Agenda SSL Secure Socket Layer TLS Transport Layer













- Slides: 34


Agenda ▣ SSL (Secure Socket Layer) ▣ TLS (Transport Layer Security) P. 2


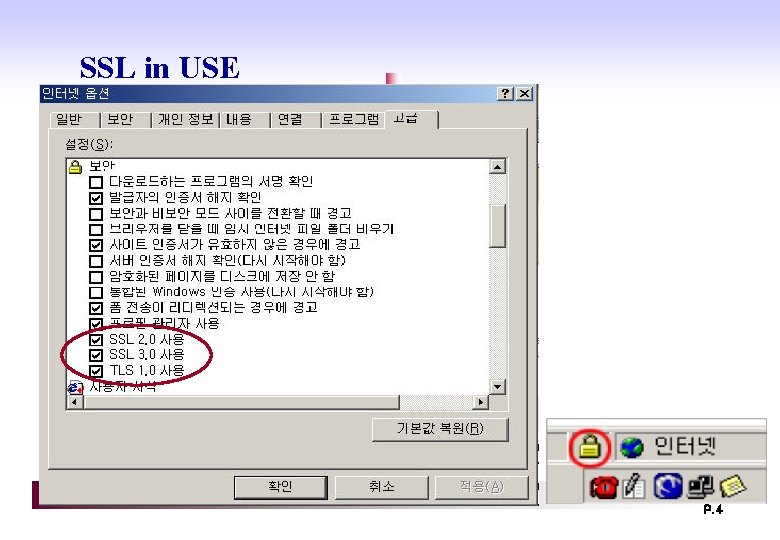
SSL in USE P. 4


SSL Architecture ▣ connection ◈ Suitable type of service ◈ Peer-to-peer relationship ▣ session ◈ By handshake protocol P. 6

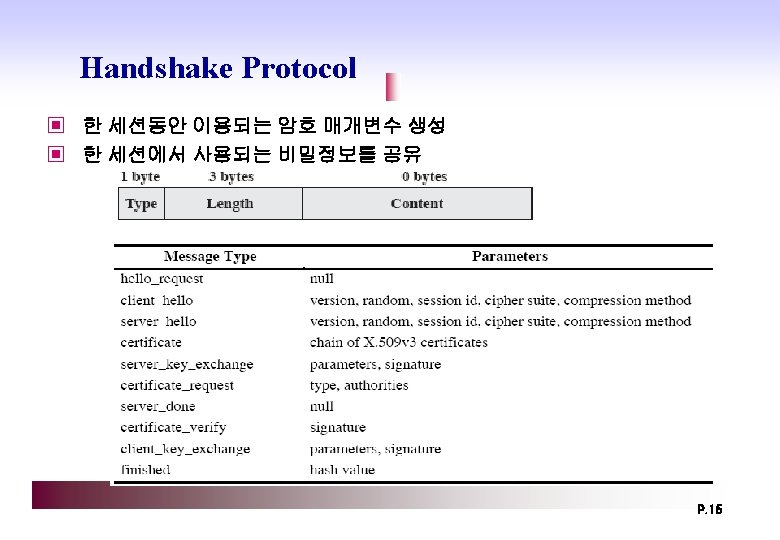
SSL의 구조 ▣ Management of SSL ◈ Handshake Protocol – Parameters (Session key, cryptography algorithm, authentication) ◈ Change Cipher Spec Protocol ◈ Alert Protocol ▣ Real security service ◈ SSL Record Protocol – Data encryption/decryption + Integrity P. 7


