Sensor Network Routing Romit Roy Choudhury and Pradeep













- Slides: 46

Sensor Network Routing Romit Roy Choudhury and Pradeep Kyasanur (Some slides are based on Dr. Nitin Vaidya’s tutorial)

A Review of Current Routing Protocols for Ad Hoc Mobile Wireless Networks Elizabeth M Royer, Chai-Keong Toh

Mobile Ad Hoc Wireless Networks • Unreliable wireless medium • Mobile nodes • No central authority • Traffic patterns application specific • Energy constraints • More information in MANET Charter

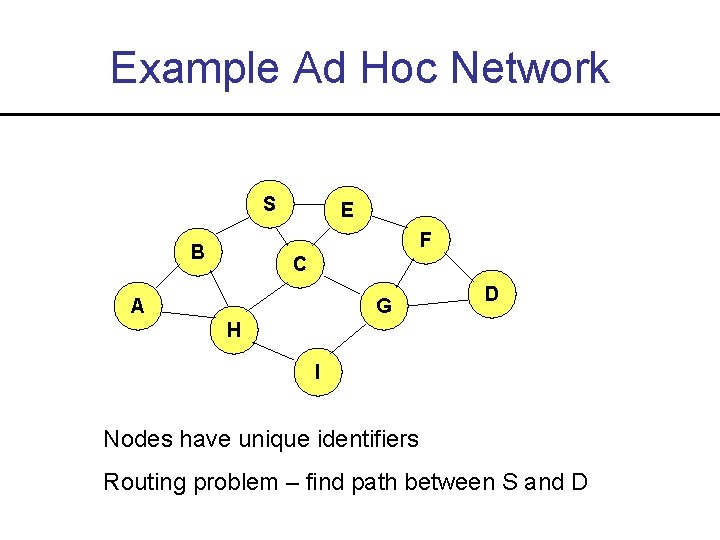
Example Ad Hoc Network S E F B C A G D H I Nodes have unique identifiers Routing problem – find path between S and D

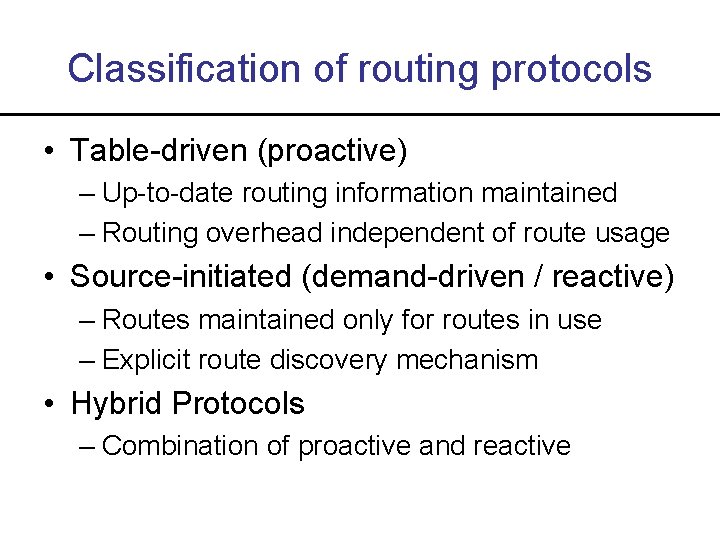
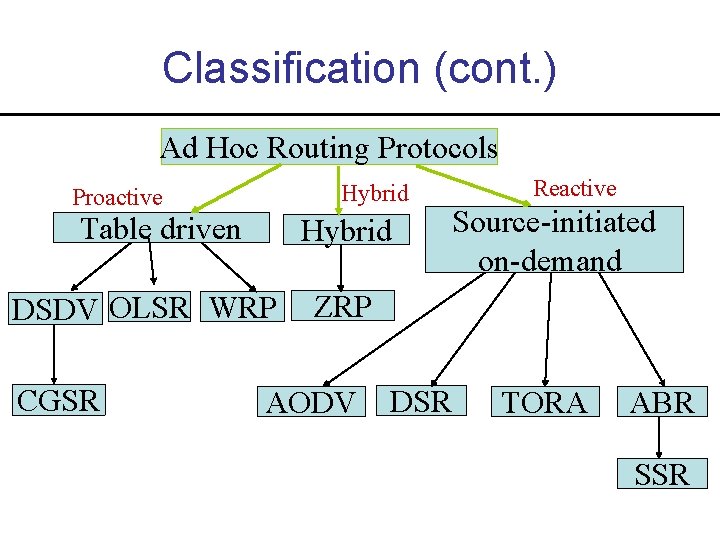
Classification of routing protocols • Table-driven (proactive) – Up-to-date routing information maintained – Routing overhead independent of route usage • Source-initiated (demand-driven / reactive) – Routes maintained only for routes in use – Explicit route discovery mechanism • Hybrid Protocols – Combination of proactive and reactive

Classification (cont. ) Ad Hoc Routing Protocols Hybrid Proactive Table driven Hybrid DSDV OLSR WRP CGSR Reactive Source-initiated on-demand ZRP AODV DSR TORA ABR SSR

