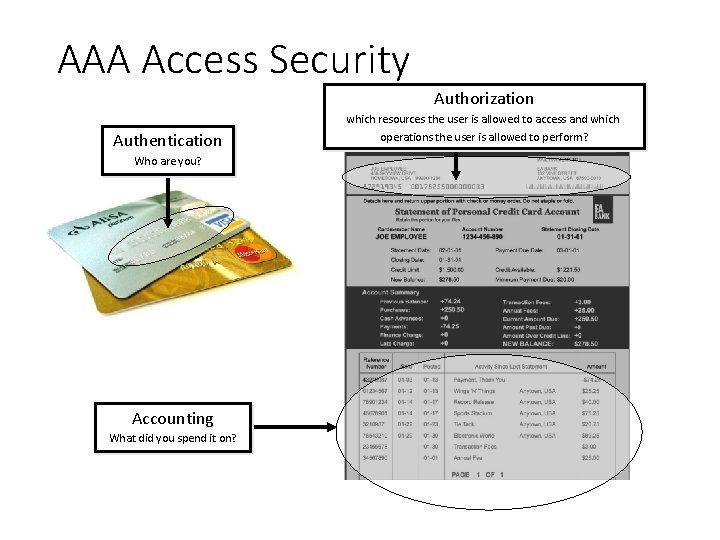
AAA in Cisco IOS AAA Access Security Authorization

















- Slides: 42

AAA in Cisco IOS

AAA Access Security Authorization Authentication Who are you? Accounting What did you spend it on? which resources the user is allowed to access and which operations the user is allowed to perform?

Authentication – Password-Only Method Internet User Access Verification Password: cisco 12 % Bad passwords R 1(config)# line vty 0 4 R 1(config-line)# password cisco R 1(config-line)# login • • Uses a login and password combination on access lines Easiest to implement, but most unsecure method Vulnerable to brute-force attacks Provides no accountability

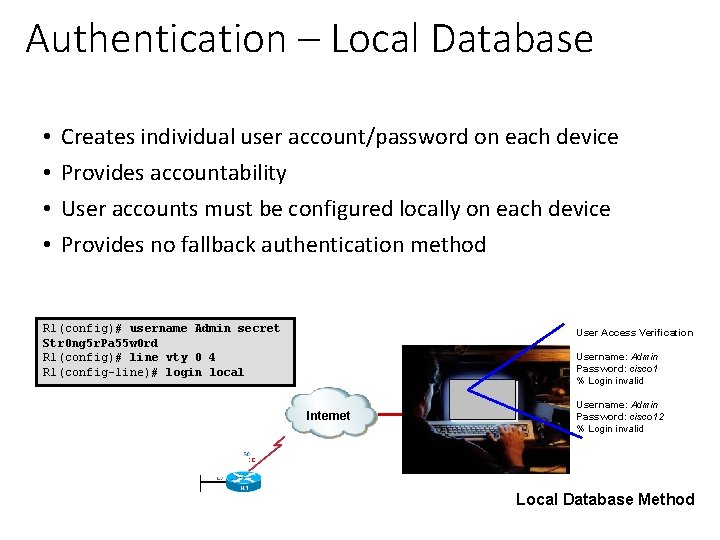
Authentication – Local Database • • Creates individual user account/password on each device Provides accountability User accounts must be configured locally on each device Provides no fallback authentication method R 1(config)# username Admin secret Str 0 ng 5 r. Pa 55 w 0 rd R 1(config)# line vty 0 4 R 1(config-line)# login local User Access Verification Username: Admin Password: cisco 1 % Login invalid Internet Username: Admin Password: cisco 12 % Login invalid Local Database Method


Local Versus Remote Access Local Access Remote Access LAN 2 R 1 LAN 1 Internet Firewall R 2 Internet LAN 3 Console Port Administrator Requires a direct connection to a console port using a computer running terminal emulation software Management LAN Administration Host Uses Telnet, SSH HTTP or SNMP connections to the router from a computer Logging Host

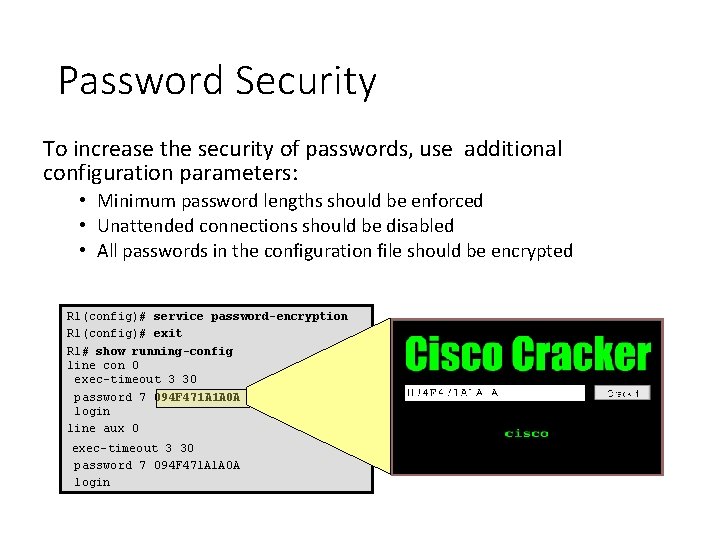
Password Security To increase the security of passwords, use additional configuration parameters: • Minimum password lengths should be enforced • Unattended connections should be disabled • All passwords in the configuration file should be encrypted R 1(config)# service password-encryption R 1(config)# exit R 1# show running-config line con 0 exec-timeout 3 30 password 7 094 F 471 A 1 A 0 A login line aux 0 exec-timeout 3 30 password 7 094 F 471 A 1 A 0 A login