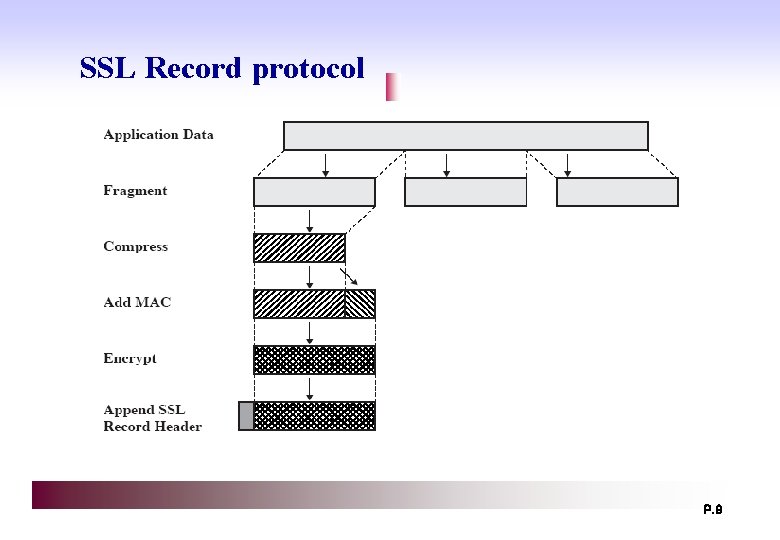
SSL Record protocol P. 9

SSL Record protocol ▣ Confidentiality ◈ using symmetric encryption with a shared secret key defined by Handshake Protocol ◈ IDEA, RC 2 -40, DES, 3 DES, Fortezza, RC 4 -40, RC 4 -128 ◈ message is compressed before encryption ▣ Message integrity ◈ using a MAC with shared secret key ◈ similar to HMAC but with different padding P. 10

SSL Record protocol ▣ Fragmentation ◈ 2^14 byte(16348 byte) or less ▣ Compression ◈ Optional, lossless ◈ No compression in SSLv 3, TLS ▣ MAC ▣ Encryption ◈ IDEA, RC 2 -40, DES, 3 DES, Fortezza, RC 4 -40, RC 4 -128 P. 11

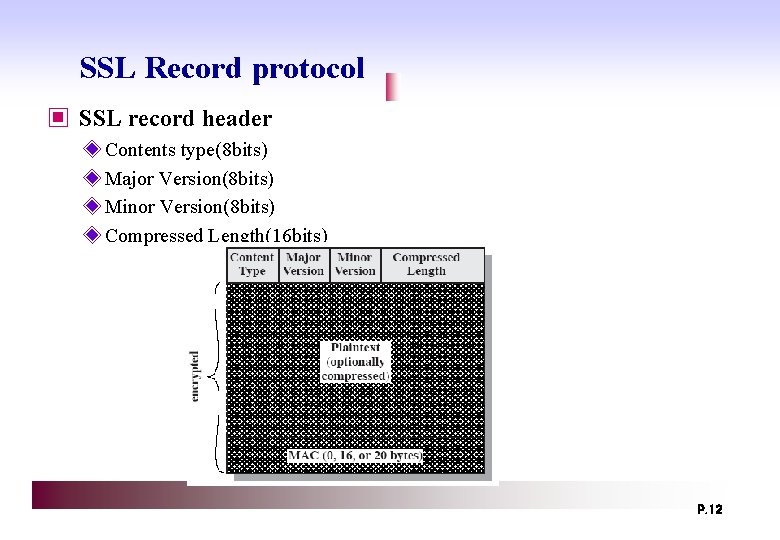
SSL Record protocol ▣ SSL record header ◈ Contents type(8 bits) ◈ Major Version(8 bits) ◈ Minor Version(8 bits) ◈ Compressed Length(16 bits) P. 12

Change Cipher Spec Protocol ▣ one of 3 SSL specific protocols which use the SSL Record protocol ▣ a single message ▣ causes pending state to become current ▣ hence updating the cipher suite in use P. 13

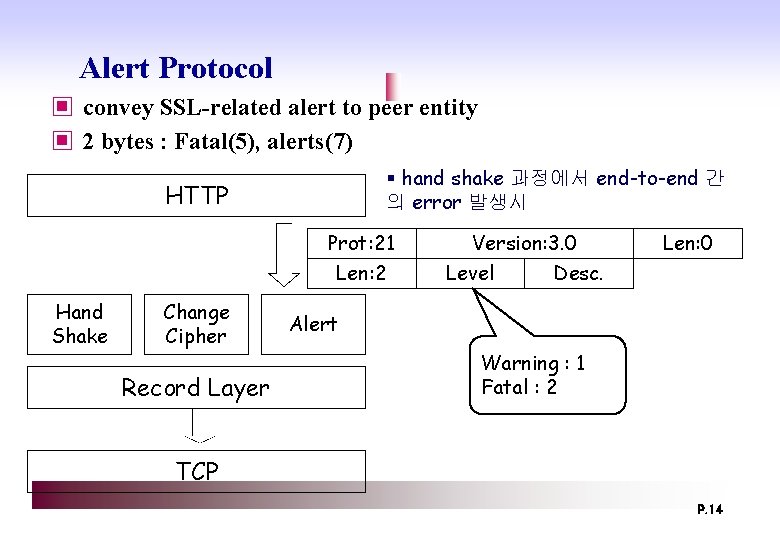
Alert Protocol ▣ convey SSL-related alert to peer entity ▣ 2 bytes : Fatal(5), alerts(7) § hand shake 과정에서 end-to-end 간 의 error 발생시 HTTP Prot: 21 Len: 2 Hand Shake Change Cipher Record Layer Version: 3. 0 Level Desc. Len: 0 Alert Warning : 1 Fatal : 2 TCP P. 14



