Altruistic Routing in P 2 P Networks Solutions









- Slides: 30

Altruistic Routing in P 2 P Networks: Solutions and Problems Sukumar Ghosh Alina Bejan Amlan Bhattacharya University of Iowa The University of Iowa

Background The University of Iowa 2

Background Structured P 2 P networks provide a flat response to query processing. Traffic flow in P 2 P networks exhibits a degree of variability as supported by various measurements, but routing is immune to traffic flow patterns. The University of Iowa 3

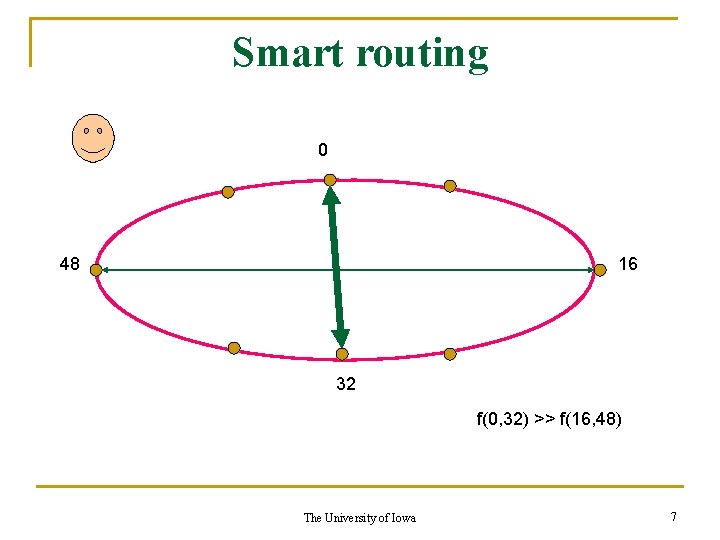
Smart routing To optimize “routing cost” the network must reduce the latency of the frequently used routes, perhaps at the expense of an increased latency in the rarely used routes. The University of Iowa 4

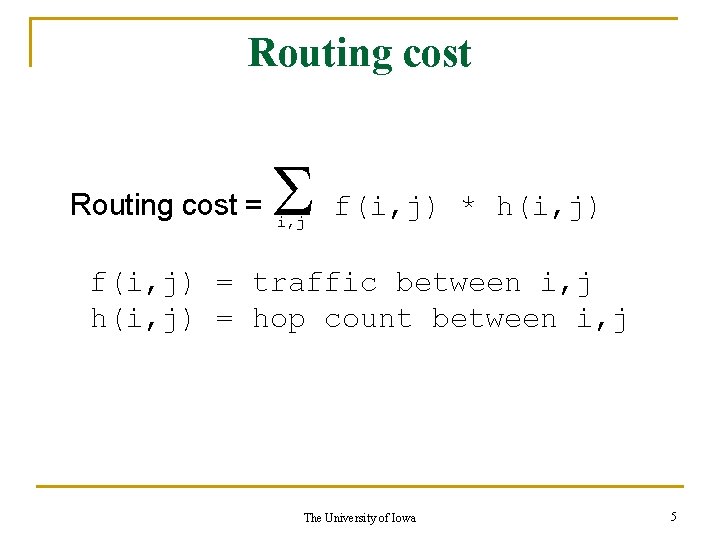
Routing cost = f(i, j) * h(i, j) i, j f(i, j) = traffic between i, j h(i, j) = hop count between i, j The University of Iowa 5

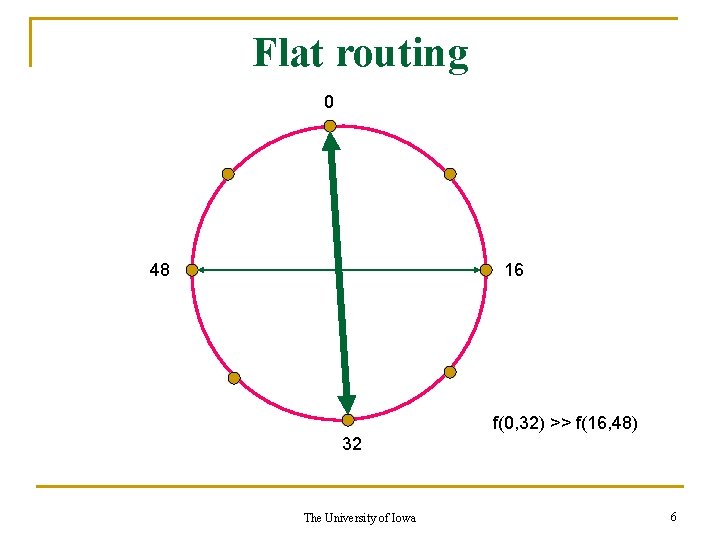
Flat routing 0 48 16 f(0, 32) >> f(16, 48) 32 The University of Iowa 6

