Privacy Management Mechanisms Course Security and Privacy on






























![References [1] Rolf Oppliger, “Microsoft. NET Passport”, IEEE Computer Society, July 2003, pp. 29– References [1] Rolf Oppliger, “Microsoft. NET Passport”, IEEE Computer Society, July 2003, pp. 29–](https://slidetodoc.com/presentation_image/19f18e24b731611109f7714a93772be2/image-43.jpg)

- Slides: 44

Privacy Management Mechanisms Course: Security and Privacy on the Internet Instructor: Dr. A. K. Aggarwal Presented By: Rachita Singh Fadi Farhat Fall, 2007 1 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Table of Contents Introduction n Security and Privacy n Basic Security Services n Privacy Mechanisms n Proposed Techniques - Centralization of Information - Smart Card Technology using different keys n What people should do to help their privacy? n Conclusion n References n Questions n 2 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Introduction Our paper has two major purposes: 1 - Define some terms and concepts of basic cryptographic methods by using the Privacy Mechanisms. 2 - Present two useful strategies: 2. 1 - Centralization of Information. Smart Card Technology using different keys. 2. 2 - 3 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Security and Privacy n Security can be defined as the “mechanisms and techniques that control who may use or modify the computer or the information stored in it” n Privacy can be defined as “the ability of an individual (or organization) to decide whether, when, and to whom personal (or organizational) information is released. ” 4 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

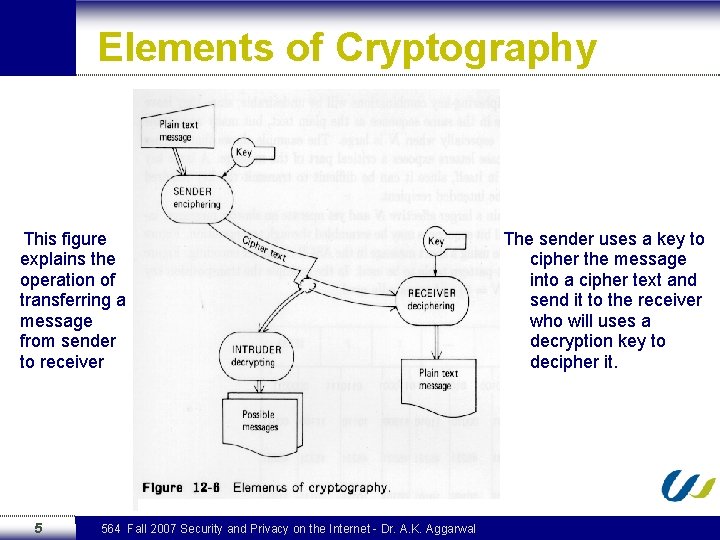
Elements of Cryptography This figure explains the operation of transferring a message from sender to receiver 5 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal The sender uses a key to cipher the message into a cipher text and send it to the receiver who will uses a decryption key to decipher it.

Basic Security Services 1. Authentication It provides us the assurance that the communicating entity is the one it claims to be Two types of Authentication: Peer entity authentication It provides mutual confidence in the identities of the parties involved in a connection. 1. 1 Data origin authentication It insures the assurance about the source of the received data. 1. 2 6 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Basic Security Services 2. Access Control The prevention of unauthorized use of a resource (i. e. this service controls who can have access to a resource, under what conditions access can occur, and what those accessing the resource are allowed to do). 3. Confidentiality It is the protection of information from unauthorized disclosure (against eavesdropping). 7 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Basic Security Services 4. Traffic-flow confidentiality The protection of information that might be derived from observation of traffic flows. 5. Integrity Data integrity is the assurance that the data is consistent, correct and accessible. Assurance that data received are exactly as sent by an authorized sender i. e. no modification, insertion, deletion or replay. 8 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Basic Security Services 6. Non-repudiation It is the concept of protection against denial by one of the parties in a communication. There are two types of non-repudiation: Origin non-repudiation It is the proof that the message was sent by the specified party. 6. 1. Destination non-repudiation It is the proof that the message was received by the specified party. 6. 2. 9 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Privacy Mechanisms 1. Encryption (Encipherment) It is the process of encoding information into a secret code by using a special key. To read an encrypted file, you must have the key of the decoding that enables you to decrypt it. By using an algorithm for encryption we can protect our personal information that we don’t want other people to see such as: - Credit-card information - Bank-account information - Medical information 10 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

