LINK STATE PROTOCOLS contents Disadvantages of the distance


- Slides: 13

LINK STATE PROTOCOLS (contents) Disadvantages of the distance vector protocols Link state protocols Why is a link state protocol better? 1

Disadvantages of the Distance Vector Protocols Slow convergence Counting to infinity problem Lack of variety of metrics No possibility of hierarchical routing Bad performance in large networks 2

Link State Protocols developed to overcome the disadvantages of the distance vector protocols centralized database describes the topology of the whole network calculation and routing are still distributed 3

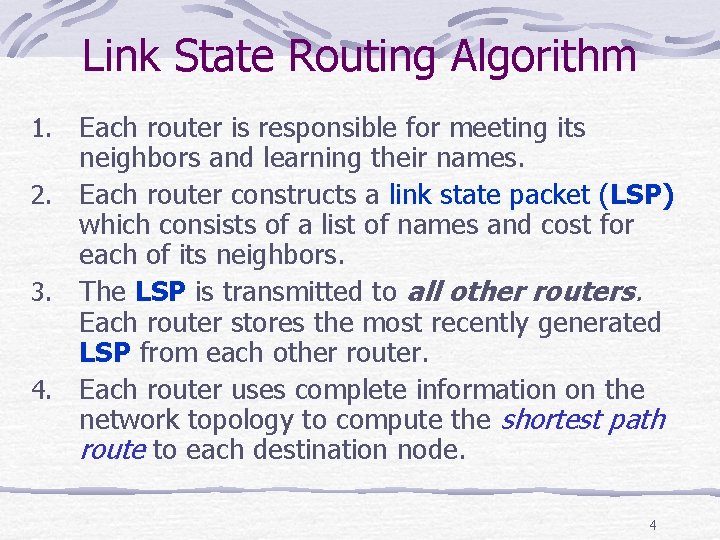
Link State Routing Algorithm Each router is responsible for meeting its neighbors and learning their names. 2. Each router constructs a link state packet (LSP) which consists of a list of names and cost for each of its neighbors. 3. The LSP is transmitted to all other routers. Each router stores the most recently generated LSP from each other router. 4. Each router uses complete information on the network topology to compute the shortest path route to each destination node. 1. 4

Characteristics information about adjacencies sent to all routers only when there is a change each router maintains an identical database a “shortest path” algorithm is used to find the best route converge as quickly as databases can be updated 5

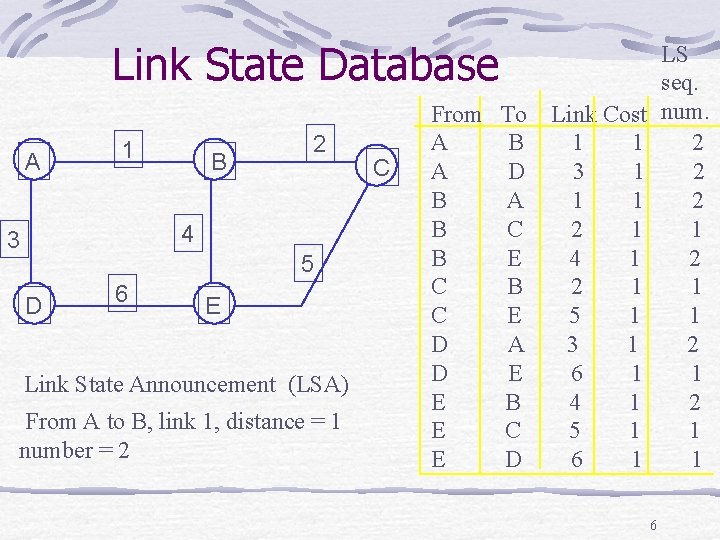
Link State Database A 1 B 2 4 3 5 D 6 E Link State Announcement (LSA) From A to B, link 1, distance = 1 number = 2 C From A A B B B C C D D E E E To B D A C E B E A E B C D LS seq. num. 2 2 2 1 2 1 1 Link Cost 1 1 3 1 1 1 2 1 4 1 2 1 5 1 3 1 6 1 4 1 5 1 6

The Flooding Protocol every node sends the message on every link except the one from where it received the message very fast and very reliable, but wastes bandwidth used for ordinary traffic in military networks messages are sent only when there is a change or every 45 minutes 7

Securing the Map Updates the flooding procedure includes hop-by-hop acknowledgments the database description packets are transmitted in a secure fashion each link state record is protected by a timer and is removed from the database if a refreshing packet does not arrive in due time all records are protected by checksum the messages can be authenticated, e. g. by passwords 8