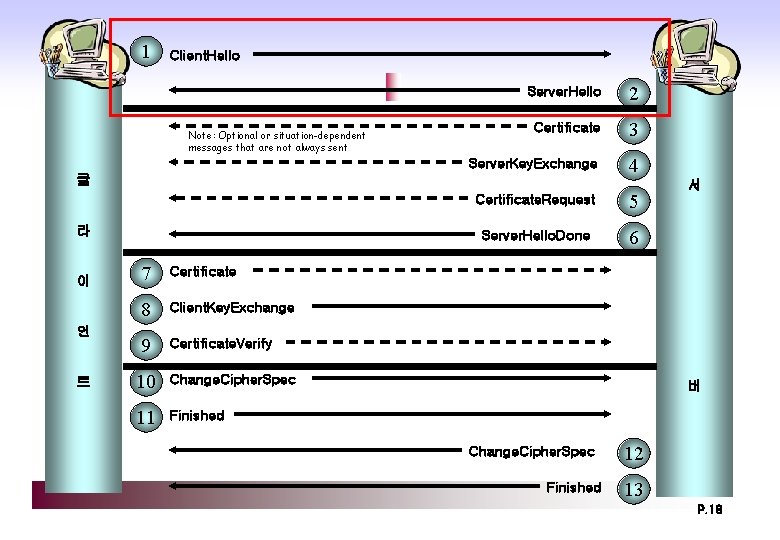
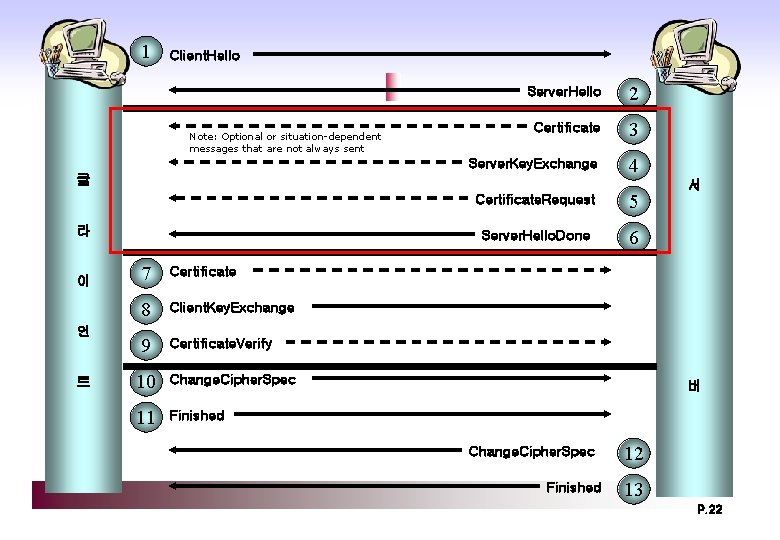
Handshake Protocol Phase 1. Establish Security Capabilities protocol version, session ID, cipher suite, compression method, initial RN Phase 2. Server Authentication and Key Exchange key exchange, request certificate Phase 3. Client Authentication and Key Exchange client sends key exchange, certificate verificaiton Phase 4. Finish change cipher suite, finish P. 17