Smart routing 0 48 16 32 f(0, 32) >> f(16, 48) The University of Iowa 7

Goal of this exercise How can processes in a P 2 P network spontaneously “tweak” their routing tables to optimize the routing cost? We studied this on Chord (Stoica et al) The University of Iowa 8

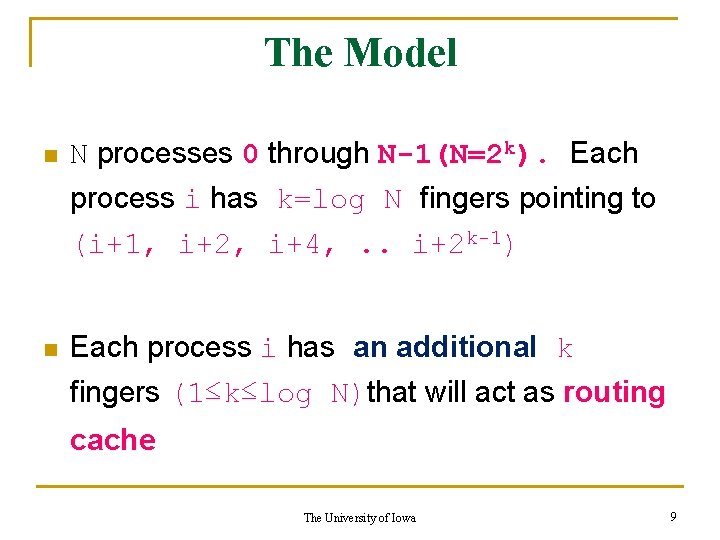
The Model n N processes 0 through N-1(N=2 k). Each process i has k=log N fingers pointing to (i+1, i+2, i+4, . . i+2 k-1) n Each process i has an additional k fingers (1≤k≤log N)that will act as routing cache The University of Iowa 9

The Model For a given packet, if a node has a routing cache entry points to the destination of a packet (cache hit), then that packet will reach the destination in the next hop. Otherwise it will follow the traditional Chord route The University of Iowa 10

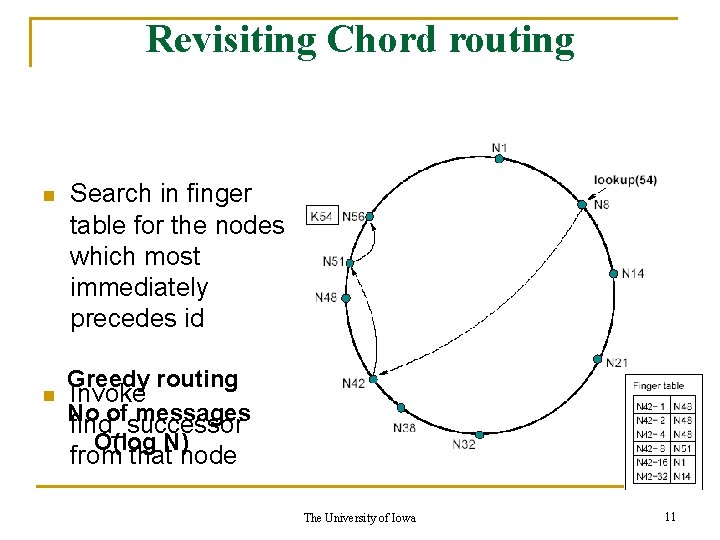
Revisiting Chord routing n n Search in finger table for the nodes which most immediately precedes id Greedy routing Invoke No of messages find_successor O(log N) from that node The University of Iowa 11

