University of Colorado at Colorado Springs Engineering Applied















- Slides: 31

University of Colorado at Colorado Springs Engineering & Applied Science Department Cloud Computing & Security Issues Prepared by: Hamoud Al-Shammari July 25, 2011 CS 6910 Professor Chow

First Part What is Cloud Computing? n Layers of Cloud Computing. n Technical Security Issues in Cloud Computing. n Second Part What are the problems? n Opportunities for Advancement. n The Idea of PVI model. n 7/25/2011 Alshammari/Cloud Security 2

What is Cloud Computing? n It is a new paradigm for the provision of computing services. n Shifting the location of these services to the network causes reducing the costs of hardware and software resources. 7/25/2011 Alshammari/Cloud Security 3

Models of Cloud Computing 1 - Software as a Service. 2 - Platform as a Service. 3 - Infrastructure as a Service. 7/25/2011 Alshammari/Cloud Security 4

Models of Cloud Computing 1 - Software as a Service: • Provides users to use the applications online. • Ex: www. zoho. com Mail, Writer, Projects … etc. 7/25/2011 Alshammari/Cloud Security 5

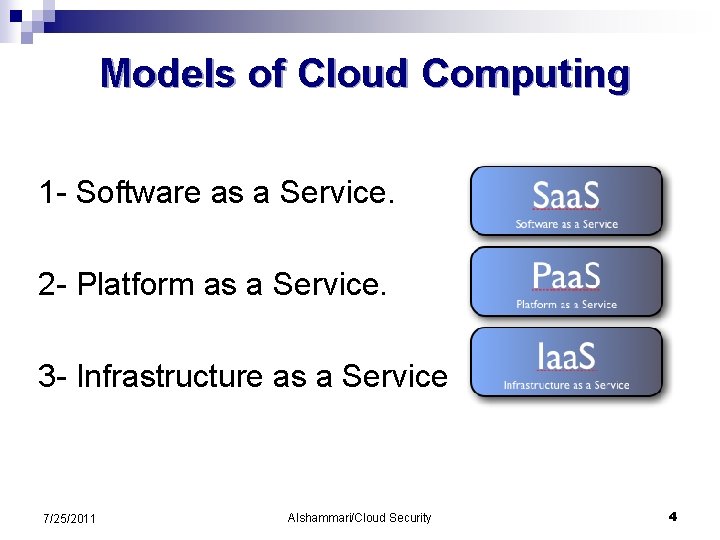
Models of Cloud Computing 2 - Platform as a Service: • To control the hosting environments to specific needs. • Ex: Google App Engine to deploy and dynamically scale Python and Java based web applications. 7/25/2011 Alshammari/Cloud Security 6

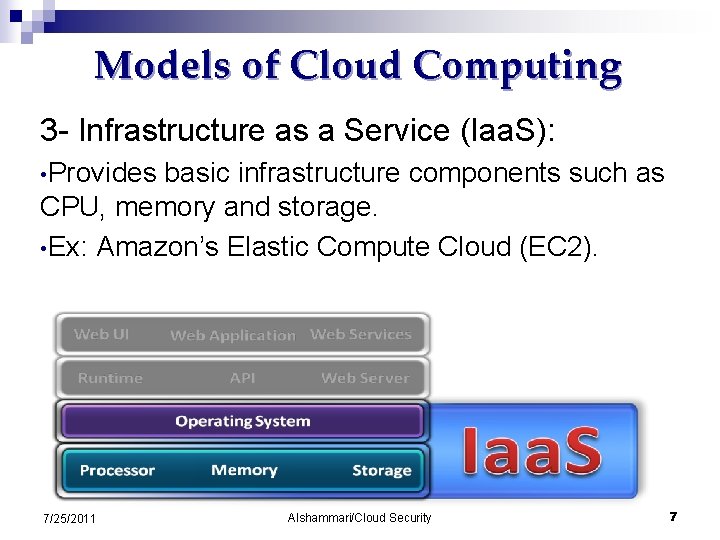
Models of Cloud Computing 3 - Infrastructure as a Service (Iaa. S): • Provides basic infrastructure components such as CPU, memory and storage. • Ex: Amazon’s Elastic Compute Cloud (EC 2). 7/25/2011 Alshammari/Cloud Security 7