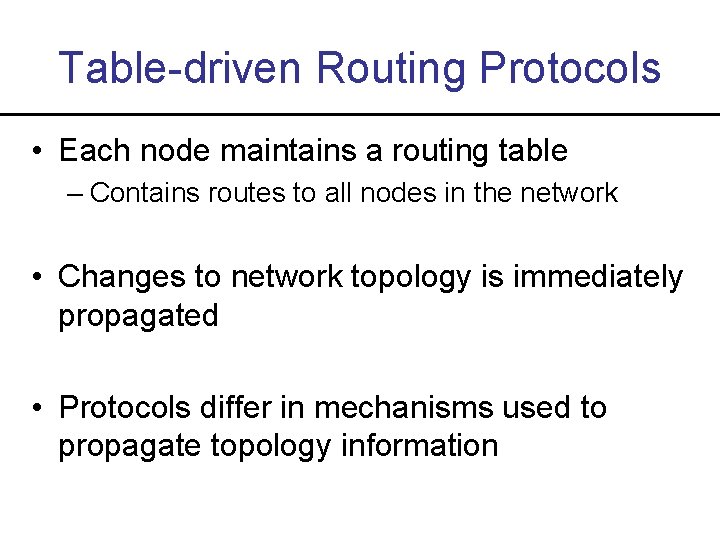
Table-driven Routing Protocols • Each node maintains a routing table – Contains routes to all nodes in the network • Changes to network topology is immediately propagated • Protocols differ in mechanisms used to propagate topology information

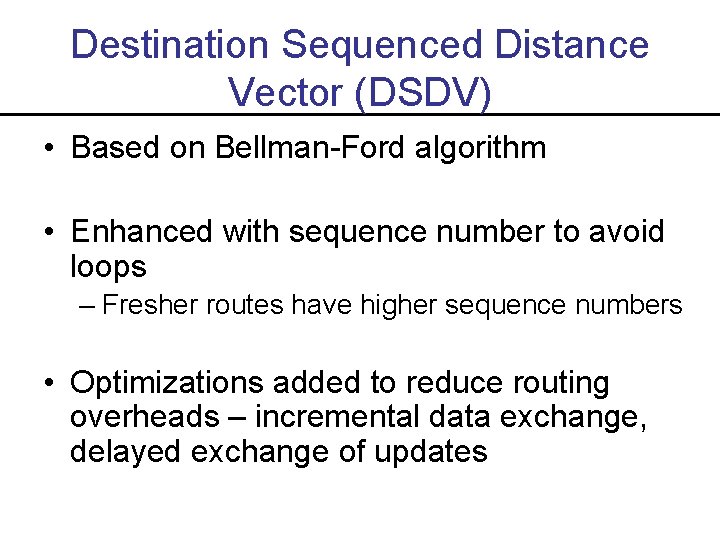
Destination Sequenced Distance Vector (DSDV) • Based on Bellman-Ford algorithm • Enhanced with sequence number to avoid loops – Fresher routes have higher sequence numbers • Optimizations added to reduce routing overheads – incremental data exchange, delayed exchange of updates

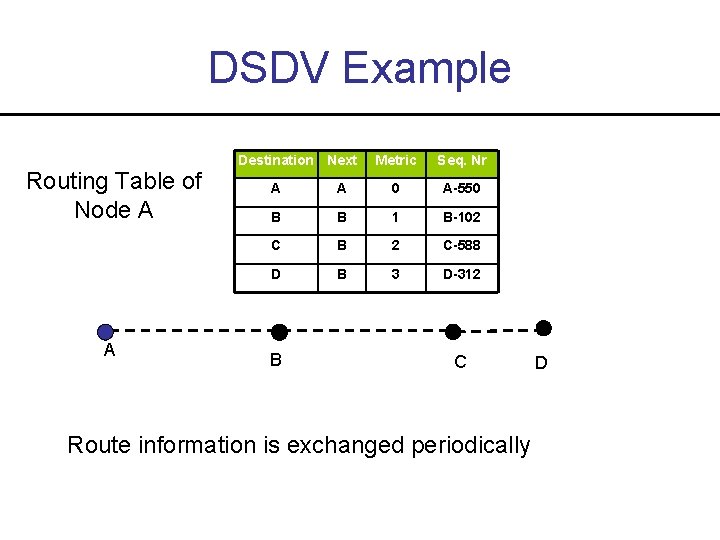
DSDV Example Routing Table of Node A A Destination Next Metric Seq. Nr A A 0 A-550 B B 1 B-102 C B 2 C-588 D B 3 D-312 B C Route information is exchanged periodically D

