Computer Security Elaine Munn Introduction to Computer Security





- Slides: 14

Computer Security Elaine Munn Introduction to Computer Security

Introduction n Computer systems and networks are all around us. q q q Online banking Automated supermarket checkouts Online classes Online shopping Online travel resources © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 2

Malware n Software with a malicious purpose q Virus q Trojan horse q Spyware q Logic Bomb © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 3

Malware (cont. ) Virus q q q One of the two most common types Usually spreads through email Uses system resources, causing slowdown or stoppage © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 4

Malware (cont. ) Trojan Horse q q The other most common kind of malware Named after the wooden horse of ancient history © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 5

Malware (cont. ) Spyware q The most rapidly growing types of malware n n Cookies Key logger © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 6

Malware (cont. ) Logic Bomb q Lays dormant until some logical condition is met, often a specific date. © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 7

Compromising System Security Intrusions q Attacks that break through system resources n n Hackers Crackers Social engineering War-driving © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 8

Basic Security Terminology People: q Hackers n n n q q q White hats Black hats Gray hats Script kiddies Sneakers Ethical hackers © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 9

How do I protect my computer? Antivirus: Whenever Windows is up, it should be running an up-todate antivirus program. These work in the background, blocking not only viruses, but all sorts of malware. © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 10

Firewall: Like an antivirus, this type of program runs in the background at all times. But this one controls the traffic between your PC and the rest of the network (and Internet). Windows comes with a perfectly good firewall, but you should make sure it’s on. Search for firewall and select Windows Firewall in Control Panel. In the left pane, click Turn Windows Firewall on or off. © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 11

Updates Make sure Windows updates itself automatically. In Windows 7 or 8, search for and launch Windows Update. Click Change settings in the left pane. If Install updates automatically (recommended) isn’t selected, select it. In Windows 10, search for windows updates and select Windows Updates Settings. Scroll down to the bottom of the window and click Advanced options. Make sure Automatic (recommended) is selected. © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 12

Your browser Just like Windows, your browser needs to be up-to-date and secure. Go to your browser’s settings to make sure it updates regularly and that it’s set to block suspicious sites. © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 13

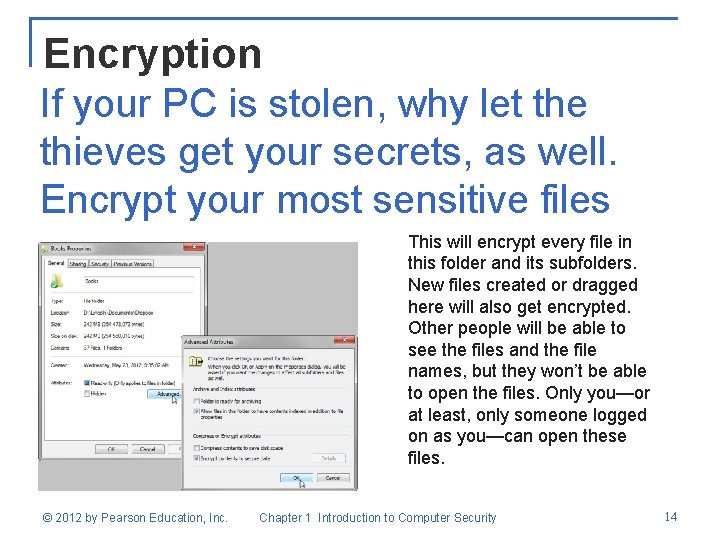
Encryption If your PC is stolen, why let the thieves get your secrets, as well. Encrypt your most sensitive files This will encrypt every file in this folder and its subfolders. New files created or dragged here will also get encrypted. Other people will be able to see the files and the file names, but they won’t be able to open the files. Only you—or at least, only someone logged on as you—can open these files. © 2012 by Pearson Education, Inc. Chapter 1 Introduction to Computer Security 14