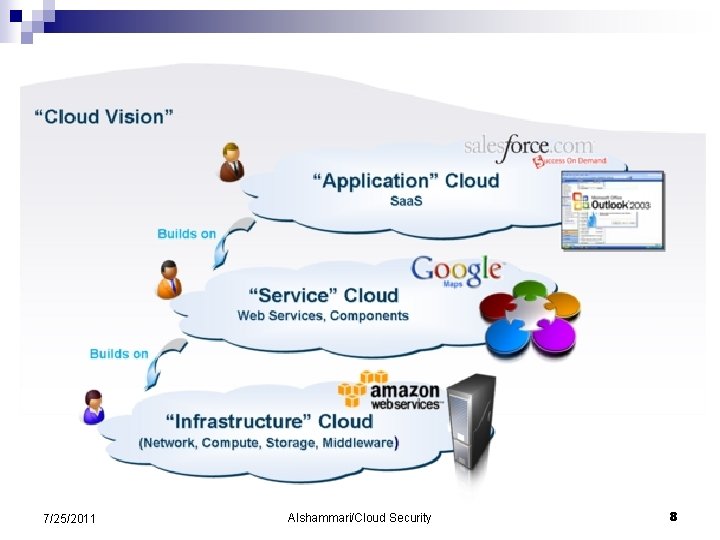
7/25/2011 Alshammari/Cloud Security 8

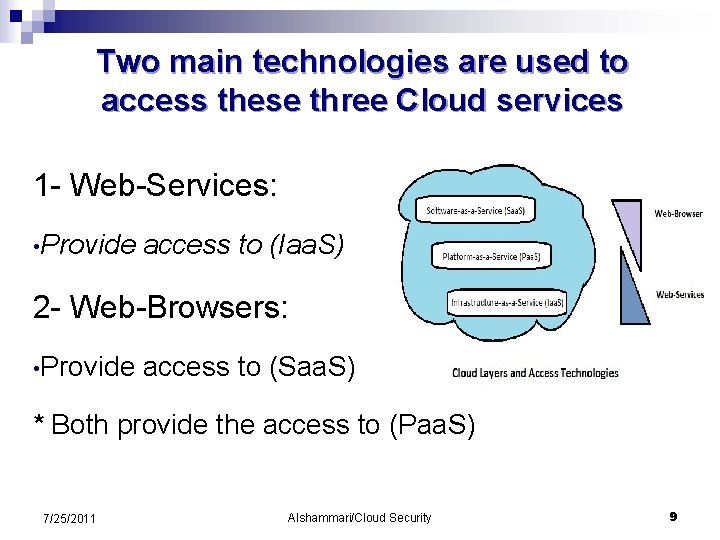
Two main technologies are used to access these three Cloud services 1 - Web-Services: • Provide access to (Iaa. S) 2 - Web-Browsers: • Provide access to (Saa. S) * Both provide the access to (Paa. S) 7/25/2011 Alshammari/Cloud Security 9

Why we use Cloud Computing? n To reduce the costs: (Pay – As – You – Go) 1 - To reduce hardware costs (Iaa. S). 2 - To reduce software license costs (Saa. S), (Paa. S). n To support the Scalable Systems: - To NOT worry about increasing of users and requests. 7/25/2011 Alshammari/Cloud Security 10

Some Technical Security Issues in Cloud Computing n Cloud Security issues focus on: 1 - Confidentiality. 2 - Integrity. 3 - Authentication. n Two places that must be secure in Cloud which are: 1 - Web-Services (WS). 2 - Web-Browser (WB). 7/25/2011 Alshammari/Cloud Security 11

1 - Web-Service Security Ø WS-Security: it is a mechanism for web service working in message level. Ø How to provide Confidentiality, Integrity, and Authentication for messages? 1 - By using XML signature: For XML fragments to be digitally signed to ensure integrity and authentication. 2 - By using XML Encryption: For XML fragments to be encrypted to ensure data confidentiality. 7/25/2011 Alshammari/Cloud Security 12

2 - Web-Browser Security Ø Also works with: 1 - XML Signature. 2 - XML Encryption. Ø Modern Web-Browser are using AJAX techniques (Asynchronous Java Scripts and XML) to develop platform independent I/O tools. Ø New names for that techniques (Web Applications, Web 2. 0, or Saa. S). 7/25/2011 Alshammari/Cloud Security 13

3 - Transport Layer Security (TLS) OR Secure Sockets Layer (SSL) 1 - Record Layer: Encrypts/Decrypts TCP data stream. 2 - TLS Handshake: Used to authenticate the server and the client. ØSSL became the most important cryptographic protocol worldwide, because it is implemented in every web browser. 7/25/2011 Alshammari/Cloud Security 14

4 - Cloud Malware Injection Attack Ø Attacker adds his own system to the Cloud system. Ø To Solve the PROBLEM: Ø Store a hash value in the cloud and compare any new service or request with the hash value. Ø WHAT if the attacker can create a valid hash value !!! 7/25/2011 Alshammari/Cloud Security 15

5 - Flooding Attacks Ø Ø Ø Attacker sends a huge amount of nonsense requests to a certain service which make the problem by having the data traffic of different time zones operated by the same server. That cause, the servers will NOT serve the other requests from another users. To Solve The PROBLEM: Ø Cloud Computing enables a dynamic adaptation of hardware requirements to the actual workload occurring by using Virtual Machines (VM). 7/25/2011 Alshammari/Cloud Security 16

Second Part “What are the problems? ” 7/25/2011 Alshammari/Cloud Security 17

What is the problem with Web-Services? Ø XML Signature Element Wrapping: Ø SOAP messages are generally transmitted through HTTP protocol with an XML format. Ø Ø Attacker is able to manipulate a SOAP messages by copying the target element and inserting another value and moving the original element to somewhere on the SOAP message. To Solve The Problem: Ø Using a combination of WS-Security with XML signature to sign particular element and digital certificated such as X. 509. Ø Create a list of elements that is used in the system, and reject any other messages. 7/25/2011 Alshammari/Cloud Security 18

What is the problem with Web-Browser? Ø The web-Browsers are not able to apply WS-Security concepts (XML signature and XML encryption). BECAUSE: 1 - Data can only be encrypted through (TLS) which is Transport Layer Security. 2 - XML signatures are only used within the (TLS) handshake. 7/25/2011 Alshammari/Cloud Security 19

What is the problem with TSL/SSL? Ø The TSL/SSL technique is point-to-point. Ø Messages will be Encrypted and Decrypted many times in the process. Ø possibility of breaking the security between the browser and the clouds. Ø Then, attacker can get the DECRYPTED message and change it ! 7/25/2011 Alshammari/Cloud Security 20

Opportunities for Advancement 1 - For the problems in Web-Browsers / SSL ØCreate new web browsers that apply WS-Security concepts. ØThe WS-Security works in message level, so it appears to be more suitable than SSL/TLS. ØThen, these web browsers are able to use XML Encryption in order to provide end-to-end encryption in SOAP messages. 7/25/2011 Alshammari/Cloud Security 21

Opportunities for Advancement 2 - Private Virtual Infrastructure (PVI) ØUsually, cloud computing place an organization’s data in the control of a third party. ØPVI model is designed to separate the duties between the users and the providers: 1 - The PVI datacenter is under control of the information owner. 2 - The cloud fabric is under control of the service provider. 7/25/2011 Alshammari/Cloud Security 22

Opportunities for Advancement Private Virtual Infrastructure (PVI) ØClient CANNOT manipulate the security settings of the fabric. ØClient CAN remove, destroy, or lock down their data at any time. ØThe Service Level Agreement (SLA) between the user and the provider determines the responsibilities of all parties. ØIn this model Client needs to: 1 - Vision into the security settings and configuration of the fabric. 2 - Communicate to VPI through virtual private network and all links should be encrypted with tunnels like SSL. 7/25/2011 Alshammari/Cloud Security 23

Opportunities for Advancement Private Virtual Infrastructure (PVI) ØTrusted Computing: Ø Providers are required to use trusted computing technologies, so organizations can verify their security posture in the cloud and control their information. Ø The key component here is Trusted Platform Model (TPM) which is a cryptographic component that stores cryptographic keys. Ø Cryptographic keys can be used to attest the operating state of the platform. Ø Platform Configuration Registers (PCRs) are places where cryptographic keys are stored in. 7/25/2011 Alshammari/Cloud Security 24

Opportunities for Advancement Private Virtual Infrastructure (PVI) ØTrusted Computing: Ø PROBLEM with TPM: it only works for non-virtualized environment. Ø Virtual TPM (VTPM): is implemented by providing software instances of TPMs for each virtual machine. Ø The developers here developed an architecture that secures each VM by coupling a VTPM in its own sub domain called Locator Bot (Lo. Bot). Ø Lo. Bot allows each VM to be verifiable by its owner and provide secure provisioning and migration of the VM within the cloud as well. 7/25/2011 Alshammari/Cloud Security 25

