Supply Chain Risk Management SCRM Response Plan RP











- Slides: 25

Supply Chain Risk Management (SCRM) Response Plan (RP) Training IT Security Category Guide to the ITC SCRM RP Cybersecurity Acquisition Training Overview (CATO) Information Technology Category (ITC) IT Security Subcategory 20 Nov 2017

Intended Audience Who should take this training? IT Security Category professionals responsible for handling suspected or confirmed supply chain incidents that affect Information and Communications Technology (ICT) products. 01 Contracting Professionals 02 Communication Professionals 03 04 Incident Response Professionals Responsible for managing contracts and overseeing the implementation (e. g. , Contracting Officer [CO] and Contracting Officer’s Representative [COR]). In regard to the supply chain, Contracting Professionals in collaboration with the Chief Information Security Officer (CISO) ensure agency’s contracting policies and contracts adequately address the supply chain risk management requirements. Responsible for the building and development of relations between the General Services Administration (GSA) and its customers, politicians, government agencies, and other decision-makers. Responsible for handling an event in a way that limits damage and reduces recovery time and costs. Program and Project Managers (P/PMs) Responsible for performing program and project management activities and functions in developing accurate government requirements, defining measurable performance standards, and managing life cycle activities to ensure that intended outcomes are achieved.

Introduction Background and Purpose Definitions Key Definitions and Terminology, Event Escalation Roles and Responsibilities Entities Responsible for Incident Handling Notification Types and Events SCRM RP Process and Response Times SCRM RP Framework, Response and Resolution Times for Incidents Agenda

Introduction Background and Purpose Attacks and disruptions to complex supply chains for ICT products are increasingly gaining attention. Incidents, such as the Target breach, the Havex series of attacks on the energy infrastructure, and the disclosed series of intrusions affecting Department of Defense (Do. D) U. S. Transportation Command (TRANSCOM) contractors, highlight SCRM as a cross-cutting cybersecurity problem. In response to these threats, the Office of Information Technology (IT) Security Category developed the SCRM RP to address the risk to the federal supply chain. The IT Security Category regularly practices the RP to update and refine the process based on lessons learned and industry feedback. This training provides: ü The different roles and responsibilities in managing and handling incidents. ü A framework for organizing the SCRM Response Team (RT), key contacts, and supporting materials to assist in managing and executing the incident response. ü SCRM RP best practices. NOTE: ITC has a specific incident response plan to manage the potential threats, impacts, and countermeasures of product tampering and counterfeit incidents. In short, this training material can be used as the IT Security Category’s SCRM response guide that provides the tasks and activities for identifying, evaluating, mitigating, and monitoring ICT supply chain events.

Definitions Key Definitions and Terminology § Supply Chain Threat Event (SCTE): Any observable occurrence, not yet assessed, that may affect the security of an ICT supply chain or that prompts a SCRM External Notification (Ex. NOTE), SCRM Internal Notification (i. NOTE), SCRM External Query (Ex. Q) or SCRM Internal Query (i. Q). § Query: A question addressed to an official or organization. § Incident: An adverse event in a product or the threat of such an event’s occurrence. § Tampering Incident: The intentional modification of products in a way that would make them harmful to the consumer. § Counterfeiting Incident: An unauthorized copy or substitute that has been identified, marked, and/or altered by a source other than the item’s legally authorized source and has been misrepresented to be an authorized item of the legally authorized source. § Vendor: A supplier, system integrator or external provider of products. § Customer: Any person or organization that purchases products through GSA.

Definitions Key Definitions and Terminology (continued) § Third Party: Any person or group besides the two primarily involved in a situation. This may include an external or internal GSA source. An external source may be a reporter or congressman. An internal source may include the GSA Office of Strategic Communications (OSC), Inspector General (IG), Chief Information Officer (CIO) or CO. § Impact: A measure of the effect of an incident. § Response Time: A measure of the time taken to complete a query. § Resolution Time: The time that elapses between acknowledged receipt of an incident and incident resolution. § Priority: A category used to identify the relative importance of an incident. § Hierarchical Escalation (also known as Fast Track): Engaging senior levels of management to oversee and coordinate the SCRM RP. § Functional Escalation: Transferring an incident to a technical team with a higher level of expertise to execute the response plan tasks.