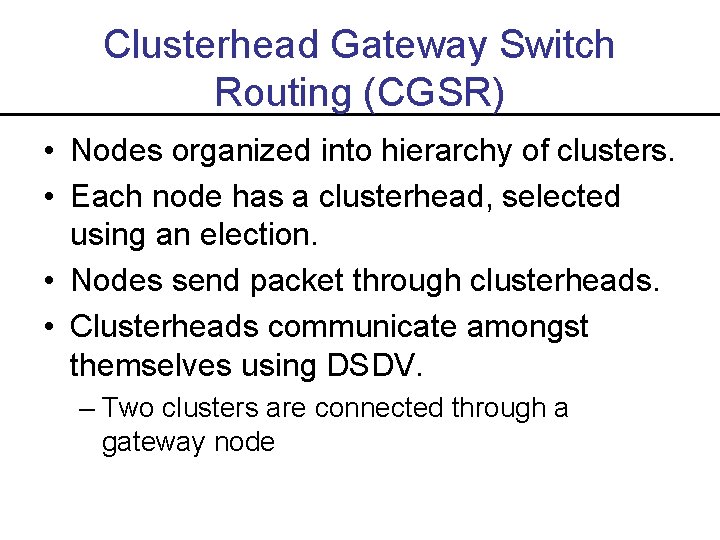
Clusterhead Gateway Switch Routing (CGSR) • Nodes organized into hierarchy of clusters. • Each node has a clusterhead, selected using an election. • Nodes send packet through clusterheads. • Clusterheads communicate amongst themselves using DSDV. – Two clusters are connected through a gateway node

Wireless Routing Protocol (WRP) • Maintains multiple tables – Distance, routing, link-cost, etc. • Link change messages exchanged only between neighbors • Loop freedom using novel algorithm – Uses predecessor hop information

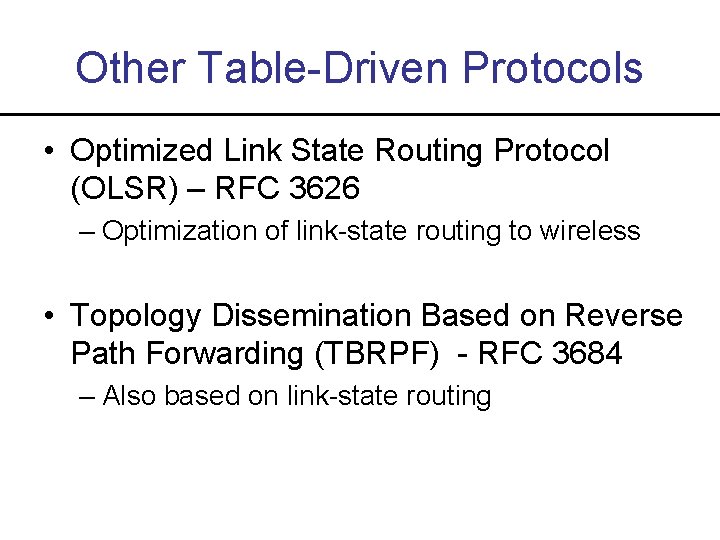
Other Table-Driven Protocols • Optimized Link State Routing Protocol (OLSR) – RFC 3626 – Optimization of link-state routing to wireless • Topology Dissemination Based on Reverse Path Forwarding (TBRPF) - RFC 3684 – Also based on link-state routing

Source-Initiated On-Demand Routing • Create routes only when needed • Routes found using a “route discovery” process • Route maintenance procedure used to repair routes

Ad Hoc On-Demand Distance Vector Routing (AODV) • Now RFC 3561, based on DSDV • Destination sequence numbers provide loop freedom • Source sends Route Request Packet (RREQ) when a route has to be found • Route Reply Packet (RREP) is sent back by destination • Route Error messages update routes

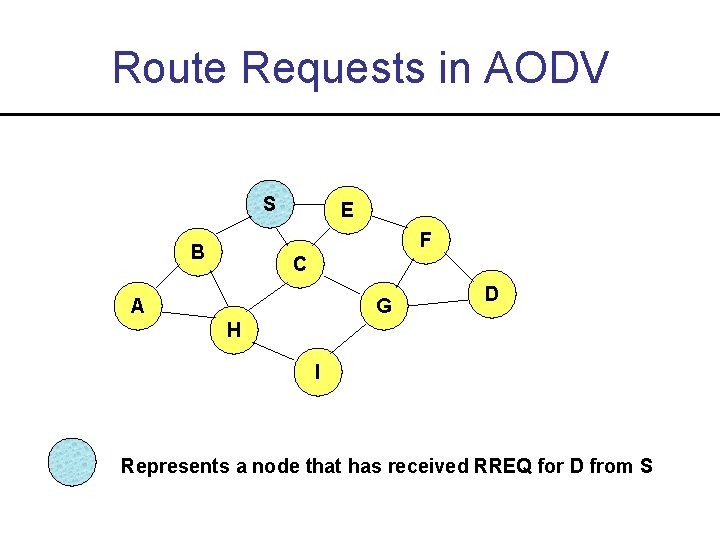
Route Requests in AODV S E F B C A G D H I Represents a node that has received RREQ for D from S

