WLCG Security Trust and Policies GDPR David Kelsey
















- Slides: 26

WLCG Security – Trust and Policies (& GDPR) David Kelsey (STFC-RAL) WLCG Collaboration Workshop – Naples – 28 March 2018 eosc-hub. eu @EOSC_eu EOSC-hub receives funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No. 777536.

Overview HSF Roadmap – Security (section 3. 13) - 3 key areas, including “Trust and policies” § this includes trust models, policies, compliance, data protection issues So I will address activities in: Policies, Trust and GDPR Increasingly working together with others to align policy, build trust and interoperate - EOSC-hub – EGI, EUDAT, Thematic Services, … - AARC 2 policy - includes WLCG for security policy – long history of joint policy development (JSPG in 2004) Trust models - WISE Community – other e-Infrastructures (globally) Including “Security for Collaborating Infrastructures” - Interoperable Global Trust Federation (IGTF) – OIDC Federations WLCG & GDPR 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 5

Why the use of EOSC-hub slide template? EOSC-hub – EU H 2020 project – Jan 2018 to Dec 2020 - a single contact point for European researchers and innovators to discover, access, use and reuse a broad spectrum of resources for advanced data-driven research I lead the operational security task in EOSC-hub (WP 4 Task 4. 4) - Includes Security Policies and Trust § together with operations, incident response, vulnerability handling, monitoring, training - EOSC-hub, EGI Foundation & Grid. PP all fund me to work on Security Policy I also lead the Community Engagement sub-task in AARC 2 Policy and Best Practice Harmonisation - The EU H 2020 Authentication and Authorisation for Research and Collaboration Hence all the logos on the title slide! 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 6

Security Policies 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 7

Security Policies At end of EGI-Engage (31 Aug 2017) - Complete revision of all policies was complete - Community policies developed jointly with AARC 2 - Also being adopted by WLCG All policies written to be general - And may be used by any Infrastructure https: //wiki. egi. eu/wiki/SPG: Documents 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 8

New work on Security Policies (2018) AUP alignment (AARC 2 & EOSC-hub) - In 2005, JSPG achieved a common, simple & short User AUP This has been used by many Infrastructures – but versions diverged Time to re-align (can we agree a new single simple baseline version? ) User accepts when they register with their Community (or Infrastructure) Data Protection & GDPR - See later More generally, a full review of all EGI & EUDAT security policies - What is needed to move towards a common shared security policy? - Is it even possible? Or do we stick to SCI? (see next slide) 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 9

Trust 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 10

SCI History • “Security for Collaborating Infrastructures” (SCI) • A collaborative activity of information security officers from large-scale infrastructures • EGI, OSG, PRACE, EUDAT, CHAIN, WLCG, XSEDE, … • Developed a Trust framework (published in 2013) • • Enable interoperation (security teams) Manage cross-infrastructure security risks Develop policy standards Especially where not able to share identical security policies • Joined with GEANT SIG-ISM to become “WISE” (Oct 2015) SCI at WISE/NSF Cybersecurity Summit 15 Aug 2017 11

SCI Version 1 paper (2013) • Proceedings of the ISGC 2013 conference http: //pos. sissa. it/archive/conferences/179/011/ISGC%202013_011. pdf • The document defines a series of numbered requirements in 6 areas SCI at WISE/NSF Cybersecurity Summit 15 Aug 2017 12

SCI version 1 - children • Both separate derivatives of SCI version 1 • REFEDS Sirtfi - The Security Incident Response Trust Framework for Federated Identity • https: //refeds. org/sirtfi • AARC/IGTF Snctfi – The Scalable Negotiator for a Community Trust Framework in Federated Infrastructures • https: //www. igtf. net/snctfi/ SCI at WISE/NSF Cybersecurity Summit 15 Aug 2017 13

