ITGS Security Security Authentication Computer security The process





















- Slides: 29

ITGS Security

Security Authentication • Computer security – The process of protecting hardware, software and data from unauthorized access, while allowing authorized users to perform their work • Authentication – requires users to prove their identity so a system knows they are genuine, authorized users • Something you know – Passwords - must be chosen carefully so that they can’t be easily guessed

Authentication • Something you have – Requires a user to have a physical object in order to authenticate • Security token - using a physical object to enter a system • Multifactor authentication - since security tokens can be stolen, another form of authentication in addition to them is used • Something about you – Biometrics • Using a part of a person’s body to identify them – Fingerprints, iris patterns, face shape , voice pattern – Biometrics are unique for each user » Not 100% accurate; a biometric system must attempt to make a good match rather than an exact match with the stored biometric data ( always a margin of error)

Biometric authentication » False negative - when the system fails to recognize an authorized user, and he/she must begin the authentication again » False positive-when an unauthorized user is mistakenly allowed access because the system mistakes their data for that of an authorized user • Something you know – Passwords • Computers do not store passwords as plain text – A one-way function is used to generate a cryptographic hash of a password » It is not possible to retrieve the original password from the hash, making it safe to store the hash. » When the user logs in, another hash is generated and is compared to the original hash value; if the two match, the user is authenticated » The password itself is never stored, nor is it sent across a network

Cryptographic Hash

Passwords • Not all websites use the cryptographic hash method to store passwords securely • If a website or system is able to send you a reminder of your password, it means it is stored in a way accessible to the system administrators • If the forgotten password function sends you a new password, the system administrators don’t have access to your old password (cryptographic hash) • Biometric enrollment • Collecting biometric samples from users along with their identities

Passwords • Example: fingerprints • The computer analyzes the fingerprints, looking for the key features and measurements • It produces a biometric template containing these values • This template is stored for future use • When the user tries to authenticate, another biometric sample is taken and used to produce a biometric template

Access privileges • The new template is compared with the old, and if they match, its authenticated • Most system administrators don’t want all authenticated users to have the same access privileges • Most operating systems provide a way to grant access privileges to individuals or groups of users • A series of rights can be assigned: • The ability to read (view), write (modify) and delete material

Hacking • These rights can be done on individual files, folders, drives and resources like printers • Each user is assigned his own home directory • The system administrator’s account has full access to all items • Hacking – Gaining unauthorized access to computer systems • A hacker exploits weaknesses in the target system’s security • Once the hacker has compromised the system, information is usually stolen

Hacking • Social engineering – Tricking people into giving away passwords • Software tools for hacking: – Packet sniffer - a program that captures data as it travels over networks • Legitimate use: helping diagnose network problems – Key loggers - plug into computer between keyboard and keyboard port • Key loggers run in the background, silently recording keys pressed • Can be detected by anti-virus software – Password cracker - program designed to guess passwords • Dictionary attack - they try every word in a list of known English words until the password is found

Hacking • Brute force method - try every single combination of characters until the right word is guessed – Brute force is slow at 10 million passwords per second, it would take years to guess a long password – END OF MONDAY’S NOTES

Hacking • Preventing the use of password cracking tools – Limiting the number of times a user can try to log in before temporarily locking the account – Small delay between login attempts • OS Fingerprinting tools – Used to give more information about a target system, such as versions of OS and webserver software • The hacker can them investigate possible flaws

Security Updates • Software vendors frequently release patches for their system – Downloading and applying these updates is important because new vulnerabilities are constantly being found • Vulnerability scanner tools – Used by hackers to test a system for vulnerabilities which have not been patched, so they can exploit them

Hacking in action • Zero day exploit – When hackers target a company using vulnerable security, acting on a newly reported and unfixed vulnerability • Malicious software – Viruses • Malicious programs designed to replicate themselves and cause damage to computer systems – Viruses usually attach to other programs or email attachments, and are triggered when a user opens the program or attachment – When the virus spreads, at a given point, such as a certain date, viruses trigger their “payload”, which might be deleting or overwriting files or even wiping the hard disk

Macro viruses • Macro virus – Written using the macro programming languages designed in automated tasks in some software, such as word processors, spreadsheets and databases • They can be configured to run automatically when a document is opened and quickly infect computers – Worms - similar to viruses, but sread without any user interaction • Example: a user opens a worm infected email attachment - the worm might immediately copy itself to other machines on the network or automatically forward to everyone in the user’s address book • Worms consume large amounts of bandwidth as they propagate