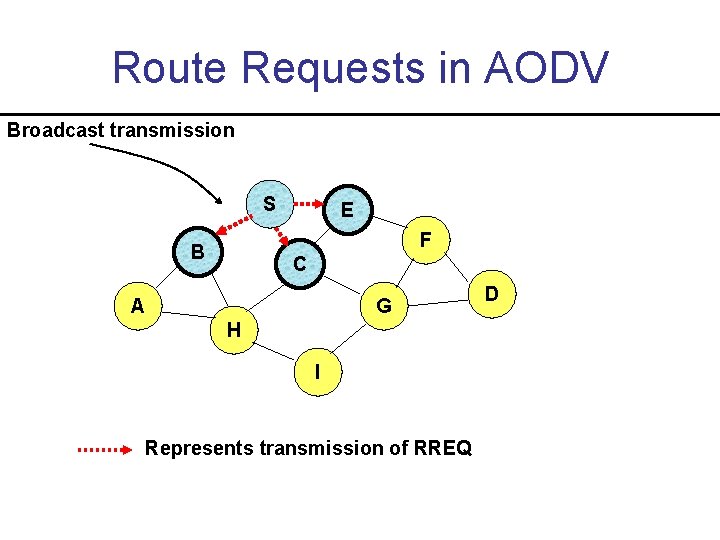
Route Requests in AODV Broadcast transmission S E F B C A G H I Represents transmission of RREQ D

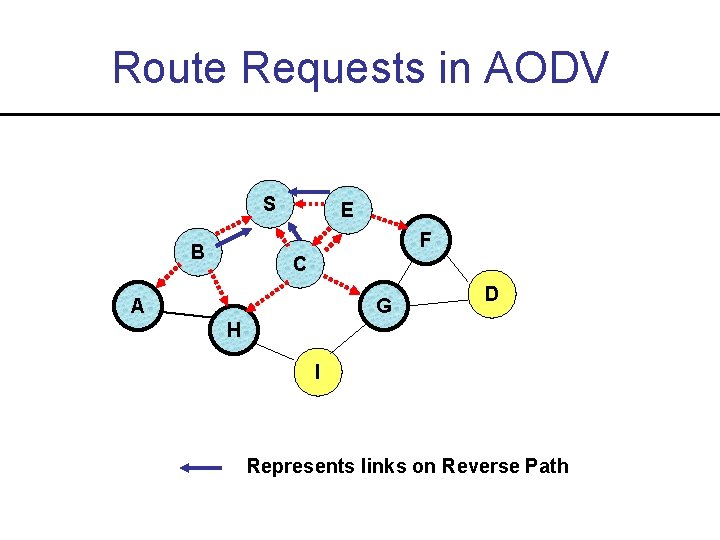
Route Requests in AODV S E F B C A G D H I Represents links on Reverse Path

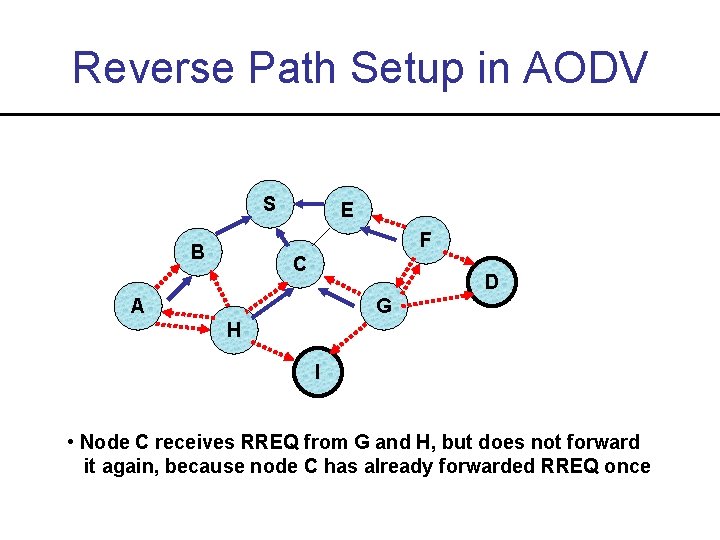
Reverse Path Setup in AODV S E F B C D A G H I • Node C receives RREQ from G and H, but does not forward it again, because node C has already forwarded RREQ once

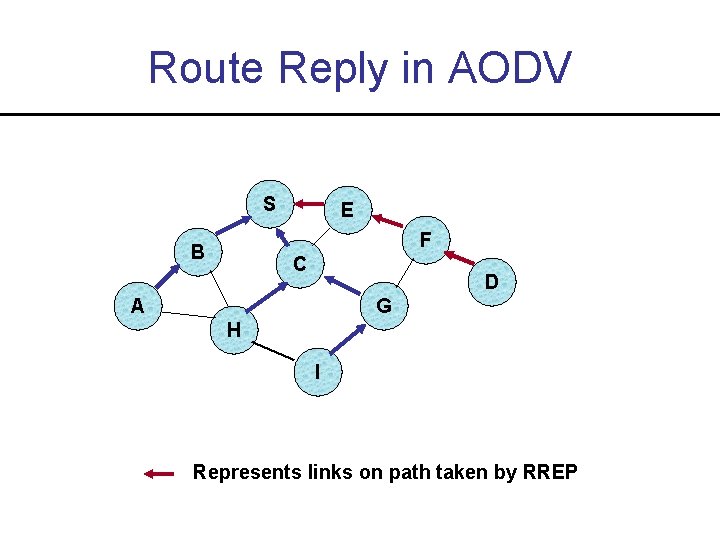
Route Reply in AODV S E F B C D A G H I Represents links on path taken by RREP