Sirtfi SCI at WISE/NSF Cybersecurity Summit 15 Aug 2017 14

Snctfi SCI at WISE/NSF Cybersecurity Summit 15 Aug 2017 15

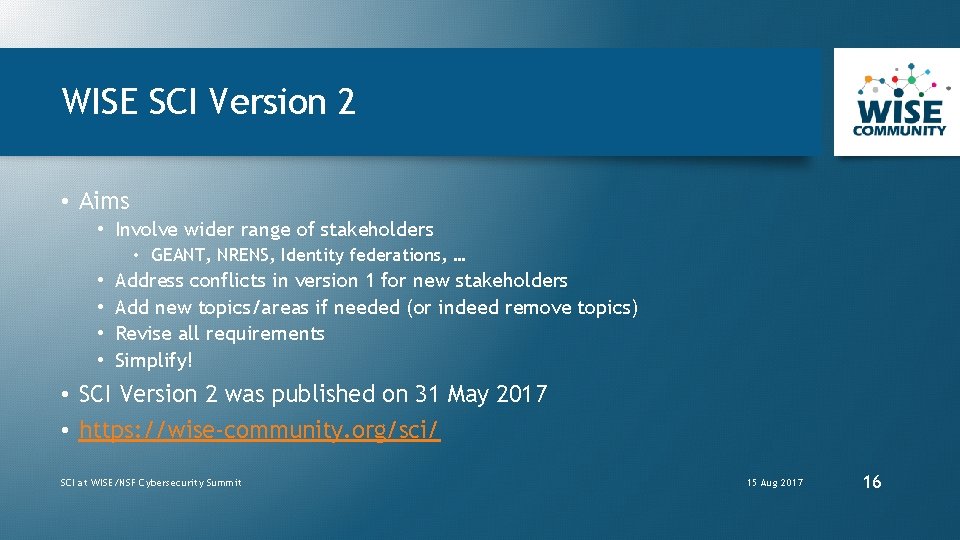
WISE SCI Version 2 • Aims • Involve wider range of stakeholders • GEANT, NRENS, Identity federations, … • • Address conflicts in version 1 for new stakeholders Add new topics/areas if needed (or indeed remove topics) Revise all requirements Simplify! • SCI Version 2 was published on 31 May 2017 • https: //wise-community. org/sci/ SCI at WISE/NSF Cybersecurity Summit 15 Aug 2017 16

Endorsement of SCI Version 2 at TNC 17 (Linz) • 1 st June 2017 • Infrastructures endorse the governing principles and approach of SCI, as produced by WISE, as a medium of building trust between infrastructures, to facilitate the exchange of security information in the event of a cross-infrastructure incident, and the collaboration of e-Infrastructures to support the process. These Infrastructures welcome the development of an information security community for the Infrastructures, and underline that the present activities by the research and e-Infrastructures should be continued and reinforced • Endorsements have been received from the following infrastructures; EGI, EUDAT, GEANT, Grid. PP, MYREN, PRACE, SURF, WLCG, XSEDE. • https: //www. geant. org/News_and_Events/Pages/supporting-security-for-collaboratinginfrastructures. aspx SCI at WISE/NSF Cybersecurity Summit 15 Aug 2017 17

