IOS Firewall IOS Ciscos Internetwork Operating System the




- Slides: 15

IOS Firewall • IOS: Cisco’s Internetwork Operating System (the primary system running on Cisco’s routers) • IOS Firewall: a stateful packet-filter firewall that runs on a router, providing firewall capabilities • CBAC: Context-Based Access Control (at the core of the IOS Firewall functionality

IOS Firewall Features • Major subsystems: – – – – SPI: Stateful Packet Inspection CBAC: Context-Based Access Control IOS IPS: Intrusion Prevention System User-level authentication PAM: Port-to-Application Mapping NAT ZFW: Zone-Based Policy Firewall • Other security features: – IPsec, AAA support, ACLs, … T. A. Yang Network Security 2

CBAC (Context-Based Access Control) • Replaced by ZFW (Zone-based Policy Firewall) Implement packet filtering on a Cisco router (similar to ASA on Cisco PIX) • • Three basic functionalities: 1. Dynamic modification of the extended access lists – To allow connections initiated from the inside 2. Inspection of the application/transport level protocols ~= multimedia support in PIX 3. Control of the number/length of sessions T. A. Yang Network Security 3

CBAC Functions 1. Dynamic traffic filtering (based on upper-layer protocols) – – – T. A. Yang In principle, only traffic that originates from the trusted network and goes out to the untrusted network are allowed. Set up ACLs to open holes for inbound access to inside servers Set up the router to inspect outbound packets Network Security 4

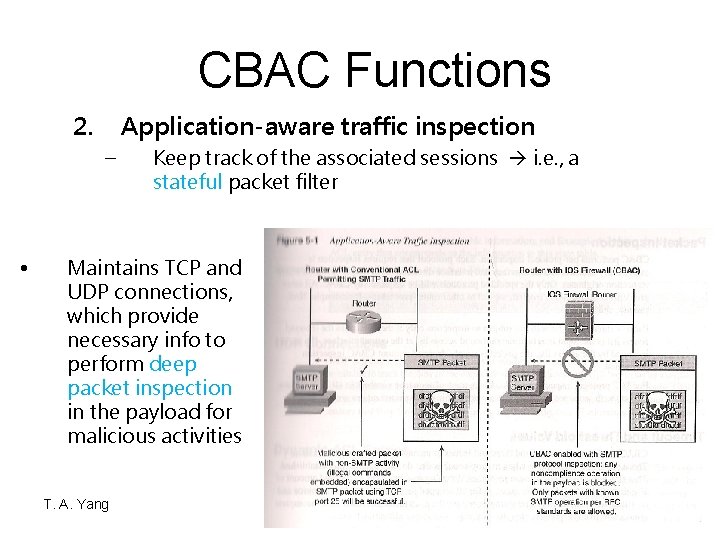
CBAC Functions 2. Application-aware traffic inspection – • Keep track of the associated sessions i. e. , a stateful packet filter Maintains TCP and UDP connections, which provide necessary info to perform deep packet inspection in the payload for malicious activities T. A. Yang Network Security 5

CBAC Functions 3. Alerts and audit trails – Real-time event alerts • – Enhanced audit trails • • T. A. Yang SYSLOG notification messages for all the session information maintained in the state table Uses SYSLOG to track all network transactions Record information such as source/destination host addresses, ports used, the total number of transmitted bytes with time stamps, etc. Good for session-based reporting, anomaly identification, … Network Security 6

How does IOS maintain session state information? • State Information Structure (SIS) – – T. A. Yang A SIS is created for each logical session. The SIS uniquely identifies a connection using the IP and the port#. When necessary, other info such as TCP connection state, TCP sequence number, etc. are also maintained. The SIS is deleted when the associated session/connection is terminated. Network Security 7