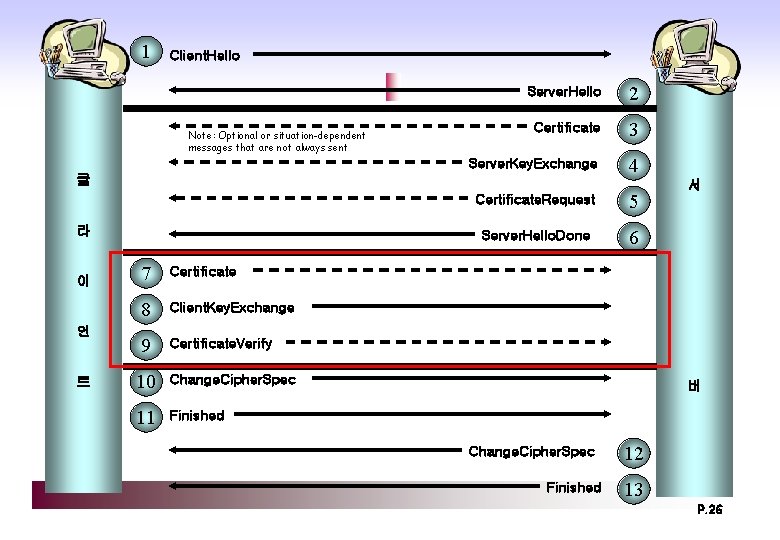
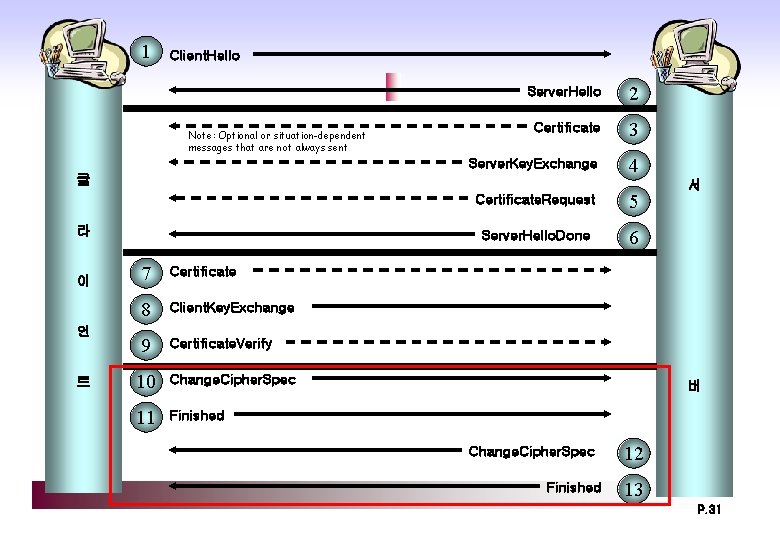
1 Client. Hello Note: Optional or situation-dependent messages that are not always sent Server. Hello 2 Certificate 3 Server. Key. Exchange 4 클 라 이 언 트 7 Certificate 8 Client. Key. Exchange 9 Certificate. Verify 10 Change. Cipher. Spec 11 Finished Certificate. Request 5 Server. Hello. Done 6 서 버 Change. Cipher. Spec Finished 12 13 P. 18

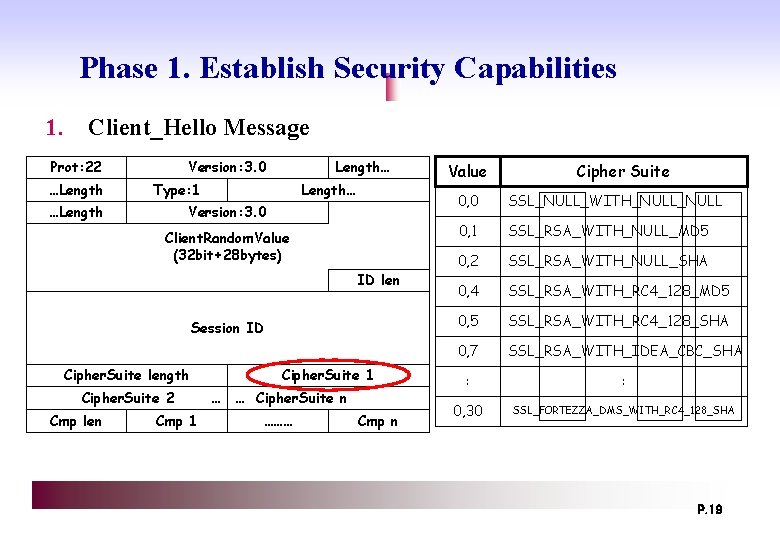
Phase 1. Establish Security Capabilities 1. Client_Hello Message Prot: 22 …Length Version: 3. 0 Length… Type: 1 …Length… Version: 3. 0 Client. Random. Value (32 bit+28 bytes) ID len Session ID Cipher. Suite length Cipher. Suite 2 Cmp len Cmp 1 Cipher. Suite 1 … … Cipher. Suite n ……… Cmp n Value Cipher Suite 0, 0 SSL_NULL_WITH_NULL 0, 1 SSL_RSA_WITH_NULL_MD 5 0, 2 SSL_RSA_WITH_NULL_SHA 0, 4 SSL_RSA_WITH_RC 4_128_MD 5 0, 5 SSL_RSA_WITH_RC 4_128_SHA 0, 7 SSL_RSA_WITH_IDEA_CBC_SHA : : 0, 30 SSL_FORTEZZA_DMS_WITH_RC 4_128_SHA P. 19

