The Role of Intrusion Detection Systems IDSs Presentation








- Slides: 14

The Role of Intrusion Detection Systems (IDSs) Presentation: - Ali Ardalan - October 12 th, 2000 Article Authors: - John Mc. Hugh - Alan Christie - Julia Allen

Article Overview “This article considers the role of IDS’s in an organization’s overall defensive posture and provides guidelines for IDS deployment, operation & maintenance. ”

Intrusion Detection Historical Context Yesterday: – Early hackers were simply interested in proving that they could break into systems – 1980, John Anderson’s - Computer Security Threat Monitoring & Surveillance – 1987, Dorothy Denning’s - An Intrusion Detection Model Today: – Hackers of today are motivated by financial, political and military objectives

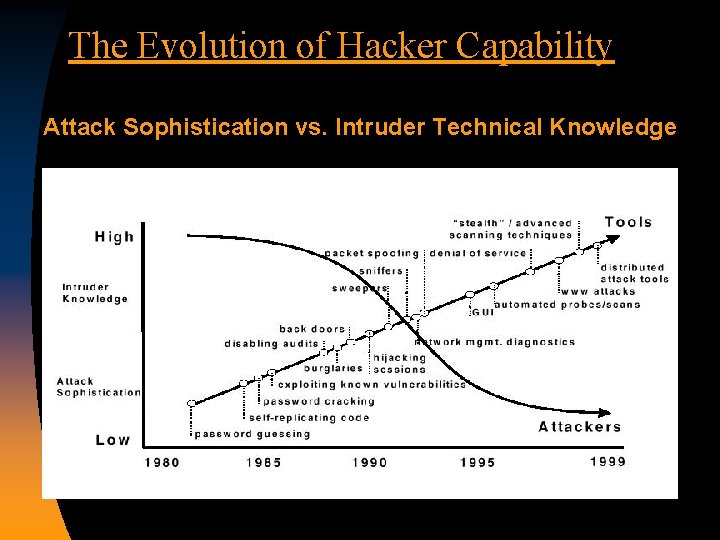
The Evolution of Hacker Capability Attack Sophistication vs. Intruder Technical Knowledge

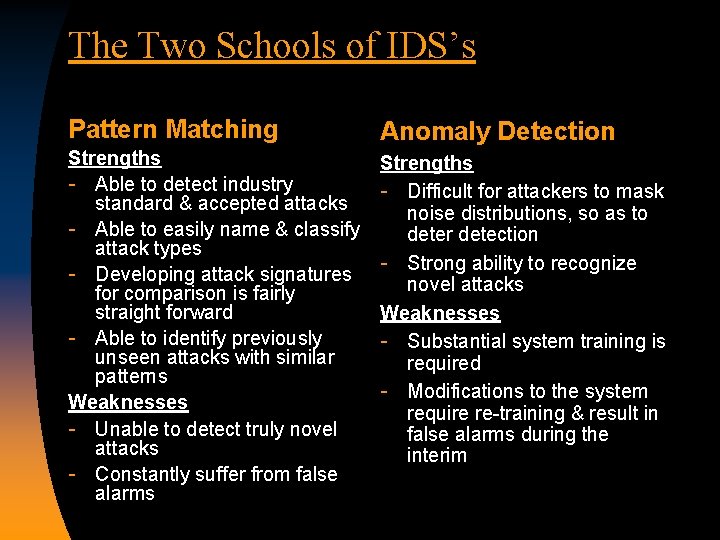
The Two Schools of IDS’s Pattern Matching Anomaly Detection Strengths - Able to detect industry standard & accepted attacks - Able to easily name & classify attack types - Developing attack signatures for comparison is fairly straight forward - Able to identify previously unseen attacks with similar patterns Weaknesses - Unable to detect truly novel attacks - Constantly suffer from false alarms Strengths - Difficult for attackers to mask noise distributions, so as to deter detection - Strong ability to recognize novel attacks Weaknesses - Substantial system training is required - Modifications to the system require re-training & result in false alarms during the interim