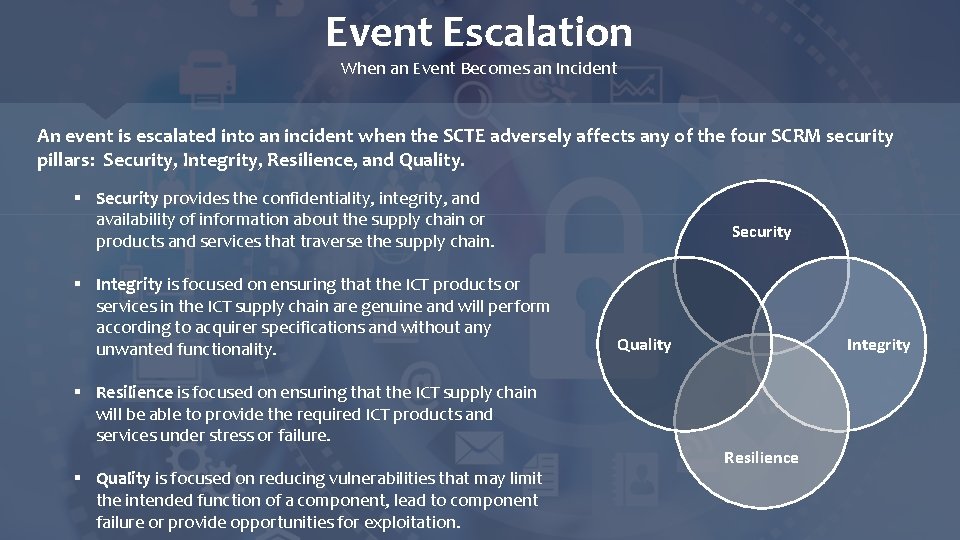
Event Escalation When an Event Becomes an Incident An event is escalated into an incident when the SCTE adversely affects any of the four SCRM security pillars: Security, Integrity, Resilience, and Quality. § Security provides the confidentiality, integrity, and availability of information about the supply chain or products and services that traverse the supply chain. § Integrity is focused on ensuring that the ICT products or services in the ICT supply chain are genuine and will perform according to acquirer specifications and without any unwanted functionality. § Resilience is focused on ensuring that the ICT supply chain will be able to provide the required ICT products and services under stress or failure. § Quality is focused on reducing vulnerabilities that may limit the intended function of a component, lead to component failure or provide opportunities for exploitation. Security Quality Integrity Resilience

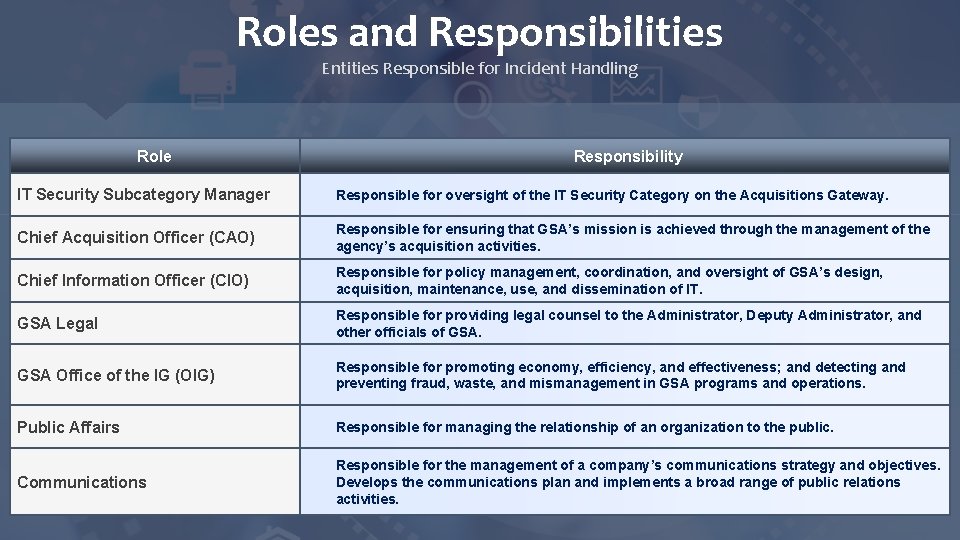
Roles and Responsibilities Entities Responsible for Incident Handling Role Responsibility IT Security Subcategory Manager Responsible for oversight of the IT Security Category on the Acquisitions Gateway. Chief Acquisition Officer (CAO) Responsible for ensuring that GSA’s mission is achieved through the management of the agency’s acquisition activities. Chief Information Officer (CIO) Responsible for policy management, coordination, and oversight of GSA’s design, acquisition, maintenance, use, and dissemination of IT. GSA Legal Responsible for providing legal counsel to the Administrator, Deputy Administrator, and other officials of GSA Office of the IG (OIG) Responsible for promoting economy, efficiency, and effectiveness; and detecting and preventing fraud, waste, and mismanagement in GSA programs and operations. Public Affairs Responsible for managing the relationship of an organization to the public. Communications Responsible for the management of a company’s communications strategy and objectives. Develops the communications plan and implements a broad range of public relations activities.