Cipher Suite (Netscape 7. 1) P. 20

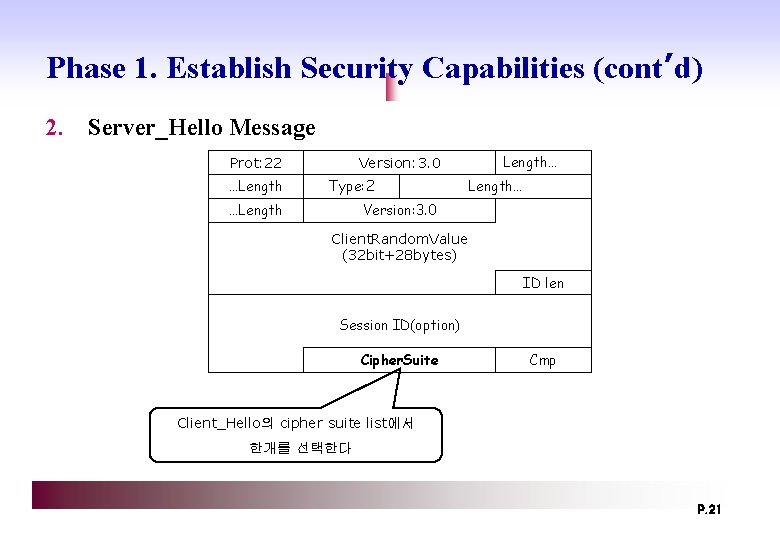
Phase 1. Establish Security Capabilities (cont’d) 2. Server_Hello Message Prot: 22 …Length Version: 3. 0 Type: 2 …Length… Version: 3. 0 Client. Random. Value (32 bit+28 bytes) ID len Session ID(option) Cipher. Suite Cmp Client_Hello의 cipher suite list에서 한개를 선택한다 P. 21

1 Client. Hello Note: Optional or situation-dependent messages that are not always sent Server. Hello 2 Certificate 3 Server. Key. Exchange 4 클 라 이 언 트 7 Certificate 8 Client. Key. Exchange 9 Certificate. Verify 10 Change. Cipher. Spec 11 Finished Certificate. Request 5 Server. Hello. Done 6 서 버 Change. Cipher. Spec Finished 12 13 P. 22

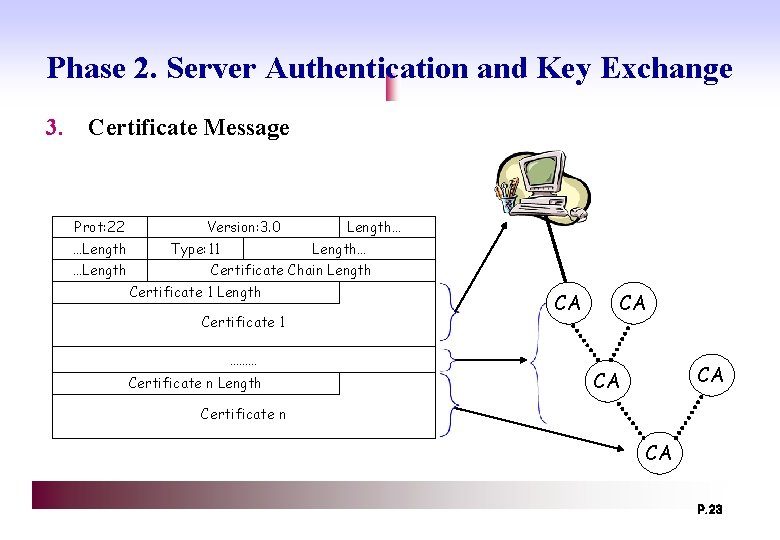
Phase 2. Server Authentication and Key Exchange 3. Certificate Message Prot: 22 …Length Version: 3. 0 Type: 11 Length… Certificate Chain Length Certificate 1 ……… Certificate n Length CA CA Certificate n CA P. 23