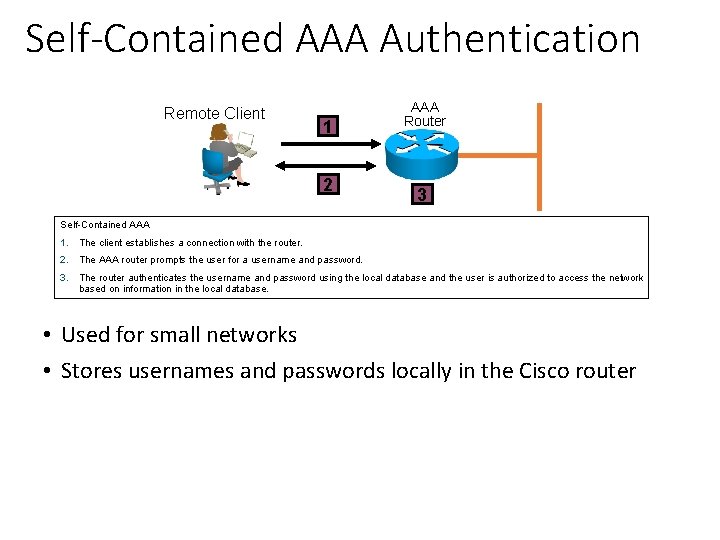
Self-Contained AAA Authentication Remote Client 1 2 AAA Router 3 Self-Contained AAA 1. The client establishes a connection with the router. 2. The AAA router prompts the user for a username and password. 3. The router authenticates the username and password using the local database and the user is authorized to access the network based on information in the local database. • Used for small networks • Stores usernames and passwords locally in the Cisco router

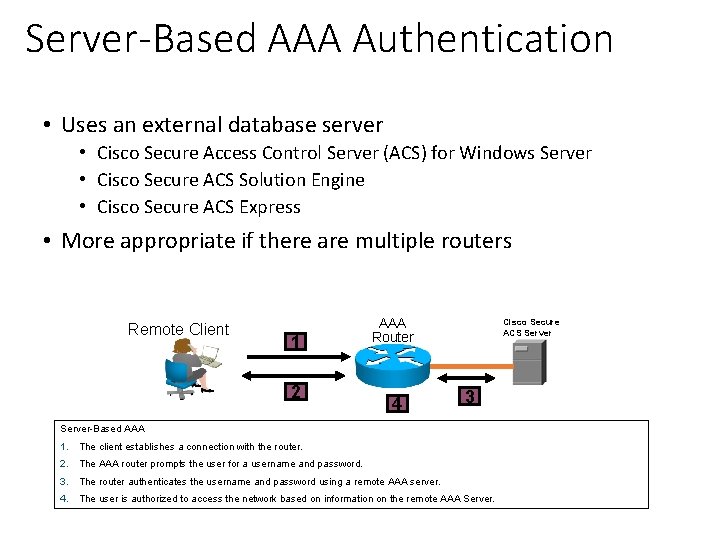
Server-Based AAA Authentication • Uses an external database server • Cisco Secure Access Control Server (ACS) for Windows Server • Cisco Secure ACS Solution Engine • Cisco Secure ACS Express • More appropriate if there are multiple routers Remote Client 1 2 AAA Router 4 Cisco Secure ACS Server 3 Server-Based AAA 1. The client establishes a connection with the router. 2. The AAA router prompts the user for a username and password. 3. The router authenticates the username and password using a remote AAA server. 4. The user is authorized to access the network based on information on the remote AAA Server.


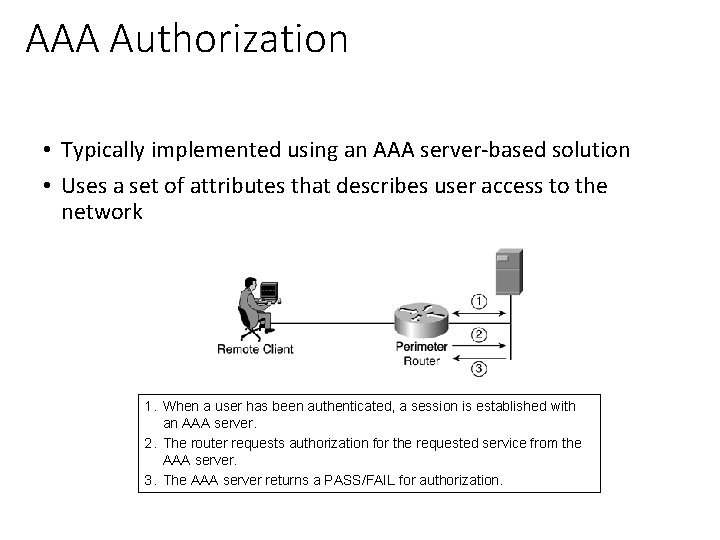
AAA Authorization • Typically implemented using an AAA server-based solution • Uses a set of attributes that describes user access to the network 1. When a user has been authenticated, a session is established with an AAA server. 2. The router requests authorization for the requested service from the AAA server. 3. The AAA server returns a PASS/FAIL for authorization.