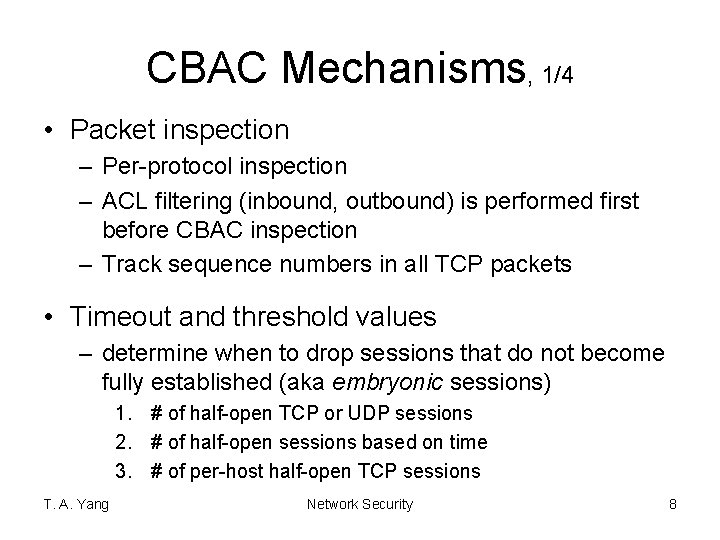
CBAC Mechanisms, 1/4 • Packet inspection – Per-protocol inspection – ACL filtering (inbound, outbound) is performed first before CBAC inspection – Track sequence numbers in all TCP packets • Timeout and threshold values – determine when to drop sessions that do not become fully established (aka embryonic sessions) 1. # of half-open TCP or UDP sessions 2. # of half-open sessions based on time 3. # of per-host half-open TCP sessions T. A. Yang Network Security 8

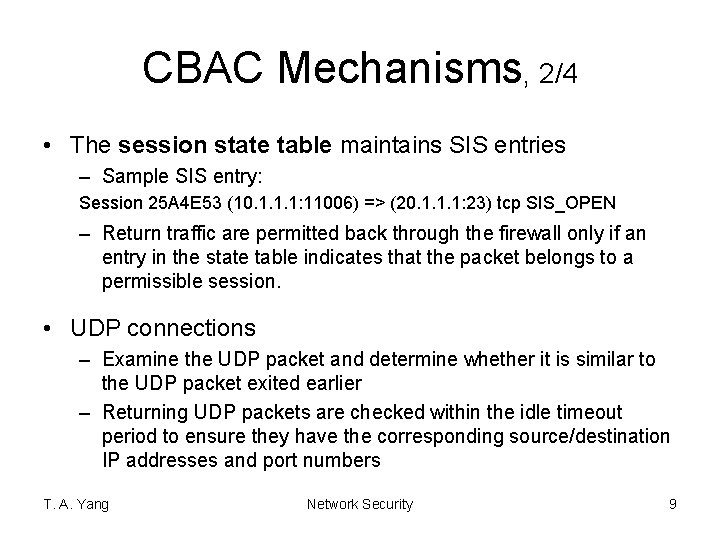
CBAC Mechanisms, 2/4 • The session state table maintains SIS entries – Sample SIS entry: Session 25 A 4 E 53 (10. 1. 1. 1: 11006) => (20. 1. 1. 1: 23) tcp SIS_OPEN – Return traffic are permitted back through the firewall only if an entry in the state table indicates that the packet belongs to a permissible session. • UDP connections – Examine the UDP packet and determine whether it is similar to the UDP packet exited earlier – Returning UDP packets are checked within the idle timeout period to ensure they have the corresponding source/destination IP addresses and port numbers T. A. Yang Network Security 9