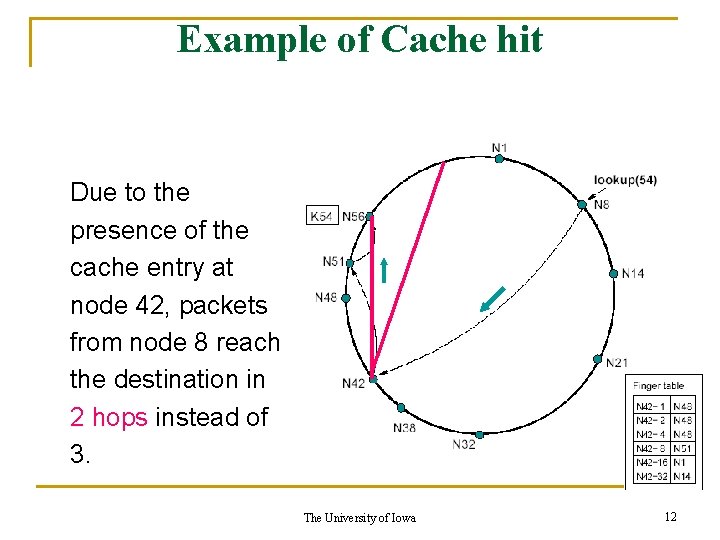
Example of Cache hit Due to the presence of the cache entry at node 42, packets from node 8 reach the destination in 2 hops instead of 3. The University of Iowa 12

The strategies The routing cost will very much depend on on the content of the routing caches. What routes will be cached by a node? We look into two strategies: (a) selfish (b) altruistic The University of Iowa 13

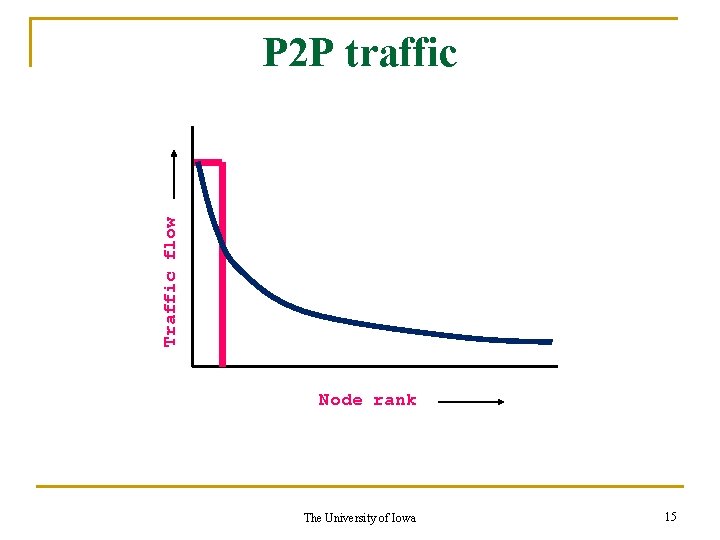
A selfish strategy For any node, define a top destination as one to which the traffic flow is “high”. Then each node will orient its cache entries towards its own top destinations. What is the impact of this strategy? The University of Iowa 14