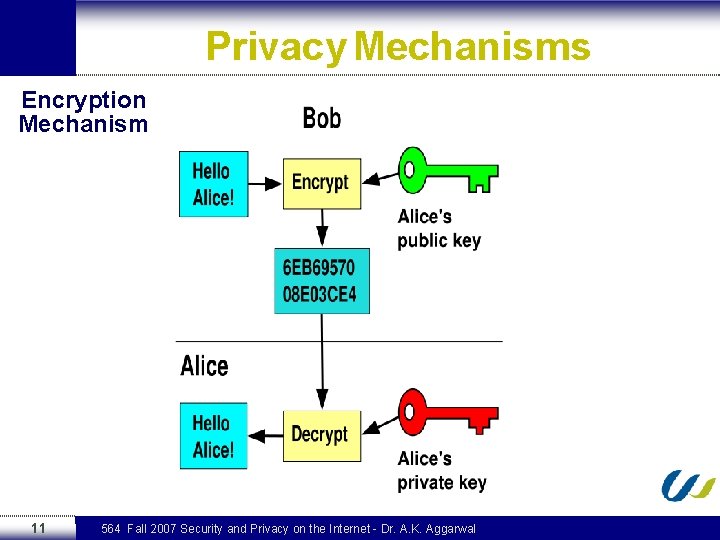
Privacy Mechanisms Encryption Mechanism 11 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Privacy Mechanisms The two main types of Encryption are: n Asymmetric encryption (also called public-key encryption) n Symmetric encryption 12 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Privacy Mechanisms Public-key cryptography n A user has a pair of cryptographic keys - a public key and a private key. The private key is kept secret, while the public key may be widely distributed. § A message encrypted with the public key can be decrypted only with the corresponding private key. 13 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

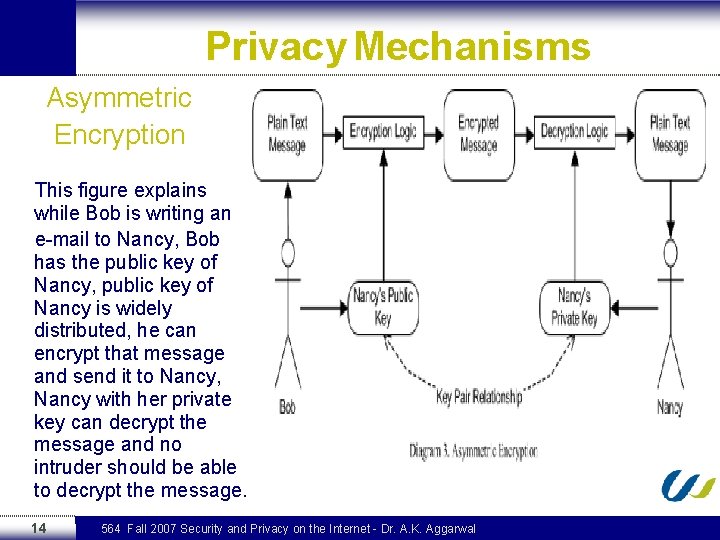
Privacy Mechanisms Asymmetric Encryption This figure explains while Bob is writing an e-mail to Nancy, Bob has the public key of Nancy, public key of Nancy is widely distributed, he can encrypt that message and send it to Nancy, Nancy with her private key can decrypt the message and no intruder should be able to decrypt the message. 14 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Privacy Mechanisms Private Key encryption 15 n Private Key means that each computer has a secret key that it can use to encrypt a packet of information. n It requires that you know which computers will talk to each other and install the key on each one. n If "A" becomes "C" and "B" becomes "D". You have already told the other party that the code is "Shift by 2“ 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Privacy Mechanisms Difference between Symmetric and Asymmetric In a symmetric cryptosystem, the same key is used for encryption and decryption while in an asymmetric cryptosystem the key used for decryption is different from the key used for encryption. 16 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Privacy Mechanisms 2. Digital Signature A digital signature is basically a way to ensure that an electronic document is authentic. Authentic means that you know who created the document and that it has not been altered. 17 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