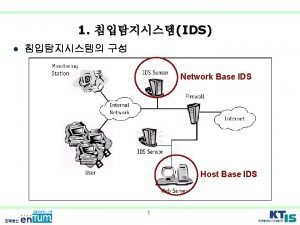
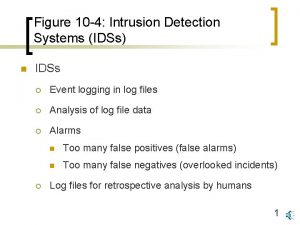
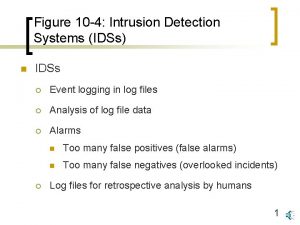
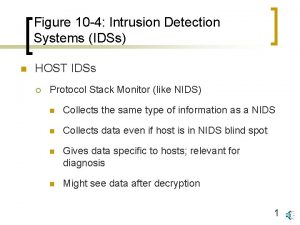
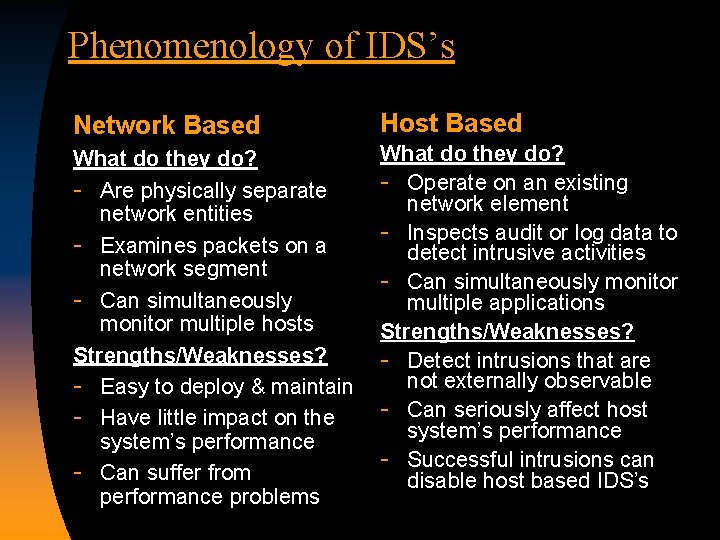
Phenomenology of IDS’s Network Based Host Based What do they do? - Are physically separate network entities - Examines packets on a network segment - Can simultaneously monitor multiple hosts Strengths/Weaknesses? - Easy to deploy & maintain - Have little impact on the system’s performance - Can suffer from performance problems What do they do? - Operate on an existing network element - Inspects audit or log data to detect intrusive activities - Can simultaneously monitor multiple applications Strengths/Weaknesses? - Detect intrusions that are not externally observable - Can seriously affect host system’s performance - Successful intrusions can disable host based IDS’s

A Properly Deployed IDS #1 Can recognize both intrusions and DOS activities and invoke countermeasures against them in real time. #2 Can provide warnings that the system is under attack, even when not vulnerable. #3 Can confirm secure configuration and operation of other security mechanisms such as firewalls. #4 Can collect forensic information during an attack allowing for future location & prosecution of intruders.

A Suggested Security Solution: Make Intruder Tasks Substantially More Difficult: – – – – Configure inner network sensors to recognize intrusive & unexpected protocols Place external sensors beyond firewalls to validate firewall rules Configure host based sensors on servers, looking for abnormal behavior by applications and within the operating system Install a well designed network of multiple firewalls Adhere to a clearly defined mission-specific security policy Remove ability to use all unneeded services Regularly use of integrity checking tools Minimize vulnerability by constantly applying updates & patches

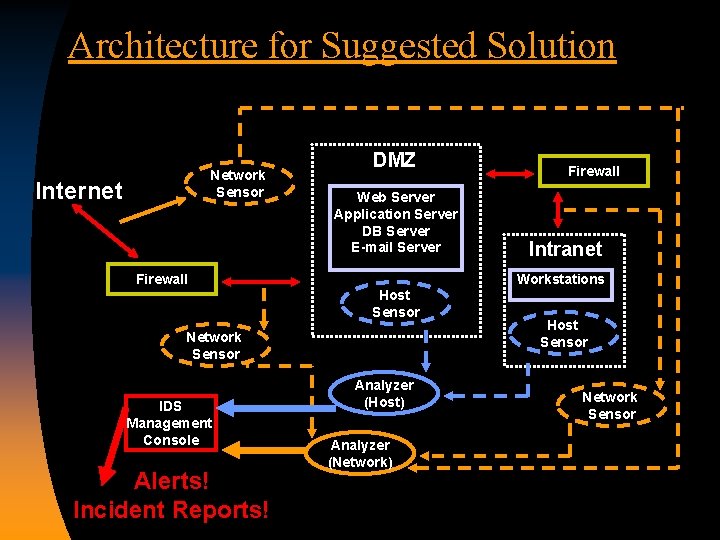
Architecture for Suggested Solution Network Sensor Internet Firewall DMZ Web Server Application Server DB Server E-mail Server Host Sensor Network Sensor IDS Management Console Alerts! Incident Reports! Analyzer (Host) Analyzer (Network) Firewall Intranet Workstations Host Sensor Network Sensor

The IDS Landscape • • • Vendors frequently release new IDS products Vendors aggressively compete for market share, buy out each other and discontinue IDS product lines. There are no Industry Standards for Comparison This are very little objective third party evaluations IDS Marketing literature is vague, not clear Work required to use & maintain IDS systems – Metrics for proper functioning & false alarms… –