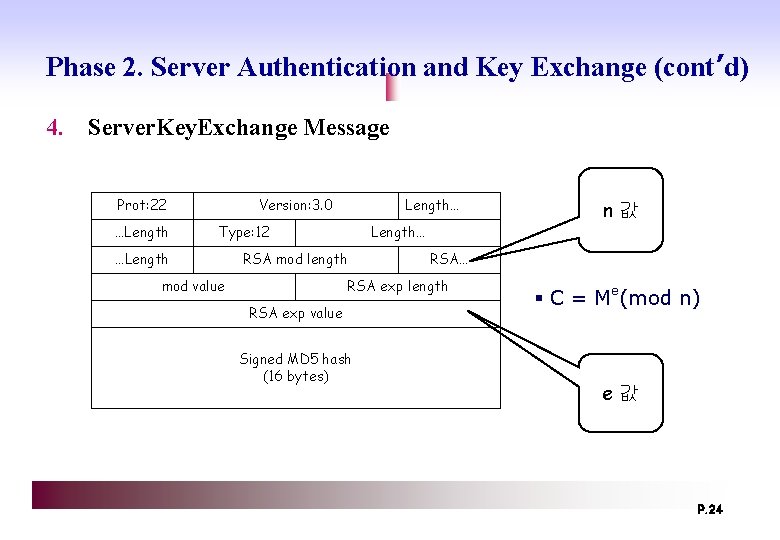
Phase 2. Server Authentication and Key Exchange (cont’d) 4. Server. Key. Exchange Message Prot: 22 …Length Version: 3. 0 Length… Type: 12 …Length… RSA mod length mod value RSA… RSA exp length RSA exp value Signed MD 5 hash (16 bytes) n값 § C = Me(mod n) e값 P. 24

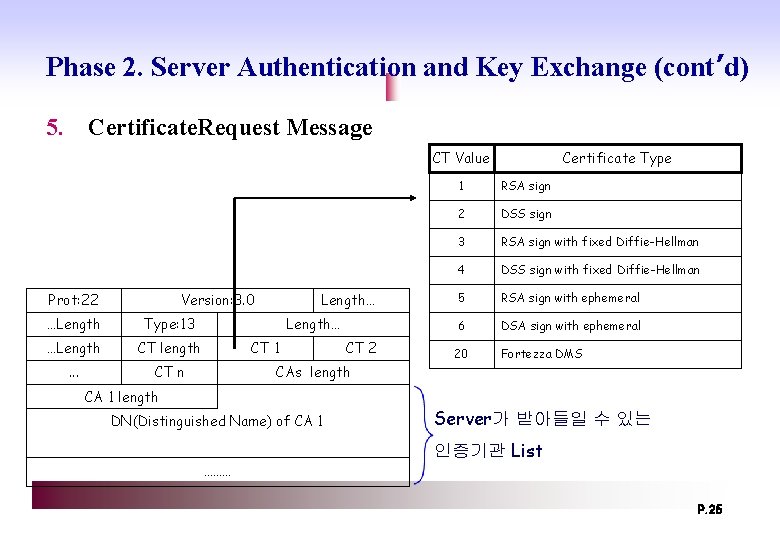
Phase 2. Server Authentication and Key Exchange (cont’d) 5. Certificate. Request Message CT Value Prot: 22 Version: 3. 0 …Length Type: 13 …Length CT length . . . CT n Length… CT 1 CT 2 Certificate Type 1 RSA sign 2 DSS sign 3 RSA sign with fixed Diffie-Hellman 4 DSS sign with fixed Diffie-Hellman 5 RSA sign with ephemeral 6 DSA sign with ephemeral 20 Fortezza DMS CAs length CA 1 length DN(Distinguished Name) of CA 1 ……… Server가 받아들일 수 있는 인증기관 List P. 25

