2006 IEEE Symposium on Security and Privacy SP




- Slides: 20

2006 IEEE Symposium on Security and Privacy (S&P) Sub. Virt: Implementing malware with virtual machines 14 pages, cited: 163 Samuel T. King, Peter M. Chen (University of Michigan) Yi-Min Wang, Chad Verbowski, Helen J. Wang, and Jacob R. Lorch (Microsoft Research) proof-of-concept By Mike Hsiao, 20100423

Outline • Introduction • Virtual machines • Virtual-machine based rootkit design and implementation • Evaluation • Defending against virtual-machine based rootkits • Related work • Conclusions 2

Introduction • New type of malware – Virtual-machine based rootkit (VMBR) installs a VM monitor underneath an existing operating system and hoists the original operating system into a virtual machine. • rootkit: tools used to hide malicious activities – VMBR are hard to detect and remove because their state cannot be accessed by software running in the target system. – Further, VMBRs support general-purpose malicious services by allowing such services to run in a separate operating system 3

Introduction (cont’d) • A major goal of malware writers is control. – Controlling the system allows malware to remain invisible by lying to or disabling intrusion detection software. – Lower layers can control upper layers. – If the defender’s security service occupies a lower layer than the malware, then that security service should be able to detect, contain, and remove the malware. • E. g. , ps, kernel-level rootkit, check the integrity of the kernel ds, hide/check memory footprint, 4

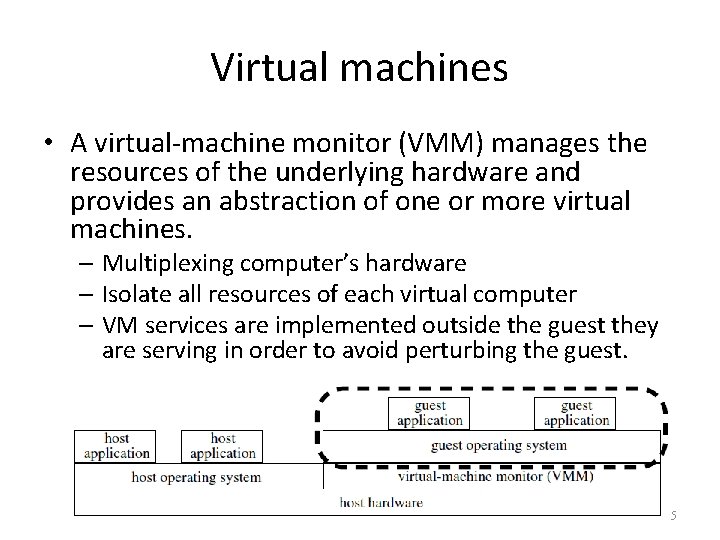
Virtual machines • A virtual-machine monitor (VMM) manages the resources of the underlying hardware and provides an abstraction of one or more virtual machines. – Multiplexing computer’s hardware – Isolate all resources of each virtual computer – VM services are implemented outside the guest they are serving in order to avoid perturbing the guest. 5

Virtual machines (cont’d) • VM services – debug operating systems and system configurations – migrate live machines – detect or prevent intrusions • Software running outside of a VM views low-level VM state such as disk blocks, network packets, and memory. • Software inside the VM interprets this state as high-level abstractions such as files, TCP connections, and variables. • It is called the semantic gap. Virtual-machine introspection (VMI) [18, 27] describes techniques that enables a VM service to understand modify states and events within the guest. [18] T. Garfinkel and M. Rosenblum, “A Virtual Machine Introspection Based Architecture for Intrusion Detection, ” in proc. NDSS, 2003. [27] A. Joshi, S. T. King, G. W. Dunlap, and P. M. Chen, “Detecting past and present intrusions 6 through vulnerability-specific predicates, ” in proc. SOSP, 2005.

Virtual-machine based rootkit design and implementation • 3. 1 describes how a VMBR is installed on an existing system. • 3. 2 describes the techniques VMBRs use to implement malicious services, and • 3. 3 discusses the example malicious services we implemented. • 3. 4 explains how VMBRs maintain control over the system. • They implemented two proof-of-concept VMBRs for the x 86 platform using Virtual PC and VMware Workstation VMMs. – The Virtual PC VMBR uses a minimized version of Windows XP for the host OS and the VMware VMBR uses Gentoo Linux. – They modify the host Windows XP kernel, Virtual PC, and the host Linux kernel. (They don’t have VMware source code. ) 7