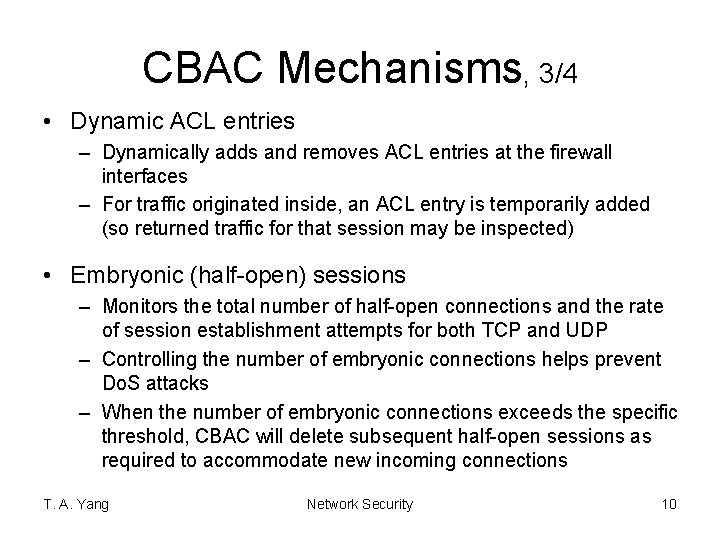
CBAC Mechanisms, 3/4 • Dynamic ACL entries – Dynamically adds and removes ACL entries at the firewall interfaces – For traffic originated inside, an ACL entry is temporarily added (so returned traffic for that session may be inspected) • Embryonic (half-open) sessions – Monitors the total number of half-open connections and the rate of session establishment attempts for both TCP and UDP – Controlling the number of embryonic connections helps prevent Do. S attacks – When the number of embryonic connections exceeds the specific threshold, CBAC will delete subsequent half-open sessions as required to accommodate new incoming connections T. A. Yang Network Security 10

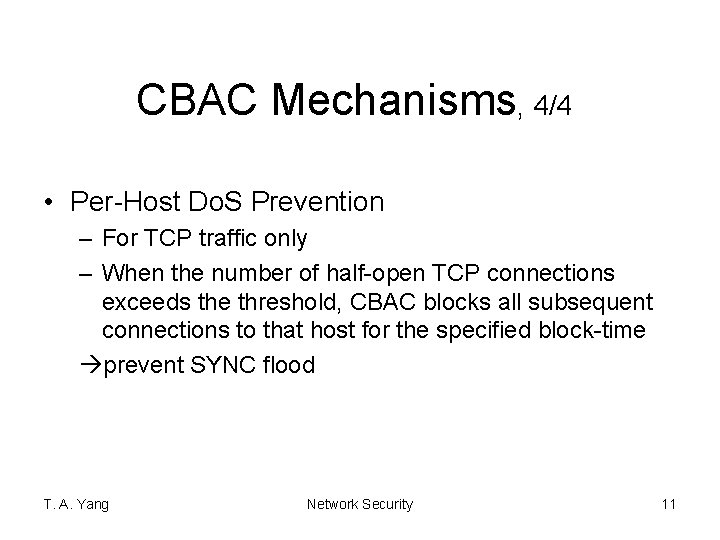
CBAC Mechanisms, 4/4 • Per-Host Do. S Prevention – For TCP traffic only – When the number of half-open TCP connections exceeds the threshold, CBAC blocks all subsequent connections to that host for the specified block-time prevent SYNC flood T. A. Yang Network Security 11

Two modes of inspections • Single-channel, or generic, TCP/UDP inspection – The return traffic must have the same source/destination IP address and port numbers – Must be within the sequence number window • Application-specific inspection – Takes precedence over the generic inspection – Many application-layer protocols are supported (CUSee. Me, FTP, H. 323, HTTP, ICMP, …) T. A. Yang Network Security 12

Other CBAC functionality • • • Out-of-sequence TCP packets are dropped. TCP packets with invalid sequence numbers are dropped. The reassembly of IP packets is not supported (as in PIX firewall). Does not inspect packets originated by the IOS Firewall router. ICMP packets are not inspected. (They are manually managed using static ACLs). ICMP unreachable packets are ignored. T. A. Yang Network Security 13

Zone-Based Policy Firewall (ZFW) • After IOS release 12. 4(6)T • Switched from the interface-based inspection model (as in CBAC) to a zone-based inspection model • Changes – Traffic passing through an interface do not need to be inspected the same way (as in interface-based model) – Interfaces are assigned to zones – Policy inspection is applied to traffic moving btwn zones • Benefits – Higher granularity – Flexibility – scalability T. A. Yang Network Security 14

Features of IOS Firewall • • • T. A. Yang Transport Layer Inspection Application Layer Inspection Filtering for Invalid Commands Java Blocking Safeguarding against Do. S attacks Fragment handling Network Security 15