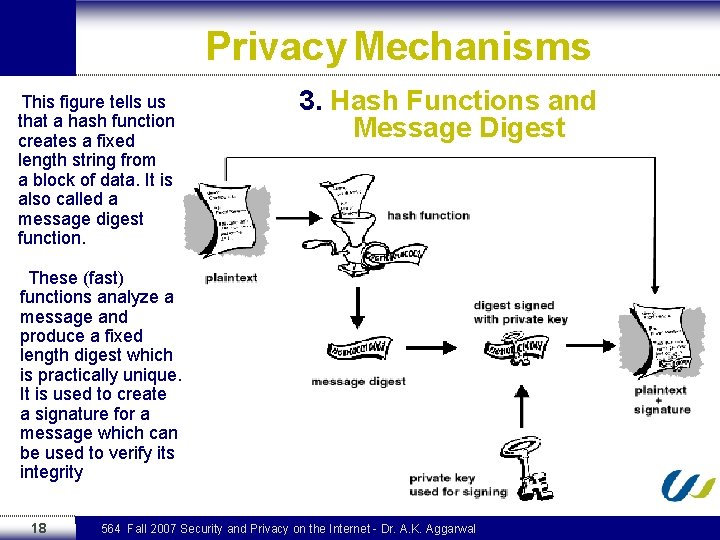
Privacy Mechanisms This figure tells us that a hash function creates a fixed length string from a block of data. It is also called a message digest function. 3. Hash Functions and Message Digest These (fast) functions analyze a message and produce a fixed length digest which is practically unique. It is used to create a signature for a message which can be used to verify its integrity 18 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Privacy Mechanisms 4. Access Control Access control is way of talking about controlling access to a web resource. Access can be granted or denied based on a wide variety of criteria, such as the network address of the client, the time of day, or the browser which the visitor is using. 19 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Privacy Mechanisms 5. Traffic Padding 20 n It is the process of intercepting and examining messages in order to deduce information from patterns in communication. n The attacker might not know what A and B were talking but he could know that they were talking and how much they talked. n Padding messages is a way to make it harder to do traffic analysis. A number of random bits are appended to the end of the message. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Privacy Mechanisms 6. Routing control Enables selection of a particular physically secure route for certain data and allows routing changes, especially when a breach of security is suspected. 7. Notarization It’s the use of a third party to assure the other party. 21 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Proposed Techniques We will present two useful Techniques. 1 - Centralization of Information. 2 - Smart Card Technology using different keys. 22 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Centralization of Information 23 n The idea is to create a Passport account with the detailed information that will be saved in a central database and protected by several security levels. n Every user will have a unique identifier for his account in addition to some personal information like the e-mail address, phone number and the first and last name. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Centralization of Information Objectives 24 n Authenticate users for participating sites. n Secure sign-in. n Log in to many websites using one account. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Centralization of Information Two of the famous groups The Liberty Alliance Project: It was established in September 2001 for more than 160 companies. The goal of the group was to establish an open standard for federated network identity. n . NET Passport: It is a unified-login service presented by Microsoft to allow users log in to many websites using one account. (MSN Messenger, MSN Hotmail, MSN Music, and other sites and services ) n 25 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Centralization of Information Secure sign-in service 26 n To access a participating site, the browser will send an initial HTTP request message. n The site will return an HTTP redirect message for the cobranded sign-in page on the Passport server. n The site will add its unique ID and a return URL to the HTTP. n Passport server will check the site ID and return URL before displaying the authentication. n The Passport server and the participating site server never communicate users’ authentication and profile information directly but over secure channels. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Centralization of Information Security levels Microsoft. NET Passport provides three security levels: n n n 27 Standard sign-in Secure channel sign-in Strong credential sign-in 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Centralization of Information Standard sign-in security level In standard sign-in, the SSL/TLS protocols (Secure Sockets Layer /Transport Layer Security) only secure the transmission of user credentials between the browser and the Passport server, not between the browser and the participating sites. Sites that don’t require a high level of security, such as Microsoft’s Hotmail service, use standard sign-in. 28 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Centralization of Information Secure channel sign-in security level In the secure channel sign-in, all communication takes place over secure channels as HTTPS (HTTP&SSL/TLS). With secure channel sign-in, traffic is encrypted with an SSL/TLS session key held only by legitimate participants and that will be to ensure reasonable protection from eavesdroppers and man in the middle attacks. 29 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Centralization of Information Strong credential sign-in security level 30 n If a user enters a password incorrectly five consecutive times, . NET Passport automatically blocks access to the account for two minutes, making it difficult for an attacker to launch a password cracker. n Passport’s designers chose a two-stage sign-in process for protecting participating sites with more stringent security requirements. Stage one is identical to secure channel sign-in. Stage two involves a second sign-in page that requires the user to enter a four-digit security key, or PIN. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