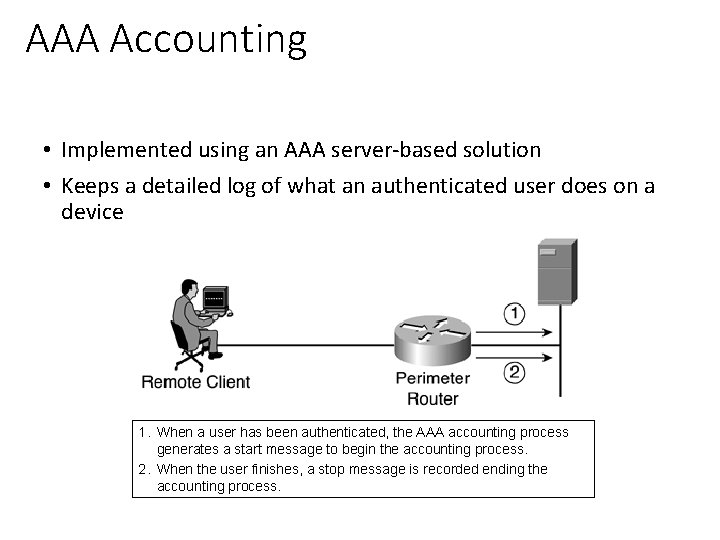
AAA Accounting • Implemented using an AAA server-based solution • Keeps a detailed log of what an authenticated user does on a device 1. When a user has been authenticated, the AAA accounting process generates a start message to begin the accounting process. 2. When the user finishes, a stop message is recorded ending the accounting process.

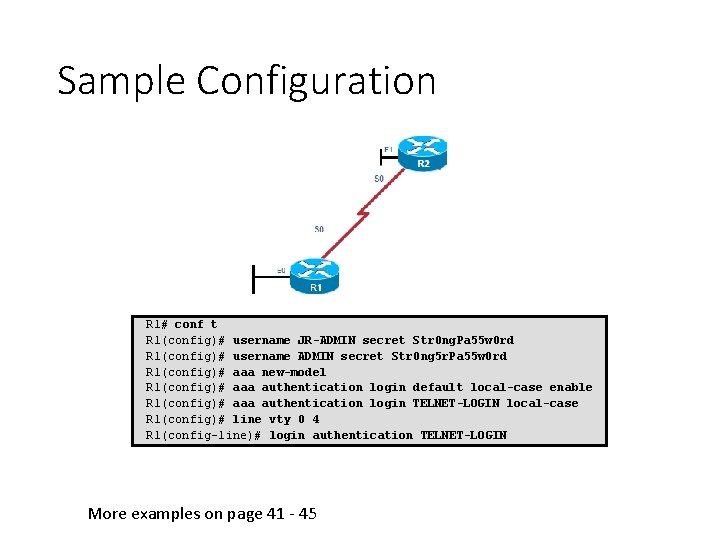
Sample Configuration R 1# conf t R 1(config)# username JR-ADMIN secret Str 0 ng. Pa 55 w 0 rd R 1(config)# username ADMIN secret Str 0 ng 5 r. Pa 55 w 0 rd R 1(config)# aaa new-model R 1(config)# aaa authentication login default local-case enable R 1(config)# aaa authentication login TELNET-LOGIN local-case R 1(config)# line vty 0 4 R 1(config-line)# login authentication TELNET-LOGIN More examples on page 41 - 45

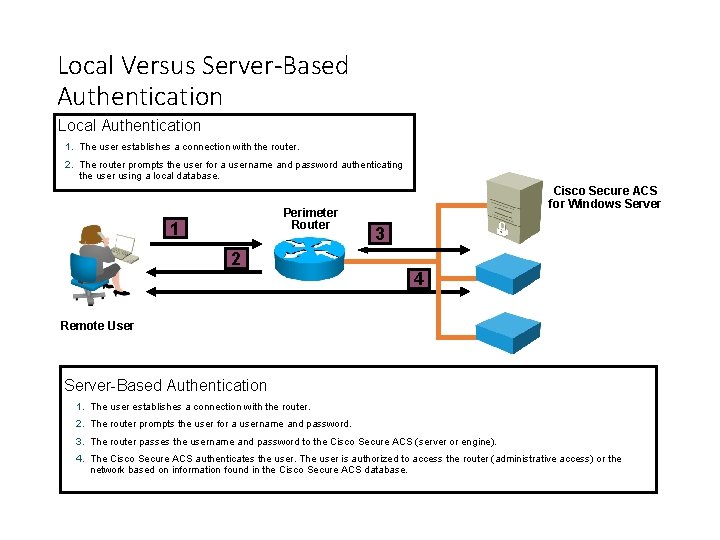
Local Versus Server-Based Authentication Local Authentication 1. The user establishes a connection with the router. 2. The router prompts the user for a username and password authenticating the user using a local database. Perimeter Router 1 Cisco Secure ACS for Windows Server 3 2 4 Remote User Server-Based Authentication 1. The user establishes a connection with the router. 2. The router prompts the user for a username and password. 3. The router passes the username and password to the Cisco Secure ACS (server or engine). 4. The Cisco Secure ACS authenticates the user. The user is authorized to access the router (administrative access) or the network based on information found in the Cisco Secure ACS database.