1 Client. Hello Note: Optional or situation-dependent messages that are not always sent Server. Hello 2 Certificate 3 Server. Key. Exchange 4 클 라 이 언 트 7 Certificate 8 Client. Key. Exchange 9 Certificate. Verify 10 Change. Cipher. Spec 11 Finished Certificate. Request 5 Server. Hello. Done 6 서 버 Change. Cipher. Spec Finished 12 13 P. 26

Phase 3. Client Authentication and Key Exchange 7. Certificate Message ◈ If the server has requested a certificate, – The client sends a certificate message P. 27

Phase 3. Client Authentication and Key Exchange (cont’d) 8. Client. Key. Exchange Message Prot: 22 …Length Version: 3. 0 Type: 16 Length… Encrypted Premaster Secret Server의 공개키로 암호화 48 bytes random value P. 28

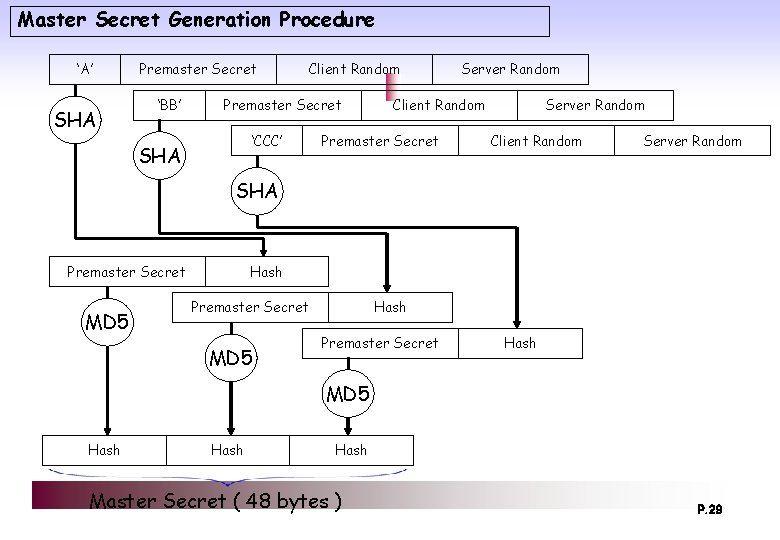
Master Secret Generation Procedure ‘A’ SHA Premaster Secret ‘BB’ Client Random Premaster Secret ‘CCC’ SHA Server Random Client Random Premaster Secret Server Random Client Random Server Random SHA Premaster Secret MD 5 Hash Premaster Secret Hash MD 5 Hash Master Secret ( 48 bytes ) P. 29

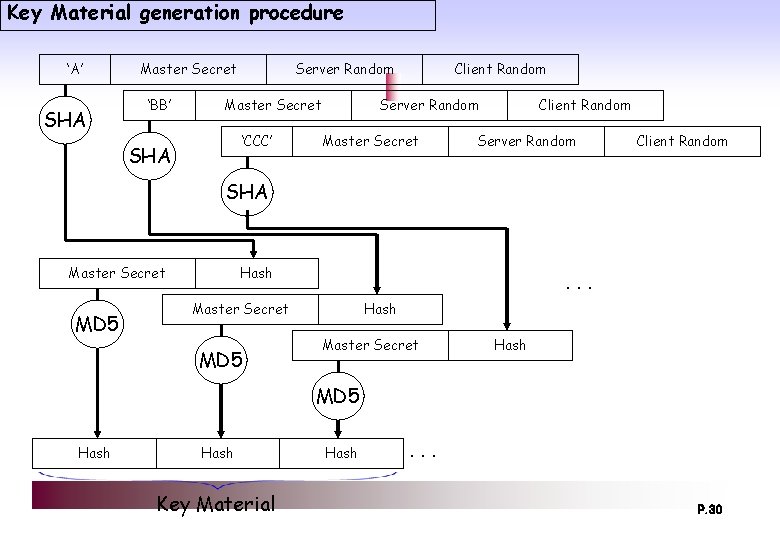
Key Material generation procedure ‘A’ SHA Master Secret ‘BB’ Server Random Master Secret ‘CCC’ SHA Client Random Server Random Master Secret Client Random Server Random Client Random SHA Master Secret MD 5 Hash . . . Master Secret MD 5 Hash Master Secret Hash MD 5 Hash Key Material Hash . . . P. 30