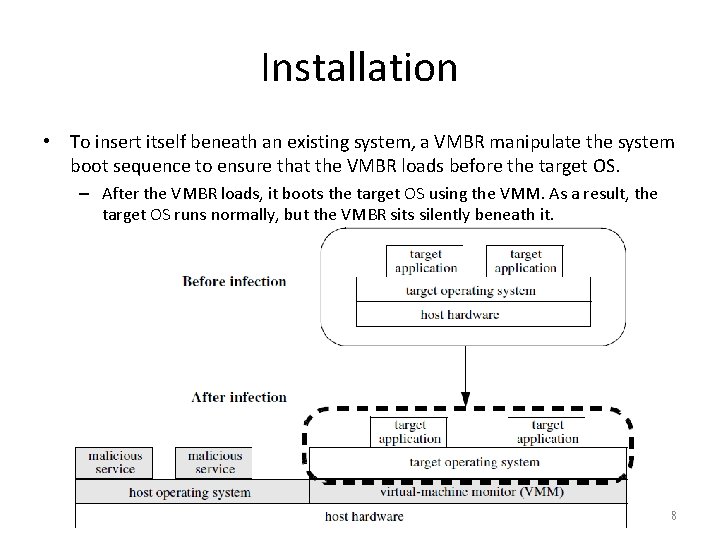
Installation • To insert itself beneath an existing system, a VMBR manipulate the system boot sequence to ensure that the VMBR loads before the target OS. – After the VMBR loads, it boots the target OS using the VMM. As a result, the target OS runs normally, but the VMBR sits silently beneath it. 8

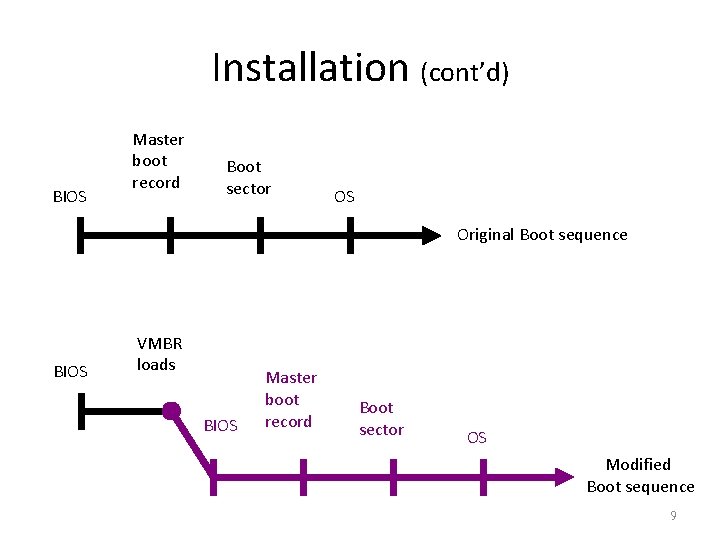
Installation (cont’d) BIOS Master boot record Boot sector OS Original Boot sequence BIOS VMBR loads BIOS Master boot record Boot sector OS Modified Boot sequence 9

Installation (cont’d) • To install a VMBR on a computer, an attacker must first gain access to the system with sufficient privileges to modify the system boot sequence. – exploit a remote vulnerability – fool a user into installing malicious software – bribe an OEM or vendor – corrupt a bootable CDROM or DVD image on P 2 P • Install the VMBR’s state on persistent storage – unused blocks elsewhere on the disk (Windows) – Disable swapping and use the swap partition (Linux) 10

Installation (cont’d) • Modify the system’s boot sequence to ensure our VMBR loads before the target OS – modify the boot records on the primary hard disk – But, anti-malware applications detect modifications to the hard disk’s boot blocks. – But, the author manipulate the boot blocks during the final stages of shutdown (after most processes and kernel subsystems have exited). • Windows XP: registers a Last. Chance. Shutdown Notification event handler – They use the low-level disk driver to copy our VMBR boot code (to bypass the file system layer). • Linux: modify the boot sequence using user-mode code – They modify the shutdown scripts so that our installation code runs after all processes have been killed but before the system shuts down. 11

Malicious services • VMBRs use a separate attack OS to deploy malware that is invisible from the perspective of the target OS but is still easy to implement. • Three categories (malicious services) – those that need not interact with the target system at all • E. g. , spam relays, DDo. S zombies, phishing web servers – those that observe information about the target system • VMBRs can use virtual-machine introspection to help observe and understand the software-level abstractions in the target OS and applications. • Not affect the virtual devices presented to the target OS. • E. g. , VMBRs enable logging of hardware-level data (e. g. , keystrokes, packets) • E. g. , if a target application uses an encrypted socket, attackers can use virtualmachine introspection to trap all SSL socket write calls and log the clear-text data before it is encrypted. – those that intentionally perturb the execution of the target system • The third class of malicious service deliberately modifies the execution of the target system. • A VMBR can customize the VMM’s device emulation layer to modify hardware -level data. 12

Example malicious services • The author implemented – a phishing web server, • in another VM – a keystroke logger, • in the VMM keyboard control module – a service that scans the target file system looking for sensitive files, and • use VM introspection to scan the target OS’s file system to copy the password file – a defense countermeasure that defeats a current virtual-machine detector. • redpill [39] J. Rutkowska. Red Pill. . . or how to detect VMM using (almost) one CPU instruction, 2005. 13 http: //invisiblethings. org/papers/redpill. html.