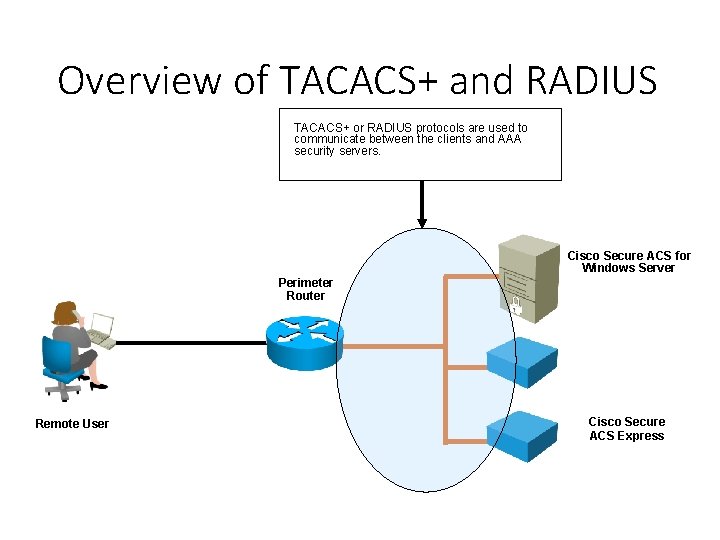
Overview of TACACS+ and RADIUS TACACS+ or RADIUS protocols are used to communicate between the clients and AAA security servers. Cisco Secure ACS for Windows Server Perimeter Router Remote User Cisco Secure ACS Express


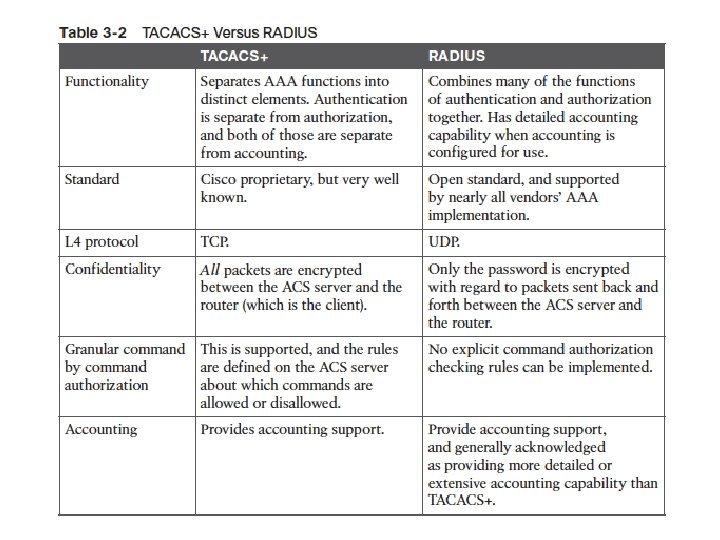
RADIUS vs TACACS+ (Things to know) • Traditionally, and in common practice, TACACS+ is used to authenticate and authorize administrators for command line access. • RADIUS is typically used to authenticate and authorize end users who just want their packets to go through a network device. • Why?

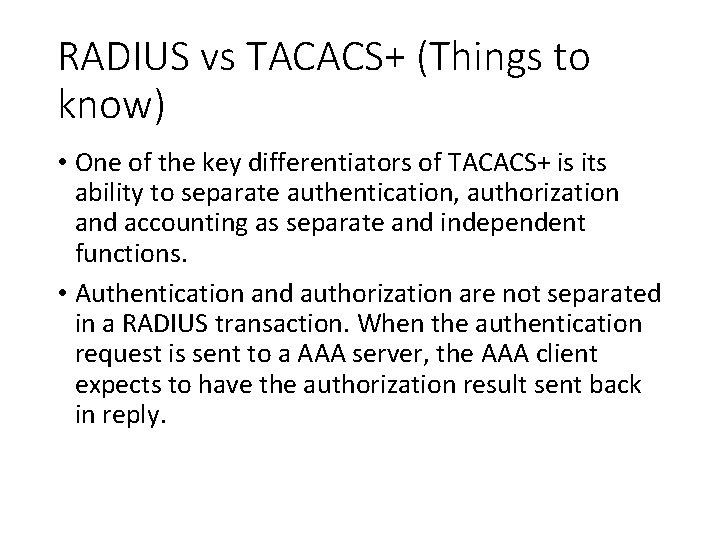
RADIUS vs TACACS+ (Things to know) • One of the key differentiators of TACACS+ is its ability to separate authentication, authorization and accounting as separate and independent functions. • Authentication and authorization are not separated in a RADIUS transaction. When the authentication request is sent to a AAA server, the AAA client expects to have the authorization result sent back in reply.