Traffic flow P 2 P traffic Node rank The University of Iowa 15

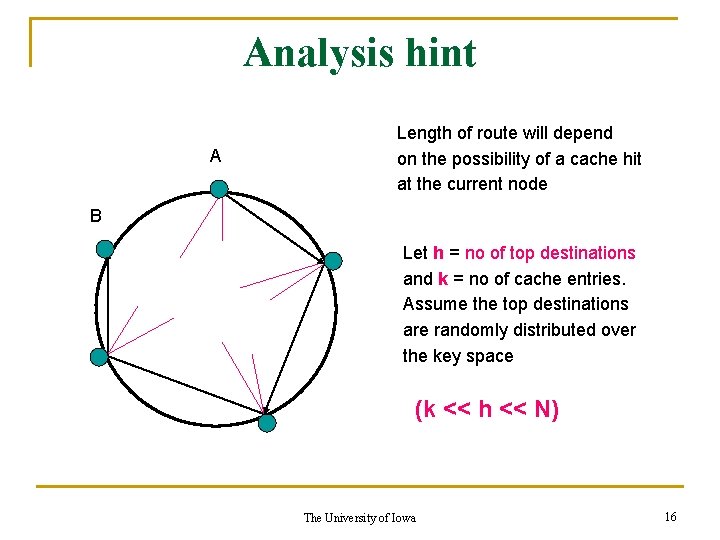
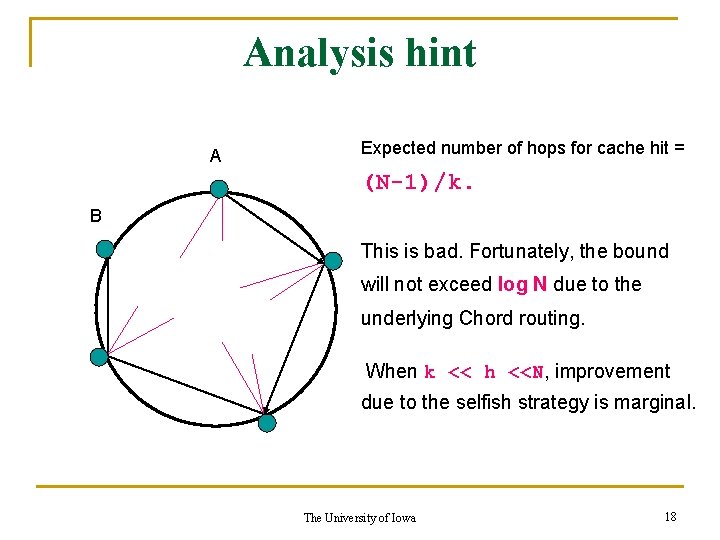
Analysis hint A Length of route will depend on the possibility of a cache hit at the current node B Let h = no of top destinations and k = no of cache entries. Assume the top destinations are randomly distributed over the key space (k << h << N) The University of Iowa 16

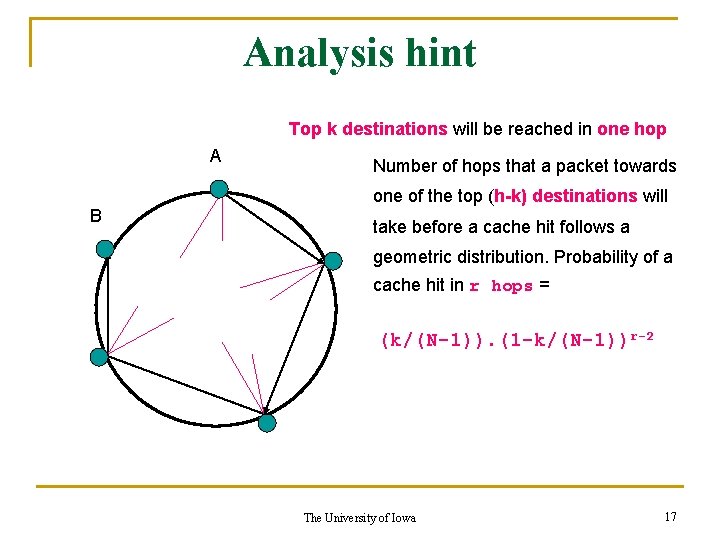
Analysis hint Top k destinations will be reached in one hop A B Number of hops that a packet towards one of the top (h-k) destinations will take before a cache hit follows a geometric distribution. Probability of a cache hit in r hops = (k/(N-1)). (1 -k/(N-1))r-2 The University of Iowa 17

Analysis hint A Expected number of hops for cache hit = (N-1)/k. B This is bad. Fortunately, the bound will not exceed log N due to the underlying Chord routing. When k << h <<N, improvement due to the selfish strategy is marginal. The University of Iowa 18