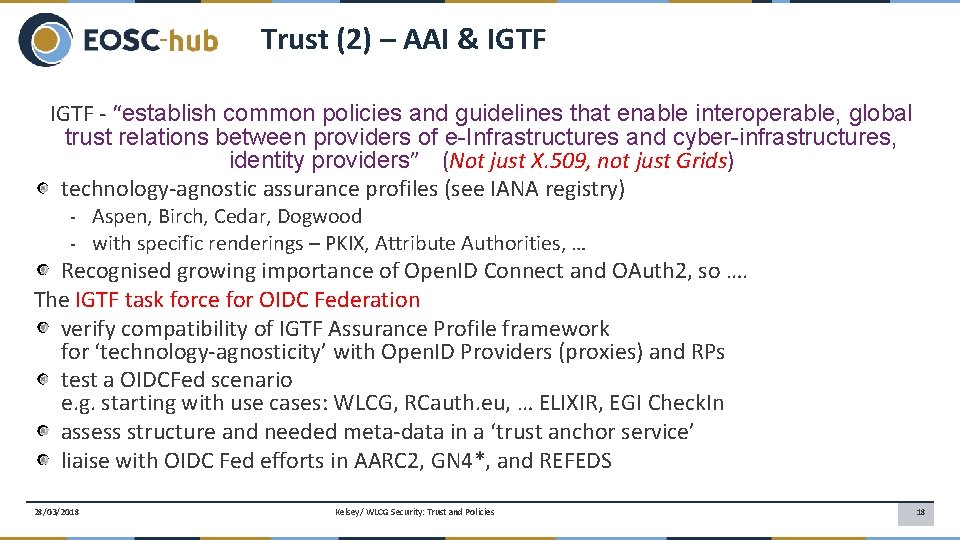
Trust (2) – AAI & IGTF - “establish common policies and guidelines that enable interoperable, global trust relations between providers of e-Infrastructures and cyber-infrastructures, identity providers” (Not just X. 509, not just Grids) technology-agnostic assurance profiles (see IANA registry) - Aspen, Birch, Cedar, Dogwood - with specific renderings – PKIX, Attribute Authorities, … Recognised growing importance of Open. ID Connect and OAuth 2, so …. The IGTF task force for OIDC Federation verify compatibility of IGTF Assurance Profile framework for ‘technology-agnosticity’ with Open. ID Providers (proxies) and RPs test a OIDCFed scenario e. g. starting with use cases: WLCG, RCauth. eu, … ELIXIR, EGI Check. In assess structure and needed meta-data in a ‘trust anchor service’ liaise with OIDC Fed efforts in AARC 2, GN 4*, and REFEDS 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 18

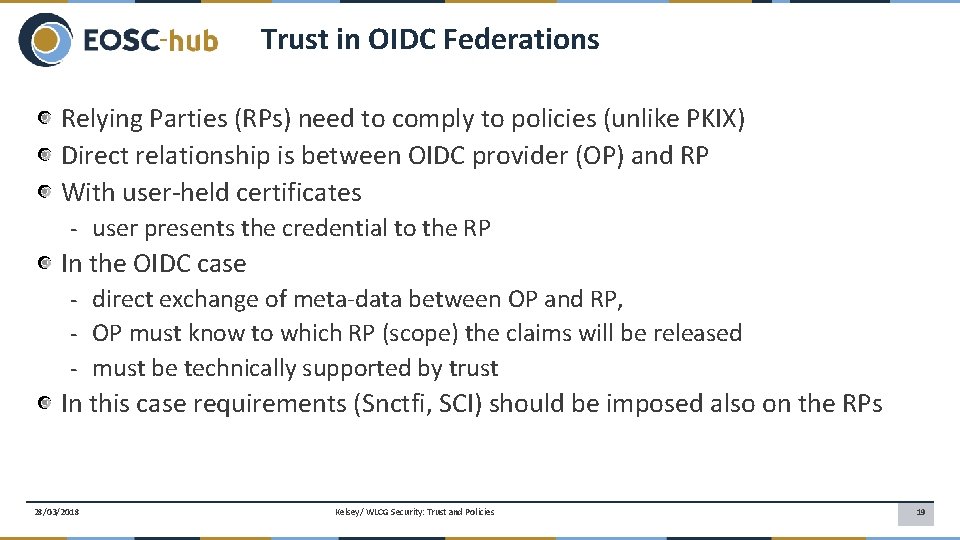
Trust in OIDC Federations Relying Parties (RPs) need to comply to policies (unlike PKIX) Direct relationship is between OIDC provider (OP) and RP With user-held certificates - user presents the credential to the RP In the OIDC case - direct exchange of meta-data between OP and RP, - OP must know to which RP (scope) the claims will be released - must be technically supported by trust In this case requirements (Snctfi, SCI) should be imposed also on the RPs 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 19

WLCG & GDPR 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 20

GDPR & WLCG? Disclaimer – I am not a lawyer – these are SPG (non-expert) views. And this is a very brief report on a complex topic! Many WLCG services consume personal data from X. 509 certificates, Id. Ps and Community Attribute Authorities (Experiment Authorisation databases) We consider all such services (run by Sites or by VOs) in general are “Data Controllers” International Transfers (outside of EU) are essential for WLCG - In current EGI/WLCG Data Protection Framework we align ourselves with “Binding Corporate Rules” to control these transfers So what changes now under the GDPR? Big thanks to Andrew Cormack (Jisc, UK) for slides he showed in webinars 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 21