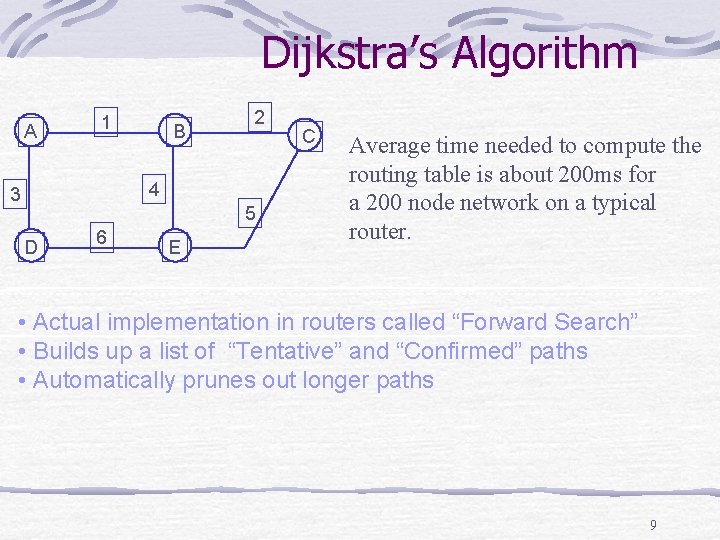
Dijkstra’s Algorithm A 1 B 2 4 3 5 D 6 E C Average time needed to compute the routing table is about 200 ms for a 200 node network on a typical router. • Actual implementation in routers called “Forward Search” • Builds up a list of “Tentative” and “Confirmed” paths • Automatically prunes out longer paths 9

Why Is a Link State protocol Better? fast loopless convergence support of precise metrics and, if needed multiple metrics support of a multiple paths to a destination splitting very large networks in areas 10

Link State Protocols Disadvantages more memory required the link state database is needed in addition to the routing tables much more complex procedure higher probability for a bug in the program 11

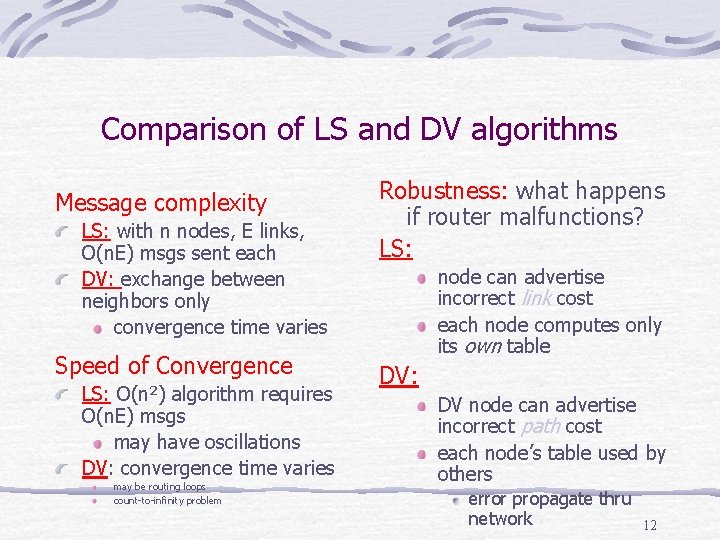
Comparison of LS and DV algorithms Message complexity LS: with n nodes, E links, O(n. E) msgs sent each DV: exchange between neighbors only convergence time varies Speed of Convergence O(n 2) LS: algorithm requires O(n. E) msgs may have oscillations DV: convergence time varies may be routing loops count-to-infinity problem Robustness: what happens if router malfunctions? LS: node can advertise incorrect link cost each node computes only its own table DV: DV node can advertise incorrect path cost each node’s table used by others error propagate thru network 12

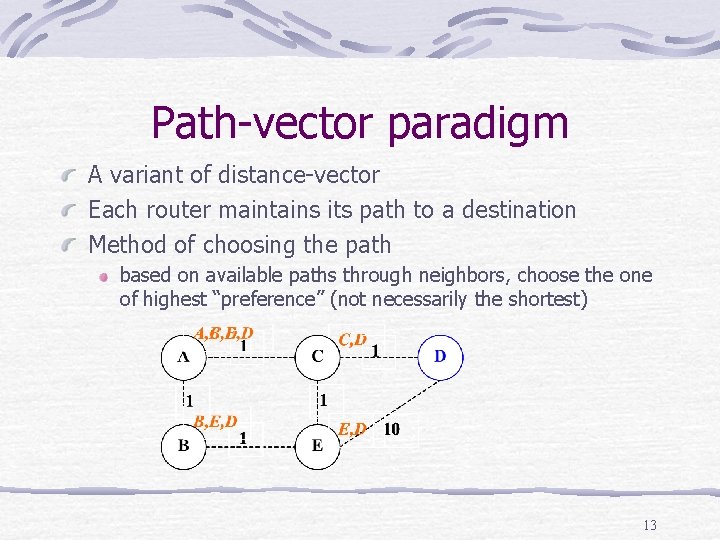
Path-vector paradigm A variant of distance-vector Each router maintains its path to a destination Method of choosing the path based on available paths through neighbors, choose the one of highest “preference” (not necessarily the shortest) 13