Malicious software • Trojan horses – Rely on tricking the user into downloading and running them, instead of spreading on their own • They pretend to perform a useful task (pose as a game or even antivirus software) • Once run, they deliver their payload, which is often spyware, turning the infected machine into a botnet. • Spyware – A form of malware which monitors the user’s activities without their knowledge or permission • Serves them with advertisements targeted to their behavior • More sinister, such a stealing personal files or using a key logger to gauge passwords, usernames and credit card numbers – It is even possible to record the user’s screen • Rootkits – A particularly hard to remove form of malware that generally infects a machine as the administrator (root) user

Malicious software – Rootkits hide their identity from the user and the OS and alter it – Difficult to detect – Usually can only be removed by installing a fresh operating system • Backdoor infections - malware that is operated by an unauthorized remote user is becoming more common – A computer infected in this way is called a zombie – Botnets - when criminal computer gangs control hundreds or thousands of zombies at once • They send out spam or phishing email, or distribute malicious software • DDOS attacks - bombarding a computer system with so many requests that it can’t keep up, becomes slow, or crashes • Drive-by downloads – Programs which are downloaded or installed automatically, without the user’s consent, when he visits a webpage • Usually either infect a system with malware or make money by tricking the user into buying unnecessary security software – Java. Script, Active. X and Java - technologies that can be used to create enhanced, interactive webpages, but also can be misused to deliver driveby downloads • END OF WEDNESDAY’S NOTES

Spam • Spam - unwanted messages that are sent to many users at once. – Usually e-mail, but can also refer to phone text messages (SMS) – Usually advertise products, many illegal or unregulated, such as prescription drugs • 419 Scams (also known as Nigerian Scams): scam messages which try to entice the user into sending money – Common spamming techniques: » A subject line which seems personal » Spam sent by a virus or worm may actually use the name of a sender you know – Large amounts of spam also slow down email servers, consuming space and bandwidth – Employees in businesses waste valuable time dealing with spam - 7. 3 minutes every week, adding up to $71 billion of lost productivity in the US • Spam bot - software that scans through thousands of web pages looking for email addresses – Searches through web pages for email addresses, HTML code, mailto tags, and web forms filled in by users • Some companies exist with the sole purpose of collecting and selling databases of email addresses

Spam filters • Spam filters – Used by most email providers to reduce the amount of spam you have • Organizations can install their own spam filters on an email server or client computer – Spam. Assassin - an open source program • Use Bayesian filtering to examine email and determine how likely it is to be Spam, based on the words it uses • Monitor global spam email and make available the IP addresses or domain names of spam sources • Many websites use CAPTCHAs or “scribble text” to prevent abuse by automated spam bots – CAPTCHAs create an image using distorted text, background noise, and disorienting lines, designed to be impossible for a spam bot program to decipher but easy for a human. • Commonly used on websites to create accounts (especially email systems) to prevent spammers writing software to automatically generate hundreds or thousands of false accounts • Avoiding spam filters – Spammers use various techniques to avoid the filters • Embed a paragraph of text from a website or book into the spam email to fool the Bayesian filters into thinking the message is genuine – This works because the ‘normal’ text reduces the relative frequency of words associated with spam

Avoiding Spam Filters • Image spam – Spammers try to avoid spam filters by including their message in an image file instead of text • Since spam filter’s can’t read or understand the text in an image, such emails may be passed through – Web bugs • Links in spam messages to images stored on the spammer’s server – When you open the email with the web bug, the image is fetched from the server, and your email address is confirmed, encouraging the spammer to send you more spam » This can be avoided by switching off images in email software • Ways to avoid spam – Use BCC (blind carbon copy) to protect others’ email addresses – Use disposable email addresses when using email on sites that may cause problems » Some web mail companies offer disposable addresses that temporarily point to your real email address but expire after a time

Phishing • Phishing – Impersonating a genuine organization in order to fool the user into providing sensitive personal data • Such emails usually contain a link to a web site which is an exact copy of the original site, but is operated by criminals – Some phishing sites display an ‘incorrect password’ error after details are entered and direct users to the real site, making you think you just made a typing mistake • Smishing - using text messages to commit phishing attacks • Vishing - using a phone call to commit a phishing attack – Vo. IP software allows inexpensive calls to be made, even from overseas, and they are very hard to trace

Phishing • Pharming – Also known as DNS poisoning • Another technique used by phishers to direct users to a fake website when they enter the URL of a genuine site – Criminals illegally access a DNS server and put the IP address of their fake site in lace of the IP address of the real site – When the user enters the compromised domain name in their browser, the DNS server returns the false IP address and takes them to the fake site – Identity theft • Phishing is performed to commit identity theft - stealing personal data to impersonate them • ***Don’t use links to get to banks - type in the URL manually to avoid phishing