Opportunities for Advancement Private Virtual Infrastructure (PVI) ØFive Tenets of Cloud Computing: 1 - Trusted Cloud Platform: the provider needs to provide security services which protect and monitor the fabric. 2 - PVI Factory: - The most sensitive component of PVI. - It is the root authority for: - Provisioning. - VTPM key generation. - Certificate generation & management. - Should be under full control of the information owner. - It serves as the controller and policy decision point for the PVI. 7/25/2011 Alshammari/Cloud Security 26

Opportunities for Advancement Private Virtual Infrastructure (PVI) 3 - Measurement and Secure Provisioning: -Providers must allow clients transparent insight into their infrastructures. -Lo. Bot can perform the fabric pre-measurement which allows PVI to share the responsibility of security management. -Lo. Bot is a VM architecture and secure transfer protocol based on VTPM. 4 - Secure Shutdown and Data Destruction: -This process is required to ensure all sensitive data is removed before new processes are allowed to run on it. -The PROBLEM: the VM do not provide that, so the authors recommended to enclose that on future VM monitors or through Lo. Bot. 7/25/2011 Alshammari/Cloud Security 27

Opportunities for Advancement Private Virtual Infrastructure (PVI) 5 - Monitoring and Auditing: -Lo. Bot provide continuous monitoring of the cloud environment. -Clients provide the auditing process. -But with that number of users and amount of information the legal using of the information will be decreased. -The authors recommend the sharing of auditing responsibilities between the service providers and clients. -Locator Bot (Lo. Bot) is the authors’ architecture and protocol for secure provisioning and secure migration of virtual machines within an Iaa. S cloud. Lo. Bot provides many other security features for PVI such as environmental monitoring, tamper detection and secure shutdown. 7/25/2011 Alshammari/Cloud Security 28

Conclusion Two main technical security points: 1. WS-Security Mechanism: XML Signature. Ø XML Encryption. With developing new browsers this mechanism might be applied. Ø 2. Ø Ø Private Virtual Infrastructure (PVI) Model: Ø Duties between provider and client. Ø Locator Bot (Lo. Bot). Because users are part of the solution, this model will face many problems to be applied well. 7/25/2011 Alshammari/Cloud Security 29

References 1. Cloud Computing: Security Risk. La’Quata Sumter, Department of Computer and Information Sciences. Florida A&M University. 1. Infrastructure As A Service Security: Challenges and Solutions. Wesam Dawoud, Ibrahim Takouna, Christoph Meinel, Hasso Platter Institute. Postdam, Germany. 2. On Technical Security Issues in Cloud Computing. M. Jensen, J. Schwenk. Horst Gortz Institute for IT Security, Ruhr University Bochum, Germany. 3. Private Virtual Infrastructure for Cloud Computing. F. John Krautheim. University of Maryland. 4. Security Issues In Cloud Computing and Countermeasures. D. Jamil, H. Zaki. University of Engineering and Technology. Karachi, Pakistan. 7/25/2011 Alshammari/Cloud Security 30

Cloud Computing & Security Issues Thank you
 Mt st francis colorado springs
Mt st francis colorado springs Colorado springs school districts
Colorado springs school districts Brandon monson colorado springs
Brandon monson colorado springs Aaron choate colorado springs
Aaron choate colorado springs Audrey field
Audrey field Cloud computing colorado springs
Cloud computing colorado springs Recycled asphalt colorado springs
Recycled asphalt colorado springs Norwood development colorado springs
Norwood development colorado springs Rio grande
Rio grande Applied geotechnical engineering
Applied geotechnical engineering Principles of applied engineering
Principles of applied engineering Fu foundation school of engineering
Fu foundation school of engineering Uc ceas
Uc ceas Gerling applied engineering
Gerling applied engineering Van hall larenstein university of applied sciences
Van hall larenstein university of applied sciences Vaasa university of applied sciences
Vaasa university of applied sciences Oulu university of applied sciences
Oulu university of applied sciences Fh triesdorf agrartechnik
Fh triesdorf agrartechnik Kodolanyi janos university budapest campus
Kodolanyi janos university budapest campus Western norway university of applied sciences
Western norway university of applied sciences Esslingen university of applied science
Esslingen university of applied science Piraeus university of applied sciences
Piraeus university of applied sciences Jade university of applied sciences
Jade university of applied sciences Iuas
Iuas Eberswalde university of applied sciences
Eberswalde university of applied sciences University of manitoba applied business management
University of manitoba applied business management University of applied sciences cologne
University of applied sciences cologne International university of applied sciences bad honnef
International university of applied sciences bad honnef Brock university applied linguistics
Brock university applied linguistics Subu mkm
Subu mkm Piramk
Piramk University of eastern colorado firewatch
University of eastern colorado firewatch