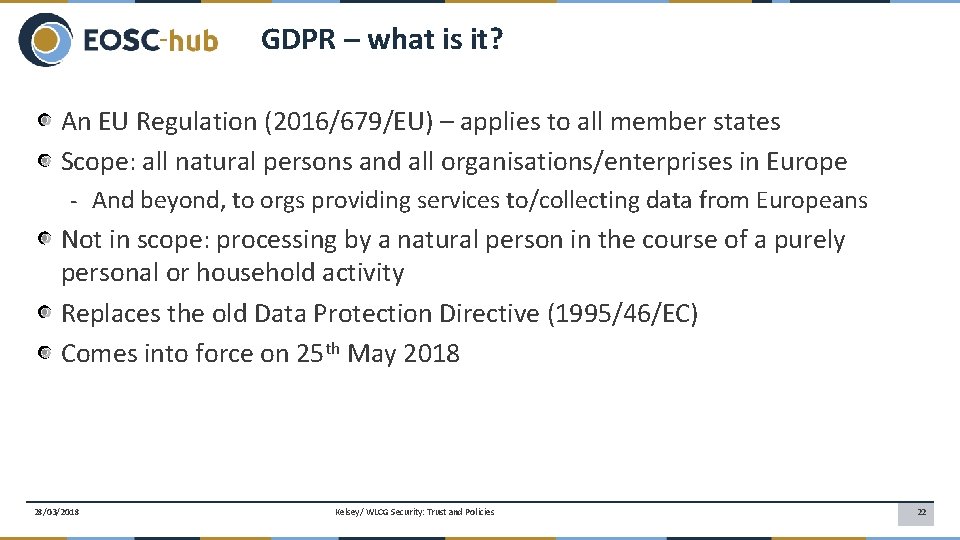
GDPR – what is it? An EU Regulation (2016/679/EU) – applies to all member states Scope: all natural persons and all organisations/enterprises in Europe - And beyond, to orgs providing services to/collecting data from Europeans Not in scope: processing by a natural person in the course of a purely personal or household activity Replaces the old Data Protection Directive (1995/46/EC) Comes into force on 25 th May 2018 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 22

GDPR – what is new? An incomplete list! Accountability (need to document) » What, why, where, how long for, who may obtain it? » Risks, and how they are managed » Information lifecycles, not just asset registers Data Protection by Design/Default - Data minimisation, anonymisation, pseudonyms, etc. Options default to privacy-protecting: users must choose to relax Formal Data Protection Impact Assessments (DPIA) – risks to individuals Consent - New, tighter, conditions for consent to be valid not a condition of service, not under compulsion Designed to be hard to obtain/manage (“reduce overuse”) – not relevant in most WLCG use cases! User Rights - Information, access, portability, rectification, erasure, objection, restriction, no automation Security 28/03/2018 Must protect data, notify breaches and there is explicit support for security incident response Kelsey/ WLCG Security: Trust and Policies 23

GÉANT Data Protection Code of Conduct V 2 Produced by GN 4 -2 (Mikael Linden, CSC, leading) with extensive legal advice - For all of Research and Education – including Research Infs and e-Infrastructures GDPR Articles 40 & 41 address “Codes of Conduct” (Co. Co) - Associations and other bodies representing categories of controllers or processors may prepare codes of conduct - to provide appropriate safeguards within the framework of personal data transfers to third countries (Service outside of EU abiding by Co. Co V 2) the Controller inside EU must § make binding and enforceable commitments, via contractual or other legally binding instruments (This is one area of discussion) - Article 41 requires a body to monitor compliance with the Co. Co § What are the responsibilities and liabilities of this monitoring body? Co. Co V 2 is limited to the processing of Attributes which are released for enabling access to a Service - Includes many related purposes (Authorisation, Accounting/Billing, Science gateways etc. ) A new final draft being produced now for submission to Authorities at end of May 2018 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 24

Display names versus Pseudonymisation? GDPR encourages the pseudonymisation of personal data as a method of data protection - But an opaque persistent ID is still personal data (can be used to identify) - GDPR says “is not intended to preclude any other measures of data protection” The Co. Co V 2 recognises importance of: - Researcher unambiguity i. e. ensuring that a researcher’s scientific contribution is associated properly to them § notes that identifiers like ORCID are important - a name attribute (such as common. Name or Display. Name attribute) is necessary for a wiki or other collaboration platform, if the End Users know each other in real life and need to be able to transfer their existing real-world trust to an online environment 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 25

What do WLCG participants need to do? Abide by (the to be submitted, unapproved) GÉANT Data Protection Code of Conduct V 2 - And of course the GDPR itself Comment (via WLCG GDB or join SPG) on modified Data Protection Policy Framework - EOSC-hub/AARC 2 will produce draft for GDPR in coming weeks For all services which consume/process personal information directly from end-users (e. g. workload management portals, user registries, data transfer portals, GOCDB, accounting, etc) - Prepare and make easily available an updated Data Privacy statement - Template will be provided (based on GÉANT Data Protection Code of Conduct) § And updated EOSC-hub/WLCG framework WLCG (Operations? ) should create a register of all such services - Together with contact names and copies of Data Privacy statements We (EGI SPG) need to write a risk statement (for end users) – one general one - Risks to rights and freedoms are very small (only names, institutes and email addresses) We should prepare to make immediate reports following any data breach 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 26

More information on GDPR issues With many thanks to Andrew Cormack, Jisc, UK – nice recorded webinars https: //www. jisc. ac. uk/training/moving-toward-GDPR https: //community. jisc. ac. uk/blogs/regulatorydevelopments/event/webinar-gdpr-practice GDPR Regulation: https: //eur-lex. europa. eu/legal-content/EN/TXT/? uri=celex: 32016 R 0679 GÉANT Draft Data Protection Code of Conduct V 2 (29 Jan 2018): https: //wiki. refeds. org/download/attachments/1606455/G%C 3%89 ANT%20 Data%20 Protection%20 Code %20 of%20 Conduct%20 v 2_29 Jan 2018. pdf Mikael Linden (CSC, Finland) – webinar on the V 2 Code of Conduct https: //www. youtube. com/watch? v=x. F 1 L 57 Cvumg 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 27

Final words on Trust and Policy 15 years of experience (WLCG policy started in 2003) - Building Trust in collaboration with others works best § Forces us to produce general documents (of use to many) § Saves effort and improves quality - In spite of all the complaints, the IGTF X. 509 PKI has worked really well - We will continue to work with others (EOSC, WISE, IGTF, TF-CSIRT, etc. ) Auth. N/Auth. Z infrastructure (AAI) and Operational Security - The two areas where Trust matters most - Will hear about these areas next Ever-growing collaboration between Research Communities (shared IT resources) - WLCG should not “go it alone” - Trust is as important as the technology - Important that our AAI is interoperable and can easily co-exist with others 28/03/2018 Kelsey/ WLCG Security: Trust and Policies 28

Thank you for your attention Contact David. Kelsey@STFC. ac. uk Questions? eosc-hub. eu @EOSC_eu
 Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Security private
Security private Database security policy
Database security policy Bell lapadula model
Bell lapadula model Charitable work
Charitable work Microsoft azure security privacy and compliance
Microsoft azure security privacy and compliance Aws gdpr compliance
Aws gdpr compliance Kelsey wise
Kelsey wise Lingual split bone technique
Lingual split bone technique Kelsey fry technique
Kelsey fry technique Kelsey-hayes abs schematic
Kelsey-hayes abs schematic Kelsey libner
Kelsey libner Kelsey faber
Kelsey faber Chapter 7 nutrition and your fitness
Chapter 7 nutrition and your fitness Kelsey ostrowski
Kelsey ostrowski Bowdler henry technique
Bowdler henry technique Kelsey bri
Kelsey bri Boston pizza kelsey
Boston pizza kelsey Alexa bergman
Alexa bergman Bogus
Bogus Kelsey pruitt
Kelsey pruitt Kelsey cook nsf
Kelsey cook nsf Camille grammer divorce
Camille grammer divorce

















