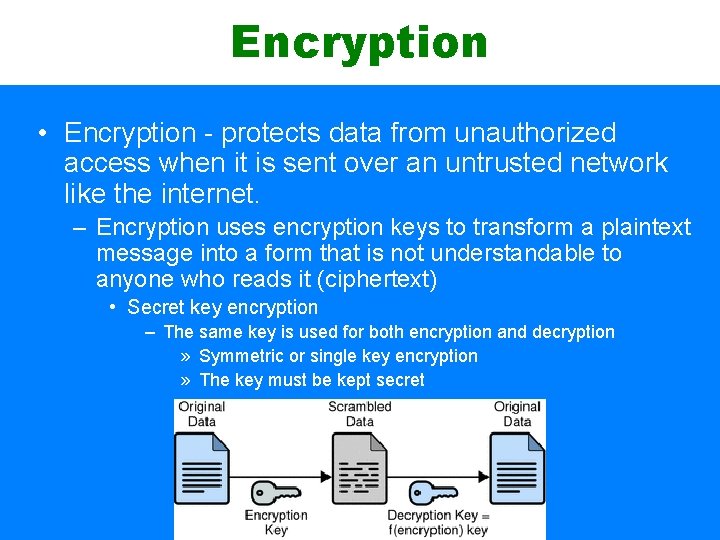
Encryption • Encryption - protects data from unauthorized access when it is sent over an untrusted network like the internet. – Encryption uses encryption keys to transform a plaintext message into a form that is not understandable to anyone who reads it (ciphertext) • Secret key encryption – The same key is used for both encryption and decryption » Symmetric or single key encryption » The key must be kept secret

Encryption • Public key encryption – Asymmetric key encryption - uses a key pair: • Public key is used only for encryption • Private key - used only for decryption – The keys work only when together » Once a message is encrypted with public key, only corresponding private key can decrypt it – An encrypted connection to a web site is indicated by https at the start of the URL • This signifies SSL (secure socket layer) or TLS (Transport Layer Security) encryption is being used

Digital signing • Digital certificate - used to authenticate the sender of a message – Using a private key to digitally sign your message to prove your identity • Certificate authorities verify the owner of public keys and issue digital certificates (key pairs) to organizations after checking their identity • END OF THURSDAY’S NOTES

Digital signing • Certificate authority – Responsible for issuing digital certificates (key pairs) to organizations , after checking their identity. • Used by many online businesses to prove that they are dealing with genuine businesses • Encryption in Action – Transport Layer Security (TLS) and Secure Socket Layer (SSL) • Standard encryption protocol used for secure web communication – TLS - used for logins to email providers and social networks, and for online banking and shopping transactions » An encrypted website will show the https protocol at the start of the URL in the web browser.

Encryption • Extended Validation SSL (EV SSL) – A digital certificate system designed to verify the identity of online organizations (Certificate authority) • Wired Equivalent Privacy (WEP) – An older encryption algorithm used by wireless networks • It is superseded by Wi-Fi protected access (WPA) and WPA-2 – Encrypted protocols keep data safe as it is transmitted from computers with wi-fi cards to wi-fi routers • Encryption and hard disks – Data stored on laptop computers and portable storage devices is particularly vulnerable to loss or theft – It’s easy to remove hard disks from computers and attach them as a slave disk on another computer • Full disk encryption - prevents hard disks from being stolen by asking for a passphrase which is used to decrypt data from the disk

Encryption – The correct passphrase decrypts sectors in memory as they are read from the disk – As data is written to disk from memory, it is automatically encrypted • Encryption Ethics – Strong encryption guarantees that no one without the key can view the plaintext - not even the law • Criminals know that they can encrypt their illegal data – This leads to lack of evidence in criminal prosecutions – Key escrow - an authorized authority has users’ encryption keys, and reveals them to law enforcement if requested • Wireless security – Wireless networks are riskier than ethernet networks • Wireless network data is vulnerable to interception because it is broadcast through the air – All wireless networks should be encrypted » WPA 2 is the best wireless encryption standard

Wireless security • SSID (service set identifier) – Possible to hide a wireless network’s name (SSID) to prevent it from appearing in the list of networks shown by computers • MAC address filtering - can be configured on most wireless routers, and denies access to the wireless network from an computers whose MAC addresses are not on a list – To secure a router, change the default password • Most of the routers from factories come with default usernames – Lists of these default names can be found on the internet • Physical security – Preventing intruders from gaining access to a computer system to steal it or compromise it