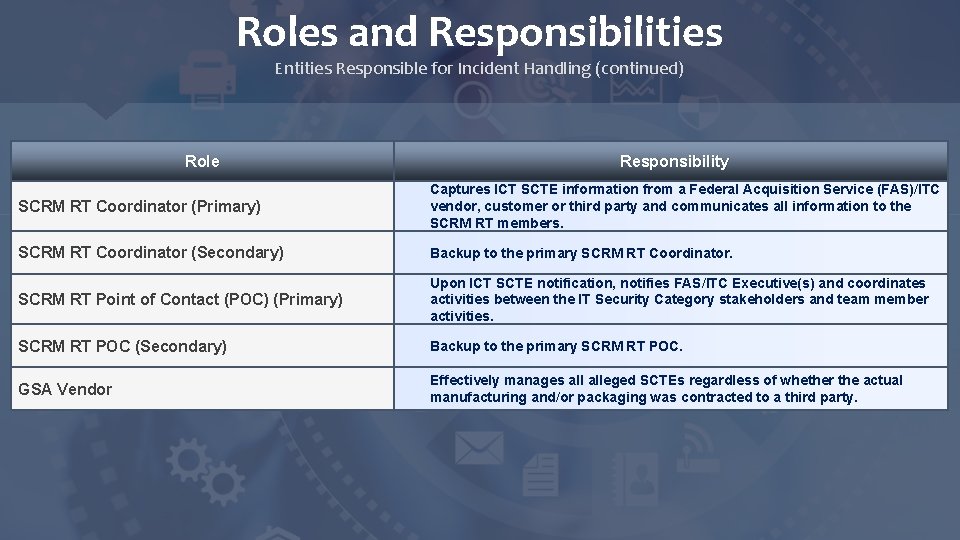
Roles and Responsibilities Entities Responsible for Incident Handling (continued) Role Responsibility SCRM RT Coordinator (Primary) Captures ICT SCTE information from a Federal Acquisition Service (FAS)/ITC vendor, customer or third party and communicates all information to the SCRM RT members. SCRM RT Coordinator (Secondary) Backup to the primary SCRM RT Coordinator. SCRM RT Point of Contact (POC) (Primary) Upon ICT SCTE notification, notifies FAS/ITC Executive(s) and coordinates activities between the IT Security Category stakeholders and team member activities. SCRM RT POC (Secondary) Backup to the primary SCRM RT POC. GSA Vendor Effectively manages alleged SCTEs regardless of whether the actual manufacturing and/or packaging was contracted to a third party.

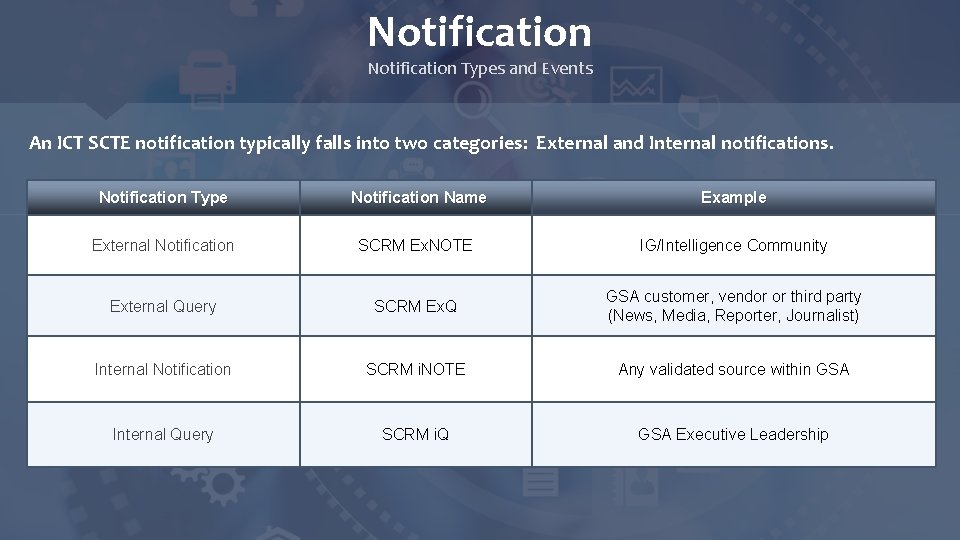
Notification Types and Events An ICT SCTE notification typically falls into two categories: External and Internal notifications. Notification Type Notification Name Example External Notification SCRM Ex. NOTE IG/Intelligence Community External Query SCRM Ex. Q GSA customer, vendor or third party (News, Media, Reporter, Journalist) Internal Notification SCRM i. NOTE Any validated source within GSA Internal Query SCRM i. Q GSA Executive Leadership

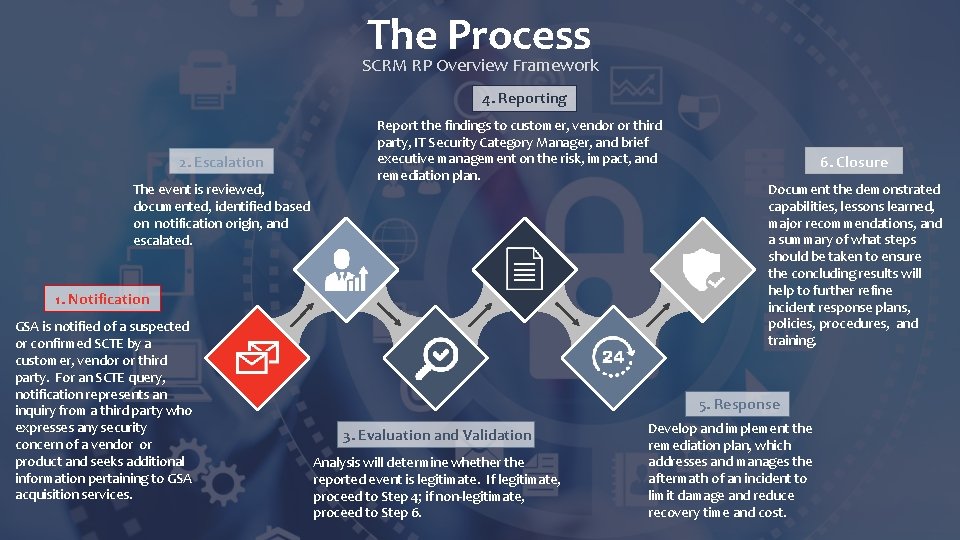
The Process SCRM RP Overview Framework 4. Reporting 2. Escalation The event is reviewed, documented, identified based on notification origin, and escalated. Report the findings to customer, vendor or third party, IT Security Category Manager, and brief executive management on the risk, impact, and remediation plan. 1. Notification GSA is notified of a suspected or confirmed SCTE by a customer, vendor or third party. For an SCTE query, notification represents an inquiry from a third party who expresses any security concern of a vendor or product and seeks additional information pertaining to GSA acquisition services. 6. Closure Document the demonstrated capabilities, lessons learned, major recommendations, and a summary of what steps should be taken to ensure the concluding results will help to further refine incident response plans, policies, procedures, and training. 5. Response 3. Evaluation and Validation Analysis will determine whether the reported event is legitimate. If legitimate, proceed to Step 4; if non-legitimate, proceed to Step 6. Develop and implement the remediation plan, which addresses and manages the aftermath of an incident to limit damage and reduce recovery time and cost.

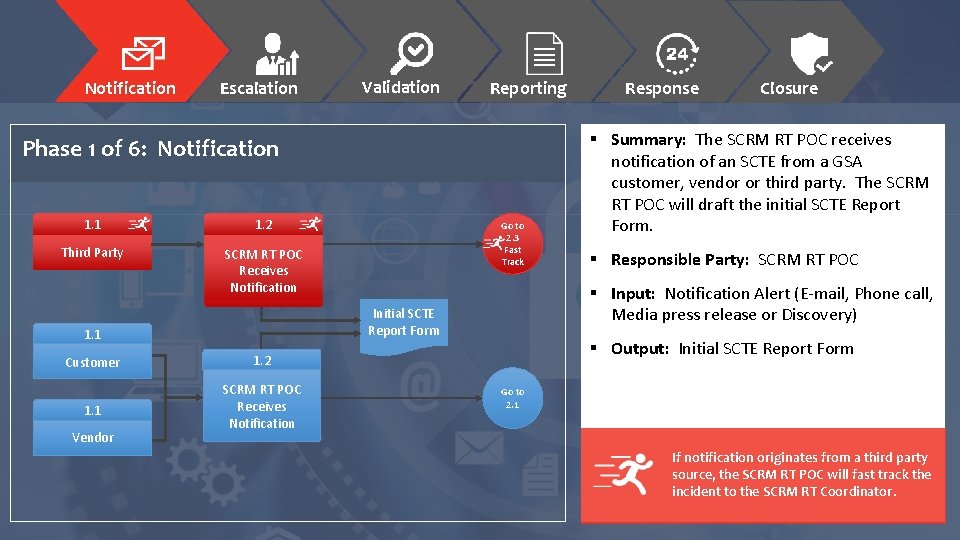
Notification Escalation Validation Reporting Phase 1 of 6: Notification 1. 1 1. 2 Third Party SCRM RT POC Receives Notification Customer 1. 2 1. 1 SCRM RT POC Receives Notification Closure § Summary: The SCRM RT POC receives notification of an SCTE from a GSA customer, vendor or third party. The SCRM RT POC will draft the initial SCTE Report Form. § Responsible Party: SCRM RT POC § Input: Notification Alert (E-mail, Phone call, Media press release or Discovery) Initial SCTE Report Form 1. 1 Vendor Go to 2. 3 Fast Track Response § Output: Initial SCTE Report Form Go to 2. 1 If notification originates from a third party source, the SCRM RT POC will fast track the incident to the SCRM RT Coordinator.

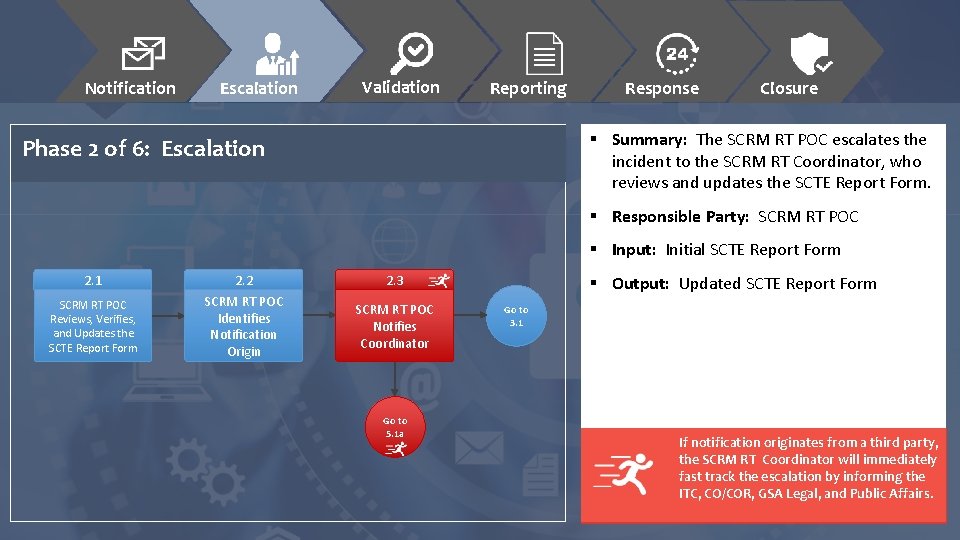
Notification Escalation Validation Reporting Response Closure § Summary: The SCRM RT POC escalates the incident to the SCRM RT Coordinator, who reviews and updates the SCTE Report Form. Phase 2 of 6: Escalation § Responsible Party: SCRM RT POC § Input: Initial SCTE Report Form 2. 1 SCRM RT POC Reviews, Verifies, and Updates the SCTE Report Form 2. 2 SCRM RT POC Identifies Notification Origin 2. 3 SCRM RT POC Notifies Coordinator Go to 5. 1 a § Output: Updated SCTE Report Form Go to 3. 1 If notification originates from a third party, the SCRM RT Coordinator will immediately fast track the escalation by informing the ITC, CO/COR, GSA Legal, and Public Affairs.

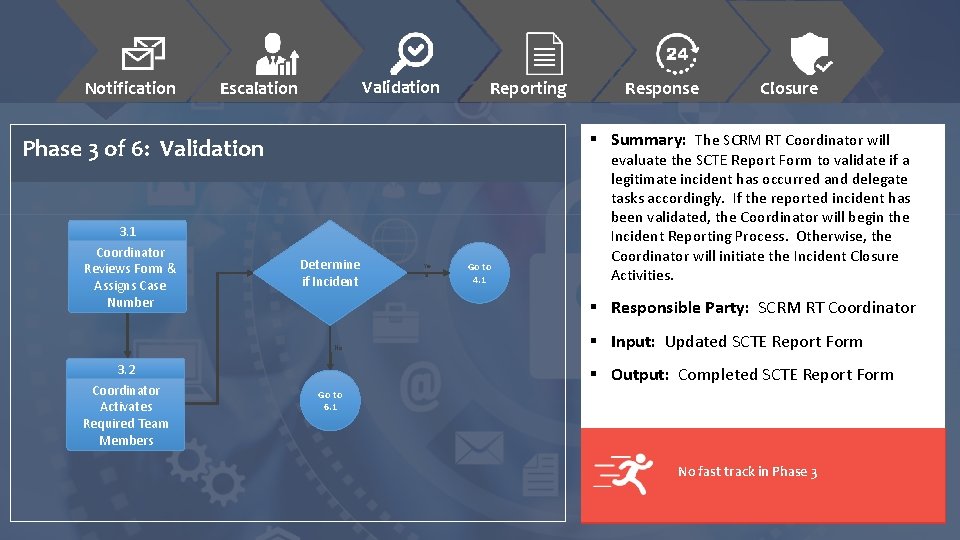
Notification Validation Escalation Reporting Determine if Incident Ye s Go to 4. 1 evaluate the SCTE Report Form to validate if a legitimate incident has occurred and delegate tasks accordingly. If the reported incident has been validated, the Coordinator will begin the Incident Reporting Process. Otherwise, the Coordinator will initiate the Incident Closure Activities. § Responsible Party: SCRM RT Coordinator No 3. 2 Coordinator Activates Required Team Members Closure § Summary: The SCRM RT Coordinator will Phase 3 of 6: Validation 3. 1 Coordinator Reviews Form & Assigns Case Number Response § Input: Updated SCTE Report Form § Output: Completed SCTE Report Form Go to 6. 1 No fast track in Phase 3

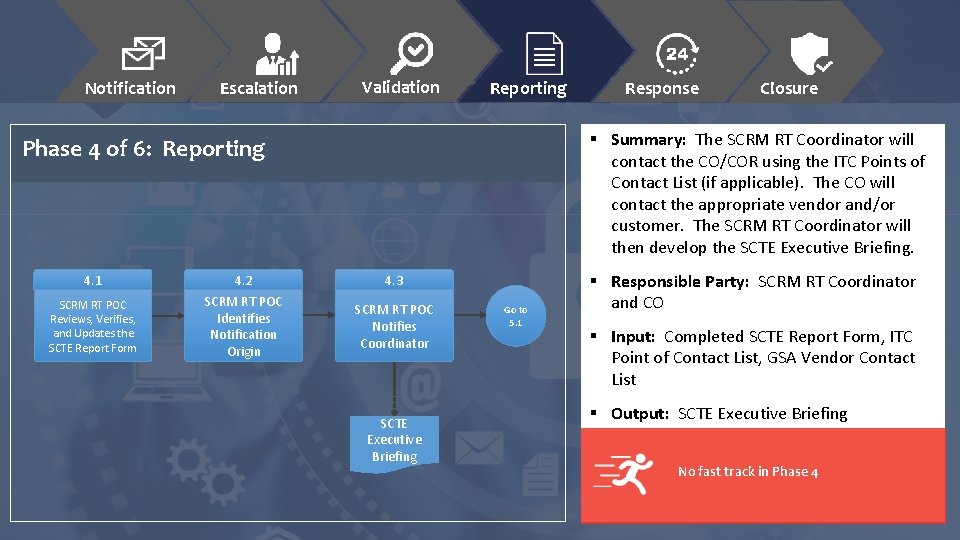
Notification Escalation Validation Reporting SCRM RT POC Reviews, Verifies, and Updates the SCTE Report Form 4. 2 SCRM RT POC Identifies Notification Origin Closure § Summary: The SCRM RT Coordinator will contact the CO/COR using the ITC Points of Contact List (if applicable). The CO will contact the appropriate vendor and/or customer. The SCRM RT Coordinator will then develop the SCTE Executive Briefing. Phase 4 of 6: Reporting 4. 1 Response 4. 3 SCRM RT POC Notifies Coordinator SCTE Executive Briefing Go to 5. 1 § Responsible Party: SCRM RT Coordinator and CO § Input: Completed SCTE Report Form, ITC Point of Contact List, GSA Vendor Contact List § Output: SCTE Executive Briefing No fast track in Phase 4

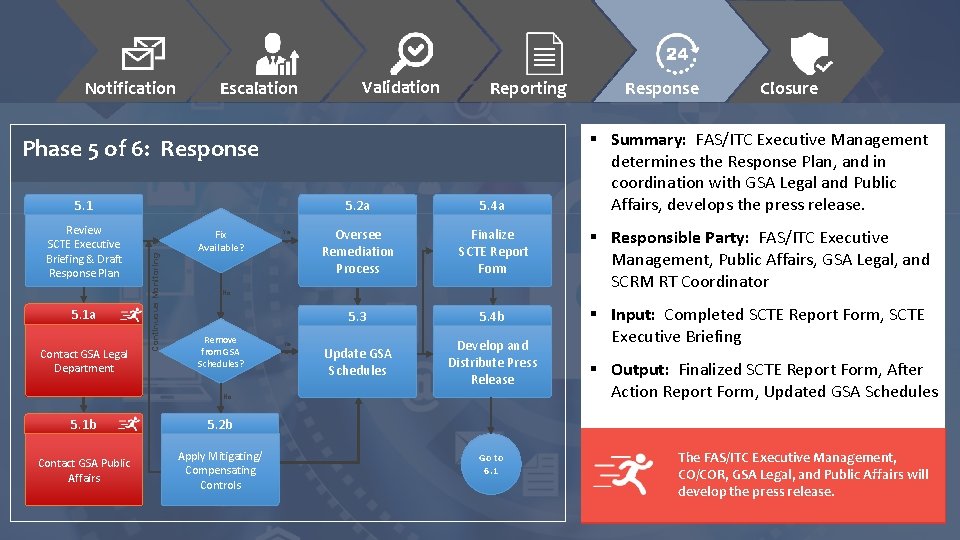
Notification Escalation Validation Reporting Phase 5 of 6: Response Review SCTE Executive Briefing & Draft Response Plan 5. 1 a Contact GSA Legal Department Continuous Monitoring 5. 1 Fix Available? Ye s 5. 2 b Contact GSA Public Affairs Apply Mitigating/ Compensating Controls § Summary: FAS/ITC Executive Management determines the Response Plan, and in coordination with GSA Legal and Public Affairs, develops the press release. 5. 4 a Oversee Remediation Process Finalize SCTE Report Form § Responsible Party: FAS/ITC Executive Management, Public Affairs, GSA Legal, and SCRM RT Coordinator 5. 3 5. 4 b Update GSA Schedules Develop and Distribute Press Release § Input: Completed SCTE Report Form, SCTE Executive Briefing No 5. 1 b Closure 5. 2 a No Remove from GSA Schedules? Response Go to 6. 1 § Output: Finalized SCTE Report Form, After Action Report Form, Updated GSA Schedules The FAS/ITC Executive Management, CO/COR, GSA Legal, and Public Affairs will develop the press release.

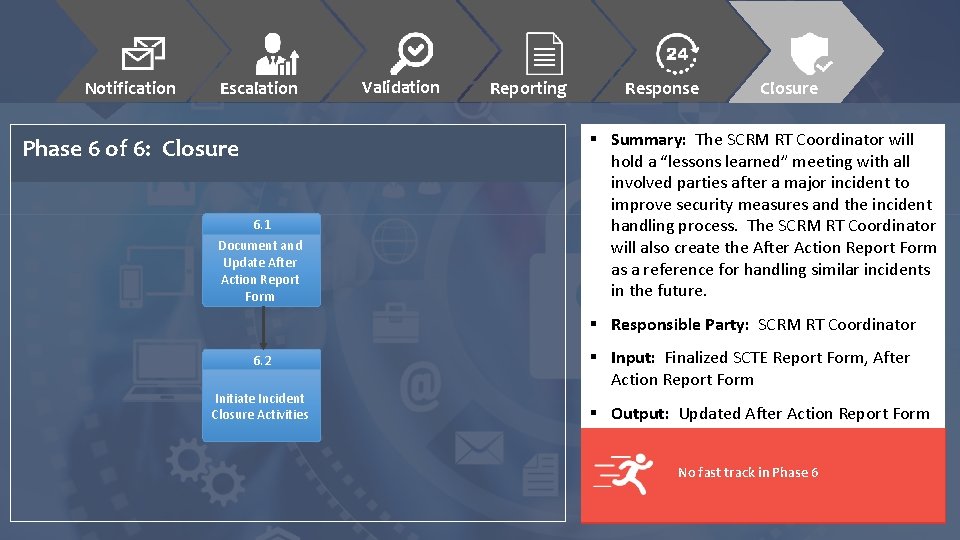
Notification Escalation Phase 6 of 6: Closure 6. 1 Document and Update After Action Report Form Validation Reporting Response Closure § Summary: The SCRM RT Coordinator will hold a “lessons learned” meeting with all involved parties after a major incident to improve security measures and the incident handling process. The SCRM RT Coordinator will also create the After Action Report Form as a reference for handling similar incidents in the future. § Responsible Party: SCRM RT Coordinator 6. 2 Initiate Incident Closure Activities § Input: Finalized SCTE Report Form, After Action Report Form § Output: Updated After Action Report Form No fast track in Phase 6

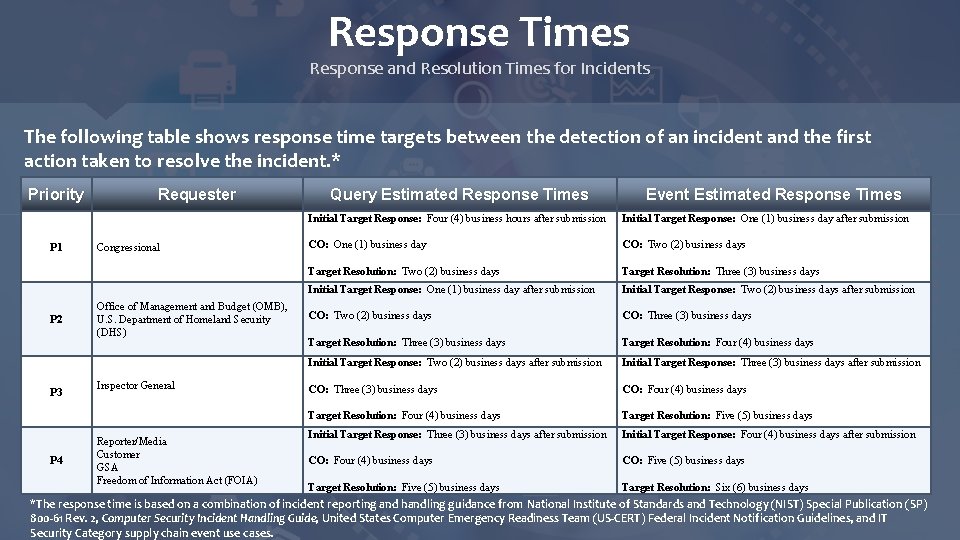
Response Times Response and Resolution Times for Incidents The following table shows response time targets between the detection of an incident and the first action taken to resolve the incident. * Priority Requester Query Estimated Response Times Event Estimated Response Times Congressional Initial Target Response: Four (4) business hours after submission CO: One (1) business day Target Resolution: Two (2) business days Initial Target Response: One (1) business day after submission CO: Two (2) business days Target Resolution: Three (3) business days Office of Management and Budget (OMB), U. S. Department of Homeland Security (DHS) Initial Target Response: One (1) business day after submission CO: Two (2) business days Target Resolution: Three (3) business days Initial Target Response: Two (2) business days after submission CO: Three (3) business days Target Resolution: Four (4) business days P 3 Inspector General Initial Target Response: Two (2) business days after submission CO: Three (3) business days Target Resolution: Four (4) business days Initial Target Response: Three (3) business days after submission CO: Four (4) business days Target Resolution: Five (5) business days P 4 Reporter/Media Customer GSA Freedom of Information Act (FOIA) Initial Target Response: Three (3) business days after submission CO: Four (4) business days Target Resolution: Five (5) business days Initial Target Response: Four (4) business days after submission CO: Five (5) business days Target Resolution: Six (6) business days P 1 P 2 *The response time is based on a combination of incident reporting and handling guidance from National Institute of Standards and Technology (NIST) Special Publication (SP) 800 -61 Rev. 2, Computer Security Incident Handling Guide, United States Computer Emergency Readiness Team (US-CERT) Federal Incident Notification Guidelines, and IT Security Category supply chain event use cases.