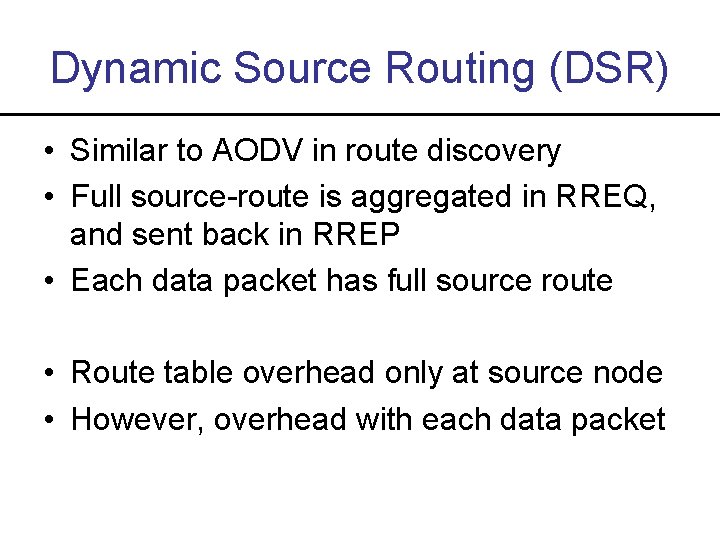
Dynamic Source Routing (DSR) • Similar to AODV in route discovery • Full source-route is aggregated in RREQ, and sent back in RREP • Each data packet has full source route • Route table overhead only at source node • However, overhead with each data packet

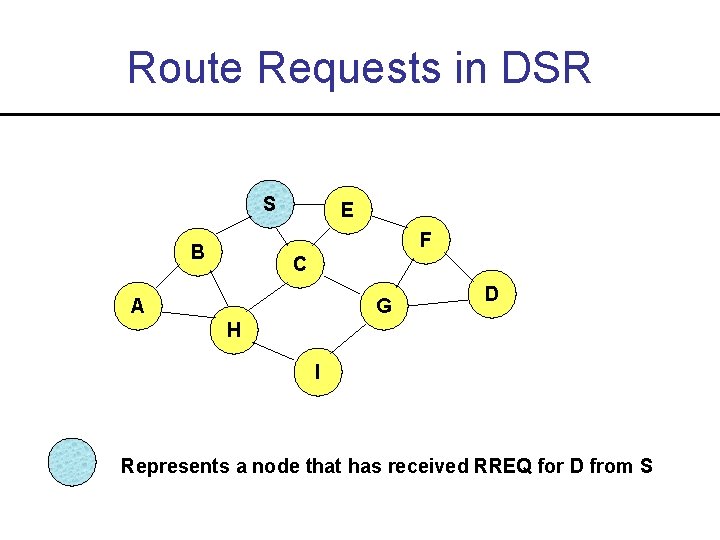
Route Requests in DSR S E F B C A G D H I Represents a node that has received RREQ for D from S

Route Requests in DSR Broadcast transmission S E F B C A G H I Represents transmission of RREQ D

Route Requests in DSR S E F B C A G D H I RREQ keeps a list of nodes on the path from the source

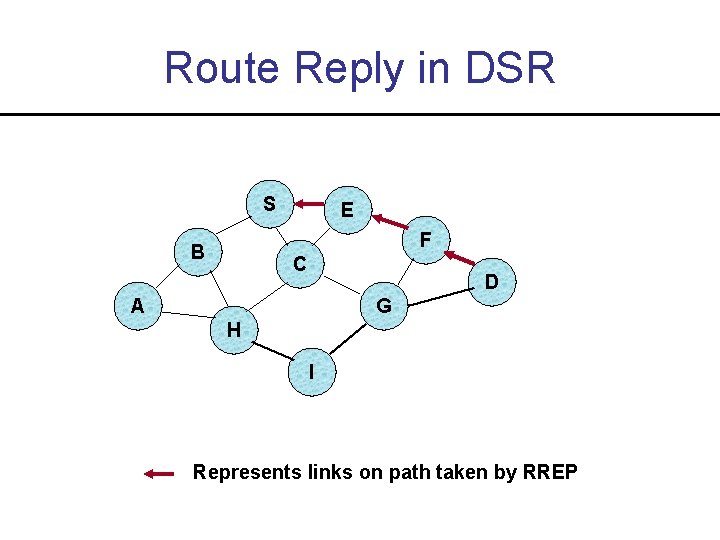
Route Reply in DSR S E F B C D A G H I Represents links on path taken by RREP

Associativity-Based Routing • Defines metric “Degree of Association Stability” – This metric used instead of shortest hop • Nodes with less mobility/better links have higher stability value • DSR-like protocol is used for routing

Signal Stability Routing • Signal strength of links is used as metric • DSR-like routing is used • RREQ is forwarded only if packet is received over a link with good signal strength

Other metrics • Expected Transmission Time (ETT) metric – Easier to compute, and more useful than signal strength • Weighted Cumulative Expected Transmission Time – Better for multi-radio, and asymmetric rate links