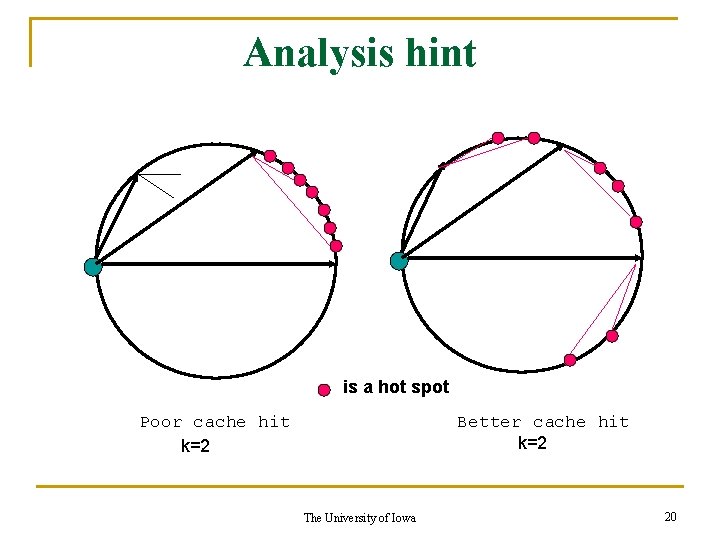
An altruistic strategy Each node will orient its routing cache entries towards its top destinations of other nodes only. How does this work? The University of Iowa 19

Analysis hint is a hot spot Poor cache hit k=2 Better cache hit k=2 The University of Iowa 20

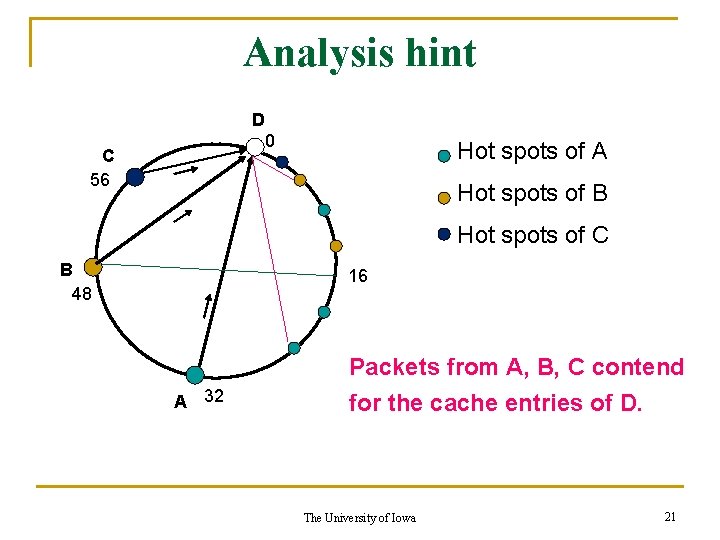
Analysis hint D 0 C 56 Hot spots of A Hot spots of B Hot spots of C B 48 16 A 32 Packets from A, B, C contend for the cache entries of D. The University of Iowa 21

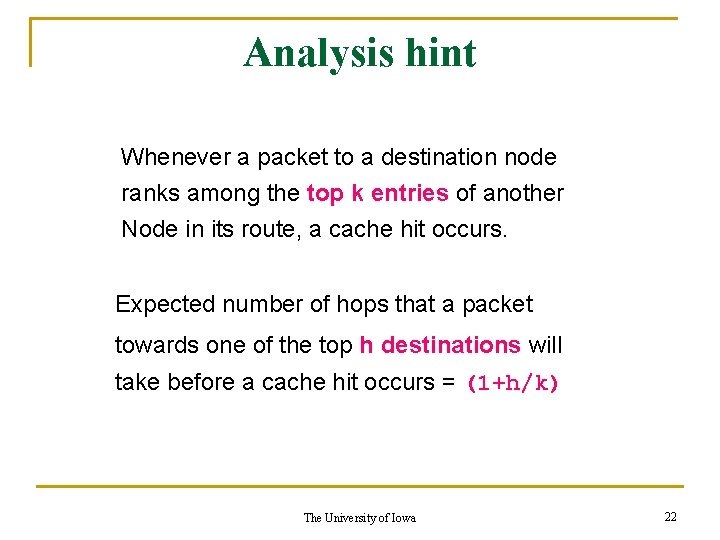
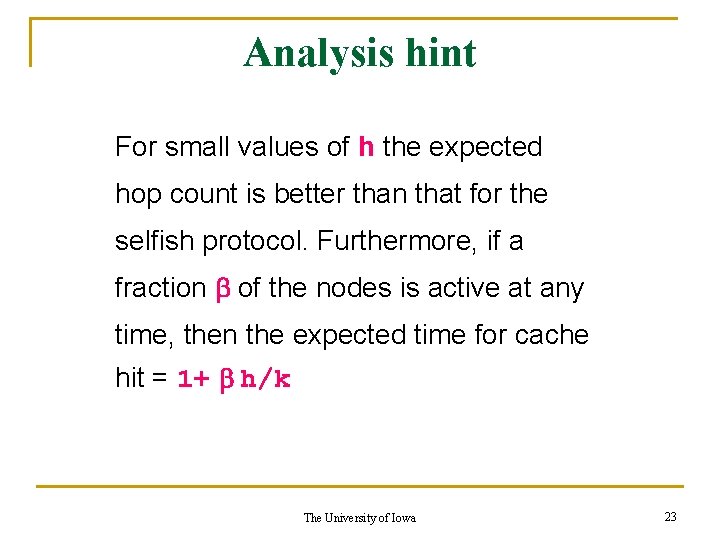
Analysis hint Whenever a packet to a destination node ranks among the top k entries of another Node in its route, a cache hit occurs. Expected number of hops that a packet towards one of the top h destinations will take before a cache hit occurs = (1+h/k) The University of Iowa 22