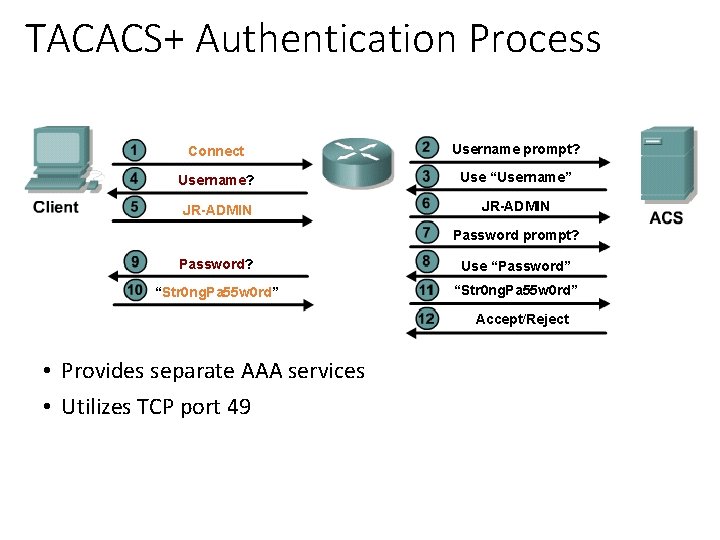
TACACS+ Authentication Process Connect Username prompt? Username? Use “Username” JR-ADMIN Password prompt? Password? Use “Password” “Str 0 ng. Pa 55 w 0 rd” Accept/Reject • Provides separate AAA services • Utilizes TCP port 49

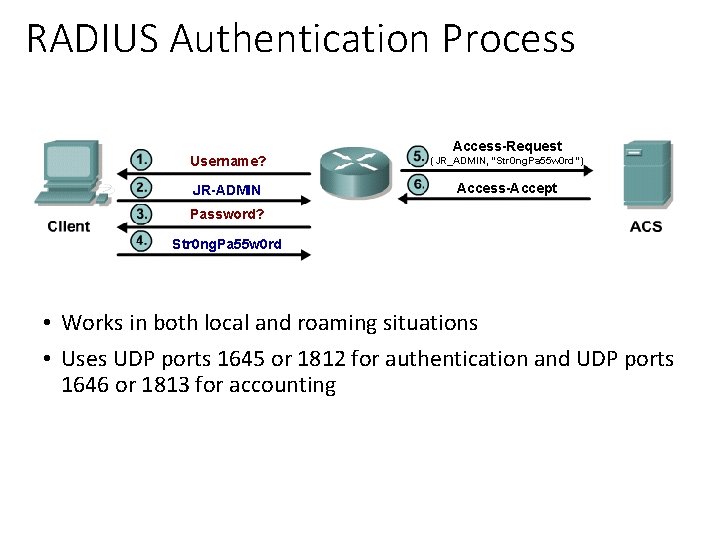
RADIUS Authentication Process Access-Request Username? (JR_ADMIN, “Str 0 ng. Pa 55 w 0 rd”) JR-ADMIN Access-Accept Password? Str 0 ng. Pa 55 w 0 rd • Works in both local and roaming situations • Uses UDP ports 1645 or 1812 for authentication and UDP ports 1646 or 1813 for accounting

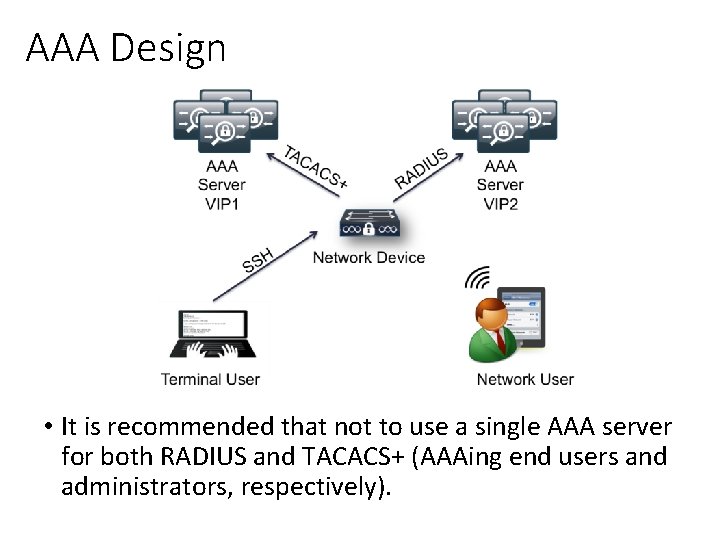
AAA Design • It is recommended that not to use a single AAA server for both RADIUS and TACACS+ (AAAing end users and administrators, respectively).

Why would we design this way? • Because we certainly don't want a network user, say John Chambers (CEO of Cisco Systems) trying to logon to his wireless network and the RADIUS server not answering before it times out - due to being so busy crunching data related to "is Aaron allowed to type show ? " and "is Aaron allowed to type show interface ? ", etc. . You could theoretically cause a network denial of service (Do. S) because of all the chattering & constant authentication requests coming from Device Admin AAA.

Cisco Secure ACS Benefits • Extends access security by combining authentication, user access, and administrator access with policy control • Allows greater flexibility and mobility, increased security, and user-productivity gains • Enforces a uniform security policy for all users • Reduces the administrative and management efforts

What is ISE? • A product called Identity Services Engine (ISE) is an identity and access control policy platform that can validate • a computer meets company’s security policy related to virus definition files, service pack levels, etc. before allowing the device on the network. • ISE leverages many AAA-like feature, but is not a 100 percent replacement for ACS. • For the near future, customers who want the features of ISE will likely use ACS for AAA and use ISE for posturing and policy-compliance checking. • Note: Security posture = overall security plan

Installation Options Cisco Secure ACS for Windows can be installed on: - Windows 2000 Server with Service Pack 4 - Windows 2000 Advanced Server with Service Pack 4 - Windows Server 2003 Standard Edition - Windows Server 2003 Enterprise Edition Cisco Secure ACS Solution Engine - A highly scalable dedicated platform that serves as a highperformance ACS - 1 RU, rack-mountable - Preinstalled with a security-hardened Windows software, Cisco Secure ACS software - Support for more than 350 users Cisco Secure ACS Express 5. 0 - Entry-level ACS with simplified feature set - Support for up to 50 AAA device and up to 350 unique user ID logins in a 24 -hour period

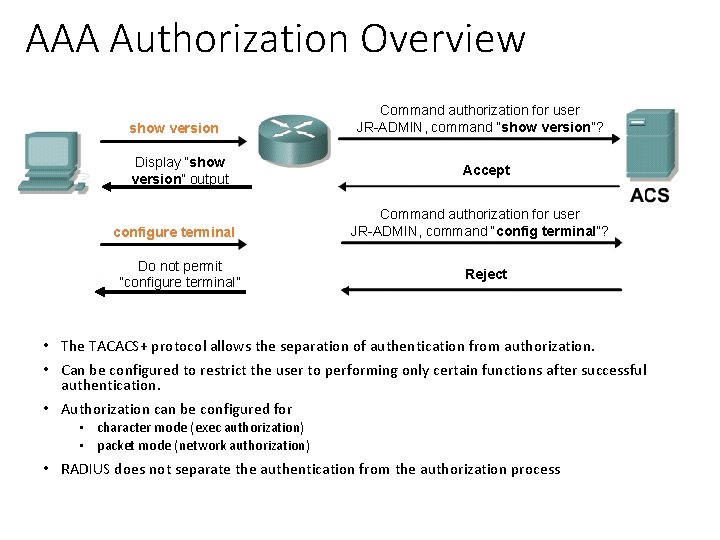
AAA Authorization Overview show version Display “show version” output configure terminal Do not permit “configure terminal” Command authorization for user JR-ADMIN, command “show version”? Accept Command authorization for user JR-ADMIN, command “config terminal”? Reject • The TACACS+ protocol allows the separation of authentication from authorization. • Can be configured to restrict the user to performing only certain functions after successful authentication. • Authorization can be configured for • character mode (exec authorization) • packet mode (network authorization) • RADIUS does not separate the authentication from the authorization process

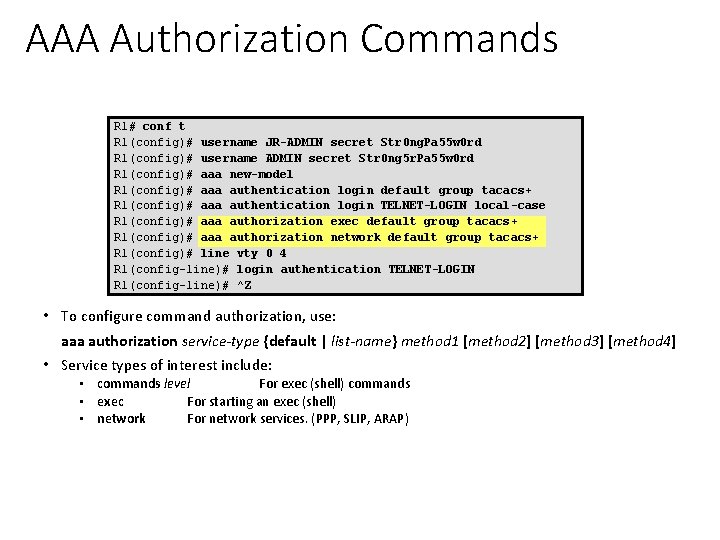
AAA Authorization Commands R 1# conf t R 1(config)# username JR-ADMIN secret Str 0 ng. Pa 55 w 0 rd R 1(config)# username ADMIN secret Str 0 ng 5 r. Pa 55 w 0 rd R 1(config)# aaa new-model R 1(config)# aaa authentication login default group tacacs+ R 1(config)# aaa authentication login TELNET-LOGIN local-case R 1(config)# aaa authorization exec default group tacacs+ R 1(config)# aaa authorization network default group tacacs+ R 1(config)# line vty 0 4 R 1(config-line)# login authentication TELNET-LOGIN R 1(config-line)# ^Z • To configure command authorization, use: aaa authorization service-type {default | list-name} method 1 [method 2] [method 3] [method 4] • Service types of interest include: • commands level For exec (shell) commands • exec For starting an exec (shell) • network For network services. (PPP, SLIP, ARAP)

AAA Accounting Overview • Provides the ability to track usage, such as dial-in access; the ability to log the data gathered to a database; and the ability to produce reports on the data gathered • To configure AAA accounting using named method lists: aaa accounting {system | network | exec | connection | commands level} {default | list-name} {start-stop | waitstart | stop-only | none} [method 1 [method 2]] • Supports six different types of accounting: network, connection, exec, system, commands level, and resource.

AAA Accounting Commands R 1# conf t R 1(config)# username JR-ADMIN secret Str 0 ng. Pa 55 w 0 rd R 1(config)# username ADMIN secret Str 0 ng 5 r. Pa 55 w 0 rd R 1(config)# aaa new-model R 1(config)# aaa authentication login default group tacacs+ R 1(config)# aaa authentication login TELNET-LOGIN local-case R 1(config)# aaa authorization exec group tacacs+ R 1(config)# aaa authorization network group tacacs+ R 1(config)# aaa accounting exec start-stop group tacacs+ R 1(config)# aaa accounting network start-stop group tacacs+ R 1(config)# line vty 0 4 R 1(config-line)# login authentication TELNET-LOGIN R 1(config-line)# ^Z • aaa accounting exec default start-stop group tacacs+ Defines a AAA accounting policy that uses TACACS+ for logging both start and stop records for user EXEC terminal sessions. • aaa accounting network default start-stop group tacacs+ Defines a AAA accounting policy that uses TACACS+ for logging both start and stop records for all network-related service requests.