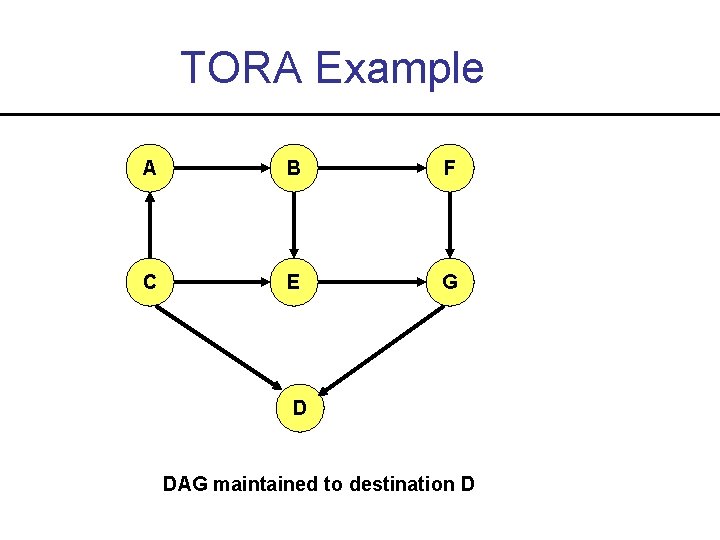
Temporally Ordered Routing Algorithm • Directed Acyclic Graph (DAG) rooted at destination is used to route packets • Link Reversal algorithm used to update DAG (along with notion of “height”) • Algorithm is distributed and loop-free • Recent result - Link reversal takes O(n 2) time and message complexity to stabilize

TORA Example A B F C E G D DAG maintained to destination D

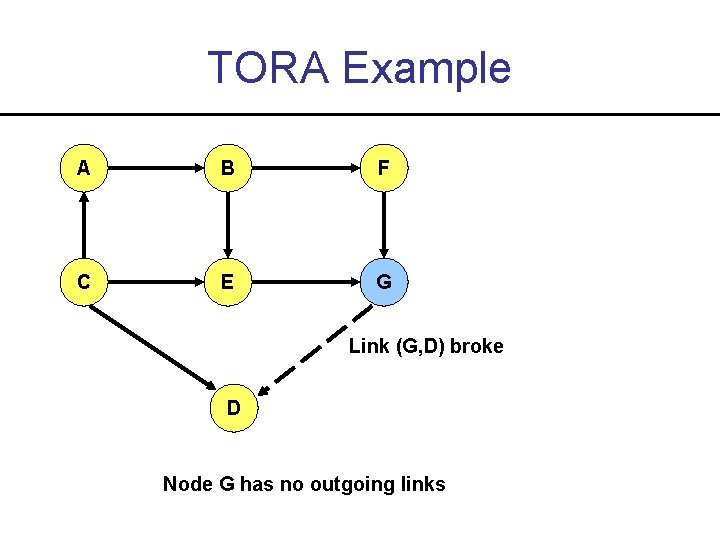
TORA Example A B F C E G Link (G, D) broke D Node G has no outgoing links

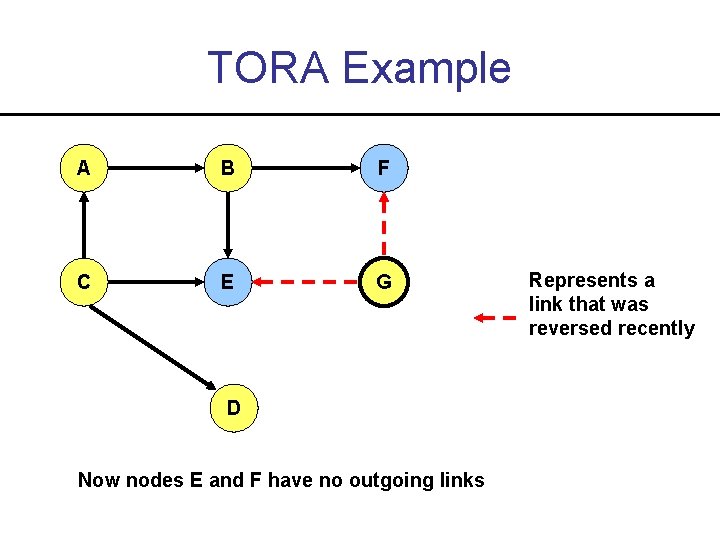
TORA Example A B F C E G D Now nodes E and F have no outgoing links Represents a link that was reversed recently

TORA Example A B F C E G Represents a link that was reversed recently D Nodes E and F do not reverse links from node G Now node B has no outgoing links

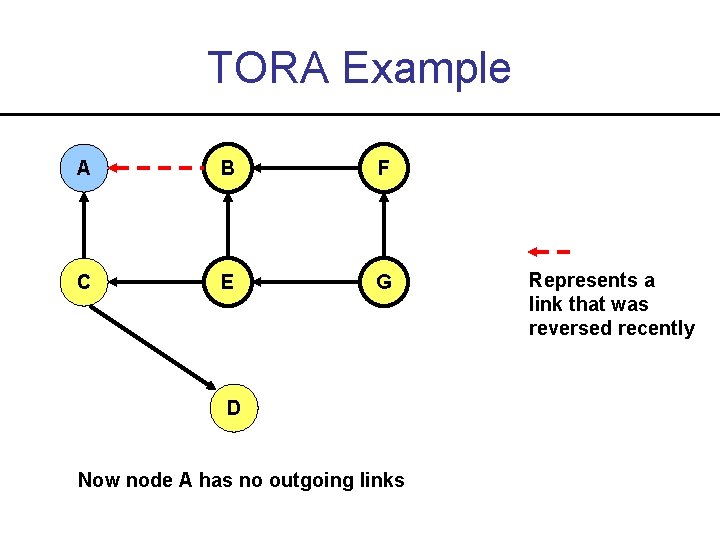
TORA Example A B F C E G D Now node A has no outgoing links Represents a link that was reversed recently