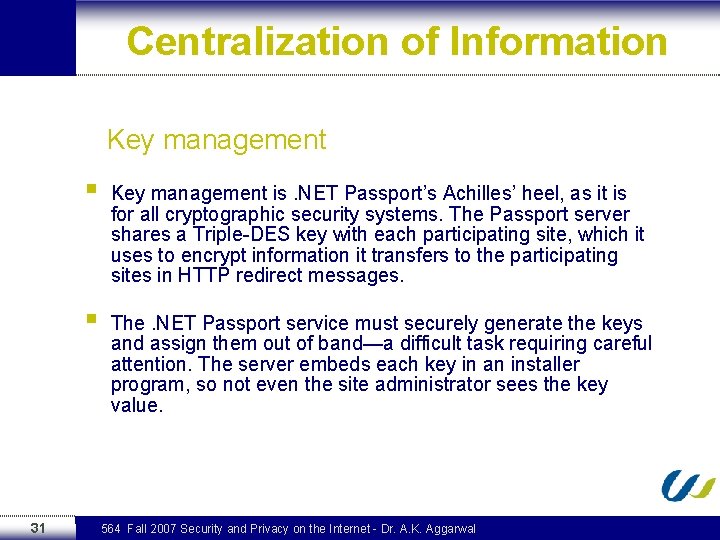
Centralization of Information Key management 31 § Key management is. NET Passport’s Achilles’ heel, as it is for all cryptographic security systems. The Passport server shares a Triple-DES key with each participating site, which it uses to encrypt information it transfers to the participating sites in HTTP redirect messages. § The. NET Passport service must securely generate the keys and assign them out of band—a difficult task requiring careful attention. The server embeds each key in an installer program, so not even the site administrator sees the key value. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Centralization of Information Suggestions for the centralization of Information As most of the websites need a verification of our personal id, and as we have to provide them with it, and to prevent the disclose of that confidential information we suggest that, the. NET Passport expands its spread by increasing the limited number of websites that it deals with to authenticate us where ever needed and that will be by playing the role of a notarized third party. 32 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Smart Card Technology using different keys n A smart card or chip card is defined as any pocket-sized card with embedded memory storage components, small processor and finger print sensor. It can: n Receive information. Process it. Deliver outputs. n n By using of a special driver. 33 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Smart Card Technology using different keys Objectives 34 n The Smart Card will store different personal information such as Medical and Banking information. n The protection of our personal information like credit card information, social security number or bank account information can be achieved using encryption, which must be done using different keys depending on the organization for which information from the smart card will be released. n Self protection (using processor) in the case of a none authorized use (destroy the memory). 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Smart Card Technology using different keys Example For example the encryption key of the bank account information for a certain person should be different from the encryption key of the medical information for the same person. This will impose that the user provides each party with the special private key to ensure that no one else can decrypt other information pertaining to other organizations. 35 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Smart Card Technology using different keys How to benefit from The Smart Card? The Smart Card can be used for commercial transactions over the Internet (using a special driver) such that the user’s encrypted information will be read thru a Smart Card Reader by the merchant who in his turn, transfers these encrypted information to the related organization. 36 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Smart Card Technology using different keys Security Issue There is a security issue concerning the use of this Smart Card for commercial transactions over the Internet; a scenario could happen where the website can use the encrypted information to process banking transactions more than authorized. 37 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Smart Card Technology using different keys Proposed Solution The proposed solution is to let the user add to his original encrypted information the number of times, that information, is allowed to be used and the amount to be paid to the merchant website at that specific transaction (for bank issues), keeping in mind that the new information will be encrypted by the same key of the original encrypted information. 38 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

What people should do to help their privacy? Internet privacy is the ability to control who will access the information and what part of information. § The first and the most important advice is not to give the personal information unless for trusted parties. § Read the Agreements provided by the websites very well before accepting it because most of the times it grants them the right to share your private information with third parties and they are always make these agreements as long as possible and sometimes hard to be understood to push you for accepting it without well understanding its terms and conditions. 39 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

What people should do to help their privacy? § Avoid answering the unnecessary questions or fill the not required fields in the Web. Pages that ask about that. n 40 Be careful about deploying your personal information in social networks because you have to put in mind that those Web. Pages are constructed to share personal information with everyone who wants to see them. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

What people should do to help their privacy? § Keep in mind that most of the Web. Pages that provides free downloading and free services ask for your personal information to use it for business purposes and in an unauthorized way. 41 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Conclusion n 42 We presented the Security Services and there role towards protecting information over the Internet. n We described the Privacy Mechanisms and how they can protect our information from attackers. n We mentioned the more privacy we can benefit from the Centralization of Information. n We offered the Smart Card Technology using different keys that can enhance our privacy over the Internet. n And at the end we suggested some important tips that can help in supporting our privacy issues. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
![References 1 Rolf Oppliger Microsoft NET Passport IEEE Computer Society July 2003 pp 29 References [1] Rolf Oppliger, “Microsoft. NET Passport”, IEEE Computer Society, July 2003, pp. 29–](https://slidetodoc.com/presentation_image/19f18e24b731611109f7714a93772be2/image-43.jpg)
References [1] Rolf Oppliger, “Microsoft. NET Passport”, IEEE Computer Society, July 2003, pp. 29– 35. [2] Maryam N. Razavi and Lee Iverson, “A Grounded Theory of Information Sharing Behavior in a Personal Learning Space”, ACM Press, 2006, pp. 459– 468. [3] Irene Pollach, “What’s wrong with online privacy policies? ”, ACM Press, Sep 2007, pp. 103– 108. [4] Jason I. Hong, Jennifer D. Ng, Scott Lederer and James A. Landay, “Privacy Risk Models for Designing Privacy-Sensitive Ubiquitous Computing Systems”, ACM Press, 2004, pp. 91 -100. 43 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal

Questions 44 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal