Figure 10 4 Intrusion Detection Systems IDSs n

- Slides: 8

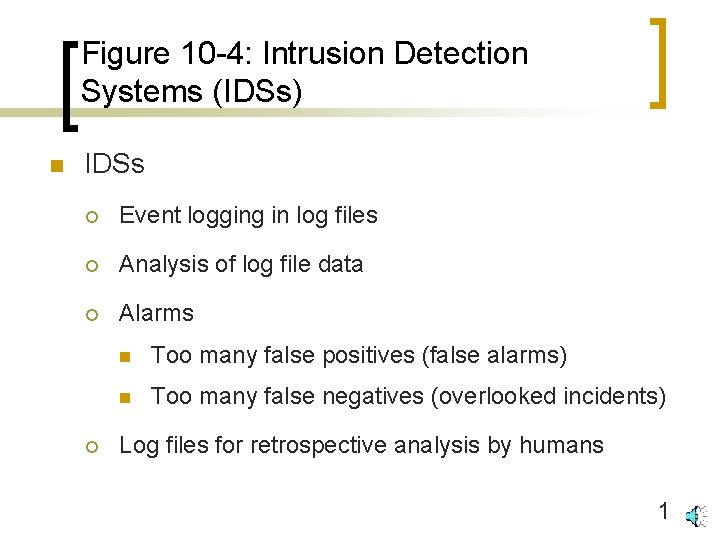
Figure 10 -4: Intrusion Detection Systems (IDSs) n IDSs ¡ Event logging in log files ¡ Analysis of log file data ¡ Alarms ¡ n Too many false positives (false alarms) n Too many false negatives (overlooked incidents) Log files for retrospective analysis by humans 1

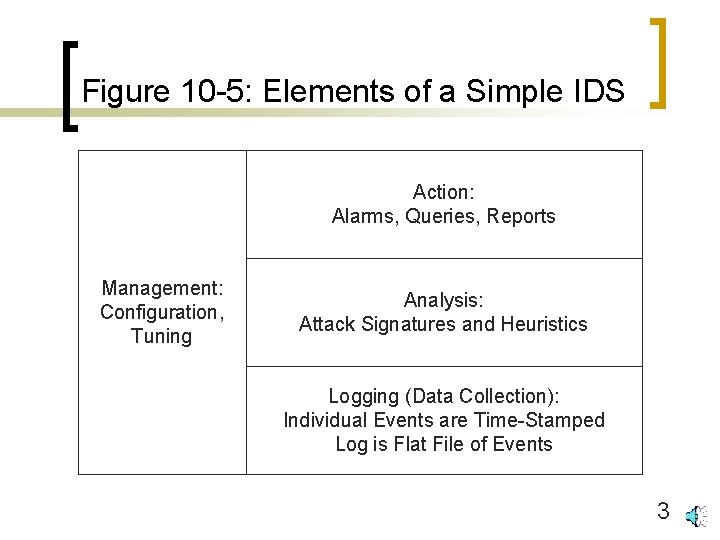
Figure 10 -4: Intrusion Detection Systems (IDSs) n Elements of an IDS (Figure 10 -5) ¡ Event logging ¡ Analysis method ¡ Action ¡ Management 2

Figure 10 -5: Elements of a Simple IDS Action: Alarms, Queries, Reports Management: Configuration, Tuning Analysis: Attack Signatures and Heuristics Logging (Data Collection): Individual Events are Time-Stamped Log is Flat File of Events 3

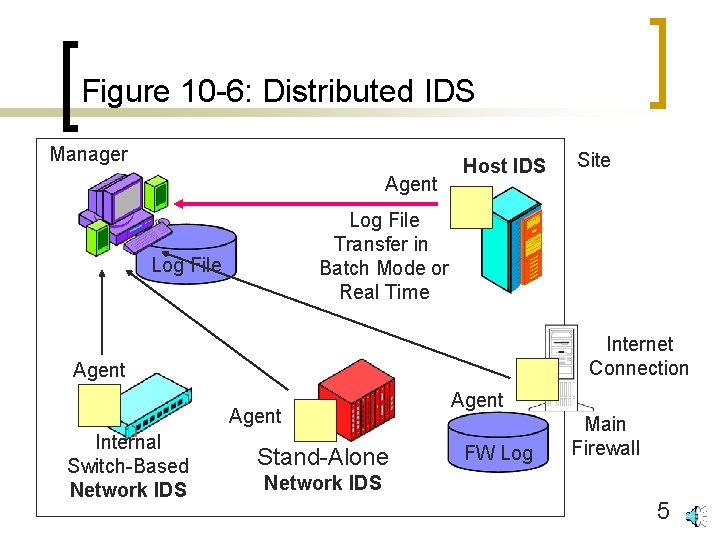
Figure 10 -4: Intrusion Detection Systems (IDSs) n Distributed IDSs (Figure 10 -6) ¡ Managers ¡ Agents ¡ Distribution of functionality between agents and managers (analysis and action) 4

Figure 10 -6: Distributed IDS Manager Agent Host IDS Log File Transfer in Batch Mode or Real Time Log File Internet Connection Agent Internal Switch-Based Network IDS Site Stand-Alone Agent FW Log Main Firewall Network IDS 5

Figure 10 -4: Intrusion Detection Systems (IDSs) n Distributed IDSs (Figure 10 -6) ¡ Batch versus Real-Time Data Transfer n Batch mode: Every few minutes or hours; efficient n Real-time: As events occur or shortly afterward; little or no data loss if attacker eliminates log file on agent’s computer 6

Figure 10 -4: Intrusion Detection Systems (IDSs) n n Distributed IDSs (Figure 10 -6) ¡ Secure manager-agent communication ¡ Vendor’s automatic updates with secure communication Network IDSs (NIDSs) ¡ Capture packets ¡ Stand-alone NIDS collects data for only its portion of the network ¡ Switch or router NIDSs can collect data on all ports 7

Figure 10 -4: Intrusion Detection Systems (IDSs) n Network IDSs (NIDSs) ¡ ¡ NIDS placement n Between main firewall and internal or external network for relevant or all attacks n At internal points to detect internal mischief Weaknesses n Blind spots in network where no NIDS data is collected n Cannot filter encrypted packets 8