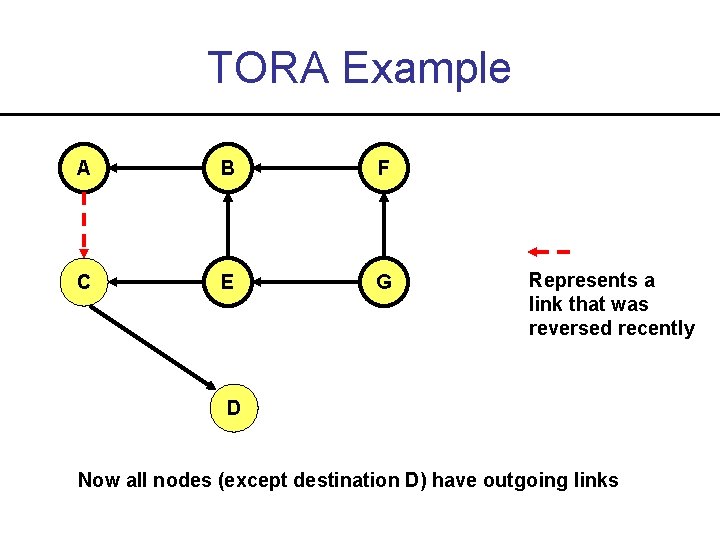
TORA Example A B F C E G Represents a link that was reversed recently D Now all nodes (except destination D) have outgoing links

TORA Example A B F C E G D DAG has been restored with only the destination as a sink

Other routing protocols • Geographic Routing Protocols – Location Aided Routing (LAR) – Distance Routing Effect Algorithm for Mobility (DREAM) – Greedy Perimeter Stateless Routing (GPSR) • Hybrid Routing Protocols – Zone Routing Protocol (ZRP)

Discussion • Proactive routing protocols suitable for high traffic load, low mobility • On-demand routing protocols suitable for low traffic load and/or moderate mobility • With high mobility, flooding of data packets may be the only option

Locating and Bypassing Routing Holes in Sensor Networks Qing Fang, Jie Gao and Leonidas J. Guibas

GPSR • Location of the destination node is assumed to be known • Each node knows location of its neighbors • Each node forwards a packet to its neighbor closest to the destination • If routing holes are found, uses perimeter routing (right-hand rule)

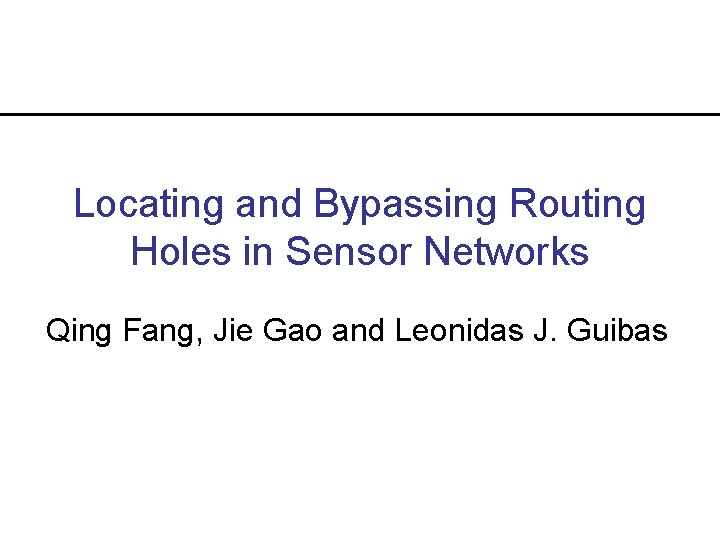
Routing Holes E C F B HOLE J S D A G I H

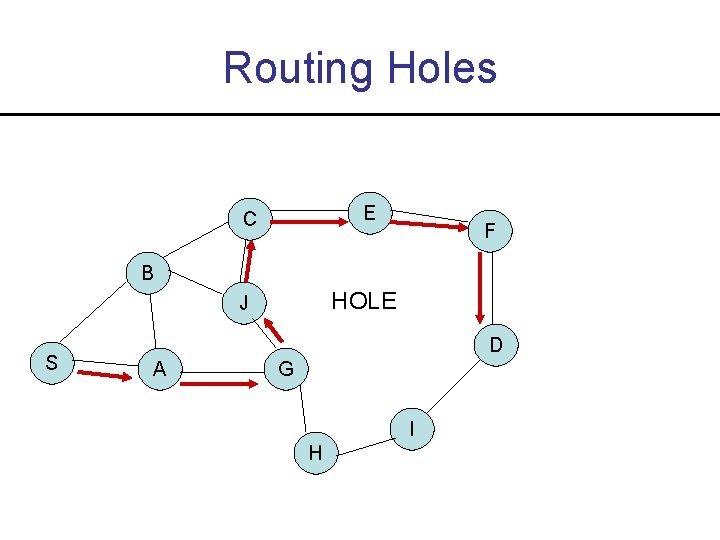
Problem with GPSR Approach • Maintaining perimeter graph expensive, especially in sensor networks • Identifying holes (and boundary around holes) useful for routing around them – Also useful for path migration, information storage • Node where packets get stuck (due to a hole) define the boundary around holes

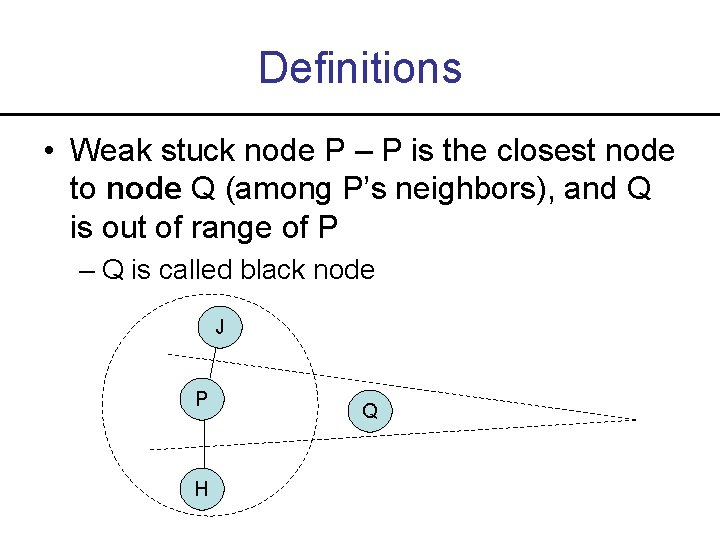
Definitions • Weak stuck node P – P is the closest node to node Q (among P’s neighbors), and Q is out of range of P – Q is called black node J P H Q

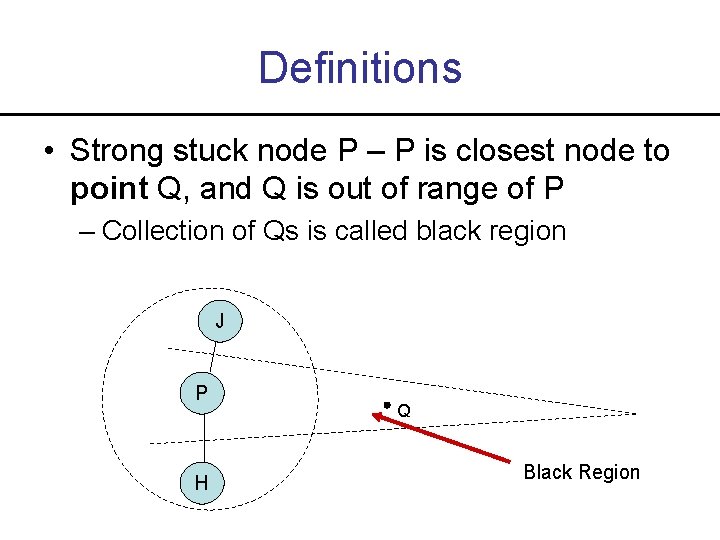
Definitions • Strong stuck node P – P is closest node to point Q, and Q is out of range of P – Collection of Qs is called black region J P H Q Black Region

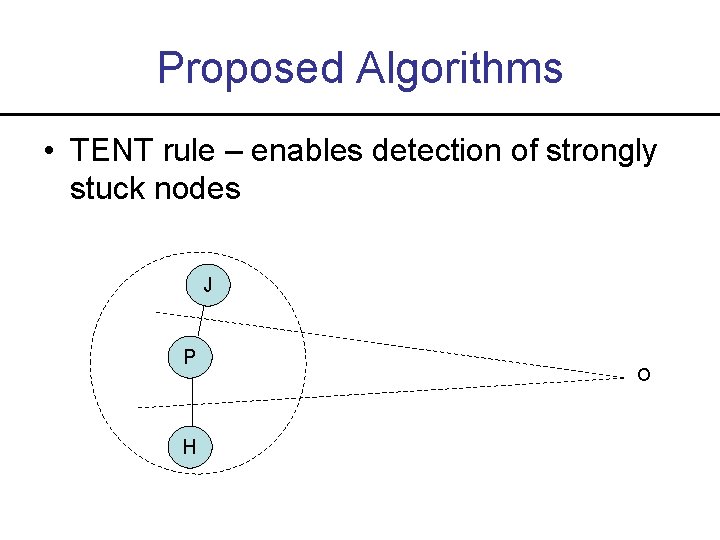
Proposed Algorithms • TENT rule – enables detection of strongly stuck nodes J P H O

Proposed Algorithms • BOUNDHOLE- identifies the boundary of a hole • Start with a stuck node, and sweep counter-clockwise • Move from stuck node to stuck node till the originating node is reached, completing loop

Discussion • Identifying “holes” useful for many applications • Hole identification assumes “circular” radio transmission pattern – Can a similar algorithm be designed using connectivity properties alone?