Troubleshoot Router-to-ACS Server Interactions • Access control filtering that is denying ICMP, so ping is not successful. • ACS server may be physically powered off. • Cable may be disconnected. • ACS may be connected to a wrong switch port or is in the wrong VLAN. • A network may not be fully converged, routing issues!!! • See page 60 for troubleshooting examples

Bring Your Own Device (BYOD)

BYOD Fundamentals • The concept of BYOD brings with it the constant challenge for network and security administrators, engineers, and management. • This challenge is to provide seamless connectivity for users bringing their own network-connected devices while also maintaining an appropriate security posture. • The organization must provide a level of security that meets the organization’s security policies and ensures that network devices, systems, and data do not get compromised through the proliferation of vulnerable devices starting with the devices brought in by employees from “the outside. ” • For end users, it is no longer a “nice to have” VPN, but legitimately need to be able to use their devices to connect to and from any network-enabled location in the world

Reasons that Drive BYOD Solutions • Wide variety of consumer devices: It seems like every day there is a new vendor, a new device, or a new version of an existing device that requires connectivity to the Internet. • Blurred lines between work and play: The term 9 to 5 used to signify the rigid start and end times of our (well, for those of us old enough to be working back then) traditional 8 -hour work day. • Connect me anytime, anywhere: End users expect to be able to connect their devices whenever and wherever they may be

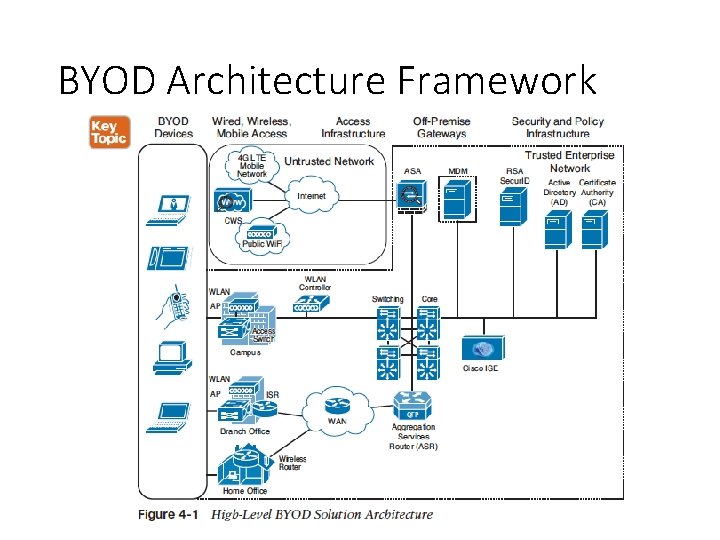
BYOD Architecture Framework

BYOD Solution Components • BYOD devices: These are the corporate-owned and personally owned endpoints that require access to the corporate network regardless of their physical location. • Wireless access points (AP): Cisco wireless APs provide wireless network connectivity to the corporate network for both corporate-owned and personally owned BYOD devices. • Wireless LAN (WLAN) controllers: Cisco WLAN controllers (WLC) serve as a centralized point for the configuration, management, and monitoring of the Cisco WLAN solution. WLCs are used to implement and enforce the security requirements for the BYOD solution that map back to an organization’s security policies. The WLC works with the Cisco Identity Services Engine (ISE) to enforce both authentication and authorization policies on each of the BYOD endpoints that require connectivity to the corporate network, both direct and remotely.

BYOD Solution Components • Identity Services Engine (ISE): The Cisco ISE is a critical piece to the Cisco BYOD solution. It is the cornerstone of the authentication, authorization, and accounting (AAA) requirements for endpoint access, which are governed by the security policies put forth by the organization. • Cisco Any. Connect Secure Mobility Client: The Cisco Any. Connect Client provides connectivity for end users who need access to the corporate network (IEEE 802. 1 x for internal users and VPN for remote users). • Integrated Services Routers (ISR): Cisco ISRs will be used in the Cisco BYOD solution to provide WAN and Internet access for the branch offices and Internet access for home office environments.

BYOD Solution Components • Aggregation Services Routers (ASR): Cisco Aggregation Services Routers (ASR) provide WAN and Internet access at the corporate campus and serve as aggregation points for all the branch and home office networks connecting back to the corporate campus for the Cisco BYOD solution. • Cloud Web Security (CWS): Formerly Scan. Safe, Cisco Cloud Web Security (CWS) provides enhanced security for all the BYOD solution endpoints while they access Internet websites using publicly available wireless hotspots and 3 G, 4 G, and 4 G LTE mobile networks. • Adaptive Security Appliance (ASA): The Cisco ASA provides all the standard security functions for the BYOD solution at the Internet edge. In addition to traditional firewall and intrusion prevention system (IPS) functions, the ASA also serves as a VPN termination point for mobile devices connecting over the Internet from home offices, branchoffices, public wireless networks, and 3 G/4 G/4 G LTE mobile networks.