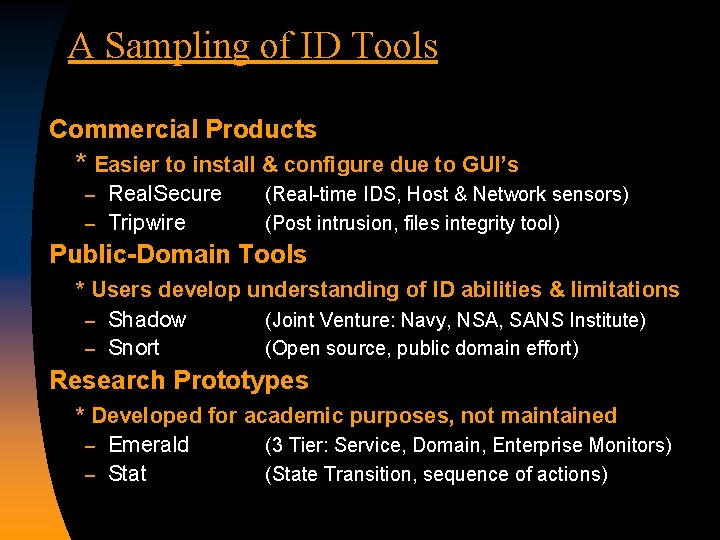
A Sampling of ID Tools Commercial Products * Easier to install & configure due to GUI’s Real. Secure – Tripwire – (Real-time IDS, Host & Network sensors) (Post intrusion, files integrity tool) Public-Domain Tools * Users develop understanding of ID abilities & limitations – Shadow (Joint Venture: Navy, NSA, SANS Institute) – Snort (Open source, public domain effort) Research Prototypes * Developed for academic purposes, not maintained – Emerald (3 Tier: Service, Domain, Enterprise Monitors) – Stat (State Transition, sequence of actions)

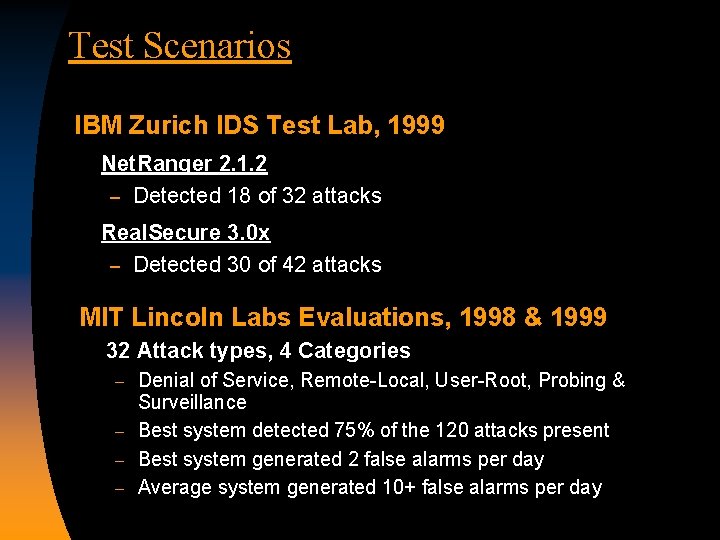
Test Scenarios IBM Zurich IDS Test Lab, 1999 Net. Ranger 2. 1. 2 – Detected 18 of 32 attacks Real. Secure 3. 0 x – Detected 30 of 42 attacks MIT Lincoln Labs Evaluations, 1998 & 1999 32 Attack types, 4 Categories Denial of Service, Remote-Local, User-Root, Probing & Surveillance – Best system detected 75% of the 120 attacks present – Best system generated 2 false alarms per day – Average system generated 10+ false alarms per day –

IDS’s, the Next Target for Attack Smart attackers will attack the IDS’s – Disable IDS entirely – Trick IDS’s into providing false information Necessity for Protection of IDS’s – Encryption of Log Files – Proper setting of IDS access controls – Regular integrity checks of IDS Files

Article Conclusions • • “ID technology is immature and its effectiveness is limited” “Much of the current effort seems to be aimed at detecting attacks made by relatively unskilled and unfocused attackers. ” Anticipate modest improvement in actual algorithms for IDS High expectations for improvements in detection and false alarms due to research in multiple sensor correlation
 Intrusion detection systems (ids)
Intrusion detection systems (ids) Firewalls and intrusion detection systems
Firewalls and intrusion detection systems Fiber perimeter intrusion detection systems
Fiber perimeter intrusion detection systems Intrusion prevention system open source
Intrusion prevention system open source Common intrusion detection framework
Common intrusion detection framework Bro intrusion detection
Bro intrusion detection Infrasonic intrusion detection
Infrasonic intrusion detection Id=idss(1-vgs/vp)^2
Id=idss(1-vgs/vp)^2 Id=idss(1-vgs/vp)^2
Id=idss(1-vgs/vp)^2 Isuzu g-idss
Isuzu g-idss Id=idss(1-vgs/vp)^2
Id=idss(1-vgs/vp)^2 Idss.com
Idss.com Weather detection systems
Weather detection systems Azure web role worker role example
Azure web role worker role example Role making krappmann
Role making krappmann