1 Client. Hello Note: Optional or situation-dependent messages that are not always sent Server. Hello 2 Certificate 3 Server. Key. Exchange 4 클 라 이 언 트 7 Certificate 8 Client. Key. Exchange 9 Certificate. Verify 10 Change. Cipher. Spec 11 Finished Certificate. Request 5 Server. Hello. Done 6 서 버 Change. Cipher. Spec Finished 12 13 P. 31

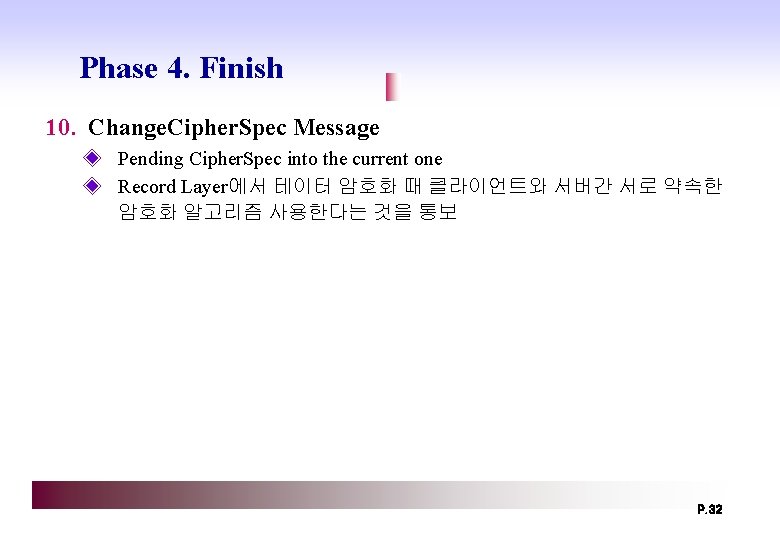
Phase 4. Finish 10. Change. Cipher. Spec Message ◈ Pending Cipher. Spec into the current one ◈ Record Layer에서 테이터 암호화 때 클라이언트와 서버간 서로 약속한 암호화 알고리즘 사용한다는 것을 통보 P. 32

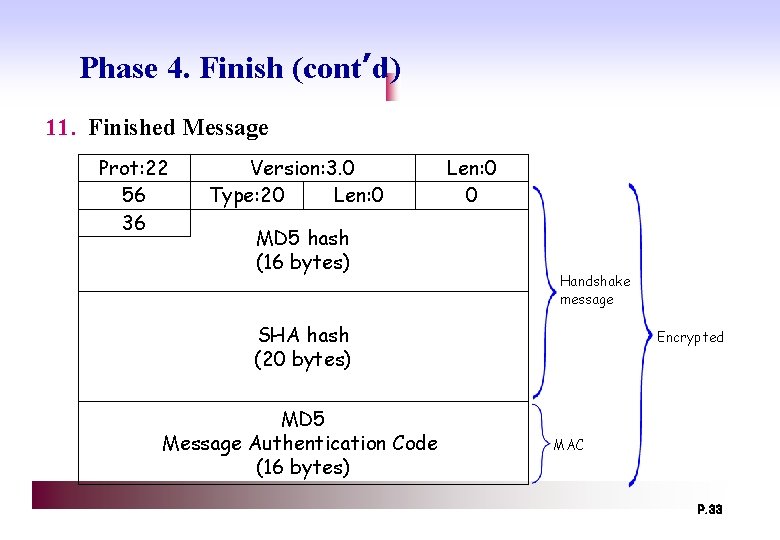
Phase 4. Finish (cont’d) 11. Finished Message Prot: 22 56 36 Version: 3. 0 Type: 20 Len: 0 MD 5 hash (16 bytes) Len: 0 0 Handshake message SHA hash (20 bytes) MD 5 Message Authentication Code (16 bytes) Encrypted MAC P. 33

Transport Layer Security (TLS) ▣ IETF standard RFC 4346 similar to SSLv 3 ▣ with minor differences ◈ in record format version number – Major : 3, minor : 1 ◈ uses HMAC for MAC ◈ has additional alert codes ◈ some changes in supported ciphers – With except of Fortezza ◈ changes in certificate negotiations ◈ changes in use of padding(1, 9, 17…. , 249 bytes) P. 34