BYOD Solution Components • RSA Secur. ID: The RSA Secur. ID server provides one-time password (OTP) generation and logging for users that access network devices and other applications which require OTP authentication. • Active Directory: The Active Directory (AD) server enforces access control to the network, to servers, and to applications. It restricts access to those users with valid authentication credentials. • Certificate authority: The certificate authority (CA) server provides for, among other things, the onboarding of endpoints that meet certificate requirements for access to the corporate network. The CA server ensures that only devices with corporate certificates can access the corporate network.

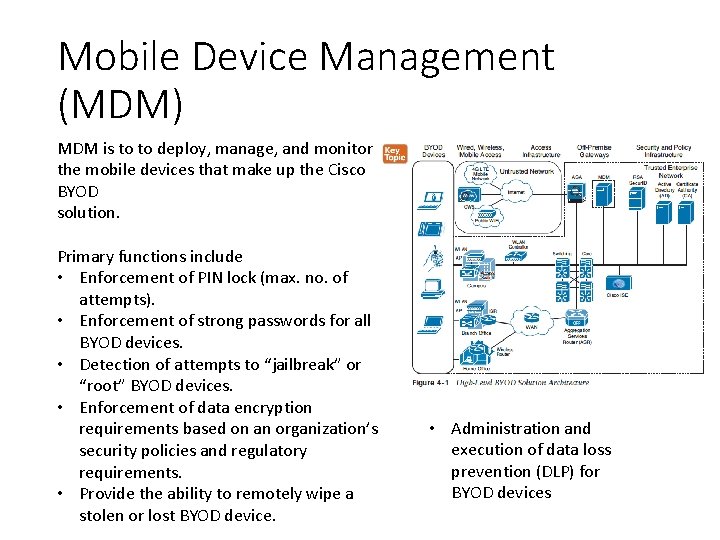
Mobile Device Management (MDM) MDM is to to deploy, manage, and monitor the mobile devices that make up the Cisco BYOD solution. Primary functions include • Enforcement of PIN lock (max. no. of attempts). • Enforcement of strong passwords for all BYOD devices. • Detection of attempts to “jailbreak” or “root” BYOD devices. • Enforcement of data encryption requirements based on an organization’s security policies and regulatory requirements. • Provide the ability to remotely wipe a stolen or lost BYOD device. • Administration and execution of data loss prevention (DLP) for BYOD devices

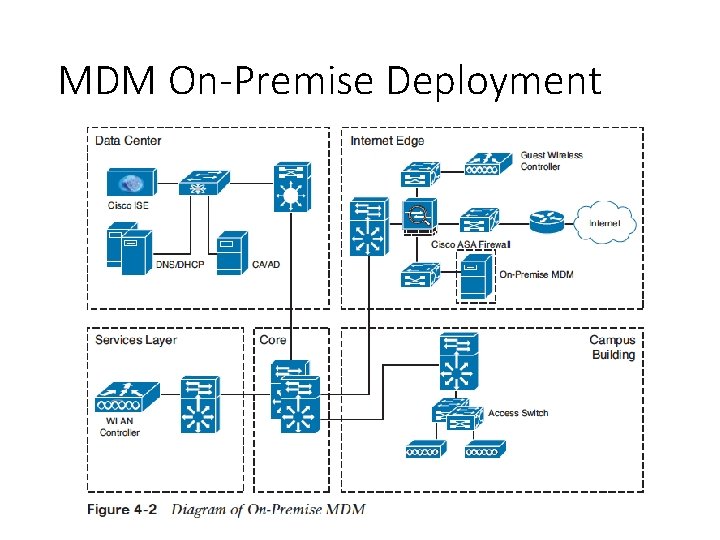
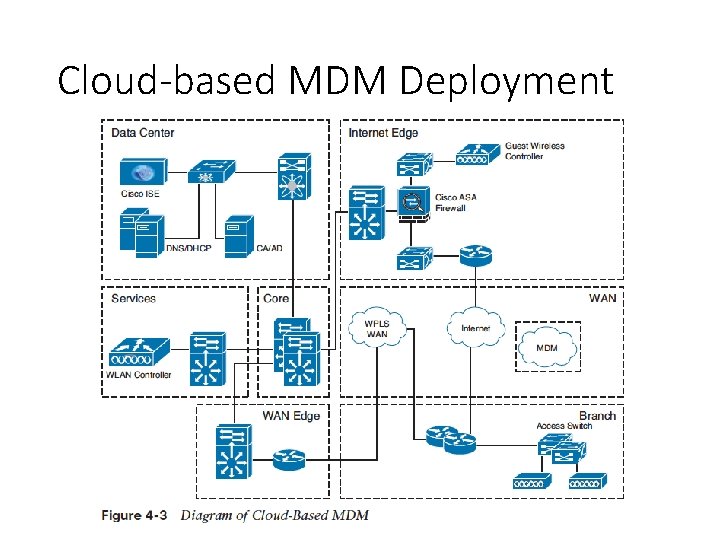
MDM Deployment Options • On-premise MDM deployment • In an on-premise deployment, MDM application software is installed on servers that are located within the corporate data center and are completely supported and maintained by the network staff of the corporation. • Cloud-based MDM deployment • In a cloud-based MDM deployment, MDM application software is hosted by a managed service provider who is solely responsible for the deployment, management, and maintenance of the BYOD solution.

MDM On-Premise Deployment

Cloud-based MDM Deployment