Analysis hint For small values of h the expected hop count is better than that for the selfish protocol. Furthermore, if a fraction b of the nodes is active at any time, then the expected time for cache hit = 1+ b h/k The University of Iowa 23

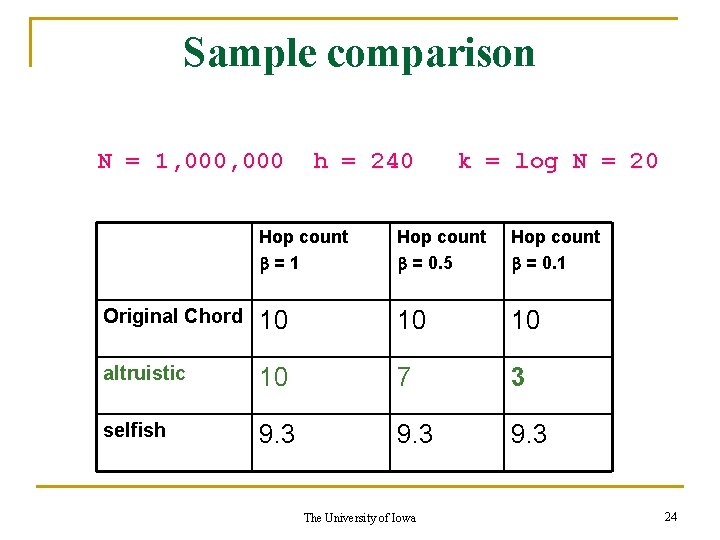
Sample comparison N = 1, 000 h = 240 k = log N = 20 Hop count b=1 Hop count b = 0. 5 Hop count b = 0. 1 Original Chord 10 10 10 altruistic 10 7 3 selfish 9. 3 The University of Iowa 24

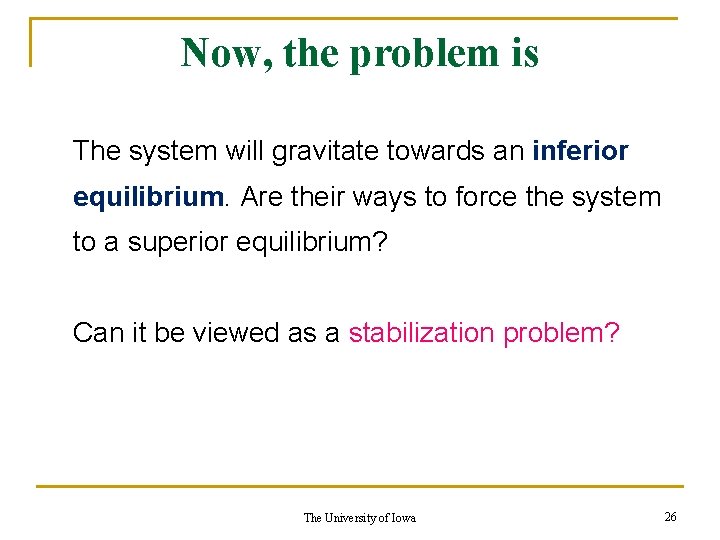
Now, the problem is Why will all nodes agree to run the altruistic protocol? Some may cheat by running a selfish version, and get an unfair advantage. This may make every node think: “may be many others are running the selfish version. Let me stop being altruistic. ” The University of Iowa 25

Now, the problem is The system will gravitate towards an inferior equilibrium. Are their ways to force the system to a superior equilibrium? Can it be viewed as a stabilization problem? The University of Iowa 26

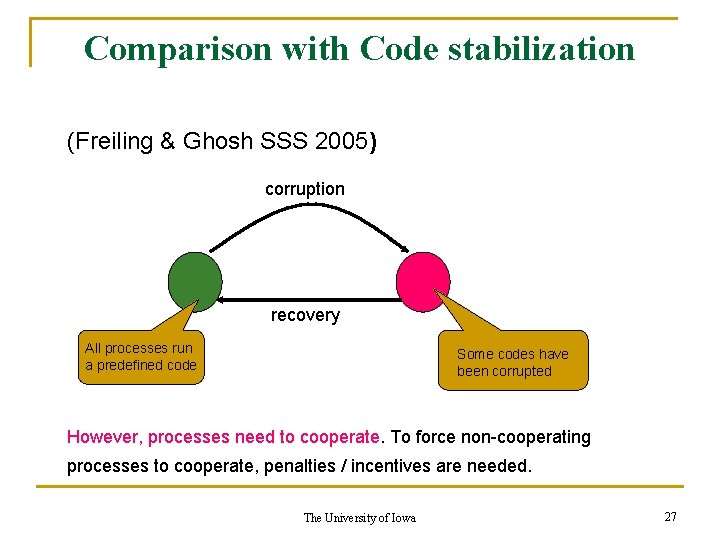
Comparison with Code stabilization (Freiling & Ghosh SSS 2005) corruption recovery All processes run a predefined code Some codes have been corrupted However, processes need to cooperate. To force non-cooperating processes to cooperate, penalties / incentives are needed. The University of Iowa 27

Mandating externally imposed behavior N processes 0 through N-1 each runs a program P A fraction of them do not cooperate and run a program P’≠ P We want all of them to eventually run the same program P Issue 1. How to detect deviations? Issue 2 How to develop a system of penalties / incentives? Issue 3. Quantifying resilience The University of Iowato deviations 28

Conclusion n Many of these are application dependent n Non-cooperative behaviors add new challenges to the problems of self-stabilization / selforganization The University of Iowa 29

Questions? The University of Iowa 30
 Static routing and dynamic routing
Static routing and dynamic routing Hydrologic routing and hydraulic routing
Hydrologic routing and hydraulic routing Routing in physical design
Routing in physical design Vertical line in html
Vertical line in html Psychology chapter 13 social psychology
Psychology chapter 13 social psychology Polygyny in animals
Polygyny in animals Diffident etymology
Diffident etymology English 10 unit 5 vocabulary
English 10 unit 5 vocabulary What is love?
What is love? Altruistic behavior
Altruistic behavior Algorithms in computer networks
Algorithms in computer networks Broadcast routing in computer networks
Broadcast routing in computer networks Datagram network diagram
Datagram network diagram Backbone networks in computer networks
Backbone networks in computer networks Nokia
Nokia Dsdv
Dsdv Routing control platform
Routing control platform Continuity equation hydrology
Continuity equation hydrology Routing table
Routing table Eigrp advantages
Eigrp advantages Systematische handling analyse
Systematische handling analyse Advantages of link state routing vs distance vector
Advantages of link state routing vs distance vector Routing table
Routing table Routing table longest prefix match
Routing table longest prefix match Goodrich method flood routing
Goodrich method flood routing Hello
Hello Routing area update
Routing area update Enterprise integration patterns
Enterprise integration patterns Delivery routing algorithms
Delivery routing algorithms Ortec routing and dispatch
Ortec routing and dispatch Routing system 2
Routing system 2