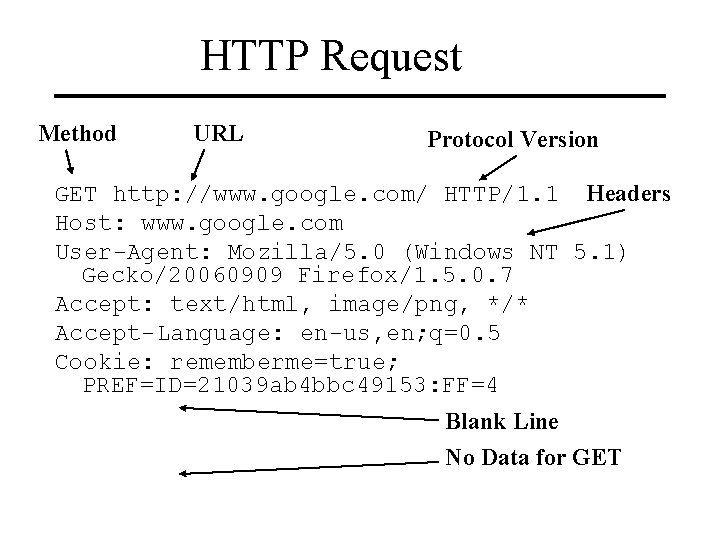
HTTP Request Method URL Protocol Version GET http: //www. google. com/ HTTP/1. 1 Headers Host: www. google. com User-Agent: Mozilla/5. 0 (Windows NT 5. 1) Gecko/20060909 Firefox/1. 5. 0. 7 Accept: text/html, image/png, */* Accept-Language: en-us, en; q=0. 5 Cookie: rememberme=true; PREF=ID=21039 ab 4 bbc 49153: FF=4 Blank Line No Data for GET

HTTP Response Protocol Version HTTP Response Code Headers HTTP/1. 1 200 OK Cache-Control: private Blank Content-Type: text/html Line Server: GWS/2. 1 Date: Fri, 13 Oct 2006 03: 16: 30 GMT <HTML>. . . (page data). . . </HTML> Web Page Data

HTTP GET Parameters http: //ex. com/path/app. cgi? param 1=val 1¶m 2=val 2 Format parameter_name=value Multiple parameters separated by & URI encoding Encode chars as ISO-Latin hex val: %XY Special characters must be encoded. Any character may be encoded.

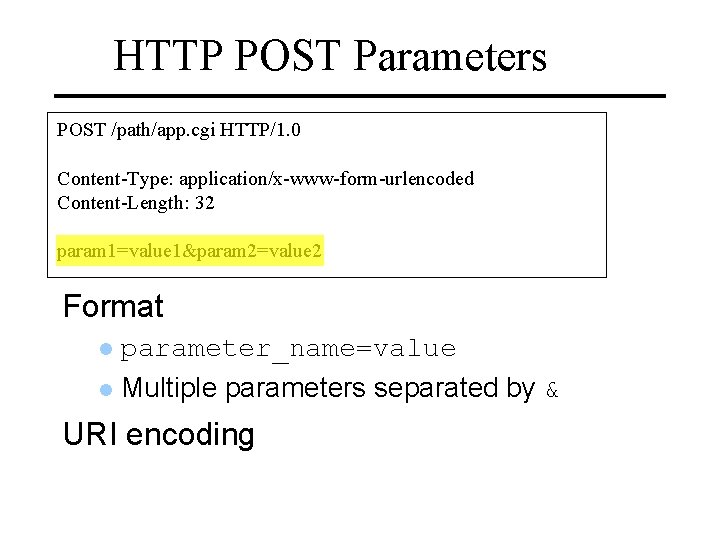
HTTP POST Parameters POST /path/app. cgi HTTP/1. 0 Content-Type: application/x-www-form-urlencoded Content-Length: 32 param 1=value 1¶m 2=value 2 Format parameter_name=value Multiple parameters separated by & URI encoding