Summary Key Takeaways An effective SCRM RP is essential in protecting the integrity of the ITC supply chain as it relates to the products and solutions offered by GSA. As globalization increases, so do the critical interdependencies and complexities between suppliers, logistics providers, and a successful enterprise. A breakdown in any part of the supply chain connecting these entities can potentially lead to catastrophic consequences. Key Takeaways: � The SCRM RP is an ongoing process that benefits GSA most when both proactive and reactive approaches are executed. � The GSA SCRM RP process offers an efficient means to identify, assess, and mitigate supply chain threats while providing methods to avoid potential supply chain risks from materializing into an actual incident. � While supply chain risks cannot be fully prevented, the SCRM RP provides foundational preparatory processes, tasks, and activities to effectively manage supply chain incidents and reduce their potential impact.

Questions & Answers What would you like clarification on?

THANK YOU Thank you for attending this training session. Going forward, we hope you are able to utilize aspects of the program which were of particular benefit to your day-to-day work. We look forward to seeing you at our next session. Please feel free to share any comments you may wish to make about this or any future programs.

Contact Information For more information regarding SCRM RP activities or to learn more about the recommended security practices for ITC, contact Shon Lyublanovits (shondrea. lyublanovits@gsa. gov).

Backup Slides

Key Guidance Laws, Regulations, and Best Practices § Section 818 of Public Law 112 -81, National Defense Authorization Act for Fiscal Year 2012 (31 December 2011) Description: Public law for the detection and avoidance of counterfeit electronic parts § Do. D Instruction 4140. 67, “Do. D Counterfeit Prevention Policy” (26 April 2013) Description: Establishes policy and assigns responsibilities necessary to prevent the introduction of counterfeit material at any level of the Do. D supply chain; provides direction for anti-counterfeit measures for Do. D weapon and information systems acquisition and sustainment to prevent the introduction of counterfeit material; and assigns responsibilities for prevention, detection, remediation, investigation, and restitution to defend the Do. D against counterfeit material that poses a threat to personnel safety and mission assurance. § Defense Acquisition Guidebook (DAG), CH 3– 4. 3. 3 Anti-Counterfeiting Description: The Defense Acquisition Guidebook, Chapter 3, provides overarching guidance on the systems engineering discipline, its activities and processes, and its practice in defense acquisition programs which may be used by the Program Manager and the Systems Engineer to effectively plan and execute program activities across the system life cycle.

Key Guidance Laws, Regulations, and Best Practices (continued) § National Institute of Standards and Technology Interagency Report (NISTIR) 7622, Notional Supply Chain Risk Management Practices for Federal Information Systems (16 October 2012) Description: Provides a wide array of practices that, when implemented, will help mitigate supply chain risk to federal information systems. It seeks to equip federal departments and agencies with a notional set of repeatable and commercially reasonable supply chain assurance methods and practices that offer a means to obtain an understanding of, and visibility throughout, the supply chain. § NIST Special Publication 800 -161, Supply Chain Management Practices for Federal Information Systems and Organizations (08 April 2015) Description: Provides guidance to federal agencies on identifying, assessing, and mitigating ICT supply chain risks at all levels of their organizations. This publication integrates ICT supply chain risk management (SCRM) into federal agency risk management activities by applying a multi-tiered, SCRM-specific approach, including guidance on supply chain risk assessment and mitigation activities. § ISO/IEC 27036, Information technology — Security techniques — Information security for supplier relationships (Parts 1 -4; 2013 -2016) Description: Provides a broad focus on all supplier relations. Processes apply primarily to the sourcing and supply chain and the supplier relationships throughout.