Maintaining control • To avoid being removed, a VMBR must protect its state by maintaining control of the system. – The only time the VMBR loses control of the system is in the period of time after the system powers up until the VMBR starts. • The first code is BIOS. – By restarting the virtual hardware, VMBRs provide the illusion of resetting the underlying physical hardware without relinquishing control. – VMBRs can also emulate system shutdowns such that the system appears to shutdown, but the VMBR remains running on the system. • We use ACPI sleep states to emulate system shutdowns and to avoid system power-downs. • When the user “powers-up” the system by pressing the power button the VMBR resumes. (powers-off only suspends the VMBR) 14

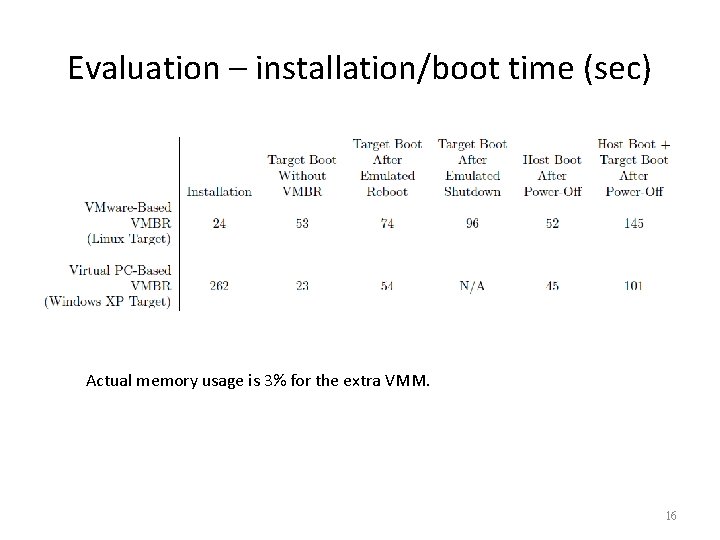
Evaluation • VMware-based VMBR – Run on a Dell Optiplex Workstation with a 2. 8 GHz Pentium 4 and 1 GB of RAM – compromises a Red. Hat Enterprise Linux 4 target system – VMBR image 228/95 MB (un-/uncompressed) • Virtual PC-based VMBR – a Compaq Deskpro EN with a 1 GHz Pentium 4 and 256 MB of RAM – compromises a Windows XP target system – VMBR image 251/106 MB (un-/uncompressed) 15

Evaluation – installation/boot time (sec) Actual memory usage is 3% for the extra VMM. 16

Defending against virtual-machine based rootkits • Security software below the VMBR – Such detection software can read physical memory or disk and look for signatures or anomalies that indicate the presence of a VMBR. – Other low-level techniques such as secure boot can ensure the integrity of the boot sequence and prevent a VMBR from gaining control before the target OS. • Intel’s La. Grande [25], AMD’s platform for trustworthy computing [2], and Copilot [36]. – Boot from a safe medium such as a CD-ROM, USB drive or network boot server – Use a secure VMM [17] (Terra) • does not by itself stop a VMBR, but does retain control over the system 17

Defending against virtual-machine based rootkits (cont’d) • Security software above the VMBR – (CPU overhead) by comparing the running time of benchmarks against wall-clock time – (memory and disk space) extra paging activity may increase the running time of the program – (I/O devices) VMMs only emulate a small number of virtual devices (often with customized interfaces to improve performance) – (x 86 processor features) sidt 18

Related work • Layer-below attacks – operating system kernel • Using virtual machines to enhance security – – VMs to detect intrusions, analyze intrusions isolate services encrypt network traffic implement honeypots • Detect the presence of VMMs • Inserting new software layers into existing systems – A key feature of all these applications is that they preserve compatibility with existing systems by not modifying interfaces of the existing layers. – E. g. , file system, firewall 19

Comments • Considering the characteristics of VM in security issues. – VMM layer – VM Image can be ”power on/off” • Some people don’t like VM environment. – How to detect that I’m in a VM? – How do I know my host/VMM/VM/OS is secure? – Can other vulnerable or hostile VM penetrate my VM? • Auditing mechanisms (such as VMMs) are benefits or harms for me? • Provide better visibility! 20