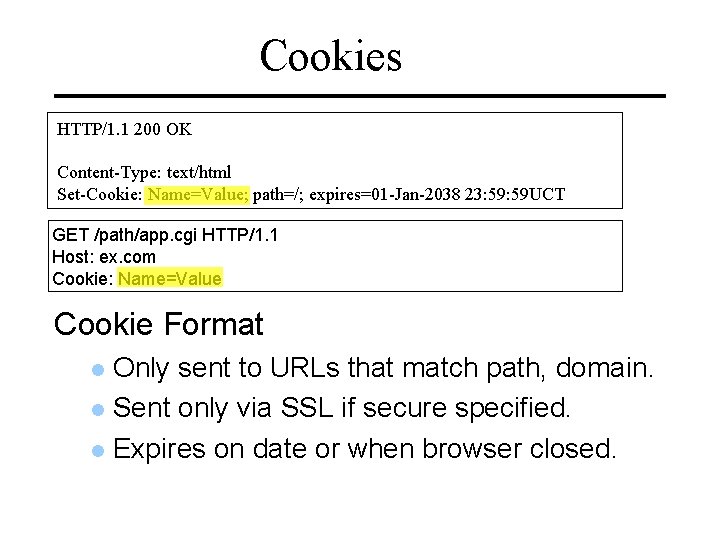
Cookies HTTP/1. 1 200 OK Content-Type: text/html Set-Cookie: Name=Value; path=/; expires=01 -Jan-2038 23: 59 UCT GET /path/app. cgi HTTP/1. 1 Host: ex. com Cookie: Name=Value Cookie Format Only sent to URLs that match path, domain. Sent only via SSL if secure specified. Expires on date or when browser closed.

Web Application Vulnerabilities Input-based Security Problems – Injection Flaws – Insecure Remote File Inclusion – Unvalidated Input Authentication and Authorization – Authentication – Access Control – Cross-Site Scripting Other Bugs – Error Handling and Information Leakage – Insecure Storage – Insecure Communications

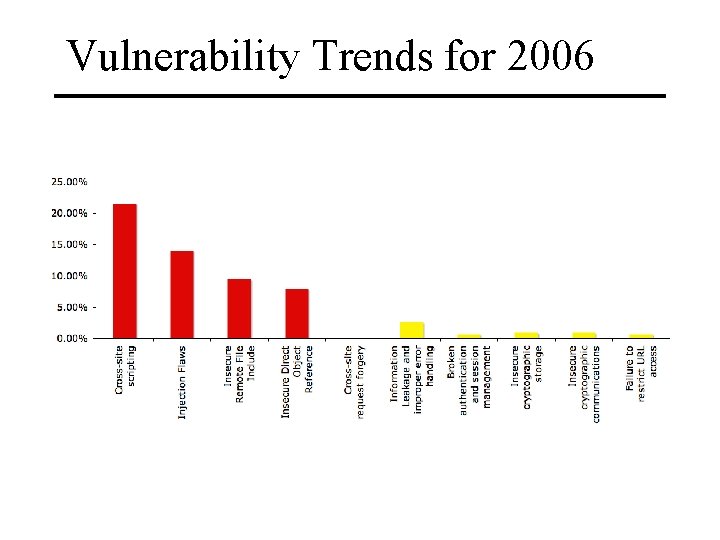
Vulnerability Trends for 2006

Key Points • Components of security – Confidentiality, Integrity, Availability • States of information – Storage, Processing, Transmission • Security is a matter of trade-offs. • Web Input – HTTP stateless request/response protocol. – Cookies are HTTP headers used to provide state. – SSL protects data in transit, but not in storage. Computer Security: Art and Science 39

References 1. Ross Anderson, Security Engineering, Wiley, 2001. 2. Matt Bishop, Introduction to Computer Security, Addison-Wesley, 2005. 3. Peter Neumann, (moderator), Risks Digest, http: //catless. ncl. ac. uk/Risks/ 4. Bruce Schneier, Beyond Fear, Copernicus Books, 2003. 5. Ken Thompson, “Reflections on Trusting Trust”, Communication of the ACM, Vol. 27, No. 8, August 1984, pp. 761 -763 (http: //www. acm. org/classics/sep 95/) Computer Security: Art and Science 40